JURUTERA has an estimated readership of 198,000 professionals. Our esteemed readership consists of certified engineers, decision making corporate leaders, CEOs, government officials, project directors, entrepreneurs, project consultants, engineering consulting firms and companies involved with engineering products and services.
Our business partners can be assured that their products and services will be given the circulation and exposure they deserve, thus maintaining a sustained advertising presence to our core readers of decision-making engineers and technical experts. Our website offers an even wider market reach, with added international presence, aided by our international affiliation with official engineering bodies all over the world. Our online and offline advertising features such as banner advertising, article sponsorship and direct e-mail announcements have proven to be successful marketing strategies that will set the businesses of our partners apart from their competition.



For advertising enquiries, please contact:















Protecting
Trace





Number 06, JUNE 2019 IEM Registered on 1 May 1959
MAJLIS BAGI SESI 2019/2020 (IEM COUNCIL SESSION 2019/2020)
YANG DIPERTUA / PRESIDENT
Ir. David Lai Kong Phooi
TIMBALAN YANG DIPERTUA / DEPUTY PRESIDENT
Ir. Ong Ching Loon
NAIB YANG DIPERTUA / VICE PRESIDENTS
Ir. Prof. Dr Norlida bt Buniyamin, Ir. Prof. Dr Jeffrey Chiang Choong Luin, Ir. Ellias bin Saidin, Y.Bhg. First Admiral Dato’ Ir. Ahmad Murad bin Omar, Ir. Dr Tan Chee Fai, Ir. Mohd Aman
bin Hj. Idris, Ir. Dr Wang Hong Kok
SETIAUSAHA KEHORMAT / HONORARY SECRETARY
Ir. Mohd Khir bin Muhammad
BENDAHARI KEHORMAT / HONORARY TREASURER
Ir. Chen Harn Shean
BEKAS YANG DIPERTUA TERAKHIR / IMMEDIATE PAST PRESIDENT
Ir. Dr Tan Yean Chin
BEKAS YANG DIPERTUA / PAST PRESIDENTS
Y.Bhg. Academician Tan Sri Datuk Ir. (Dr) Hj. Ahmad Zaidee bin Laidin, Y.Bhg. Dato’ Ir. Dr
Gue See Sew, Y.Bhg. Dato’ Paduka Ir. Hj. Keizrul bin Abdullah, Y.Bhg. Academician Dato’ Ir. Prof. Dr Chuah Hean Teik, Ir. Choo Kok Beng, Y.Bhg. Dato’ Ir. Lim Chow Hock
WAKIL AWAM / CIVIL REPRESENTATIVE
Ir. Dr Lee Yun Fook
WAKIL MEKANIKAL / MECHANICAL REPRESENTATIVE
Ir. Fam Yew Hin
WAKIL ELEKTRIK / ELECTRICAL REPRESENTATIVE
Ir. Lim Kim Ten
WAKIL STRUKTUR / STRUCTURAL REPRESENTATIVE
Ir. Dr Ng Soon Ching
WAKIL KIMIA / CHEMICAL REPRESENTATIVE
Ir. Prof. Dr Lee Tin Sin
WAKIL LAIN-LAIN DISPLIN / REPRESENTATIVE TO OTHER DISCIPLINES
Ir. Bhuvendhraa Rudrusamy
WAKIL MULTIMEDIA DAN ICT / ICT AND MULTIMEDIA REPRESENTATIVE
Ir. Dr David Chuah Joon Huang
WAKIL JURUTERA WANITA / WOMAN ENGINEERS REPRESENTATIVE
Ir. Mah Siew Kien
AHLI MAJLIS / COUNCIL MEMBERS
Ir. Dr Leong Wai Yie, Ir. Razmahwata Mohd Razalli, Ir. Abdul Razak Yakob, Ir. Yau Chau Fong, Y.Bhg. Dato’ Ir. Foong Choy Chye, Y.Bhg. Dato’ Ir. Kisai bin Rahmat, Y.Bhg. Dato’ Ir. Nor Hisham Mohd Ghazali, Ir. Toh Chin Kok, Ir. Dr Jeyanthi Ramasamy, Ir. Yim Hon Wa, Ir. Yam Teong Sian, Y.Bhg. Dato’ Ir. Fakharazi bin Wahijan, Ir. Yasotha Ramachandran Chetty, Ir. Mohmad Asari bin Daud, Ir. Ng Beng Hooi, Ir. Dr Lai Khin Wee, Ir. Prof. Dr Ruslan bin Hassan, Ir. Mah Siew Kien, Y.Bhg. Dato’ Ir. Mohd Azmi bin Ismail, Ir. Ng Yong Kong, Ir. Dr Mui Kai Yin, Y.Bhg. Dato’ Ir. Noor Azmi bin Jaafar, Ir. Ting Chek Choon, Ir. Sukhairul Nizam bin Abd Razak, Ir. Lai Sze Ching, Y.Bhg. Dato’ Ir. Dr Ahmad Anuar bin Othman
WAKIL BAHAGIAN JURUTERA SISWAZAH / YOUNG ENGINEERS SECTION
REPRESENTATIVES
Dr Yew Weng Kean, Mr. Addison Koh Yang Mun, Mr. Tony Ong Chong Yong, Mr. Kuugan Thangarajoo, Sdr. Cheah Khai Chun PENGERUSI CAWANGAN / BRANCH CHAIRMAN
1. Pulau Pinang: Ir. Yau Ann Nian
2. Selatan: Ir. Teo Ki Yuee
3. Perak: Ir. Simon Yeong Chin Chow
4. Kedah-Perlis: Ir. Haji Abdullah bin Othman
5. Negeri Sembilan: Ir. Dr Oh Seong Por 6. Kelantan: Ir. Abrizan bin Abdul Kadir
7. Terengganu: Ir. Abdullah Zawawi bin Haji Mohamad Noor
8. Melaka: Ir. Sreedaran a/l Raman
9. Sarawak: Ir. Haidel Heli
10. Sabah: Ir. James Yong Hon Min
11. Miri: Ir. Dr Lau Hieng Ho
12. Pahang: Y.Bhg. Dato’ Ir. Sharuddin bin Mohd Simin
AHLI JAWATANKUASA INFORMASI DAN PENERBITAN/ STANDING COMMITTEE ON INFORMATION AND PUBLICATIONS 2019/2020
Pengerusi/Chairman: Ir. Dr Wang Hong Kok
Naib Pengerusi/Vice Chairman: Ir. Dr David Chuah Joon Huang Setiausaha/Secretary: Ir. Lau Tai Onn Ketua Pengarang/Chief Editor: Ir. Dr Wang Hong Kok
Pengarang Bulletin/Bulletin Editor: Vacant
Pengarang Prinsipal Jurnal/Principal Journal Editor: Ir. Dr David Chuah Joon Huang
Pengerusi Perpustakaan/Library Chairman: Ir. C.M.M. Aboobucker
Ahli-Ahli/Committee Members: Ir. Abdul Razak bin Yakob, Ir. Ong Guan Hock, Ir. Yee Thien Seng, Ir. Chin Mee Poon, Ir. Dr Oh Seong Por, Ms. Michelle Lau Chui Chui, Ir. Prof. Dr Abdul Aziz bin Abdul Samad, Ir. Razmahwata bin Mohd Razalli, Y.Bhg. Dato’ Ir. Nor Hisham Mohd Ghazali, Ir. Yasotha Ramachandran Chetty, Dr Sudharshan N. Raman, Ir. Bhuvendhraa Rudrusamy, Ir. Hasril bin Hasini
LEMBAGA PENGARANG/EDITORIAL BOARD 2019/2020
Ketua Pengarang/Chief Editor: Ir. Dr Wang Hong Kok
Pengarang Bulletin/Bulletin Editor: Vacant
Pengarang Prinsipal Jurnal/Principal Journal Editor: Ir. Dr David Chuah Joon Huang
Ahli-ahli/Committee Members: Ir. Lau Tai Onn, Ir. Abdul Razak bin Yakob, Ir. Ong Guan Hock, Ir. Yee Thien Seng, Ms. Michelle Lau Chui Chui, Ir. Dr Oh Seong Por, Ir. Yasotha Ramachandran Chetty, Dr Sudharshan N. Raman, Ir. Bhuvendhraa Rudrusamy
Secretariat: Janet Lim, May Lee
THE INSTITUTION OF ENGINEERS, MALAYSIA
Bangunan Ingenieur, Lots 60 & 62, Jalan 52/4, P.O. Box 223, (Jalan Sultan), 46720 Petaling Jaya, Selangor Darul Ehsan. Tel: 603-7968 4001/4002 Fax: 603-7957 7678 E-mail: sec@iem.org.my Homepage: http://www.myiem.org.my




ARTICLES An Inspiration to Young Engineers ......................12
Industrial Control Systems What are Industrial Control Systems and Why is it Important to Secure Them?...........................18
Building Information Modelling: Digital Detoxing of Malaysian Construction Industry for Digital Productivity.............................23
Malaysia National Industry 4.0 Policy-Industy4WRD: Opportunity and Challenges.........................................................26
Consultant Engineers Showcase at Estic.....33
Factory Visit to Khind-Mistral Industries
PINK PAGE Professional Interview
Explore our full set of Professional and Integrated PUBLISHING MANAGEMENT SERVICES:
» Project Management
» Crea�ve Management
» Ad Space Management
» Mailing Management
» Print Management
• Annual Reports
• Booklets • Brochures
• Bun�ngs • Business Cards
• CD / DVD Replica�ons
• Calendars • Cards & Invita�ons
• Cer�ficates • Custom Prin�ngs
• Envelopes • Folders
• NCR Bill Books • Notepads
• Leaflets • Le�erheads
• Paper Bags • Posters
• S�ckers • Others









































DIMENSION PUBLISHING SDN. BHD. (449732-T)
Level 18-01-02, PJX-HM Shah Tower, No. 16A, Persiaran Barat, 46050 Petaling Jaya, Selangor Darul Ehsan, Malaysia. Tel: +(603) 7493 1049 Fax: +(603) 7493 1047
E-mail: info@dimensionpublishing.com Website: www.dimensionpublishing.com
ROBERT MEBRUER
PATRICK LEUNG
SHIRLEY THAM shirley@dimensionpublishing.com
JOSEPH HOW joseph@dimensionpublishing.com
TAN BEE HONG bee@dimensionpublishing.com
PUTRI ZANINA & LAURA LEE putri@dimensionpublishing.com laura@dimensionpublishing.com
SUMATHI MANOKARAN sumathi@dimensionpublishing.com
NABEELA AHMAD beela@dimensionpublishing.com
THAM CHOON KIT ckit@dimensionpublishing.com
YEN YIN
yenyin@dimensionpublishing.com
For advertisement placements and subscriptions, please contact: DIMENSION PUBLISHING SDN. BHD. (449732-T)
Level 18-01-02, PJX-HM Shah Tower, No.16A, Persiaran Barat, 46050 Petaling Jaya, Selangor Darul Ehsan, Malaysia. Tel: +(603) 7493 1049 Fax: +(603) 7493 1047
E-mail: info@dimensionpublishing.com
Subscription Department E-mail: info@dimensionpublishing.com
Printed by
PERCETAKAN SKYLINE SDN. BHD. (135134-V) No. 35 - 37, Jalan 12/32B, TSI Business Industrial Park, Off Jalan Kepong, 52100 Kuala Lumpur. Mailer
SM UNIQUE MAILING SERVICES SDN. BHD. (44277-W) 80, Jalan Nadchatiram Satu, Taman Taynton View, Cheras, 56000 Kuala Lumpur, Malaysia. Tel: +(603) 9132 9192
JURUTERA MONTHLY CIRCULATION: 22,500 COPIES
Submission or placement of articles in JURUTERA could be made to the:Chief Editor THE INSTITUTION OF ENGINEERS, MALAYSIA (IEM) Bangunan Ingenieur, Lots 60 & 62, Jalan 52/4, P.O. Box 223 (Jalan Sultan), 46720 Petaling Jaya, Selangor. Tel: +(603) 7968 4001/4002 Fax: +(603) 7957 7678 E-mail: pub@iem.org.my or sec@iem.org.my IEM Website: http://www.myiem.org.my
© 2019, The Institution of Engineers, Malaysia (IEM) and Dimension Publishing Sdn. Bhd.
PUBLICATION DISCLAIMER
The publication has been compiled by both IEM and Dimension with great care and they disclaim any duty to investigate any products, process, services, designs and the like which may be described in this publication. The appearance of any information in this publication does not necessarily constitute endorsement by IEM and Dimension. There is no guarantee that the information in this publication is free from errors. IEM and Dimension do not necessarily agree with the statement or the opinion expresssed in this publication.
COPYRIGHT
JURUTERA Bulletin of IEM is the official magazine of The Institution of Engineers, Malaysia (IEM) and is published by Dimension Publishing Sdn. Bhd. The Institution and the Publisher retain the copyright over all materials published in the magazine.
and

The IEM magazine cover art is crafted around this month’s theme, Consulting Engineering Special Interest Group (CESIG). CESIG has always picked the latest and trendiest engineering activities for IEM’s benefit, including Building Information Management (BIM) industrial revolution 4.0, underground tunnelling etc, highlighted within.
As a Special Interest Group within IEM, we can do so with minimal hindrances. It is everyone’s perception that CESIG should address issues on consulting fees and the ever-observable depleting expertise in the Malaysian consultancy arena. However, it is our belief that there are many remedies to the symptoms mentioned above. These are highlighted in the articles within where engineering dedication (Dr Ooi’s interview), academic excellence and extensive use of technology forms the foundation of building expertise in the consultancy field. These are further supported by engineering research and the sharing of engineering knowledge. Read about build synergy towards IE4.0, smart building, process automation, cyber-security (feature story), robotics and AI.
These new areas being pursued by all profit-seeking entities and future-proofing companies require consultation, wisdom and second opinions from an external entity, for a successful undertaking. It is here that CESIG sees itself as being relevant and as an evercontributing group under IEM.
We have started this by putting together in this issue of JURUTERA some thought-provoking ideas and approaches. So, enjoy our gift to our members and feel free to be part of our contribution towards IEM being a learned body in the engineering fraternity and a catalyst to the nation’s economic development in the future.

by Ir. S. Vignaeswaran
Computer security, cyber-security, or IT security, is the protection of computer systems from theft of or damage to hardware, software or electronic data, as well as from disruption or misdirection of the services they provide, with respect to all stakeholders.
If attempts are made to comply with the above across the board in any company, the cost will not only be prohibitive but the measures will also be complex, tedious and
The scope of the cyber-security has to be established and defined precisely for maximal effectiveness. This allows for the focusing of solutions towards only the area of vulnerabilities, thereby reducing cost and increasing simplicity.
However, this depends on the level of computer automation and the level of cyber-threat that can be imposed upon it. As such, cyber-security approaches will differ from system to system, just as the perspectives to risk differ from company to company.

Even within real-time online systems, we have fire-fighting, HVAC, telecommunication, lighting etc. systems that may or may not fall under the cyber-security system coverage.
self-defeating. As such, prudence and innovation combined require that cyber-threats be defined and identified so that specific counter measures can be applied at acceptable compromises.
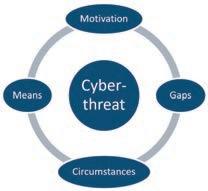
Cyber-threat is defined as “the possibility of a malicious attempt to damage, disrupt a computer network or system, deny access or steal information”.
This definition, though more concise, places the impact of all cyber-threats, irrespective of their origin, on an equal footing. It is not
So, segmentation of the potential cyber-threat targets is an essential part of the evaluation process.
The objective of SCADA cyber security is to funnel all system threats away from the critical, operational and end-user systems for the purpose of elimination. Utility, production line and business SCADA systems are continuously operating systems that continuously generate revenue for the business entity. As such, its unanticipated downtime is not only unacceptable but it can also be unaffordable, like that of a nuclear reactor. To put it in another way, SCADA systems are computer systems that oversee the generation of corporate revenue by controlling the relevant processes or productions.
The risk to a SCADA system is the impact of not fulfilling its deliverables correctly, consistently and in a fail-safe manner.
the correct approach for SCADA systems and therefore, it has to be refined with the weightage of the potential source of cyber-threats and the SCADA impact. It has to be explicitly stated that SCADA is NOT an IT system but is related to it. Unfortunately, all if not most cyber security measures are for IT and not SCADA systems specifically. This metaphorical kitchen knife being in the bedroom is an issue and concern that is being addressed here. The best way to protect systems is to do a cyber-security scoping.
There were several technology trends driving the cyber-threat landscape in 2018 and into 2019. The basis for these trends is as follows;
i. The computer is superior to humans in so many ways that it is impossible to get anything done without them. It is this extreme reliance on them that has caused cyber-threats to be ever present in our lives.
ii. The computer works so fast, accurately and without rest that it
does not allow human intervention or supervision as desired. The computer applications are result-orientated more than correct process orientated. The correctness of process is basically programmed in and it is this that carries with it the human errors and weakness, to be exploited by the cyber-threats. All this is done with the speed of computing which makes cyber-threats undetectable to the humans until it is too late or it manifests itself in a humanly detectable manner.
iii. Computer networks, systems, Internet, application programming etc. are man-made and so have inherently human flaws built into them. Therefore, the cyber-threats exploits these inherited DNA flaws. Using more humans to offset the “computer flaw” only increases instead of decreases cybersecurity threats.
iv. We are increasingly dependent on standardisation of networks, protocols, data, application etc. It is this standardisation that allows cyber-threats to use the consistencies, to affect many people, many places, many times over. Does this mean that we should abandon the notion of standardisation?
v. Computer interconnectivity has reached a level where being “not connected” is considered “out-of-place” and unacceptable at times. This has allowed cyberthreats to reach the masses in a multitude of ways, simultaneously and instantaneously.
vi. Lifestyle digitalisation has seen TV, phones, radio, newspaper etc. digitalised and computerised. So now, the doors to cyber-threats includes hand phones, iPads, laptops and USB drives, among others.
To understand any problem, we as engineers, must go back to the first principles and see the root cause, the circumstances and frequency of occurrence … to be able to identify a permanently viable solution
vii. High mobility of company staff has given rise to in-house information slowly drifting to the outside world at an increasing rate. This only arms the cyber-threat even more.

viii. Centralised, cost optimised, cloud-based data storage has seen more and more confidential company information leave the physical boundaries of the company premises. This has encouraged cyber-threats in ways that were not possible before.
ix. High-speed communication mediums have allowed data and applications to travel faster than before, increasing with time “exponentially”. This in turn has allowed cyber-treats to propagate at a similar rate, faster than before as well.
x. The contextual nature of computer and IT applications with respect to human values is the basis for cyber-threats. Deleting unwanted files is acceptable but deleting wanted files is not. Hence, the definition of wanted is vague, contextual, varies from person to person and it is time-based. Therefore, it is the “intent” of the computer activities that decides whether it is detrimental or beneficial. Unfortunately, the former or the latter cannot be established without letting it happen first and then only, in hindsight, judge the consequences of the actions.
xi. Solution providers often tell their clients that their applications are 100% compatible and will operate seamlessly with the current IT infrastructure, and for the most part, this is true. The problem arises when we start adding IT security solutions from different manufacturers regardless of the
granularity of their configuration settings – thereby causing “technology gaps” to be always present.
No cyber-threat could ever affect or impact a typewriter … so why do we even think of protecting it? A digital calculator is not web-based to protect, a digital watch is too cheap to protect, a digital microwave has no business basis to protect and the only protection for PC is a re-format. Therefore, what we are exactly protecting is… computer availability, business functionalities and its data/ information/knowledge... which are the organs and blood of a company.
xii. Technology gaps will always appear for another simple reason: Developers will always keep certain portions of their code proprietary as part of their competitive advantage. Hence, true compatibility and interoperability may only be 90% at best. It is these that are known as technology gaps and it is through these gaps that attacks usually occur.
xiii. One of the most problematic elements of cyber-security is the constantly evolving nature of security risks. The traditional approach has been to focus resources on crucial system components and protect these against the biggest known threats, which meant leaving “lower priority” components and system undefended. It is via these unprotected systems less dangerous that cyber-threats exploit.
xiv. Internet of Things (IoT) where individual devices connecting to the Internet or other networks is the buzzword and trend of things. However, it is also the very same connection to cyber-threats as well.
xv. Big data is another buzzword of the times, allowing highspeed, automated processing of enormous information stored in hand phones, laptops, Web
browser, desktops and elsewhere. These are the very means and targets of cyber-threats.
xvi. Automation of computer activities with artificial intelligence (AI) so that there is minimal human supervision required, is spreading across the IT landscape. Who has stopped to think that it is this very same AI that powers and nourishes the cyber-threats?
xvii. Modern co-operative and coordinated processing trends in IT are the very means that cyberthreats are being used to target the individuals and the collective. Gone are the days of individualistic glory hunting virus writers who boost their ego by being a nuisance.
xviii. Data is the new “oil” of the digital economy, so it is perceived by many, and like “oil reserves” that most companies are equated to, that cyber-threats mine and undermine, threatening that very commodity.
In the above, we have identified at least most of the “whys” that give rise to the existence of cyber-threats. Now, let us look at the categorisation of the cyber-threats so that we can exploit their weakness and weaken their strengths.
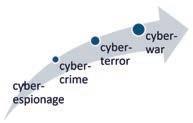
Let us look at the macro or broad categories of cyber-threats. Cyberthreats are siloed into the following groupings:
i. Cyber-espionage is the practice of using computer systems and information technology networks to obtain secret information without the permission from its owners or holders. Cyberespionage is most often used to gain strategic, economic, political or military advantage, and is conducted using cracking techniques and malware.
ii. Cyber-crime which includes single actors or groups targeting computer systems and corporate IT networks for financial gain, directly and/or indirectly.
iii. Cyber-terror which is intended to undermine electronic systems and cause panic or fear. The
disruptive use of information technology by terrorist groups to further their ideological or political agenda. This takes on the form of attacks on networks, computer systems and telecommunication infrastructures.
iv. Cyber-warfare involves nationstates using information technology to penetrate another nation’s networks to cause damage or disruption. Cyberwarfare has been acknowledged as the fifth domain of warfare (following land, sea, air and space) to impair such infrastructural services as transportation and medical services or to interrupt commerce.
SCADA professionals only talk about cyber-security or cyber-threats in terms of the 4 categories listed above. There is a cyber-threat perspective that a SCADA system is not a financial or library of confidential information system. Since SCADA systems do not have direct (banking) financial information or digital currencies, the concern about cyber-crime can be misleading. If the aspect of ransomware is included, then the notion of “being robbed without having money stolen” takes on a whole new meaning.
Cyber-espionage has the least bearing on a “pure” SCADA system. Knowing about the field devices detail only embarrasses the company in terms of its confidentiality and security aspect, which could be rectified accordingly. However, both cyberespionage and cyber-crimes tools which are meant for generic purpose IT networks can hang, corrupt or disrupt SCADA systems unintentionally. On that basis, they are considered as threats. National-level SCADA systems are more concerned with cyber-terror and cyber-warfare. This is because a national-level infrastructure SCADA
system can be modified as a “DDOS” tool for an enhanced multi-level multiprong cyber-attack weapon. Such Distributed Denial Of Service (DDOS) to the public has dire consequences.
Cyber-war by nations or cyberterrorism by “pseudo-nations” has the same outcome to the intended victim with a nationalistic SCADA system. They both interrupt and threaten national security.
SCADA systems are self-contained business systems that need not communicate with “outsiders”. Hence, they can be Web-isolated.
The purpose of a SCADA system is to automate and with that comes ever reducing human intervention. As such, human interfacing can be restricted to the maximum. The SCADA system software is specifically built for a specific purpose. So the software is “cast in stone” by functionality. There should be no need to amend, modify or enhance the software that should function like a “pencil” (in functionality) to its end-user.
Unfortunately, building SCADA systems upon the Windows platforms defeats this purpose with the default Web-access requirement for Windows update.
Nevertheless, the measures against cyber-threats include:
i. Eliminating web access and surfing
ii. Eliminating or minimising human access and errors
iii. Restricted patching and modifications
iv. “Technology gap” reductions
In many ways, this will be seen as a “regression” of the SCADA system.

Without going to into too much detail, the matching of the threats in the wild to the following measures has to be done with the hope minimising their potential impact.

Sika provides an extensive range of injection systems for all types of leak sealing applications in concrete, masonry and natural stone structures. These can be used at any time, including during the initial construction works, or later to extend the service life during any subsequent refurbishment, according to the specific project’s requirements.
The above has to be augmented with the following layering approach to SCADA security systems, to eliminate technology gaps.
i) Macro operational gaps
Threats originate from the boundaries of the SCADA system. It is unfortunate that the modern SCADA system has at least 3 interface points:
• Corporate IT system
• Field data network system.
• SCADA – human interface (HIS)
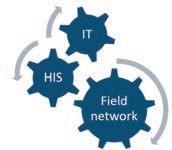
Each of these boundary points has a unique functional aspect that carries with it differing points of vulnerabilities. This is indirectly covered by the other cyber-security article in this magazine edition.
ii) Micro technological gaps
DVD drives can be locked or removed to prevent control operators from inserting CD-ROM or DVD-ROMs. The most damaging aspect is the ultraintelligence of Windows OS to autorun any ROM disk that is inserted into the drive. This does not allow the
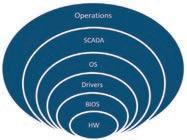
DVDs to be scanned first unless an anti-virus software specifically setup to do so. Even then, the 3rd party AV software is at the mercy of the Windows OS.
USB ports are a bit trickier now since both the new generation mouse and keyboards are USB based. Previously, they were PS2 socket based and all USBs on the PC can be generically blocked. Currently, the mouse and keyboard USB sockets can be interchangeable and can also be used as thumbdrive inputs.
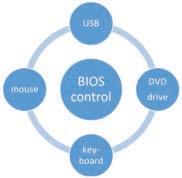
Charging of handphones via the USB ports is highly prohibited as the wireless handsets is a serious breach of the SCADA system security requirements. This is one of the reasons why the USB ports should be physically sealed to avoid this.
The use of wireless mouse and keyboard is prohibited as their use opens up the USB port and wireless signaling for abuse.
The process of keeping up with new technologies, security trends and threat intelligence is a challenging task. However, it is necessary in order to protect information and other assets from cyber-threats, which take many forms evolving over time continuously.
The primary objective of SCADA cyber-security is to avoid being hit, not to recover from a hit. This is very different from the perspective taken from the IT viewpoint.
Cyber-threats require us to change what we have been doing in the past with past values and adopt new ways and new values. If we keep doing what we have been doing, then we are going to keep getting what we have been getting so far.












Ir. Dr Ooi Teik Aun has garnered a string of achievements and accolades in five decades of his career. His commitment to lifelong learning and knowledge-sharing is nothing short of inspirational.

For his excellent contribution to the pool of knowledge, Ir. Dr Ooi Teik Aun was awarded the coveted Tan Sri Ir. Hj. Yusoff Prize 2019 from IEM in April.The award is the highest recognition for outstanding technical papers on engineering contributed by corporate members of IEM in the civil engineering discipline.
Ir. Dr Ooi’s winning paper, titled The Present & Future Sustainable Use of Underground Space in Malaysia, contains his detailed research findings, expert opinions and assessments for the advancement of Malaysia’s Sustainable Tunnelling & Underground Space Development.
Knowledge-sharing has always been a priority for Ir. Dr Ooi, who now helms the IEM Training Centre Sdn. Bhd. and IEM Academy Sdn. Bhd. He finds deep satisfaction in imparting knowledge and grooming young engineers into professionals with the necessary skills, exposure and attitude. He says integrity is one of the most important traits a professional must have.
“You can be the best engineer but if you don’t have integrity and you place money above everything else to the point of jeopardising your honour, then you will lose your self-respect,” he says, adding that everyone should embrace lifelong learning as knowledge is wealth beyond money and other material things.
“When we use knowledge in the proper direction and have the right attitude, money will come,” adds Ir. Dr Ooi, who started his career more than 5 decades ago. He has held numerous positions in various professional bodies in the field of his expertise, such as Founder Chairman of Tunnelling & Underground Space Development under the ambit of IEM’s Tunnelling & Underground Space Technical Division (TUSTD).
Among his most notable achievements was his major involvement in the elaborate design of the SMART project in Kuala Lumpur nearly 2 decades ago, with the use of the innovative Variable Density Tunnel Boring Machine (VD TBM) in the Klang Valley MRT project. The project won several international awards, including the British Construction Industry International Award (2008) and the UN Habitat Scroll of Honour Award (2011) for its innovative and unique management of stormwater and peak hour traffic.
The United Nations hailed it as one of the most innovative projects in the world for an urban issue, while CNN listed the SMART Project as one of the world’s Top 10 greatest tunnels that could prevent billions of dollars in potential flood damage and costs from traffic congestion in the city centre.
Ir. Dr Ooi says the SMART Tunnel also gained the respect of the tunnelling fraternity around the world as it broke new ground, not only in Malaysia but also worldwide, by combining the functions of stormwater drainage and motorway tunnel. Stretching 9.7km, SMART Tunnel is the longest tunnel in SouthEast Asia and the second longest in Asia. Constructed using a slurry shield Tunnel Boring Machine (TBM), it is also among the largest diameter tunnels in the world, with a diameter of 13.2m.
“The Variable Density TBM tunnelling was ‘reinvented’ in Malaysia, whereby all conservative rules were broken,” says Ir. Dr Ooi, who is noted for having the right skills and expertise to take tunnelling to the next level in innovation technology.
Ir. Dr Ooi says tunnelling and underground space development in the likes of MRT works will go on for a long time. He emphasises that a developed country must have MRT transportation networks, without which it is considered underdeveloped. As urban centres become more and more crowded, MRT transportation networks are necessary to move people quickly and efficiently. This sector of transportation as well as tunnelling and underground space development also opens up many job opportunities for the engineering and construction sector. He advises young engineers to look at the potential of this sector and to seek not only opportunities and prospects but also mentors from whom they can learn and get guidance.
“In theory, tunnelling and underground space development is a lifelong employment. Fresh graduates should learn from good mentors and learn the right skills in investigation, design and construction supervision. Money is important but this should take second place for a fresh graduate, who must be orientated to have good professional ethics in the formative years. His integrity and service for the protection of public interest must be entrenched at this stage. In the long term, the blue ocean is yours. Get all the professional memberships which will give you a passport to the global market,” he adds.
Engineering undergraduates and young engineers who join IEM can gain from its training and development programmes. Ir. Dr Ooi says that IEM, through the IEM Academy, has signed an MoU to organise the Master of Civil Engineering degree with specialisation in Tunnelling & Underground Space. In addition, IEM TUSTD will continue with IEM Academy to hold tunnelling conferences, talks, seminars and workshops.
“Civil and Structural Engineers will always be required in each and every project. The demand may be cyclical, depending on the economy as well as supply and demand. At present, the building sector is in an oversupply situation. Nevertheless opportunities, while challenging, will still be there. Malaysia is expected to achieve developed status by 2025. The growth will be slow and more opportunities will be
available in Maintenance Engineering/Asset Management,” he says, adding that it is important for engineers to keep themselves updated and to make it a point to attend educational events such as talks and lectures.
At the third Ir. Chiam Teong Tee Memorial Lecture held in March this year, Academician Dato’ Ir. Prof. Dr Chuah Hean Teik gave a lecture on Developing Engineering Workforce, Designing A Better Future, which focused on trends and challenges the world was facing, with the coming of the new Digital Revolution or 4th Industrial Revolution (4IR). These include urbanisation and inequality in wealth distribution, clean air and clean water, food distribution, energy, global warming, climate change, ageing population and physical-space and cyber-space security. Dato’ Ir. Prof. Dr Chuah also touched on challenges that future engineers will face, vis-à-vis globalisation and mobility and the skills young graduates should acquire to overcome these challenges as well as issues and challenges for STEM education in Malaysia.
“To tackle the challenges, one requires new ideas and inventions which will only be possible with excellent knowledge workers. New technological breakthroughs will require brand new skill sets, particularly Science, Technology, Engineering & Mathematics (STEM) skill sets, in the engineering workforce. A good engineering workforce (engineer, engineering technologist and engineering technician) is considered the driver for success in this globalised world,” says Ir. Dr Ooi.
“What is important now is for universities to produce graduates who can embrace lifelong learning and possess strong basic fundamentals of natural sciences and engineering, and who are ready to evolve rather than graduates who are just ready-to-market as many will be entering a whole new sea of employment,” he says, emphasising that it is important to deal with the mobility of the engineering workforce globally and to look at how IEM can work with the institutions of higher learning and the Ministry of Education.“Let us look forward to having locally trained graduates with a global employment outlook and benchmark with the global best.”
To gain international acceptance, Ir. Dr Ooi says the initiative must come from young engineers themselves. “In my opinion, young graduates must plan to sit for MIEM and CEng MICE for Civil Engineers within the first five years after graduation. For each year of delay, it will become progressively more difficult to achieve these qualifications,” he says.
According to Ir. Dr Ooi, it is an advantage for young engineers to have mentors to help them develop their careers. “Mentoring is important as I myself can testify. I would not be where I am today without mentors who helped guide me in my early career development,” he says.
He names nine mentors. The first was the late Prof. P.W. Taylor, a Professor in Geotechnical Engineering and later Dean of School of Engineering, Auckland University, New Zealand, who put him on the right path for research and development work, paper writing and getting papers published, including internationally.
Next was the late Ir. Thean Lip Thong, Director-General of PWD (1971-1974), President IEM (1964-1966), Director Peruding SSP (1974-1988) and Founder of the IEM Thean Lip Tong Scholarship (from 1989). Ir. Thean regarded Ir. Dr Ooi’s assessments of two incidences – Bukit Gasing Development landslide in Petaling Jaya and the collapse of a low-level bridge in Temerloh in 1970 – as highly credible and accepted them as expert witness reports. He also picked Ir. Dr Ooi to attend the 3rd Southeast Asian Geotechnical Society (SEAGS) conference in Hong Kong in November 1972, which opened up opportunities to network with fellow engineers in the same field of interest.
His other mentors are:
The late Tan Sri Datuk Ir. Prof. Dr Chin Fung Kee, who had a long list of achievements and contributions, including being the honorary consultant to the Malaysian Government on numerous engineering problems and projects. He appointed Ir. Dr Ooi as Honorary Secretary to the 4th SEAGS and shaped both his



Now there is a waterproofing solution specifically engineered for this application. With the AQUELLA™ system, you can specify with confidence, as it:
• Bonds fully to both substrate and skin wall
• Seals around rebar and penetrations
• Has excellent weather and exposure resistance
• And can be spray-applied
Specifying the AQUELLA™ system delivers peace of mind waterproofing performance for your project, long after it is completed. The main contractor also enjoys speedy spray application, schedule flexibility and minimal application hazards at the job site.
Contact GCP today for a free demo: asia.enq@gcpat.com.
career path and higher academic achievements to reach the doctorate level.
Ir. Dr Ting Wen Hui, who held various positions including Superintendent Engineer, Research and Laboratory, PWD, and IEM President (1995/97). Both Ir. Dr Ooi and Ir. Dr Ting co-authored numerous papers on Geotechnical Engineering. Ir. Dr Ting made an impact on Ir. Dr Ooi’s life, both professionally and academically.
The late Tan Sri Datuk Ir. Mahfoz bin Khalid, Director-General of PWD (1977) and President of IEM (1977), had a close relationship with Ir. Dr Ooi and was responsible for him pursuing a PhD degree overseas.
The late Dato’ Ir. Mustafa b. Ahmad, Director-General of Malaysian Highway Authority (1980 - 1992) and the President of IEM (1990/1992) opened many doors for Ir. Dr Ooi in
The late Prof. Thomas Hamilton Hanna, Professor and Head of Civil & Structural Engineering at University of Sheffield, United Kingdom, was a dear friend who lent a shoulder for Ir. Dr Ooi’s trials and tribulations.
The late Ir. Chiam Teong Tee, lecturer and later Dean of Engineering Department, University Malaya (1973 - 1976), President of IEM (1981/1982) and Founder of Perunding Bakti Sdn Bhd in 1976. Ir. Dr Ooi credits him for his initial involvement in a big arbitration case and for sharing knowledge on arbitration and dispute resolution.
Prof. Bala Subramaniam, Professor of Geotechnical Engineering, Asian Institute of Technology, Bangkok, who also sits on the SEAGS Executive Committee and the Editorial Board of Geotechnical Engineering Journal. He and Ir. Dr Ooi had been President of SEAGS and knew each other since 1975. Prof. Bala had always been there to help Ir. Dr Ooi in his times of need.
Ir. Dr Ooi’s life is not one without regrets. If he could turn back the clock, he said, he would not have left PWD because serving the government meant opportunities to serve the people, to get first-hand knowledge of government developmental plans for the nation and to make an impact on the people’s wellbeing.
He explains: “My greatest regret was leaving PWD in 1982. I was Superintendent of Laboratory & Research in the Design & Research Branch of PWD. I often tell people that during my time, Class 1 Engineers were those in Government Service. They had the authority and everyone wanted to see them. Class 2 Engineers were engineering consultants who had secured jobs from Government contracts but were subservient to Class 1 Engineers. Class 3 Engineers worked as contractors or served contracting organisations. In turn, they were subservient to Class 1 and Class 2 Engineers.
“In today’s context, Class 3 Engineers can obtain jobs from Class 1 Engineers and employ Class 2 Engineers to work for them. Roles have been swapped. This means engineers in consulting practice have become Class 3 Engineers. Class I Engineers have a greater role to play in shaping the country and changing the livelihood of the people. Fortunately, I am always friendly with everyone. Those in the industry still regard me as a geotechnical expert, as if I have not left PWD. When Highland Tower Condominium collapsed in December 1993, I was invited to serve on the Technical Committee Independent Investigation team of the Ampang Jaya Municipal Council Commission of Enquiry. At that time, I had already left PWD for 10 years but I still played a key role in that independent voluntary service,” he says.
In the public service, integrity is a must and Ir. Dr Ooi stresses that without it, society and even the nation will collapse. He says: “In Malaysia or anywhere in the world, mega infrastructure projects are usually driven by politicians in power. It is believed that rampant corruption brings about kleptocracy, a term to describe a government ruled by corrupt politicians who use their political power to receive kickbacks, bribes and special favours at the expense of the populace.”
He adds that kleptocrats may use political leverage to pass laws which enrich them or their constituents and they usually circumvent the rule of law. Situations can get very bad, requiring the government to cut and suspend infrastructure projects,
The principal of a long-established Environmental Engineering Company in Malaysia is seeking to divest his shareholding. The company has extensive experience in sewage treatment, air and water pollution control and treatment, solid waste handling and ancillary turnkey projects related to the reduction of environmental pollution. The principal is seeking a gradual divestment. Return of investment projected to be within four years. Interested parties are invited to discuss particulars by contacting the principal via Phone/WhatsApp at +6012 383 0564.





as well as impose contract price reductions. Professionalism and ethics of protection of public interest have been called to question.
“Unfair prices topped up by greedy politicians and unscrupulous contractors will inflate the tender price for private interest at the expense of public interest. The rot must stop in order to allow the country to progress and to achieve developed nation status. Professional engineers must uphold their ethics. People must reject kleptocracy for the sake of public interest,” he says.
In relation to the protection of public interest, he reveals that the International Tunnelling & Underground Space Association (ITA-AITES), in collaboration with FIDIC, is preparing the Emerald Book for Tunnelling & Underground Space Works, due for publication at the World Tunnel Congress 2019 (WTC 2019) in Naples, Italy on 2-8 May, 2019.
“I have suggested to the drafting committee of the ITA ExCo (Executive Council) to include an exclusion clause in the Conditions of Contract contained in the Emerald Book to outlaw any clause of the contract document which is in conflict with the protection of public interest. A professional engineer who prepares the contract document for mega infrastructure project is duty-bound to protect public interest as spelt out in his professional conduct and ethics,” he says.
Through his involvement in such professional associations, Ir. Dr Ooi continues to play his part in highlighting issues and influencing decisions in areas that matter, particularly those concerning public interest protection.
“We can be successful in everything we pursue, provided we have certain sets of discipline, such as having integrity, being prudent in our spending and having wisdom when making investments for our future,” he says.
Ir. Dr Ooi says his latest achievements are bringing the World Tunnelling Congress (WTC) 2020 and the 46th General Assembly to Malaysia through IEM for the first time in 46 years since the founding of the International Tunnelling & Underground Space Development Association (ITA-AITES). The event is held annually and member nations wishing to play host can bid for it three years in advance. At the WTC 2018 General Assembly, ITA had 75 Member Nations and 300 corporate/individual Affiliate Members.
“IEM TUSTD was formed in February 2000 and I became the founder Chairman. It was endorsed as the 50th Member Nation of ITA at the General Assembly in Durban in May 2000. By hosting WTC 2020 in Malaysia, IEM has achieved Global Engineering Player status, especially in the emerging market of tunnelling & underground space. Furthermore, Malaysia is acknowledged by the tunnelling world as the most innovative Member Nation and has won many awards,” says Ir. Dr Ooi.
IEM TUSTD has systematically organised International Conferences & Exhibitions in Tunnels & Underground Space (ICETUS) to record the significant stages of the development such as ICETUS 2006, ICETUS 2011, ICETUS 2015, SEACETUS 2017, SEASET 2018 and WTC 2020. IEM TUSTD has also held evening talks, short courses, workshops and seminars.
Ir. Dr Ooi and the WTC 2020 organising committee have specific deliverables to achieve. “We aim to hit the target of more than 2,000 participants, which will be the biggest historical recorded number of participants from all over the world. We also want to get the largest number of exhibitors in the history of WTCs with a target of 200 booths. In addition, we want the best keynote lectures to be delivered by invited professionals,” he says.
The professionals are Prof. Charles Ng, Chair Professor of Civil & Environmental Engineering, The Hong Kong University of Science & Technology and President of International Society of Soil Mechanics & Geotechnical Engineering (ISSMGE), Prof. Chung Sik Yoo, Professor of Civil & Environmental Engineering at Sungkyunkwan University in South Korea and President of International Geosynthetic Society (IGS), Er. Seng Tiok Poh, Planning and Design Director for Mass Rapid Transit Corporation (MRTC), Malaysia, and Prof. HeHua Zhu, Distinguished Professor in Geotechnical Engineering of Tongji University, Changjiang Scholar Chair Professor of China, Director of Engineering Research Center of Information Technology in Civil Engineering of the Ministry of Education of China.
Ir. Dr Ooi adds that the MuirWood Lecture will be decided by the ITA Council and the WTC 2020 committee expects to receive paper contributions of more than 500, which will add to the existing wealth of knowledge.
What’s next for Ir. Dr Ooi? Despite his tight schedule, the 78-yearold has another “big job” in the pipeline. He is writing a book. This comprehensive account of his life will include stories about people who have helped shape him into what he is today, from close family members to professionals in the engineering fraternity. Through this book, which will be self-published before the end of the year, Ir. Dr Ooi shares personal stories, peppered with the rags-to-riches family history, his setbacks and achievements and his principles and outlook in life. He is also imparting his knowledge in engineering by including many papers which contain his research findings, opinions and assessments in his areas of expertise.
“I hope to inspire the young generation and tell them the route I have taken in my professional journey as well as the principles that I hold dear in discharging my duties and responsibilities. I believe in mentorship and, while I would love to become mentor to every young engineer I meet, I know that’s beyond my capacity so I hope this book can do that and reach out to as many young engineers and aspiring engineers as possible,” he says.
With his roles in the educational arms of IEM to help develop both young talents and professionals in engineering, Ir. Dr Ooi walks the talk, driven by his belief in lifelong learning not only for others but also for himself, as well as his love to continuously impart knowledge and serve the community.

WHAT ARE INDUSTRIAL CONTROL SYSTEMS AND WHY IS IT IMPORTANT TO SECURE THEM?

What is an Industrial Control System (ICS)? You may have heard a lot of different acronyms that purport to describe ICS, SCADA or Supervisory Control and Data Acquisition, DCS Distributed Control System, PLC or Programmable Logic Controllers.
Basically ICS is any system – whether it is a PC or other purpose-built hardware or software – that is actually controlling a process in the real world. You can find these types of systems in industries like manufacturing, oil & gas, petro-chemical and other types of industrial sectors. One of the key things in defining industrial control systems is to really get the differentiation between other terms like critical infrastructure and Internet of Things.

You can have something that is a part of IoT and which is also in an industrial control system and certainly something that's part of the IoT in an industrial control system which is also part of critical infrastructure.
In industrial control systems, the keyword is INDUSTRIAL. A system that automates milking cows would definitely fall into the category of an industrial control system; however, I would not consider this as critical infrastructure.
Likewise, something such as a Wall Street financial system is certainly critical infrastructure but is probably not an industrial control system as it contains only informationbased type assets and does not control anything in the physical world. Certainly there is a lot of overlap between ICS and critical infrastructure. Think about electricity and water for example.
The last thing to talk about is the Internet of Things (IoT) Here the keyword is “things”. This is where networks merge with previously-unconnected everyday items such as door locks, cars, toasters, trains and drones; it is a big trend in both the consumer and the industrial sectors.
In traditional enterprise IT, we think about information security as achieving confidentiality, integrity and availability of information with confidentiality being our primary concern. We want to protect data like personal identifiable information, credit card numbers or intellectual property. We want to keep secret data secret.
In ICS, our primary consideration is safety, followed by availability, where we ensure the control system stays up and running. Integrity here ensures that what is on the control room screen actually matches what is going on in reality. There can be some intellectual property on the plant floor or maybe on an engineering laptop, so confidentiality does come into play. However, information like the fill level of
a particular tank doesn't require the same level of security controls that you will have on sensitive data that you will find on the IT network.
1. Industrial control systems are really hard to change, as some of them have 20/30-year lifecycles. The attitude in the ICS world is if it's working, don't touch it. This makes traditional enterprise IT security activities such as security testing and patching very difficult in the ICS space.
2. There is a lot of different technology and significant differences between the IT and the ICS environment. If you have a great IT security program, it may not necessarily cover your ICS assets and there are a couple of reasons for that.
Firstly, your IT team may not actually be managing your ICS assets. ICS systems are commonly acquired along with the equipment they control, so they are mostly installed, configured and run by plant engineers on site, not IT. This means IT does not know what control systems are being used, and there is rarely a reliable inventory.
Secondly, ICS is generally vulnerable. Some of the security features that you would expect in the enterprise IT security space, like authentication and encryption, aren't necessarily available on ICS communication protocols. We also find that ICS is a lot more connected to enterprise IT networks and to the Internet than some asset owners think, hence creating a lot more exposure there. This provides a vector for bad guys to pivot from one network to another.
When building a cyber-security program for your organisation, we recommend taking into account both the IT and ICS assets and build an overarching Enterprise program that addresses the needs of both.
I shall discuss four different iconic industrial controls systems attacks that had occurred in the past decade.

STUXnet (a.k.a. Operation Olympic Games) was the name given to a computer worm that was widely believed to have been created by a nation-actor, allegedly the USA and Israel, though neither country admitted it. Its initial purpose was to
disrupt manufacturing at a uranium-enrichment facility at the Natanz plant in Iran for the explicit purpose of slowing down Iran’s nuclear power program. First launched in 2008 as a series of cyber-attacks, it wasn’t clearly identified until two years later.
STUXnet spreads by moving from machine to machine looking for PLC software. This software controls programmable logic controllers (PLC). PLCs are devices which control industrial processes. In this case, the process affected was the gas centrifuges that enriched uranium. The worm, having infected these machines, began to continually replicate itself. It became dormant when it encountered a machine that had no PLC software. Once the worm detected a machine with the software on it, STUXnet fed the PLC with false information, intercepted the data the PLC generated using the false information and reported normal operation back to PLC so that it appeared that everything was working within operating parameters. The affected software was and continue to be prevalent in industrial controls networks.
When the centrifuges began malfunctioning, the plant operators did not know about it until it was too late. How did the worm infiltrate the production network? It is plausible that the agent used was the IT networks of the subcontractors. There the subcontractors became the attack vectors when they transferred files from their laptops to USB drives and, unknowingly, infected the plant control networks.
Other repeated attacks continued to take place before the Iranian authorities, in June of 2010, with the aid of security consultants, realised that their plant was the victim of a cyber-attack and responded by identifying the Command & Control servers, blocking them and eventually taking them offline. The infections were purged over the next several months.
This attack is seen to be iconic and unprecedented due to both the geopolitical context surrounding the attacks and the magnitude of the operation. It is the first known attack to have succeeded in undermining operations of a critical infrastructure and damaging the facilities.
December 23, 2015, was a watershed day in the history of cyber-security.That was the day that Ukraine’s electrical grid came under a cyber-attack. Approximately 225,000 people were affected, 30 electrical substations were switched off and consumers were without electricity for between 1 and 6 hours.
The malware responsible for this cyber-attack was BlackEnergy. It was also the second ever to be designed and deployed for disrupting physical industrial processes (STUXnet was the first).
There are still many grey areas surrounding this cyberattack which targeted the Ivano¬Frankivsk power station in West Ukraine. No nation-actor was attributed in this attack, though sentiment ran high that it was the Russian group, The Sandworm, that was behind the attack. What was


Source: www.bankinfosecurity.com
interesting was that the attack was synchronised and coordinated and that it affected three regional electric power companies.
The cyber-attack was complex and could be broken down to the following steps:
1. Prior compromise of corporate networks using spear-phishing emails with BlackEnergy malware
2. Seizing SCADA under control, remotely switching substations off
3. Disabling/destroying IT infrastructure components (uninterruptible power supplies, modems, RTUs, commutators)
4. Destruction of files stored on servers and workstations with the KillDisk malware
5. Denial-of-service attack on call-center to deny consumers up-to-date information on the blackout.
Further study of the attack showed that six months before the attack, the BE malware was sent, via phishing emails, to plant engineers and operators. Here the malware managed to gather legitimate login credentials, with which the attack was mounted. After the attack was concluded, another malware, KillDisk, was deployed to delete certain files from certain targeted systems, to overwrite firmware and to disrupt communications to server Uninterruptable Power Supplies (UPS) so as to interfere with restoration efforts.
One year later, a week before Christmas, Kiev suffered a power blackout which left 80,000 homes without electricity. The malware, called CrashOverride/ Industroyer, that attacked the Kiev grid, turned out to be more sophisticated, adaptable and dangerous than the cyber-security community had imagined. Together, these two attacks (2015 and 2016) comprise the only confirmed cases of hacker-caused blackouts in history.
Imagine you’re driving on the highway when suddenly, someone has remotely taken control of your vehicle. The air-conditioning vents start blasting hot air. The radio blares metal rock music at high volume. Your car dashboard lights up like fireworks. The windshield wipers turn on. Your steering is locked. You can’t move. You’re stuck. You panic.
Sounds far-fetched? It shouldn’t. It’s been done.
In 2015, two American researchers, Charles Miller and Chris Valasek, and a journalist from Wired magazine, Andy Greenburg, proved that it was possible to remotely take control of a connected vehicle. From the comfort of their living rooms, the researchers hacked the control system of a Jeep that was being driven by Greenburg. They were able to remotely take control of the vehicle using the Uconnect software that connected the Jeep to the Internet. They then went
Yes! I would like to be a subscriber of The Institution of Engineers, Malaysia’s publications
Name: _________________________________________________________________________________________________________
Mailing Address: _________________________________________________________________________________________________
Country: ________________________
Company/Institution: ______________________________________________________________________________________________
Title: ____________________________________________________________________________________________________
Telephone No: _________________________ Fax: _________________________ Email: _________________________________
New Subscriber Renewal
Please commence my subscription from: _________________________(month/year) Signature: _______________________________
To start your subscription of IEM’s publications, complete this form and mail it back to the address below. For faster processing, fax it to: +603 7493 1047. Thank you.
What is your primary job title?
Corporate Management (including chairman, president, proprietor, partner, director, vice president, general manager, division manager, import/export manager, other corporate title)
Management (including project/contract/equipment/service/transport district manager, clerk of works, other technical or operating manager)
Engineering/Design (including chief engineer, chief designer, civil/ highway/mechanical/planning engineer, other engineering/design title)
Buying/Purchasing (including chief buyer, buyer, purchasing officer, other buying/purchasing title)
Titles allied to the field (architect, consultant, surveyor, research and development professor, lecturer, supervisor, superintendent, inspector or other allied title)
Others (please specify) ____________________________
What type of organisation do you work in? (Tick one box only)
Contractor
Sub-contractor specialist
Design and build contractor
Consulting engineering/architectural/quantity surveying practice
Mining/quarrying/aggregate production company
Petroleum producer
International/national authorities
National/regional/local government
Public utilities (electricity, gas, water, deck and harbour, other)
Manufacturer
Distributor/importer/agent
Construction department of large industrial/Commercial concern
Association/education establishment/research
Construction equipment hire/rental company
Project/construction management consultancy
Others (please specify) _______________________________
What are the main activities of your organisation? (Tick all that apply)
Constructions of:
Roads/bridges

Manufacturer of:
Construction equipment
Dams/reservoirs/irrigation Cement
Harbours/offshore structures Other construction materials
Foundations/tunnels
Distribution
Pipelines/refineries Construction equipment
Structures/steel work
Construction materials
Building (commercial, industrial) Hire/rental of construction equipment
Housing Design
Construction management Earth-moving/open cast mining Deep mining Aggregate production
Others (Please specify) _________________________________________
Rate (Please tick)
RM360.00 - 12 issues of JURUTERA
RM84.00 - 2 issues IEM Journal (Half-yearly)
Terms and Conditions:
1) The subscription is to be prepaid.
2) Please make cheque payable to Dimension Publishing Sdn. Bhd.
3) Subscriptions are not refundable.
4) Magazine/s will be sent to the mailing address given.
5) Students are entitled for a 20% discount from the above subscription rate.
6) Students must submit a photocopy of the student identification card together with the payment.
7) The above rate is inclusive of delivery charges and applicable in Malaysia only.
8) Additional delivery charges will apply to overseas subscribers.
For subscription enquiries, please contact +603-7493 1049 or email to info@dimensionpublishing.com

Source: Andy Greenberg/Wired.com
on to activate the radio, the ventilation system, and other systems, while the driver watched helplessly from behind the wheel.
The researchers also stopped the engine while the Jeep was speeding along the highway at 63 mph. A further example saw the braking system being switched off while in a parking lot and they also took over the steering system.
The researchers and journalist wanted to use this exercise to show how vulnerable connected cars could be when dealing with attackers.
Furthermore, this exercise is a clear example of what industry players face with when designing new systems.
In this case, IT infrastructure was not the only target: Products and services were the main focus of the attackers’ attention. Manufacturers often think their products are protected because their product development approach is hidden. However, “security by obscurity” and “security by air gap”, which involves stopping attackers penetrating directly into the information systems, just aren’t enough.
Cars are exposed to the same types of risks as other industries; in the past, these products were not linked to the Internet. Now, everything, including factories, vehicles and personal devices are connected and, as a result, they are left vulnerable and in need of more efficient and effective protection from cyber-attacks.
* Note: Jeep recalled 1.7 million vehicles after the vulnerability was made public.
Three attacks, three motives, three operating models. Attacks are becoming more diverse, methods are continually evolving, actors are increasingly bold. While motives are often different, their kinetic impact is dramatic. This is why raising awareness among industry players is paramount in the effort towards predicting, preventing, detecting and responding to similar attacks.
In each of the above mentioned scenarios, the approach to these attacks had a common theme. In most
cases, industrial attacks took advantage of the human element of cyber-security, followed by insecure systems, i.e. vulnerable computer networks and a lack of knowledge on the part of the individual operator.
A deeper look into those attacks on physical facilities revealed a common denominator. In the physical facilities attack, it was apparent that the plant operator did not know what was in the control network. There was no insight at all.
It is highly recommended that production/control networks be scanned as part of a security assessment exercise. How do you protect something that you do not know that you have? Once an initial scan of the control network is done, a plan can be made to remediated the findings and trigger the relevant processes.
The initial scan of the network will enable the facility to map out the control network. In most cases an accurate network diagram is not available. Once the network topology is known, several risk mitigation strategies can be put in place.
Strategies include setting up a layered defence which addresses security throughout the entire ICS extended network. There should be proper physical and logical separation between different types of networks. For example, access to PLC and SCADA devices should not be available on the corporate network. Security policies, people awareness and sufficient training are among other steps to be undertaken in setting up a defence. In many critical infrastructure attacks, the malware entered into the control networks after infecting the enterprise network via a USB drive. Policies prohibiting the usage of similar devices can be drafted and enforced.
Another recommendation would be to properly segment the network and install an industrial firewall in that network. The usage of a data diode is gaining traction as that allows control signals to flow one way and allows information to flow the other way, like a normal diode.
Practices from the enterprise security world could also be applicable in industrial control security. Practices such as very strict user privileges, independent from corporate network credentials, using strong passwords and authentication techniques are all applicable in industrial control systems security.
Securing industrial control systems is an ongoing affair and should not be at the expense of safety and uptime of the industrial facilities as lives are at stake.
Further reading: https://ics-cert.us-cert.gov/alerts/IRALERT-H-16-056-01
Author's Biodata
Ir. S. Vignaeswaran
The implementation of Building Information Modelling (BIM) in the country has been fragmented, to say the least. However, wide spread acceptance resides in a few major stakeholders with current and future benefits.
i. Architects have been using BIM for aesthetic purposes to sell their imagination via the 3-D visualisation of desired building.
ii. Engineers have been “putting together” building facilities with hindsight and foresight. With the depletion of engineering expertise over time, BIM may be the only tool that provides engineering insight in the future.
iii. Contractors are “doers” who need to anticipate physical issues that go against a smooth cost-effective field implementation endeavours. They will benefit the most from the standard approaches with high volume implementations.
iv. The “owners” need full contextual information for renovation, change, enhancement and functional opportunities to be exploited both now, and in the future. BIM serves as the “database” for that purpose.
v. The Government hopes the full implementation of BIM will assist in transferring knowledge between the generations of engineers to come. It is also the means of putting knowledge in the hands of many – one of the many measures of a nation’s progress.
As the world progresses, the need to be effective and efficient has only increased. This can be seen in the way our lifestyle has changed from the early days to the present and in the projected future.
It is futile to hang on to our past practices, old habits and comfort zones based on cultural, political, religious and human nature basis. One such area is the adoption of BIM in the construction industry.
Unfortunately, the only measurement for efficiency and effectiveness has been KPIs in terms of ringgit, as balanced scorecard practices and other measurements
have yet to be prevalent. This has led to such KPIs being subjected to cost increases and misplaced optimisation. Some argue that it is realistic to use cost-based KPIs only, but if engineering excellence is the objective, then this can be misleading. This is especially so when risk, safety, reliability, innovation etc. cannot be quantified exactly and comfortably with costs.
Therefore, it will be these areas that are going to be compromised when we go overboard with the cost-based BIM engineering KPIs. Having said that, when should we have proper engineering based KPIs for BIM, for an industry wide comparison?
There are numerous digital AutoCad drawings from previous projects that will be used in future projects with slight modifications. However, any experienced engineer knows that brown field (modification) projects are far more tedious than green field (new approach) projects. As such, when one modification is made to a building, then multiple discipline related drawings have to be updated accordingly. With BIM, all the relevant and related drawings are updated automatically. This comes with the benefit of clashes, conflicts and constraints in space being checked in 3-D and real-time before the 2-D drawings are produced for the Contractor’s activities.
The best candidate for this are housing developers who build high-volume, standard construction on a short delivery time mode basis. Therefore, a quick achievable success factor for BIM implementation should be to target this segment of users.
Applying BIM to a nuclear or rail project may be deemed necessary, but where are the track records for the validation and verification process in the Malaysian construction scene going to come from? The focus should be chronologically shifted from the architectural and consultancy companies to the housing development application area, by the power that be.




There are various BIM systems running in various architects, consultants and engineering companies.
This variety of systems with their various levels of application has been the main toxification against the successful application of BIM in Malaysia. Everyone claims to be BIM compliant and a BIM practitioner for one purpose:The Malaysian Government directive to be BIM-centric by 2020.
The benefit of being perceived to be so, is being awarded projects by clients who are BIM-biased. However, incompatibilities between the architect’s, engineer’s and contractor’s BIM systems can only result in such awards having complications and increased cost of implementation. Hence, not a single BIM “solution” can take on the Microsoft approach of Windows dominance. BIMdata mobility has to be the primary focus of future solutions. It is this that will be recommended as the detox to the widespread adoption of BIM. The data associated with layouts, look and feel from the architects should be a BIM template for the engineering of facilities within, that will be construction-wise sequenced by the contractors. For this, the data set has to be contextually universal.
Data mining of the construction industry and applying contextual data analytics to the BIM application areas should be the focus of BIM evangelists. BIM is the most data-centric application that engineers in the Malaysian construction industry have faced so far.
BIM cannot and should not be under the jurisdiction of a single “authority” entity as it is part of the engineering construction process in an ever-expanding construction industry.
Fortunately, the focused implementation will come from international expectations, effective approaches and efficient implementations that will make BIM a necessity in the face of stringent times, adverse competition scenarios and the use of highly in demand resources and knowledge.
Author's Biodata
S.
is a Distributed Control Systems (DCS), Supervisory Control and Data Acquisition Systems (SCADA), Substation Control System (SCS) and Electrical Engineer. He

















































Date : 17 – 18 June 2019 (Monday - Tuesday)
Time : 9.00 a.m. - 5.30 p.m.
Venue : Wisma IEM
Approved CPD : 14.0
Speaker : Ir. Lai Sze Ching
2-Day Course on “Contract Management Hiccups”








Half-Day Technical Series Talk by Mun Hean Malaysia on "Basic Fundamental and Design of Low Voltage Protection Relay Solution"
Date : 19 June 2019 (Wednesday)
Time : 8.30 a.m. to 1.00 p.m.
Venue : Wisma IEM
Approved CPD : Applying
Speaker : Mr. Chong Swee Long


Today, the manufacturing industry faces even bigger challenges. A slowdown in productivity growth, decline in competitiveness, globalisation and new technology have redefined the industry.
Because of this, Germany developed a new strategy to improve its competitiveness internationally. The world has embraced the term, Industry 4.0, which originated from a Germany high-tech strategy project on digital manufacturing.
The term was revived in 2011 at the Hannover Fair. In 2012, a set of recommendations for the implementation of Industry 4.0 was presented to the German government. On 8 April, 2013, at the Hannover Fair, the final Industry 4.0 report of the working group was presented and it created a huge impact on existing manufacturing industries [1]. Many countries such as China, Korea, UK, US and EU nations, announced new policies to support local manufacturing towards a high value manufacturing chain. For example, China announced its “Made in China 2025” and “Internet Plus” policies in 2015 to support its industries towards high-tech manufacturing [2]. Singapore launched Smart Industry Readiness Index as the tool to catalyse the transformation of industrial sectors toward 4th Industrial Revolution [3]. In Malaysia, the first initiative was started by the Ministry of International Trade & Industry (MITI) to develop a National Industry 4.0 Policy Framework since 2017.
In 2017, the Malaysian government initiated a nationallevel technical working group led by MITI to develop a National Industry 4.0 policy, comprising members from the Ministry of Communications & Multimedia, Ministry of Higher Education, Ministry of Human Resource, Ministry of Finance, Ministry of Science, Technology & Innovation and SME Corporation Malaysia. In addition, various organisations such as Federation of Malaysian Manufacturers (FMM), Intel Malaysia, Malaysia Investment Development Authority (MIDA), Malaysia Technology Development Corporation (MDEC), Universiti Teknologi Malaysia, etc. also contributed to the input for the Industry
4.0 draft. The Industry4 WRD - Malaysia National Industry 4.0 Policy (Figure 1) was launched on 31 October, 2018, by Prime Minister Tun Dr Mahathir Mohamad.

There are seven factors that drive Malaysia Industry4WRD [4]:
1. The change of global economic order.
2. The wide coverage and lower cost of technological products.
3. New knowledge and skills.
4. The systematic of global supply chain management.
5. Greater global competitiveness.
6. The increased of regulations.
7. Dynamic customer behaviour.
The 11 technological drivers for Malaysian industries towards Industry 4.0 are [4]:
1. Systems integration (SI).
2. Internet of things (IoT).
3. Additive manufacturing.















4. Autonomous robots.
5. Simulation.
6. Big data analytics.
7. Artificial intelligence (AI).
8. Augmented reality (AR).
9. Cloud computing.
10. Cybersecurity.
11. Advanced material.
These will impact social and geopolitical transformation, systematic change and new mental models. With the technology adoption, these will create smart production systems in factories and nurture talent in the new generation. The adoption of Industry 4.0 will in-crease productivity, efficiency and competitiveness.
The vision of Industry4WRD is to enable Malaysia to become a strategic partner for smart manufacturing and related services in the Asia Pacific region as well as become the primary destination for the high tech industry and a hub for advanced technology solutions providers [4]. Its goals are [4]:
1. To increase the level of productivity in the manufacturing sector.
2. To elevate the contribution of the manufacturing sector to the economy.
3. To strengthen the Malaysian innovation capacity and capability, reflected in global innovation rankings.
4. To increase the high-skilled worker in the manufacturing industry.
The 3 shift factors for industry towards Industry4WRD are people, process and technology. For the people factor, it’s to critically develop, upgrade and retain required talent and skills. The second shift factor is to focus on improving both manufacturing and business processes by creating a favourable environment and facilitating public-private partnerships. The third shift factor, technology, is to foster a seamless and accelerated adoption of Industry 4.0 technologies with the aim to improve our competitiveness in the global scenario.
The strategic enablers that determine the strategies, policies and action plans are:
1. Funding – funding and outcome-based incentives.
2. Infrastructure – enabling ecosystems & efficient digital infrastructure.
3. Regulations – regulatory framework & industry adoption.
4. Skill & Talent – up-skilling existing and producing future talents.
5. Technology – access to smart technologies.
There will be plenty of opportunities for SMEs under the Industry4WRD initiative. These are:
1. Funding – incentive packages and development funds.
2. Catalogue and collaboration platform for service providers.
3. Awareness programme.
4. A regulatory sandbox and guidelines.
5. Industry 4.0 Readiness Assessment tool.
6. Manufacturing industry data depository.
7. Industry 4.0 talent competency & technology mentoring programme.
8. Expert certification programme.
9. Training.
10. Public-private partnerships and collaborative programmes.
11. Smart manufacturing research.
12. An inventory of Industry 4.0 related standards.
Local industries need time to adopt Industry 4.0 technologies into their manufacturing process. SMEs in particular, still need to understand and to trust the new technologies as well as learn how the adoption of Industry
We are a supplier of high quality geosynthetic products used for soft soil stabilization, slope reinforcement, coastal erosion protection, river bank protection, landfills, drainage, road and railway construction.
Our Products:
NEXTILE NON-WOVENS
NEXGRID GEOGRIDS
We also provide design, specification, bill of quantities, cost estimate and drawings free-of-charge




NEXFORCE HIGH-STRENGTH WOVENS




Get in touch with us: Tel: 03-6142 6638 Fax: 03-6142 6693
sales@neusynthetics com
Sales Team:
For further information on our range of geosynthetics products, please contact:
Lee Hui Seng : 012 355 9151 : 012 329 3378 (Whatsapp only) Gordon Teh : 012 355 0872
Lee Hui Seng (012-3293378) Fazrol (012-3163341)
Tel : 603 6142 6638
Fax : 603 6142 6693
NEHEMIAH GEOSYNTHETICS SDN BHD 45-3 Jalan PJU 5/20, The Strand, Kota Damansara, 47810 Petaling Jaya, Selangor Darul Ehsan.
Email : leehuiseng@nehemiahwalls.com
Email : enquiry@nehemiahwalls.com www.nehemiah-grp.com
A Nehemiah Group of Companies www neusynthetics com
5/20, The Strand, Kota Damansara, 47810 Petaling Jaya, Selangor Darul Ehsan Malaysia Former y Neusynthetics Sdn Bhd
Email : gordonteh@nehemiahwalls.com


4.0 can improve their competitiveness and profitability. The challenges SMEs face are [4]:
1. Lack of awareness on the impact and need for Industry 4.0 technologies.
2. Low digital adoption among SMEs.
3. Shortage of required talent, skills and knowledge for Industry 4.0.
4. Change in customer behaviour.
5. Misperception and inadequate understanding of costs vs benefits and ability to conduct industry 4.0 business case analysis.
6. Lack of local success stories of applying Industry 4.0 technologies.
Malaysia is moving towards the development of an end-to-end Industry 4.0 ecosystem. With Industry4WRD, Malaysia aims to achieve four key goals: GDP contribution, national productivity, high-skilled employment and innovation capabilities. Local industries are in critical need to upskill and reskill the current and future workforce. SMEs contributed RM435.1 billion (37.1% of Malaysian GDP) in 2017 to the nation's economy [5].
The government will focus on SMEs to increase productivity. Next, funding needs to be in place as soon as possible for the industry to kickstart the adoption and to complement private sector investment. Innovation has to be encouraged and supported to create cost-effective Industry 4.0 related technologies for SMEs. Lastly, there must be good digital infrastructure, especially cost-effective high-speed internet, to support the National Industry 4.0 Policy initiative.
[1] Wikipedia, “Industry 4.0”, https://en.wikipedia.org/wiki/Industry_4.0.
[2] Hong Kong Trade Development Council, “Integration of Made in China 2025 and Internet Plus Strategies”, http://economists-pick-research.hktdc.com/business-news/article/ Regulatory-Alert-China/Integration-of-Made-in-China-2025-and-Internet-Plus-Strategies/bacn/ en/1/1X000000/1X0A54WS.htm.
[3] Singapore Economic Development Board, “The Singapore Smart Industry Readiness Index”, https://www.edb.gov.sg/en/news-and-resources/news/advanced-manufacturing-release.html.
[4] Ministry of International Trade & Industry, "Industry 4WRD: National Policy on Industry 4.0", October 2018.
[5] Syahirah Syed Jaafar, "SME contribution to Malaysia's economy rose to 37% in 2017", http:// www.theedgemarkets.com/article/sme-contribution-malaysias-economy-rose-37-2017.
Ir. Dr Tan Chee Fai has over 19 years experience in the mechanical and manufacturing industry. He is the Chief Technical Officer of Robolab Technology Sdn. Bhd. and Senior Lecturer at Malaysia Japan International Institute of Technology (MJIIT), Universiti Teknologi Malaysia.
















































Half-Day Course on “Introduction to Marine Engineering”
Date : 19 June 2019 (Wednesday)
Time : 8.30 a.m. - 1.00 p.m.
Approved
CPD : 3.5
Venue : Motor Yacht Puteri Samudra at Royal Selangor Yacht Club, Port Klang Selangor
Speaker : Ir. Roznan bin Abdul Rashid








1-Day Course on “Technical Report Writing”
Date : 20 June 2019 (Thursday)
Time : 9.00 a.m. - 5.30 p.m.
Venue : Wisma IEM
Approved
CPD : 6.5
Speaker : First Admiral Dato’ Ir. Hj. Ahmad Murad bin Hj. Omar (Rtd) and Ir. Dr. Ching Yern Chee


The magnificent Sultan Omar Ali Saifuddien Mosque sits in the very heart of Bandar Seri Begawan, the capital city of Brunei. Built in 1958 and named after the 28th Sultan of Brunei, it is one of the most impressive mosques in South-East Asia. Set in a lagoon, it is perfectly reflected in the water, with light shimmering in the background, surrounded by lush greenery and floral gardens, while its golden dome soars above the skyline. The mosque brings together the best materials in a tour de force of architectural beauty and spiritual ambience, reflecting upon a reflection, a spiritual journey.

reported by


The first Engineering, Science & Technology International Conference (ESTIC), co-organised by the Consulting Engineer Special Interest Group (CESIG) of IEM, MAHSA University’s Faculty of Engineering & Information Technology, is a platform for sharing innovative ideas, latest technological information, research findings and strategic solutions.
Present were the Guest of Honour, Y.B. Tuan Haji Mohd Anuar bin Mohd Tahir (Deputy Minister of Works), and other guests including Ir. Ong Ching Loon (Deputy President, IEM), Ir. Yam Teong Sian (President of Technological Association Malaysia), Ir. Ellias Saidin (Immediate Past President, Environmental Management and Research Association of Malaysia) and Ir. David Chuah (The Institution of Engineering & Technology or IET). More than 20 sponsors and supporting agencies took part in the exhibitions.
The inaugural ceremony was initiated with opening speeches by Tuan Haji Mohd Anuar and Ir. Ong Chin Loong. During the conference, MAHSA received a welding robot worth RM140,000 from its industry partner, MSM Metal Industries Sdn. Bhd. The robot will be used to enhance research and provide learning experiences for its Engineering students.
There were 9 speakers from various universities, professional bodies and relevant industries invited for the keynote sessions: Dr Subramaniam Karuppannan (MAHSA University), Mr. Fong Swee Hin (MSM Metal Industries Sdn. Bhd.), Prof. Dr Norani Muti Mohamed (Universiti Teknologi Petronas), Ir. Jimmy Wan Yoon Hin (IEM),Associate Professor Ir. Dr Sharifah Hafizah Syed Ariffin (Universiti Teknologi Malaysia),
Prof. Ir. Dr Denny K.S. Ng (IEM Chemical Engineering), Ir. Dr Tan Chee Fai (IEM Honorary Treasurer), Ir. David Chuah (IET Treasurer) and Ir. Ellias Saidin (IEM Vice President).
Six international companies from the industrial sector and three professional bodies participated as exhibitors. They were IEM, Technological Association Malaysia (TAM) and IET (Malaysia).
The Technical Review Committee selected 65 out of 100 papers from various countries, including Indonesia, Algeria, Nigeria, China and Malaysia for presentation at the conference.
The event concluded with the various award presentations at the closing ceremony by Ir. Yam Teong Sian, President of TAM. The Young Scientist Network –Academy of Science Malaysia Awards went to Nazriah Mahmud, Hilton Ahmad and Lim Sin Nie. The Engineering, Science & Technology International Conference Young Icon Award went to Ir. Dr Oh Chai Lian. The Best Paper Awards went to Yagasena Appannah, Siaw Wee Ong, Teck Leong Lau, Tuck Wai Yeong, Mohammed Parvez Anwar, Wael Elleithy, Sagevindren Mariappan and Preethi Shrivastava. The Best Presenter Awards went to Noorhidayah Sunarti, Raziff Hamsan, Saeed Isa Ahmed, Preeti Shrivastava and Yagasena Appannah.
The Organising Chairperson of ESTIC, Ir. Prof. Dr Leong Wai Yie, said the conference provided a platform for consultant engineers, scientists and academicians to network and collaborate. IEM has also played an important role to share experiences and skills with the delegates.








reported by

Ir. Dr Ng Kok Chiang
On 6 October, 2018, CESIG organised a factory visit for 25 engineers from IEM to KHIND-Mistral Industries Sdn. Bhd. in Jalan Perusahaan 2, Sekinchan, Selangor. The visit had a CPD/PDP of 2.5 hours. We started at 7.30 a.m. from Wisma IEM and on arrival at 9.38 a.m., we were welcomed by the staff of KHIND, led by Mr. Khoo and Mr. Sew.
KHIND was established in Sekinchan in 1961 by Mr. Cheng King Fa. The manufacturing plant has a total builtup area of approximately 200,000 sq. ft. on approximately 5.6 acres of land. We were told that it had a total workforce of 380 employees, with very little dependence on foreign labour. KHIND has even adopted to Integrated Computerised System (ERP) for the manufacturing process and is certified to ISO 9001: 2015.
At the introductory seminar, we were told that today, KHIND manufactures and distributes world-class electrical home appliances in Malaysia as well as exports to over 60 countries worldwide.
Among the products manufactured and assembled at the KHIND factory are:
• Electrical fans (table fan, stand fan, wall fan, ceiling fan, floor fan, auto fan, exhaust fan, ventilation fan, industrial fan).
• Lighting (rechargeable portable light, emergency light).
• Home appliances (mixer, desk blender, hand blender, personal blender, air fryer).
• Others (insect killer, money detector etc.)
During our visit to the factory floor, we were told that being internationally accepted as “a world brand from Malaysia”, KHIND was posed to play a bigger role in international

arena. We were shown the many aspects of manufacturing fans, including the making of various parts of the fans from scratch.
The testing facilities to ensure the quality of the products manufactured was also explained in detail. There were many questions from the floor during our visit and these were explained in detail by Mr. Khoo, a director of KHIND Industries.
After the visit, we felt proud to know in detail the inside operation of one of the most successful home-grown electrical home appliances manufacturers in Malaysia and abroad.
After the factory visit, we were treated to a hearty lunch at one of the local seafood restaurants. This allowed us to further mingle with and talk to the employees of KHIND who were mostly locals.
We then returned to KHIND for a question-and-answer session. This was when we also found out that KHIND realised that protection of the environment was closely related to its long-term sustainability goals. So the factory management had adopted various green business practices to ensure sustainable development in the future.
The visit ended at 3 p.m. when Ir. Yim presented a token of appreciation from IEM to Mr. Khoo. As we were the first group of IEM engineers to visit the KHIND factory, Mr. Khoo generously presented all of us with a limited edition KHIND Flower Fan as a souvenir. This was the most memorable visit that CESIG had ever organised and we were very grateful for the hospitality and generosity shown us.

NEGERI SEMBILAN BRANCH

Atalk on Sustainable Product Design was held at the seminar room of The Institution of Engineers Malaysia Negeri Sembilan (IEMNS) on 16 March, 2019.
IEMNS Chairman Ir. Dr Oh Seong Por delivered the talk to 31 participants comprising engineering consultants, industry operational engineers, lecturers and student members of the Technical Association of Malaysia (TAM).
The talk was co-sponsored by Mr. Lim Swee Ee, President of Kibing Group (M) Sdn. Bhd. and an ardent supporter of IEMNS activities. Four key contents were shared, namely the definition and necessity of sustainable product design, sustainable product life-cycle, combined effort of government-industryuniversity and case studies.
Sustainable Product Design is a design approach that fulfills needs and acquires reasonable profit to maintain business and prevents adverse impact on the planet through the following:
1. Conservation of energy and water as well as protecting air quality.
2. Optimisation of material usage with no over-consumption and no waste.
3. Right material selection that is recyclable and nonhazardous.
4. Protection of supply chain that is renewable and able to sustain resources.
Every product produced creates an impact on the environment although the product may bring convenience to humans. The impact may be big or small, immediate or delayed. Sometimes the impact can be only seen over a period of time of application, for example, the plastic bag.
When it was first introduced, consumers found plastic bags useful as these were convenient for carrying materials or goods. This is so even today. But recently it was established that plastic bags contributed to an enormous amount of waste which was harmful to the environment and living creatures; this triggered a ban on its use in many places.
A sequence of product development flow starts from identifying the problem to finding a solution (satisfying need), creating design, production and distribution to buyers with consideration of product disposal function. It covers the entire cycle, from
creation for use and beyond. In short, it is a flow sequence from cradle to grave (See Figure 1). Some common product disposal functions are:
• To recycle scrap product to reclaim complete or teardown parts which can be reprocessed for making same product or other applications.
• Quick natural or safe degradation that can be retuned to the eco system.
• To reduce or eliminate the usage of hazardous chemical.
• By-product or process residual which can be recycled or reclaimed.
This refers to the three key parties – government, industry and university – with each having specific roles and yet supports each other to boost the success of sustainable product design.
According to Ir. Dr Oh, the government sector, which is empowered with executive and legislative powers to dictate policy and to perform mitigation roles, has the biggest influence to spearhead the sustainable initiative.
For example, the Norwegian government is committed to completely abolish internal combustion cars and to replace them with electric cars by 2025. Incentives such as toll free, subsidy and zero tax, have encouraged many people to switch to electric cars, significantly cut down CO2 emission,


the main cause of global warming. Other countries like Finland, Britain, France, China and India are also taking a similar stand. The demand for electric cars has created a domino effect and encouraged electric car makers such as Tesla and battery makers to increase production.
No. Substance Permissible Level
1. Lead (Pb) <1000 ppm
2. Mercury (Hg) <100 ppm
3. Cadmium (Cd) <100 ppm
4. Hexavalent Chromium (Cr, VI) <1000 ppm
5. Polybrominated Biphenyls (PBB) <1000 ppm
6. Polybrominated Diphenyls Ethers (PBDE) <1000 ppm
7. Bis (2 - Ethylhexyl) phthalate (DEHP) <1000 ppm
8. Benzyl butyl phthalate (BBP) <1000 ppm
9. Dibutyl phathalate (DBP) <1000 ppm
10. Diisobutyl phthalate (DIBP) <1000 ppm
Another example is the introduction of Restriction of Hazardous Substance or RoHS directive by European Union (2002) to mitigate 10 hazardous chemicals (See Table 1) and prevent pollution to the environment. Any violation will lead to a ban on the goods in the market.
The industry sector has two main roles:
1. To enshrine sustainable product development and protection of environment into the corporate business philosophy.
2. To continuously innovate products or services to optimise usage of resources (material, energy and water) and to cut down waste generation or emission of process residuals.
One good example is the cathode ray tube industry. A lean product design approach has been consistently applied to eliminate non-value added features and production processes. The product has become slimmer, thinner and lighter, which successfully reduces energy and material needed to make the product. The environment degrading chemical trichloroethylene (TCE) has also been replaced with an eco-friendly material. Recycling of process waste residuals like phosphor and water has been implemented, reducing the amount of waste impact on the environment. All these initiatives not only minimises contamination to the environment but also improves product cost and competitiveness.
The university, a place to cultivate the mind and create new knowledge, can be an important platform to develop or assist industry in green technology. For this reason, some universities have established green technology courses, department or


research centre to engage in teaching as well as forming useful knowledge about eco-friendly applications. Exposing students – future engineers, technologist and industry leaders – is a good way to prepare them to be mindful and responsible about protecting the planet from pollution. Post graduates students and lecturers may be deployed to industry to participate in sustainable design tasks. Experiences gained will be further enhanced and documented as best practices which can be applied to other sustainable applications.
The close collaboration between government-industryuniversity, with each seriously pursuing respective initiatives to protect the environment, is an effective way to achieving sustainable product design (See Figure 2).
The speaker concluded the talk with a Malay pantun before awarding certificates to all participants.
Negara kita serba ada Ada teknologi ada inovasi
Sustainable product baik berganda Melindung dunia dan generasi


is a retired civil engineer who derives a great deal of joy and satisfaction from travelling to different parts of the globe, capturing fascinating insights of the places and people he encounters and sharing his experiences with others through his photographs and writing.

With a population of 1% that of our country occupying a land almost the size of our country, Iceland does not have any urban centre that can be truly classified as a city in the normally accepted sense. Even its capital, Reykjavik, has only a population of 124,000 people and is one of the smallest “capital cities” in the world. Iceland has much more nature than culture to offer tourists.
During our 38-day exploration of Iceland, my wife and I, together with my younger brother and his wife, travelled round the island in a rented car in a clockwise direction, starting from Reykjavik near the southwest corner. We followed the ring road but turned off every so often to visit almost every nook and corner of the island accessible to a 2WD passenger car. Some of the roads, especially those in the interior, are not paved and are open only to 4WD vehicles. We were able to visit many tiny hamlets spectacularly situated at different points on the many fjords that characterise the coastlines of west, north and east Iceland. And of course we came across tens of thousands of birds and other wildlife. We also saw more sheep than people.
The Westfjords is a peninsula somewhat resembling a hand sticking out from the northwest corner of the island. The dozens of fjords along the coast of this large peninsula provide not only beautiful settings for many villages and hamlets but are also home to a large variety of birds. In the 10 days we were in this area, we came across large flocks of eider ducks, arctic terns, kittiwakes, northern fulmars, guillemots, razorbills, some whooper swans, greylag geese, black-headed gulls, blackbacked gulls, harlequin ducks, oyster catchers, red-breasted mergansers, red-throated loons, black-tailed godwits, shags, a few rock ptarmigans, golden plovers, sandpipers, common snipes, whimbrels, arctic skuas, etc.
We had our first close encounter with the clownish but iconic puffins at the world-famous Látrabjark Bird Cliffs in the southwestern corner of Westfjords. We were extremely lucky to see a king eider among a group of ordinary eider ducks. We came across a small colony of harbour seals in one of the fjords too. It was also in this peninsula that we saw Dynjandi, the first of the many spectacular waterfalls in this country.
On the day before we left Westfjords for North Iceland, we were doubly lucky to come across a few harbour seals basking on rocks in a fjord, followed by two arctic foxes beside the road. A few days earlier we saw two orphaned arctic foxes in the Arctic Fox Centre near the small village of Suðavik. The arctic fox is the only native mammal in Iceland.
In North Iceland, we saw more harbour seals and some new species of birds, including a large colony of northern gannets, some red-necked phalarope, meadow pipit and Slavonian grebe. In Husavik, we went whale watching and saw several humpback whales and caught sight of a minke whale. I did not, however, forget that Iceland is one of the 3 countries that kill a large number of whales every year, and I find it extremely hard to reconcile this with the Icelanders’ efforts to promote whale watching as a major tourist attraction.
In East Iceland, we had our most satisfying and memorable close encounter with a large number of cute puffins at Hafnarhólmi, many of them back from the sea with a row of small fish in their beaks to feed the newly hatched chicks in their burrows.
Remembering Iceland as a “Land of Fire and Ice”, we climbed the craters of a few dead volcanoes and visited a cluster of pseudo-craters formed by steam explosions when hot lava flowed over frozen ground. We also got to view glacier tongues, glacier lakes and icebergs at very close range in South Iceland.
Iceland is truly a nature lover’s paradise.




Kepada Semua Ahli,
Tarikh: 17 Mei 2019
CALON-CALON YANG LAYAK MENDUDUKI TEMUDUGA PROFESIONAL TAHUN 2019
Berikut adalah senarai calon yang layak untuk menduduki Temuduga Profesional bagi tahun 2019.
Mengikut Undang-Undang Kecil IEM, Seksyen 3.8, nama-nama seperti tersenarai berikut diterbitkan sebagai calon-calon yang layak untuk menjadi Ahli Institusi, dengan syarat bahawa mereka lulus Temuduga Profesional tahun 2019.
Sekiranya terdapat Ahli Korporat yang mempunyai bantahan terhadap mana-mana calon yang didapati tidak sesuai untuk menduduki Temuduga Profesional, surat bantahan boleh dikemukakan kepada Setiausaha Kehormat, IEM. Surat bantahan hendaklah dikemukakan sebulan dari tarikh penerbitan dikeluarkan.
Ir. Mohd Khir bin Muhammad FIEM, PEng Setiausaha Kehormat, IEM (Sessi 2019/2020)
PERMOHONAN BARU
Nama Kelayakan
KEJURUTERAAN AWAM
ROSNANI BINTI ABDUL SAMAD BE HONS (MALAYA) (CIVIL, 1996)
KEJURUTERAAN ELEKTRIKAL
KHAIRUN SYAZMIN BINTI ISMAIL BE HONS (UPM) (ELECTRICAL & ELECTRONICS, 2003)
TENG CHENG REEN BE HONS (USM) (ELECTRONIC, 2010)
PERMOHONAN BARU / PERPINDAHAN
MENJADI AHLI KORPORAT Nama Kelayakan
KEJURUTERAAN AWAM
WAN NAZRI BIN WAN ARIA BE HONS (UiTM) (CIVIL, 2004) MSc (STUTTGART) (COMPUTATIONAL MECHANICS OF MATERIALS & STRUCTURES, 2009)
PERPINDAHAN AHLI
No. Ahli Nama Kelayakan
KEJURUTERAAN AWAM
52503 RAMESH RAMANATHAN BE HONS (UNITEN) (CIVIL, 2009) MSc (UPM) (STRUCTURAL ENGINEERING & CONSTRUCTIONS, 2012)
58859 TAN TEIK NING BE HONS (USM) (CIVIL, 2012) MSC (USM) (STRUCTURAL, 2013)
KEJURUTERAAN ELEKTRIKAL
61176 CHAN WEI JIAN BE (ADELAIDE) (ELECTRICAL & ELECTRONIC, 2010)
88815 MUHAMMAD ASYRAF BIN MOHD SAH BE HONS (MALAYA) (ELECTRICAL, 2015)
43580 NIK MOHD SAIFUL BIN NIK ABDUL HALIM BE HONS (UPM) (ELECTRICAL & ELECTRONICS, 2009)
84942 WEE CHAI SIANG BE HONS (MMU) (ELECTRONICS MAJORING IN ROBOTICS & AUTOMATION, 2012)
KEJURUTERAAN ELEKTRONIK
62050 SANKARA A/L SIVALINGAM BE HONS (KLiUC) (ELECTRONICS, 2012)
KEJURUTERAAN GEOTEKNIKAL
34573 MAN SHEE LEONG BE HONS (MALAYA) (CIVIL, 2004) 33746 NUR IRFAH BINTI MOHD PAUZI BE HONS (UNITEN) (CIVIL, 2004) MSc (UPM) (GEOTECHNICAL & GEOLOGICAL, 2007) PhD (UPM) (GEOTECHNICAL & GEOLOGICAL, 2013)
KEJURUTERAAN MEKANIKAL
18848 CHOO VUI JIN BE HONS (GLASGOW) (MECHANICAL, 1995)
101047 MOHD FIRDAUS BIN SAID BE HONS (UTM) (MECHANICAL - MARINE TECHNOLOGY, 2002)
101990 RAMESH A/L SURIANARAYANAN BE HONS (UTM) (MECHANICAL, 2004)
KEJURUTERAAN PEMBUATAN
38036 WAN SHARUZI BIN WAN HARUN BE HONS (UNIMAS) (MECHANICAL & MANUFACTURING SYSTEMS, 2004) ME (UTM) (MECHANICAL - ADVANCED MANUFACTURING TECHNOLOGY, 2008) PhD (KYUSHU) (MECHANICAL, 2013)
PERMOHONAN BARU / PERPINDAHAN MENJADI AHLI KORPORAT Nama Kelayakan
KEJURUTERAAN AWAM
78464 CHAI SHIONG YEN BE HONS (MALAYA) (CIVIL, 2011)
57091 MOHD HAFIZ ARIF BIN ZAKARIA BE HONS (UiTM) (CIVIL, 2011)
18153 MOHD SARUDIN BIN MOHD AZIZ BE HONS (MALAYA) (CIVIL, 1994)
KEJURUTERAAN ELEKTRIKAL
49283 OOI KEAN LEONG BE HONS (UPM) (ELECTRICAL & ELECTRONICS, 2007)

















































Date : 25 June 2019 (Tuesday)
Venue : Wisma IEM
Approved CPD : Applying
1-Day Course on “Sustainable Development Goals (SDG6) - Clean Water and Sanitation What Can We Do! “
Time : 9.00 a.m. - 5.30 p.m.
Speaker : Ir. Gary Lim, Ms. Rachel Koh & TPr. Lee Lih Shyan









2-Day Course on “Optimising Compressed Air System Energy Efficiency”
Date : 26-27 June 2019 (Wednesday - Thursday)
Time : 9.00 a.m. - 5.30 p.m.
Venue : Wisma IEM
Approved CPD : Applying
Speaker : Ir. Luk Chau Beng and Mr. Kelvin Low

2-Day Course on “Basic Welding Knowledge in Engineering & Construction”
Date : 3 - 4 July 2019 (Wednesday - Thursday)
Time : 9.00 a.m. - 5.30 p.m.
Venue : Wisma IEM
Approved CPD : 14
Speaker : Ir. Nik Mohd Hasmizie Nik Mohd Kamil
The Sub-Committee of Engineering Hall of Fame under the auspices of the Standing Committee on Professional Practice is proud to invite nominations for the IEM Engineering Hall of Fame Award 2020.
It is timely and expedient to induct and to record the accomplishments of engineers in the country who have or had demonstrated particularly outstanding professional achievements and provided excellent services to the Institution, the engineering industry and the Nation.
The IEM Engineering Hall of Fame is established with the aim to confer recognition and to celebrate the accomplishments of members of the IEM:
• Who have demonstrated outstanding professional achievements.
• Who have made significant contributions to the engineering profession, the Institution of Engineers, Malaysia (IEM) and the Nation.
• Who have rendered valuable service to the Community.
The Engineering Hall of Fame will serve as the focal point or showcase of outstanding Malaysian engineers, past and present, who had or have made great contributions to the engineering profession and to the quality of life in Malaysia. Engineers honoured in the Engineering Hall of Fame will also serve as a beacon and as role models for young engineers as well as create greater interest in engineering
in general and awareness of the contributions made by outstanding engineers in the country.
Nominations for the Award are open to Malaysian citizens who are or have been Corporate Members of the IEM.
The closing date for receipt of nominations for IEM Engineering Hall of Fame Award is 30 September 2019.
Please submit nominations to:
Honorary Secretary
The Institution of Engineers, Malaysia Bangunan Ingenieur, Lots 60&62 Jalan 52/4, 46720 Petaling Jaya, Selangor.
The nomination form can be downloaded from the IEM website at www.myiem.org.my
For further details, kindly contact IEM Secretariat at 03-7968 4001/2
To encourage an interest in engineering and to recognise important services or contributions to engineering in Malaysia, the IEM Award for Contribution to the Engineering Profession in Malaysia is to be presented to the person(s), who has:
• Contributed to the advancement of engineering in Malaysia, and/or
• Designed and constructed an original engineering device or system of merit and applicability to industry.
This Award is open to all Malaysian citizens and permanent residents.
NOMINATIONS
• Nominations will be invited annually. The
closing date for receipt of nominations for each year is 30 September.
• Nominations shall be made through a member of the Institution. Each member is restricted to one nomination per year.
• Each nomination shall be accompanied by a brief write up of the services rendered or contributions made or system designed and/or constructed together with relevant photographs and other documents.
AWARD
• The Award is to be made by the Council upon recommendation by the Awards Committee.
• The Award shall comprise a metal plaque, a scroll and a sum of RM1,000.
The closing date for nominations is 30 September 2019.
Please submit nominations to:
Honorary Secretary
The Institution of Engineers, Malaysia Bangunan Ingenieur, Lots 60&62 Jalan 52/4, 46720 Petaling Jaya, Selangor.
The nomination form can be downloaded from the IEM website at www.myiem.org.my
For further details, kindly contact IEM Secretariat at 03-7968 4001/2
The IEM Outstanding Engineering Achievement Award is created to confer recognition to an organisation or body for outstanding engineering achievements within Malaysia. The award will be given to an organisation or body responsible for an outstanding engineering project in the country.
The basis for the award shall be an engineering achievement that demonstrates outstanding engineering skills which has made a significant contribution to the profession and to the quality of life in Malaysia. In making the selection, the following criteria will be given special consideration:
1. Contribution to the well-being of people and communities,
2. Resourcefulness in planning,
3. Creativity in the solution of design problems,
4. Pioneering use of materials and methods,
5. Innovations in planning, design and construction,
6. Unusual aspects and aesthetic values.
Engineering achievements which include, interalia, the following can be submitted for consideration:
• Bridges, Tunnels, Waterways Structures, Roads
• Telecommunications of national/ international character, Power Transmission and Transportation
• Dams and Power Stations
• Ports and Harbours
• Building and Structures
• Airports
• Water Supply, Waste Disposal Projects
• Military projects such as bases, launching units, harbour facilities
• Drainage, Irrigation and Flood Control Projects
• Local design and manufacture of high technology products
• Energy, Heat, Mass Transfer
• Outstanding work in engineering research and development
• Chemical processing of indigenous raw resources such as rubber, palm oil and various other local plants
• Innovative use of local engineering materials
• Outstanding contribution in engineering education
• Original discovery of useful engineering theory
Nominations are invited from all members of the Institution. Each nomination submitted should contain a brief summary/write-up of the project in approximately 1,000 to 2,000 words together with full relevant reports on the project and three copies of supporting documentation including photographs. A project or component part thereof which has received an earlier award, from IEM does not qualify for nomination.
• The award in the form of a metal plaque, naming the achievement shall be given to the organisation or body responsible for the project for permanent display.
• The award shall be presented with due ceremony at an appropriate function of the IEM.
The closing date for nominations is 30 September 2019.
Please submit nominations to:
Honorary Secretary
The Institution of Engineers, Malaysia Bangunan Ingenieur, Lots 60&62 Jalan 52/4, 46720 Petaling Jaya, Selangor.
The nomination form can be downloaded from the IEM website at www.myiem.org.my
For further details, kindly contact IEM Secretariat at 03-7968 4001/2
The objective of the Award is to encourage interest in engineering and to recognise potential among young engineers in Malaysia. The Award will be presented to the person who has shown outstanding ability and leadership qualities, either i. in the design and/or construction of an engineering device or system of merit; or ii. in the research and development or teaching of engineering.
In any one year, the Award may be made in either one or both of the categories mentioned above. If the Award is to be made in only one of the two category may be made in the year. The Award is open to candidate who are:
The primary objective of the Award is to recognise the contributions by women engineers. This Award may also incidentally encourage interest in engineering among women and encourage them to strive towards greater excellence. The Award will be presented to the woman engineer who has shown outstanding ability and leadership qualities, or has been a pioneer in any more of the following areas:
• In the design and/or construction of an engineering device or system, structural system, planned development, environmental improvements or,
• In the research and development of engineering device, systems, processes and/or materials, publication of paper or,
• In the teaching of engineering or,
• In the management of engineering projects,
• Entrepreneurship in the commercial sector.
In making the selection, the following criteria
SENARAI PENDERMA KEPADA
WISMA DANA BANGUNAN IEM
Institusi mengucapkan terima kasih kepada semua yang telah memberikan sumbangan kepada tabung Bangunan Wisma IEM. Ahli-ahli IEM dan pembaca yang ingin memberikan sumbangan boleh berbuat demikian dengan memuat turun borang di laman web IEM http://www.iem. org.my atau menghubungi secretariat di +603-7968 4001/5518 untuk maklumat lanjut. Senarai penyumbang untuk bulan April 2019 adalah seperti jadual di bawah:
i. Registered member with the Board of Engineers, Malaysia and under 35 years of age
ii. Malaysian citizens or permanent residents of Malaysia
iii. Graduate or Corporate Members of IEM.
The Proposer may or may not be a member of IEM. However, each nomination shall be supported by a brief recommendation from two Referees who are Corporate members of IEM. If the Proposer himself is a Corporate member of IEM (or higher), then he may also act as one of the two required Referees.
The Award will comprise a cash prize of
will be given special consideration:
• Contribution to the well-being of people and communities
• Resourcefulness in planning and in the solution of design problems
• Pioneering in use of materials and methods
• Innovations in planning, design and construction
• Unusual aspects and aesthetic values
The Award is opened to candidates who are:
• Registered members of the Board of Engineers, Malaysia,
• Malaysian citizens or permanent residents of Malaysia,
• Graduate or Corporate Members of The Institution of Engineers, Malaysia.
The Proposer may or not be a member of IEM or BEM, or an engineer. However, each nomination shall be supported by a brief recommendation from two Referees who are Graduate or Corporate member of IEM. If
RM500.00, a scroll and plaque, to be presented with due ceremony to each recipient of the Award.
The closing date for nominations is 30 September 2019.
Please submit nominations to:
Honorary Secretary
The Institution of Engineers, Malaysia Bangunan Ingenieur, Lots 60&62 Jalan 52/4, 46720 Petaling Jaya, Selangor. The nomination form can be downloaded from the IEM website at www.myiem.org.my
For further details, kindly contact IEM Secretariat at 03-7968 4001/2
the Proposer is herself either a Corporate or Graduate member of IEM (or higher), then she may also act as one of the two required Referees.
The Award shall comprise a cash prize of RM800.00, a scroll and plaque, to be presented with due ceremony to each recipient of the Award.
The closing date for nominations is 30 September 2019.
Please submit nominations to:
Honorary Secretary
The Institution of Engineers, Malaysia Bangunan Ingenieur, Lots 60&62 Jalan 52/4, 46720 Petaling Jaya, Selangor. The nomination form can be downloaded from the IEM website at www.myiem.org.my
For further details, kindly contact IEM Secretariat at 03-7968 4001/2
























































1-Day Course on “Safety Integrity Levels (SIL) Training for Workshop Participants”
Date : 4 July 2019 (Thursday)
Time : 9.00 a.m. - 5.30 p.m.
Venue : Universiti Putra Malaysia, UPM Serdang
Approved CPD : 6.5
Speaker : Ir. Razmahwata bin Mohd Razalli
Persidangan Majlis IEM yang ke-415 pada 14 Januari 2019 telah meluluskan sebanyak 2134 ahli untuk permohonan baru dan permindahan ahli. Berikut adalah senarai ahli mengikut disiplin kejuruteraan:
Senarai nama ahli dan kelayakan adalah seperti di bawah. Institusi mengucapkan tahniah kepada ahli yang telah berjaya.
Ir. Mohd Khir bin Muhammad FIEM, PEng
Setiausaha Kehormat, Institusi Jurutera Malaysia, Sesi 2019/2020
PEMINDAHAN AHLI KEPADA AHLI FELLOW No. Ahli Nama Kelayakan
AWAM
24416 LIM PHAIK LENG BE (NEW SOUTH WALES) (CIVIL, 1986) MSc (NEW SOUTH WALES) (CIVIL, 1986) PhD (NEW SOUTH WALES) (1994)
08998 CHUAH LAM SIANG BE (NUS) (CIVIL, 1998)
13939 ARUL RAJ S/O SELVARAJ BE HONS (HANYANG) (CIVIL, 1990) MSc (YAMANASHI) (CIVIL & ENVIRONMENTAL, 1997)
23894 CHEN HARN SHEAN BE HONS (MALAYA) (CIIVL, 1998) ME (NUS) (2002)
26373 TEO FANG YENN BE HONS (UKM) (CIVIL & ENVIRONMENTAL, 2001)MSc (WATER) (2004) PhD (CARDIFF) (CIVIL) (2010)
13221 TAN KUANG LEONG BE HONS (UTM) (CIVIL, 1993) ME (NUS) (1996) PhD (NUS) (2003)
38707 LEE YUN FOOK BE HONS (UTM) (CIVIL, 2003) ME (UTM) (ENVIRONMENTAL MGMT, 2005) ENG. DOC (UTM) (PROCESS PLANT MGMT, 2016)
07933 SUNDRARAJ S/O KRISHNASAMY BSc HONS (LONDON) (CIVIL, 1986)
KEJURUTERAAN KOMPUTER
57551 CHUAH JOON HUANG BE HONS (UTM) (COMPUTER, 1999) ME (NUS) (2002) MPhil (CAMBRIDGE) (2008), PhD (CAMBRIDGE) (2013)
KEJURUTERAAN ELEKTRIKAL
20215 YAU CHAU FONG BE HONS (MALAYA) (ELECTRICAL, 2001)
KEJURUTERAAN KIMIA
27985 LEE TIN SIN BE HONS (UTM) (CHEMICALPOLYMER, 2006) PhD (UTM) (POLYMER, 2011)
KEJURUTERAAN MEKANIKAL
16292 MOHD HAZANI BIN SHAFIE BE HONS (UTM) (MECHANICAL, 1994)
28476 OH SEONG POR BSc (HANYANG) (MECHANICAL, 1991) ME (UKM) (MANUFACTURING, 2000) PhD (UTM) (ENGINEERING, 2011)
KEJURUTERAAN PERTANIAN
16021 S. KUMAR A/L S. SUBRAMANIAM BE HONS (UPM) (AGRICULTURAL, 1994)
PEMINDAHAN AHLI KEPADA AHLI SENIOR No. Ahli Nama Kelayakan
KEJURUTERAAN AWAM
02014 MAU KWONG CHING @ MOO KWANG CHING BE HONS (MALAYA) (CIVIL, 1976)
Note: Continuation of the Transfer Graduate, Graduate, Incorporated, Affiliate and Associate would be published in July 2019. For the list of approved “ADMISSION TO THE GRADE OF STUDENT”, please refer to IEM web portal at http://www.myiem.org.my.