
Award Winning World’s Fastest Growing Cybersecurity Company














The Best Ai-Powered Threat INtel PLATFORM
• Uncover hidden threats.

• Predict and prevent attacks.
• Empower informed decision-making.
• Stay ahead of evolving risks.
• Secure your digital ecosystem.
See Cyble Vision in Action















Editorial Management
Augustin Kurian Editor-in-Chief editor@thecyberexpress.com
Avantika Chopra Associate Editor avantika@thecyberexpress.com
Vishwa Pandagle Journalist vishwa@thecyberexpress.com
Ashish Khaitan Journalist ashish@thecyberexpress.com
Samiksha Jain Magazine Producer samiksha.jain@thecyberexpress.com
Ishita Tripathi Senior Tech Journalist ishita.tripathi@thecyberexpress.com
Rajashakher Intha Head - Marketing & Sales raj@thecyberexpress.com
Ashish Jaiswal Conference Manager ashish.j@thecyberexpress.com
Priti Chaubey Content Strategist priti.c@thecyberexpress.com

Ravi Gupta SEO Analyst ravi@thecyberexpress.com
Vittal Chowdry Design Lead vittal@thecyberexpress.com
This month is especially noteworthy as we commemorate the 20th anniversary of Cybersecurity Awareness Month (CSAM), an annual campaign of paramount importance, shedding light on the essential role of cybersecurity in our interconnected digital society. CSAM is a reflection of our commitment to fostering a deep and enduring awareness of the evolving challenges and opportunities in cybersecurity.
We believe CSAM acts as a beacon of vigilance, underlining the necessity for enhanced cybersecurity defenses in the face of relentless and evolving digital threats. This edition explores the sophisticated landscape of cyber threats and delves deep into incidents like the Colonial Pipeline and SolarWinds attacks, bringing forth the imperative need for heightened awareness and a proactive defense mechanism against the growing spectrum of cyber risks.
This meticulously curated edition features a series of enlightening dialogues with industry pioneers and thought leaders. My conversations with Juhani Hintikka, the President and CEO of WithSecure, and Ryan Davis, CISO at NS1, are laden with
profound insights into the dynamic field of cybersecurity, offering a nuanced understanding of the multifaceted challenges and the revolutionary impact of Artificial Intelligence on security landscapes.

In our exploration of innovative educational methodologies, we delve into the groundbreaking training modules by ELB Learning. A revealing conversation with John Blackmon, CTO of ELB Learning, introduces the challenges and solutions in overcoming the limitations of traditional learning methodologies, focusing on the enduring impact of active learning experiences in the field of cybersecurity.
We also navigate through the rising trend of teenage hacking, offering a comprehensive analysis of the instances involving young cyberprodigies. This exploration seeks to understand the intricate motivations driving young minds to the realm of cyber intrusions, and the subsequent repercussions and emphasizes the necessity to direct the innate curiosity and technical prowess of the youth toward positive and constructive avenues.
Furthermore, we delve into the intricate interconnection between space technology and cybersecurity. The edition scrutinizes the advancements and burgeoning investments in space exploration
and underscores the vital role of cybersecurity in maintaining the resilience and integrity of celestial assets. The intersectionality of space technology and cybersecurity is elaborated to highlight the significance of robust cyber defenses in the continually evolving realm of space exploration.
This edition is meticulously curated to serve as your guide through the multifarious terrains of cybersecurity. The rich insights, expert analyses, and comprehensive guides embedded in this issue are aimed at empowering our readers to traverse the maze of the cyber world with enhanced awareness and fortified resilience.
I invite you to immerse yourself in this enriching journey through the cyber frontier, hoping that the diverse array of topics and insights within these pages will act as a beacon, enlightening your path to enhanced cybersecurity awareness and resilience.
Most importantly, we welcome your feedback at editorial@thecyberexpress.com
Stay Informed, Stay Secure.
Augustin Kurian Editor in Chief The Cyber Express

With the news of Cricket leagues including the ICC World reaching people, scammers might target followers, members, and players who need to be alert of social engineering attacks.
- By Vishwa PandagleAs billions of fans gather in India to witness the muchawaited 13th edition of the ICC Men’s Cricket World Cup on October 5, 2023, cybersecurity experts face a significant challenge. Following the successful G20 summit in the first week of September this year, despite being targeted by hacktivist groups, it’s now crucial to safeguard the integrity of the ICC World Cup.
With fans from all over the world converging in India to cheer for their favorite teams, the cybersecurity community has a herculean task ahead. Throughout the 48 matches at nearly 10 venues, fans will flock to the Narendra Modi Stadium in Ahmedabad, India for the opening game. Scammers will attempt to exploit these enthusiastic spectators with enticing offers aimed at financial gain.

In the cybersecurity landscape of 2023, data breaches, often stemming from deceptive spearphishing emails, constitute nearly 90% of cyber attacks. Opportunistic scammers are quick to leverage crises, using them as opportunities to establish fraudulent websites and prey on unsuspecting individuals.
Even global sporting events have been hit by cyber attacks, with headlines frequently reporting data breaches exposing customer data online. For instance, CricketSocial, an online platform that provides cricket analytics and tournament data to fans, players, and authorities, was involved in one such event. An unintentional data leak revealed a database with approximately 100,000 client entries, including admin login info, emails, and hashed passwords. “Alongside the admin’s passwords and user PII the open instance also holds all of the content stored on the website,” stated a Cybernews report
The consequences of such breaches are far-reaching. Cybercriminals, armed with tools to exploit cricket data, pose a significant threat. The grandeur of events like the ICC World Cup, T20 World Cup, and IPL not only attracts passionate spectators worldwide but also invites cybercriminals.
In this digital age, where billions of fans unite to embrace the spirit of cricket, it’s crucial to bolster cybersecurity measures and prioritize data privacy to safeguard both the sport and its devoted enthusiasts. In this article, we’ll explore cricket cybersecurity, emphasizing the need for a proactive and collaborative effort to preserve the sport’s integrity and the security of its passionate followers.
Cricket has evolved into a vast
industry propelled by data and technology in the digital age, becoming more than just a sport. While the digital revolution has brought fans closer to the game than ever before, it has also created serious worries about data protection. Cricket organizations, like several other entities, collect and use personal information from spectators and players for a variety of objectives. However, mismanagement or leakage of this data can have serious implications not only for the players but also for the sport.
Collection of personal data and usage: Cricket organizations collect personal data from fans and players through ticket purchases, online merchandise orders, and social media interaction. This information includes names, addresses, contact information, and, in certain situations, financial information. The data is frequently used for marketing, targeted advertising, and improving fan experiences. For example, cricket websites may use cookies to track user activity and preferences to provide customized content.
Risk of data breach: Data breaches in cricket can have far-reaching consequences. In 2023, a data breach exposed the passport details of cricket icons and current stars such as Wasim Akram, Chris Gayle, Ian Bell, and Mohammad Babar Azam. Over 500 cricketers, including players from India, New Zealand, and Afghanistan, were affected by the breach, which was discovered by UK-based researcher Etizaz Mohsin, who also identified phone numbers and email addresses of players and their agents in the data. This case clearly shows that violations not only result in financial losses, but also degrade the reputations of the individuals involved and the sport itself. Fans may lose faith in the ability of cricket organizations to preserve their data.
Furthermore, the costs of data

breaches go beyond people. Cricket organizations also keep sensitive strategic data, player contracts, and financial records, making them appealing targets for fraudsters. The disclosure of such information may jeopardize the sport’s competitive balance and financial stability.
Cricket firms are prioritizing cybersecurity to reduce the risk of data breaches and comply with data protection rules. Individuals inside any organization, including cricket, are subject to privacy rules defined by the country’s data governing organizations. The ICC cricket website notifies users about data gathering techniques, such as IP addresses, browser type, time zones, and items viewed. This data is used for internal operations and statistical purposes, and it is shared with ICC affiliates.
The ICC adheres to the International Standard for the Protection and Privacy of Personal Information (ISPPPI) to ensure data security, particularly in conducting anti-doping programs aligned with privacy rights
The USA Cricket Privacy Policy collects user and player information for various purposes, including fraud prevention and research, utilizing Google Analytics for internal evaluation.
Personal data is retained only as long as necessary and then securely disposed of. The policy emphasizes that personal information of children under 13 is not collected without parental consent.

In New Zealand, cricket communities like Cricket Nation collect user information but exclude financial data. Sharing occurs with sporting initiatives and organizations as required by law. Users have the right to access their personal data. Addressing the correction of personal data by users, the portal read, “You are entitled to obtain confirmation of whether or not we hold any personal information about you and to obtain access to that information.”
The Kent County Cricket Club in the United Kingdom complies with data protection legislation, including the EU General Data Protection Regulation and the Privacy and Electronic Communications Regulations (PECR). Information collected is accessible to authorized entities such as health service providers and government organizations.
The Greater Manchester Cricket League (GMCL), working with the Lancashire Cricket Foundation and the England and Wales Cricket Board, collects data related to club support, player registration, complaints, and participant demographics for diversity monitoring.
These measures help cricket organizations and communities ensure data protection and cybersecurity while complying with regulations.
Cricket has the second-highest global audience of any sport, with the ICC Men’s Cricket World Cup, which is set to conclude in November 2023 and is set to bring together more than 1,000 nations and 4,200 players. This massive following, however, has made
it a great target for cyber scammers attempting to take advantage of cricket fans’ excitement.
Cricket’s huge attraction, spanning genders and decades, makes it a rich playing field for con artists. The sport’s popularity is as broad as it is large, with millions of followers. For instance, the 100-ball Cricket event in 2021 drew a sizable 21% female viewership, demonstrating its broad popularity. While England’s cricket enthusiasm accounted for 65% of spectators in several matches, India alone has 1.1 billion cricket fans
As the world excitedly awaits ongoing cricket matches and upcoming tournaments, cricketlovers throughout the world are preparing to participate in a variety of sports-related activities, such as purchasing online tickets, visiting to stadiums, acquiring souvenirs, and photographing memorable moments. Scammers, on the other hand, are well aware of these fan engagements and have begun creating fraudulent offerings such as counterfeit tickets, cloned websites, and alluring games with cricket-related incentives.
The ICC itself was the victim of a hoax, that led to a significant financial loss of around US$2.5 million. This shows scammers’ ever-changing techniques, which include social engineering attacks such as fake emails and attention-grabbing website pop-ups. Common online cricket scams include a variety of alluring hotel discounts, restaurant coupons, and shopping incentives, all designed to deceive naïve participants.

To stay away of cyber traps and prevent falling prey to cybercrime, individuals should take note of the following safety guidelines:
Cross-check with official websites: Make sure to visit official websites for all your cricket-related needs. Be wary of duplicated or cloned websites that lack complete material. Examine all webpages for legitimacy and the accompanying social media pages.
• Be cautious while sharing on social media: Use caution while sharing travel and personal information on social media platforms, especially with strangers who may be friends with you.
Be mindful of freebies: Be wary of free ticket scams that promise incentives for clicking on dubious websites, spinning wheels, or updating gadgets due to purported virus concerns. These are frequently used as traps for cybercriminals.

• Read emails carefully: Keep an eye on your email inbox. Malware can damage your browser data and provide hackers information about your online habits. If you receive unexpected emails advertising discounted Cricket-related products or services, it is most certainly a fraud. To improve security, change passwords and enable multi-factor authentication.
Cricket fans can assure a safer online experience by taking simple steps, protecting both their personal information and the integrity of the sport. Keeping in mind cricket’s global popularity, all users need to improve their defenses and keep cyber scammers at bay, allowing fans to enjoy their favorite game without falling subject to digital deception.

Cybersecurity Awareness Month across the globe brings together experts, and learners who share about success and experiences related to cybersecurity and encourage the spirit of cybersecurity.
- By Vishwa PandagleIn response to the growing threat of cyber attacks, governments worldwide are actively working to streamline cybersecurity efforts. Cybersecurity, for many, has been perceived as a complex realm of technical knowledge encompassing protection against scams, scammers, malware, ransomware, and software codes. In a concerted effort to simplify cybersecurity, government agencies have chosen “It’s Easy to Stay Safe Online” as the theme of Cybersecurity Awareness Month (CSAM) 2023.
While there is a plethora of educational resources available online to enhance digital safety, it can be daunting to navigate this environment while keeping up with the new dangers, threat actors, cybersecurity regulations, and policy changes. Therefore, the choice of this year’s theme supports the notion that cybersecurity may be made simple and accessible to everyone.

This year marks the 20th year of observing Cyber Security Awareness Month (CSAM) since its inception. The slogan of the 2022 CSAM was, “See Yourself in Cyber: Together We Make It Safer,” drawing parallels with the Olympics’ drive for unification, which gained notoriety during the COVID-19 pandemic-induced isolation. The International Olympics Committee introduced the “Stronger Together,” campaign, fostering a sense of unity and celebration of the Olympic spirit despite the challenges faced by participants.

Back in 2004, the President of the United States and Congress established an entire month to raise awareness about cybersecurity. Various agencies along with the Cybersecurity and Infrastructure Security Agency (CISA) partner with organizations to raise awareness. This program brought together various entities, including the CISA, partnering with organizations to amplify awareness efforts. This marked the pivotal collaboration between the government and the industry, aimed at reaching a larger audience and achieving maximum impact.
Notably, the National Institute of Standards and Technology (NIST), a government agency operating under the United States Department of Commerce, plays a significant role in hosting campaigns and workshops. For instance, the “Block Cipher Modes of Operation 2023,” which focuses on encryption standards, is one such advanced workshop.
IAS the United States marks the 20th year of championing Cybersecurity Awareness Month, the central theme revolves around the ongoing journey of security education and
heightened awareness. Throughout National Cyber Security Awareness Month (NCSAM) in the United States, a series of engaging activities and initiatives will take center stage.

In this October, the spotlight shines on four fundamental steps, carefully curated as part of Cybersecurity Awareness Month 2023 in the USA. All these steps have been designed to be simply remembered and implemented, acting as a barrier against misunderstanding and potential risks. A comprehensive study provided by the Cybersecurity and Infrastructure Security Agency (CISA) highlights these critical steps, underlining their importance not only during NCSAM but all year.
“Simple actions we should all take not only during Cybersecurity Awareness Month but every day throughout the year,” highlights the CISA report.
Let us dive into these four essential steps that the US encourages everyone to adopt:
• Creating a strong password – Using a combination of phrases, letters, numbers, and other characters, in conjunction with a trustworthy password manager, ensures robust protection. A password manager makes it easier to safely store several passwords.
• Embracing multifactor authentication – In an age when advanced hacking techniques like bruteforcing are used to crack common passwords, simple username and password combinations are no longer sufficient. Choosing multifactor authentication, which sends a one-time password to a device in
your possession, dramatically improves account security.
• Identifying phishing attacks –As proven by multiple incidents in the past few years, phishing remains a significant driver for successful data breaches. As a result, recognizing questionable emails from diverse sources, such as businesses, e-commerce sites, government agencies, and even friends, is critical. Crossreferencing their legitimacy on their own is an important strategy for avoiding potential risks.
– There have been numerous data breaches this year that may have been avoided with timely software updates. For instance, ransomware gang Clop breached hundreds of customer systems via a weakness in MOVEit File Transfer software, highlighting the significance of staying up to date.
With the collective efforts of the United States government and its agencies, this year’s Cybersecurity
Awareness Month 2023 looks poised for a huge success. Individuals and organizations alike are encouraged to join forces with CISA, volunteer their expertise, and participate in campaigns that promote cybersecurity. Those interested in knowing more about this initiative, can send emails to AwarenessCampaigns@cisa.dhs. gov and learn more about how to create their own awareness campaigns.
The Japanese government has designated February 1st to March 18th as Cybersecurity Awareness Month. During this campaign this year, Chief Cabinet member Matsuno Hirokazu expressed concerns about the enormous economic impact of ransomware on Japan during a press conference. Hirokazu emphasized the need for collective action, stating, “Together, let’s work on the improvement of cybersecurity with everyone’s participation.”
As part of Cybersecurity Awareness Month 2023, the Japanese government worked actively in close coordination with the worldwide community. This partnership included participation in the “Cyber Challenge Campaign,” a collaborative project of Quad members from Australia, India, Japan, and the United States aimed at improving global cybersecurity.
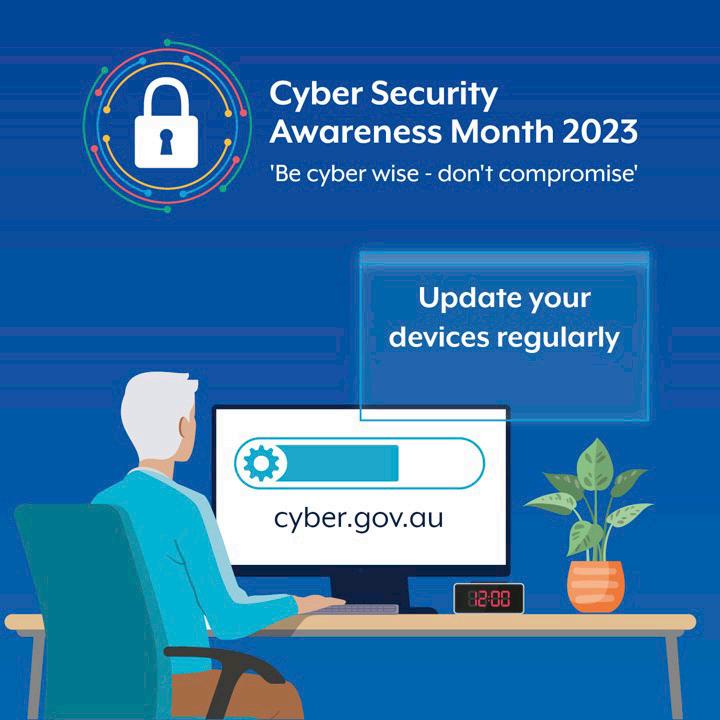

The theme for Cyber Security Awareness Month 2023 in Australia is, “Be Cyber Wise – Don’t Compromise.” Australian government agencies have made a wealth of resources and toolkits available to empower users in enhancing their online security.

The University of Queensland, in conjunction with the Australian Cybersecurity Awareness Month 2023 initiative, has outlined a comprehensive four-step plan for ensuring online safety. This year, they have dedicated each week to a specific cyber safety tip, mirroring the recommendations highlighted in US CASM 2023:
• Use strong passwords and password managers.
• Opt for multi-factor authentication.
• Take backup of important documents.
• Update device and software frequently.
They will be holding a workshop on keeping a personal password manager, and a webinar on phishing called, “Pavlov’s hackers… unleashing phishy tricks.” A panel discussion to protect data online will also be held.
Canada
Canada is all set to embark on a cyber journey with an interesting theme for this year’s Cybersecurity Awareness Month: “Step up your cyber fitness.” This theme, as described on the Government of Canada’s portal, encourages individuals and organizations alike to flex their cybersecurity muscles and take gradual, deliberate steps towards bolstering their digital defenses. “It’s all about stretching your cyber security muscles and taking things one step at a time,” reads a report published on the Government of Canada’s portal

Highlighting the significance of collective responsibility in addressing Cybersecurity Awareness Month 2023, the website offers several informative resources for those seeking knowledge in this domain. Drawing parallels between cyber fitness and personal wellbeing, the website aptly notes, “Just like starting a new fitness routine, finding the motivation to become your best, the most cyber safe self can be tough.” Active participation is encouraged, as underscored in the portal’s message: “The best way to raise awareness about cyber security is to have more organizations involved – and that includes yours!”
To become a part of this cyber-awareness movement, participants are required to follow these steps:
• Highlight the importance of Cybersecurity Awareness Month among employees within the organization.
• Use Canadian government’s pre-designed internal communication messages.
• Use hashtags like #CyberMonth2023, #GetCyberSafe, #Cyber and #CyberSecurity.
• Use co-branded social messaging and images from Canadian government toolkit to engage with audience.
• Collaborate and tag them in post to participate in conversations about cybersecurity by using @GetCyberSafe.
• Share the successes with the government for a stronger collective effort in cybersecurity awareness.
Every year, the European Union dedicates a month to cybersecurity awareness, known as European Cybersecurity Month (ECSM). Like its predecessors, ECSM 2023 promises a variety of exciting events, such as conferences, workshops, training sessions, and presentations. This effort is co-ordinated by the European Union Agency for Cybersecurity (ENISA) and the European Commission, with participation from not just government agencies but also think tanks, universities, and non-governmental organizations (NGOs).
The ECSM was founded in 2012, and its enduring motto, “Cybersecurity is a Shared Responsibility,” reflects a strong sense of solidarity. In 2022, the official slogan of the ECSM campaign was, “Think Before U Click.”
The theme for the European Union Cybersecurity Awareness Month 2023 is “Become a Cyber Hero,” highlighting the collective responsibility to enhance cybersecurity across the EU.
The ECSM sees the launch of cybersecurity initiatives in partnership with EU member states over the years, contributing to a considerable decrease in the success rate of cyberattacks.
While emphasizing the importance of European Cybersecurity Month in a press release, Juhan Lepassaar, the Executive Director of ENISA, stated, “The number of successful online attacks could be greatly reduced if more people knew how to detect and react. This is what the activities of the European Cybersecurity Month are all about.”
In today’s interconnected world, a seemingly minor cyber attack exploiting a software vulnerability has the potential to jeopardize not only individuals but also the critical infrastructure of entire nations. The simple act of installing updates can be the barrier that protects a complete system and its interconnected devices from the impending possibility of a security breach.
While Cybersecurity Awareness Month officially runs from October 1st to 31st, 2023, the need to be on the lookout for suspicious activity goes far beyond these days. Protecting our digital realm is a continual effort, one that is critical in an era marked by digitalization and reliance on constant connectivity.

 - By Ashish Khaitan
- By Ashish Khaitan
As we navigate the ever-changing digital landscape, the cybersecurity business has not only experienced unparalleled development but has also secured its status as one of the world’s fastest-growing sectors. In 2023, the projected revenue for the cybersecurity market stands at an impressive US$166 billion, with an expected annual growth rate of 10.48% from 2023 to 2028, culminating in a market volume of $273.60 billion by 2028.
Despite these amazing statistics, we must remain watchful as the alarming threat posed by hackers and cybercriminals remains large. In the year 2023 alone, a whopping 300,000 new instances of malware are developed every day, with a significant 92% of these dangerous entities being disseminated via email channels, with detection taking an average of 49 days.
The Cyber Express is here to serve as a complete guide on cybersecurity strategies for 2023 when it comes to a rapidly expanding threat. Our comprehensive guide is intended to provide you with the knowledge and resources you need to safely and securely navigate the digital landscape throughout the year. So, let’s dive in and learn how to remain safe in this digital age:

From its status as an external facet, cybersecurity has evolved into the core of organizations. Regardless of size, geographical location, or business model, every organization requires protection. The proliferation of online hackers has now reached a point where they can mobilize their private armies, potentially influencing governmental stability and even inciting international unrest.
In this context, the world is calling for cybersecurity as a necessity. This presents a unique opportunity to invest in and cultivate this domain, as the viability of companies now hinges upon it. A survey conducted by the Deloitte Center for Controllership reveals that 34.5% of polled executives reported that their organizations’ accounting and financial data fell prey to cyber adversaries in the past year.
These cyber attacks are not only on the rise but are also growing in sophistication with each passing day. In 2023, artificial intelligence and open-source tools have emerged as new breeding grounds for hackers. While AI and machine learning excel in research and analytics, they can also be exploited by hackers for advanced attacks. Already, deep fakes are in use, and bots continue to proliferate. Moreover, the geopolitical consequences of events like the Russian invasion of Ukraine have highlighted critical infrastructure vulnerabilities to nation-state threats, including an increase in Distributed Denial of Service (DDS) attacks on websites and infrastructure.
Here are the top five reasons explaining the significance of cybersecurity in 2023 and why
adhering to security best practices is imperative:
The rapid pace of digital transformation across industries has been a defining feature of recent times. From remote work setups to cloud-based operations, organizations have embraced technology to enhance productivity and efficiency. While this shift has brought numerous benefits, it has also opened up new attack vectors for cybercriminals. Protecting these digital ecosystems is vital to ensure the continuity of operations and the confidentiality of sensitive information.
Cyber threats have evolved to an unprecedented level of sophistication. Today’s cybercriminals employ advanced techniques such as artificial intelligence (AI), machine learning (ML), and social engineering to breach even the most fortified defenses. The rise of state-sponsored hacking groups and organized cybercrime syndicates further underscores the gravity of the threat landscape. Robust cybersecurity measures are essential to detect and mitigate these sophisticated attacks.
The proliferation of connected devices through the Internet of Things (IoT) has exponentially expanded the attack surface for potential cyber threats. Smart homes, industrial control systems, and medical devices are now interconnected, providing more entry
points for cybercriminals. These devices can become vulnerable targets without robust cybersecurity measures, potentially compromising privacy, safety, and even public infrastructure.

With the enactment of data privacy regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), organizations are legally obligated to protect the personal information of their users. Non-compliance with these regulations can result in severe financial penalties and reputational damage. Consequently, investing in cybersecurity measures is both a best practice and a legal requirement.
Ransomware attacks have emerged as one of the most devastating threats in recent years. Cybercriminals use malicious software to encrypt critical data, demanding a ransom for its release. The financial and reputational consequences of falling victim to a ransomware attack can be crippling for businesses. Furthermore, in 2023, we are witnessing an uptick in extortion-based attacks, where sensitive data is stolen and threatened to be released unless a ransom is paid.

A recent survey conducted by Yahoo Finance has unveiled a startling statistic: a staggering 78% of respondents believe that their organization’s security measures require immediate attention. Even more concerning, approximately 43% of companies openly admit to having inadequate cyber defenses in place. Considering these revelations, businesses must take proactive steps to fortify their cybersecurity defenses and equip their experts with specialized training.
To begin, consider implementing an additional layer of protection for your organization through innovative services such as Cyble Vision. This cutting-edge platform offers a unified view of your organization’s external threat landscape by collecting and consolidating intelligence from the dark web, deep web, and surface web. By harnessing the power of comprehensive threat intelligence, businesses can gain a critical edge in anticipating and countering potential cyber adversaries.
Beyond these strategic measures, there are practical actions that employees can take to fortify your organization’s defenses. Here are ten crucial steps for bolstering your cybersecurity:

1. Keep software updated: Regularly updating operating systems and applications is paramount. These updates often include patches for known vulnerabilities. Enable automatic updates to ensure you’re consistently running the latest, most secure software versions across your computer’s operating system, web browsers, office suites, and antivirus programs.
2. Use strong and unique passwords: Employing robust, distinctive passwords represents one of the most fundamental yet effective cybersecurity practices. A strong password should consist of a minimum of 12 characters, comprising a blend of uppercase and lowercase letters, numbers, and special symbols. Avoid using easily guessable information like birthdays or common words. Consider utilizing a reputable password manager to generate and securely store complex
passwords for all your accounts.
3. Enable two-factor authentication (2FA): 2FA provides an additional layer of security by necessitating a secondary form of authentication. This could involve a temporary code sent to your mobile device or generated by a dedicated app. With 2FA, unauthorized access remains highly unlikely, even if your password is compromised.
4. Regularly backup data: Ensure that critical data is consistently backed up to prevent loss in the event of a ransomware attack or hardware failure. Employ a combination of on-site and cloud-based backups for added redundancy. Periodically test your backups to ensure data restoration is seamless when needed.
5. Implement firewalls and antivirus software: Firewalls serve as a protective barrier between your network and potential online threats. Both hardware and software firewalls are essential for filtering incoming and outgoing traffic. Robust antivirus software aids in
detecting and removing malicious programs, adding an extra layer of defense against malware.
6. Educate employees about cybersecurity: Imparting cybersecurity training to employees is essential for creating a secure work environment. Conduct workshops and seminars to raise awareness about potential threats, best practices for online safety, and the ability to recognize phishing attempts. Foster a culture of vigilance where employees promptly report any suspicious activity.
7. Implement Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS and IPS solutions actively monitor network and system activities for malicious or suspicious behavior. IDS alerts you to potential threats, while IPS can take automated action to block or prevent these threats from executing.
8. Conduct security audits and vulnerability assessments: Regular security audits and vulnerability assessments helps uncover potential weaknesses in your systems and networks. This proactive approach allows you to address vulnerabilities before cybercriminals can exploit them.
9. Monitor for anomalies: Utilize security information and event management (SIEM) systems to monitor network traffic, identify unusual patterns, and receive alerts for potential security incidents. These systems
provide real-time visibility into your network, enabling prompt responses to any suspicious activity.
10. Stay informed about emerging threats: Stay abreast of the latest cybersecurity threats and trends by following reputable cybersecurity news sources and forums. Understanding the evolving threat landscape empowers you to adapt your security measures accordingly.

In an era where cybersecurity has become the foundation of organizational resilience, the necessity for vigilance cannot be underscored. The everchanging world of cyber threats, combined with the ever-expanding digital realm, necessitates that we be vigilant in protecting our data and operations. By implementing these critical measures and remaining vigilant to emerging dangers, we not only strengthen our organizations but also contribute to the overall security of our linked globe.

 - By Ishita Tripathi
- By Ishita Tripathi
The world of cybersecurity is constantly evolving, with cybercriminals developing new and sophisticated methods to exploit vulnerabilities and steal data. As a result, cybersecurity awareness is more important than ever before. This year marks the 20th anniversary of Cybersecurity Awareness Month (CSAM), an annual campaign to raise awareness about the importance of cybersecurity and encourage individuals and organizations to take steps to protect themselves from cyber threats.
The campaign comes at a time when cyberattacks are on the rise. In a decade, we have seen several high-profile attacks, including the Colonial Pipeline ransomware attack, the SolarWinds hack, and the Microsoft Exchange hack. These attacks demonstrate the need for everyone to be aware of the cybersecurity risks they face and to take steps to protect themselves.

The digital age has been a constant battleground in the cybersecurity world, with cybercriminals continually refining their tactics to exploit vulnerabilities in our ever-expanding digital universe. According to Cybersecurity Data by Getastra, there is an attack every 39 seconds, with an estimated 2,200 attacks per day. The average cost of a data breach in the US$9.44 million, and cybercrime is expected to reach US$8 trillion globally by 2023. These statistics from the University of North Georgia’s report underscore the pressing need for a pervasive culture of cybersecurity awareness and stand as a sobering reminder of the enduring risks that organizations face.

Let’s delve into some of the most momentous cyberattacks that have indelibly shaped our digital landscape over the past decades.
1990s:
• The Melissa Virus: In 1999, programmer David Lee Smith unleashed the Melissa Virus, which wreaked havoc by luring users into opening a seemingly
innocuous Microsoft Word file. The virus quickly spread, affecting several businesses, including Microsoft itself, and causing extensive damage that cost an estimated US$80 million to repair.
• NASA Cyber Attack: Around the same time, 15-year-old hacker James Jonathan accomplished a startling feat by taking control of NASA’s computers and shutting them down for 21 days. The brazen attack resulted in about 1.7 million software downloads, costing NASA approximately US$41,000 in repairs.
2000s:
• Estonia Cyber Attack: In April 2007, Estonia was subjected to what is believed to be the first national cyberattack. The hack, which targeted 58 Estonian websites, disrupted many services, including those of the government, banks, and media.
• Sony’s PlayStation Network Breach: A major security breach on Sony’s PlayStation Network in 2011 resulted in the compromise of 77 million users’ personal data. This event exposed the
vulnerability of online gaming platforms and highlighted the necessity of effective cybersecurity controls to protect user information.
2010s:
• Stuxnet: The development of a virus called Stuxnet, which was discovered in 2010, targeted industrial control systems. It wreaked havoc on Iran’s nuclear program, infecting over 200,000 computers and physically damaging 1,000 pieces of equipment. Stuxnet is believed to be the first instance of a cyberweapon being used to influence the physical world.
• Yahoo Data Breach: In 2013, Yahoo announced a major data breach that exposed the personal data of over 3 billion users. This incident served as a stark reminder of the widespread impact of cyberattacks, especially when popular email platforms are compromised.
• Adobe Cyber Attack: The Adobe cyber-attack in the same decade compromised the data of up to 38 million users. This attack revealed how sophisticated
cybercriminals have become and their ability to hack even large organizations.
• Ukraine’s Power Grid Attack: The first known cyberattack on a power grid occurred in Ukraine in 2015, knocking out power to half of a region’s households for several hours. This incident highlighted how critical infrastructure can be vulnerable to cyberattacks.
2020s:
• WannaCry Ransomware Attack: In 2017, the WannaCry ransomware attack affected over 200,000 systems in over 150 countries. The attack’s catastrophic global remediation cost of approximately £6 billion highlights the financial devastation ransomware can inflict on a wide range of businesses.
• Colonial Pipeline Ransomware Attack: The Colonial Pipeline ransomware attack in 2021 led to major gas shortages and anxiety over the fuel supply. This incident serves as a stark reminder of the power infrastructure’s vulnerability and potential real-world consequences.
• RockYou2021 Password Leak: In June 2021, the RockYou2021 attack exposed approximately 8.4 billion passwords, making it the largest password leak since the RockYou website breach in 2009. This incident served as a reminder of the ongoing threat of data breaches and the necessity of stronger password security measures.
Amid the vast ocean of digital peril, Cybersecurity Awareness Month emerges as a beacon of hope. National Cybersecurity Awareness Month (NCSAM) is an annual, month-long public awareness campaign initiated by the US Department of Homeland Security (DHS) each October. This pivotal program serves a dual purpose: it illuminates the path of cybersecurity best practices and underscores the need for collaboration in thwarting cyberattacks and scams.
Origin: The origins of this initiative can be traced back to 2004, when US President George W. Bush declared October to be National Cybersecurity Awareness Month. During this time, the public and private sectors, as well as tribal communities, work together to raise awareness about the importance of cybersecurity.
Purpose: National Cybersecurity Awareness Month emphasizes the criticality of cybersecurity awareness. It serves as a vital resource for educating consumers, businesses, and governments about emerging threats, best practices, and the importance of protecting sensitive data. Importantly, it empowers these organizations to defend their digital infrastructure against the ever-evolving landscape of cyberattacks.


Cybersecurity Awareness Month (NCSAM) helps to raise awareness of cybersecurity threats and best practices among individuals and organizations. Here are some success stories in which awareness helped to prevent major cybersecurity breaches with the help of Information Sharing and Analysis Centers (ISACs):
A major vendor detected chatter about a new Java Script Remote Access Tool (RAT) and tied it back to a spear-phishing campaign. They notified three other major retailers, who in turn alerted their suppliers. This information was also shared with an ISAC, which found that the malware was targeting up to 30 retailers.
• A large financial services provider detected an internal IP address attributed to an advanced persistent threat (APT) actor that they had been aware of for years. They tasked their ISAC to reach out to law enforcement, who confirmed that the actor was still using the same IP address. The enterprise was able to defend itself from the attacker and update its threat models.
• An ISAC unrelated to aviation received an advisory related to a malware campaign targeting the country’s aviation infrastructure. They shared this information with their members, who were able to use it to protect themselves from the campaign.
• An ISAC received a tip about a government feed that had been compromised and was being used to send malicious emails to members who used certain online streaming devices. The ISAC was able to work with the hardware manufacturer to identify and fix the supply chain issue.
As we mark the remarkable milestone of 20 years of Cybersecurity Awareness Month, it is important to reflect on the significant strides made in security education and awareness over this period. We must also look ahead to the path that lies ahead as we strive to create a safe, secure, and interconnected society.
The National Cybersecurity Alliance (NCA) and the Cybersecurity and Infrastructure Security Agency (CISA)
have formed a formidable team, harnessing their collective resources and knowledge to provide guidance and information to businesses. These resources serve as a wellspring of inspiration for enterprises as they engage in vital discussions about online security with their employees, clients, and affiliates.
Here are some major cybersecurity milestones from the National Institute of Standards and Technology (NIST):
• 1977: Published the first data encryption standard
• 1997: Developed the principles of role-based access control
• 1999: Created the National Vulnerability Database
• 2008: Issued recommendations for supply chain security
• 2014: Released the NIST Cybersecurity Framework

These milestones have helped to make the internet a safer place for everyone.
In 2023, we celebrate the 20th anniversary of Cybersecurity Awareness Month, a testament to two decades of unwavering dedication to protecting our digital world. CISA has launched a revolutionary awareness campaign to mark this milestone, promoting four basic yet powerful techniques that anyone can use to improve their internet security:
• Be CyberSmart: Make smart choices online to protect yourself from cyber threats.
• Use Strong Passwords: Create and use strong passwords to keep your accounts safe.
• Enable Multi-Factor Authentication: Add an extra layer of security to your accounts by enabling multi-factor authentication.
• Keep Your Software Up to Date: Install software updates as soon as they are available to patch known vulnerabilities.
By following these four simple steps, you can help to protect yourself and your loved ones from cyberattacks.
During Cybersecurity Awareness Month, the Cybersecurity and Infrastructure Security Agency (CISA) launched a new initiative to boost the country’s cybersecurity workforce. The Cyber Careers Pathway Tool, which includes microchallenges, is designed to guide people towards careers in cybersecurity, regardless of their experience level.
The 14 micro-challenges expose learners to 10 different technical roles related to core job functions, such as Technical Support Specialist, Cyber Defense Analyst, and Database Administrator. The self-paced or guided challenges empower learners to take action on key cybersecurity tasks while providing information about learning and career paths. Users can explore an interactive educational environment and acquire detailed knowledge about specific cybersecurity work roles, as well as related educational, training, and job opportunities.
“CISA’s commitment extends beyond the current cyber workforce; we’re passionate about growing the future of the profession,” acting CLO Chris Lein said in the statement. “That means making sure the K-12 population understand how dynamic this field is, what “CISA’s larger mission is to develop a deep bench of top tier cybersecurity talent that can address the ever-changing needs of our cybersecurity workforce,” said Lein.
The micro-challenges align closely with the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework and offer insight into the many different pathways in the cybersecurity field. CISA is laying out the responsibilities of essential cyber jobs to help individuals see those positions within reach and imagine a place for themselves in the cyber workforce, fortifying America’s cyber defenses today and tomorrow.
As our world becomes more connected digitally, NCSAM becomes more important than ever before. The exponential increase in cyber threats underscores the need for organizations to be aware of them and take proactive steps to protect themselves.
As the industry evolves, we can expect to see more and smarter AI-based threat detection, widespread growth of cyber hygiene practices, and an increasing focus on IoT security. All stakeholders must play a role in NCSAM, making cybersecurity a primary concern in their digital lives and remaining alert for new threats. Ensuring the security of our online world requires community response and constant attention.


In a captivating conversation between Augustin Kurian, the Editorin-Chief of The Cyber Express, and Juhani Hintikka, President and CEO of WithSecure, a wide range of relevant cybersecurity topics were discussed,
shedding light on the field’s dynamic nature, nuanced approaches to security, and the challenges posed by the constant evolution of hacking techniques.



Hintikka passionately advocates for the integration of security measures into the very fabric of a company’s foundational processes. He stresses the importance of perceiving security not as an optional addition, but as a fundamental core component. At the heart of this philosophy lies the recognition that humans, being inherently prone to errors and oversights, are essential elements within the security infrastructure. Hence, striking a balance between trust and vigilance within organizational ecosystems is paramount.
Delving deeper into the organizational aspects, Hintikka highlighted the paradox inherent within the cybersecurity sector— the natural inclination toward distrust. Building trust within organizations and extending it to customers and partners presents a formidable
challenge, given the inherent skepticism that characterizes this profession. Leveraging its Finnish heritage, WithSecure embraces a national legacy renowned for its high levels of trust. The aim is to foster associations marked by reliability and integrity, which are invaluable in nurturing international collaborations.
The conversation further delves into the empowerment and evolution of hackers, with Hintikka shedding light on the metamorphosis of ransomware gangs into credible brands. This remarkable empowerment of these entities is attributed to their ability to amass funds through ransomware payments, a phenomenon significantly facilitated by the emergence and proliferation of cryptocurrencies. The concept of “cybercriminal unicorns” underscores the speculative market value of these increasingly potent hacking groups, derived from the enhanced value and ease of cryptocurrency transactions.
When delving into the aftermath of ransomware attacks, Hintikka sheds light on the pressing dilemma that companies often find themselves grappling with - should they comply with the ransom demands or stand firm in defiance? Unfortunately, the lack of robust preventive measures frequently leaves these organizations with little recourse but to accede to the demands of cybercriminals. What’s particularly intriguing is that these criminal groups are not oblivious to the importance of upholding their “brand reputation.” Hence, they often ensure data recovery as a gesture of goodwill following the ransom payments, further complicating the ethical landscape.
In tackling this quandary, WithSecure has charted a distinct course, advocating for proactive security postures and developing innovative solutions, such as Outbreak Control, which proactively detects and mitigates the impact of ransomware
attacks. However, the pursuit of absolute security remains elusive, as the inevitability of vulnerabilities and loopholes persists in the ever-evolving threat landscape.
While the notion of completely eradicating ransom attacks may seem like a Herculean task, Hintikka remains steadfast in his belief that unity and collective efforts within the security community can serve as formidable countermeasures against these prevailing threats. Embracing collaboration and strategically directing outcome-oriented security investments represent pragmatic avenues to bolster defenses and thwart the sophisticated arsenal of hackers.

The wisdom shared in this interview underscores the critical importance of adopting a holistic approach to cybersecurity. This approach involves blending trustbuilding mechanisms, intrinsic security integrations, and collaborative efforts to effectively navigate the complex landscape of cybersecurity. Hintikka’s philosophies represent a transformative shift in how we address cybersecurity challenges, potentially leading to a future where security professionals and hackers can find a harmonious and secure coexistence.
Hintikka emphasizes the significance of outcome-based cybersecurity, focusing on identifying and safeguarding critical components and processes within companies. This approach ensures minimal disruptions and zero data loss, essentially creating a fortress around business operations.
While this approach undoubtedly benefits larger enterprises, the concern arises for smaller companies, which constitute a substantial 40% of today’s business landscape. Many of them believe that such robust cybersecurity is out of their reach due to limited resources. However, Hintikka reassures us that the core security solutions offered are not mere tools; they represent a partnership. They provide essential automated means to counter and protect against threats while offering services to manage these systems. The round-the-clock monitoring service ensures comprehensive security solutions tailored to the diverse needs of mid-sized businesses.
The merger of WithSecure and F Secure demonstrates a keen focus on the B2B market, leveraging world-class technology to bring affordable cybersecurity to the midmarket. With 125,000 of their 135,000 customers in the mid to small category, WithSecure is a notable player in this segment. Their strategy is highly differentiated for larger enterprises, offering a plethora of products and services across the board, with an emphasis on software and services.
The evolving landscape of phishing attacks, with AI now playing a central role in crafting malicious emails, presents a growing challenge for detection. Hintikka envisions a future battle of “good AI vs. bad AI,” with a focus on anomaly
detection and defensive AI. With 18 years of investment in AI and machine learning, the company has developed capabilities to adapt defenses and counter advanced threats. The concern, however, lies in the malicious use of AI, necessitating heightened AI defenses to detect nuanced threats, particularly in the context of AI-generated mutated malware.
The alignment of WithSecure’s solutions with business objectives exemplifies a paradigm shift in cybersecurity approaches. The company’s commitment to delivering affordable, world-class technology to mid-sized enterprises, along with their evolving defenses against advancing AI threats, plays a crucial role in our rapidly changing environment. Their focus on providing more than just tools, fostering a partnership that empowers businesses to counter threats while receiving the necessary support to run these systems, ensures a balanced blend of autonomy and assistance.
WithSecure’s adeptness in addressing challenges, especially in the evolving AI landscape, highlights their forwardthinking approach and dedication to providing robust solutions. Their journey to seamlessly integrate advanced technologies, personalized services, and ongoing innovation is essential for navigating the intricate cybersecurity terrain. This approach safeguards businesses from everevolving threats and ensures a secure digital future for all. Their evolving defensive strategies, investment in AI, and commitment to affordable security solutions make WithSecure a beacon of progress and resilience in the cybersecurity landscape.
Finally, the fundamental revelation is the intricate and multifaceted nature of cybersecurity. It is patently evident that cybersecurity is no longer a secondary concern, but rather a critical component of organizational strength.

Security applications that are linked with human expertise are crucial, stressing the intersection of trust and alertness within organizational structures. This is especially important in an era characterised by widespread skepticism and the inherent paradox of trust in the cyber sphere.
This detailed discussion emphasizes the importance of balancing security, trust, and technical advancement. The emphasis on a comprehensive, integrated, and trust-centric approach to security marks a paradigm changes in cybersecurity concepts. This viewpoint emphasizes the critical combination of security measures, trust-building methods, and innovative technology in navigating the complex modern cyber ecology. These insights have the potential to drive future cybersecurity tactics and solutions.


 - By Augustin Kurian
- By Augustin Kurian
The advent of artificial intelligence (AI) heralds a significant transformation, poised to redefine industries, human interactions, and problem-solving methodologies. In an insightful conversation between Augustin Kurian, Editor-in-Chief of The Cyber Express, and Ryan Davis, Chief Information Security Officer at NS1, the profound implications and evolutionary trajectory of AI were brought to the forefront.
With over 15 years of experience in IT and security management, Davis elucidates that the unfolding AI revolution presents both challenges and abundant opportunities. AI is on track to replace or augment certain jobs within the next 5 to 15 years. However, this transformation serves as a conduit to human progression, enabling us to tackle more intricate problems and streamline fundamental processes through technological advancements.
At its core, AI revolves around pattern recognition— utilizing algorithms designed to emulate and enhance human cognition and capabilities. The imperative here is not to strive for perfection but rather to focus on progress, evolution, and the mitigation of inherent and lurking cyber risks. Delaying acceptance and adaptation to AI only serves to benefit malicious entities, propelling them forward in this technological race.
Davis’s journey into cybersecurity commenced at the tender age of three. Growing up in the 80s, his early exposure to computers fueled his curiosity, propelling him into the realms of exploration, understanding, and even circumvention of computer systems. This initial dalliance with computers evolved into a deep-seated passion and unwavering commitment to cybersecurity. Ryan’s professional journey led him to prestigious institutions such as MIT Lincoln Laboratories, and his experience spans work with the Department of Defense, culminating in his current role at NS1.


The significance of AI lies in its capacity to redefine industries, reminiscent of the Industrial Revolution and the advent of the internal combustion engine. Ryan posits that AI is the harbinger of a fundamental societal and human operations shift. The choice is stark—we either embrace or reject AI, and the repercussions are profound.
Deepfakes serve as a stark illustration of AI’s dual nature, capable of crafting convincing counterfeit content that blurs the line between reality and fiction. In the realm of security, the decision boils down to embracing AI or courting failure by turning a blind eye to its existence. AI integration is an inevitability, demanding a balanced approach from security experts who must continuously assess the associated risks and rewards. The stance on AI is not fixed; it evolves in tandem with the ever-changing technological landscape.
Davis underscores that his primary mission is risk mitigation. With AI permeating our technological landscape, the strategy is to establish guardrails. This involves setting expectations and protocols for AI utilization, safeguarding intellectual property rights, and fortifying against vulnerabilities. It’s about charting a structured and secure course that aligns with human behavior while enabling the safe harnessing of technology’s power without exacerbating inherent risks.
Davis, on the other hand, approaches new technologies with optimism, believing that despite their potential for harm, there is inherent good to be derived from them. He envisions an AI revolution unfolding in the next 5 to 15 years, during which entire job landscapes may be reshaped or augmented by AI. This transformative period offers humanity unprecedented opportunities to address both new and longstanding challenges as technology delves deeper into fundamental issues.
He further highlighted that the deployment of AI not only promises innovative solutions but also demands a revaluation of our problem-solving approach. The convergence of human intelligence and technology could unlock uncharted potential for tackling challenges previously deemed insurmountable.
Yet, the monumental impact of AI comes with inherent risks and uncertainties. The ongoing rapid development and integration of AI across various sectors necessitate careful consideration of its ethical implications, the establishment of robust regulatory frameworks, and perhaps even the creation of new governance models.

The discussion delved deeper into the realm of critical infrastructure, an area where Davis boasts extensive experience. The focal point revolved around the protective measures now in place within the medical infrastructure. Until recently, security was often an afterthought—a ‘nice-to-have’ rather than a necessity. However, the tides are changing. Security is now integral and indispensable, not just for governments but for everyone.
Davis stressed that regulatory bodies have come to recognize the paramount importance of security. With the introduction of regulations such as General Data Protection Regulation (GDPR) and Central Consumer Protection Authority (CCPA), there has been an intensified focus on safeguarding personal data. However, the advent of AI necessitates a more profound examination within regulatory frameworks, particularly considering AI’s capacity to generate content that could compromise individual identities.
The potential misuse of AI-generated content raises crucial questions about personal identity and privacy, bringing to the forefront issues that current regulations have yet to address. Furthermore, concerns linger regarding the deployment of AI in critical infrastructure, a domain that has received limited scrutiny concerning the implications of AI.

Davis delved deeper into the conversation, shedding light on both its impressive strides and underlying pitfalls. Notably, he highlighted the swift progress in AI, citing innovations like ChatGPT as prime examples of technological advancement. The AI’s capacity to craft entire lesson plans serves as a testament to its transformative potential. However, nestled within these technological marvels are fallacies that beckon caution. A society that leans heavily on AI for information and decision-making may encounter formidable challenges if these AI systems churn out biased or factually incorrect data.
Davis’s reflections extend beyond the confines of AI itself, drawing intriguing parallels with the evolution of Wikipedia during the late ‘90s and early 2000s. During its nascent stages, Wikipedia faced skepticism primarily due to its open-source nature. Over time, however, the platform adopted governance structures, trusted editors, and rigorous fact-checking mechanisms, ultimately earning credibility among its users. In stark contrast, AI currently lacks such robust governance, resulting in a lingering cloud of mistrust and skepticism that hampers its seamless integration into society.
As the conversation progressed, Davis underscored the urgent need for the industry to set standards and expectations to govern the use of AI, especially in critical infrastructure. Given the slow-paced evolution of government regulations, industries should proactively define operating standards and agree upon the ethical use of AI.
Davis highlighted the pressing need for government interventions and regulations surrounding Artificial Intelligence (AI). He noted that it’s high time for government bodies to institute regulations around AI, echoing the sentiments of companies like OpenAI, which recently advocated for policies to govern AI development and utilization.
In addition, Davis pointed out the crucial significance of the ongoing dialogue about AI regulation, highlighting the fact that even CEOs have testified before Congress about its urgency. Nevertheless, he expressed deep concerns about the limited understanding of the technology exhibited by many politicians. Davis emphasized that industries and cybersecurity professionals must take the lead in shaping the discourse on regulatory frameworks due to their familiarity with the potential risks associated with emerging technologies.
Drawing parallels with previous revolutionary technological advancements, Davis recounted the historical shifts in computing, from mainframes to distributed computing, and reflected on the cyclical nature
of technological progress. He underlined that the experiences of security professionals offer invaluable insights into proactively identifying and mitigating potential pitfalls associated with this groundbreaking technology.

Turning our focus to a critical facet of cybersecurity, Davis delves into the evolving reputation and organizational frameworks of ransomware groups. He highlights a notable trend where these criminal syndicates are gaining recognition for their reliability in promptly releasing data once the ransom is met.
Davis points out the intriguing shift in trust dynamics, with businesses increasingly inclined to comply with ransom demands, placing faith in the “reliability” of these unlawful organizations. Notably, some affected companies seek advice from previous victims, often learning that the transactions were straightforward, with data returned upon payment.
This emerging landscape, where trust is bestowed upon criminal entities, presents a complex challenge. Companies often perceive payment as the quickest resolution to such predicaments. However, Davis contends that this problem is not new; it has persistently plagued the digital realm. He references initiatives like the ‘No More Ransom’ project, aimed at curbing the ransomware epidemic by discouraging ransom payments.
Davis underscores the need to undermine the profitability of
ransomware as a business model. He calls for society to recognize the intricacies of computer security and acknowledge that security breaches are inevitable, ranging from basic phishing emails to sophisticated state-sponsored attacks.
Expanding on the ransomware discussion, Davis emphasizes its lucrative nature and how it has led companies to view paying ransoms as the quickest remedy. He notes that cybersecurity insurance companies are taking proactive measures by incorporating specific provisions for ransomware and establishing prerequisites for coverage.
To render ransomware an ineffective business model, Davis argues for a collective resolution to resist ransom demands. He stresses the importance of companies openly addressing their security vulnerabilities rather than concealing them, as every company is susceptible to breaches at some point.
Davis highlights the alarming rise in ransomware attacks, fuelling the growth of an illicit industry. Companies that acquiesce to monetary demands only perpetuate this cycle of attacks. This situation calls for a paradigm shift in how we approach ransomware, marked by an urgent need for awareness, resilience, and collaborative efforts against these criminal actors.

Davis underlines the pressing need for government intervention and regulation in the realm of AI. He aligns his perspective with that of OpenAI, which took the bold step of releasing its technology early to catalyze policy development and legislative action around these potent technologies. Davis emphasizes the pivotal role
of AI organizations in shaping conversations about regulations, citing OpenAI’s CEO testifying before Congress on the necessity and implications of AI regulation.
Davis expresses concern about the limited technological expertise of politicians and underscores the importance of industry professionals leading the way in fostering understanding and shaping policy.
He posits that security professionals, well-aware of the dangers posed by emerging technologies, must take a proactive role in these discussions to formulate pre-emptive measures against potential threats. Davis likens the transformative impact of AI to previous technological shifts and advocates for informed security measures to counter possible pitfalls.
The conversation takes a deep dive into the enigmatic world of ransomware gangs and their unexpected reputation for reliability. Davis sheds light on the burgeoning organizational structures within the criminal underworld, were reputation reigns supreme. Remarkably, companies now find themselves relying on the experiences of previous victims to gauge the trustworthiness of these criminal entities, creating a peculiar paradox where criminals are deemed dependable.
Contrary to the belief that ransomware is a mounting threat, Davis argues that it has persistently plagued the cybersecurity landscape. He points to the “No More Ransom” project, a collaborative effort aimed at combatting ransomware, as a potential solution to this enduring problem. He underscores the
imperative for victims to resist paying ransoms, as this only bolsters the ransomware operators’ business model.
Davis also delves into the importance of transparency and honesty when dealing with security breaches. He critiques attempts to obscure the details surrounding security incidents and urges companies to openly share their experiences, fostering collective learning and resilience within the industry. He sheds light on the evolution of cyber insurance, noting its role in limiting liabilities and requiring evidence of protective measures.

Davis navigates the evolving terrain of attack surfaces and the pivotal role played by AI in this shifting landscape. He paints a vivid picture of algorithms being weaponized, advancing at a
pace that often outstrips our capacity to detect and counteract them. He emphasizes the pressing need for robust detection mechanisms, all the while highlighting the inherent challenges in distinguishing algorithm-generated content from human-created content.
Davis issues a stark warning about a future where viruses could evolve faster than our ability to define them, posing substantial challenges to established cybersecurity paradigms. Nevertheless, he presents a balanced perspective, exploring the potential of harnessing AI for proactive defense mechanisms. He also shines a light on the ongoing race to employ AI for security, an arena where malevolent applications often precede benevolent ones.
In contemplating the inherent limitations of AI, Davis underscores the need to refine our approach to pattern recognition. In conclusion, he issues a resounding call to arms, urging us to fortify our defenses and continuously enhance our technologies, lest we allow malicious entities to perpetually outpace us.
In summary, Davis highlights AI’s potential in pattern recognition and its role in enhancing human capabilities. He emphasizes the need to strategically integrate AI into security measures, continually assessing risks. Davis
also discusses the changing perception of security in critical infrastructure, calling for updated regulations and resistance against ransomware attacks.
Davis underscores the importance of proactive collaboration, informed governance, and technology evolution in the AI-cybersecurity intersection. We must focus on ethical alignment, strong governance, and effective risk management. This discussion encourages stakeholders and regulators to shape a secure technological future collaboratively.
In an era where technology is deeply woven into our daily lives, the demand for robust cybersecurity education has reached unprecedented levels. However, traditional training methods often fall short, lacking engagement and ensuring retention. Recognizing this critical gap, ELB Learning has embarked on a mission to revolutionize cybersecurity education with its groundbreaking training module.
In a candid chat with John Blackmon, Chief Technology Officer of ELB Learning, Augustin Kurian, Editor-in-Chief of The Cyber Express, gained insight into the innovative
training module. Blackmon highlighted a common challenge in traditional training methods: the “forgetting curve.” Learners tend to forget approximately 80% of what they’ve learned within a week. He underscored that passive learning doesn’t engage the brain as effectively as active learning.
To illustrate, he drew an analogy with driving a car: actively participating as a driver makes it more likely that you can find your way back than being a passive passenger.



ELB Learning’s gamified experience, developed in collaboration with Cybercatch, aims to counteract the forgetting curve by fostering active involvement. Learners assume the role of a hacker in this immersive experience, encouraging a depth of engagement akin to “experiencing” rather than “learning.” Such experiential learning methodologies are instrumental in reinforcing retention and understanding, allowing users to vividly remember training details.
Integrating gamified elements and a role-reversal approach is groundbreaking in cybersecurity education. When learners step into the shoes of an adversary, they gain a unique perspective on potential vulnerabilities and attack vectors. This experience enables users to think proactively about cybersecurity threats and to understand the nuances of spear-phishing and other prevalent hacking techniques, developing a cybersecurity mindset that is anticipatory rather than reactive.
This innovative approach represents a “giant leap” in cybersecurity training and education, particularly considering the current digital landscape, where corporations continually grapple with sophisticated cyber threats. The human factor often serves as the weakest link in organizational security, making this training essential for employees at all levels of the corporate hierarchy.
Contemporary trends in cybersecurity education gravitate toward more interactive and engaging learning experiences. This is imperative in today’s digital era, where incessant advancements and increasing reliance on technology make it essential for individuals and organizations to stay abreast of evolving cybersecurity threats. Incorporating immersive learning experiences is crucial in fostering a more informed and vigilant workforce.
The game leverages a multiple-choice interface, offering an innovative and entertaining platform that enhances the training experience. The evolution of the modern workplace and its employees has elevated expectations for training modules. Immersed in an era teeming with engaging streaming options, modern employees demand similar entertainment in their learning experiences. The project’s inception stemmed from recognizing this unmet need in the market, especially within a domain traditionally perceived as dry and lackluster: cybersecurity training.
To address this, the game integrates elements of sarcasm and humor, simulating real-life interactions with colleagues. This approach makes the learning process enjoyable and enhances retention and comprehension of the knowledge imparted. It reflects a conscious effort to align learning methodologies with entertainment formats that today’s employees are familiar with, rendering the learning experience more aligned with contemporary entertainment consumption habits.
Current trends in cybersecurity education highlight a shift towards more interactive and engaging learning experiences. The increasing complexity and sophistication of cyber threats necessitate a well-informed, regularly updated workforce engaged in cybersecurity best practices. This ongoing transformation aims to dismantle the preexisting, monotonous structures of cybersecurity education, replacing them with dynamic and immersive learning experiences.
Traditional training modules, often characterized by extensive documents or slides, are becoming outdated and ineffective. The gamified experience provided by innovative platforms is set to become a staple in cybersecurity education, given its alignment with contemporary preferences for interactive and entertaining content. This shift is essential in maintaining employee engagement and ensuring the assimilation of crucial information, thereby fostering a more robust cybersecurity culture within organizations.TH
When queried about forthcoming plans and enterprise adoption strategies, Blackmon expressed optimism without committing to a specific launch date. Collaborative marketing efforts with Cybercatch will likely expedite the game’s introduction to the market. The approach for this innovative project appears to be multifaceted, catering to individual users and large organizations, predicting its eventual normalization across diverse organizational structures.
This anticipation of widespread adoption is not just limited to cybersecurity training. The dynamic and interactive nature of this game has the potential to redefine expectations for other training modules within an organization. Questions arise: “Why can’t my sexual harassment course be like this? Why can’t my corporate rules course be like this?” The longing for engagement and interaction within training modules is clear, and current trends reflect the integration of entertaining elements into serious instructional
content, harmonizing education with entertainment.
Blackmon’s insights on the potential of virtual reality (VR) experiences to replace traditional certifications offer a glimpse into the future of cybersecurity training. The immersive and engaging nature of VR can simulate real-world scenarios, making it a viable alternative to traditional certification methods. VR’s adaptability to diverse learning environments and its ability to offer gradable, interactive content position it as a promising tool for reshaping the landscape of certifications in various domains, including cybersecurity.
The discussion also extends into the realm of entertainment-based education, exploring its applicability beyond cybersecurity to diverse sectors like transportation and trucking. This demonstrates the versatility and adaptability of immersive learning. Blackmon’s examples, particularly in the trucking industry, illustrate the shift in training methodologies, leveraging real-life
scenarios and user-centric content to elevate the learning experience. Incorporating employees instead of actors in creating content further authenticates the learning material, making it more relatable and enriching.
Cybersecurity education trends reflect the increasing need for more interactive and engaging learning platforms. Traditional methods of imparting cybersecurity knowledge predominantly revolve around theoretical learning and are evolving to accommodate more pragmatic and experiential learning experiences.
The fast-evolving threat landscape in cybersecurity requires professionals to possess both theoretical knowledge and practical skills to navigate and mitigate cyber threats effectively.
The rise of immersive learning is a testament to the recognition of hands-on experience in enhancing learning outcomes. The juxtaposition of traditional learning with more advanced, entertainment-based education is heralding a new era in cybersecurity education.

While seemingly unconventional, this approach is pivotal in fostering an environment conducive to learning, especially in fields like cybersecurity where the concepts can be intricate and complex.

The dramatization of interactions with hackers, as highlighted by Blackmon, is an intriguing aspect of the course. While it enhances engagement by introducing amusing characters and dialogues, it also retains the essence of real hacking, which is fundamentally about exploiting vulnerabilities, selecting targets, and crafting phishing emails. This balance between entertainment and realism is crucial in maintaining the integrity of the learning material.
The emergence of immersive learning in sectors beyond cybersecurity indicates its universal appeal and effectiveness. The growing adoption of this form of learning across different industries is fueling innovations in training methodologies, catering to diverse learning preferences, and making education more accessible and enjoyable.
ELB Learning’s groundbreaking cybersecurity training, led by Blackmon, represents a paradigm shift from passive to active, immersive, and gamified learning. This innovative approach leverages real-world scenarios and strikes a balance between entertainment and realism to foster a deeper understanding of cybersecurity threats and mitigation strategies.
Not limited to cybersecurity, ELB Learning’s approach is versatile and applicable to various sectors. It illustrates a broader trend towards merging education and entertainment to create lasting learning experiences. Blackmon’s insights and the ensuing developments highlight the pivotal movement towards integrating learning and entertainment, destined to reshape the learning landscapes in multiple domains.





 - By Ashish Khaitan
- By Ashish Khaitan

In recent years, the cybersecurity landscape burgeoning trend marked by a surge in hacking incidents masterminded by teenagers. One noteworthy case involves Kurtaj, an 18-year-old hacker who successfully breached Rockstar Games, the firm responsible for the highly anticipated release of GTA VI. In a startling turn of events, this young hacker infiltrated Rockstar Games’ networks and then used this unlawful access to trick the corporation into making an offer, effectively averting the spread of key GTA VI information.
Notably, this episode is not isolated; it is a part of a larger trend in which kids are more attracted to the world of hacking. Take for instance, the case Ellis Pinsky, who began crypto thievery spree at the age of 15 and earned over US$100 million in ill-gotten assets by the time he was 18. Similarly, Jonathan James, another juvenile offender, delved into cybercrime when he was just 15, and at the age of 16, he found himself facing legal consequences for his actions in the United States.

What common between these individuals is their age, and what propels them into the realm of cybercrime is their innate curiosity about technology. These incidents highlight an increasing trend of young people using their technical prowess to exploit vulnerabilities within high-profile organizations. This trend, in turn, leaves businesses and law enforcement agencies grappling with the multifaceted repercussions that follow in the wake of such cyber intrusions.
There are multiple key reasons for the increase in teen hackers. One crucial aspect is the increasing accessibility of technology. Computers and the necessary resources for hacking have become more affordable and widely available. This accessibility allows individuals, especially teenagers, to specialize in specific areas of hacking without the need to master every facet of computing.
Today, teenagers can dedicate time and effort to honing their hacking skills thanks to the proliferation of affordable hardware and open-source software. Gone are the days when hacking required expensive, specialized equipment. Now, a teenager armed with a basic laptop and an internet connection can begin hacking Wi-Fi networks and nearby devices after just a few months of free online training.
Additionally, the modular nature of computer systems enables enthusiasts to focus on specific aspects of
technology. From understanding network protocols to learning cryptographic algorithms, hacking encompasses a vast spectrum of skills. Teenagers, with their curious minds and ample time, can gradually develop expertise in these specialized areas.
Another significant factor contributing to the prevalence of teenage hackers is the presence of weak security measures within organizations. Many businesses have yet to prioritize robust cybersecurity, leaving vulnerabilities that savvy hackers can exploit. The internet, originally designed without security as a primary consideration, inherently contains numerous vulnerabilities. As a result, hackers only need to identify one flaw, while defenders must address every potential weakness. This creates an asymmetrical advantage for attackers.
Although strides have been made in enhancing cybersecurity practices, many organizations, especially smaller ones, still need to implement comprehensive security measures. This situation provides opportunities for teenage hackers to exploit vulnerabilities, as they often possess a deeper understanding of these weaknesses than the organizations themselves.

For many teenagers, hacking is more than just a hobby; it’s an engaging blend of problem-solving, intellectual stimulation, and excitement. The allure of understanding and controlling complex systems naturally lures young brains into the arena of hacking challenges.
Unlike conventional career paths, hacking offers a distinct form of entertainment that resonates with tech-savvy individuals. This recreational side of hacking is similar to a digital puzzle-solving hobby. In a way akin to enthusiasts dedicating hours to solving crosswords or building intricate models, teenage hackers channel their curiosity and intellect toward unraveling the complexities of computer systems.
In today’s digital world, children encounter technology at an early age. Some teenagers have been delving into programming since before they reached adolescence , giving them a head start in acquiring technical skills. Whether influenced by parents working in the IT industry or guided by coding enthusiasts, these young minds develop proficiency in programming languages and systems, making them adept hackers by their mid-teens.
This early exposure to programming not only equips teenagers with technical knowledge but also fosters a problem-solving mindset. Through interactions with coding languages and software development, they gain a deeper comprehension of how systems operate, enabling them to spot potential vulnerabilities.
The rise of cryptocurrencies and non-fungible tokens (NFTs) has created new avenues for cybercrime. Tempted by the potential for financial gain, teenagers may venture into hacking to exploit these emerging technologies. Instances of young people earning significant riches through unlawful operations in the crypto sphere highlight the attraction of these opportunities.
Cryptocurrencies offers an anonymous and decentralized method of making financial transactions, which attracts hackers looking to avoid detection while benefitting from their efforts. Furthermore, the boom in NFT popularity has created a market ripe for exploitation, with youth taking advantage of their technical expertise to engage in cybercrime related to non-fungible tokens.
Television series and movies that portray hackers as heroic people fighting against corporate greed may romanticize hacking for naïve youth. While dramatized, this portrayal might instill a sense of responsibility or rebellion in young minds. This narrative, as exemplified by shows like “Mr. Robot,” can motivate some individuals to explore hacking as a means of achieving change.
The depiction of hackers as protagonists battling powerful corporations resonates with teenagers who may harbor a sense of injustice or a desire to challenge established norms. While the reality of hacking is considerably more complex than portrayed in the media, the influence of these narratives cannot be underestimated.

Teenage hackers have different personality traits that distinguish them in the digital realm. Their qualities are summarized below:
• Curiosity and tech enthusiasm- Teenage hackers are characterized by an insatiable curiosity about technology and a relentless desire to delve into their inner workings. This innate curiosity serves as a powerful motivator, driving them to explore systems, networks, and applications.
• Motivation beyond money- The National Crime Agency, as reported by The Guardian, found that, contrary to the popular belief, teenage hackers are more likely to be motivated by ideals and the need to impress their peers than by the desire to make money.
• Outstanding problem-solving capabilities- Hackers, including their young counterparts, are known for having remarkable problem-solving skills. They excel in dismantling complex systems, pinpointing vulnerabilities, and devising innovative solutions. Bridewell notes that both white hat and black hat hackers share a motivation to uncover computers and networks vulnerabilities.
• Black hat vs. White hat- While black hat hackers do more harm to companies, white hat hackers “inform enterprises and web developers of the changes that need to be made.” This proficiency allows both subsets of hackers to navigate intricate security measures and devise creative ways to exploit weaknesses.
• Propensity for taking risks- Teenage hackers often demonstrate a higher risk tolerance compared to adults. This inclination towards risk-taking can be attributed to their relative lack of experience and, in some cases, an inherent sense of invincibility. Teenagers are naturally drawn to exciting events because of the excitement they bring, according to Dr. Lisa Damour. “While the longing for excitement rises quickly in adolescents, their capacity for suppressing impulses develops more slowly. The spike we see in teenage risk-taking can be partially accounted for by the fact that neurologically speaking, teenagers can be all gas and no brakes,” said Dr. Damour.
• Independent and self-governing- Many teenage hackers prefer working independently or in small, tightly knit groups. Their autonomy provides them with the freedom to pursue their interests and explore new challenges, fostering the development of innovative hacking techniques.
• Ethical difficulty- It’s crucial to remember that not all adolescent hackers engage in malicious activities. Some have a strong sense of ethical responsibility, utilizing their skills to uncover vulnerabilities and safeguard systems. However, the moral boundaries of teenage hackers vary widely, with some justifying their actions based on their perception of justice or activism. This moral ambiguity is a complex trait within the teenage hacker’s community.
All things considered, the growth of young hackers is a complicated and dynamic issue. It is crucial to comprehend the causes of this trend as well as any potential societal repercussions. Teenage hackers present cybersecurity dangers that need to be addressed, but we also need to be aware of the possible advantages they may present.
The risk that young hackers bring to cybersecurity can be reduced by teaching them how to use technology ethically. This is possible through educational initiatives, extracurricular pursuits, and online tools. Enhancing businesses’ security posture is a crucial next step. To safeguard their systems from assault, organizations should put in place thorough security procedures.
Finally, we must acknowledge and support the beneficial contributions that young hackers can make to society. We should provide them with chances to put their talents to good use by creating educational materials or working on cybersecurity solutions, for example. By doing these things, we can make sure that the emergence of young hackers is a positive force in the world.


Not just insider threats, organizations must take into consideration the reasons why office insiders have failed as reflected in famous cyber attacks, and make sure that those mistakes are repeated by their employees.
- By Vishwa PandagleNo company wants to lose money because of an employee error. The tedious process of hiring, background checking, interviewing, etc., is meant for making the best choices in hiring assets who fight the cause of the enterprise. Insider threats, however, can come out of any department and cost the company not only millions in losses but also, its reputation.
To train employees, an employer makes several opportunities available by scheduling awareness exercises during work hours, so the employees are well aware of todos and don’ts. However, despite all the attempts, it fails to strengthen the employees to act in accordance with basic cyber hygiene.

Cyber attacks due to Insider threats have increased by 44% in comparison with the past two years. The time taken to mitigate risk from incidents arising from insider threats increased from nearly 77 days to over 85 days on average.
Employees knowingly or unknowingly allow cybercriminals to successfully attack the digital infrastructure, leading to the compromise of data and bringing in regulatory actions.
Insider Threats outlined in a post by CISA says it can be –


1. A contractor, vendor, or custodian to whom the organization has given access to its data
2. Someone who was given the company device to work
3. May be trusted by the organization
Addressing how an employee poses a risk to the company the post by CISA read that the employee in question could have authorized access or have an understanding of the organization which could be adversely used.
Infosec website about how he started hacking at age 11, was trained into better hacking, and eventually attacked organizations against whom he holds grudges.
USDoD announced that they were successful in exfiltrating 3,200 records belonging to Airbus vendors using employee credentials of a third-party Turkish airline. The Turkish employee was found by Hudson Rock, a cybercrime firm.
While discussing mitigation of similar incidents, Alon Gal, Chief Technology Officer at Hudson Rock told The Cyber Express, “Monitoring for info-stealer infections is a critical aspect of preventing data breaches like the one experienced by Airbus.”
It is time, organizations such as Airbus which is Europe’s multinational aerospace corporation serving defence, security and other organizations with critical services and infrastructure follow security protocols such as monitoring of info-stealers.
Infostealers or Information-stealing malware are found advertised on the dark web for a small price and several evasion detection benefits. Some are even sold for subscription to make it more affordable along with a manual with step by step instructions to steal system data with minimal technical expertise.
In the Airbus cyber attack, USDoD completed their mission of stealing the login credentials of an employee in other words, an insider threat who was unaware of what was going on with their account behind their back.
This use could be in the hands of the employee or another individual who may either trick the employee into releasing access-related data or bribe him to do so. Negligence is a prime reason an employee allowed an opportunistic hacker to find a way to system data.
The Airbus cyber attack was claimed by a cybercriminal named USDoD who confessed to breaching the systems by exploiting the credentials of an insider. The arrested member of the lapsus group, Arion Kurtaj was known to bribe office insiders to gain entry into the organizations’ systems. Let’s understand the incidents better as unfolded by the culprits themselves.
A cybercriminal USDoD was active on the now-closed RaidForums as NetSec. He spoke with DataBreaches an
USDoD’s Answer
In the interview, when USDoD was asked about targeting NATO and CEPOL. The answer was, “I have already accomplished access to NATO and CEPOL, so Phase 1 of operations is finished and now I will pivot to Phase 2.”
He said that he needs to study and exploit the weak spots of the above-mentioned organizations in Phase 2. He gained access to CEPOL and NATO by registering using fake credentials and posing as legitimate staff.
He chose CEPOL because it is an e-learning platform for law enforcement and is associated with Europol. His modus operandi involves participating in vendor websites to study the workings of it so he can understand the defense mechanism in place.
Explaining the same he said, “NATO uses custom and modified versions of endpoint security and AV. Plus they have their own version of policy, browser, etc. So put both together and I can take them down because I know their methods and I know how they protect themselves. This is enough for me to get more access.”
USDoD targeted a third party, the Turkish Airlines employee for his credentials because that let him have access to Airbus. Even though this may seem like a long shot, hackers find this limited access enough to exfiltrate sensitive user records and post them online on breach forums.

Investigating the method employed by USDoD who was himself surprised at being approved by the website admin as a user of the service, is a prime attack tactic needing keen attention. Seeing the name of a senior employee or someone from the management requesting access can lead to creating pressure on the website administrator.
They would approve the request of someone posing as a senior staff as they are of a lower designation and would risk losing their job if they denied access to senior staff. The process of cross-checking the applications of each and every employee is the need of the hour, as this scenario highlights.
No matter who is on the other side, it must made clear to all employees and website administrators that no access request must be approved before checking with proof to make sure it is a genuine request sent by the person who is who he says he is.
To avoid becoming an insider threat, careful measures must be taken to verify the authenticity of each applicant regardless of their designation or social status. The concerned person can be called on their contact number, they must be emailed to their alternate email address as provided on company records and should be asked to confirm via an OTP or on personal office chat messaging service for verification.

The InfraGard cyber attack was claimed by USDoD which allowed him to pilfer information of over 80,000 members. InfraGard was targeted by USDoD as it works as a bridge between businesses and the FBI. If this is the prime focus of hackers to target a critical infrastructure by targeting a vendor or third party, then it is time to train and manage vendor cybersecurity as their own.
Because what is at stake is not just the vendor data but also the information belonging to the client and their customers. Similar to gaining access to the portal of NATO as claimed by USDoD, he applied to become a member and aimed to get accepted on InfraGard. Which he did!
This time, he impersonated the CEO of a financial firm who was not a member but whose application, USDoD expected would likely be accepted, read the interview of the hacker on DataBreaches.
To his surprise, the interview read, his application was accepted without any further vetting.
The impersonator was cautious not to get caught while posing as the CEO of a well-known company. “First, I created a sketchy application with some false information and submitted it to see how InfraGard would respond,” USDoD stated.
He improvised his technique by using the feedback he received when rejected by the company. He wrote, “Once I saw what they said was wrong with my application, then I knew what I had to be accurate about.”
Adding more importance to the need to vet access and registration requests is the statement by USDoD that read, “I was very surprised though, that they accepted the final application because I did not use the professional email for the CEO I was impersonating.”
He created a fake email on Tutanota emailing platform impersonating the CEO. He claimed that the email ID was – staff@tuta.io
USDoD stated that they rely 100% on social engineering attacks. With the next targets usually named on the hacker forums and leak sites of hackers, it is time they keep an eye out for new registrants. Social engineering attacks involve communications that is based on the intuition and planning of the hackers that manipulate the receiver and trick them into approving requests or performing tasks that let cybercriminals conveniently perform a cybercrime.
This fatigue is nothing but a social engineering attack in an attempt
get rid of whoever is bothering them.
The famous Uber hack was claimed by teenage hackers who sent several login authentication requests on Slack, the messaging service used by the staff of Uber. The hackers posed as employees of Uber and sent notifications to other Uber staff for over an hour. This caused the target MFA Fatigue also called Multi-Factor Authentication Fatigue.
to circumvent the MFA feature. The cybercriminal sends several push notifications related to authentication on email, phone, or registered devices.
The victim, on the other side, may get bored, or tired and approve a request from the several ones received on their device to get rid of the notifications. Hackers may use techniques which may seem akin to child’s play involving instigation and persistence trying the patience of the other person so they do whatever is needed to
No matter how much a company spends on cybersecurity, governments train staff, legal agencies fine the defaulting companies, and threat detection tools are used to prevent threats, a simple click by an employee or an insider threat can potentially dissolve all the effort in a jiffy. Hence, while every guard must be put in place to tackle cyber criminals, insider threats must be avoided by having the workforce made clear about identity and access management. They should be assured that their jobs will not be taken away if they perform authentication checks on any individual regardless of who they are.

It is not worth losing the data, exposing critical infrastructure to threats, and sacrificing one’s standing in society to an insider threat who was either not trained well or was not capable enough to fight persistent hackers.

 - By Ishita Tripathi
- By Ishita Tripathi
The realm of space exploration is in a constant state of evolution, yielding continuous advancements and discoveries, all thanks to the ever-improving capabilities of space technology. A report by Spherical Insights & Consulting projects that the global space exploration market is set to reach an astounding US$1,879 billion by 2032, a significant leap from its 2022 valuation of US$486 billion.
As of June 2023, the United Nations Office for Outer Space Affairs reports an astonishing 37.94% increase in the number of individual satellites orbiting Earth since January 2022, totaling 11,330. This astronomical growth underscores the vital role of space technology in our daily lives,
encompassing communication, navigation, weather forecasting, and more. This exponential expansion emphasizes the growing importance of space technology, which has become an integral part of our daily existence. Our reliance on satellites spans a wide spectrum of communication needs, from global connectivity to weather forecasting and precision GPS navigation. Moreover, space systems play a critical role in strengthening the national security of numerous countries due to their surveillance and reconnaissance capabilities.
Highlighting the pivotal role of satellites in governmental functions, the 2022 Statista report reveals
a historic milestone in global government spending on space programs, reaching an impressive US$103 billion. Notably, the United States Government led this investment, allocating nearly US$62 billion to its space initiatives in 2022, solidifying its position as the world’s leading spender in space exploration. Following closely, China allocated nearly US$12 billion to government expenditure on space programs.
As we witness significant growth in investment within this sector and increasing dependence on it in our daily lives, it becomes abundantly clear that factors such as cybersecurity and the associated risks can no longer be ignored.

Space assets are not impervious to the continuously shifting world of cyber threats. Space cyberattacks may be undertaken for a variety of reasons, ranging from criminal motivations, where hackers seek financial gain, to intelligence gathering and operations disruption, often involving nation states at odds with each other. As countries become more interconnected through space technology, the stakes for successful cyberattacks in space continue to grow.
Among the most susceptible targets in space are satellite systems, which include satellites themselves, space stations, and the ground control systems that manage them. These assets are vulnerable to various types of cyberattacks, such as jamming, eavesdropping, spoofing, and outright hacking. The resulting effects can range from interference with essential services to the potential damage or complete annihilation of expensive space equipment.

To emphasize the severity of this issue, let’s examine a few past events. In 2019, hackers infiltrated an Indian satellite control room, raising concerns about the security of space infrastructure and potential information leaks. Similarly, in 2007, the Chinese military launched an anti-satellite missile against a defunct Chinese weather satellite, resulting in the creation of hundreds of thousands of fragments of debris scattered in space around Earth.
The consequences of such attacks can vary from the direct loss of assets in orbit to more indirect hazards caused by orbiting debris, which can pose problems for future launches and reentries.
Another emerging concern is the link between space debris and cybersecurity. The threat of space assets being targeted by anti-satellite tests continues to exist, with debris posing both physical and cyber threats to operational spacecraft. Space agencies and entities must account for this when developing their cybersecurity strategies.
Securing space assets presents unique technical hurdles. The vast distances involved in space communications create significant delays, hindering real-time threat monitoring and response. Additionally, the harsh space environment, characterized by extreme temperatures and high radiation levels, strains the reliability of electronic systems. Nonetheless, the space sector has made strides in addressing these issues through innovations such as encryption and authentication.
Ensuring the security of satellite communication, particularly for military and government systems transmitting sensitive data, is paramount. These communications are safeguarded through encryption, authentication using signed certificates, and secure protocols like HTTPS and APIs. Secure access to these connections is crucial to safeguarding national security interests.
The global nature of space activities necessitates a robust regulatory framework. Institutions such as the United Nations and the International Telecommunication Union wield considerable influence in shaping these standards. Yet, to adequately address space cybersecurity challenges, these policies must undergo expansion and modernization.
Addressing space cybersecurity requires international cooperation, given the inherently global nature of spacerelated activities. Nations must collaborate in initiatives and forums to establish norms and standards. In this interconnected world, multilateralism, rather than unilateralism, is the key to safeguarding space assets and preserving the sustainable space environment.
Looking ahead, the future of space cybersecurity presents both escalating challenges and promising opportunities. As governments and commercial entities continue to launch satellites into space, new vulnerabilities emerge. Artificial intelligence (AI) and machine learning (ML) will play a pivotal role in proactively detecting and responding to these threats by analyzing vast datasets for signs of cyber attacks.
Further, modern infrastructure, comprising internet of things (IoT) sensors, cutting-edge edge analytics, and sophisticated network monitoring systems, wields the capability to meticulously sift through vast datasets. Their discerning eye can unearth anomalies that might serve as harbingers of impending cyberattacks. As we continue to explore the depths of space, the importance of these technological advancements will undoubtedly soar.
However, these technological strides grapple with a significant obstacle—the sheer abundance of satellites currently orbiting our planet. Companies like SpaceX, OneWeb, and Amazon’s ambitious Project Kuiper have ambitious plans to deploy thousands more satellites, envisioning a global internet service.

In exchange for the promise of global connectivity that touches every corner of Earth, space endeavors face an enormous responsibility – safeguarding an ever-growing constellation of hardware in the celestial realm, a domain that is now truly taking flight. Satellites, a linchpin of this connectivity, represent a critical cybersecurity concern, with each one a potential target for malicious actors.
The “NewSpace” paradigm, characterized by flourishing publicprivate partnerships, is gaining momentum. However, this surge in innovation and cost reductions in space access must be met with a resolute commitment to cybersecurity. Industry stakeholders are increasingly acknowledging their responsibilities, fostering collaboration among regulators, space agencies, and the private sector. The need for cybersecurity standards and best practices in this dynamic ecosystem is becoming increasingly evident.
Another noteworthy development is the rise of secure and closedloop satellite communication systems. These solutions deploy advanced encryption methods, rigorous key management, and continuous monitoring to fortify their defenses against cyber risks. These technologies are attracting substantial investments from military and government entities, reflecting their commitment to preserving the security of sensitive communications.
The trajectory of our space cyberfuture hinges on the pace at which we expand our “man-made” presence beyond our planet. As we launch satellites into orbit and increasingly rely on space for critical service delivery, the demand for robust cybersecurity tools will inevitably surge. In the vast cosmic expanse, the identification, quantification, and effective mitigation of cyberthreats will depend on the application of AI and machine learning techniques. Moreover, our continued cooperation among nations and the establishment of industry standards for space exploration will be pivotal in shaping our destiny in space.


In the realm of cybersecurity, 2023 has proven to be a pivotal year marked by a surge in sophisticated cyberattacks. New threat actors have entered the scene armed with novel techniques, displaying unwavering determination in their quest for confidential data

Recent global conflicts, including the Russian invasion of Ukraine, have further ignited the flames, ushering in a new era state-sponsored cyberattacks spanning all regions.
This monthly roundup serves as a chronicle of the most significant cyberattacks witnessed throughout the year, offering insights into the tactics, techniques, and procedures employed by cybercriminals.

The Monti Ransomware Group claimed responsibility for responsibility for a breach at Auckland University of Technology (AUT), citing perceived security vulnerabilities. The incident, acknowledged by AUT, involved unauthorized access to their IT environment. Despite this breach, normal operations continued, both on-campus and online. AUT acted swiftly, isolating affected servers and fortifying security measures. External cybersecurity experts joined the investigation, and the incident was reported to relevant authorities. AUT pledged close collaboration with law enforcement during their response.


In Pasig, Metro Manila, the Philippine Health Insurance Corporation (PhilHealth) fell victim to a cyberattack, resulting in a temporary shutdown of certain systems to contain the breach. The Department of Information and Communications Technology, in tandem with other government entities, initiated a comprehensive investigation.
PhilHealth planned to issue updates and advisories upon system restoration, as their website remained inaccessible. A representative from PhilHealth assured the public that additional information about the investigation would soon be available.

The Government of Bermuda fell victim to a significant Distributed Denial of Service (DDoS) attack, attributed to Russian hackers. The attack impacted IT systems across all government departments, resulting in widespread service interruptions. During a briefing, Premier of Bermuda, David Burt, stated that no evidence of data theft had been uncovered thus far. Similar attacks may have targeted neighboring governments.
Ongoing investigations persisted, with efforts underway to restore services. The attack affected payroll and vendor payments, resulting in anticipated delays. Cash and checks became the sole accepted forms of payment, and additional disruptions were expected due to network issues. The Department of Information and Digital Technology prioritized a swift resolution.

Air Canada issued an official statement reporting a brief unauthorized access to an internal system containing limited employee data and specific records. It’s noteworthy that flight operations and customer-facing systems remained unaffected, ensuring the security of customer information.
The airline promptly notified affected parties and relevant authorities, confirming that all systems were now fully operational. To prevent future incidents, additional security measures were implemented, with support from leading global cybersecurity experts, reaffirming their commitment to data security. The company opted not to release further public statements on the incident.

Hong Kong’s Consumer Council, a consumer protection organization, fell prey to a ransomware group, raising concerns about a potential data breach. The attack occurred on Tuesday night, severely impacting 80% of their systems and causing widespread disruptions to their services and tools.

Sensitive information, including HKID numbers and credit card details of staff, family members, and 8,000 magazine subscribers, may have been compromised. Even job applicants faced potential risks. The case has been reported to both the police and the Privacy Commissioner’s Office, which have urged affected individuals to remain vigilant.

Jerusalem’s Eitanim psychiatric hospital experienced suspected cyberattack, leading to manual operations while medical treatments continued without interruption. The Health Ministry promptly reported the incident, transferring responsibility to the National Cyber Directorate. While patient treatment remained unaffected, the full extent of the attack remains undisclosed, and the identity of the perpetrator remains unknown.
In a related incident last month, hackers targeted the Mayanei Hayeshua Medical Center, demanding millions to withhold sensitive information about politicians, including Prime Minister Benjamin Netanyahu. This group, known as Ranger Locker, had previously disrupted the same hospital in August with a “financially motivated” attack. Notably, Ranger Locker is not affiliated with any organization or state and represents a concerning trend of cyber threats in the healthcare sector.

Lingerie group Wacoal, owner of brands like Fantasie, Freya, and Elomi, fell victim to a cyberattack that resulted in website outages and disruptions to indie stockists’ orders. Visitors to the affected websites were greeted with a maintenance message. The attack was reported on September 19 and impacted the ordering systems, websites, and phone lines.
Independent retailers expressed concerns over potential financial losses and order delays. Wacoal responded promptly by informing its stockists about the cyber attack and providing updates through emails and calls. While some retailers had not yet experienced delays, they remained vigilant, thanks to regular communication from Wacoal representatives regarding the issue.


Canada’s border agency, CBSA, confirmed that it had been hit by recent DDoS attacks, affecting which affected airport kiosks and gates, leading to significant delays at border checkpoints nationwide. Fortunately, CBSA assured the public that no personal data had been compromised.
The group claiming responsibility, NoName057(16), appeared to be a pro-Russia entity, potentially state-backed. They were known for targeting anti-Russia or pro-Ukraine entities. This incident was particularly notable as it extended beyond a mere website attack, exposing potential vulnerabilities in CBSA’s systems.


On September 17, 2023, BIGG Digital Assets Inc. reported a cybersecurity incident involving its subsidiary, Netcoins, a cryptocurrency brokerage. Internal controls detected suspicious activity on hot wallets, prompting an immediate response. A malicious actor gained access to the network but was swiftly removed, and security measures were reinforced.
Fortunately, no customer funds were compromised; only operational float funds totaling CAD 343,000 were affected. An investigation into an attempted access of customer information was underway. Netcoins took immediate action by resetting all passwords and implementing enhanced security measures. They continued operations with a focus on 1:1 asset and fund security. A forensic investigation remained ongoing, with law enforcement informed, prioritizing stakeholder safety.



Pittsburg, a Kansas town with a population of 20,000, experienced a cyberattack that impacted government email, phone, and online payment systems. The incident was discovered over the weekend, leading to an IT outage. However, 911 dispatch and utilities remained unaffected. City Manager Daron Hall emphasized their swift response and ongoing assessment, which could take several weeks.
Despite the attack, operations and public safety services continued, with data protection measures in place. The city did not confirm whether it was a ransomware attack or if a ransom would be paid. Additionally, no group had claimed responsibility for the incident. It’s worth noting that other U.S. municipalities, like Hinds County, Mississippi, had also grappled with recent cyberattacks.
On September 14, cryptocurrency exchange Remitano suffered a hack, resulting in US$2.7 million in crypto withdrawals. Among the stolen assets were US$1.4 million in Tether, US$208,000 in Coin, and 104,000 Ankr tokens. Tether took swift action by freezing one of the attacker’s addresses, safeguarding US$1.4 million in customer funds.

Cyvers, a blockchain analytics platform, flagged the suspicious transactions. Remitano attributed the breach to a third-party data breach, reassuring users that their funds remained unaffected. The exchange anticipated resuming normal operations within 48 hours, albeit with certain networks temporarily unavailable. Remitano primarily served emerging markets like Pakistan, Ghana, Venezuela, and others.

The International Joint Commission (IJC), responsible for overseeing US-Canada water systems, disclosed a recent cyberattack after ransomware group NoEscape claimed to have stolen 80 GB of sensitive data. Established by the 1909 Boundary Waters Treaty, the IJC managed cross-border water levels and flows.
The gang demanded an undisclosed ransom and imposed a 10-day ultimatum on the IJC. While confirming the incident, the IJC did not provide details regarding law enforcement involvement or operational impacts. NoEscape, active since May, had targeted various global organizations. This incident underscores the growing importance of cybersecurity in Water management bodies, with ongoing disputes over annual audits and the availability of new vulnerability scanning services.

A wood processing company in the Deggendorf district recently fell victim to a digital attack when unidentified hackers planted ransomware on their servers. The incident triggered a swift response from the Deggendorf Police Department, who promptly initiated an investigation. The attackers successfully encrypted several servers, temporarily pushing the company into emergency mode. However, the company decided not to contact the perpetrators, and ransom demands were made.
The Deggendorf criminal police led the investigation, deploying a rapid response team to secure digital traces and offer assistance. After restoring operations using a backup, no data breach occurred. Authorities emphasized the importance of proactive measures, particularly robust data backup strategies, to thwart future attacks.


CoinEx, a global cryptocurrency exchange, confirmed a security breach that led to the theft of an estimated US$31 million in various cryptocurrencies, including ETH, TRON, and Polygon. The exchange moved swiftly to reassure its users that their assets remained secure and unaffected, pledging 100% compensation for those impacted.
To address the incident, CoinEx temporarily suspended deposit and withdrawal services for a thorough review. The exchange actively worked to identify and isolate the wallet addresses linked to the attack, while also urging vigilance among other cryptocurrency platforms.

The Quebec government faced a denial-of-service cyberattack orchestrated by the pro-Russian group NoName, impacting several official websites, including the Treasury Board and regulatory agencies. Quebec’s cybersecurity minister, Eric Caire, attributed the attack to NoName but assured the public that no personal data was compromised.
The Cybersecurity Department reported that the attack occurred overnight, causing temporary downtime for some websites. The denialof-service attack overwhelmed servers with traffic, resulting in crashes. NoName, known for past cyberattacks, previously targeted HydroQuebec in April. Despite the disruption, the government maintained the integrity of its data.


A recent cyberattack affected over 50 Colombian state entities and private firms, as confirmed by Colombian President Gustavo Petro. The attack included a ransomware strike on IFX Networks, which led Petro to criticize the company for its inadequate cybersecurity measures, potentially breaching contracts.
Colombia’s Minister for Information, Technology, and Communications, Mauricio Lizcano, announced administrative measures and the possibility of legal action against IFX Networks. The company acknowledged the complexity of the incident and its impact on clients, highlighting their swift response to mitigate the attack’s extent.


Save the Children International, a global charity focused on aiding children in developing countries, confirmed a cyberattack after the BianLian hacker gang claimed to have breached their systems. While unauthorized access was gained to parts of their network, operational disruption was averted.
The ongoing investigation was ongoing in collaboration with law enforcement agencies revealed that the attack involved the theft of 6.8 TB of data, including personal information, finances, healthcare files, and emails. BianLian, known for targeting various industries, shifted its focus from ransomware attacks. The FBI, CISA, and ACSC urged organizations to implement mitigations against this and similar threats.


MGM Resorts International faced a cybersecurity issue that prompted the shutdown of various systems, including its main website, online reservations, and in-casino services like ATMs and credit card machines. The company launched an immediate investigation and implemented measures to safeguard data.
The disruption began at night, leading to manual operations in affected resorts. Customers were redirected to make reservations via phone as MGM’s main website remained inaccessible. MGM Rewards users were advised to contact Member Services during specific hours. All MGM websites under the mgmresorts.com domain remained offline as the company addressed the cyber incident.


The Campania Region’s website successfully repelled a cyberattack, as announced by President Vincenzo De Luca. The IISFA recommended urgent checks on the national network, with De Luca stressing the necessity for production systems to align with robust protection measures.
During his address at the Italian Physics Society’s 109th congress at the University of Salerno, De Luca revealed plans for a twin IT system at the university to safeguard Campania Region’s data. Gerardo Costabile, President of IISFA, called for a comprehensive national cyber health assessment and emphasized the need for enhanced cyber skills, certifications, and broader public awareness of cybersecurity.
During the G20 Summit of 2023 in New Delhi, a series of cyberattacks targeted the websites of both Delhi and Mumbai Police, resulting in temporary disruptions. The group known as “Team Insane PK hackers” claimed responsibility, specializing in tactics like DDoS attacks and defacement.
Falcon Feed raised concerns about ongoing threats, including DDoS attacks and data breaches orchestrated by various hacktivist groups targeting India. They emphasized the critical importance of adopting a “Zerotrust” policy and fortifying security measures, especially for government infrastructures, to prevent future attacks.

The National Program for Community Agricultural Estates (Prodac) recently experienced a cyberattack that resulted in the posting of explicit content on their Facebook page. In response, Prodac promptly filed a complaint and initiated an investigation to identify the perpetrators.
The breach began with the deletion of administrator accounts and subsequent alterations to the page’s settings, cover images, and explicit postings. Unfortunately, Prodac’s technical team lacked access to their own Facebook page.
The International Press Institute (IPI) encountered a cyberattack, likely in response to their advocacy for press freedom in Hungary. The attack, which commenced on September 1, involved severe DDoS incidents that led to a three-day website outage. Despite enhanced security measures to restore the site, milder DDoS attacks persisted, along with attempted breaches.
This attack marked a significant event in IPI’s history and mirrored a concerning trend of using digital means to silence critical voices. The assault aligned with a wave of DDoS attacks on Hungarian independent media, attributed to the same perpetrators, who sought reprisal for the institute’s transparency efforts.

As we close the book on September 2023’s major cyberattacks, one thing is crystal clear: the digital battlefield is ever-changing. The world of cybersecurity confronts constant difficulties as new threat actors emerge and advanced strategies are deployed. Recent worldwide wars have underlined the weight of statesponsored cyberattacks, casting a shadow across vast territories.
In this ongoing drama, businesses and countries are being pushed not merely to strengthen their defences, but also to band together in the pursuit of digital resilience. As we traverse these tumultuous seas, the lessons learnt from these tragedies act as lighthouses, pointing us to a more safe and alert cyberspace future.




