




The task of empowering women to stay and thrive in cybersecurity is starting to feel akin to that of a hamster caught in a hamster wheel: tirelessly running but making no tangible progress. The task of building a diverse workforce and elevating individuals to serve as beacons of representation is demanding enough, but now a new obstacle looms on the horizon. A deeply concerning trend has emerged in our field: women departing from cybersecurity positions at an alarming pace. This development not only magnifies the pre-existing gender gap in the industry but also stifles its capacity for advancement and innovation.
The cybersecurity landscape is facing unprecedented challenges; from sophisticated cyber attacks to the rapid evolution of technology. The lack of gender diversity poses a significant impediment to effectively addressing and overcoming these challenges. While women have made notable strides in various sectors, the cybersecurity industry remains male-dominated with women constituting only a small fraction of the workforce.
So why are women leaving our cybersecurity workforces? A mixture of systemic bias, unconscious stereotyping and a lack of inclusive work environments all seem to contribute to a sense of isolation that can drive women away from the field. This attrition often occurs as women transition from education into professional roles. The lack of female role models and mentors, coupled with the scarcity of supportive networks, can make it difficult for women and young individuals to envision a long and successful career in cybersecurity.
To reverse this disheartening trend we need to shift our approach to address the root causes and provide solutions to empower women and young individuals in cybersecurity.
1. Fostering inclusive work environments: creating an inclusive and diverse workplace is not only a moral imperative but also a strategic necessity. Organisations must work diligently to eliminate bias and create an atmosphere where every employee feels valued and heard. Initiatives like mentoring programs, affinity groups and unconscious bias training can contribute to a more welcoming environment that encourages women to stay and thrive.
2. Nurturing talent early: empowering women and young individuals in cybersecurity starts with early education and exposure. Schools and colleges need to actively encourage young people to explore STEM fields and raise awareness and consideration of careers in cybersecurity. Engaging young minds through workshops, competitions and educational campaigns can spark interest and confidence in pursuing a career in this dynamic and impactful industry.
3. Providing role models and mentors: visibility matters. Women and young individuals need access to relatable role models and mentors who can guide them through their professional journeys. Organisations can establish mentorship programs that match experienced professionals with newcomers, creating a support network that fosters growth, skill development and career advancement.
4. Encouraging lifelong learning: the cybersecurity landscape is ever evolving. Encouraging continuous learning and professional development is crucial to keeping women and young individuals engaged and competitive in the industry. Employers can provide opportunities for employees to upskill, attend conferences and obtain certifications, helping them stay at the forefront of technological advancements.

5. Celebrating success stories: highlighting the achievements of women and young individuals in cybersecurity can inspire others to follow suit. Sharing success stories through this magazine and our Australian and New Zealand Women in Security awards platforms showcases the remarkable contributions women and young individuals make to the field, breaking down stereotypes and encouraging more to join and remain in cybersecurity.
6. Advocating for equal opportunities: organisations and industry leaders must advocate for equal opportunities and representation. Commitment from the top level of management is essential to creating a culture that values diversity and promotes women to leadership positions.
7. Collaborative efforts: government bodies, educational institutions, industry associations and the private sector need to collaborate in tackling this issue. Partnerships can lead to the development of comprehensive programs, policies and resources that support women and young individuals in cybersecurity at every stage of their careers.
The benefits of retaining and empowering women and young individuals in cybersecurity are numerous. Diverse perspectives lead to more innovative solutions, improved decision-making and a stronger ability to tackle complex challenges. Moreover, a more balanced workforce can help address the severe shortage of cybersecurity professionals the industry currently faces.
Reversing the trend of women leaving cybersecurity is not just about gender equality; it's about harnessing the full potential of our industry. By creating inclusive environments, nurturing talent, providing mentorship and advocating for equal opportunities we can inspire women and young individuals to overcome obstacles, stay in the field and become the driving force behind a safer digital future.
PUBLISHER, and CEO of Source2Create
www.linkedin.com/in/abigail-swabey-95145312
aby@source2create.com.au


The path ahead requires a collective commitment to change, a shared vision of inclusivity and a resolute determination to empower women to not only enter but also thrive in cybersecurity. The time to act is now, for the betterment of our industry and the security of our digital world.
Abigail Swabey


















































No job is too big or too small.
We look after your marketing & content needs so you can get on with what you do best. GET CONNECTED AND TAKE CONTROL OF YOUR BUSINESS SUCCESS TODAY!





the book itself. She is a 9 year old avid internet user, and I do worry about what she gets up to and the choices she makes. We limit her access and have cyber security overlays on her devices - but we are not too clued up on cyber security so it was always a worry. This book has been great to get conversation flowing that I didnt really know how to start up, and it has definitely taught her some worthwhile lessons on things to look out for and "shadowy corners" of the internet to be cautious of! I recommend this book.

For all the effort put into attracting women into IT in general, and cybersecurity in particular, there is often far too little effort put into keeping them there or addressing the reasons that make many want to leave.
The recent Voice of Women at Work 2023 report from WomenRising found a range of problems drove 55 percent of young women—those aged 18 to 24 years of age—who had only recently entered the workforce to be already considering changing careers.
That number increased to 58 percent of 25 to 34 year olds as frustration with stalling careers, lack of opportunities and lack of training drove many to reassess their career plans, often after returning to work from having children.
Those making it to what should be the peak years of their careers—45 to 54 years of age—were still considering drastic change, with 49 percent thinking about changing careers and 36 percent thinking about leaving the workforce altogether.
One respondent said her stress was due to “increased workload, bullying as a result of lack of project planning, and people not listening to my expertise only to find out I was right all along.”
These and other issues contributed to a constant level of on-the-job stress that left 46 percent of respondents admitting they felt overwhelmed, not coping, hanging by a thread, or completely burnt out, and dealing with the repercussions of a yawning gap between executive rhetoric about diversity, equity and inclusion (DEI) initiatives and everyday workplace dynamics.

Workplace bullying is still wearing women down. But many are learning to tap their experiences to help others.
The right workplace, and the right support in that workplace, can make all the difference, particularly for younger women who are starting out in the industry and may not have the experience and emotional maturity to navigate workplace bullying situations.
“I had a lot of doubts early in my career, not just about cyber, but whether I wanted to work in technology,” admitted Vanessa Wong, head of information security with consulting firm RSM Australia during a recent fireside chat at AusCERT2023
Her achievements show she made the right decision. However, she admitted encountering her own challenges with workplace culture, but said she drew on those experiences to become a more active mentor and champion to help others navigate organisational complexities.
“There are a lot more people advocating for themselves, but also champions advocating for others as well,” she explained. “I’ve tried to remember my own experiences starting out, and working in general: just knowing how a workplace works, what’s right, what’s wrong and what’s borderline. That has
certainly gotten a lot easier in that people are much more supportive by calling out bad behaviour.”

However, given such behaviour cannot be excluded entirely from the workplace, critical to balancing this effect is knowing “who you can trust to go to and ask for help, and what resources are available to support you,” she said.
Naomi Buckwalter, director of product security with San Francisco-based Contrast Security, had a similar experience after starting her career with an optimistic outlook.
“In the beginning of my career, it was difficult for me because I didn’t understand why I would be treated differently,” she said during a recent webinar

“I just always assumed that if you’re good at what you do, it doesn’t even matter what your gender is, or what you look like.”
Those assumptions were soon dispelled after Buckwalter realised she was not getting the same assignments, promotions or opportunities as her co‑workers.
“It clicked that maybe it was a little different for me,” she said. “I realised there is bias everywhere, and that I had to stand up for myself, start advocating for myself and for others and say, ‘it’s not cool for you to be treating me this way, or putting down other women, or not even giving us the benefit of the doubt’.”
Kayla Williams, chief information security officer of security analytics company Devo Technology, told the same webinar she had also dealt with bullying

throughout her career and has used her early experiences to “try to help other women that are put in those situations.”
These include her own daughters. “I’m trying to break that cycle by teaching them empathy,” Williams explained. “By teaching them how to arm themselves to defuse situations by using mechanisms I’ve learnt only from being in the workplace.
“As good citizens, it’s up to all of us to hold ourselves, our peers and our children accountable. Because when they get into the workplace, they think they’ll be fired if they speak up.”
Based on the Voice of Women at Work 2023 report’s figures, many women face similar issues and still lack the belief that recourse is available when they are faced with bullying and confrontational behaviour.
Thirty-one percent of respondents, for example, cited conflict with peers or work leaders as a key contributor to their workplace stress levels, while 20 percent put the blame squarely on their manager.
Many respondents called out failures of company leaders. They were described as ‘arrogant’ and ‘aggressive’ by 26 percent and 21 percent of respondents, respectively.
“Many high-powered male leaders show domineering behaviours that do not align with our company’s values of customer driven and inclusiveness,” said one software and IT services worker.
“On the other hand, many mid-level leaders are empathetic and supportive. However, these leaders don’t have a lot of influence, nor do they intervene when bullying surfaces.”
Many women struggle not only with overt bullying but with the more subtle microaggressions that may seem like part of everyday dialogue at first, but ultimately add up to give them the perception women simply are not valued as highly as men.
For example, 74 percent of women report being talked over or interrupted in a meeting while 57 percent said they had been undermined by a male leader; a considerably higher percentage than the 37 percent of women who said they had been undermined by a female leader.
Microaggressions and outright bullying often fester within organisations. According to Janelle St Omer—vice president of growth and partnerships with global corporate social responsibility consultancy Realized Worth, and a long time diversity advocate—they are amplified by managers whose homogeneity often means they fail to see the confrontational and minimising behaviours on display in front of them.
“We often find that, when there’s not full buy in at the top in terms of the leadership, then there are challenges with how your middle-level managers
“There are a lot more people advocating for themselves, but also champions advocating for others as well. I’ve tried to remember my own experiences starting out, and working in general: just knowing how a workplace works, what’s right, what’s wrong and what’s borderline. That has
are showing up with their employees during microaggressions in the workplace,” she said.

Junior employees feel the impact of chronic microaggressions even more profoundly, according to St Omer. “A junior employee typically wants to excel and ascend through the ranks of your corporation. But if they feel all their efforts will be in vain because who is promoted, or who gets to the top, doesn’t include any individuals that look like them, they start to feel demotivated and there is a disincentive for them to continue to work hard.”
The end result of unaddressed workplace bullying is highly predictable, and one every manager should be working hard to avoid, according to St Omer.
“You’ll end up seeing those individuals leaving your organisation and going to work for organisations where they do feel like they have equal opportunity to ascend to whatever they want to do within their career, and to be the best and highest versions of themselves.”
certainly gotten a lot easier in that people are much more supportive by calling out bad behaviour."
– Vanessa Wong
Cybercrime is big business, thanks to technical advancement and interconnectivity creating more opportunities. This regular column will explore various aspects of cybercrime in an easy-to-understand manner to help everyone become more cyber safe.
Mobile phone number portability is a feature of all mobile services in Australia. It enables a customer to have their number transferred to a new SIM when they wish to change mobile service providers or if they lose their phone. Unfortunately this feature can be exploited by criminals to defraud customers.
Using identity details about a person previously phished or leaked in a data breach a criminal can contact a mobile service provider pretending to be that person and get the target’s mobile number transferred to their own SIM card, and hence their own phone. The first indicator that this has happened is usually when the victim’s phone loses connection to the network.
Once they have control of the victim’s mobile number the criminal is able to receive multifactor authentication text messages and, in combination with other personal details they have obtained about their target, gain access to the victim’s bank and other accounts and initiate funds transfers.
There are several things you can do to protect yourself from SIM swapping fraud.
• Speak with your mobile service provider, because many now offer specific measures designed to prevent illegal number porting.
• Limit the amount of sensitive or personal information you post about yourself online.

• Be very suspicious of emails, calls or texts asking you for personal information.
• Protect all your accounts with strong unique passwords and multifactor authentication where available.
• If your mobile phone stops working contact your service provider immediately to make sure your number has not been illegally transferred.
More information can be found at https://www.simprotect.org.au/
www.linkedin.com/in/amandajane1
www.demystifycyber.com.au

Uloaku Okechukwu-Philip is rather unusual: she holds degrees in both law and cyber security and is active in both domains. She works at Sycom Integrated Solutions, an IT services company, in the UK.

“I hold a unique and diverse role as a lawyer, data protection officer and cybersecurity expert at Sycom,” she says. “My position entails ensuring the company complies with data protection laws, and implementing robust cybersecurity measures to safeguard their systems and clients’ data.
“As a cybersecurity expert, I am responsible for securing Sycom Integrated Solution’s digital infrastructure, protecting against cyber threats and conducting risk assessments. As a data protection officer my role entails ensuring the organisation complies with data protection regulations, and implementing policies and procedures to safeguard sensitive information.
“A typical day involves conducting data protection audits, reviewing cybersecurity measures, drafting legal documents related to privacy policies and collaborating with IT teams to implement security measures. It is never monotonous. I start my day by reviewing security alerts and analysing potential
threats. Meetings with the team involve devising strategies to strengthen the company’s cybersecurity posture. As a data protection officer, I ensure the organisation remains compliant with relevant laws and regulations. It’s a dynamic and multifaceted role that keeps me on my toes.
“What I enjoy most about my position is the opportunity to combine my legal expertise with my knowledge of cybersecurity. This unique combination allows me to address complex legal and privacy issues while staying up to date with the latest developments in cybersecurity.
“One aspect I find particularly fulfilling in my current role is the constant challenge it presents. Each day brings new and intricate cybersecurity issues that require creative problem-solving and innovative solutions. I take great satisfaction knowing my efforts are instrumental in safeguarding the digital world.”
Okechukwu Philip’s first degree was in law, from Babcock University in her native Nigeria, where, she says, a passion for cybersecurity ignited during her studies began to take root.
“Babcock University incorporated a special program, the Diploma in Security Studies, alongside my degree in law. This program became compulsory during the summer holidays, requiring law students to stay and take the courses. During this time my interest in the field of security grew significantly, surpassing my interest in law. I decided to explore this area further and understand how I could relate law to security, until I realised they were actually two sides of the same coin.
“It was while studying for a Diploma in Security studies at Babcock University that I became inquisitive and curious to know what the next big thing in security would be. I realised where the world was heading, which motivated me to apply for a masters in security and intelligence instead of the traditional pathway for most lawyers who apply for an LLM or Master of Laws after their degree in law.”
Driven by “a deep curiosity for the world of security, intelligence, and diplomacy,” Okechukwu Philip went on to gain a master’s degree in Security, Intelligence and Diplomacy from the University of Buckingham in the UK. It was there, she says, that she experienced “the pivotal moment that solidified my desire to pursue a career in cybersecurity, when I presented a paper on Bletchley Park which holds immense significance in the history of cryptography, codebreaking, and the development of modern computing.”
Her decision to transition from law to data protection then to cybersecurity was driven by “a passion to make a tangible impact in the digital world and protect individuals and businesses from cyber threats,” she says.
“I realised the critical importance of securing sensitive data and protecting individuals and organisations from cyber threats. After graduation I made a bold decision to veer from the traditional path of law and plunge headfirst into the realm of cybersecurity.
“I sought out cybersecurity training and invested years in acquiring various certifications, honing my
skills and expertise in this rapidly evolving field. My dedication and determination earned me the title of a cybersecurity expert.
“My ability to analyse data flows, data protection issues and develop appropriate procedures or policies has been key in my role. My background as a lawyer has been a useful skill in making sure that my organisation is up to date with the evolving data protection legal landscape.
“The dynamic nature of cybersecurity demands continuous learning and adaptability in all aspects. With great challenges come significant obstacles, and I find myself in a continuous battle against cyber threats that constantly evolve and adapt. Staying ahead of the curve requires constant learning and the implementation of proactive strategies, making my role both exciting and demanding.”
Okechukwu-Philip says she has never regretted her decision to combine law and security studies. “Throughout my journey I faced both highs and lows, but I never once regretted my decision to add to my career paths by combining law and security. To me, law and security are two sides of the same coin, which is why I used the word ‘add’ instead of ‘turn’. There were moments of self-doubt, especially when delving into a relatively unfamiliar territory, but my determination and unwavering belief in the significance of my work kept me going.”
“The journey in cybersecurity is continuous, and no one should expect to reach a point where they consider themselves ‘done’. The field is ever evolving, and there is always something new to learn and explore. So, the feeling of truly working in security is an ongoing journey of learning, contributing, and making a positive impact.”
Okechukwu-Philip’s career might have been very different. While in high school she had other passions: movies and modelling, and achieved considerable success. In high school in Nigeria she was named Best Actress of the Year and, in the UK, went on to win the Miss Black UK and Miss Black Europe Awards
in 2014. In addition to her full-time role at Sycom she has her own media business in Nigeria, Naija Eagle Watch, which she says, “allows me to write scripts for production, blending my interests in security movies and documentaries.”
And, today, her involvement in cybersecurity extends well beyond her main role. She is the founder of SecureTechJuris a non profit digital technology platform through which she disseminates cybersecurity awareness information, information on the legal and ethical implications of digital technology.
She has a vision to expand SecureTechJuris to embrace artificial intelligence and machine learning. She is also involved with Cybersafe Foundation, CyBlack Foundation and Cybersecurity Nigeria (Cysecng). Cybersafe is a non profit organisation dedicated to promoting cybersecurity awareness and online safety. Okechukwu-Philip is a mentor for women around the world aged 18 – 28, and also a mentor in CyBlack, a non profit organisation that connects cybersecurity professionals and enthusiasts in the UK and beyond.
“Being involved in industry associations, particularly in mentoring and speaking roles, has been an incredibly rewarding experience for me, she says. “Not only does it allow me to contribute to the growth and progress of the cybersecurity community, but it also enriches my own professional and personal growth.
“Through mentoring I’ve been able to guide and support aspiring cybersecurity professionals on their transformative journeys. Witnessing their growth and
success brings me immense satisfaction and a sense of fulfilment in giving back to the community.
“Moreover, engaging with like-minded professionals, experts and conference attendees through networking opportunities has expanded my professional network and opened doors to valuable collaborations. It keeps me up to date with the latest trends and developments in cybersecurity, enabling me to stay at the forefront of the field.
“Building credibility and reputation as a mentor and speaker has boosted my visibility and expertise within the cybersecurity community. It has established me as an authority in my field and paved the way for exciting opportunities and partnerships.”
At each stage of her journey, Okechukwu-Philip says particular individuals played key roles. First was Edward Onyenweaku, today Head of Risk and Compliance (Cybersecurity) in Etranzact Nigeria.
“In my final year as a lawyer he contacted me several times advising me to start up my cybersecurity journey giving reasons, but it seemed farfetched to me and impossible, because as a lawyer I was looking at it from another angle. Edward never gave up on me and he has mentored and helped me during challenging times, and I want to use this opportunity to appreciate him.”
Second was Dr Julian Richards, Associate Dean in the School of Humanities and Social Sciences; and Director of the Centre for Security and Intelligence Studies at the University of Buckingham (BUCSIS). “Julian was my supervisor who made me understand the intersection between security and intelligence with cybersecurity and guided me through my research works. Julian has taught me an immense amount on this journey.”
Sycom CEO, Abdulrahman “has been consistent with granting me opportunities for continuous development and further training which have made a significant impact in my career today. He still mentors me, and am very grateful to him.”
Dr. Kenneth Okereafor, Head Cybersecurity, NHIS, “proved to be an extraordinary mentor who transformed my career trajectory from law to cybersecurity. With unwavering support and guidance, he nurtured my passion for the field, instilling confidence and inspiring me to excel.
Counter all this support have been “individuals who acted as roadblocks during my journey,” Okechukwu Philip says.
“As a female cybersecurity professional I have faced discrimination and bias when trying to establish myself or advance in the industry. I have experienced




www.linkedin.com/in/uloaku-philip

“Despite these challenges, I remain resilient and determined. I have broken through these barriers, proving my worth and making significant contributions to cybersecurity. I am committed to demanding greater inclusivity and equality for all in the industry. My experiences have only strengthened my resolve to promote diversity and create a more supportive and empowering environment for everyone in cybersecurity.”

Then she co-found a web development, digital agency and web hosting business. “I applied for small business funding and was able to kick start the business,” she says. “This was super challenging, in the best of ways. I had to wear many hats, learn all about how to run a business, mentor employees, find contractors, form customer relationships, as well as actually doing the work such as designing and web development.
Yianna Paris encountered computers, and hacking, at an early age. “When I was a kid, I used to love sneaking onto the computer. I found out my parents’ password and was on there playing video games and editing system files for fun,” she recalls. She was “five or six” at the time.
And she did not stop there. “I didn’t always know what I was doing, especially the first time I pulled apart our family PC,” she says. “Eventually it was up to me to learn how to put it back together again. In video games I was always finding broken functionality, and sometimes this led me to new areas to explore by skipping over levels or bosses, using the functionality to make the game easier or faster.”
However, her early manifestation of hacking skills did not initially lead to a career in security, or even IT. Paris left school at 15, was homeless for a time and found her first job in an automotive retail store. She “loved cars and car parts, so it was fun learning more about these things.”
She went on to have multiple part time and casual jobs at various retail stores, including an electronics store, and for a time held a trainee management position. On the side she made websites and cosplay costumes for friends, and enjoyed being creative.
“I also hired people who were specifically struggling to find opportunities to work due to various things such as disability, travel time and family commitments. This meant we actually supported working from home (a decade before Covid!). I offered flexibility because I knew what it was like to need that kind of understanding. People are motivated and work in different ways, so I also provided working holidays, where we did some training and enjoyed being away in the countryside for a few days.”
Paris has also had a multifaceted educational journey since leaving school. First a Certificate IV in Small Business Management, Business/Commerce, General, from Swinburne University of Technology. This was followed by a Diploma of Visual Art and Advanced Design and a Bachelor of Digital Media Design, Animation, 3D and Communication Design, both from Swinburne, and a Bachelor of Computer Science from RMIT University.
It was at university that Paris gained exposure to cybersecurity, but it failed to really pique her interest. “We had security clubs at university and I happened to meet a few people in them. They introduced me to Hack the Box, capture the flags, which servers in the school were open, what a rogue access point is, how dangerous chmod 777 is. Many things were on my radar. But I still didn’t think this was a career for me. I wasn’t a hardcore hacker or sysadmin like others. I wasn’t really sure what skills were important or how viable a career it was. It seemed out of reach.”
However, she did discover a flair for open source intelligence gathering. “I wasn’t aware of the ‘intelligence’ part of that before I joined cybersecurity, but I did understand how to gather information from public sources. I was good at picking up details, investigating small clues that led me to big findings. I still practice and refine this skill.”
While studying for her Bachelor of Computer Science Paris got a job as a software developer with SEEK in Melbourne and seven months later switched roles to become a security engineer. “After showing initiative and interest in security, asking questions, learning how to pentest, and giving workshops to my team, I was asked by Dr Pam O’Shea if I’d like an opportunity to see what it’s like to work in a security team,” she recalls.
“Liam Connolly (the CISO) agreed to take the chance and I am so glad he did. This was the opportunity I needed. It felt like I had found ‘my people’ and I haven’t looked back since.
“Learning what fast-paced agile software development is like gave me a different view in security. Traditionally, I think infosec teams have been seen as the ones in the basement, the ones who find issues and throw them over the fence, demanding things be fixed. Or the auditor imposing some kind of checklist governance.
“When a web developer can be deploying several times a day, the traditional ways we may have approached security don’t work as well. My view around strong relationships with people across the business started here. It’s not always easy talking to people and it can be incredibly tiring, but knowing who I was helping with security meant I could collaborate and introduce security activities where they would actually be followed. It’s no use making a policy if nobody is going to follow it because it doesn’t fit into their workflow.”
She adds: “I felt like I was really working in security during log4j [a zero-day vulnerability discovered in November 2021 and branded “the single biggest,
most critical vulnerability of the last decade”]. I think a lot of us were battle tested in those weeks, especially as a team still forming together. I was on Twitter when I saw it blowing up and I jumped on to the company chat.
“I remember having to make the call whether I should bother people in the middle of the night, if it was something we needed to worry about. I learnt what it meant when people say ‘cybersecurity is a marathon, not a sprint’. I also learnt I loved the adrenaline rush. I liked helping and organising people, and it really tested how well I could understand a problem in a very short amount of time. It also sparked the investigator side within me, which led me to even more opportunities.”
Paris left SEEK in February 2023 and moved to The Netherlands to join global IT consultancy Xebia as an application and offensive security consultant.
“Xebia contacted me on LinkedIn, because they liked my approach to security,” she says. “My values, my talk at the Diana Initiative in Vegas [A diversity driven conference committed to helping all underrepresented genders, sexualities, races and cultures in information security] and how I present my ideas really resonated with the security team and I feel lucky to be a security consultant for Xebia now.
“I work with web, hardware and embedded software, doing penetration testing, secure code review, hunting threats and increasing visibility. My job mostly consists of exchanging knowledge with people. I was once referred to as a ‘security therapist’. People open up to me, I figure out their needs and I help integrate security in a way that works for them. If I’m not exchanging knowledge, I’m trying to gain it, often very quickly. It’s not uncommon for me to be learning new technologies such as programming languages or platforms, both the software kind and physical hardware kind.
“My background in software development has helped with understanding a lot more of the software engineering side of building products.
For many companies, how effectively teams work together really impacts the quality of the product being created.”
Paris describes her typical day at Xebia as being chaotic. “It could be me asking people ‘why’ a lot. I might be delving deep into a software application, looking for bugs or ways to exploit its functionality. Then I’d talk to an engineer or team, validating and finding more areas of work that need extra security eyes. I question everything. I usually spend time exchanging knowledge, either in a workshop, or Q&A presentation on different topics such as the importance of secure design and threat modelling.
“The biggest challenge is having to switch the language when I talk to people in different domains. We need to find a common way to understand each other. I spend a lot of time thinking about how to best communicate concepts - visual, written, verbal, all of the above.
“Is right now the time to talk about how a user created a file that is not validated when read and when passed to an execute function, lead to command injection, or do I need to better communicate what the actual risk is here in more appropriate language for higher management?”
Paris has also faced challenges many readers will be familiar with, challenges that arise simply from her gender.
“As a co-owner of a software business I was looked at as the ‘customer relationship’ person,” she recalls. “In a way, this taught me a lot about stakeholder management, but it also showed me how people underestimated me.
“I remember presenting technical solutions to meeting rooms full of men, and any time they had a technical question, they’d look to my male colleague instead of me. He advocated for me by telling them to direct their question at me, as it was my solution, but that feeling of not being trusted or looked at as ‘technical’ always stuck with me.
“In recent years I’ve been part of teams that had the cliquey boys club. It took a lot of learning opportunities away from me because I was never included in projects or research. I enjoyed organising team bonding events until I realised it was always left to me, and now I intentionally do not put my hand up for these, even when I see they are needed for morale.
“I can’t let myself keep being put in that position until others show they are also willing to do this kind of organisation. Even interviewing for security positions in a different country has shown me that we have a long way to go. I’ve been asked questions such as my age, if I’m married, when I plan to have kids.”
Paris’ experience of poverty—she has “been in the position where I couldn’t even afford groceries for the week”—has driven her to helping others disadvantaged.
“Seeing I could provide knowledge into technology and how fun a job in tech can be, I wanted to share this with people of many ages,” she says. “I’ve run coding workshops weekly for primary school kids, helped run events for highschoolers learning about code and jobs in tech.
“I have run events like hackathons for university students so they can learn a new skill and how to collaborate with other people. I run capture the flag
events internally at different businesses, and have created scavenger hunts so people from any domain and background can learn about security.
“I want to provide an opportunity to learn and collaborate. It’s two-way. I get to show people a bit of my world in security and tech, but I also get to learn about theirs. We find ways to speak a common language and involve each other in projects. I expand my knowledge and get a deeper understanding of why we see certain problems in security and who can help us solve these problems.”
Paris also volunteers with AWSN and the Women in Cybersecurity Community Association (WICCA) in the Netherlands. With AWSN she has been involved as a mentor, guest speaker and has made many connections delivering workshops to women who want to learn about the information security industry.
With WICCA she helped organise its first convention, to be held in October 2023 and organised a community meetup hosted by her employer, Xebia.

For herself, Paris says she plan to do further research, possibly by studying for a master’s or PhD. ‘I still have so many ideas that I want to pursue. At the moment I am going deeper into code analysis, how organisation culture can affect software engineering and what that means for security. I really love data, so when I do technical discovery and detections for companies, I try to find new insights or clues.”
www.linkedin.com/in/salted-hash
Calister Apollonary Simba’s cybersecurity career journey began after completing a Diploma in Electronics and Telecommunications and failing to fulfil her dream of becoming a pilot. “I had a great passion for flying and airplanes,” she says. “Unfortunately pursuing a pilot’s education was not feasible in Tanzania at the time, because of financial constraints: it was a costly field.”
It was while studying electronics she discovered cybersecurity, courtesy of a student leader who recommended a cybersecurity degree. “Although I had limited knowledge about the field, I embraced the opportunity to learn and get closer to my aviationrelated aspirations,” Simba says. She went on to gain a Bachelor of Science in Computer and Information Security from the University of Dodoma, also in Tanzania.
Over time, Simba developed a genuine love for cybersecurity and excelled in her academic studies. “Each day presented new challenges to solve, continuous learning opportunities and a sense of purpose in defending against potential threats. Despite the challenges I faced during my college years, my passion for cybersecurity never waned. This dedication led me to become the top student in the program upon completing my course.”
Today she is an information systems security engineer with the Central Bank of Tanzania and says the most enjoyable aspect of her job is confronting novel cybersecurity challenges and threats.

“I find great motivation in encountering new attacks or increasingly sophisticated threats. Each day brings an opportunity to expand my knowledge and devise innovative ways to defend against these cyber threats. As a defender (blue teamer/purple teamer), I take immense pleasure in facing diverse attacks that employ various techniques.
“This process not only enhances my understanding of these methods but also allows me to protect my organisation effectively while finding joy in the work I do. Defending against cyber threats is a thrilling and fulfilling experience that keeps me passionate and engaged in the cybersecurity domain.
“On a day-to-day basis, my job is multifaceted, encompassing various responsibilities and projects. I typically dedicate five hours to my routine tasks, using a wide range of tools and leveraging automation as a 21st-century approach. I employ techniques like risk assessment and threat modelling to diligently detect and analyse threats within the bank’s network. Staying current is paramount, so I continuously scour different security sources and professional networks to be well-informed about the latest developments in the cybersecurity landscape.
Calister Apollonary Simba Information Systems Security Engineer at Central Bank of Tanzania“Additionally, I spend the other five hours of my workday immersed in project-related activities. As a DevSecOps engineer I collaborate closely with DevOps engineers to ensure comprehensive security measures are applied across all phases of project management. By aligning security seamlessly with development operations we effectively address and mitigate potential security threats throughout the project lifecycle.”
In addition to her academic and career achievements, Simba has become a staunch advocate for gender equality in Tanzania’s technology and cybersecurity communities. She founded Cyberdada Tanzania. It’s an online initiative that empowers girls and women aged nine to 30 who have a passion for technology and cybersecurity by connecting them with women already established in the industry.
“The initiative aims to foster digital safety awareness and skill-building through both physical and virtual training and mentoring sessions,” Simba says.
“Through Cyberdada we strive to create a supportive network where these two groups can interact, learn from each other and bridge the gender gap in cybersecurity.
“The Cyberdada family, which I take immense pride from forming and creating, has become a source of motivation. Receiving calls or texts from young girls within the Cyberdada group rejuvenates me and fuels my determination to advance in the cybersecurity journey.”
To date, Cyberdada has successfully empowered over 70 girls and its mentoring efforts extend beyond Tanzania, reaching women in Kenya and Nigeria, contributing to narrowing of the gender gap in cybersecurity.
Simba also cofounded CyberJamii, an organisation that, she says, “intends to reduce cybercrime by providing awareness to the society and promoting ICT and cybersecurity skills and innovations with a number of male professionals.” She was the sole female among the founders. “Remarkably, we have
maintained a strong bond, supporting each other throughout our journeys,” she says.
And Simba has gained a number of accolades and awards during her career. She was an International Telecommunication Union Innovation Challenge winner in 2020. In the same year she was honoured as the Woman Hacker of the Year by Cyber in Africa/ African Women in Security Network, and in 2021 selected as the IFSEC Global Influencer in Security and Fire - One to Watch by IFSEC Global – Security and Fire News. She was also recognised as one of the 100 ‘Sheroes’ in Tanzania for 2020/2021.
Aside from gender-related barriers, Simba says anyone in Tanzania aspiring to a career in cybersecurity faces significant hurdles. “The country is still in the early stages of technological development and cybersecurity is often overlooked by both large and small organisations. Consequently, cybersecurity professionals may find fewer opportunities, and when they do gain a position, they may not be valued or compensated adequately.
“The scarcity of females in senior positions in Tanzania creates a lack of visible role models and mentors that hinders young girls from envisioning a path for career advancement in cybersecurity. Building a more diverse leadership in the field is essential to inspire and guide the next generation of women professionals.
“I encourage my professional network in Tanzania to raise their voices, advocate for the significance of cybersecurity and demand fair compensation. By doing so, we hope to see positive change in coming years, with increased recognition and better opportunities for cybersecurity professionals in Tanzania.
“Women often face less exposure to cybersecurity than their male counterparts. They may not receive the same level of encouragement from educators, family members or peers to pursue careers in this field. In Tanzania, for example, many families do not traditionally encourage girls to enter tech related fields.”
Simba hopes her career journey can change this situation by example. “My journey serves as a wakeup call to challenge these norms and inspire change. As more parents reach out seeking guidance for their daughters, I see progress towards my goal of fostering greater interest and participation among young girls in cybersecurity.”
For Tanzanian women aspiring to cybersecurity careers, Simba says networking, engagement and mentorship are essential. “Cultivate a professional network by connecting with cybersecurity experts and attending industry events. Engaging in online forums and communities can also provide valuable insights and expose you to potential job opportunities. Seek out mentors who can guide you throughout your career journey. Having someone to offer guidance, correct your course, or provide encouragement is invaluable.”
Simba herself credits mentors, supporters and advocates with having played pivotal roles in her career journey.
“One individual stands out—Macbethana Wilfred, my exceptional mentor. Although we faced challenges in the beginning, our shared experiences brought us closer professionally, fostering a profound personal understanding,” she says.
“Additionally, I have had the privilege of meeting remarkable women like Yuster Cornerly and Jamila Wafula whose unwavering dedication to the cybersecurity path inspires me. In times of uncertainty, I find myself seeking their guidance: they exemplify resilience and tenacity.
“An early source of inspiration was my first female boss, a head of project management. In my interview she left a lasting impression by advising me not to settle for less than I deserved, effectively convincing me to seize the position.”
Simba, meanwhile, has her sights set on gaining further cybersecurity skills. “I find myself drawn towards roles such as cybersecurity architect, governance, risk and compliance, and DevSecOps. These positions excite me as they allow me to integrate my creativity with my career, providing a dynamic and fulfilling path,” she says.
“Looking ahead, my aspirations extend to fields like cyber psychology and cyber law. I firmly believe that cybersecurity encompasses a wide spectrum of roles, each playing a vital part in defending against threats. Delving into cyber psychology holds immense significance for me. By understanding the motivations and behaviours of cyber attackers from a human perspective I can gain a unique angle that complements the technical aspects of cybersecurity.”
Beyond her passion for cybersecurity, Simba likes to immerse herself in various artistic pursuits. “Creating art has always been close to my heart, and my love for poetry dates back to my secondary school days,” she says. “Recently, I’ve taken up painting, embracing the joy of expressing myself artistically. For me, fun is synonymous with artistry.
“In my leisure time, I find solace in the enchanting melodies of Jazz music. It’s not uncommon to spot me dancing or grooving to the rhythm, completely lost in the harmonies.
“Cooking is another cherished pastime, especially when it’s for my loved ones. Preparing a delicious meal and sharing it with them brings immense satisfaction and joy. Often, I find myself engaged in deep conversations about life and exploring wild and imaginative scenarios.”
www.linkedin.com/in/calister-apollonary-simba34



As CISO roles go, Nancy Taneja must have one of the biggest. She is the CISO for the Primary Health Sector at Te Whatu Ora (Health New Zealand) and supports the cybersecurity of more than 150,000 plus healthcare providers, 3,000-plus small to medium sized businesses and hundreds of suppliers. They include primary health organisations, general practices, pharmacies, allied health professions and Māori healthcare providers, as well as their respective IT, security and health system suppliers.
If scale were not challenge enough, she says, “The sector has been undergoing significant reform, faced the challenges of a global pandemic, and been experiencing a healthcare workforce crisis.” All this in addition to “skill shortages, restricted budgets and limited awareness.”
She adds: “Bringing cybersecurity as an important conversation to the table in such challenging times has not been an easy task, but it’s been a journey worth pursuing. A key part of my role is forming relationships and working together to achieve shared cybersecurity goals, which I find very fulfilling.
“Taking on a role as large as the CISO for the primary health sector was daunting at first, but it has been truly rewarding. Working for an organisation like
Te Whatu Ora with amazing leadership, and with other organisations that have a shared focus to strengthen the security of our health sector, means the highs certainly outweigh any lows.”
Taneja has a bachelor’s degree in business administration, a master’s in IT and substantial experience in senior IT roles. Her move into cybersecurity was very recent.

Security had become an ever-growing focus in the last few years of her previous role and Taneja found herself drawn to cybersecurity as a field of knowledge and expertise. “I’m very proud of myself for making the deliberate choice to move into cybersecurity,” she says.
“Having led major technology transition programmes in the past, ensuring all technology was implemented, used and maintained in a secure manner was vital to our success.
“After building the cybersecurity portfolio from the ground up in my previous role and working alongside healthcare providers in the region to focus on the secure use of technology, it quickly became clear to me that this was the right direction in which to take my career.”
CISO - Primary Health Sector at Te Whatu Ora Health New ZealandShe says many skills have been important to enable her career journey: business analysis, project management, agile, basic and advanced security concepts, risk management, change management, global and national security standards, and a strong understanding of the sector or industry in which she is working.
“It’s very important to look beyond your role and department to understand the purpose of the services being delivered and the overall strategic objectives of the business.”
Taneja says she has risen steadily through the ranks in the course of her career by focusing on using the opportunities of her various roles to further develop her skills and her knowledge of how organisations function and deliver services, and on the role secure technology plays.
She adds: “Developing soft skills has also been hugely important in my journey, and observing other leaders on their leadership journeys through forums like Women in Leadership has been a key part of my development.”
Despite her success, Taneja says a lack of confidence and self-doubt have been a major roadblock, along with another personal attribute over which she had little control. “I am a short, stout Indian woman who has come far in a world where first impressions are everything. However, over time I’ve come to understand that bias can be a natural instinct with many forms. I’ve personally found that focusing on managing your weaknesses and growing your strengths is the best strategy to get ahead in life.”
She has also drawn support and inspiration from multiple, diverse sources. “The great leaders of the world have inspired me to be resilient and brave. My parents have inspired me to work hard and be confident. Some of my amazing managers have inspired me to develop strategic thinking, servant leadership, relationships and partnerships, risk-based thinking, taking people on the journey of change,
and building high-performance teams. My husband has inspired me to embody the art of balance in my thinking and my daughter has truly inspired me to be disciplined.”
However, there was one person early on who played a pivotal role in Taneja’s career trajectory: her university maths teacher. “I wasn’t academic, and maths particularly was my nemesis, until I found a teacher (or should I say that a teacher found me!) while I was taking accounting as part of my bachelor’s degree,” she recalls.
“I was working hard and getting better to the point my tutor casually told me my maths was so good I should have pursued engineering. That one statement changed my confidence. While I had been working hard, that positive reinforcement at the right time made me feel that, if I could conquer maths, then I could conquer anything.
“Everything started making sense, and from that year on, I topped my college and university classes throughout my bachelor’s and master’s degrees. I was a late bloomer, but I made it due to the right guidance and effort.”
Outside of work, Taneja says she is “the IT helpdesk and security advisor for all of my family!” She also puts her IT skills to good use as a board member for a charitable trust focused on delivering equitable and accessible music lessons to children. When pandemic lockdowns hit New Zealand, she supported the trust to deliver music lessons securely online, which she describes as “a great achievement at the time.”
She also works to upskill herself. Her current area of learning is on the technology capability future roadmap and the security issues thrown up by artificial intelligence.
www.linkedin.com/in/nancytaneja
“Cyber attacks on critical infrastructure are amongst top five global risks in 2023. We therefore need to be more proactive and keep one step ahead of cyber criminals to protect the electricity network in a more efficient and robust manner.”
Group Head: Information Security at National State Owned Entity
As CISO roles go there can be few more onerous than Sithembile Songo’s. As CISO for the state-owned entity responsible for producing 95 percent of South Africa’s electricity she bears great responsibility.

My role enables organisations to fulfil their mandates in a secured manner through a defined and well executed cyber security strategy and programme. My current role primarily focuses on protecting the national critical infrastructure from potential cyberattacks at a strategic level, thus preventing a negative impact on the economy, which is very rewarding” she says. “I enable secure business operations, including secure generation, transmission, and distribution of electricity, which depend on operational technology (OT) that largely depends on secured computer networks and systems to produce electricity.
“My day is quite fast paced and typically involves a mix of strategic planning, team management and guidance on operational requirements. Being in a leadership role, I often participate in meetings with executives and other stakeholders. Overall, my day as the CISO is hectic, but it’s also rewarding to see how our efforts protect the organisation and the country from potential cyber-attacks.
She has held the role for just under two years. It’s the culmination of a 20-year career in information security and experience gained in various sectors that has included leadership cyber security roles in the financial, investment, telecoms, energy and public sectors. She “fell in love with cybersecurity right from the outset. and never looked back despite the hecticness and challenges that come with the job.”
And she has achieved her current role despite very humble beginnings. “My late father told me he used to live on a farm where he would be obliged to serve as a slave to the owner of the farm when he reaches a certain age,” she says. “Failure to comply would result in his entire extended family being banished, with no place to stay or food to eat. Nevertheless, my father decided to take the risk and escaped to create a better life for his parents and his future immediate family, us.”
From him Songo appears to have inherited an appetite for risk. “Taking calculated risks became a hallmark of my journey,” she says. “In a world where many preferred the safety of the familiar, I chose the path less travelled, such as choosing high grade maths and high-grade science at school, leaving my comfort zone several times. Each risk was an opportunity to learn, to evolve and to become the person I envisioned.”
Her parents were also instrumental in her bucking the trend and pursuing an education. “They had big dreams for my sisters and I, despite society’s then opposition to educating girls.”
Songo says there are no career role she regrets taking. “However, there were certain offers that I couldn’t accept when my kids were still very young. Looking back, I’m glad that I stepped outside my comfort zone several times and embraced uncertainty with open arms.
“Each environment contributed to my growth and development, shaped my expertise, career path and contributions to cybersecurity. Embracing each of these positions with enthusiasm and a willingness to contribute and learn led to a fulfilling and successful cybersecurity journey.”
With her humble beginnings, Songo says she faced financial struggles early in her career and, later “countless hurdles: imposter syndrome, stereotypes and naysayers,” all of which she tackled with “a fierce passion for success, a hunger to rise above adversity, create a brighter future, aspire and be a blessing to other people,” aided by “both male and female leaders who recognised my potential and supported me, and whose confidence in my expertise propelled me forward when self doubt threatened to take hold.”
Songo’s first higher education qualification was a National Diploma in Computer Systems Engineering from Vaal University of Technology after which she was introduced to and “fell in love with” information security through an information security internship.
“It also suits my personality very well because I’m protective of everyone who is valuable to me,” she says. “I then occupied various positions, while furthering my studies in the field and expanded my horizons. These experiences not only added valuable expertise but also instilled a sense of self-belief and confidence.”
She went on to gain a Master of Science in information Security from the University of London and several globally recognised cybersecurity professional certifications.
Today she is a mentor, advisory board member, a speaker at local and global cybersecurity events, and a member of several global security forums including Information Security Alliance Media Group, Young CISO Network mentor, Women in Cyber Security and CorpSecurity International Community, CISO2CISO community.
She describes her early career as being a mix of supportive structures and adversity. “I came across stereotypes who undervalued women and assumed women are less capable compared to their male counterparts. As a woman, I had to work twice as hard compared to the male colleagues.
“Early in my career my work contract was terminated when my manager discovered that I was expecting a child. This occurred despite a verbal agreement that my contract would be renewed. However, another better opportunity presented itself.
“I also came across both male and female leaders and colleagues who recognised my potential and supported me. Their confidence in my expertise propelled me forward when self-doubt threatened to take hold.”
Looking ahead Songo sees herself as a strategic business partner that enable organisations to uplift their cybersecurity maturity. She is also contemplating enrolling for PhD when her workload and daily schedule allow.
“I hope my career journey will inspire others and become a beacon of hope for those who are still walking the path I once trod,” she says. “And most importantly I hope it will also serve as a reminder to everyone that humble beginnings or adversity along the way do not define one’s destiny.” Last but not least, embrace each opportunity, do your part with diligence, passion, integrity and allow God to do rest. www.linkedin.com/in/sithembile-songo-08695328
a tough ride at times, as female representation in that part of the business was low and the few females who were there were often overlooked by their peers and leaders,” Hatziioannou says.
“There was a perception that the females were lacking in technical capabilities and were only employed because of their soft skills, or to meet gender equality targets. As a female, you must work harder to be recognised and heard. That said, I soon found proving people wrong to be one of my motivators.
In school Magda Hatziioannou was drawn to science and maths because she enjoyed problem solving and the science experiments. She did try a broad range of subjects but decided none of them were for her, so she continued down the science path and gained a Bachelor of Physics degree and a Diploma of Telecommunications. This led her to the telecommunications industry and roles focused on incident management and people management. She started as a trainee at Telstra monitoring the national transmission network before moving into a real time incident management leadership role. This led her into people management: her last role at Telstra was leading Telstra’s major incident management team. This gave her exposure to all Telstra’s products, national and international networks and security.
With this operational experience she was asked to accompany one of Telstra’s security experts to Telstra’s Security Operations Centre to review operational processes and identify what was needed to align the security operations business with the network and IT business processes. This gave her the opportunity to meet the security team, talk about the industry and understand their accountabilities, pressures and challenges. This experience helped spark her interest in security.
During her time at Telstra, she was given several opportunities that helped her career trajectory. “It was

“I found great satisfaction in taking those opportunities to let my work and abilities speak for themselves. I can thank my mum for this drive. She taught me to go for what I want and not let anyone stop me or tell me otherwise. She didn’t want me missing out on getting an education and doing what I wanted like she did. Whilst personal drive assisted, it was difficult to maintain when my voice or achievements were not acknowledged.”
Hatziioannou says some great male sponsors made a real difference. “They are the ones who helped to get my achievements and capabilities recognised by believing in me and giving me the exposure and opportunities I needed to show others what they could not see.
“Working on executive sponsored programs and tasks, acting in general manager roles, compiling data and information for executive and board reports all helped to grow my opportunities and network of people. Their promotion, feedback and guidance were irreplaceable, and I will always be grateful to them.”
Hatziioannou’s move into her current role as Network Security Controls Manager at NBN came about unexpectedly and during a time of self reflection.
“A friend who was working at NBN touched base just prior to the Christmas break. She was aware of
Network Security Controls Manager at NBNmy interest in security and mentioned there was a job at NBN that sounded like it would be a good fit,” she says.
“I am not always the quickest to make decisions of this nature and I wasn’t thinking about leaving Telstra at the time as I really enjoyed working at the forefront of technology, and I had a great team and loved the work. So, I just got on with being busy. However, not long afterwards I had a very close family member pass away. I think it gave me time to stop and reflect on life in general, and I decided I would fix my resumé and submit the application. Before I knew it, I was going in for my second interview and signing a contract. I often say it was my family member nudging me to take the leap.
“I don’t have any regrets. Everything I experienced, including the tough times, helped to make me stronger, more resilient, and ultimately who I am today. My role today is like my previous roles where no two days are ever the same and the best laid plans can be thrown into disarray at the drop of a hat. Whilst no one enjoys incidents, there is a particular energy they bring, along with strong collaboration across company and industry, which is inspiring to see and be part of.
“In such events, it’s amazing seeing what the team can achieve when they are all working together towards the same goal. I have learnt so much since taking on this role, but I also realised that I had some security knowledge from my previous role.”
Hatziioannou says a typical day in her role can be quite diverse. It might include monitoring control effectiveness, uplifting capabilities, or responding to security events.
“Other than the variety of tasks, I do enjoy being able to mix technology with people management. It is extremely rewarding as a manager to see your team develop and grow their careers,” she says.
“Being able to clear the path and let them fly is such a great experience, and it’s always sad to say, ‘see you
next time’ to your staff but also awesome to see them happy and fulfilling their goals.”
Having learnt much from her managers, peers and teams, Hatziioannou decided she needed to help other women avoid some of the challenges she and her peers had experienced. So she made a very conscious decision to actively promote women across the business, to help them strengthen confidence in themselves and encourage them to speak up and take a seat at the table.
“This is something I do for all my staff but sometimes we need a bit of an extra push. Sharing our experiences and approaches are important not only to learn about ways to tackle situations but to also realise you aren’t alone and there is a light at the end of the tunnel,” she says.
“I have seen more female representation in the security industry than in any of the previous technology domains I worked in, which was pleasantly surprising. I think, in security, diverse backgrounds and thinking are important and only strengthen our defences.”
One of the biggest challenges Hatziioannou sees is embedding a strong security mindset and culture across the business. “This can never be a point in time exercise and must be an ongoing educational process, especially with the rapidly evolving threat and geopolitical landscapes. As technology becomes more powerful and more intelligent so do the adversaries.”
She enjoys the variety and challenges her role and her environment bring and says she still has much more to learn and do. “I love the change, and I am very grateful for my manager who was brave enough to take a punt on hiring me into this role with no security roles under my belt and no formal security training. I am not sure where my security journey will end, because there are so many different options, so stay tuned.”
www.linkedin.com/in/magda-h-1b7131156
Bianca Colatruglio joined Air Canada’s corporate security team in April 2019 and since June 2022 has held the position of Director, Aviation Security and Regulatory Compliance, a position that covers all aviation security matters for the company.

Her responsibilities include developing and implementing strategies and programs to ensure Air Canada complies with its domestic and international security obligations, monitoring and assessing security threats and risks to the organisation, and developing and maintaining the airline’s 24/7 Global Security Operations Centre. She says the overarching goal for her and her team is to maintain and enhance Air Canada’s security management system and security program while striving for continuous improvement.
“What I enjoy most about my role is that it is constantly evolving,” she says. “There will never be a time where I have ‘seen it all’ or know what to expect on any given day. Working at an airline is an adventure. So combining that with the ever-changing world of security means it’s unpredictable but also full of people who are passionate and thrive in this type of environment. The biggest challenge is similar:
in this industry the focus and priorities shift with the operational needs, and sometimes those needs speed up or slow down any given initiative we are working on. Adaptability needs to run through your veins.
“A typical day varies enormously. Sometimes it’s a day of back-to-back Teams meetings . Sometimes I am on the other side of the world meeting with operational colleagues and verifying compliance . However, my favourite times are when I get to be face-to-face with international industry colleagues, associations and government agencies.”
Growing up, Colatruglio wanted to be a news anchor and was passionate about being a journalist. Then, aged 16 at the start of her senior year of secondary school, 9/11 happened.
“I remember being glued to the TV for weeks, thinking about how I wanted to be one of the journalists on the ground digging up information about how and why this happened,” she recalls.
“After graduating from secondary school I spent a couple of teenage years trying to figure out what to do with my life. I eventually applied to join Canada’s
Director, Aviation Security and Regulatory Compliance at Air Canadatop journalism program and moved to Ottawa to attend university. One of my electives was a course on international relations and security. The professor had a huge impact on me and opened my eyes to a world of topics I had never been exposed to. At the same time, like most people in the nation’s capital, I became aware of all the career opportunities with the federal government.”
On a whim, with much interest but limited experience , Colatruglio applied for a position at the Department of Transport as an Aviation security intelligence analyst working in the department’s 24/7 operations centre.
“Luckily for me, the recruitment process was focused on a candidate’s good judgement abilities, critical thinking skills and ability to prioritise and multitask, rather than on aviation security knowledge and experience the organisation could later provide training on ,” she says.
“I officially entered the world of aviation security in 2011. I spent eight years working in the department, in a variety of roles. I loved my time there. I focused mostly on the Passenger Protect Program, Canada’s version of a no fly list, along with incident management and security intelligence. Collaborating with industry was my favourite aspect of the job. I found progress to be possible only when all stakeholders were involved and had a common understanding and shared goals.
“I built strong relationships with my industry colleagues, particularly at the airlines, and I always imagined one day making the move to ‘the other side ’. The general feedback was always, “why would you give up your government salary, pension and job security?” Good questions, but it was never about those for me, and still isn’t. I became so interested and passionate about aviation security that I knew I would follow the subject matter throughout the rest of my career.
“During my tenure as Chief of the Security Intelligence Assessment Branch, still focused on aviation security, I was contacted by Air Canada about a position they
thought I might be interested in. I discussed this opportunity with government and industry colleagues, wanting to weigh the option appropriately, knowing all along it was what I wanted.
“The position was focused on security regulatory compliance, which I had minimal experience in. However, I knew this was my way in the door and hoped I could eventually expand to broader aviation security issues. Before I knew it, I was hired and moving back to Montreal. It has been an absolute whirlwind since I joined Air Canada in August 2019. Working at an airline could not be more different from working for the federal government. I have to say, it is definitely enjoyable to have left the infamous layered bureaucracy behind, and I am grateful to be surrounded by passionate colleagues who constantly go above and beyond as if doing so is the norm. Being at Air Canada throughout the pandemic was an experience I will never forget, and absolutely solidified that I had made the right decision for my career.
“Security is the type of field that most people stay in for a lifetime. What I find the most important, is that being successful in this field of work is largely contingent on the ability to build trusted and strong relationships. In most cases this happens organically because most people in security share the same level of passion and motivation. We always say there is no competition in security. Commercially, two organisations can be direct competitors, but when it comes to security we are all on the same team and consistently work transparently and collaboratively. Having the connections and maintaining them makes both the day-to-day tasks and the exceptional circumstances significantly easier to deal with.
“A potential or actual crisis is when I really see what it means to work in security. The way people from all different backgrounds, locations, life experiences and industries can join together and almost seamlessly know what needs to be done and how to achieve it is incredible.
“I would like to further develop my leadership and business management and administration skills.
I want to make sure I am the best possible leader I can be for my team, colleagues and the organisation. I have been blessed with some incredible role models who inspire me to want to develop into the best version of myself I can be. I also want to learn more about the business side of the airline, how decisions are made, how the strategies are developed, and how a strategy becomes reality. Ensuring I have a comprehensive understanding of why the organisation and industry move in a certain direction will also help me develop my own objectives for our department and support the broader goals of the business.
“It’s hard for me to say I have never doubted that security is the right place for me. Unfortunately, I, like most women in security and all too many other fields, have had frustrating, upsetting, and unfair experiences working in a historically male dominated field. Naively, I had assumed that moving upward in the chain of command would convince some people that I have earned my right to be here. In some cases, it had the opposite effect. I have been told I don’t deserve my position because of my gender and my age. I have been told I will never be respected in my position because no one takes a woman seriously. I have been told that unless I have some kind of specific career experience, I will never understand security the way others do. Thankfully, my leadership throughout my time at Air Canada has stood by me and supported me through any of these challenges, and continue to support diversity across the company, and in particular within our security team.
Opportunities have not been provided to meI have missed out on professional opportunities because it would “look better” if a man participated. A previous boss once told me that I, despite being the subject matter expert, was only invited to a high-level meeting so the men would have something pretty to look at. It is disheartening that this messaging and behaviour is still happening to so many women, and even more significantly to Black and Indigenous women and women of colour.
“To this day, I am all too often the only woman in the room. Now, I know I am rightfully taking my place at the table and that I am also creating space for more women to join in. Conversely, there are some exceptional women who have paved the way for me to be here. I am so grateful to all the women who surely experienced much worse than I have well before I entered this field, and never gave up. Their experiences, guidance and support are so incredibly valuable and need to be highlighted. I hope I can encourage and inspire other women the way they have encouraged me.
There are two occasions in my career that I made lateral moves to different teams and areas in security so that I could broaden my experience. One, when I moved from government to industry . I took a significant pay cut and what most would consider a demotion. I think sometimes people are focused on moving up and overlook opportunities at other levels. In my experience, my moves in directions other than up have all worked out for the best in the long run. Sometimes I do wish I had made the change to industry earlier, but then I realise the experiences I gained before making the move contributed greatly to how I work and accomplish things today. However, there are two notable occasions where I wish I had fought for myself and the recognition I deserved. I wish I had advocated more strongly for myself and my abilities rather than agreeing to passively see how things played out.
“I am actively part of a number of industry associations where I have thankfully met a great group of people in security and fostered strong
working relationships and friendships. It is also a wonderful way to meet other women in security, and naturally creates a strong support network with women around the world. I cannot place enough value and importance on participating in these associations. Participation completely reinforces the focus on building trusted relationships. I have found support from these colleagues in so many ways, and truly appreciate these invaluable connections. The shared experiences and support across the airline industry is indescribable . I have never seen so many people constantly go above and beyond to help each other out. The associations that involve cross-industry members are also critical, as there is no limit to what we can learn from each other.
My aspirations are still in development! I definitely plan to continue my studies . I think I am a lifelong learner and try and take advantage of any learning opportunity. I am naturally a very curious person and try and learn before I act. Career-wise, the security

role I am working towards is to be the first woman to lead Air Canada’s security department.
There are a number of people who stand out as role models and mentors in my career. The ones who stand out the most are t hose who walk the walk and don’t just talk the talk. It is so easy to make promises, give advice and present a version of yourself that you then fail to live and breathe. The easiest way for a leader to lose the confidence of their colleagues is to not follow through on agreements or commitments. My most valuable and memorable supporters and mentors are the ones who have truly listened, given clear and tangible advice on how to tackle an issue or implement a strategy, and supported me throughout the entire experience. Being reliable and consistent and having strong integrity is so important to me. I hope that throughout my career in security that is the type of colleague and leader I am for others.
www.linkedin.com/in/bianca-colatruglio-647148181
Sanne Maasakkers is a 31-year-old security researcher and ethical hacker working at the Dutch National Cyber Security Centre, a division of the Dutch Government Ministry of Justice and Security.

Her work primarily involves identifying new hacking techniques employed by adversaries in order to bolster the resilience of the Dutch Government and critical infrastructure. Prior to her current role she worked as a penetration tester (red teamer) in a private organisation. However, her desire to contribute more to society drove her to shift gear and join the public sector, a decision she says she found rewarding because of the intriguing nature of the work and colleagues with shared motivations.
“Every day at my job brings a new set of challenges,” Maasakkers says. “Aside from my weekly research projects on malware analysis, CTI and vulnerability research, I also play a role as a technical advisor during major incidents, carrying out analyses to present a situational overview of unfolding events.
She traces her interest in IT and programming to when, at age 11, her parents brought home the family’s first PC. “This newfound interest coincided with the rise of platforms like CU2 and MySpace, where I learnt to customise profiles using HTML, CSS and JavaScript,” she says.
“Eventually, this led me to create a website for teaching other young girls to code and create pixel art: Hello Kitties and Hello Worlds! However, when my website was hacked I took this as an opportunity to enhance my security knowledge by attempting to hack my own website and strengthen its defence mechanisms.”
Studying computer science seemed a logical choice for Maasakkers, and one advocated by her parents, but she opted for industrial engineering. “The IT sector seemed more like a hobby to me, and I was apprehensive about being the only female in the class,” she explains.
“However, six months into the program I realised my mistake and switched to computer science and information science. In the third year I was recruited by a cybersecurity firm for a job related to my studies and after a year and a half I moved on to a traineeship with a well-known cybersecurity organisation in The Netherlands to focus more on pen testing.”
Looking back, she says the best part of her other studies was learning to make IT accessible for everyone, defining risks and understanding where people are most likely to make mistakes in IT systems. “The key competency in hacking, as I see it, is the ability to put yourself in someone else’s shoes,
coupled with dedication and creativity, because IT systems and processes are human creations.”
As Maasakkers progressed in her career she found herself driven to give back to society: she created a platform to teach children aged 8+ about ethical hacking. She also faced significant challenges, including sexism and sexual harassment, leading her to look for organisations with diverse teams.
So, after more than five years working as a pentester at a private company she got a job with the Dutch Government and started working with her new colleagues organising a major cybersecurity crisis exercise where she was responsible for creating a scenario for 2000 participants.
“One of my proudest achievements is coaching Team Europe, the European hacking team participating in the International Cybersecurity Challenge,” she says. “Winning the first edition last year was a truly significant milestone, and I›m eagerly anticipating another win this coming August!

“Given my passion for teaching and coaching the next generation of hackers and cybersecurity experts, my ideal job would involve a balanced combination of these duties and further development of my own technical skills through research on adversaries and vulnerabilities. I hope an increasing number of individuals within the cybersecurity field will dedicate their efforts to empower the new generation, inspiring them to fortify our defences against bad guys and girls. Together, we can build a more resilient future.”
www.linkedin.com/in/sannemaasakkers
Group CISO at Life Healthcare
Venisha Nayagar is the Group CISO for Life Healthcare, a global private healthcare company listed on the Johannesburg Stock Exchange. It provides all aspects of private healthcare services from acute care, mental health, rehabilitation, dialysis and oncology. There are operations of 66 healthcare facilities across southern Africa and includes the International business of Alliance Medical which provides diagnostic imaging services such as PETCTS, ultrasounds, x-rays and MRIS. (It is not connected with Australian company LifeHealthcare).

Nayagar is responsible for all aspects of data protection: the security operations centre, security governance, cybersecurity architecture, business information security and advisory, cyber risk management, threat intelligence, pentesting, and cybersecurity engineering services that govern and protect the global organisation.
Healthcare, she says, is an exciting industry in which to practice cybersecurity because new challenges emerge almost every day. “Some challenges include securing medical networks, securing the builds of
specialist medical equipment, and constantly being on the lookout for attackers looking to compromise patient data through various means.
“Educating our end users on more secure ways of working and behaving is also a keen focus. An attack in the medical and healthcare industry is a matter of life-or-death if we are unable to service patients on time.”
Her day starts by engaging with her team members, following up on any tasks and viewing any new risks and projects that require security design and monitoring.
“My work week ends by reviewing our global threat intelligence/new vulnerabilities and indicators of compromise for the week as well as dealing with progress of the strategic security initiatives per country,” she says.
“My day also involves working with multiple stakeholders: business heads, clinicians, suppliers, IT team functions, marketing, HR and so forth on either advising or designing more secure ways of working
and delivering. I ensure there is also an element of fun, innovation and humour within the teams. Security is sometimes criminalistic and serious, so keeping a positive and motivated workforce is also quite important.”
Her CISO role bring challenges requiring her “being very adaptive, making decisions quickly, being seen as an ethical and trusted advisor, and working at a very fast pace and dealing with crises and adaptive change management.”
As a CISO There have been, Nayagar says, “moments of physical and mental exhaustion, mostly from working close to 48 hours non-stop to recover from cyber-attacks, keeping teams motivated to keep organisations safe, constantly being on high alert and available to respond to any aspect of an attack including when on leave.”
Attracting and retaining talent to build strong teams and bringing them on a journey of a common vision has also been challenging but rewarding and she has been able to do in most organisations, she says.
“A lot of the time most companies do not see the real value of security, so it’s a constant requirement to keep proving the investment, and sometimes acknowledging the silent achievements and revelations made in the background.
“Some of the skills I have found most useful have been the ability to understand digital risk and to almost think like a hacker and a fraudster, and to then create a security system that is relevant for that organisation.
“The ability to influence, understand data and information technology and keep security agile, aligning it with business and digital changes also becomes quite important, as does persuading executives of the importance of cybersecurity in a simple yet meaningful manner.
“Other skills helpful to a CISO are being technically astute, being solution-driven, a clear communicator who can proactively understand the ecosystem of an organisation to prevent data compromises, define a fit for purpose security strategy, being a quick decision maker and being an assertive leader who transforms cultures and people to make them more security aware.”
Nayagar has held the CISO role at Life Healthcare for two and a half years and says she was a CISO in other industries for many years prior to taking on the role.
In addition to years of being a CISO, she also started and ran her own information security and risk management consulting company, Crypt IT, which as female she successfully solely founded in 2018 having worked with diverse large corporates on improving digital and data strategies. Both roles are a long way from her early career aspirations: to become a chartered accountant.
To that end she embarked on a bachelor of commerce (accounting) course when she finished high school, but says, “after being exposed to information technology and programming, which I enjoyed the most out of all other subjects, I pursued postgraduate degrees in commerce with majors in information systems, and was then awarded a scholarship to complete a master’s degree via research in technology.”
She also completed an industrial psychology major in her final year, which she says, “taught me acute insight into working with people, culture and understanding and profiling behaviour over and above the technical education and expertise which has proved immensely valuable as a leader in cyber security.”
It was while working as an auditor to complete her accountancy training and gain her articles that Nayagar discovered cybersecurity. “I enjoyed the IT audit and forensic investigations a lot, which led me
into leading digital risk and technology governance within a large bank in South Africa. And working abroad gave me exposure to insider trading, anti money laundering, financial crime and fraud,” she says.
“The subject of cybersecurity only came onto academic courses after my study time. However, it was growing rapidly and started becoming the ‘cool’ career and the place to be, especially after the explosive growth of internet e-commerce, big data, mobile devices, applications, social media and increased digitisation within almost every industry.
“At that point I decided to pursue a career in cybersecurity and have never looked back. I absolutely love being a cybersecurity professional. I am incredibly passionate about technology and data and how it is the catalyst to transform organisations. Being in a cyber security has given gives me the advantageous opportunity to work across an enterprise, always learning and growing and being creative to find ways of implementing security that are practical and effective and support the vision of an organisation.
“I enjoy the constant pressure the function places on me and the daily learning and solution driving I experience. I also have the privilege of leading a very dynamic team who are equally passionate about what they do and constantly deliver to an excellent standard servicing our patients and employees.”
Nayagar is one of very few female Group CISOs in South Africa and says the gender-based challenges to her career trajectory have been many but have forged her character into “one of resilience and determination through difficult experiences.” The gender challenges have also included experiences with females.
She has a long list of these challenges throughout various stages of her growing career: salary imbalances, exclusion from decisions and networks, preferential treatment of male colleagues, exclusion from job opportunities as a woman, being spoken down to or disrespected, being branded emotional, overconfident or aggressive, being victimised, threatened and harassed while her male counterparts were treated with respect and handed roles without much effort.
“Over time I have seen all too well that a lot of these behaviours stemmed from insecurity, cultural differences and men not having been around assertive female leaders and decision makers,” she says. “I’m a firm believer in teaching people how one would like to be treated and making sure I do not tolerate levels of female victimisation or disrespect towards me or my females’ colleagues within technology as being a female with a career in technology is constantly demanding in multiple ways which needs to be acknowledged to shatter preexisting glass ceilings.”
However, she also acknowledges “the amazing line managers and mentors across the various companies I have worked for that have been instrumental in teaching me how to handle situations, helped grow my career path by supporting and creating new roles, pushing me to achieve more at a higher standard and who have demonstrated fair and transparent leadership empowering female subordinates and helped me become a leader who is authentic.”
Also, Nayagar says: “I have been fortunate to work in organisations that invested aggressively in female talent, which allowed me to take on roles that included governance, digital strategies, information technology management, security operations,
technology compliance, privacy, and engineering. The depth of exposure has contributed immensely to my professional work ethic, and I am quite confident I can take on any role now and make it a success.

“I am an independent technical advisor to some government boards and gain a sense of personal gratification in helping the public sector with security and technology management. I am also a mentor to females wanting to grow in the cybersecurity and technology fraternity and I am a member of women in tech committees winning multiple awards as well as a speaker in various conferences and tertiary institutions, educating people and students on the importance of information security and the role of a CISO as a career aspiration.”
For her own career growth, Nayagar says she would like to “explore roles and functions surrounding digitisation, robotics, data and AI as these topics are
very closely linked to cybersecurity and influence how adaptable we are to changing data models, scaling organisations, uses and transactions.
“The influence technology advancement has on cybersecurity is vast. There are more unknown ways to manipulate data, deceive employees, generate algorithms through robotic automation and stretch the ability to effectively layer security controls without stalling business innovation.
“I study and read a lot on technology and leadership advancements including multi bio technologies, quantum data models, AI innovation and security and plan to study advanced courses on managing these concepts within organisations to increase my technical leadership acumen.”
www.linkedin.com/in/venisha-n-89314239
Growing up in Israel, Tal Kollender became a tomboy because her mother was out at work most days and her father out in the evenings working as an investigator. There were few girls her age living nearby, so Kollender was left on her own much of the time to hang out with her brother and the neighbourhood boys, outdoors playing ball. She quickly realised that Barbie’s and Polly Pocket dolls were not for her.
When she was 11 years old Kollender was given her first computer. The internet and online games were just starting to gain traction. She was intrigued, and very quickly learnt how to cheat at games. She greatly enjoyed competing and winning.
There was one particular game she had mastered and in which she always came out on top. But after one long night of play she awoke the next morning only two hours later to find someone had beaten her top score. She concluded the only way they could have done this in two hours was by cheating.
To figure out how this had been achieved she became a hacker at age 14. She did not at the time see this as
hacking; to her it was simply playing with the game’s scoring system and its database.
Over time she learnt to hack many online games and saved herself many hours of playing hard. She became driven by how easy it was that she didn’t need to invest as much time to play over and over again winning items. This was in the days before Google and explanatory videos made such hacks easily accessible: hers were all self-taught from scratch. She became the Robin Hood of her neighbourhood, handing out her winnings.
At 16, no one looked at her as someone serious so she decided to prove to them that they needed her product by showing them how easy it was to hack into their accounts.
A few years later when Kollender had been called up for her mandatory Israeli Defence Force service she entered pilot training but failed. However her superiors recognised her potential and assigned her to the intelligence service, which obliged her to mend her ways in order to gain security clearance and serve her country. She changed from being a

Black Hat hacker to a White Hat hacker and learnt to use her knowledge to create programs and develop technologies. The experience transformed Kollender into the person she is today.
After leaving the Army she got a job with Dell EMC in cybersecurity and continued to use her newlyacquired talents. She worked there for five years before leaving to start her own company, Gytpol There was no program to do what she wanted to do and it was a lot of manual effort, therefor she used her own skills to try to automate it.
Often the first she would know about problems with a product were complaints from users. She would approach the vendor and other sources in search of a solution, often to be told none existed.
With her feisty attitude she decided to find her own solution and started to write her own code on a napkin in a café in Tel-Aviv. She shared her work with a good friend, Tal Catran, a technology innovation expert. He believed in her, supported her and opened doors for her.
She needed finance to turn her ideas into a commercial product and found Gilad Raz. He liked the idea and brought on Yakov Kogan. The pair decided to partner with Kollender. The three cofounded Gytpol with Kollender becoming CEO, Raz CTO and Kogan VP R&D. They began working on the first prototype of their product, also called Gytpol, which was released in November 2017.
Gytpol continuously detects and automatically and transparently Remediates device Endpoint Security Gaps caused by misconfigurations. As at September 2022 over three million licences had been sold.
Writing on her LinkedIn page, Kollender says: “We created Gytpol to change the way organisations
protect themselves from a cyberattack by seeing their network like a hacker. Because a hacker trusts no-one, Gytpol created its own zero trust policy to enable organisations to eliminate the risk before it becomes a real threat.”
Kollender has been awarded the 2023 Cybersecurity Women Entrepreneur of the Year from the United Cybersecurity Alliance. This recognition reflects the collective commitment to innovation and excellence Kollender has in the world of cybersecurity.
In her journey the people who have been most important in Kollender’s career have been: Catran who, she says, helped her become the person she is today, strong enough to fly on her own; her late father who always believed in her and taught her to see obstacles as challenges; and her brother.
She says she loves him deeply; he understands her and is her best supporter, her number one fan.
Kollender says her next big challenge is to open a philanthropic organisation that will provide a “school within hospitals” to help children don’t get to be in school at all and learn because they are in the hospital. So she wants to give them training within the hospitals and is looking for people with teaching credit that know the subject.
www.gytpol.com
www.gytpol.com/video/gytpol-short-demo-4-mins-duration
www.linkedin.com/in/tal-kollender-gytpol
Todaro says she found herself trying to decide what to do next. “I was struggling to find my professional identity after two changes and a break.”
It was there that Todaro found her vocation: HR. “My husband co founded a startup and needed help,” she recalls. “I joined and was exposed to everything from hiring to recruiting to supporting employees, creating the first website, finding the first office, and so on.
Emanuela Todaro is not a cybersecurity professional: she’s a human resources professional working for a cybersecurity company, Yubico, in the Bay Area of San Francisco. It’s the latest in a series of three, widely different careers in which she has held significant roles that were terminated by location changes.

In 1996, she gained a Bachelor of Science in Materials Science and Engineering in Turin and started work in the automotive industry. After two years, her husband got a job with Cisco in Silicon Valley and the couple moved there.
Automotive jobs were hard to come by In The Valley so Todaro went back to university, gained a Master of Science in Materials Science and Engineering from Stanford and was hired by chip maker AMD in “a very technical role.”
However, her new career was short-lived. Two years later, Todaro and her husband moved to London where there is neither a semiconductor nor an automotive industry. “At that point I decided to take a break as I had two very young kids,” she says. Three years later the family moved back to the US where
“It was a great gift to try all those hats on and it provided me the opportunity to realise that my passion was in HR. So I made the switch and never looked back.”
Todaro might have discovered her passion and aptitude for HR serendipitously, but it came as no surprise to her husband. “He was the one, in my engineering years, who kept telling me I’d be really good in HR,” she says. “I think he saw something in me that I did not see at the time.”
However, she has no regrets about having pursued two other careers before discovering her true calling. “While I made a lot of career changes, none were a mistake, and all led me to where I am today. I would not change anything because of what I’ve learnt from every single step of the way. I use these acquired skills every day in my work. Not all careers are linear, and I see detours as enriching, rather than a mistake.”
Her husband’s startup, Embrane, produced software products for the delivery of software defined networking services and was acquired by Cisco, a development that enabled Todaro to further explore her passion for HR.
“I joined Accellion, a company that was in the security space in enterprise file sharing,” she says.
“There I gained a deeper knowledge of HR, and I was encouraged to get HR credentials and education by an experienced VP of HR.
“After a little less than two years at Accellion, I planned to take a few months off, but then Yubico came calling. The company’s founder, Stena Ehrensvard, was so convincing and the opportunity was so appealing that I could not turn it down. It was growing globally and to be part of that was really exciting. I’ve now been with Yubico for six years and couldn’t be happier.”
It was at Yubico that Todaro really embraced cybersecurity. “When I interviewed for my role at Yubico, I was scheduled to spend 20 minutes with the company’s co-founder and CEO. Those 20 minutes lasted more than two hours. Her passion and drive were so contagious.
When she spoke to me about what she was planning to do, what the product could do, and what the impact would be on people, on society, on companies and industry, I knew I wanted to be part of it. For the first time I saw security not as scary, but as an exciting field full of opportunities and something that really makes a difference in people’s lives. That was when I decided this was a company that had a mission I could, and wanted to, align to.
“I love being part of the security industry and never once have I felt like I took a wrong turn. I’m passionate about Yubico’s mission, working to help make the internet safer for everyone.”
Since joining Yubico, Todaro says she has become a huge advocate for security. “Whenever I get a moment to talk about it, especially with people outside of the industry, I really take advantage to make sure they’re protecting themselves, to further the mission of keeping everybody safe online. In fact, before my daughter went to college, I sat down with her and had the ‘security talk’, gave her YubiKeys and made sure she understood the importance of keeping her accounts safe and secure.”
She describes her role at Yubico as overseeing everything related to people: recruiting, human resources and facilities. “This means that from the time we recruit people to the time they join the team (and if they leave, even after), my job is to work with them, help them get acclimatised to the team, and ensure they are working in a productive and friendly environment.
I enjoy helping grow the company and that doesn’t just mean the number of employees. The culture is even more critical: creating an inclusive environment that people love and where they can perform at their best. And, perhaps what I enjoy most is helping people find solutions that work, and keeping them engaged and motivated in the workplace.
I don’t really have a typical day, and this is also what I like about my job. It’s unpredictable and every day is new. Activities could include tasks like strategizing on recruiting, meeting with managers or executives, or discussing how the people team can best support them.”
To be successful in her role, Todaro says “you need to be very process oriented, organised, strategic and able to understand compliance. But at the same time, you need to have very developed soft skills (people management, empathy, etc) and be comfortable with understanding a situation and working in the grey area.
“I like the creativity that comes with working in a space that is not fully defined. I feel people skills and emotional intelligence are also critical for the role. What we do impacts real people, so we need to do it thoughtfully and communicate it clearly.
I want—and need—to keep learning more on all aspects of my role as well as broader company operations, including the area of finance, which is of particular interest to me.
And of course, in my day-to-day role, working with people, I’m continuing to learn. Keeping up to date with everything that is going on with people, HR trends, recruiting, diversity, inclusion and belonging
are all very important aspects to my role. I couldn’t be more excited by this. I don’t think you’re never done learning. It does not end with your graduation.”
Tell us about your current position: What does it entail? What do you enjoy most about it? What are the biggest challenges?
In my role, I oversee everything related to people: recruiting, Human Resources (HR), and facilities. This means that from the time we recruit them to the time they join the team (and if they leave, even after), my job is to work with them, help them get acclimated to the team, and make sure they work in a productive and friendly environment.
I enjoy helping grow the company and that doesn’t just mean the number of employees. The culture is even more critical: creating an inclusive environment that people love and where they can perform at their best. And, perhaps what I enjoy most is helping people find solutions that work, and keeping them engaged and motivated in the workplace.
What does a typical day look like? How long have you held it?
I don’t really have a typical day and this is also what I like about my job. It’s unpredictable and everyday is new. Activities could include tasks like strategizing on recruiting, meeting with managers or executives to discussing how the people team can support them.
At the end of my day I go for a walk or do a more intense workout. What I really enjoy most in my evenings is to cook a nice meal with my husband and eat it together. It is a creative and social moment that also helps to unwind from a busy day.
Give us a quick rundown of your career journey from school to where you are now. Please try to make it complete, even if some parts get only the briefest mention. Tell us how and why you came to make significant transitions.
I graduated in Material Science and Engineering In Turin, Italy and started working in the automotive industry. After two years, my husband got an opportunity with Cisco Systems in Silicon Valley. Living in Silicon Valley, I found it was really hard to find a job with my automotive background. So, I went back to school and pursued a MS in engineering at Stanford- this time with a semiconductor focus. I was then hired by AMD into a very technical role.
After two years, we moved to London where there is no semiconductor or automotive industry and I found myself back to square one. At that point, I decided to take a break as I had two very young kids at the time. After 3 years, we moved back to the US and found myself trying to decide what to do next. I was struggling in finding my professional identity after two changes and a break.
During this same time, my husband co-founded a startup and needed help. I joined and was exposed to everything from hiring to recruiting, to supporting employees, creating the first website, finding the first office and so on.
It was a great gift to try all of these hats on and it provided me the opportunity to realize that my passion was in HR. So I made the switch and never looked back. The startup was acquired and I decided to start looking for another role.
I joined Accellion, a company that was in the security space in enterprise file sharing. There I gained a deeper knowledge of HR and I was encouraged to get HR credentials and education by an experienced VP of HR.
After a few years at Accellion, I planned to take a few months off. But then Yubico came calling. The company’s founder, Stina Ehrensvard, was so convincing and the opportunity was so appealing that I could not turn it down. It was growing globally and to
be part of that was really exciting. I’ve now been with Yubico for six years and couldn’t be happier.
Tell us what courses you took and the formal training you have undertaken at university and elsewhere. What skills do you see as being most important in your current role?
To be successful in this role, you need to be very process oriented, organized, strategic and be able to understand compliance. But at the same time, you need to have very developed soft skills (people management, empathy, etc) and be comfortable with understanding a situation and working in the gray area. I like the creativity that comes with working in a space that is not fully defined.
I feel people skills and emotional intelligence are also critical for the role. What we do impacts real people, so we need to do it thoughtfully and communicate it clearly.
What skills do you plan to further develop, and why? I want - and need- to keep learning more on all aspects of my role as well as broader company operations, including the area of finance, which is of particular interest to me.
And of course, in my day to day, working with people, I’m continuing to learn. Keeping up to date with everything that is going on with people, HR trends, recruiting, diversity, inclusion and belonging, are all very important aspects to my role.
I couldn’t be more excited by this. I don’t think you’re never done learning- it does not end with your graduation.
Tell us about the most pivotal moments in your journey. When did you first realise you wanted to pursue a career in security? When did you first feel that you really were working in security?

When I interviewed for my role at Yubico, I was scheduled to spend 20 minutes with the company’s co-founder and CEO. That 20 minutes lasted more than two hours. Her passion and drive was so contagious. When she spoke to me about what she was planning to do, what the product could do, and what the impact will be on people, on society, on companies and industry, I knew I wanted to be part of it.
For the first time I saw security not as scary, but as an exciting field full of opportunities and that really makes a difference in people’s lives. This is where I decided this is a company that has a mission I could and wanted to align to.
Tell us about the highs and lows. Did you ever feel you had taken a wrong turn and really should not be working in security?
I love being part of the security industry and never once have I felt like I took a wrong turn. I’m passionate about Yubico’s mission, working to help make the internet safer for everyone.
Looking back, were there any career/job changes you regret taking, or ones you wished you had taken, and if so, why?
I have no regrets. While I did a lot of career changes, none were a mistake and all led me to where I am today. I would not change anything because of what I’ve learned from every single step of the way. I use these acquired skills every day in my work. Not all careers are linear and I see detours as enriching, rather than a mistake.
Tell us about the people who have been most important in your career, either as mentors, supporters or simply sources of inspiration. Are there one or two in particular who stand out?
I need to mention my husband first. I had the opportunity to change my path thanks to the experience of working with him, through the amazing adventure to grow a company from ground zero to acquisition. He was also the one, in my engineering years, that kept telling me that I’d be really good in HR. I think he saw something in me that I did not see at the time.
I’m really blessed with a lot of people around me that inspire me everyday. Amongst them, I want to mention my own team. We have a great working relationship, bond and alignment- we sometimes even finish each other’s sentences. It’s truly a dream team dynamic!
Tell us about the ones who represented roadblocks, in whatever way (Stories of sexism and misogyny are, unfortunately, all too common in WHJs - so don’t hold back)
One of the greatest events of my life- having my children- also proved to be a professional challenge. Back then, I had to pause my career because I did not have a good setup to be able to take care of them while still working full time.
Based on these types of experiences that many parents have and feedback from our employees, we know they cherish flexibility in their work schedule and location. At Yubico, we have adopted this philosophy and believe it is critical for parents. It has been a strategic win in being able to recruit talent.
Things are starting to change in the industry and I am looking forward to what the future holds.
Tell us about your involvement in cybersecurity outside your paid employment. What industry associations do you belong to? What value do you get from your involvement? Do you play an active role in the industry, either in these organisations, or perhaps as a mentor?
I’ve become a huge advocate for cybersecurity! Whenever I get a moment to talk about it, with people that are outside of the industry, I really take advantage of that to make sure that they’re protecting themselves to kind of further the mission of keeping everybody safe online. In fact, before my daughter went to college, I sat down with her and had the “security talk”, gave her YubiKeys and made sure she understood the importance of keeping her accounts safe and secure.
With an affordable annual fee, AWSN members will have access to discounts on programs and industry events, the membership Slack space, post or share job opportunities, and receive our monthly and any special edition newsletters


Dasha Díaz founded and runs cybersecurity training company itrainsec from Barcelona. It’s a role far removed, geographically and intellectually, from her education and initial career aspirations. She graduated from the State Moscow Regional University as a linguist and a specialist of multicultural communications, dreaming of a career in public relations.
Her first step to realising this dream was to take on an internal communications role with an insurance company in, hoping this would lead to a job in the PR department. However, marriage and pregnancy disrupted those plans and, returning to the workforce when her son was two years old, Díaz was pushed into a PR role with Kaspersky by a recruiter in an employment agency.
“I had no idea what cybersecurity was. But she convinced me not to give up as she had hired the whole marketing team there, and felt I could make it,” Díaz recalls. “I learnt everything about cybersecurity from zero and my head was exploding with everything I was learning about it during my first years there.
“Learning and understanding different aspect of this area of IT, I started falling in love with it and wanted to learn more every day. The conferences I was organising helped a lot. Creating them, I was getting
more familiar with the community, trends, even jokes and memes! I’d say that around 2013-2014 I finally felt I belonged, and I don’t want to change: this industry is fascinating.”
That was the start of what is now a 14-year career in cybersecurity, which saw Díaz, in 2020 set up and run itrainsec after getting married and moving to Barcelona, which meant she had to leave Kaspersky. She says she made this move despite self-doubt and a lack of ambition, and it was transformative.

“I started looking at myself as a real professional. People started telling me to my face that I did a great job. They introduced me to others saying I was an excellent choice, that they could trust me to fulfil their training needs or conference organising. I had to learn to accept the complements. And it was another step for my personal growth.”
itrainsec, Díaz says, “is a company that connects businesses with cybersecurity experts to teach cybersecurity and protect organisations around the world at the highest level. What we do is organise cybersecurity training and IT and cybersecurity conferences and networking events.”
She was able to get itrainsec off the ground thanks to the network of cybersecurity experts she had built up working for Kaspersky for more than a decade.
“I had to establish relationships with a team made up of guys only. It was pretty challenging to build their trust and respect. But bit by bit, talking, asking questions, becoming friends, diving deep into all things happening in their research, brainstorming on how to present those findings creatively at the conferences, etc was a real learning experience.
“Also, while organising an international cybersecurity conference ‘from zero to hero’ I read hundreds of
abstracts and research papers, which allowed me to learn a lot about cybersecurity as well as how to build some amazing agendas. I am now taking some courses by (ISC)² because I want to dig deeper into the technical side to build up my knowledge about some particular topics.”
Starting itrainsec, Díaz says was “quite scary, stepping into something I had no idea how to build and manage. Being a small business in Europe, and Spain in particular, is a big challenge in terms of the market competitiveness, taxes, administration flow, and of course brand visibility. But, once again, my friends and family supported the whole thing from the beginning, and here I am three years later still running the show.”
She says her networking and relationship building skills are the keys to her success. “Building strong relationships with industry experts, potential clients and partners can lead to valuable collaborations and business opportunities. Networking is also essential for staying updated on the latest cybersecurity trends and innovations. So, generally speaking it’s all about constantly learning something new, never stopping.
“I strive to collaborate with renowned cybersecurity experts and thought leaders to ensure our events feature industry-leading insights and practical knowledge. By maintaining these strong connections with experts we can continuously enhance the quality and relevance of our offerings.
“I’d love to expand my business. My primary aspiration is a focus on continuous learning and on making a positive impact in the cybersecurity community. By fostering a security first mindset throughout our organisation and empowering our clients worldwide with cutting edge knowledge we aim to contribute significantly to the collective effort to create a more secure digital world.
“I do my best together with my team and partners to be proactive in monitoring industry trends, emerging threats and new technologies in order to continually adapt our training programs and conference topics to
address the most pressing security challenges faced by individuals and organisations.”
She adds: “It’s very pleasing to be on your own and plan your day as you want. Yet, when you’re working mostly from home with four kids and a dog you have to be very organised and stick to the schedule. I am still failing with this and overworking a lot, but I know for sure it’s getting better bit by bit in terms life/ work balance.”
Díaz acknowledges the downside to running a small business. “Ask my husband how many times I wanted to give it up,” she says. “But as he’s also in the same industry he was always encouraging me not to drop it (he still does), to move forward, build relationships, talk to people and be visible.
“It’s a tough thing to be everywhere at the same time and take responsibility to provide the best services, experts and training programs, or a conference that will be unique. At the same time you have to be ready for losing tenders, for unstable income, tonnes of paperwork, etc, etc, etc.”
And despite running a startup, Díaz finds time to be involved in the cybersecurity community in Barcelona in multiple ways. “Apart from running my business, I help the Women4Cyber Organisation. I am building a conference with them, and I help to orchestrate the whole project,” she says.
“I am also a part of Barcelona Cybersecurity Community NGO. We talk a lot and I help them to get connected to people interested in supporting them. We have several events planned. I am also a co-director of Cybersecurity Master’s in Harbour Space University. In this role I am building a program as well as bringing experts on board to teach in the university’s campuses in Barcelona and Bangkok.”
www.itrainsec.com
www.linkedin.com/company/itrainsec
www.linkedin.com/in/dasha-diaz






































































































































































































































































































Information Security Lead at KODE Labs
Rina Basholli’s first step into a career in cybersecurity was to gain a bachelor of science from the University of Sheffield’s (UK) international faculty at City College, in Thessaloniki, in Greece. She made a good start, earning the Academic Staff Honorary Award for her “ethos, academic performance, genuine interest, positive and mature attitude towards learning and active engagement in extracurricular activities.
She also served as an ICT consultant for an entrepreneurship intern program, assisting business students with ICT-related enhancements for their dissertation pitch decks and, in her third year, serving as a teaching assistant for the object-oriented programming course, an experience she says enabled her to gain valuable teaching and mentoring skills.
After gaining her bachelor’s degree she took a entrepreneurship bootcamp program, Stratify7, cofounded a company, GetMeHome in which she acted as its CTO, and then won a scholarship to undertake a master’s course in Advanced Software Engineering in Information Security (Digital Forensics).
Basholli was led to this decision by her observations of poor cybersecurity practices during her undergraduate course and her other roles.

“I noticed security was often overlooked or not given the attention it deserved,” she says. “Many solutions and systems were being developed, mainly with the client’s needs in mind but without adequate security measures in place, leaving them vulnerable to potential cyber threats.
“These observations deeply concerned me. Driven by my passion for addressing these vulnerabilities and creating a more secure digital environment, and supported by my mentors, I decided to pursue my postgraduate MSc degree in Advanced Software Engineering with a specific focus on information security.
“This program provided a comprehensive understanding of cybersecurity principles, digital forensics techniques, applied cryptography, attack and defence techniques and mechanisms, and risk management strategies.
“I delved into various aspects of information security further developing my expertise in the field and deepening my commitment to advocating for security first approaches in all aspects of software development and IT operations.”
Concurrent with her studies Basholli started working as an information security consultant, gaining practical experience in compliance domains such as ISO 27001, SOC 2, GDPR, and PCI DSS. She also “took part in hackathons and bug bounties, which helped me further refine my white hacking skills.”
She says her degree course exposed her to the captivating world of cybersecurity and digital forensics, making her realise the profound impact security has on safeguarding critical information and systems. “Understanding the inherent flaws of the internet from its inception, and the lack of security in early-stage development, spurred my desire to contribute and make cyberspace a safer place.”
Basholli then took on the role of Information Security Development Manager at PECB, a Canada-based education certification body with a presence in 150 countries. This role was followed by what Basholli describes as “a significant transition”: to a role as information security specialist with Banka Ekonomike in Kosovo.
“The bank had recently encountered a sophisticated ransomware attack perpetrated by a prominent eCrime banking trojan. My experience and expertise led me to play a pivotal role in helping the organisation navigate through the crisis,” she says.
“As I began my career as an information security consultant, I knew I had found my passion. The moments that solidified my determination were successfully educating breached companies, leading compliance projects, witnessing the tangible benefits of implementing robust security measures, and inspiring others to do the same. These experiences fortified my passion for information security.
“I truly felt like I was working in security when I had the opportunity to take a hands-on approach to implement security measures and guide organisations to adhere to industry best practices and compliance standards. This involvement in addressing diverse security needs and challenges made me feel like an integral part of the cybersecurity white hats of the global cyberspace.”
From Banka Ekonomike Basholli took on her current role as information security lead with KODE Labs, a developer of smart building software headquartered in Detroit. She describes it as “a leadership
opportunity that allows me to have a more substantial impact on the organisation’s cybersecurity initiatives.”
Her role involves implementing a continuous proactive cyber security plan, overseeing the information security controls implementation, cross team collaboration, team education and awareness, researchand lead compliance initiatives of the organisation. “I am at the moment responsible for ensuring our company adheres to various regulations such as ISO 27001, SOC 2, GDPR and PCI DSS, and that we comply and follow with the NIST CSF iterations in the early stages of development. Additionally, I lead and manage compliance probono projects for different companies, develop and implement security policies, and provide guidance and training to teams on best practices in information security.
“What I enjoy most about my position is the opportunity to work with a talented team and the constant challenge of staying up to date with the rapidly evolving cybersecurity landscape. Every day brings new challenges. I’m constantly on the edge, and that keeps my job exciting and fulfilling.
“In my current role, strong leadership and communication skills are vital as I need to guide and educate teams on security practices and compliance requirements effectively. Additionally, technical expertise in information security, cybersecurity, digital forensics and auditing is crucial to excel in predicting possible landscapes our team should focus on to mitigate the emerging threats of our industry.
“A typical day is quite dynamic. It usually starts with reviewing security alerts and incidents and prioritising the tasks for the day, which may include conducting compliance audits, reviewing security policies, providing training sessions to our staff on security best practices, working closely with our DevOps, Management, Dev Team, IT, HR to implement robust security measures and processes in place, collaborating with our clients on their compliance requirements, and researching and implementing new security measures to enhance our overall cybersecurity posture.
“On some less busy days you can find me trying out that new PoC in a VM, doing digital forensics for a GIAC certification, re reading my favourite Kevin Mitnick or Bruce Schneier books and simply catching up on the recent global threat landscape developments.
“Bruce Schneier and Kevin Mitnick have had a profound impact on how I perceive security threats and challenges. Learning from their experiences and insights has been instrumental in shaping my approach to tackling cybersecurity issues.”
And, like any career journey Basholli’s has had its highs and lows. “The highs come from the satisfaction of successfully securing organisations, contributing to the cybersecurity community and seeing my efforts make a positive impact,” she says.
“The lows mostly stem from the challenges that come with working in a rapidly evolving field and having not much time for my friends, family, and loved ones. There have been moments of pressure, particularly when handling complex projects or facing new and sophisticated cyber threats and I would sit for hours to solve the problem losing sense of time. However, these have been valuable learning opportunities that have helped me grow both professionally and personally.
“Despite the occasional challenges, I have never doubted my choice to work in security. The meaningful impact of protecting our society,
organisations and individuals from cyber threats outweighs any temporary frustration.
“Each step has been a learning experience, and even challenges have presented opportunities for growth and development. My career path has been dynamic, and every transition has contributed to my expertise and success in the field of information security.
“Every job change presented unique challenges and opportunities, and through them, I gained new skills, expanded my knowledge, and built a diverse network of professionals in the field. These experiences have shaped me into the professional I am today, and I wouldn’t be where I am without the career choices I made.
“It’s important to remember that every career path is filled with ups and downs, and it’s natural to encounter challenges along the way. What matters most is how we respond to those challenges and how we use them to develop ourselves both personally and professionally.
“I believe that my journey has been purposeful, and I’m grateful for every step that has led me to my current position. My focus now is on continuing to excel in my role and contributing to the growth and development of the cybersecurity industry.”
And Basholli makes contributions aplenty. She is an active member of Women in Cybersecurity (WiCyS) where she has served as a technical advisor and executive board member of its Privacy Law and Policy program and where she is now serving in its mentoring program for women aspiring to cybersecurity careers.
“Being a mentor with WiCyS has been a truly fulfilling experience,” she says. “It has provided me with the opportunity to offer guidance, share insights and provide support to talented individuals from all over the globe seeking to advance their careers in cybersecurity. Witnessing the growth and development of mentees, and
knowing I can contribute to their success brings immense satisfaction.”
Basholli is also active in the Association for Computing Machinery (ACM) and its Council on Women in Computing (ACM-W) which she says has provided her with a broader platform to engage with cybersecurity professionals from diverse backgrounds.
“As both a mentor and an active participant in these organisations, I have gained immeasurable value in terms of professional networking, knowledge-sharing and the satisfaction of making a positive impact on the cybersecurity community. I will continue to play an active role in supporting these associations and promoting diversity and inclusivity within the industry.”
In addition to all this activity, along the way Basholli has found the time to acquire several cybersecurity certifications including ISO/IEC 27001 Lead Audit, ISO/IEC 27001 Lead Implementer, Certified Information Security Manager (CISM), Computer Hacking Forensic Investigator (CHFI), SIEM Enterprise Security Manager (McAfee).
And she says her cybersecurity aspirations are ever evolving. She plans to expand her knowledge in areas such as threat intelligence, cloud security, digital fingerprinting, blockchain security and artificial intelligence in cybersecurity to better address emerging challenges, and gain additional certifications along the way.
She’s carrier of many contribution awards among them: Woman Game Changer for Extraordinary Contribution to the Women Cybersecurity Community of Kosova, she’s a policy contributor of her state, has been shortlisted for the Cybersecurity Woman of the year 2023 from The Cybersecurity Alliance, and is considered as a woman cybersecurity pioneer of Kosova, and currently has been chosen member of the WiCyS Speaker Spotlight Program. She has been part of many cybersecurity panel discussions and interviews. Rina is considered a Woman Cybersecurity Pioneer in her country and unique success story.
Some articles relevant:
1. Kosovo Women Leaving Their Mark in ICT
2. Best Practices for Easing Security Concerns Around Smart HVAC
3. Public-Private partnership ramps up national cyber security
One of her main goals is to secure a PhD scholarship at a renowned university and to bring WiCyS to the Balkans. “By pursuing a doctorate in cybersecurity I aim to deepen my expertise and contribute to the academic community through ground-breaking research and advancements in the field,” she says. “While being part of WiCyS for so long has inspired me to bring the amazing spirit of Women in CyberSecurity (WiCyS) in the Balkan area and enhance cross-collaboration between balkan cyber women.”
“The expected developments in the cybersecurity landscape are undoubtedly going to impact my current role. With the rise of emerging technologies such as AI and the increasing reliance on cloud services, the challenges to ensuring information security will become more complex. Therefore, staying adaptable and continuously updating our strategies will be essential to address these new threats effectively. My aim is to proactively tackle these challenges and provide valuable insights to organisations, enabling them to stay resilient in the face of evolving cyber risks.”
And Basholli envisages taking on more significant leadership positions, contributing to policy development, shaping nationwide cyber defence strategies, playing an active role in shaping cybersecurity practices on a global scale, and “to continue being a catalyst for positive change in the industry and to inspire others—especially women—to pursue rewarding careers in cybersecurity.”
www.linkedin.com/in/rina-basholli

Suzanna Alsayed describes her current role as CEO of Evolutz, a Toronto-based branding, marketing, copywriting, SEO optimisation and website development company she founded in 2020. She says: “I am a lifestyle writer, world traveller, content creator and polyglot,” who is “working on a self help book scheduled for publication at the end of 2023.”
But that’s not the half of it. According to her LinkedIn profile, she has five other current roles. She is also: the founder of the Evolutz Academy, which “provides affordable academic and professional resources to a broad demographic;” a freelance content creator for US News & World Report; cofounder and creative director of Forward Unlimited “a collaborative platform that creates educational and purposeful videos to bring awareness to the security and executive protection industry;” founder of Hilt International Security “a holistic security and emergency management firm” and holds multiple volunteer roles with ASIS International “the world’s largest association for security professionals.”
No surprise then that Alsayed says, “I often wish I could clone myself because there never seems to be enough time in a day to accomplish everything I want to do.” She says she meticulously plans her days, weeks, and months well in advance, sometimes
down to the hour, to ensure she can accomplish all necessary tasks.
“A typical day for me starts with a coffee and breakfast, usually around 9 am or 10 am, as I’m not much of a morning person. Afterward, I refer to my organiser, which already contains a prioritised list of tasks. This allows me to stay focused throughout the day.”
On Sundays, she devotes time to organising the week ahead. “I use a notepad that helps me structure each day with a ‘week at a glance’ overview. Next, I prioritise these tasks based on their importance and the specific day they should be accomplished. To add clarity, I colour-code them and, when needed, delegate specific tasks to my steadfast Evolutz team members.”
No surprise that Alsayed admits, “Sometimes, things can get overwhelming, and I might briefly lose focus.” At such times she quickly reminds herself of the importance of caring for herself. “I am the primary resource behind my business. This internal competition with myself keeps me striving to do better and protect my well-being amidst the demanding challenges of entrepreneurship.
“In entrepreneurship, drawing a clear line between personal and professional life is challenging because they often intertwine. Embracing this reality and finding ways to harmonise both aspects while continuously making minor improvements is the key to initiating and sustaining success. It’s important to remember that success is subjective and varies from one individual to another. By recognising this, we can define our own measure of success and work towards achieving it, embracing the journey along the way.”
Alsayed is somewhat reticent to detail her life journey, saying: “I invite you to delve into the pages of my upcoming book, which will be published in a few months. It encapsulates my life’s journey and the chapters that have led me to where I am today.”
However, she provides some tantalising snippets. “My journey to where I am today is an amalgamation of various factors, including my involvement in professional sports, my time in the Russian circus, my passion for academia and the valuable personal life experiences I’ve encountered. All this knowledge has instilled a deep sense of discipline, which has played a pivotal role in shaping the person I am today.”
Her passion for academia is evident from the number of degrees she holds: a masters in disaster and emergency management, a bilingual honours bachelor of arts in international studies, and a bilingual bachelor of arts in political science from York University (Canada, not the University of York in the UK); a certificate of bilingualism (French/English) from Glendon College, York University. And she is about to start studying for a Ph.D. at York University’s Faculty of Graduate Studies.
Throughout her studies, Alsayed also worked fulltime. “I took on various roles, starting in retail, then progressing to become an executive assistant to the CEO,” she says. “I even worked as a flight attendant before delving into several internships within the emergency management field to acquire relevant experience.
“When I graduated six years later with three degrees, I had amassed over five years of valuable corporate experience. This combination of education and hands on work in different fields gave me a strong foundation, preparing me for my next life phase.”
The security and cybersecurity phase of Alsayed’s life started, of all places, in a Starbucks café through a chance encounter with a stranger. At the time, she was finishing her second degree in international
studies and contemplating pursuing a master’s in global politics or becoming an international lawyer.
“During our conversation, the stranger observed that my personality and cultural exposure were well-suited for security and risk management,” she recalls. “This serendipitous encounter led me to find my true calling in security.
“This served as a powerful reminder of the significance of remaining open to new opportunities and chance encounters. You never know how a single moment can completely alter your life or career trajectory. Embracing the unexpected can lead to unforeseen paths and remarkable transformations, enriching your journey in ways you might have never imagined.”
The stranger recommended Alsayed explore the master’s program at York University, join ASIS International and look into their young professionals programs. “Intrigued by his words of wisdom, I decided to follow his advice,” she says. “As I embarked on this new path, I joined the master’s program and became a part of ASIS.
“I consider myself part of the ‘new trend’ of individuals who entered the security industry through academia. Traditionally, professionals transitioned into security from backgrounds in law enforcement, investigations, and the military or stumbled upon it by chance.”
Joining ASIS in 2017, Alsayed says, marked her official entry into the security field. “Becoming involved with ASIS International allowed me to be part of the group that contributed to developing the Associate Protection Professional (APP) Certification. This experience solidified my passion for the security industry and set me on a dedicated path to further grow and contribute to this dynamic field.”
Her founding of Hilt International Security Inc. in 2019 and Evolutz Inc. in 2020 marked her debut as an entrepreneur, and she says she has never looked back. “What I find truly rewarding about this journey
is the freedom, creativity and discipline it brings. To succeed, one must remain consistently accountable and act as a self-motivator daily. Contrary to what social media may portray, overnight success is exceedingly rare. It’s a day-to-day endeavour that can take a fair toll on you. It’s a constant juggling act, wearing multiple hats to make a genuine impact in the market you aim to excel in.
“My success as an entrepreneur and individual relies heavily on organisation and accountability. It’s what has shaped me into the person I am today. Balancing my responsibilities as a business owner, building a family, maintaining a social life, travelling, working on internal and external projects and prioritising my mental and physical well-being is not easy, but still achievable.
“One of the perks of being an entrepreneur is the flexibility it grants me. I can work from anywhere worldwide and make the most of it. Whether in Europe, the USA, the Middle East, Canada, or even from the comfort of my home or a coffee shop, I diversify my work locations to keep things exciting.
“Recently, I’ve enjoyed working from various places, like Istanbul (Turkey), Saint-Tropez (France), and my all-time favourite spot, Edinburgh (Scotland). This lifestyle of exploring new destinations while continuing to work on my business is truly one of the joys in my life.
“I consider myself an ‘international butterfly’ because I can fluently speak three languages and comprehend approximately seven to nine other different languages. Working as a flight attendant during my university years allowed me to travel to various international destinations, which ignited my passion for diverse cultures.”
Like most women in security and cybersecurity, Alsayed has been in a minority but says this has never troubled her. “I’ve never really struggled with being the only woman in the room, perhaps because I grew accustomed to being ‘judged’ in professional sports.
As a former professional athlete, I was used to having a panel of 10-25 judges scrutinising my every move and scorecard during performances. This experience has given me an advantage in being the only woman in certain environments. It is an opportunity to confidently state my opinions and provide a unique perspective.
“Navigating the security industry as a woman and minority has brought unique encounters. However, I have tackled these obstacles head-on by actively networking and fostering a solid support system that believes in my mission, business acumen, and skills. This unwavering support from both men and women has allowed me to thrive and rapidly grow in an industry I have come to love.”
Regarding support, Alsayed seems to have menteeship down to a fine art. “I have different mentors for different aspects of my life,” she says. “I have a mentor for my financial and investing needs, another for my relationships, one who serves as a confident sounding board, and another for my business ventures. This diverse range of mentors provides valuable insights and support in various areas, helping me navigate challenges and opportunities.
“I always preferred to seek various mentors throughout my life instead of sticking with one specific person. Since I was six years old, I have had between five and eight mentors in multiple areas, and I would rotate them every one to two years. By ‘rotating’ mentors, I mean there comes a point when a mentor becomes a friend, and they might become biased in their guidance, or I may outgrow their mentorship. It is a normal and healthy practice and keeps you grounded when making minor to lifechanging decisions in your life.”
Along her career journey, Alsayed has collected numerous awards. These include: Security Industry Innovator Award from Security Business Magazine in 2023; being listed among the ‘Top 40 under 40’ by Security Systems News in 2022; being honoured as
one of York University’s ‘Top 30 Alumni under 30’ in 2022; being acknowledged as an emerging leader in the security industry through the Canadian Security Emerging Leader Award in 2021; being named a top influencer by the International Security Journal from 2020 to 2023; ranked second on IFSEC’s Global Influencers List in 2020.

Summing up her attitude to life, Alsayed says one of her defining features is that she has no regrets. “I make sure to pursue everything I desire, even when fear tries to hold me back. Some moments overwhelm me, and inside I might feel a mix of emotions because I’m hesitant to take on particular challenges. However, despite the fright, I face those tests head-on and take action.
“I firmly believe that stepping outside my comfort zone daily is crucial for personal growth and selfimprovement. Embracing discomfort and confronting
fears allows me to continually evolve and reach new levels of personal development. I am convinced that by pushing through fear and pursuing what I truly want, I can become the person I aspire to be and lead a fulfilling life.
“My nature as an ardent overachiever and competitor propels me forward, guided by the belief that our actions and efforts shape our destinies. I try to remain resilient when faced with closed doors, knowing that another opportunity will arise or I will summon the determination to build a new one. I firmly believe that for every problem, there is a solution, and our mindset and actions govern how we approach and conquer adversities. Embracing this perspective has empowered me to confront challenges with a tenacious spirit and succeed even in adversity.”
www.linkedin.com/in/suzannaalsayed
Hearing your dreams derided as fleeting or trivial can be disheartening. That was Vanessa Henri’s experience when she set out to pursue a PhD at the confluence of law and cybersecurity. This at a time when the news cycle was dominated by Edward Snowden’s revelations of mass surveillance, Julian Assange’s disruptive WikiLeaks and allegations against Chelsea Manning.
“The notion of cultivating a professional niche at the nexus of law and technology was widely regarded as imprudent,” Henri says. “Without any precedents in postgraduate legal academia or mentors to guide me, my project plan was met with consecutive refusals.”
Nevertheless, she persisted in the face of repeated rejections, describing the experience as an invaluable lesson in tenacity. “I believed the legal profession had much to gain from applying law at the product level, where code effectively serves as law. I struggled to forge a voice in the budding field of technology law without established methodologies or recognised expertise, navigating an archaic legal landscape resistant to change.”
As Henri struggled to navigate the legal professionshe was recommended to pursue family law, because “there’s no future in cybersecurity.” Nevertheless, she seized an opportunity to work at one of Quebec’s pioneering cybersecurity startups. “Without a clear role or title,” she says.

“I began developing proposals for cybersecurity services. As I asked questions and learnt from industry experts, I was able to apply my legal acumen.” This, enabled her to identify the need for a multidisciplinary approach to reveal insights into the interactions between what were at the time diverse disciplines.
“It was then, that I realised I needed to formalise my legal credentials. Studying for the bar was challenging; I had no sponsorship, a family to care for, and a career to put on hold. I had to revisit foundational law principles that my real-world experience had shown to be obsolete. My first attempt was unsuccessful, but my resilience paid off on the second try.”
She secured an equivalency in France, joined a leading Canadian law firm, and “ (I) was privileged to work with startups navigating the legal intricacies of emerging technologies like artificial intelligence.”
Henri says straddling the line between tradition and innovation can be challenging. “Technology is a rapidly evolving field, and requires self directed learning to keep abreast of developments, in contrast to the legal profession which favours a more structured approach. However, my selftaught proficiency conferred a distinct advantage. I gained extensive legal expertise but also recognised its limitations.”
She says her journey was anything but smooth: arcane traditions, scepticism and frustration were commonplace. “But each setback became a steppingstone towards a novel business model. My entrepreneurial family had instilled in me the ability to transform abstract ideas into viable businesses.
I saw junior lawyers struggling to grow, and I knew that interfacing with technologists was the key to broadening legal perspectives.
“I also realised that cybersecurity demands diversity. Individual voices matter. By blending two disciplines I found my unique voice, which helped dismantle institutional silos. Today, cybersecurity law, once a nascent field, is a well established concept. I am privileged to serve on Quebec’s Ministry of Cybersecurity’s cybersecurity and digital committee.”
Henri the went on to found Henri & Wolf, a boutique law firm dedicated to resolving complex technology, data security and governance legal issues, based in Montreal.
She describes the firm as “a multidisciplinary community founded by an engineer and a lawyer,” and a natural progression of her journey. “We believe our combined insights lead to better solutions. Today, our community comprises lawyers, engineers, project managers, ethical hackers and governance experts, all bringing unique expertise to the table.”
Henri says her entrepreneurial endeavours garnered numerous accolades but did not guarantee success. “Over time, I pursued specific certifications and continuous training to broaden my horizons, striving to be a cybersecurity expert with legal proficiency. I faced scepticism and was typecast as a cyber insurance expert at panels, but over time I achieved recognition, being named one of the Top 20 Women in Cybersecurity by IT World Canada and a global influencer by IFSEC. These honours provided opportunities for further outreach and inspiration for those considering a career in this field.”
Looking back on her career, Henri’s advice to others seeking similar is: “Be authentic. Maintain your mental health and balance your life amidst the rapid evolution of the field. As essential as technical and legal expertise are, don’t neglect the importance of mental wellbeing. In the balance of life, friendships, love and career are the three pillars: neglect none for the growth of others. They complement and shape you into a well rounded person.”
To young women aspiring to a career in cybersecurity, she says: “Your unique perspective can fuel change and innovation. Certifications, degrees and internships matter, but they’re not the be-all and end-all. Embrace unconventional learning experiences outside the typical academic or professional environment.
“Remember, your career journey is a communal one, built on fostering relationships, learning from mentors and discovering your voice. It’s about challenging norms and pushing boundaries. It’s a worthwhile endeavour, and every step, no matter how tiny, moves you closer to your goal.”Jana Dekanovska Strategic Threat Advisor ANZ at CrowdStrike
would see very different statistics emerging. That is what I hope to see in the next generation entering the workforce.
How can companies empower women at all levels including junior and senior levels?
The recent RMIT Centre for Cyber Security Research and Innovation (CCSRI) report has highlighted the stark underrepresentation of women in the cybersecurity workforce. In simple terms, why do you think this is the case?
Women make up around a quarter of Australia’s technology workforce and many assume cybersecurity jobs are not for them. To combat this, it is important we foster a culture that encourages female leaders to be more visible and that helps ambitious women progress to the highest levels in their chosen fields.
The lack of female representation in STEM is the result of two fundamental factors: culture and confidence. I grew up in a post communist society in Czechoslovakia where, during 40 years of communist rule, it was mandatory for everybody to work regardless of whether they were male or female. It never occurred to me there would be any limitations to my career opportunities because of my gender.
I was fortunate to have many role models, including my mother who was a computer scientist, and to grow up in a society where women were confident they could pursue any career choice. These factors definitely impacted me. If we could instil a similar attitude and give girls in Australia the confidence to pursue their professional and personal dreams, we

Companies need to demonstrate by their actions that they are inclusive: mere statements aren’t enough. They need to offer equitable pay structures and career development opportunities as well as a flexible work environment. It was only after becoming a mother that I realised the importance of flexible working conditions. Being a working mother is extremely challenging, physically and mentally. And while there is little employers can do to help raise our children, creating a culture of flexibility and reminding working mothers (and fathers) it is okay not to turn the camera on in a videoconference at 8:00am (because we have not had time to brush our hair), or to say no to a 5:30pm meeting (because it is day care pick up time) does much to reduce the stress of balancing work and home duties.
Working in a supportive environment where your team trusts you to get the work done—if not at 3:00pm, then at 9:00pm when the baby is asleep—is important. This makes a real difference in stress management and builds a connection with employees based on trust, respect and a mutual understanding that everyone has commitments and lives outside of work. CrowdStrike is a flexibility leader in that it does not have a physical office: all employees are trusted to work from wherever suits them.
How can companies mentor women and partner with industry bodies to provide additional support?
While some mentorship programs are beneficial, I feel some of these programs reinforce the misconception that, because of their gender, women need ‘extra help’. Much still needs to be done to address bias in hiring and promotion decisions, but, ideally, we would
remove gender from the mentoring equation and focus instead on how to get more senior staff helping those at junior levels. Talent, passion and ambition have nothing to do with gender.
What roles do the government and media play in retaining women in the technology workforce, and are there other organisations, schools or recruitment agencies that can contribute to increasing representation?
The gender gap in technology appears in early childhood. I remember very clearly the lessons my female role models taught me that were particularly impactful in high school when I was deciding on my early career path. School age children need to see more female cybersecurity role models in the media. The government must continue to invest in early education to attract more girls and young women to study STEM subjects and help ignite their passion for technology. This can be achieved through greater funding for education and through collaborative partnerships with organisations like SheCodes—which offers online coding workshops for women—the Australian Women in Security Awards, schools, universities and other tertiary institutes.
CrowdStrike was recently named as one of the best places to work by Glassdoor and one of 100 best places to work by Fortune. What is it about the culture of the company that makes it a great workplace for women?
CrowdStrike has given me the opportunity to take my career to new heights. My current role allows me to coach executives and board members to better understand cyber threats and how threat intelligence can be used to inform their business decision-making, risk management and company profile. Nobody at CrowdStrike has ever questioned my ability on the basis of my age, gender, or nationality. The support and encouragement I have received from day one, from colleagues all the way up to our vice president, has been incredible. I love sharing my insights, encouraging the next generation of cybersecurity professionals and working towards bridging the skills gap to engage more women in the field.
What would you say to prospective employees who do not have a background in technology or cybersecurity and are interested in joining?
I would encourage anyone who, like me, comes from a non-technical background and who is interested in exploring an exciting new career to enter the cybersecurity profession. There are countless nontechnical avenues to explore, including marketing, sales, HR and legal. Any of these can be a great starting point and you can pivot later in your career. I would recommend taking extra courses, studying the latest threat intelligence and making contacts in the industry. You can never be good enough in your craft—there is always room for improvement.
What advice would you give to help others with their career transition?
I live my life by a very simple philosophy: we are not on this Earth for very long. Overthinking things, waiting until you are perfect, thinking you are not good enough—these are all things we simply do not have time for. Flow like water and see where it takes you. Be curious about what you will find, and say yes to every new opportunity. I began my career in diplomacy, somehow found myself working in broadcast journalism, was thrown into crisis management and intelligence, and ended up working in cybersecurity. Being flexible and willing to try new things will uncover opportunities you may never have considered.
What advice would you give to women studying technology at a tertiary level who want to enter the cybersecurity industry?
I would encourage students studying for a degree to intern as early as possible. Gaining early exposure and work experience will give you a significant advantage by building your hard skills, as well as your influence and your networks.
www.linkedin.com/in/janadeka
The cybersecurity industry is simultaneously one of the most amazing and one of the toughest industries in which to work. It can give you complex problems to solve, never ending learning and a never ending workload. I love the industry (although after reading that first sentence you might not think so) but it certainly has its issues.
Firstly, we make the industry really hard to get into. We ask new entrants to have years of experience for an entry level job, which basically means, most of the time, there are no true entry level jobs. We should call the positions what they are: junior mid-level, or something similar. Do not describe a role as entry level if it is not. That just complicates things for everyone, and makes it more frustrating for those looking for a way through the outer perimeter of the cybersecurity industry to join us in the fight to protect what we all hold dear.
Secondly, now we agree that we basically have no entry level positions, we need to create some. We need to go back to providing people with traineeships or apprenticeships in cybersecurity. We need to bring them in from school or after they have gained a university or TAFE qualification and give them hands on work experience.

These new entrants will need to accept that they will not be paid well. They cannot expect businesses
to invest time and effort into training them for, potentially, 12-18 months with no return and still pay them $100k a year. This is not feasible.
Thirdly, we need to work together more. Each of us is fighting alone and trying to defend our organisation when we should be more unified. We should form an alliance to share intelligence and advice more openly and help keep us all safer. I know some things cannot be shared and we cannot all have defence grade security protections for our business, but that does not mean we should not try to make things a little easier for each other.
Fourthly, diversity is key. Why are we not better embracing this? Bringing in people who differ in any way would be good. They will approach problems in different ways. Together we will all find new ways to solve our issues.
Cyber Enthusiast, Ethical Hacker, Author of A hacker I am vol1 & vol2, Male Champion of Change, Special Recognition award winner at 2021 Australian Women in Security AwardsWhat we have been doing is not working very well. We need new ideas, new approaches. We need to break away from the old stereotypical male tech image. We have no choice but to change. We need more women to join us in the industry. We also need more men.
If we do not embrace a more diverse cybersecurity workforce, we will never evolve. In 10 years we will still be doing things the same way, wondering why that way is not working, and why we continue to lose.
So, let’s recap. We need to bring more people from different backgrounds and experiences into cybersecurity so we can solve the issues facing the industry and society. To do this we need to find a way to create true entry level positions, and fill them.
We need to reset the remuneration expectations of entry level people to make it fair for organisations that put the effort into enabling people to get a foothold in cybersecurity, and fair to those new entrants as well.
If we can do all of this and work together a little better, we might just ease the workload of people in the industry. They will have more support and will be available to train new people. We will gain diversity and improve the gender balance. We can do it. I know we can. We just need to think a little differently.

www.linkedin.com/in/craig-ford-cybersecurity
www.amazon.com/Craig-Ford/e/B07XNMMV8R
www.facebook.com/AHackerIam
twitter.com/CraigFord_Cyber



That was until he found himself the only male in a room full of women at a monthly networking event for the firm’s newly formed Women in IT group. He began having more direct conversations with many of his female colleagues and realised “there were a bunch of things happening that had largely been invisible to me,” he recounted during a recent webinar

“I thought I was empathetic with my team, that I listened to them, and that I understood their concerns and their issues. But I didn’t realise some of the things that were going on, and therefore I realised I was part of the problem: unless I changed the way we did stuff, some of these issues would never change.”
It was an epiphany for the career manager who began working with his colleagues to drive a fundamental shift in the dynamics of the teams he was managing.
These initiatives included forming groups of male allies in conjunction with female colleagues and running workshops for the men, driven by feedback from their female co-workers.
“It was apparent to me that there were not enough men in this conversation, and there were plenty of them that needed to have it,” Ford recalled.
“The main thing we tried was to capture the female experience: the things women were telling us about what men were saying to them and what men were doing that were making them feel really uncomfortable. We translated that into a workshop, not to make them feel guilty but, more importantly, to begin to say, ‘what can we do about this?’.”
Over the next four or five years the program Ford started was taken up by the whole of JP Morgan—300,000 or so workers around the world—
As a manager with the Bournemouth, UK office of financial services firm JP Morgan, Gary Ford believed he was a “relatively half decent manager or leader” who engaged meaningfully with his 250 reports spread across six or seven countries.
and this success ultimately motivated him to branch out and establish the diversity-focused to help other organisations learn how to strengthen their allyship capabilities.
Partnerships with organisations such as Women on the Wharf and Male Allies for Gender Equality (MAGE) have strengthened Moonshot’s reach and influence, as has its involvement with collaborative efforts such as the 4i Forum and the annual Women’s SatNav to Success survey.
As Ford quickly realised, engagement is key to allyship, as is the all too rare unflinching introspection that helped Ford realise things needed to change within his reporting group.
Yet, while men who make a genuine effort to become allies for their female co-workers often come to realise the shortcomings of the existing environment, far too many men are going about their day-to-day business believing that simply wanting to be allies is enough; or, worse still, believing the problem to be already fixed.
A recent research study by the Integrating Women Leaders Foundation (IWL), the 2022 State of AllyshipIn-Action Benchmark Study, surveyed 1150 Fortune 500 executives and found that good intentions were often as far as many men went when it came to becoming real allies in the workplace.


While 77 percent of male executives believed most men in their organisation were either ‘active allies’ or ‘public advocates’ for gender equity, just 45 percent of women said the same.
The disparity at lower management tiers was even more pronounced, with 67 percent of male middle managers agreeing with the statement versus 36 percent of women. Only 28 percent of women in lower management roles agreed that men were pro-equity.
Women were far more likely than men to report seeing women treated in biased ways. For example, 36 percent of women said they had seen a woman overlooked for a promotion or stretch assignment, compared to just six percent of men.
And while 46 percent of women said they had seen women being interrupted or spoken over more often than others, just 10 percent of men reported seeing the same behaviour.
This suggests many men simply are not attuned to the behaviours that women perceive to be threatening or diminishing; a conclusion reinforced by a dramatic jump in awareness among men who had participated in allyship communities.
Whereas a third of white women and 39 percent of women of colour said they had seen women’s judgement questioned in their area of expertise, only nine percent of non-participant men said the same.
For men who had been involved with allyship communities that figure jumped to 27 percent, confirming men are quite capable of spotting inequality once they know what to look for.
Participation in allyship communities also made men far more likely than other men to notice women being interrupted or spoken over more often than others (29 percent versus 10 percent), women not being given credit for contributions made (18 percent versus eight percent), being questioned on their emotional state (13 percent versus five percent), and being expected to speak on behalf of all people with their ethnicity (16 percent versus four percent).
However, despite the figures pointing to a clear link between allyship initiatives and better treatment of women in the workplace, most men have not participated in such programs: less than half of survey respondents said their companies offered allyship training, and only 22 percent of respondents had undertaken it.
Participation in allyship communities was even lower, with just a third of employees aware of such communities and 12 percent participating in them.
If men are nowhere near as good at being allies as they perceive themselves to be, how can this entrenched ignorance about anti-women behaviour be dispelled? How can men be encouraged to become more proactive about engaging with their female peers?
Allied Collective founder and lead facilitator, Ruhee Meghani, suggests fostering empathy is a good starting point.
“Allyship is not a label or identity, but rather a continual process of learning and growth,” she said during a recent AWSN webinar. “When you go on LinkedIn and say you’re an ally, what does it mean? Back it up with action, rather than simply expressing sympathy or stating support.”
CREDIT: Harvard Business Review] https://hbr.org/resources/ images/article_assets/2022/10/W220926_SMITH_ALLYSHIP_ BIASED_EXPERIENCES_360-1200x3610.png
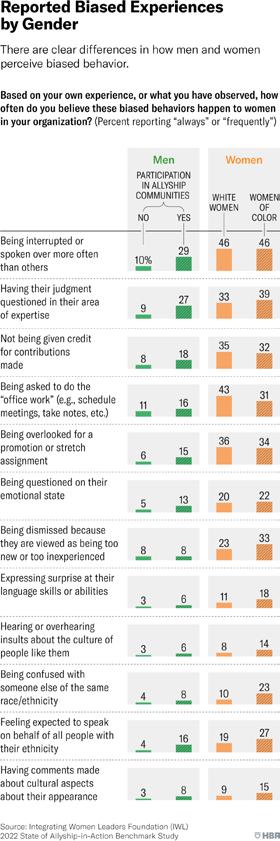

According to Meghani, “Effective allyship involves a little bit of egolessness: centring on the experiences and perspectives of marginalised groups rather than prioritising your own stories, experiences and opinions.
“It means recognising and acknowledging ways in which individuals with privileges benefit from systems of oppression, and then working together to dismantle those barriers.”
Meghani proposes a three-step process to drive real allyship: providing equitable access to training, projects and other resources to accelerate skill building; implementing a structured approach to early promotions; connecting earlytenure women with capable managers, mentors and sponsors.
It is also important to remember that the value of allyship is not limited to the elevation of women in the workplace: every racial or socially marginalised group is dealing with its own issues around the dynamics of allyship in contemporary workplaces.

Recent research into LGBTQ+ allyship noted LGBTQ+ workers’ widespread feelings of being marginalised in the workplace. It identified three key traits associated
with being an effective ally: being accepting; having humility; taking action.

And while much of the conversation about allyship centres on changing men’s behaviour, Avast chief information security officer, Jaya Baloo, points out that allyship is not only something that men bestow on women.
“We actively need to seek out our mentors and our supporters and our allies, because it’s not that simple,” she told an International Women’s Day webinar.
“There are not always natural candidates who are going to inspire you, and there are not always natural leaders who are going to help promote you beyond what you’re able to do yourself. So, it really requires some personal agency to look for those opportunities and actually act on them.”
Baloo said speaking at conferences “by women for women,” was important, as was engaging with interviewers to find out more about their organisational culture.
“If we want this, we have to show up. We need to speak out and make sure we are taking care of ourselves, because no one else is going to do that for us.”

FULL TIME MID-SENIOR LEVEL BOTSWANA REMOTE
ABOUT THE ROLE
Our client is seeking experienced Cyber Security Consultants to provide technical advice, support and guidance to clients on projects including risk assessments, policies and assurance management plans.
As a consultant your role will involve significant stakeholder engagement, liaising directly with the client, and working to programme deadlines.
• Production of formal deliverables such as accreditation evidence, security policies and operating

procedures (SyOPs), risk assessments, and security assurance management plans.
• Understanding, assessing and articulating business and information risk at a technical and business process level.
• Reviewing effectiveness of existing security controls and propose proportionate security improvements.
• Support business development; develop and manage relationships with our clients; understand their business challenges and developing proposals to meet their requirements.

FULL TIME NEW ZEALAND HYBRID MID-SENIOR LEVEL
ABOUT THE ROLE
This is a great opportunity to join a leading Government organization. As the Chief Information Security Officer (CISO), you will be instrumental in developing and maintaining the security of the organization’s information systems and assets to prevent any unauthorized access to their infrastructure, data, and IP. You’ll be leading a team of 8-10 people (directly/indirectly) in the infosec space, developing and executing the infosec strategy and roadmap, building relationships and partnering with key internal and external stakeholders/providers, along with a number of other duties to ultimately build information security capability and awareness within the business.
• Extensive technical expertise in the design and implementation of ICT architectures and cybersecurity environments
• A proven leader who has managed teams in complex organizations
• Someone with the following certifications: CISA, CISM (issued by ISACA), CISSP
• Excellent communication skills and the ability to build relationships with both operational teams and executives
• Prior knowledge or experience with TOGAF

FULL TIME INTERNSHIP FRANCE ON-SITE
ABOUT THE ROLE
Valeo Cybersecurity team is composed of skilled professionals that are identifying and managing cybersecurity risks for the all Valeo Group. The team is animated with willingness to continuously improve methodologies, tools and ways of working to increase efficiency and support the Cybersecurity strategy. By joining us, you will be part of an international team and one of its cornerstones.
RESPONSIBILITIES
• Perform regular follow up on the Cybersecurity risk remediation action plans,
• Provide and follow up the Valeo Cybersecurity risk KPIs,

FULL TIME HYBRID FRANCE
ABOUT THE ROLE
To sustain the company's growth, we are creating the position of Head of IT Security at European level to assist our CTO who has been performing this role until now, in addition to other responsibilities.
The Head of IT Security is responsible for:
• Security of our information systems and production cloud platforms
• Permanent compliance with our certifications (PCI DSS Level 1, HDS)


• Obtaining new certifications (SOC 2 type 2 or ISO 27001, SecNumCloud)
RESPONSIBILITIES
• Contribute to the identification and analysis of risks within Diabolocom
• Support the Group Cybersecurity Risk Manager in the review of the risk assessments performed for the Valeo sites


• Follow up the exemptions
• Contribute to the Risk Management process
• Learn how to perform a risk analysis and, once possible, perform some risk assessments
• Other tasks or responsibilities will be given depending on the progress of the apprentice.
APPLY HERE
• Draft, develop and maintain the security policy and all documentation related to information security

• Contribute to the maintenance of or compliance with safety standards and applicable regulations
• Implement internal security audits and manage external audits
• Support technical teams in identifying and correcting technical vulnerabilities
• Support the implementation of security processes and tools with users
• Raise awareness, train and advise all Diabolocom teams on IT security
• Support pre-sales teams on security-related topics.
APPLY HERE

This position is responsible for supporting the Group Physical Security AVP in managing and implementing the Incident and Crisis Management program.
• Design detailed Physical penetration testing plans, encompassing various aspects of physical access controls, surveillance systems, alarm systems, and other security protocols
• Implement the agreed security controls as documented and approved by management, coordinate with relevant stakeholders both internal and external for implementation of these with stakeholders.
• Stay current with emerging physical security threats, trends, and technologies, and continuously refine testing methodologies to address evolving risks.
• Manage all crisis situations including emergency response calls, emergency response training drills, and the development of emergency response plans.
• Execute Physical penetration tests, leveraging advanced techniques, tools, and methodologies to simulate real-world threats and identify potential vulnerabilities
• Ensure the bank is following central, state, and local laws while dealing with security and crisis management issues
• Manage the development, implementation and periodic reviews of crisis management documentation and policies across multiple locations and regions.
Currently, we are looking for an Information Security Officer to manage Nitro’s ISMS efforts. This role will report to Head of Governance, Risk and Compliance, which acts as first and second line of defense regarding Information Security, Data Protection and Compliance where you will operate in an international team of Information Security professionals. This role is located in Berlin or Antwerp.
This is a Trusted Role and will be subject to the checks and controls identified by Nitro for such role.
• Manage and contribute to ISO 27001 ISMS operations and new requirements.

• Manage and contribute toward Qualified Trust Services Provider certification (QTSP).
• Contribute to the development of the Common Controls Framework and evidence collection.
• Facilitate and manage the operational risks directly or indirectly impacting ISMS.
• Monitor local regulatory requirements and changes as they impact ISMS or QTSP scope.
• Facilitate ISO 27001 audit with external and internal auditors.
• Perform ISMS operational checks, identify gaps and advising on mitigations.





FULL TIME NEW ZEALAND ON-SITE
ABOUT THE ROLE
We are looking for someone who can represent the New Zealand Customs Service | Te Mana Ārai o Aotearoa across a range of interagency forums supporting engagement on national security matters, specifically relating to major events that are likely to have a significant impact on New Zealand's border. New Zealand Customs Service | Te Mana Ārai o Aotearoa protects New Zealand's border using world-class tools, world-class people and innovative approaches.
The Intelligence, Investigations and Enforcement (II&E) Group's mission is to protect the integrity of New Zealand's border system. Within II&E sits the National Security & Emergency Management team whose primary aim is to support and represent Customs within the National Security and ODESC Systems.
• Strategic tasking and coordination in relating to the Major Events portfolio
• Leading or representing for Customs at a range of forums, which could include external and/or multinational participants
• Cultivating relationships at all levels across the public and private sectors
• Contributing to other NS&EM portfolios where required
• Workplan delivery
• Internal reporting

APPLY HERE


FULL TIME NEW ZEALAND ON-SITE MID-SENIOR LEVEL
ABOUT THE ROLE
This is an exciting opportunity for you to make a difference by helping our rapidly growing and developing Cyber Security Centre team. You will have access to some of the latest cyber security technology available today with the opportunity to test out new tooling and ideas.
RESPONSIBILITIES
• Identifying root cause problems and advising mitigations and long term fixes
• Continuously developing processes and response procedures to improve cyber security response
• Co-ordinating between internal and external parties during incidents, including providing advice and direction for multiple stakeholders.
• Threat Hunting and in-depth analysis
• Research evolving threats and technologies
APPLY HERE

We all hit a plateau in our career from time to time, unsure of the next step in our professional journey. However, it is no longer necessary to leave your company to get extended time out. Larger companies are starting to value career breaks, offering paid or unpaid leave as part of HR policy to retain key people and skills.
Career breaks, defined as intentional pauses in one’s professional journey, have gained increasing recognition and acceptance in the modern workforce. Traditionally, individuals often viewed continuous employment as the only path to success, fearing that stepping away from work would lead to missed opportunities. However, the value of career breaks should not be underestimated. These intentional pauses offer numerous benefits that contribute to personal growth, skill development and overall wellbeing. More importantly, career breaks retain women in cybersecurity and give them the opportunity to consider their next move in the industry.
Women make up 24 percent of the cybersecurity workforce globally and 17 percent in Australia, according to the Australian Bureau of Statistics’ 2021 Census, which listed cybersecurity as an occupation for the first time.
However, women are leaving the industry due to a perceived lack of opportunities, despite the talent shortfalls and demand for more women to apply for open roles. For employers, retaining women with key skills makes smart business sense. And the benefits of a career break for your professional development can be significant.
Taking a career break provides you with the opportunity to engage in new learning experiences and skills development. Pursuing further education, enrolling in workshops or simply exploring hobbies can lead to the acquisition of valuable knowledge
FIONA BYRNESand expertise that may not be accessible during full-time work. Additionally, a career break offers a chance to step back and reflect on your strengths and weaknesses, giving you time to strategically align your skill set with your career aspirations.
2 INCREASED ADAPTABILITY AND RESILIENCE
A career break can be a transformative period that pushes you outside your comfort zone. Whether it be traveling, volunteering or facing personal challenges, these experiences foster adaptability and resilience. The ability to handle change and overcome obstacles is invaluable in today’s dynamic and unpredictable job market, and enhances your employability and leadership potential.
3 IMPROVED MENTAL AND PHYSICAL WELLBEING
The constant pressures of work and life can take their toll on your mental and physical health. A career break offers a much-needed opportunity to recharge
and address burnout, stress and other health-related issues. During this time you can focus on selfcare, practise mindfulness and develop healthier habits. As a result, you can return to work refreshed and re-energised, ready to tackle challenges with renewed enthusiasm.
4 ENHANCED WORK-LIFE BALANCE
A career break serves as a powerful reminder of the importance of work-life balance. During this time you can recalibrate your priorities, reassess career goals and determine how work fits into your overall life vision. A career break also creates an opportunity to redesign how you distribute and share key responsibilities at home, or address dysfunctions in your personal life. This introspection often leads to more thoughtful career decisions and healthier worklife habits when you return to the workforce.
5 CREATIVE INSPIRATION AND INNOVATION
Stepping away from the daily routine of work can
spark creativity and innovation. Engaging in activities unrelated to your profession allows the mind to wander and explore new ideas, for example, writing, art or community involvement. Whatever you choose, career breaks provide fertile ground for creative expression, which can translate to fresh perspectives and problem solving skills when you resume your career.
Career breaks hold immense value, offering a chance to grow personally and professionally. However, as we all know, taking a break is easier said than done. Here are a few tips to ensure a positive career break discussion with your employer.
While it is always prudent to invest in cross-training, knowledge transfer and succession plans, it is especially important for a career break. You need to have a strong backup available to reassure your employer that your absence will not adversely affect their business. This is possible even when there is a staff shortage. It takes planning to demonstrate you are invested in the company’s success and have considered the impact on the business.
If annual or long service leave is not available, consider unpaid leave as an option. Saving money for a focused three-month break at home can help you concentrate on your health and wellbeing, extending your career in cybersecurity.
If you negotiate a career break, stay involved in the industry. Cybersecurity moves fast. Stay involved through volunteering, mentoring, online courses or maintaining your certification credits. Use your break as an opportunity to reconnect with what you love about cybersecurity and why you gravitated to it in the first place.

If we do not ask, we do not know what is possible. As more employees take career breaks we normalise the discussion and create opportunity for a new workplace. Senior leaders have an opportunity as role models to create an open conversation with employees about what motivates people to stay in cybersecurity. As employees, you just need to ask and start the conversation about how and your employer together can make it work.
www.linkedin.com/in/byrnesfiona
WE'VE HIT 70% CAPACITY GRAB YOUR TICKETS BEFORE THEY ARE ALL GONE!

JOIN US
for an enchanting evening to celebrate and recognise the achievements within the IT Security Industry.
For more information on the 2023 Awards, please visit our website: womeninsecurityawards.co.nz

Karen is CEO and co-founder of BCyber, an agile, innovative group that works with SMEs to protect and grow their businesses by demystifying the technical and helping them to identify and address cybersecurity and governance risks. In 2021 Karen graduated from the Tech Ready Woman Academy’s Accelerator and the Cyber Leadership Institute’s CLP programs.
You might think it would be easy to empower women and retain people in the cybersecurity industry, but it is not. Sometimes the challenge seems insurmountable, almost. Therein lies the key to the problem. ‘Almost’ means there is a glimmer of hope we can focus and build upon. While there is no single all-encompassing Big Bang solution, focusing on a few well-integrated actions will help address the challenge. Here are three initiatives any individual can take to help them take their first steps into cybersecurity, or help them stay there.
• Network, network, network. Dust off your business attire and attend functions where likeminded people are to be found. Go out and ‘make a friend’. Not easy, I know. I am a natural-born introvert, and after years of Covid and lockdowns the idea of getting out of my ‘comfortable clothes’, throwing on some shoes other than joggers and then ‘making nice’ with a bunch of strangers can fill me more with concern than excitement. But you can do it. Take a deep breath, put on your business armour (aka business attire), smile big and introduce yourself to the first person who smiles back. Aim to engage with just one or two people. Trust me, it becomes easier and increases the group of people you can call on, or bounce ideas off.
• Allies. You probably already have these people in your life; you just might not label them allies. They are your supporters; the people who believe in you, even when you do not. They provide the antidote to your internal ‘I am not good enough’ voice that can chip away at your confidence. Fun fact: I would not have moved into cybersecurity and been named Female Cyber Leader of the Year in this year’s Australian Cyber Security Awards if my
business partner had not pushed me with “I know you can do this” followed quickly by a challenge I could not resist. “Isn’t it better to have tried and failed than to never have tried at all?”
Micro courses. University courses, be they undergraduate or postgraduate, while wonderful are not the only way to learn. Sometimes you do not have the time, bandwidth, or money to go down that route. And this is where micro courses come in. They are a short, sharp cheaper option. Just decide what you want to learn—for example general cybersecurity 101, or something more in-depth like threat hunting—and decide where to start. Choose your own adventure, and depending on the course you choose, you might even be able to network…network…network.
So, a few small steps, albeit ones that may take you out of your comfort zone, could be your empowerment key. And on that note, I look forward to seeing you at the next industry function. I will be the one that smiles back!
www.linkedin.com/in/karen-stephens-bcyber

 by Jay Hira , Founder and Executive Director at MakeCyberSimple
by Jay Hira , Founder and Executive Director at MakeCyberSimple
In today’s cybersecurity landscape a concerning trend is emerging: the departure of women from the sector. Efforts to attract women to cybersecurity are futile if retention continues to decline at the rate we are witnessing. As an industry, we must prioritise gender equity so our sector can operate at its full potential.
In this article I aim to explore retention issues through the prisms of diversity and collaboration, discussing strategies that have the potential to reverse this growing trend.
The gender gap in cybersecurity is an issue that requires attention. Women remain underrepresented due to factors rooted in societal influences. Gender biases have historically guided career choices, steering women away from STEM based fields. Biased interview questions, a lack of female role models, compensation gaps and other systemic barriers create an environment that discourages women from pursuing careers in cybersecurity.
While we are far from claiming gender parity, I have witnessed a positive shift in awareness that is prompting organisations and industry bodies to boost research and consultation to understand the predominant factors deterring women from entering, and staying in, the sector.
This data is informing company DE&I programs, recruitment strategies and employment conditions designed to create more diverse, inclusive and collaborative workplaces and, ultimately, to attract women and other under-represented groups to cybersecurity.
Embracing the power of diversity
Diversity is more than just a buzzword; it’s a driving force for innovation. The multifaceted challenges in cybersecurity demand diverse perspectives if they are to be overcome. Research consistently emphasises the link between diversity and enhanced problem-solving capabilities. Encouraging women and
individuals from various ethnicities, backgrounds and life experiences into the sector enriches collaboration and nurtures innovative thinking.
Promoting equal opportunities for all Initiatives to welcome and empower women in cybersecurity must start early. Encouraging STEM education devoid of traditional gender roles is vital. Engaging in STEM education can instil a lasting curiosity for technology in young minds, transcending gender norms. Additionally, crafting inclusive job descriptions, broadening entry criteria and highlighting role models can encourage women to pursue, and stay in, cybersecurity careers.
A genuinely inclusive cybersecurity environment is one where diverse voices are celebrated. Such an environment not only fosters belonging but also helps retain a diverse workforce. Embracing diversity across age, culture, background and gender creates an atmosphere where individuals can express themselves openly and without fear of retribution. Collaboration flourishes in such spaces, driving innovation and progress.
Pursuit of gender parity requires active involvement by everyone, regardless of gender. Allies, particularly male allies, play a pivotal role in bridging the gender gap. Acknowledging women’s capabilities and actively involving them in decision-making processes is essential. By championing inclusivity, allies can amplify diverse voices and contribute to more equitable workplaces. Male allies can further extend their influence by championing women’s accomplishments in the field. Recognising their achievements and sharing their success stories motivates individuals and challenges traditional perceptions. By highlighting these achievements, male allies can assist in reshaping the industry’s narrative, shifting the focus from gender to competence.
Cybersecurity is more than just a career; it’s a dynamic environment that rewards creative problem solvers. In essence, it’s a puzzle where each piece
represents a layer of complexity. As we move closer to solving one facet, the puzzle shifts, demanding innovative solutions. And these solutions are not comprehensive and complete when they come from a workforce that lacks diversity. The very nature of cybersecurity demands diversity to problem-solve and stay ahead of increasing and sophisticated cyber threats. Couple diversity with collaboration and we have a promising combination with the power to boost the productivity, astuteness and longevity of the cybersecurity workforce in Australia.
As we contemplate the critical issue of women leaving cybersecurity, it is clear what needs to be done. By nurturing diversity and collaboration we can reverse the current trend. Empowering women, fostering a welcoming environment and amplifying diverse voices through allyship are steps towards creating a thriving and inclusive cybersecurity landscape. Our collective efforts hold the potential to reshape the future of cybersecurity and drive innovation beyond boundaries.
www.linkedin.com/in/jayhira











































































































































































In recent years cybersecurity has emerged as an industry critical to safeguarding our digital infrastructure from ever-evolving threats. Yet, despite its significance, there is a disconcerting trend: a growing number of women are leaving this industry.
This concerning exodus of talented and capable women has raised important questions and shed light on the underlying challenges faced by female professionals in this male-dominated domain. There are many reasons for this exodus: women being targets of bullying and abuse; work-life balance challenges; gender bias and discrimination; the gender pay gap; a lack of representation and mentorship. In addition, cybersecurity has a massive image problem: many women leaving the industry say they do not find it welcoming.
The statistics are revealing: women account for just a quarter of all cybersecurity jobs. A recent report from BCG found just 25 percent of employees in cybersecurity were women. In addition, out of the 2000 female employees surveyed for the report:
• 87 percent reported experiencing unconscious bias.
• 19 percent reported being discriminated against.
• 18 percent reported earning between $50k to $100k annually, versus 32 percent of men.
• 54 percent reported receiving training in STEM aimed specifically at girls and young women.
• 37 percent reported struggling to achieve a good work/life balance in cybersecurity.
It is clear a significant amount of work still needs to be done to attract more women into cybersecurity, and a good starting point would be addressing cybersecurity’s image problem. But what is that image problem, and how can we fix it to make cybersecurity more welcoming for women?
For many, the term cybersecurity conjures up images of hackers in hoodies, intricate motherboard diagrams, padlocks, and binary code, military symbolism, war rhetoric, and even the notion of cyborgs or futuristic machines battling in space. This is especially true when it comes to the depiction of artificial intelligence (AI).
Cybersecurity extends well beyond these clichés, but despite efforts to correct the narrative, these exaggerated portrayals persist and show no signs of disappearing. They pose a threat to the industry because they create a sense of powerlessness among
the public. Interestingly, academia has recently taken a keen interest in discussing these depictions and exploring the role of humans in the industry.
At its core, the image problem of cybersecurity stems from several key factors that shape public perception. These include:
Misconceptions and stereotypes: Cybersecurity is often seen as a mysterious and inaccessible intellectual domain reserved exclusively for technical geniuses and hackers in dark rooms. Such stereotypes can discourage individuals, particularly women and underrepresented groups, from considering careers in cybersecurity, hindering diversity and the acquisition of new talent.
Fear and negative association: Cybersecurity is frequently associated with negative incidents, such as data breaches, cyberattacks and privacy violations. These high profile incidents can create fear and a sense of helplessness among the general public. As a result, cybersecurity is often seen as reactive rather than proactive and relevant only in the aftermath of an attack. This perception of reactivity can overshadow the proactive measures taken by cybersecurity professionals.
Complexity and lack of awareness: cybersecurity is a complex and ever evolving field which can make its nuances challenging for the general public to grasp. Lack of awareness about the role and importance of cybersecurity can hamper support for cybersecurity initiatives, which can in turn lead to underestimation of the resources required to protect against cyber threats and underinvestment in robust defence systems.
Media portrayal: media coverage often sensationalises cyber incidents by focussing on the dramatic aspects of breaches rather than the underlying issues and preventive measures. While such incidents are newsworthy, the disproportionate emphasis on their sensational aspects can perpetuate a distorted image of cybersecurity, reinforcing the notion that it is an insurmountable problem rather than an ongoing challenge that can be addressed through collective efforts.
Addressing the image problem of cybersecurity is crucial for the industry’s growth and resilience and to ensure public support. It requires concerted efforts from cybersecurity professionals, organisations, educational institutions, media and policymakers. Strategies to improve the industry’s image include:
Education and awareness campaigns: promote initiatives that raise public awareness about the importance of cybersecurity, demystify the field and highlight its positive impact on society. Emphasise the role of cybersecurity in protecting individuals,

organisations and critical infrastructure, and the career opportunities it offers.
Diverse representation: encourage diverse representation within the cybersecurity industry by showcasing the wide range of professionals from different backgrounds, genders and ethnicities working in the industry. Highlighting successful role models can challenge stereotypes and inspire a broader range of individuals to consider careers in cybersecurity.
Collaboration and transparency: foster collaboration between cybersecurity professionals, organisations and the media to promote accurate and balanced reporting of cyber incidents. Encourage transparency in disclosing incidents, sharing lessons learned, and highlighting successful defence strategies. By showcasing effective preventive measures the narrative can be shifted from doom and gloom to proactive and empowering solutions.
Enhancing accessibility and inclusivity: create inclusive pathways to cybersecurity careers by providing accessible educational resources, mentorship programs and scholarships. Foster partnerships with educational institutions to promote cybersecurity curriculums and ensure these are accessible to students from diverse backgrounds.
Proactive engagement: actively engage with the public through open forums, community events and online platforms. Encourage conversations about cybersecurity, address concerns and provide guidance on protecting personal and organisational data.
The problematic image of the cybersecurity industry will take concerted efforts and a shift in narrative to change. By fostering awareness, collaboration, inclusivity and engagement we can reshape the public perception of cybersecurity and create a more accurate and empowering image of the industry.
Addressing cybersecurity’s image problem and creating a more inclusive and supportive environment








is crucial to retaining women in the industry. By addressing biases, providing mentorship, promoting work-life balance and offering equal opportunities, organisations and the industry as a whole can encourage women to remain in cybersecurity and thrive in their careers.

Lisa Ventura MBE is an award-winning cybersecurity specialist, content writer and speaker. She is the founder of Cyber Security Unity, a global community organisation dedicated to bringing together individuals and companies who actively work in cybersecurity to help combat the growing cyber threat. Lisa is also a cybersecurity mindset and mental health coach and offers help and support to those affected by stress, burnout, bullying/abuse and mental health issues in cybersecurity and infosec.
www.linkedin.com/in/lisasventura
twitter.com/cybergeekgirl







www.csu.org.uk




 by Vannessa McCamley , Leadership and Performance Consultant, Coach, Facilitator, Author and Keynote Speaker
by Vannessa McCamley , Leadership and Performance Consultant, Coach, Facilitator, Author and Keynote Speaker
In recent years the cybersecurity industry has witnessed a steady increase in demand as technology has become an integral part of our daily lives. However, one concerning trend has emerged: disproportionate numbers of women leaving cybersecurity roles. While women initially show great promise and talent, many eventually opt for other career paths. To understand and reverse this trend we must delve into the intricacies of the human brain and examine neuroscience. By recognising the biological and cognitive factors that contribute to women leaving cybersecurity we can develop targeted strategies to promote gender diversity and create an inclusive environment in this critical industry.
The study of neuroscience has shed light on the biological and structural differences between
male and female brains. Gender differences are not absolute: they vary significantly across individuals. However, certain patterns have emerged. For example, research has shown women tend to have more connections between the left and right hemispheres of their brains, facilitating enhanced communication between these different brain regions. This connectivity often contributes to better juggling tasks, verbal communication, and emotional intelligence.
On the other hand, men tend to display stronger connections within individual brain hemispheres, which can lead to greater spatial awareness, problem-solving and logical reasoning abilities. However, the vast majority of cognitive capabilities are shared between both sexes.
Unconscious bias refers to the automatic and unintentional biases that individuals hold toward certain groups. In male dominated fields like cybersecurity, unconscious biases can influence hiring decisions, promotions and workplace dynamics leading to a less inclusive environment for women. These biases can negatively impact women’s professional experiences making them feel undervalued and discouraged.
From a neuroscience perspective such biases can activate the amygdala, the brain’s threat detection centre, leading to a heightened stress response. Additionally, the brain’s reward system may be less activated when women experience biased treatment, affecting their motivation to excel and increasing the likelihood of them leaving the profession.
Work-related stress is a common challenge in the fast-paced and high-stakes cybersecurity industry. Balancing work demands with personal life can be particularly challenging for women who often face societal expectations related to caregiving and family responsibilities. This imbalance can lead to burnout and a decision to leave the industry for a career offering greater flexibility.
Chronic stress can have detrimental effects on the brain. The prolonged release of stress hormones such as cortisol can result in reduced cognitive functioning, memory problems and emotional dysregulation—an emotional response that is poorly regulated and does not fall within the traditionally accepted range of emotional reactions. These factors can contribute to a woman’s decision to seek a less demanding career path.
The lack of female role models and mentors in leadership positions in cybersecurity can have a profound impact on women’s career
aspirations. (Hence my passion for contributing to this publication regularly to support females in the industry.) Neuroscience research suggests positive role models and mentors can activate brain regions associated with motivation, goal setting and resilience. When women lack such support their sense of belonging and confidence in the industry may be impacted.
Neuroplasticity, the brain’s ability to reorganise and form new neural connections, offers hope for reversing the trend of women leaving cybersecurity. By understanding neuroplasticity we can design interventions that encourage skill development and resilience in women pursuing cybersecurity careers.
Interventions such as targeted training programs, workshops and mentorship initiatives can reshape the neural pathways associated with confidence, problem-solving and stress management. Additionally, creating a supportive and inclusive work culture can mitigate stereotype threats and unconscious biases, and promote an environment where women feel valued and empowered.
To reverse the trend of women leaving cybersecurity we must approach the issue from a neuroscience perspective. By understanding the cognitive and biological factors at play we can develop evidencebased strategies to address stereotype threats, unconscious bias, and stress and work-life balance challenges. By leveraging neuroplasticity and creating an inclusive environment we can foster gender diversity and empower women to thrive in the cybersecurity industry. It is imperative we recognise the importance of women’s contributions and work collaboratively to build a future where gender parity is the norm in cybersecurity and beyond.

linksuccess.com.au/rewire-for-success
www.linkedin.com/in/vannessa-mccamley
linksuccess.com.au/contact-us
Vannessa McCamley is a leadership and performance expert specialising in neuroscience practices that help individuals, teams and businesses grow in meaningful ways whilst delivering measurable results in healthy ways. She has a passion for helping people and businesses to overcome obstacles and enabling them to reach their strategic goals. She brings a strong background in IT security and more than 20 years of business experience to collaborating with individuals at all levels and from several industries. She is the author of Rewire for Success, an easy guide to using neuroscience to improve choices for work, life and wellbeing.
"When women work together, they become a force to be reckoned with. Be part of a force for good in the security industry, by joining the AWSN Explorers program today!"



S t u d y i n g o r a n E a r l y C a r e e r P r o f e s s i o n a l i n i n f o r m a t i o n s e c u r i t y ?
L e a r n m o r e a t . a w s n . o r g . a u / i n i t i a t i v e s / a w s ne x p l o r e r s /
- Liz B, Co-Founder

I’ve been loving these past couple of weeks on social media. No longer is my feed crowded with doom and gloom, politically charged memes or old men yelling at clouds. Instead, there seems to be a united front with Australia getting behind our Women’s Football Team, more commonly known as The Matildas. I haven’t seen Australia get together like this behind something since… Well, ever. The team’s success lately has triggered a strong sense of optimism within the populace that does not seem to be diminishing.
I’ve been reading plenty of articles from a number of well-known Aussie pundits lately proclaiming that this World Cup, co-hosted with our brothers and sisters in New Zealand, is creating a lot of interest among young people, both boys and girls. The fact is the matches against Denmark and then France were not only the best women's football matches I’ve ever watched, but the best football matches, full stop.
However, many of those same pundits are also dishing out a serve of pessimism, predicting that nothing will come of the interest created by the World
Cup because, without further funding, the game at a grassroots level simply will not thrive. This, ladies and gentlemen, is where I draw the analogy my articles are known for, with the realm of cybersecurity.
This month’s edition of Women in Security Magazine focuses on the topic of retaining women in our industry. The question of retention is often asked alongside the question of how to attract more women into security in the first place. While my views on how we make the industry more inclusive may have altered slightly over the last couple of years, on one point they are unchanged, that is on the need for better grassroots action. There may be several very good programs out there designed to attract young women into STEM related careers. However, this is also a short-sighted approach if cybersecurity wants to simply build interest in STEM. As a former high school teacher I have always been an advocate of STEAM, where ‘A’ stands for Arts.
The reason for this is that, in security, we miss our goals of attaining and retaining good talent when we
focus only on the traditional STEM related security skills and forget about skills such as the ability to think outside the box, to recognise patterns, to understand how to effectively communicate risk, and to design the programs that will attract the next generation of youngsters into the field. STEAM is a useful description of the skills required by our industry, but one that does not get the recognition and focus it deserves, like a soccer team’s promising youthful player who never gets the coaching that would enable them to excel.
In order to ensure retention we also need to be careful not to put all women into the same box. Not all women want to start a family, so parental leave incentives and child care subsidies are not the only incentives needed to retain women in an industry. Instead, we should be focusing on mentoring programs for women seeking leadership roles. We already have a fantastic national program: the AWSN mentoring initiative powered by OKRDY. I recommend any woman in security seeking a mentor to look into this program.
I would like to see more federal funding dedicated to supporting this, as well as other similar programs across our industry. I am quite excited to see what future programs could be conceived with the right support in the right areas, and I am optimistic that national and state governments can get behind our security workforce in ways that will provide more support and better opportunities, particularly for women.
I would like to conclude by noting that initiatives to boost inclusion should not be confined to women. We need to attract more of our First Nations peoples into security, as well as those new to Australia. As a descendent of Italian immigrants who were given minimal opportunities but did as well as they were able, and as someone who mentors young members of new immigrant families, I can attest that Australian
governments and industry need to do more to provide opportunities for these young people. An all-inclusive approach to fostering diversity is extremely important, not only for young people looking to break into security, but also for our industry, because a diverse workforce drives innovation and growth.
A STEAM approach ensures we include a wide array of skills and ways of working. Some schools have already started including Arts in their STEM curriculums. Now, we just need to change the mindset of our industry and government leaders so we all take a more inclusive approach.
www.linkedin.com/in/simoncarabetta


In a world where the cybersecurity landscape is constantly evolving one program stands out as a beacon of empowerment, resilience and transformation. The Tangible Uplift Program (TUP), spearheaded by Nivedita Newar, is redefining the narrative for women in cybersecurity. As TUP unveils its 2023 cohort and celebrates a renewed partnership with the Australian Information Security Association (AISA), the program's accomplishments are a testament to the power of collaboration, mentorship and collective ambition.
At its core TUP is not only a program; it's a movement fuelled by the unwavering dedication of women determined to uplift the careers of their fellow women
in cybersecurity. The program's central goal is to empower women to pass the Certified Information Security Manager (CISM) written exam and enhance their skills, credibility, marketability and job-readiness. What sets TUP apart is the achievements of the women who emerged from the 2022 cohort, each a testament to the program's efficacy and potential for growth.
The partnership between TUP and AISA has been a driving force behind the program's success. AISA's commitment to empowerment and innovation has resonated with TUP's vision, creating a synergy that has propelled the program to new heights. As TUP embarks on its 2023 journey the renewal of AISA's partnership is a celebration of shared values and
mutual aspirations. AISA's involvement during the 2022 TUP pilot was a source of inspiration, motivating participants to excel and achieve top scores in the CISM exam. AISA's support fosters an environment where achievement is celebrated, knowledge shared and growth nurtured.
As TUP sets its sights on the transformative journey ahead, a new sponsor has joined the ranks, bringing fresh enthusiasm and support. This exciting development—announced on TUP’s LinkedIn page, is testimony to the program's expanding reach and growing significance. While AISA remains an essential partner, this new sponsor's involvement speaks volumes about TUP's impact and the potential for even greater collaborations that will shape the program, and the industry’s future.
TUP's achievements extend beyond the tangible empowerment it provides. The program's impact has been recognised through prestigious awards including the Australian Women in Security Awards 2022 where TUP was honoured as the Most Innovative Educator in Cyber Security. This accolade exhibits the program's commitment to innovative and effective educational approaches.
Additionally, TUP's dedication to cybersecurity outreach was celebrated at the AISA Cyber Security Awards 2022 where it was awarded Cyber Security Outreach Program of the Year. This recognition highlights the program's exceptional efforts in

reaching out to aspiring women in cybersecurity and providing them with the tools, knowledge and mentorship needed to thrive in the industry.


The results speak for themselves: 75 percent of active participants successfully passed the Certified Information Security Manager (CISM) exam within just 12 months. This impressive achievement emphasises TUP's commitment to providing participants with the knowledge and support needed to excel in their cybersecurity careers.
Central to TUP's success is a comprehensive suite of program inclusions designed to empower participants at every stage of their journey. These inclusions ensure participants are equipped with the knowledge, skills and support necessary to succeed. These inclusions showcase TUP's dedication to offering a holistic and empowering experience. The program not only equips participants with the knowledge needed to excel, but also provides a platform for connection, growth and mentorship. They are as follows:
• Free four-week ISACA accredited CISM Online training course, by IT Masters: an essential component that lays the foundation for success, this training course is designed to provide participants with the knowledge and insights needed to excel in the CISM exam.
• Free course completion certificate from IT Masters: this certificate recognises the dedication
and effort of participants and is testament to their commitment to growth and learning.
• Free three-month, online, rigorous group exam preparation sessions: these sessions, led by volunteers from the 2022 cohort who have successfully passed the CISM exam, provide invaluable guidance and preparation strategies.





• Collaboration platform: a space for participants to connect, collaborate and motivate one another, fostering a sense of community and shared purpose.

• One-year AISA membership.
• The chance to win one-of-five AISA Melbourne conference tickets for October this year.




• A grand prize worth $2,750 USD ($4,200+ AUD), generously sponsored by the Cyber Leadership Institute (CLI).

As TUP forges ahead with its 2023 cohort, the program represents a beacon of empowerment, mentorship and growth that continues to shine brightly. The leadership of the women from the 2022 cohort, combined with the support of partners like AISA and the involvement of new sponsors, portends
 Rebecca Ahmed
Leigh Dixon Brindha Chandramohan
Babitha Sobha Jalpa Bhavsar
Diyva Saxena Wendy Huang
Caitlin Sauza Mahrita Harahap
Nivedita Newar
Rebecca Ahmed
Leigh Dixon Brindha Chandramohan
Babitha Sobha Jalpa Bhavsar
Diyva Saxena Wendy Huang
Caitlin Sauza Mahrita Harahap
Nivedita Newar


The cybersecurity skills and workforce gap is putting the security of organisations at risk. With demand growing and with organisations unable to find talent and unable to keep up with attrition it is vital to support women in cybersecurity and stop them leaving the profession.
Here are some ideas on how to reduce the number of women leaving the profession, from four women at different stages of their careers who share their career highlights and offer advice on how to thrive in a cybersecurity career.
Olivia Conlon Cybersecurity specialist, Averto
As an early career professional Olivia Conlon has put her focus on growth and professional development, and has already been promoted. Conlon has a commitment to continuous learning and has worked to expand her skill set and to network with like-minded professionals.

She has also stepped out of her comfort zone by, amongst other things, being a panelist at the 2022 ASIA Cyber Security Conference. “These activities keep me excited about my job and the cybersecurity industry,” she says.
She enjoys the opportunity her profession gives her to protect organisations from evolving threats, and the excitement that comes from solving complex problems. She also enjoys working collaboratively and being at the forefront of technological advancements.
To help women thrive, Conlon recommends they seek out mentors, embrace diverse perspectives and maintaining a growth mindset. “Embracing new challenges and experiences, as well as developing resilience, are essential traits for success,” she says. And to support women she says it is crucial for the industry to encourage diversity and inclusivity, establish mentorship programs, and provide avenues for career advancement.
Jo Stewart-Rattray Chief Security Officer, Silverchain
Jo Stewart-Rattray was recently induced into the ISACA Hall of Fame, a first for an Australian woman, in recognition of her commitment to the organisation and the global professional community. She has demonstrated this commitment through her work on gender diversity in the tech workforce and the SheLeadsTech program. She built from scratch into a program that has been rolled out to 180 countries, empowering women to enhance their professional skills and advocate for their career advancement.
Stewart-Rattray loves what she does and relishes helping organisations keep their corporate environments safe. “In the world of continual cyber threat and attack, it is incredibly rewarding,” she says.
She sees the recent growth of hybrid and flexible working providing a real advantage for women, saying it “allows women to balance their personal responsibilities with their professional responsibilities
by being able to juggle hours to allow for child pick up and drop off, or caring for older relatives.”
For women to thrive in cybersecurity Stewart-Rattray says it is important for them to be involved with a professional body to gain further learning and insights, from events and from industry activity in general, and to “take advantage of the reports and white papers that professional bodies produce.”
“It’s incredibly important to keep up to date, to build networks and maintain relationships with other CISOs and CIOs to keep abreast of what is happening locally and globally. It is hard work, there can be no doubt about that, but what senior level role today is not? And networking is hard at first, but a really important component of our professional lives today.”
To help discourage women from leaving the profession, Stewart-Rattray says they need to feel included and find ways to compensate for being the only female in the security team, which is often the case. “I seek out female colleagues from the broader tech teams to roll ideas around with, and sometimes just have a virtual chat about stuff that interests professional women. Don’t be an island, reach out to others!”
Jenai Marinkovic Cofounder and President of non-
profit
GRCIE (GovernanceRisk and Compliance for Intelligent Ecosystems), a cybersecurity and GRC academy based in Virginia, USA
Jenai Marinkovic has worked in many different areas, including live sports, entertainment, manufacturing and healthcare systems, with a focus on emergent technology. Her passion for the intersection between the natural world and the digital world coupled with her penchant for finding the positive or humorous side of things has helped her thrive. “Every day I look at the world through the lens of our future and try to make real the preparations necessary to weather and/ or thrive in that future,” she says.
Marinkovic believes the ability to protect and defend is often innate in cybersecurity professionals. “Whether protecting a company or protecting our families — understanding cybersecurity and GRC is key to your ability to thrive in the new world.”
Her advice to any woman seeking a career in cybersecurity is to establish networks from the outset. “The people you meet and help you will be with you for decades.” She also suggests looking to volunteer. “Regardless of where you are in your journey, you are further ahead than others and they are looking to you for inspiration.” And she says it is also important to be comfortable with failure.
“Innovation is starved in the absence of failure.”
To deter women from leaving the profession, Marinkovic believes diversity to be important because it adds strength to teams and organisations. However, she says it needs to be on show and better represented to show people of all kinds that there is a place for them. “We need to showcase the different roles and opportunities.”
And, Marinkovic says, it is important for leaders to better understand how they relate to others, because “more emotionally empathetic leaders can lead to higher retention numbers.”
SandyFor Sandy Silk the highlights of her 25 year career have much in common: they are all about bringing people together to analyse and solve a problem. These highlights include rolling out multifactor authentication to 65,000 faculty, staff and student accounts at Harvard, and developing security protocols for research data on human subjects. Silk says the key to thriving is to find a role that plays to your strengths, in an organisation (employer) that matches your personal values.
She also says security professionals can make the mistake of internalising an attack and seeing it as
a personal shortcoming. “Your role, your employer and your success preventing security incidents can become your identity, and that will lead to stress and burnout.
She adds: “If you are a woman, or other underrepresented demographic working in cybersecurity, you may strive to achieve more than your team members to validate your skills and your right to be there. In such cases, people may hesitate to ask for assistance, be afraid of appearing inadequate, and possibly end up reinforcing any bias that they’re the ‘diversity hire’.”
She advises women to make sure they have people to talk to who can remind them of their skills, and to remember that nobody can ‘do it all’. “Any cybersecurity professional may start working additional hours beyond their scheduled work, such as evenings or weekends, trying to accomplish more than finite resources allow and be ‘successful’. Remember to always set boundaries to preserve your personal time, enforce those boundaries, and do things that bring you joy.”
www.linkedin.com/in/rosalyn-page
www.linkedin.com/in/olivia-conlon-1975121a4
www.linkedin.com/in/jo-stewart-rattray-4991a12

www.linkedin.com/in/jenaimarinkovic
www.linkedin.com/in/sandysilk
Silk Principal Cybersecurity Advisor, Info-Tech Research Group

It all took place in a project run by Australian organisations She Maps and Diamonds in the Rough with support from Baseball Australia and funding from the Australian Government’s Department of Foreign Affairs and Trade (DFAT).
She Maps is an Australian company that offers several programs based on drones to get children interested in STEM and to make teachers more STEM aware. Diamonds in the Rough uses baseball, traditionally a male dominated sport, to connect emerging Australian Emerald baseball players with young Indonesian girls. It is led by Australian baseball champion, Narelle Gosstray and aims to provide equal access and encourage female participation in baseball in Indonesia, challenge gender norms and raise awareness of domestic violence. It does this through a combination of skills clinics, personal development programs and games against local men’s club teams.
She Maps cofounder Paul Mead says She Maps’ STEM education program, Partnering for Purpose, has three levels. It provides drone resources to schools and female demonstrators who provide role models to the students. It also has resources for teachers that align with the Australian curriculum and a number of online training options for teachers. “We have people using our program in 14 different countries. We license our program out and train people in local communities around the world to use the program,” Mead says.
“We've run the program in hundreds of schools. We've taught over 8000 people. This year, we have an Australian government funded national roadshow. We will be in every state and territory, in 14 different locations where we're doing teacher workshops. Over 1000 people have gone through our face‑to‑face program.

It’s an unlikely combination: drones, STEM and baseball. However an Australian initiative has been teaching girls in Indonesia about baseball and simultaneously using drones to teach them about STEM.
The main focus of She Maps programs is children in the last two years of primary school, particularly girls. “Kids’ perceptions about what they want to be in the world, and what society expects them to be, starts really early in primary school,” Mead says. “By the end of primary school that unconscious bias is quite set. What we see is that the transition from primary school to high school is where there is the biggest drop off in girls choosing STEM subjects and believing they are good at those STEM subjects.
“So the groups we target are in those final two years of primary school years to really challenge that unconscious bias. It's also where students are able to operate a little bit more independently.”
She Maps also uses real world problems to make the programs more meaningful and get students thinking about how they can solve these. “We have people come in from industry, talk to students and teachers and show them what the pathways are, and the really cool stuff happening in industry, so teachers and students get excited,” says Mead.
“Those could be drones being used to capture data in emergency situations, whether that be flooding or fire, drones being used to map the Great Barrier Reef to look at the health of the of the reef, or surf lifesavers using them on the coast to keep swimmers safe, or people using them in construction and engineering.”

The recent joint She Maps and Diamonds in the Rough program in Indonesia is the second run by Diamonds in the Rough and the drone component has its origins in the first program, run back in 2016 when She Maps cofounder Mead was working for the Department of Sport and Recreation and based in Darwin. Working with Gosstray and Baseball Australia he took young women from the Australian baseball team to Indonesia to act as role models for Indonesian girls under a program funded by the Australian Government.
“Indonesian girls over 14 were not able to play baseball,” Mead explains. “The rule was they had to play softball. So we set out to challenge that, to show that women can play baseball. We had some fantastic support over there, from the associations and from the mothers of the girls.”
After that Mead left the Department of Sport and, with his wife, Dr Karen Joyce, founded She Maps. Then government grants for promoting baseball in Indonesia became available again and they and Gosstray decided there was potential in combining drones and baseball.
“We said to Narelle let's go for it again, but let's try some drones, Mead says. “Let's see what we can do with She Maps as well, because sport diplomacy is great, and baseball is great, but we've got a group of girls engaged in this program, and they are not all going to be sports people. What are some of those other skills that we can teach? Technology is coming to Indonesia. It's one of the fastest growing economies, but the opportunities for girls in STEM are just not there. So we thought, we would try drones as well.”
The first program ran in February 2020. Then Covid hit and the program recently completed was the first since. It was held in Surabaya over two days with 75 girls and in Bali with 30 girls.
“The girls were doing baseball activities and activities with drones, but they were just tools to engage these girls to enable us to put strong female role models in front of them and to have conversations and activities around leadership and confidence building,” Mead explains.

“A lot of the activities were designed to have those themes. You would see a big group of girls being split up into smaller groups by age or ability and then doing some baseball training with the baseball coaches who are all ex Australian Women's Team members. You would see them going off and doing some drone activities and learning about that technology, flying micro drones and coding the drones.

“But what you probably wouldn't see or hear is the conversations going on between the girls, and the confidence being built inside themselves, and them walking away going, ‘Oh, wow, that was awesome. I know I can do this now.’ Also the change within the associations over there giving the girls more opportunities.”
Also, he says the baseball training has delivered very tangible results. “Girls over there can now reach the highest level of baseball. They recently took a national women's team to the Asian Cup and got their first ranking points. So we've gone from girls not being able to play baseball in Indonesia beyond the age of 14 in 2016 to taking a national woman's team to the Asian Cup in 2023 and getting their first ranking points.”




Social media is without doubt the hottest topic for parents with tweens/teens. Today, social media platforms play a significant role in the lives of young people. Among these platforms, Snapchat stands out as a popular choice for sharing moments through photos and videos. However, before allowing their child to create a Snapchat account, it is up to parents to be well-informed about the platform, its features and its privacy implications, and to establish healthy boundaries and guidelines for its use.
Snapchat is a multimedia messaging app that allows users to send photos and short videos, referred to as ‘Snaps’, which disappear after being viewed. It also features Stories, where users can share a collection of Snaps that remain visible for 24 hours. While Snapchat encourages creative and visual communication, it is important for parents to realise that the short-lived nature of content does not necessarily mean it is entirely private or free from risks.
Before you let your child create a Snapchat account, you need to have an open and honest conversation about responsible social media use. Be sure to discuss both the positives and drawbacks of sharing personal moments online. Chat about topics such as cyberbullying, privacy and the importance of treating others with respect. Encourage your child to think before they share (Use the Nana rule: ‘would I be happy if Nana saw this?’). Remind them that the digital content they share can have lasting consequences, and that they are continually adding to their digital footprint.
Snapchat offers several privacy settings that parents and their children should explore together. These settings include:
1. Friends Only: Adjust the privacy settings to ensure only approved friends can view your child's content.
2. Ghost Mode: Enable Ghost Mode on the Snap Map to prevent your child's location from being shared with others.
3. Quick Add: Disable Quick Add to prevent random users from seeing your child's profile as a suggested friend.
4. Message Controls: Configure who can send your child messages and view their Stories to create a more controlled online environment.
Snapchat has introduced a Family Center feature designed to help parents stay informed about their child's activity on the platform. Through the Family Center parents can link their account to their child’s and access information about their child’s friend list, privacy settings and recent activity.
This provides an additional layer of oversight and encourages a sense of transparency. It is important to explain to your child why you are using Family Center and what it does. As part of the Family Center setup you need to invite your child to link their account. It is possible for your child to unlink their account at any time. You will receive an alert when this occurs, but it is important to first discuss with your child what will happen if they do unlink their account from yours.

Establishing clear boundaries is crucial when it comes to social media use. Talk with your child to set guidelines for their Snapchat usage:

1. Time limits: agree on a reasonable amount of time your child can spend on Snapchat daily. Excessive screen time can impact their mental and emotional wellbeing.
2. Content guidelines: discuss appropriate content to share, and the potential consequences of sharing inappropriate or sensitive material.
3. Online interactions: teach your child to recognise signs of cyberbullying and encourage them to bring anything they are concerned about to you so you can guide them and, if necessary, report it via the appropriate channels.
4. Offline engagement: emphasise the importance of balancing online interactions with real-world relationships and activities.
5. Digital footprint: help your child understand that their online actions contribute to their digital footprint, which can impact their future.
Snapchat can be a fun and creative platform on which your child can express themselves and connect with friends. However, it is crucial to be actively involved in your child's online journey. Have frequent open conversations, set clear boundaries, review them when necessary, and explore privacy settings together. By fostering a supportive and informed environment you can help your children make responsible choices while navigating the world of social media.
www.linkedin.com/in/nicolle-embra-804259122
www.linkedin.com/company/the-cyber-safety-tech-mum
www.thetechmum.com
www.facebook.com/TheTechMum
www.pinterest.com.au/thetechmum

 ELENA YAKOVLEVA
ELENA YAKOVLEVA
Role models can be a great source of inspiration, so we’d like you to share the story of your cybersecurity career to date with readers of Women in Security and inspire other young women to investigate and, hopefully, embark on training for a career in cybersecurity. Tell us what you are doing today. Today, I am a student in the Purple Team Australia program. This remarkable program has been specifically designed and developed to address the critical shortage of cyber skills while actively promoting diversity in the workplace. It aims to empower and upskill women and First Nation Australians, providing them with the necessary tools to embark on a rewarding journey in cybersecurity.
The Purple Team Australia Program goes beyond theoretical knowledge. It places a strong emphasis on practical experience, allowing students like me to apply what we’ve learned to real-world scenarios. Through a series of step-by-step practical activities and critical thinking challenges we gain valuable hands-on experience. The program’s ultimate goal is to prepare us for entry-level cybersecurity positions and ensure a successful transition into our new careers.
I am grateful for this incredible opportunity and eagerly anticipate the Employment Match process at the completion of the training program. It offers the chance to secure an entry-level cybersecurity position, marking the beginning of an exciting new chapter in my career.
What exactly is the course you are undertaking? Is it full or part time, How long have you been doing it? When do you expect to complete it? And how did you get there?
Purple Team Australia offers a flexible, self paced online program. Before joining this program, I successfully completed a full-time, campus-based journey to achieve my goal of transitioning from

a career as a business trainer and assessor to a career in cybersecurity. During this time, I obtained a Certificate III in IT and a Certificate IV in Cyber Security through TAFE NSW, which provided me with the foundational knowledge and skills necessary for this transition. I graduated from TAFE NSW on 24 June and immediately began the Purple Team Australia program.
The TAFE course was government-subsidised and allowed me to pursue my studies without any fees. To fully commit to my studies at TAFE I had to step away from my role as a business trainer and assessor in which I was responsible for delivering Certificate IV and Diploma in Leadership and Management courses.
The cybersecurity industry has traditionally divided professionals into ‘blue team’ for defensive roles and ‘red team’ for offensive roles. However, at Purple Team Australia blue and red teams come together to protect Australia against cyber-attacks and strengthen our cybersecurity.
This program offers a dynamic learning experience that combines theory and hands-on practice. With online instructor-led sessions, insightful guest speakers from the industry, and regular mentoring sessions, I am being prepared to enter the workforce as a skilled cybersecurity professional.
The program is structured into five units, with one unit being covered per month. The first unit was delivered through the University of Tasmania. In the upcoming unit we will delve into Linux, which I am eagerly looking forward to as it promises more hands-on practical experience and technical knowledge.
Communication among the students in the program is facilitated through Slack which provides a platform for collaboration and support. One of the challenges I have encountered is finding the time to balance the course with other commitments because it a part-
time course requiring a commitment of around 10 hours per week.
Regarding improvements or changes, I must say that the course has been performing at a very high level, and I do not have any specific suggestions for improvement. Overall, I find the program to be well-designed and comprehensive, providing valuable learning opportunities in cybersecurity. I am thoroughly enjoying the course and am grateful for the opportunity to be part of it.
Since starting the program on 26 June 2023 I have been fully immersed in its content. With a commitment of at least 10 hours per week, I have been able to delve into fascinating topics and acquire practical skills that are in high demand.
Most of the program is delivered online through a user-friendly learning management system, but we also have engaging in-person sessions conducted by instructors in each state. And we will have the opportunity to come together in Canberra for a memorable graduation event.
The highlight of this program is the emphasis on practical experience. At every step we are given chances to apply what we learn to real-world scenarios. The program is structured around three units: IT Essentials, Blue Team and Red Team. But we will also participate in an exciting in-person Purple Team activity where we will collaborate as a team and showcase the skills we have developed throughout the program.
Getting into this program was no small feat. After applying earlier this year, I went through a series of assessments and interviews. It was a tremendous honour to be selected from a pool of talented applicants. I believe my commitment, enthusiasm and passion for learning and career transition played a significant role in securing my spot.
Almost every aspect of cybersecurity is evolving rapidly. Do you feel your course is doing enough to keep up? Are there topics you would like to see covered, or topics you think should be omitted?
I have found that both my previous course at TAFE and the Purple Team Australia program have been effective in keeping up with the rapid evolution of cybersecurity. The teachers and instructors have demonstrated excellent industry knowledge, ensuring the course content remains up to date. The resources and equipment provided, including high-quality computers, have further enhanced the learning experience.
While the courses have been comprehensive, I believe it would have been beneficial to include additional topics related to current government initiatives in cybersecurity. For instance, incorporating insights from Minister for Cyber Security, Claire O’Neil, the Australian Signals Directorate (ASD) and the Australian Cyber Security Centre (ACSC) could provide valuable perspectives and real-world context. Furthermore, learning from recent cyber attacks that have occurred in Australia would provide practical insights into the everchanging threat landscape.
When you complete your course and gain your qualification, what next? Do you have a clear vision of a role it will help you attain, or, if you are already in work, is it something you feel will help you do your job better and, hopefully, gain a promotion?
The Purple Team Australia program holds great promise because it includes a job matching process, which I am eagerly looking forward to. My goal is to secure a position within a government organisation where I can leverage my communication skills, stakeholder management abilities and project management expertise.
In terms of specific roles, I am keen on pursuing non technical positions in areas such as governance, risk and compliance (GRC), threat intelligence, training and awareness, or a role as a business information security officer. These roles align with my strengths and interests, and I believe they will allow me to make a meaningful impact in cybersecurity.
Throughout the Purple Team Australia program, all our actions as students are closely monitored by our mentors and these records will be compiled into an employment file. This file will serve as a valuable resource during the job matching process at the end of the program.
Were you inspired by cybersecurity in high school, if so, how? Or was it a later employment role that led you there?
When I moved to Australia in 2015, the first two years were dedicated to starting a family and raising my children. My initial job in Australia was as a business trainer and assessor in a couple of registered training organisations in Sydney and Parramatta. I was enjoying success in this role until a casual encounter with my next-door neighbour changed everything.
During a conversation I asked my neighbour about her occupation and she mentioned she was studying to get a job in cybersecurity. I was genuinely amazed and expressed my belief that I could not pursue such a career because I had no background or knowledge in that field. However, my neighbour swiftly dispelled my doubts by explaining that there are non-technical roles within cybersecurity requiring a general understanding and a high-level vision of things. Her encouragement prompted me to take a closer look at this intriguing industry, and I will be forever grateful to her.
At the time we met, I was also managing a strata property, dealing with the complexities of relationships between builder, strata managers,
tenants and the owners’ corporation. My neighbour recognised my ability to get things done and complete tasks and she saw potential in me. Although teaching was fulfilling, I yearned for a new career where I could grow and thrive. Cybersecurity, with its prominence and relevance, seemed like an exciting field to explore.
As I searched for cybersecurity training I encountered numerous options and lucrative job opportunities, so I had difficulty making a choice. However, through diligent research, I stumbled upon TAFE and discovered they offered formal training in cybersecurity and that the course was fully subsidised by the government. This realisation sealed the deal, and I enrolled at TAFE in 2022.
The journey that led me to TAFE and later on to Purple Team Australia has been filled with unexpected turns. I am grateful for the friend who opened my eyes to new possibilities and for the opportunity to pursue a career that aligns with my interests and offers room for growth and prosperity.
What reaction did you get from family and friends when you decided to pursue cybersecurity?
When I made the decision to pursue a career in cybersecurity, I was fortunate to have unwavering support from both my family and friends. My husband, who is my rock, has been incredibly supportive and excited about this new chapter in my life. We had discussions around the family table and he wholeheartedly agreed that taking a career break from teaching and becoming a full-time student was the right decision for me. We understood it might come with some initial constraints, but we were confident the long term benefits and career opportunities would make it worthwhile.
My family overseas has always been incredibly supportive, especially my mother. She has consistently shown trust in my choices and believes
in my ability to make the right decisions for my future.
As a mother myself I was driven not only by my personal ambitions but also by a desire to be a positive role model for my young sons. I wanted to show them that pursuing a career in cybersecurity can be exciting and empowering at any age and I wanted to demonstrate to them the importance of technology and its responsible use. The idea of being able to engage in fancy hacking and cutting-edge security measures sparked their curiosity.
Please give us a brief rundown of your career to date. The jobs you have had, where and when, in cybersecurity and other fields. Don’t forget to tell us where you were born, where you grew up and where you live today.
I was born in Russia, which was a part of the Soviet Union. I had a challenging childhood due to a disability. I underwent multiple spinal surgeries and have had titanium rods in my spine since the age of 11. Because of my disability I was bedridden for several months and received home schooling. This was in the pre-internet era and presented some challenges. As a teenager my opportunities were limited, but I decided to take charge of my life and strive for something different.
I dedicated myself to my studies, working hard to enter a prestigious university, which I graduated from successfully. During my time as a student, I was fortunate to have the opportunity to travel to the United States as part of a work and travel program. I lived with a host family in Florida and gained exposure to the Western world, different cultures, traditions and values. I formed strong connections with my American host family and we remain good friends to this day.
Upon returning to Russia, I embarked on various career paths. I worked as a translator in Ghana and
Côte d’Ivoire, assisting with high-level translations for the Chamber of Commerce and Industrialists. Subsequently, I worked as a paralegal in a law firm in Moscow. I then transitioned to a role in an Austrian company that provided toll solutions, where I presented the company’s product portfolio to Russian government bodies, gaining valuable experience in engaging with individuals in positions of authority and the business world.
In addition to my corporate work, I established my own translation and interpretation services business catering to clients across different countries. I specialised in military and economic security, political affairs, international affairs and more. As a team of talented professionals we collaborated on various translation projects including high-level interpretation assignments with clients ranging from government entities to the Pentagon.
Continuing my educational journey, I gained my MBA from Durham University in the United Kingdom. Following that, my husband, child and I relocated to Sydney as skilled migrants where I had the privilege of welcoming my second child into the world, and my journey in Australia began. My first job in Australia was in an registered training organisation and marked a new chapter in my career.
My career path has been diverse, encompassing various fields and countries, each contributing to my growth as a professional. The challenges I faced in my early years shaped my determination and resilience, propelling me to seek new opportunities and excel in different industries.
And please, mention anyone who has been particularly influential in your journey. Throughout my journey several individuals have played a significant role in influencing and guiding me. First and foremost, I am immensely grateful to my next-door neighbour, Hari Priyanka, who showed
me that career transitions are indeed possible. Her belief in me and our friendship have been invaluable, inspiring me to pursue new opportunities.
During my time at TAFE I was fortunate to have talented teachers who imparted their knowledge and expertise, shaping my understanding of cybersecurity. Their guidance and support helped me navigate the complexities of the field and fuelled my passion for continuous learning.
Additionally, my group mates at TAFE provided a supportive and collaborative environment. We motivated and pushed each other to achieve our goals, fostering a sense of camaraderie throughout our studies.
As I embarked on my cybersecurity journey I had the privilege of being mentored by William Shipway and Nilay Sangani, both esteemed experts in the field. Their clear guidance, wealth of knowledge and unwavering support have been instrumental in shaping my path and keeping me motivated to excel.
I am grateful to all these influential individuals who have believed in me, shared their wisdom and supported me along the way. Their impact on my journey has been immeasurable, and I am thankful for their continued guidance and inspiration.
It takes much more than cybersecurity expertise to be a good cybersecurity professional. In most roles people skills are essential. There is also the ability to be creative, to ‘think outside the box’. Do you plan to undertake, or are you already undertaking, training in disciplines other than cybersecurity to support your career plans?
Absolutely! I am fully aware that being a successful cybersecurity professional requires more than just technical expertise. People skills and the ability to think creatively and outside the box are essential in
most roles. While I already possess strong people skills, I am eager to undertake additional training or take learning opportunities to further enhance my skillset as required by future employers.
I firmly believe my ability to solve problems and think creatively has been demonstrated in various situations. For instance, during my time as the chairperson/secretary of the owners’ corporation of a strata plan, the owners faced a significant legal challenge. With differing opinions on how to proceed I was able to propose a course of action that ultimately led to our victory over a major strata law firm. This success was a result of my research skills, creative thinking and willingness to explore unconventional approaches.
Therefore, I am confident in my ability to think critically and produce innovative solutions. However, I recognise the importance of continuously developing my technical skills and expanding my knowledge in areas beyond cybersecurity. I am ready and willing to undertake training or pursue learning opportunities that will support my career plans and contribute to my overall professional growth.
qualifications such as those offered by (ISC)², CompTIA and ISACA, Have you gained, or do you plan to gain any of these, if so which ones and why?
Certainly! I am fully committed to obtaining specific cybersecurity qualifications offered by such organisations. However, my plan is to pursue these certifications once I secure my first job in cybersecurity. I believe gaining these qualifications will enhance my professional profile and open doors to broader opportunities within the industry.
Please tell us about your experience of being a woman studying cybersecurity. Chances are you are in a minority. Do you feel
disadvantaged? Have you encountered sexism or misogyny? Do you feel your institution does sufficient to address such issues?
Indeed, I was in the minority as a woman studying cybersecurity at TAFE. In a group of 15 students there were only five women, and only two of us made it through to the end of the course. Because it was a full-time program, many women faced challenges due to family commitments, which affected their ability to complete the course.
However, I am grateful that, throughout my experience, I have never felt any disadvantages or encountered instances of sexism or misogyny. I have always been treated with respect and fairness, and my work ethic has been valued and recognised.
In terms of my current institution, the Purple Team Australia program is predominantly for women, which further reinforces a supportive and inclusive environment. As a result, I do not feel any sense of disadvantage based on my gender.
While it is essential for institutions to address issues related to gender diversity and promote inclusivity, I can confidently say that both TAFE and my current program have fostered an environment where individuals are respected and valued on the basis of their skills and contributions, regardless of gender.
Educational institutions, especially universities—the ‘ivory towers’—are often seen as being out of touch with the real world. If you are not already immersed in the broader world of cybersecurity you will be part of when you complete your study, what are you doing to prepare yourself for that transition, for example by joining industry bodies like the Australian Women in Security Network (AWSN).
During my time studying at TAFE I took the initiative to apply for membership of the Australian
Women in Security Network (AWSN), an incredible organisation that supports and empowers women in cybersecurity. As a member I have had the opportunity to attend numerous events, network with professionals in the industry and establish connections with mentors who have been guiding me throughout my journey.
Additionally, I am a member of the Australian Information Security Association (AISA), which has provided me with another avenue to engage with the cybersecurity community and stay updated on industry trends and developments. Being part of these industry bodies has allowed me to connect with like-minded professionals, gain valuable insights, and prepare myself for the transition into the broader world of cybersecurity.
By actively participating in these organisations and engaging with industry professionals I am proactively preparing myself to bridge the gap between educational institutions and the practical aspects of cybersecurity. These memberships have provided me with an excellent platform to learn, grow and establish a strong network within the industry.
And finally, having come this far, do you have any regrets. If you had your time again, would you take a different path?
I can confidently say I have no regrets about the path I have chosen. Pursuing a career in cybersecurity has been a fulfilling and rewarding journey for me. If given the opportunity to start over I would undoubtedly make the same choice again. This is exactly what I wanted to do, and I am grateful for the experiences, growth and opportunities that have come my way. Thank you.
www.linkedin.com/in/elenayakovlevacyber
LiFang Wei was born and raised in China. She came to Australia in 2018 and now lives in Perth.

Masters in Cybersecurity Student at Edith Cowan University
Are you in full or part-time study? Where?
What exactly is the course you are undertaking? How long have you been doing it? When do you expect to complete it? And how did you get there?
Currently, I am engrossed in the pursuit of a full-time master’s degree in cybersecurity at Edith Cowan University (ECU). I started my course in February 2022 and expect to complete it by the end of 2023. I have always been fascinated by the ever-evolving challenges in cybersecurity, and this fascination drove me to pursue this path.
I made the decision to come to Australia for my postgraduate studies. I arrived here in October 2018 on a working holiday with the intention of earning enough to cover my tuition fees and living expenses for two to three years at university. From 2018 to 2021 I travelled around Australia, had lots of interesting experiences, and met a large group of likeminded people.
In parallel with my exploratory travels I researched universities offering cybersecurity programs. My quest for the ideal institution led me to ECU, an establishment that resonated strongly with my academic aspirations and personal preferences. In retrospect, choosing ECU proved to be a wise decision. I have enjoyed rich and insightful learning experiences since enrolling in their cybersecurity program.
Reflecting upon my journey thus far, I am grateful for every experience, be it the thrill of exploration across Australia, the enriching encounters, or the rigorous academic path. They have collectively shaped my present and will indubitably continue to influence my future pursuits in cybersecurity.
Were you inspired by cybersecurity in high school, if so, how? Or was it a later
employment role that led you there? What reaction did you get from family and friends when you decided to pursue cybersecurity?
My interest in cybersecurity was sparked during my time as a post-production effects artist at an animation company in China. In 2017 this company was attacked by ransomware and lost a lot of money. This incident made me realise the importance of cybersecurity in the information age. Cybersecurity threats can have a negative impact on the economy, society and individuals.
In today’s digitised world the concept of cybercrimeas-a-service is evolving, empowered by cutting edge technologies that can be leveraged by hackers to conduct complex and destructive attacks. Recognising the immense potential and vast scope of the IT industry, particularly the cybersecurity sector, led me to re-evaluate my career trajectory. As I matured I realised cybersecurity offered a stable profession with promising prospects, so I decided to redirect my career path.
This decision led me into the world of computer networks where I took the initiative to acquire foundational knowledge in Python programming through online resources. This equipped me with the essential skills to excel academically at ECU.
The decision to specialise in cybersecurity was met with an exhilarating mix of anticipation and intrigue from my family and friends. They have been my unwavering pillars of support every step of the way. As a cherished daughter my parents have always shown me the utmost respect and tolerance, seldom intervening in my decisions. Even though the idea of me moving to a foreign country for my studies initially sparked concern, they eventually rallied behind me, encouraging me to chase my dreams and realise my ambitions.
Please give us a brief rundown of your career to date. The jobs you have had, where and when, in cybersecurity and other fields. And please, mention anyone who has been particularly influential in your journey. I have an adventurous personality and enjoy creating surprises in my life: the unknown always attracts me. Consequently, I am passionate about exploring different areas in my career. In 2013 I completed my bachelor’s degree in art design in China. After graduating I tried several roles in China, from newspaper journalist and editor to animation post effects artist and short video editor.
During my two years at a newspaper I developed the ability to identify hot news topics and learn how to communicate with people from various social classes and professional backgrounds to uncover their stories. In the three years I worked at an animation company, I learned to use postproduction software such as Adobe After Effects, Adobe Premiere Pro, Photoshop and Maya. I have also experimented with short video script writing, filming and editing. I am constantly expanding my potential by learning from new professions I have not been exposed to previously. I enjoy the sense of achievement that comes with mastering new skills.
Since my arrival in Australia I have had the opportunity to explore various roles such as barista, kitchen assistant, cook, bar attendant and retail sales assistant. While these positions may seem unrelated to my current pursuit of cybersecurity, they were instrumental in providing me with valuable life skills, a broader perspective and, crucially, funding my tuition.
The year my life took an exciting turn when I joined KZ Code Education as a coding teacher. This role not only allowed me to hone my programming knowledge but also gave me a platform to inspire young minds
in the fascinating world of coding. Subsequently, I joined Vinnies as an IT volunteer which further developed my ICT skills and provided me with handson experience in troubleshooting, enhancing my problem-solving abilities.
Most recently, I secured an internship with the ICT team at Perth College. This role fills me with immense excitement as I anticipate the chance to integrate my cybersecurity knowledge and skills into a professional environment, driving realworld impact.
Throughout this journey I have been privileged to have my best friend, Winnie Zhao, by my side. Arriving in Australia with limited language skills and no income was quite a challenge. However, Winnie graciously offered me a place to stay, shared valuable job information, and even mentored my English studies. Her selfless support has been pivotal in navigating the many hurdles that stood between me and my current position.
Looking back, my journey has been marked by diverse experiences, continuous learning and supportive relationships. Each role I have held and every individual I have met has contributed to shaping the professional I am today.
When you complete your course and gain your qualification, what next? Do you have a clear vision of a role it will help you attain, or, if you are already in work, is it something you feel will help you do your job better and, hopefully, gain a promotion?
Once I complete my course and gain my qualification I hope to continue to contribute at Perth College. My aim is to increase my professional skills by applying the theoretical knowledge I have gained in a real-world setting. I believe my academic qualification could serve as a steppingstone, paving
the way for my transition from an intern to a full-time employee, thereby enabling me to make meaningful contributions to cybersecurity.
It takes much more than cybersecurity expertise to be a good cybersecurity professional. In most roles people skills are essential. There is also the ability to be creative, to ‘think outside the box’. Do you plan to undertake, or are you already undertaking, training in disciplines other than cybersecurity to support your career plans?
Alongside my cybersecurity studies I am focusing on improving my interpersonal skills and nurturing my creativity, which I believe are equally crucial in this field.
The skills in art design gained during my undergraduate years have played a significant role in fostering my creativity. This degree inculcated a habit of approaching problems from multiple angles and devising innovative solutions. These skills were further enriched by my professional experience in the news media and animation industries.
Meanwhile, my most recent positions have served as vital training opportunities. I have been working as an IT volunteer at Vinnies since May. My primary role involves reconfiguring laptops. It is a task requiring attention to detail, technical knowledge and strong problem-solving abilities. I document every laptop I work on, keeping detailed records of specifications, issues encountered, troubleshooting steps and solutions. This practice bolsters my troubleshooting skills and maintains inventory accuracy.
This role has underscored the importance of effective team communication because we constantly exchange updates and innovative ideas in a collaborative setting.
Simultaneously, I have been working as a coding teacher at KZ Code Education. In this role I prepare coding materials tailored to different age groups, a process that has fine tuned my programming skills. Also, simplifying complex technical concepts for young students has significantly enhanced my communication skills.
In my leisure time I delve into reading, with a particular penchant for science fiction and mystery novels. These genres stimulate my creative thinking and encourage me to envision future possibilities in my field.
Overall, these experiences have equipped me with an array of indispensable skills and insights that are integral to thriving as a cybersecurity professional.
What about specific cybersecurity qualifications such as those offered by (ISC)², CompTIA and ISACA, Have you gained, or do you plan to gain any of these, if so which ones and why?
I am preparing for the AWS Certified Cloud Practitioner examination. Once I have gained this qualification my goal is to further strengthen my capabilities by acquiring additional cybersecurity credentials such as the AWS Certified Solutions Architect and (ISC)² Certified in Cybersecurity.
My decision to gain these qualifications was triggered by a realisation that the cybersecurity field is replete with remarkably skilled peers. To keep pace and ensure I do not lag behind I am driven to continually improve and expand my expertise. I recently attended the Tesserent Academy 100 Challenge training, a rigorous five day event orchestrated by Tesserent. This training shed light on the areas of professional competency I need to bolster and solidified my resolve to delve deeper into the multifaceted realm of cybersecurity.
And of course we’d like to hear about the specifics of your current course. Please give us a few details of what you are studying. What do you enjoy? What do you find challenging? What would you like to see done differently?
The cybersecurity course at ECU has a strong emphasis on the application of contemporary and emerging technologies, including ethical hacking and defence, digital forensics and data analysis and visualisation.
Upon completion of this course I will be able to develop computer programs in several contemporary scripting and programming languages and apply advanced technical strategies to investigate complex concepts in cybersecurity. In addition, I will be able to apply communication skills to demonstrate innovative methods and solutions, contribute to addressing cybersecurity issues and use highlevel self-management skills to initiate, plan and execute a complex cybersecurity research paper or professional project.
In my current course the subjects of governance, risk and compliance (GRC) and digital forensics capture my interest. I find GRC fascinating as it provides a strategic outlook on cybersecurity, an element integral to shaping an organisation’s security posture. Furthermore, the challenge of instituting solid governance structures and identifying and mitigating risks greatly appeals to me.
However, I encounter some difficulty when it comes to the unit on data analysis and visualisation. This module requires a solid foundation in mathematics and proficiency in data organisation skills, two realms that, frankly, have often tested my capabilities.
In terms of course improvements, I believe there could be greater emphasis on practical elements and
real-world scenarios in the curriculum. Technical, analytical and problem-solving skills in cybersecurity are required to understand technology, the psychology of cybercriminals and to stay ahead of the threats and make the cyber world a safer place.
Almost every aspect of cybersecurity is evolving rapidly. Do you feel your course is doing enough to keep up? Are there topics you would like to see covered, or topics you think should be omitted?
In my view the curriculum at ECU stays abreast with cutting edge cybersecurity technology. However, one component that could be improved is programming instruction. The current course focuses on a scripting language (Bash), which is not particularly applicable to cybersecurity. Including programming languages like Python or Java in the curriculum could be immensely beneficial.
Additionally, with the advent of technologies such as AI, IoT and cloud computing, the landscape of potential threats has expanded exponentially. This makes cybersecurity more pivotal than ever. In this context I feel incorporating content related to quantum computing could give us an edge, and prepare us for the emerging challenges of the digital future.
Please tell us about your experience of being a woman studying cybersecurity. Chances are you are in the minority. Do you feel disadvantaged? Have you encountered sexism or misogyny? Do you feel your institution does sufficient to address such issues?
Edith Cowan University, named after its influential female founder, continues to uphold her commitment to higher education. It’s heartening to witness the university’s emphasis on gender parity, as evidenced by the large number of female employees and the
near-even split of male and female students in my class. As a woman in cybersecurity my experience at ECU has been one of inclusivity and respect. I have not faced any disadvantage or encountered any form of sexism.
However, it is essential to acknowledge that the need for improvement and continuous dialogue always exists, and to address issues more comprehensively. Recognising this, I joined the Australian Women in Security Network (AWSN). My intent is to contribute to the growth of women in the cybersecurity industry and to champion women’s rights in the workplace, thereby sustaining the legacy of trailblazers like Edith Cowan.
Educational institutions, especially universities — the ‘ivory towers’ — are often seen as being out of touch with real work. If you are not already immersed in the broader world of cybersecurity you will be part of when you complete your study, what are you doing to prepare yourself for that transition, for example by joining industry bodies like the Australian Women in Security Network (AWSN)?
I’ve been afforded an internship opportunity with the Perth College ICT team, which will give me a foothold in cybersecurity. My work experience as an IT volunteer and coding teacher has taught me the importance of collaboration and communication skills. These abilities will enable me to contribute meaningfully to Perth College and learn from industry experts in the ICT team.
Upon graduating I plan to enrol in the ACS Professional Year Program (ICT). This course is designed to seamlessly bridge the gap between academic study and professional employment. It aims to equip participants like me with practical job skills and training, enhancing our career prospects
and ensuring our readiness for the competitive job market.
To further increase my professional preparation I have actively engaged in industry events and have become proudly associated with AWSN and AISA. I believe these proactive steps will ensure a smooth transition from academic life into the professional world.
And finally, having come this far, do you have any regrets? If you had your time again, would you take a different path?
Looking back on my journey, I harbour a twinge of regret: had I immersed myself in more industry events, applied for vacation programs and set my sights on long-term employment prospects from the first semester my progress might have outpaced my current rate. Regrettably, my academic focus was so intense I neglected to contemplate the broader picture and the future.
Given another chance, I would recalibrate the balance between my academic and professional endeavours, crafting a clear, deliberate career plan as a roadmap to loftier professional heights.
www.linkedin.com/in/lifangw


Content allows you to establish, share, and strengthen your brand. It helps build relationships which is why we are shining the light on our content service.
Content strategies don’t just define the goals your content is intended to achieve, but also the procedure, processes and governance required to get there. We can show you how to manage your content effectively .
We can then use that content to attract, acquire and engage your customer and new prospects, deepening your relationships


What are you waiting for?
REACH OUT TODAY
Chisom Uchechukwu Elekwa was born and still lives in Abuja in Nigeria and is studying medical radiography at the University of Nigeria in Nsukka, Enugu State. She is due to complete her course in 2024 and is also studying cybersecurity full time.

Medical Radiography student at the University of Nigeria and Cybersecurity student at Cybersafe Foundation
Were you inspired by cybersecurity in high school, if so, how? Or was it a later employment role that led you there? What reaction did you get from family and friends when you decided to pursue cybersecurity?
Although I do not have a technological background, I have keen interest in cybersecurity and I’m presently taking a full-time training as a cloud security engineer at Cybersafe Foundation. I applied for the training last year and was accepted. The course runs for seven months and I am four months in, so I should have completed it by November.
I got to know about cybersecurity in 2022 from a friend (Glory Agu). She encouraged me to do some research and take the cybersecurity course on Simplilearn. After doing so, I became more interested in cybersecurity and began pursuing my passion. I got to know about Cybersafe Foundation from her and followed that organisation closely.
I took several courses online covering the foundations of cybersecurity. I took the Linux Unhatched course, joined bootcamps (including one organised by Tech4Dev) and also obtained the ICTTF Cyber Risk Certification from a boot camp organised by the International Cyber Threat Task Force (ICTTF). I joined communities where I’ve volunteered for various roles and activities. I’ve taken the opportunity to speak at a cybersecurity event and, to crown it all, I was accepted into Cybersafe Foundation as a CyberGirl to learn cybersecurity.
My journey as a CyberGirl has been filled with learning. From taking the Junior Cybersecurity Analyst course from Cisco, to learning about identity and access management and Linux on Infosec Skills, to learning about Active Directory, Windows operating systems and ITIL 4. Accompanying all this learning were multiple assessments, which I aced.
After this generalised learning, I was qualified to specialise in a specific cybersecurity path and I chose cloud security. So far I’ve taken the Microsoft Azure Fundamentals course and passed the AZ 900 exam brilliantly. I have completed the Certificate of Cloud Security Knowledge (CCSK) foundational course designed by the Cloud Security Alliance (CSA). Currently, I’m taking the AWS Cloud Practitioner Essentials course on the AWS platform.
I’m glad to say I have enjoyed an enormous amount of support from my family and friends, especially after a video interview about my cybersecurity journey was featured on Dr Ronke Babajide’s YouTube channel (Women in Technology Spotlight).
Please give us a brief rundown of your career to date. The jobs you have had, where and when, in cybersecurity and other fields. And please, mention anyone who has been particularly influential in your journey. Several people have directly influenced me on my career journey, and I am grateful to them. They include the Executive Director of the Cybersafe Foundation, Confidence Staveley. Bukunmi Ojo’s guidance has had a great impact to me. My various tutors left no stone unturned when dispensing knowledge. Personalities like Segun Ebenezer Olaniyan, Peter Odey, Janet Njoku and Oreoluwa Jetawo, and friends have helped me in various ways.
There are also people I admire whose actions have pushed me to greater heights. They include Iretioluwa Akerele, Simbiat Sadiq, Chukwudi Theodore, Dr Obadare Peter Adewale, Dr Fene Osakwe, Tayvion Payton, Day Johnson, Olivia Rose and Zinet Kemal.
Although I have not yet gained a job in cybersecurity, I have been taking lab work while studying. I have also been involved in some research and project work. This has included:
• Working on a project to help a company implement endpoint security measures.
• Carrying out research on various APT threat actors, their tactics, techniques and protocols.
• Research on various cyber threats and the government’s regulatory role.
When you complete your course and gain your qualification, what next? Do you have a clear vision of a role it will help you attain, or, if you are already in work, is it something you feel will help you do your job better and, hopefully, gain a promotion?
Considering the intense training we undergo at Cybersafe Foundation and the plethora of information and knowledge I am gaining, I am certain I will be ready for entry-level roles when I am done with my cloud security training in a few months. I am hoping to gain an entry-level cloud security engineer role immediately Fingers crossed!
It takes much more than cybersecurity expertise to be a good cybersecurity professional. In most roles people skills are essential. There is also the ability to be creative, to ‘think outside the box’. Do you plan to undertake, or are you already undertaking, training in disciplines other than cybersecurity to support your career plans?
I’m currently not taking any other training but, amazingly, Cybersafe Foundation affords its students the opportunity to grow their interpersonal skills. The CyberGirls program has women from more than 22 African countries coming together to learn about cybersecurity. It gets them working together on various projects, helping them develop great soft skills.
Personally, I have been able to gain soft skills like team collaboration, problem solving, communication, critical thinking and leadership skills which I’ve exercised while doing project work to see that deadlines are met and that the work is accurate.
We’re also encouraged to be visible on LinkedIn. Frequently posting on LinkedIn has enabled me to improve my writing skills. I recently completed a consistency challenge on LinkedIn by posting for 25 consecutive days on cloud security related concepts. I hash tagged it #25DaysCloudSecurity.
Also, coming from a medical background, there are a number of transferrable skills I possess that will be very useful in my cybersecurity career; skills like attention to detail. This is key in radiology because failure to pay attention to details could expose patients to unnecessary radiation. Also, adaptability. The medical field improves continually, as does the cybersecurity field. The ability to be ready to learn and unlearn is key to staying current, and these skills I possess. I also have good ethical awareness skills, which I have demonstrated when handling patients’ confidential information and by adhering to strict hospital rules and regulations. Lastly, having to interact daily with patients, colleagues, superiors and nurses has enabled me to build great communication and listening skills. I have also taken the Jobberman Soft Skills certification course.
qualifications such as those offered by (ISC)², CompTIA, and ISACA, Have you gained, or do you plan to gain any of these, if so which ones and why?
The cybersecurity industry is big on certifications and gaining some of these can be a game changer in any cybersecurity career. However most of the recognised certifications are costly to acquire.
I have plans to gain some certifications. I am hoping to gain the CompTIA Sec+ certification soon and also some cloud security certifications. As part of my training at CyberSafe Foundation I will also obtain vendor specific cybersecurity certifications from Microsoft and AWS. As I progress in my career, I also plan to take the CCSK and CCSP certification exams.
And of course we’d like to hear about the specifics of your current course. Please give us a few details of what you are studying. What do you enjoy? What do you find challenging? What would you like to see done differently?
I’m specialising in cloud security, which deals with the procedures and technology to secure cloud-based infrastructures and data stored in the cloud. So far, I have learnt about various cloud deployment models: the shared responsibility model, the consumptionbased model, pricing models, service types, and more.
I have also gained a good understanding of, and have practiced, various Microsoft Azure services, including:
Microsoft Azure core services like Storage, VMs, networking and identity and access management with Azure Active Directory. I have gained knowledge of Azure governance including policies, the service trust portal and Azure security, which includes its Security Center, NSGs and firewall, and also monitoring with Azure Monitor and Log Analytics. I also learnt about Azure pricing, subscriptions, cost management and support plans, and I have also interacted with the various tools like the Azure Portal, Azure Cloud Shell and Azure CLI.
In taking the CCSK Foundational course, I learned about: infrastructure security; software defined networks; cloud network security; business continuity and disaster recovery; cloud governance, compliance, and audit; cloud data storage and security; encryption for the various cloud models; securing cloud applications, users, and related technologies; encryption key management; identity and access management; security as a service; big data; internet of things; mobile and serverless security, and more.
Currently, I’m taking learnings on the Amazon Web Services (AWS). So far I have learned about: AWS global infrastructure; AWS services like the Compute service using the Amazon EC2 Instance; Amazon S3 storage service; Amazon EBS and Amazon EFS;
networking services with the Amazon VPC; Subnet; network ACLs; security groups etc, and databases service using the Amazon RDS, Amazon DynamoDB etc, and AWS Database Migration Services.
I’ve understood AWS security services like the Amazon Guard Duty, AWS WAF, Amazon Inspector, identity and access management (IAM), the various monitoring tools on AWS and best practices for securing AWS resources. I have learnt about AWS billing models, cost management tools and strategies for optimising costs in the cloud.
I was intrigued to learn about the pay-as-you-go model of cloud services. I enjoyed learning about the serverless computing services of Azure (Azure Functions) and AWS (AWS Lambda).
I’ve also developed an interest in identity and access management and about how attribute-based access control is better than role-based access control For securing cloud usage.
Cloud security is a really broad field. Before learning about the security aspect of it, you have to understand what cloud computing is about because you need to understand what you are securing. It would be difficult to complete these courses quickly because they are very broad and deep.
From the knowledge I have gained so far, I would say cloud services offer more benefits and security than traditional data centres. I really want to see a time when small businesses will fully adopt the cloud. Most small business owners see such services as being only for the big companies.
Almost every aspect of cybersecurity is evolving rapidly. Do you feel your course is doing enough to keep up? Are there topics you would like to see covered, or topics you think should be omitted?
I would say my training is covering the vast amount of information I will need to step into the real world. This
training also includes hands-on experience to help solidify our technical skills. However, I still draw on other resources to improve my knowledge.
Please tell us about your experience of being a woman studying cybersecurity. Chances are you are in a minority. Do you feel disadvantaged? Have you encountered sexism or misogyny? Do you feel your institution does sufficient to address such issues?
The stereotype of male dominance persists in Africa and this has greatly affected how women are related to and treated. But there is a mindset shift underway and women’s potential is being recognised.
Personally, being a woman in cybersecurity has been an amazing journey. I came into cybersecurity at a time when women were making great strides, and countering the patriarchal mentality. I do not feel disadvantaged in any way, but rather motivated and inspired by the challenges ahead of me.
I have not experienced sexism or misogyny, although I have heard stories of women who have encountered such treatment.
It pleases me to see organisations dedicated to the inclusion of women in technology. One of such is Cybersafe Foundation which I’m learning under. With its CyberGirls Fellowship program—currently hosting it third cohort—the foundation been able to train more than 1000 girls from different African countries in various aspects of cybersecurity. Most of these girls have secured internships and jobs and are excelling.
Educational institutions, especially universities—the ‘ivory towers’—are often seen as being out of touch with the real world. If you are not already immersed in the broader world of cybersecurity you will be part of when you complete your study, what are you doing to prepare yourself for that transition, for example by joining industry
bodies like the Australian Women in Security Network (AWSN)?
As, initially, a self-learner in cybersecurity I have been greatly influenced by the communities I have been part of. Joining communities helped me stay on track, gave me access to resources and helped me understand the scope of cybersecurity. I have also been able to contribute through voluntary work in these communities and gained my first chance to speak publicly on a cybersecurity related topic.
With this experience, and with my genuine desire to one day become an industry leader, I have come to understand the importance of industry bodies. I’m currently a member of ISACA (Information Systems Audit and Control Association). I am working to become a member of more industry bodies by actively networking and gaining meaningful connections, creating visibility for myself on various social media platforms, sharing the knowledge I have gained from studying, and by working towards gaining industry certifications.
And finally, having come this far, do you have any regrets. If you had your time again, would you take a different path?
I certainly have no regrets about being in cybersecurity. I can recall trying to decide what area of technology I wanted to venture into. I wanted something that was significant and had longevity. I am grateful to a dear friend who introduced me to cybersecurity.
I would say I have found purpose in cybersecurity. I would rather be in cybersecurity than any other area of technology. Cybersecurity gives me a sense of relevance and responsibility. As a cybersecurity professional, I cannot shut my eyes or ignore the problems around me because any lack of focus increases the likelihood of a breach. I know I want to be a cybersecurity professional.
www.linkedin.com/in/chisom-elekwa-095075232


Vamika, who was born in India, went to Bahrain when she was four years old. In 2013, she relocated once more with her family to New Zealand in search of a better lifestyle and educational opportunities. Later, she travelled to Australia to pursue a specialised degree course.

Tell us what you are doing today. As the new semester has begun I find myself occupied with an array of assignments. However, the inclination to procrastinate has surfaced and I am concerned that it may affect my progress this time around.
Are you in full or part-time study? Where? What exactly is the course you are undertaking? How long have you been doing it? When do you expect to complete it?
I am currently engaged in full-time study at Deakin University. My chosen course is a four-year double degree program encompassing cybersecurity and criminology. I am in my second year. I anticipate completing the course by late spring of 2025.
And how did you get there? Were you inspired by cybersecurity in high school, if so, how? Or was it a later employment role that led you there? What reaction did you get from family and friends when you decided to pursue cybersecurity?
My initial proclivity was for cryptography. I contemplated taking a mathematics major. I found myself captivated by the novels of Dan Brown and the enigmatic world he created. Although it may appear somewhat juvenile to attribute such a significant life decision to a book, this fascination led me to consider a path in cryptography. However, during high school, my perspective shifted when I participated in a threeday cybersecurity bootcamp.
The experience unveiled the intriguing possibility of merging cryptography with technology via cybersecurity. As an avid enthusiast of truecrime documentaries the prospect of integrating cybersecurity and criminology in my tertiary studies was compelling. After researching available options I discovered Deakin University offered a unique program incorporating both disciplines. So I chose this institution as my academic destination.
During my time studying computer science in high school cybersecurity garnered little interest or attention amongst the girls. Only three others in my year pursued computer science. Consequently, exposure to cybersecurity was limited. This lack of interest among female students served as a catalyst for me to advocate for greater female involvement in STEM related fields, particularly in technology.
Although my decision to pursue cybersecurity and criminology received support from my family and friends, some scepticism lingered within my family circle. Given that no member of my extended family had previously pursued a career in cybersecurity or criminology, my idea of committing to a degree outside the realms of engineering or medicine was greeted with some surprise. Nevertheless, my family remained encouraging and refrained from imposing their own perspectives or ideologies upon my chosen path.
Here is a brief rundown of my career to date. At the age of 16 during my final year of high school I started saving for tertiary studies and sought work experience. I was limited by my rural location but I took positions in retail and hospitality, and refined my adaptability and customer service skills by working at McDonald’s
Following my high school graduation in early 2022 I seized the opportunity to serve as an online part-time tutor for students aged 7 to 14 in Melbourne, teaching mathematics and English. Although lacking formal certification to teach children with learning difficulties, I dedicated extensive efforts to employing interactive methods and creative tools beyond rote learning, such as picture books and modelling clay, to enhance my students’ abilities. My goal was to foster a learning environment conducive to their growth and progress.
After completing my first year as an undergraduate student I worked as an intern with an oil and gas company in my hometown. Over three months I
immersed myself in my role as a data analyst, collaborating with colleagues across departments to comprehend the company’s core operations and the industry landscape.
My primary responsibility involved analysing extensive datasets encompassing driver safety, route frequency, mileage, carbon emissions and location specific hazard zones. I leveraged SQL and Power BI to manage and visualise the data and provide valuable insights. This opportunity allowed me to expand my network and enhance my technological acumen.
Currently, I serve as a casual student ambassador at Deakin University while I seek placements and internships in cybersecurity. It is challenging to secure such positions but my optimism remains steadfast as I persistently explore and apply for opportunities across Australia and New Zealand.
It is challenging to single out any particular individual who significantly influenced my journey towards a career in cybersecurity and criminology. However, the unwavering support and encouragement from my family have been pivotal in my pursuit of these skills. They provided consistent backing, allowing me the freedom to explore my aspirations without imposing their own dreams upon me. Their belief in the value for real-life experiences over traditional classroom-bound education empowered me to set ambitious goals and reach for the highest echelons of achievement.
Furthermore, my sister serves as a pillar of strength and inspiration. Her remarkable educational and professional achievements have always been a source of pride to me, and I am delighted to boast about her accomplishments wherever I go. She has been a role model whom I have always admired and looked up to, although I may not have explicitly expressed my admiration to her.
Lastly, my computer science and English teachers during high school hold a special place in my journey. They consistently challenged me to think beyond the confines of standard curriculum objectives and encouraged me to seek knowledge for the sake of learning and personal growth rather than solely for achieving high grades. Their guidance and mentorship left a profound impact on my approach to education and self-improvement.
When you complete your course and gain your qualification, what next? Do you have a clear vision of a role it will help you attain, or, if you are already in work, is it something you feel you need to do your job better and, hopefully, gain a promotion?
While I have considered several paths my ultimate objective is to become an intelligence analyst. However, the precise route to achieve this goal remains somewhat indistinct at present. Following graduation I may pursue a master’s degree in either cybersecurity or criminology and subsequently seek employment as an entry-level cybersecurity analyst. I am also considering the possibility of joining the police force.
My intention is to engage in either of these paths prior to seeking admission into the graduate program at the Australian Secret Intelligence Service (ASIS), thus bringing me closer to my lifelong passion. However, my current employment does not directly contribute to advancing my qualifications for my desired role. Nevertheless, I am diligently exploring opportunities such as internships and placements to immerse myself in either cybersecurity and/ or criminology, a pursuit that has proven to be a challenging venture.
It takes much more than cybersecurity expertise to be a good cybersecurity professional. In most roles people skills are essential. There is also the ability to be creative, to ‘think outside the box’. Do you plan
to undertake, or are you already undertaking, training in disciplines other than cybersecurity to support your career plans?
Concurrent with my cybersecurity studies I am pursuing criminology studies to complement my career objectives, because my interest lies in cybercrime. This amalgamation of disciplines facilitates a comprehensive understanding of criminal activities at both the technical and psychological levels.
What about specific cybersecurity qualifications such as those offered by (ISC) 2 , CompTIA and ISACA, Have you gained, or do you plan to gain any of these, if so which ones and why?
I have not yet attained any certifications from (ISC)2, CompTIA or ISACA. However, I am actively pursuing the Certified Application Security Engineer qualification as part of my current course of study. Moreover, I have plans to obtain the (ISC)2 certification once I have honed my skills and accumulated relevant work experience in cybersecurity, and I will challenge myself to gain others as well.
And of course we’d like to hear about the specifics of your current course. Please give us a few details of what you are studying. What do you enjoy? What do you find challenging? What would you like to see done differently?
I am a second-year student pursuing a double degree and my current course consists predominantly of units covering foundational cybersecurity principles and programming. Topics include an introduction to cybersecurity, object-oriented programming and secure coding. Among these, I gained immense enjoyment studying malware analysis and basic penetration testing during my first year, which ignited my passion for delving further into these areas.
However, I must admit that my enthusiasm wanes when it comes to back-end development and the study of C languages. Despite dedicating two years
to these subjects, they have proven to be the most challenging for me due to my limited interest in them.
In light of this, I hope to witness a shift in the curriculum during the next two years. I earnestly desire a more comprehensive exploration of topics aligned with my genuine passions, such as advanced malware analysis and cutting edge penetration testing. This redirection in coursework would invigorate my engagement and deliver a more rewarding academic experience for me.
In terms of criminology, the approach is mostly theoretical and my units so far have dealt with theories, understanding policing and government policies, facilitating a more rehabilitative than punitive approach to recidivism, and garnering researching skills. These topics have all been quite enjoyable to learn and I would love to engage in more profound studies of these subject areas during my time at Deakin.
Almost every aspect of cybersecurity is evolving rapidly. Do you feel your course is doing enough to keep up? Are there topics you would like to see covered, or topics you think should be omitted?
The dynamic landscape of cybersecurity demands continuous adaptation and growth. Thus, I question whether our current academic curriculum keeps pace with these ever-evolving trends. While the course has demonstrated efforts to refine assessment methodologies and practical components, its emphasis on theoretical concepts and programming prevails.
I recognise the value of foundational IT and computer science subjects. However, I have a profound interest in acquiring tangible, real world skills specific to cybersecurity roles. Regrettably, the current units have leaned more towards addressing the needs of software engineers and generic IT positions rather than catering directly to the demands of cybersecurity.
In pursuit of my aspirations I yearn for a more immersive experience in cybersecurity-related topics that align closely with my core ambitions. Particularly captivating to me is cryptography, which initially propelled me towards this degree. Thus, I earnestly hope for the incorporation of a cryptography module within our curriculum to enrich our cybersecurity education and further ignite my passion for this field.
Please tell us about your experience of being a woman studying cybersecurity. Chances are you are in a minority. Do you feel disadvantaged? Have you encountered sexism or misogyny? Do you feel your institution does sufficient to address such issues?
In STEM-related subjects the gender enrolment ratio often suffers from a significant imbalance, with females constituting a minority, usually around 25 percent. This is particularly evident in cybersecurity classes where the overwhelming majority are male students. This is in stark contrast to my criminology classes where the situation is reversed. As a woman studying cybersecurity, I empathise with my male counterparts in my criminology classes.
Despite being in the minority, I have never perceived any inherent disadvantage due to my gender, because I have always valued skills and aptitude over gender distinctions. While ‘mansplaining’ is prevalent within my cohort, I view it as a challenge to be more assertive and I regard it as a hurdle to be overcome, recognising that workplace dynamics may not always be equitable. This experience has honed my ability to navigate encounters with diverse individuals and personalities.
Thankfully, while studying at Deakin University, I have been fortunate not to encounter any severe forms of sexism or misogyny. The institution appears to foster an environment that does not create significant barriers based on gender, which has contributed positively to my educational journey in cybersecurity.
Educational institutions, especially universities—the ‘ivory towers’—are often seen as being out of touch with the real world. If you are not already immersed in the broader world of cybersecurity you will be part of when you complete your study, what are you doing to prepare yourself for that transition, for example by joining industry bodies like the Australian Women in Security Network (AWSN)?
I recognise the importance of proactively preparing myself to ensure a smooth transition into the broader cybersecurity domain upon completing my studies. To this end I am considering joining industry bodies such as the Australian Women in Security Network (AWSN).
Having had a brief encounter with AWSN during a cyber conference last year, I was captivated by their mentoring program. This program presents a highly appealing opportunity for someone like me who is earnestly seeking to break into the cybersecurity industry.
And finally, having come this far, do you have any regrets. If you had your time again, would you take a different path?
Looking back on my journey, I can honestly say I have no regrets. However, I do acknowledge I could have been more strategic in planning my path and prioritised gaining industry experience from the outset. Despite any missteps I made or challenges I faced, I firmly believe in embracing the entirety of my journey without dwelling on the outcomes. I take pride in my current position and the direction I am headed. If I were to revisit my past decisions, I would still choose to move forward with the same determination and resolve.
www.linkedin.com/in/vsatrasala379
Are you in full or part-time study? Where? What exactly is the course you are undertaking?
I’m currently balancing a few commitments. I’m undertaking my Diploma in Cybersecurity part-time at TafeSA. In addition to that, I’m proud to be part of the Purple Team Australia Student 2023 cohort and the AWSN PentesterLab program.
How long have you been doing it?
My cybersecurity journey began towards the end of 2021 when I decided to make a career change.

When do you expect to complete it? And how did you get there?
My goal is to complete the Diploma in Cybersecurity within the next two years. The Purple Team Australia Program and cybersecurity cadetship are set to finish in November 2023 and the AWSN PentesterLab in February 2024.
Were you inspired by cybersecurity in high school, if so, how? Or was it a later employment role that led you there? What reaction did you get from family and friends when you decided to pursue cybersecurity? My interest in cybersecurity was sparked by reading The Art of Deception by Kevin Mitnick, which was recommended as supplementary reading during my Secure and High Integrity System subject at university. I also witnessed forensic work in action during the women in technology mentoring program, and this further inspired me to pursue cybersecurity later in life.
Thankfully, I had the unwavering support of my family when I decided to make this career change. They have been eager to learn about my progress and the cybersecurity landscape, especially in light of the rise in scams and phishing incidents during the pandemic, and the shortage of cybersecurity specialists.
When you complete your course and gain your qualification, what next? Do you have a clear vision of a role it will help you attain, or, if you are already in work, is it something you feel will help you do your job better and, hopefully, gain a promotion?
I aspire to work in a purple team role on large-scale projects where I can make a meaningful impact on businesses, communities and individuals.
It takes much more than cybersecurity expertise to be a good cybersecurity professional. In most roles people skills are essential. There is also the ability to be creative, to ‘think outside the box’. Do you plan to undertake, or are you already undertaking, training in disciplines other than cybersecurity to support your career plans?
I have actively upgraded my soft skills through professional development courses in communication and cultural intelligence, and I plan to further enhance my critical thinking, strategic thinking and leadership abilities in light of the growing influence of AI on the industry.
What about specific cybersecurity qualifications such as those offered by (ISC)², CompTIA and ISACA. Have you gained, or do you plan to gain any of these, if so which ones and why?
I am currently pursuing my CompTIA Security+ and (ISC)² certifications. These globally recognised accreditations provide valuable upskilling opportunities and are advantageous in the everevolving cybersecurity industry.
And of course we’d like to hear about the specifics of your current course. Please give us a few details of what you are studying. What do you enjoy? What do you find challenging? What would you like to see done differently?
My current course in cybersecurity covers a wide range of interesting subjects, including networking, network security design, pen testing, Python programming, Linux and incident response. It is also introducing me to open-source intelligence. I particularly enjoy the practical aspects such as training, labs and capstone projects. Initially, learning was a challenge with numerous acronyms and jargon. However, the well-designed courses have helped ease the process.
Almost every aspect of cybersecurity is evolving rapidly. Do you feel your course is doing enough to keep up? Are there topics you would like to see covered, or topics you think should be omitted?
I do feel my course is doing its best to keep up with the rapidly evolving cybersecurity landscape. However, I believe it is essential to continuously review and update the curriculum to stay at the forefront of cybersecurity advancements. For example, the AI tool ChatGPT has seen huge uptake in the past year. It would be great to have some coverage of this in the course.
Please tell us about your experience of being a woman studying cybersecurity. Chances are you are in a minority. Do you feel disadvantaged? Have you encountered sexism or misogyny? Do you feel your institution does sufficient to address such issues?
I have not encountered sexism or misogyny, especially since most of my studies were conducted virtually during COVID. The tertiary institutions I have attended have actively promoted diversity, equity and inclusion.
Educational institutions, especially universities—the ‘ivory towers’—are often seen as being out of touch with the real world. If you are not already immersed in the
broader world of cybersecurity you will be part of when you complete your study, what are you doing to prepare yourself for that transition, for example by joining industry bodies like the Australian Women in Security Network (AWSN)?
I have actively sought to connect with industry bodies like the Australian Women in Security Network (AWSN) and the Australian Information Security Association (AISA). These networks provide valuable support, knowledge-sharing and mentorship opportunities.
And finally, having come this far, do you have any regrets? If you had your time again, would you take a different path?
I have no regrets about my decision to pursue a career in cybersecurity. Cybersecurity is a constantly evolving field, and I believe that, by continuing to learn and adapt, I can make a meaningful contribution and continue to grow both professionally and personally.
www.linkedin.com/in/kim-huynh-b7baaa139
 Author of How We Got Cyber Smart | Amazon Bestseller
Author of How We Got Cyber Smart | Amazon Bestseller
Twins Olivia and Jack love going to school, learning new things and making new friendships. Each week, first thing on a Monday morning after rollcall, they venture into the hall for the weekly school assembly. After everyone sings the national anthem and the school song they hear announcements about what is happening in the school community and which students are receiving awards. One morning the school principal, Ms Fields, got up and spoke about a new issue that had been brought to her attention. She said: “Kids, today I want to talk to you about something that is worrying me, and I need to share it with you. We think some of you may be tempted to use artificial intelligence to cheat on your schoolwork. The teachers and I know most of you are not doing this. However we need to talk about it.
“AI can be a great tool that can be used for good, and it’s important we learn how to use it, because it is now part of our society. We learnt recently about software that can answer questions for us and write essays in just a few seconds. This is indeed a very handy tool and has its place. However, we believe it's important to do your own work and not rely on machines to do it for you.”
After assembly Olivia and Jack walked back to their classrooms and chatted to their friends about what Ms Fields had said. One of their friends told them his father used AI a lot for his work and that his older sister sometimes used it to help with her homework. However, she still did all the required reading. She knew
that, when she was in an exam, she would need to have studied herself, because she could never know what questions would be asked. Also, some of the children in high school had got into trouble for using AI to cheat, and had been expelled.
In the classroom the teacher continued the conversation about how cheating was wrong and how it could get them into trouble. Olivia said: “Using AI to cheat is not fair to the other students who are doing their own work.”

Olivia and Jack had always tried their best to work hard on their schoolwork. They made sure to read all the books and do all the assignments themselves. They used AI as a tool like a search engine. They learnt it was important to be honest and do your own work, even if it was difficult. They also learnt that technology, used responsibly, can have a positive impact.
www.linkedin.com/company/how-we-got-cyber-smart


How We Got Cyber Smart addresses cyber safety, cyber bullying and online safety for elementary school-aged children.












 1. AMANDA-JANE TURNER Author of the Demystifying Cybercrime series and Women in Tech books. Conference Speaker and Cybercrime specialist
2. ULOAKU OKECHUKWU-PHILIP Cyber Security Consultant at Sycom Solutions
3. YIANNA PARIS Application & Offensive Security Consultant at Xebia
4. CALISTER APOLLONARY SIMBA Information Systems Security Engineer at Central Bank of Tanzania
5. NANCY TANEJA CISO - Primary Health Sector at Te Whatu Ora Health New Zealand
6. SITHEMBILE SONGO Group Head: Information Security at National State Owned Entity
7. MAGDA HATZIIOANNOU Network Security Controls Manager at NBN
8. BIANCA COLATRUGLIO Director, Aviation Security and Regulatory Compliance at Air Canada
9. SANNE MAASAKKERS Security specialist at NCSC-NL
10. VENISHA NAYAGAR Group CISO at Life Healthcare
1. AMANDA-JANE TURNER Author of the Demystifying Cybercrime series and Women in Tech books. Conference Speaker and Cybercrime specialist
2. ULOAKU OKECHUKWU-PHILIP Cyber Security Consultant at Sycom Solutions
3. YIANNA PARIS Application & Offensive Security Consultant at Xebia
4. CALISTER APOLLONARY SIMBA Information Systems Security Engineer at Central Bank of Tanzania
5. NANCY TANEJA CISO - Primary Health Sector at Te Whatu Ora Health New Zealand
6. SITHEMBILE SONGO Group Head: Information Security at National State Owned Entity
7. MAGDA HATZIIOANNOU Network Security Controls Manager at NBN
8. BIANCA COLATRUGLIO Director, Aviation Security and Regulatory Compliance at Air Canada
9. SANNE MAASAKKERS Security specialist at NCSC-NL
10. VENISHA NAYAGAR Group CISO at Life Healthcare
Cyber Enthusiast, Ethical Hacker, Author of A Hacker



I Am vol1 & vol2, Male Champion of Change Special Recognition award winner at 2021 Australian Women in Security Awards



IBM Security Managed Services Delivery Executive, Asia Pacific and Japan – currently on a career break and completing a degree in psychology



 11. TAL KOLLENDER Co-Founder & CEO, CISO at Gytpol
12. EMANUELA TODARO Chief People Officer at Yubico
13. DASHA DÍAZ Founder & CEO at itrainsec
14. RINA BASHOLLI Information Security Lead at KODE Labs
15. SUZANNA ALSAYED CEO of Evolutz
16. VANESSA HENRI Co-Founder of Henri & Wolf
17. JANA DEKANOVSKA Strategic Threat Advisor ANZ at CrowdStrike
18. CRAIG FORD
19. FIONA BYRNES
11. TAL KOLLENDER Co-Founder & CEO, CISO at Gytpol
12. EMANUELA TODARO Chief People Officer at Yubico
13. DASHA DÍAZ Founder & CEO at itrainsec
14. RINA BASHOLLI Information Security Lead at KODE Labs
15. SUZANNA ALSAYED CEO of Evolutz
16. VANESSA HENRI Co-Founder of Henri & Wolf
17. JANA DEKANOVSKA Strategic Threat Advisor ANZ at CrowdStrike
18. CRAIG FORD
19. FIONA BYRNES









 21. JAY HIRA Founder and Executive Director at MakeCyberSimple
22. LISA VENTURA Founder, Cyber Security Unity
23. VANNESSA MCCAMLEY Leadership and Performance Consultant, Coach, Facilitator, Author and Keynote Speaker
24. SIMON CARABETTA Project Coordinator at ES2
25. CAITLIN SAUZA Program Lead, Training Delivery at Cybermerc Pty Ltd
26. ROSALYN PAGE Award-winning tech, innovation & digital lifestyle writer
27. OLIVIA CONLON Cybersecurity specialist, Averto
28. JO STEWART-RATTRAY Chief Security Officer, Silverchain
29. JENAI MARINKOVIC Cofounder and President of nonprofit GRCIE (Governance Risk and Compliance for Intelligent Ecosystems), a cybersecurity and GRC academy based in Virginia, USA
30. SANDY SILK Principal Cybersecurity Advisor, Info-Tech Research Group
21. JAY HIRA Founder and Executive Director at MakeCyberSimple
22. LISA VENTURA Founder, Cyber Security Unity
23. VANNESSA MCCAMLEY Leadership and Performance Consultant, Coach, Facilitator, Author and Keynote Speaker
24. SIMON CARABETTA Project Coordinator at ES2
25. CAITLIN SAUZA Program Lead, Training Delivery at Cybermerc Pty Ltd
26. ROSALYN PAGE Award-winning tech, innovation & digital lifestyle writer
27. OLIVIA CONLON Cybersecurity specialist, Averto
28. JO STEWART-RATTRAY Chief Security Officer, Silverchain
29. JENAI MARINKOVIC Cofounder and President of nonprofit GRCIE (Governance Risk and Compliance for Intelligent Ecosystems), a cybersecurity and GRC academy based in Virginia, USA
30. SANDY SILK Principal Cybersecurity Advisor, Info-Tech Research Group







 31. NICOLLE EMBRA Cyber Safety Expert, The Cyber Safety Tech Mum
32. ELENA YAKOVLEVA Purple Team Australia Student
33. LIFANG WEI Masters in Cybersecurity Student at Edith Cowan University
34. CHISOM UCHECHUKWU ELEKWA Medical Radiography and Cybersecurity Student at the University of Nigeria
35. KHATIA KVATCHADZE Cybersecurity Student @SANS Technology Institute
36. VAMIKA SATRASALA Cybersecurity and Criminology Student at Deakin University
37. KIM HUYNH Diploma in Cybersecurity Student at TafeSA
31. NICOLLE EMBRA Cyber Safety Expert, The Cyber Safety Tech Mum
32. ELENA YAKOVLEVA Purple Team Australia Student
33. LIFANG WEI Masters in Cybersecurity Student at Edith Cowan University
34. CHISOM UCHECHUKWU ELEKWA Medical Radiography and Cybersecurity Student at the University of Nigeria
35. KHATIA KVATCHADZE Cybersecurity Student @SANS Technology Institute
36. VAMIKA SATRASALA Cybersecurity and Criminology Student at Deakin University
37. KIM HUYNH Diploma in Cybersecurity Student at TafeSA
This is a well-structured and organized course intended for more advanced students. The course is ideal for those with some modest experience with computer programming and is targeting to incorporate security implementations and designs with their codes.
Also, this free online class gives you a good idea, coupled with labs, about domain security like low-level systems, application, penetration testing, and the likes.
VISIT HERE
In this course, you will look at digital innovations and technologies from the standpoint of a CIO (chief information officer). You will learn about Cybersecurity, Agile frameworks, IT investments, risk management, and vendor management. A CIO plays an essential role in developing the digital ecosystem.

CIOs can infuse strategic business moves with new course instructor digital technologies. This means one should understand the different technologies that help evolve how businesses are done.
VISIT HERE
This course is open to both students and working professionals who wish to learn more about the exciting field of Cybersecurity. You will clearly understand what Cybersecurity is through their engaging and expertly produced videos and lectures. Industry experts provide helpful insights.
You can also join in knowledge assessments, gain access to materials addressing governance and risk management, practice how to assess environmental awareness, and so much more.
VISIT HERE
This course introduces current information and system protection methods and technology and is designed for those who wish to enhance their understanding of the topic. The goal of the course is simple: to help students embrace their appreciation and passion for cyber security. When you have a clear understanding of this course, this can help you in your future endeavors.


This free online course offered by New York University is perfect for students, web developers, engineers, managers, and even the plain private citizen. The projects and quizzes are designed to train each learner’s retention of all the topics covered.

VISIT HERE


This class is a part of the Cybersecurity in the Cloud Specialization course offered by the University of Minnesota. As its name implies, Cloud Security Basics introduces you to Cybersecurity for the cloud.
In this course, you are taught how to apply classic but efficient security techniques to the cloud. You will also analyze the most recent threats to cloud security using standard and systematic strategies. This course also teaches you how to build your web service case studies, and from there, come up with the best security solutions.
VISIT HERE
The University of ColoradoBoulder offers a course called Vital Skills for Data Science Specialization. Part of this course is the Cybersecurity for Data Science, a free online class offered via Coursera.





This course is designed to help anybody interested in data science and wants to understand better the cybersecurity risks and the methods and tools used to nip those threats in the bud.



Unlimited access to hundreds of cybersecurity courses including ethical hacking, penetration testing, and much more. Beginner-friendly and great value for money.
VISIT HERE
VISIT HERE
This course introduces you to real-time cybersecurity methods and ways in the context of the TCP/IP protocol suites. It introduces some TCP/IP security hacks needed for network security solutions like stateful and stateless firewalls.
When you enroll, you will find out about the many techniques utilized in designing and configuring firewall solutions like proxies and packet fillers to safeguard the asset of an organization. This is the third of the four courses under Introduction to Cyber Security specialization and is designed for intermediate learners.
VISIT HERE
FEATURING FREE SECURITY TRAINING RESOURCES THAT ARE AIMED AT INCREASING SECURITY AWARENESS AND HELPING PEOPLE BUILD AND UPSKILL THEIR SECURITY SKILLS.
The Graduate Certificate in Cyber Security and Networks is a course designed for existing professionals who have a background in IT, and wish to upskill in cyber security. If you are transitioning from a non-IT background, the Graduate Diploma in Information Technology (Cyber Security and Networks) will equip you with foundational IT skills, as well as opening a pathway for you to specialise in cyber security.
Along with being able to demonstrate a comprehensive information security and network management discipline knowledge, the design and problem-solving skills you develop will allow you to analyse complex environments, assess alternate solutions, and evaluate outcomes.




The Graduate Diploma in Information Technology (Cyber Security and Networks) is a course designed to open up a pathway for individuals from an unrelated field of study to transition into the ICT industry, acquiring foundational discipline knowledge and specialising in cyber security. If, however, you are an existing IT professional and wish to develop skills in cyber security, the Graduate Certificate in Cyber Security and Networks will help you upskill and specialise in cyber security.
In an increasingly digital world, the demand for talented data analysts is predicted to jump 27.7% within the next five years.
The Data Analytics Bootcamp teaches you the techniques and skills to understand and interpret complex data. Backing up these technical skills, you will also gain the ability to clearly communicate data to a wide range of stakeholders so that you can inform key business decisions.
This Bootcamp will arm you with the practical and hands-on problem-solving skills through units that bring the real world to you. By the time you graduate, you will possess analytical skills that will help you navigate future data analytics challenges and get you ready for a job in a soughtafter industry.
Our 100% online Web Development Bootcamp is specifically designed for those looking to build their technical proficiency in web development from the ground up. Through a combination of theoretical and practical study, you will gain the skills to effectively analyse and solve complex web development challenges. Your Bootcamp will also enable you to design and implement front-end and back-end web development projects, focusing on practical and accessible user experiences.

With Alex Pender and Gaby Ortega
Girls Gone Boss brings you amazing conversations with real women, overcoming real obstacles yet defying them with style & grace. We want to empower and motivate the next generation of women to always dream big.

With Ariana
The Women in Tech with Ariana podcast is a global podcast in 10 countries that features women in tech and entrepreneurship, talks about the latest news in tech, and shares tangible resources to help women navigate the tech industry.


With Katy Campbell
Disrupting the entry barriers to female entrepreneurship through inspiring first-hand stories and key insights. FemGems light your way to start up!
With Abadesi Osunsade and Michael Berhane
Produced by People of Color In Tech, Techish is a podcast about the intersection of tech, pop culture, and life. A podcast by two millennials talking about all things tech, pop culture, and life. Starring tech founders Abadesi Osunsade [@abadesi] and Michael Berhane [@michaelberhane_].

With Charlotte Fuller
The Women in Tech – Success Stories | Xledger podcast features the inspirational stories of women in technology.

With Robin Kinnie
Modern Figures is a conversational-style podcast elevating the voices of Black female scholars in computing.


With Alesha Dixon
The Always #LikeAGirl Squad, including Alesha Dixon and YouTuber Hannah Witton take on confidence issues and the dreaded fear of failure.
With Anney and Samantha
Join hosts Anney and Samantha to listen to Stuff Mom Never Told You, continuing the conversation of what it is to identify as female through research-based discussion around feminism and how it impacts everyday life.

With Emily Pendlebury
Cyber security, no longer a place for tech heads, speaking another language. Join us at Girls Talk Cyber, the podcast to help you decode this space and redefine how you act online.

With Hillary Kerr
Join our host, Who What Wear co-founder Hillary Kerr, as she chronicles the career changes that can come at any age in our podcast, Second Life.

With Jessica Huynh
Go Girl director Jessica Huynh sits down in an 8-part series focussed on people involved in and around the Go Girl, Go for IT program. Go Girl, Get Heard is a women in STEM focussed podcast all around exciting and engaging minds across the nation.

With Farai Chideya
Our Body Politic is unapologetically centered on reporting on not just how women of color experience the major political events of today, but how they're impacting those very issues. Weekly episodes feature in-depth conversations about the economy, health, politics, education, the environment, and the most prescient issues— because all issues are women's issues.

Authors // Katty Kay and Claire Shipman
In The Confidence Code, Claire Shipman and Katty Kay completely undress the concept of confidence. Is it selfworth or self-esteem? Is it real or imagined? They endeavor to understand how widespread the lack of it is and how this impacts the larger subject of leadership and success. They dig into the critical question of growing up female: where confidence comes from and why it feels so ephemeral. By examining cutting-edge research, sharing their own and other notable women's stories and providing practical principles, Kay and Shipman do more than merely admonish women to "lean in" to their careers. Rather, they give them the inspiration and the tools to close the gap between insecurity and fulfillment.


Author // Dr. Susan Nolen- Hoeksema
Being a woman isn’t easy at all anyway, top that with the millions of things we need to worry about! It’s only natural to get stressed and overworked which ultimately takes away from our happiness. In this book, renowned psychologist Susan Nolen-Hoeksema lays out plans to break free of self-sabotaging patterns of overthinking and not letting negative thoughts control our life.
BUY THE BOOK
Author // Lilly Singh
From actress, comedian and YouTube sensation Lilly Singh (aka Superwoman) comes the definitive guide to being a BAWSE - a person who exudes confidence, reaches goals, gets hurt efficiently, and smiles genuinely because they've fought through it all and made it out the other side.


BUY THE BOOK
Author // Sheekah Singh
Have you wondered if IT/Tech is more than just coding? Are you one of those who thinks that the tech field is difficult and meant for nerds? Are you a parent concerned about the future of your child and want them to consider a career in IT/Tech? Are you a woman already in tech and need to switch career paths? Are you thinking if Computer Science is the right major for you? If yes, then this book is for you. This book debunks myths and helps young women choose a career in IT.
 By // The Scarlett Series
By // The Scarlett Series
Scarlett Chevalier (red outfit) and Sophia (black outfit) are two characters from from the Scarlett series. The Scarlett series is about a gothic heroine called Scarlett Chevalier and the women who work for her at her cybersecurity firm. They expose corruption around the world using their cybersecurity and tech skills. Scarlett uses technology, cool gadgets and her motorcycle to achieve justice for those who have been downtrodden.

Author // Marcia
DempsterIn this book, Marcia Dempster, a global sales leader in the cybersecurity space, will teach you: How to find your allies, both male and female. How to make space for yourself and other women at the table. Ways to confront "Imposter Syndrome" head-on. How to set boundaries and stay true to your authentic self, whoever that may be!

Authors // Rachel Walsh and Bill
O'NeillThere have been countless badass women who have changed the world for the better, yet most people have never even heard of them.
Women throughout history have fought for their rights and the rights of others, defended their countries during wartime, healed the sick and the wounded, invented new technologies, led countries, made inspiring art, and so much more.

Author // Judy Nure
This book is a labor of love; a statement; a new passionate call to attention to the African women in cybersecurity agenda in Africa. The goal is to recognize and celebrate remarkable ladies shaping the way. To show the value added by the women; provide reflection on what women are, and can do for cybersecurity; provide an inspiration for girls and other women to join the field. We hope this book be an enduring investment for current and future generations of cybersecurity ladies.We could not have every lady of interest included in this book, so we've created a Twitter List with the African women in security we know. We will be updating the list to include more women always. Find the list at: twitter.com/CyberInAfrica/lists/african-wincyber

Need a professional marketing, strategy and implementation agency that is dedicated, responsive, professional, dedicated, creative, innovative, hardworking, and really cares about your business outcomes?

REACH OUT TODAY FOR AN INSTANT QUOTE.
With:
The team at Source2Create has all the necessary skills to get the job done for you, so your time can be reserved to focus on other things. aby@source2create com au
Women & Hi Tech exists to change the landscape of women represented in STEM to be equally inclusive to all. To achieve our goal, we work to connect female STEM professionals with each other and our community in Indiana. Our members and sponsors represent a wide array of STEM fields, including life sciences, accounting, engineering, psychology, statistics, and information technology. They work as engineers, analysts, scientists, business developers, marketers, educators.
READ BLOG
This resource illuminates how some of today’s leading infosec women experts got started in the cybersecurity industry and embraced the common goal of creating a more secure world for everyone. It also demonstrates how one person’s impact can be amplified when they get together with like-minded individuals, support one another and advocate for change.
We at Cisco recognize that this fact holds true for women in security. That’s why we decided to put together a list of organizations through which women can collectively effect change in the industry. A dozen of those organizations are shared below.

READ BLOG

 By Vladimir Unterfingher
By Vladimir Unterfingher
Marked by significant geopolitical shifts and unrest, 2022 has galvanized the cybersecurity landscape as well; war-profiteering fueled by endless media disputes has allowed the threat actors not only to operate unhindered but also to find safe harbor with states that choose to turn blind eye to cybercriminal activity.
2023 will most likely be just as challenging as the previous few years, but I’m confident that the cybersecurity market has the right tools to deal with the constantly shifting cybercrime landscape and new/consolidated threats, whether we’re talking about supply chain attacks, ransomware, deepfakes or cyber espionage.
READ BLOG
Sabio's Women In Tech blog is designed to help women get tech careers as the pandemic restrictions begin to lift. Classes beginning now! We are the premier software-engineering program specifically designed for the exceptionally motivated.
READ BLOG

 By Clare Schexnyder
By Clare Schexnyder
Girls' Globe is the media organization that amplifies the voices of women and girls to strengthen human rights, social justice and gender equality. We fight to create a sustainable world shaped by peace and solidarity, free from any discrimination, inequality and violence, enabling all girls and women to live up to their fullest potential.
This cybersecurity blog belongs to April C. Wright who is a speaker, teacher, community leader, and hacker with more than 25 years of experience in the information security industry. She teaches others how to use simple actions that can lead to a better and safer place.
There’s been a lot of talk about the Angler exploit kit lately, but, for most people, the warnings don’t strike a chord. And they’re definitely not to blame.



 By Ana Dascalescu
By Ana Dascalescu
If you’re a Star Wars fan (and you probably are), then you know what the HK-47 droid had to say about humans. He called us meatbags. It’s a term with a long history in SciFi circles. It appeared in Futurama as well.
 By Jurgita Lapienytė
By Jurgita Lapienytė
Agnese Morici, a security expert, once walked into a NATO Committee meeting, and everyone thought she was a waitress. A woman, then 25 years old, surely couldn’t be advising a roomful of military men – could she?
Challenging young women to be builders, creators, and innovators - the protagonists in their own lives. Built By Girls is building the next wave of tech leaders - who just happen to be girls. We give young women the exposure, skills and network they need to get their first job in tech. We're her secret women.
Founded by Cameka smith, BOSS stands for 'Bringing Out Successful Sisters' and our mission is to promote and encourage the small business spirit and career development of women. The BOSS Network is an online community of multicultural professional and entrepreneurial women who support each other through conversation, online and eventbased networking.

READ BLOG
Learn more about the work we're doing to help women and nonbinary technologists succeed. AnitaB.org envisions a future where the people who imagine and build technology mirror the people and societies who use it. As a 503(c)(3) organization, AnitaB.org stands by our mission to serve women in technology 365 days per year. We are here to provide women technologists with programs, services and events to drive inclusive technology.
READ BLOG
 By Nathaniel Raymond
By Nathaniel Raymond
An evolving set of credential phishing activity targeting Microsoft Office 365 credentials has been observed reaching enterprise email inboxes. This activity is categorized by several key components that make it stand out from other campaigns. Key components include:
• Over 120 unique phishing domains created using the “bulletproof” registrar R01-RU, hosting thousands of phishing URLs.
• Abuse of Cloudflare CAPTCHA and IP proxying services for efficacy and anti-analysis

• The use of phishing services attributable to the seemingly defunct Phishing-as-a-Service operation called “Caffeine”, which was created by the kit maker “MRxC0DER” and features an API for email validation

READ BLOG
Adora Hack contains articles on Technology and Software Development. I am Nenne Adaora (Adora) Nwodo, a Software Engineer based in Lagos, Nigeria
READ BLOG
Chic Geek is a welcoming, supportive, beginner-friendly community for women exploring the intersection of technology and entrepreneurship. News, stories and perspectives from women in technology. Learn about leadership, career development and how to build a thriving career in tech.
READ BLOG

