HOW HACKERS THINK…
and what UAE businesses must do to protect themselves
ENCRYPTION’S NEW DAWN
Meet the future direction of cryptographic design


and what UAE businesses must do to protect themselves
Meet the future direction of cryptographic design

Limitless Parking’s Mohamed Hediya explores the future of car parks — and how it is taking shape today

EDITORIAL
Publisher Barry Bebbington +44 1708 229354 barry@pubint.co.uk
Editor Cora Lydon +44 7834 244613 cora.lydon@securitymiddleeastonline.com
ADVERTISING
Worldwide
Mike Dingle
+44 1752 267330 mike@securitymiddleeastonline.com
Ryan Bickerton
+44 1752 265802 ryan@securitymiddleeastonline.com
Gareth Driscoll
+44 1752 260603 gareth@securitymiddleeastonline.com
Rahul Vara
+44 1752 604352 rahul@securitymiddleeastonline.com
Will Russell
+44 7800 513300 will@securitymiddleeastonline.com
Digital Editor
Britt Jones britt@securitymiddleeastonline.com
Marketing Manager
Mark Doyle
+44 7517 452283

PUBLISHED BY
Publications International Ltd
+44 1708 229354
166 Front Lane, Upminster, Essex, RM14 1LN, UK
This publication may not be reproduced or transmitted in any form in whole or in part without the written consent of the publishers.
©Publications International Ltd. 2025
For subscriptions and advertising enquires, or for further information on the magazine visit our website at: securitymiddleeastmagazine.com
Welcome to our Intersec Saudi Arabia Special Edition, dedicated to helping security professionals make the most of the Kingdom’s premier security, safety and fire protection event. As the official media partner, we are proud to be attending the show and in this issue we bring you an exclusive look at what to expect. You’ll find the full show agenda, profiles of keynote speakers and a chance to hear from some of the show’s exhibitors, all curated to give you the actionable details you need for a rewarding visit (page 59).
On page 18, Jeff Zindel, Vice President of Cybersecurity Programs at Parsons, examines why integrated cybersecurity is foundational to the Middle East’s smart city success. While page 31 features Jack Fletcher, Senior Director, Technology Advisory at FTI Consulting, who explores the workplace impact of AI and its
implications for data security, alongside exclusive views from our Ambassadors on this crucial topic.
Finally, don’t miss Hadi Jaafarawi, Regional VP – Middle East & Africa at Qualys, discussing the role of a dedicated Risk Operations Centre on page 50, and how this innovation empowers organisations to strike the optimal balance between risk and value management.
Cora Lydon Editor cora.lydon@securitymiddleeastonline.com
03 Up front Foreword from the Editor
07 News Monitor
The latest regional and international security news
10 Market Monitor
A roundup of the latest security products and solutions
14 Cover story: Limitless Parking
Find out how Limitless Parking is transforming urban mobility in the region
16 Encryption’s new dawn
Dr Víctor Mateu, Chief Researcher of the Cryptography Research Center at the Technology Innovation Institute, considers what the HQC Standard means for the future of cryptography
18 Beyond the blueprint
Jeff Zindel, Vice President of Cybersecurity Programs, Parsons, looks at how integrated cybersecurity is essential for smart cities
22 AI’s cloud challenge
The Middle East’s AI ambitions face a security reality check, according to Dario

26 Case study: Hytera and Iraqi Ministry of the Interior
In a bid to streamline its emergency services, the Ministry of Interior in Iraq evaluated solutions that could unify diverse technologies under one resilient system, before selecting Hytera
28 The future of retail security
Genetec takes a closer look at AI-powered video analytics – could this be a force multiplier for retail security and operations?
31 AI tools and data security
Jack Fletcher, Senior Director, Technology Advisory, FTI Consulting, shares his thoughts on the use of AI in the workplace and the implication it can have on data security, while our Ambassadors share their thoughts on the same topic
39 Voyage vulnerabilities
Jason Lane-Sellers, Director of Fraud and Identity, LexisNexis® Risk Solutions, shares the hidden threats posed by fraud in the travel industry

50 Risk value control
Hadi Jaafarawi, Regional VP – Middle East & Africa at Qualys, makes the case for a Risk Operations Centre and the ability to finally control the relationship between value and risk management

44 From reactive to proactive Mazen Adnan Dohaji, Vice President & General Manager, IMETA, Exabeam, shares his thoughts on achieving smarter, more scalable SOC strategies in the Middle East with agentic AI
55 How hackers think… and what UAE businesses must do to protect themselves, according to Danny Jenkins, CEO and co-founder of ThreatLocker®

18
59 Intersec Saudi Arabia
Everything you need to successfully navigate the forthcoming exhibition and get the most out of your attendance
60 Welcome from show director
61 Agenda
63 Meet the speakers
65 Meet the exhibitors



69 PSSA: Empowering the security industry
Learn more about the transformative alliance that has been forged between IFPO and PSSA
70 Interview: unified security Ali Laribi, Founder & IT/ OT – Cyber/ Physical Security Advisor, Fortress Plus talks to Meshal Aljohani, Security Operations Specialist

35 Johnson Controls
Johnson Controls is powering the future of building technology –we meet the newly appointed General Manager, Emerging Markets, Tony Nasr, to find out how
Mazen Adnan Dohaji
Vice President & General Manager, (iMETA), Exabeam
Mazen Adnan Dohaji has helped numerous organisations in the region plan for cyber security risks.
Dr Víctor Mateu
Chief Researcher of the Cryptography Research Center at the Technology Innovation Institute (TII)
Dr Mateu works at the TII, a leading global scientific research centre and the applied research pillar of Abu Dhabi’s Advanced Technology Research Council (ATRC).
Danny Jenkins
CEO and Co-Founder of ThreatLocker
Danny Jenkins is a recognised authority in the cybersecurity sector and has over two decades of experience in building and securing corporate networks, including red and blue team operations.
Enquire about 2026 sponsorship packages








Hanwha Aerospace has launched its regional headquarters in Riyadh for the Middle East and North Africa region, marking a significant milestone in the company’s strategic expansion in the region. This move reflects Hanwha’s long-term commitment to enhancing partnerships, advancing industrial cooperation and supporting defence modernisation initiatives across the region.
About 80 distinguished delegates from the Korean Embassy in the Kingdom, the Saudi Ministry of Defense, the Ministry of National Guard, the Ministry of Investment, and the Saudi Arabian Military Industries (SAMI) attended the inauguration ceremony, alongside the global leadership team of Hanwha represented by Hanwha Aerospace, Hanwha Systems and Hanwha Ocean.
The launch of Hanwha’s operations in Saudi Arabia not only marks a significant step forward in enhancing local content and building sovereign capabilities in the military industries sector, but also broadens cooperation beyond defence into smart cities, renewable energy, and the space sector, positioning the Riyadh RHQ as a gateway for expansion across the Gulf and North Africa. hanwha.com
A newly identified ransomware strain named Charon is making headlines in the Middle East, targeting public sector organisations and aviation companies.
Researchers from cybersecurity firm Trend Micro have described Charon as possessing advanced persistent threat (APT)-style capabilities, drawing comparisons to the tactics of the China-linked cyber-espionage group, Earth Baxia.
Charon operates by disabling antivirus and security measures, deleting backups and emptying the recycle bin to hinder recovery efforts before encrypting files.
Victims receive a custom ransom note detailing the organisation’s name, a list of encrypted data and payment instructions, suggesting a targeted approach rather than random attacks. trendmicro.com
The UAE Cyber Security Council (CSC) has issued a warning that 70% of smart home devices are at risk of cyberattacks if proper security measures are not implemented. The council noted weak security practices, such reliance on default settings, significantly contribute to the vulnerability of these devices.
Saudi Minister of Interior Prince Abdulaziz bin Saud has signed security agreements with his British counterpart, Yvette Cooper, during an official visit to London to strengthen future cooperation between the two nations.
At the fourth symposium on security and safety in vital facilities, held in Oman, Brigadier General Eng. Saeed bin Suleiman Al-Asimi, Chairman of the symposium’s organising committee stated that Oman is “prepared to become an advanced regional centre for facility safety, and perhaps also for artificial intelligence safety.”
The US Department of State has approved the possibility of Foreign Military Sale of M142 HighMobility Artillery Rocket System and other equipment to Bahrain, as per the US Defense Security Cooperation Agency’s announcement on 14 August. Lockheed Martin will be the principal contractor.
Qatar’s Ministry of Interior has launched a new service on the Metrash App, allowing users to submit complaints about violations by security service companies, surveillance activities that have been carried out without a license and establishments against security companies.
A major security campaign from the Ministry of Interior, resulted in over 1,000 traffic violations being identified and the arrests of 14 violators and wanted people. The MoI said such intensified security campaigns are a priority to protect citizens, residents and the homeland.
The Royal Oman Police has updated is official mobile app to support access to make public services faster and more convenient. Newly introduced digital services now allows users to display family information and view digital documents such as passports, birth certificates and investor cards.
In a new educational initiative, the UAE Ministry of Education will introduce cybersecurity lessons to students from Grades 1 through 12, starting in the 2025-2026 academic year.
The initiative aims to enhance digital literacy and ensure younger generations are equipped to navigate the online world safely.
The Ministry will roll out teaching guides in English, accompanied by practical instruction designed to promote better cybersecurity practices. These changes are part of the UAE’s broader strategy to enhance digital literacy and technology skills within the education system. moe.gov.ae
A large-scale phishing campaign has been uncovered, in which threat actors exploit Google Classroom to distribute over 115,000 malicious emails to more than 13,500 organisations worldwide. The campaign, identified by Check Point, unfolded in five waves from August 6 to August 12, 2025, weaponising the educational platform to bypass standard security filters. The attacks targeted a range of industries across North America, Europe, the Middle East and Asia.
Attackers created fake ‘classrooms’ and sent invitations from an official Google email address. As the emails appeared to originate from a valid Google domain, they had a higher chance of evading security gateways that rely on sender reputation and typical filtering rules.
The phishing invitations offered commercial services, including SEO optimisation and pitches for product reselling.

A recent survey by Accenture revealed that nearly 90 per cent of organisations believe they are inadequately prepared for AI-centred cyber-attacks.
Despite the adoption of artificial intelligence across various sectors, only 22 per cent have established clear policies and training for generative AI use, leaving them vulnerable to potential threats.
The study, which included responses from 2,286 executives, encompassed 24 industries in 17 countries. It found a concerning oversight regarding cybersecurity measures related to AI adoption, with only 25 per cent of organisations utilising encryption and access controls to safeguard sensitive data. accenture.com

On Wednesday, August 27 2025, ASIS Dhahran Chapter hosted a special forum on ‘AI in Security: Trends & Perspectives’ at Aldarah Hall, Dammam.
The evening brought together security professionals, thought leaders and industry experts for an engaging discussion on the future of AI in the field. A special highlight of the evening was the Keynote Address by Sami Al Ajmi, Senior Vice President of Digital & Information Technology at Aramco, who shared an inspiring vision on AI-driven transformation for security and resilience.
The distinguished speakers included:
• Mohammed Alries – Sr. Manager Corporate Security, New Murabba (Moderator)
• Dr Mohammed Alhamid – Executive Director, Center of Artificial Intelligence, Ministry of Interior
• Prof. Jonghyuk Kim – Director, AI for Security Master Program, Naif Arab University of Security Science
• Abdullah Jarwan – CEO, CNTXT
The panel explored practical applications, policy perspectives and the operational impact of AI in security, sparking valuable dialogue and knowledge-sharing among attendees. It was not only an opportunity to learn but also a platform to connect, collaborate, and envision how AI will continue shaping the future of security. asisonline.org
Era is the first series of compact outdoor stations with advanced access control functions, specifically designed for residential applications.
It can be expanded up to 4 users or in a version with numeric keypad and includes a proximity reader with MIFARE/NFC technology as standard.
It is a product entirely designed and manufactured in Italy.
















Kibo and Sentrycs have announced a collaboration that delivers a fully integrated, mission-ready security platform designed to counter both ground and aerial threats.
The Kibo–Sentrycs integrated platform is a plug-and-play mobile system that combines field-proven infrastructure with advanced aerial threat defence in a single, unified solution. It streamlines deployment, reduces personnel and logistical demands and delivers full-spectrum protection against both ground and airborne threats.

The integrated solution combines Kibo’s bulletproof modular structures, already used by military, police and critical infrastructure operators, with Sentrycs’ autonomous counter-drone system, which is operational in over 20 countries across six continents.
“Integrating Sentrycs’ Cyber over RFC-UAS system into Kibo’s mobile, bulletproof structures delivers a unique combination of advanced drone defense and physical protection,” said Meir Avidan, VP Business Development and Strategic Partnerships at Sentrycs. “It serves as a force multiplier for missions requiring speed, reliability, and multidomain readiness, providing security forces with both tactical flexibility and enhanced protection.” kibocabins.com sentrycs.com

Carrington Textiles has announced an expansion of its specialist portfolio with the introduction of the ProTact by Haartz®range of laminated fabrics.
A partnership with Germany’s Haartz® GmbH is set to enhance the offerings available to tactical equipment manufacturers. The ProTact range is specifically engineered to meet the
stringent requirements of modern military applications, encompassing essential gear such as rucksacks, load-carrying systems, vests and pouches.
With high-performance technical laminates at its core, the ProTact collection offers a series of advantages for manufacturers in the tactical sector. It features laser-cut ready fabrics for clean edges without residue, reduced fraying due to precision layer bonding, and superior flexibility that provides a softer feel for enhanced comfort during wear.
Additionally, the inclusion of CORDURA® Truelock technology ensures consistent colour and resistance to UV fade, while the engineered materials maintain their integrity without delamination, even in extreme conditions. Proven field performance further highlights the reliability of the range under pressure.
carrington.co.uk/en/
The United Arab Emirates has launched its first quantum-secure communications testbed.
The testbed will investigate the application of Quantum Key Distribution (QKD) for ultra-secure data transmission. TII has implemented its proprietary QKD solution across a three-node network within ADGM, creating a commercialscale ‘living lab’ for real-time testing of quantum-safe communication in an operational environment. adgm.com/adgm-authority

TCL Home Security announced the TCL D2R Max Retrofit Smart Lock, the world’s first retrofit lock with multi-biometric authentication, alongside the TCL Cam D2 Pro and TCL Cam B2 Pro, two AI-powered solar cameras designed to deliver ultimate clarity and protection.
The TCL D2R Max is the first of its kind to integrate three biometric technologies — 3D facial recognition, palm vein scanning and fingerprint authentication — in a sleek retrofit design.
3D face recognition and palm vein scanning provide military-grade accuracy, preventing spoofing by photos or replicas. All biometric data is encrypted and stored locally on the device, ensuring complete privacy and protection.
A built-in high-precision gyroscope detects the door’s status in real-time, automatically locking once closed. This seamless operation delivers peace of mind in one smooth motion.
The universal design fits most European door locks, eliminating the need to replace the cylinder. tclhomesecurity.com







UNDER VEHICLE INSPECTION SYSTEM MADE IN GERMANY



29. September01. October 2025 Riyadh, KSA SAUDI ARABIA
MEET US AT OUR BOOTH 4-D09
SURFACE MOUNT - NO ROADWORKS
COLOR IMAGING
FULL VIEW OF UNDERCARRIAGE FOR MOBILE AND PERMANENT USE
AUTOMATIC COMPARISON FEATURE
EXTREMELY ROBUST - HEAVY DUTY COVER
HIGH RESOLUTION CLEANING SYSTEM

As urban centres across the Middle East grow denser and more dynamic, the need for intelligent infrastructure has never been greater. Among the most pressing challenges, parking. From circling congested blocks to dealing with ticket machines, inefficient parking systems contribute not only to driver frustration but also to environmental and economic strain. Stepping boldly into this gap is Limitless Parking, a UAE-based company on a mission to redefine how we think about urban mobility.
At the helm of this transformation is Mohamed Hediya, the visionary founder and Managing Director of Limitless Parking. With deep expertise in parking technology, urban infrastructure and project management, Mohamed is
blending cutting-edge innovation with practical problem-solving. The result, a seamless, AI-powered, ticketless parking system that is already making waves across the Middle East and beyond.
From frustration to innovation
The spark for Limitless Parking came from a simple yet universal experience: the irritation of traditional parking. Long queues, faulty ticket machines, inefficient payment options and wasted time searching for a space — it was clear that parking needed a 21st-century upgrade.
“I set out to create a system that doesn’t just function, but one that thinks – an intelligent solution that adapts, automates and continuously enhances the urban experience” said Hediya.
This philosophy laid the groundwork for the company’s flagship innovation: the Limitless Intelligent Parking System, a completely automated, ticketless and barrier-less solution designed to make parking effortless for users and cost-effective for operators.
The Ticketless Parking System eliminates the need for physical tickets or access cards entirely. Instead, the system uses ANPR (Automatic Number Plate Recognition) cameras to identify vehicles as they enter and exit. Payments are processed automatically via a secure app, QR-code web portal, WhatsApp payment link, or contactless terminal.
The result is a frictionless experience that saves time, reduces congestion and cuts emissions. Users can now drive in and out of parking spaces without ever needing to interact with a machine or manpower, while operators enjoy increased efficiency and reduced cost.
The smart dashboard: Parking in real time
At the heart of Limitless Parking’s ecosystem is its powerful Smart Parking Dashboard — a web-based interface that gives operators full visibility and control over their parking assets. Designed with intuitive UX and real-time analytics, the dashboard provides a complete overview of parking activity, occupancy, transaction history and system performance.
Operators can:
Monitor space availability in real time. View license plate logs and ANPR camera data.
Track revenue and payment trends. Set dynamic pricing based on usage or time of day.
Generate customised reports. Access live alerts and system health checks.
This centralised command centre is what makes Limitless Parking not just a solution provider, but a strategic partner in urban planning and smart infrastructure development.
AI that does more than think
One of the company’s most powerful assets is its use of Artificial Intelligence. Far from being a buzzword, AI is deeply embedded into every aspect of the
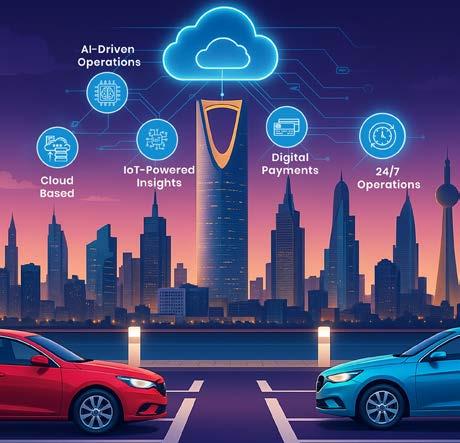
Limitless system — from analysing traffic patterns and optimising space allocation to predicting demand and improving user interfaces.
The system learns from user behaviour, traffic flow and seasonal trends to make smarter recommendations. For example, during peak hours at a shopping mall, the AI can adjust pricing or direct drivers to less congested areas via real-time notifications. For the operator, this translates into higher space utilisation and maximised revenue, while ensuring drivers enjoy a seamless and comfortable experience.
“We don’t just collect data — we turn it into action,” Hediya explained. “That’s the difference between automation and intelligence.”
With every smart solution comes the responsibility of protecting user data. Limitless Parking is committed to the highest levels of data security and compliance, including full GDPR adherence. All transactions are encrypted, and sensitive data is stored on secure, cloud-based servers with multi-layered protection.
Regular cybersecurity audits and partnerships with leading security providers ensure that user information — from license plates to payment details — is safe at every stage of the process.
What makes Limitless Parking truly scalable is its modular design, tailored to serve a wide range of industries:

Retail & Shopping Malls: Increase customer satisfaction with fast, automated entry and exit.
Airports & Transportation Hubs: Streamline traffic with predictive flow management.
Hotels & Hospitality: Offer guests a premium, ticketless arrival experience.
Hospitals: Reduce stress and improve patient access with real-time space availability.
Commercial Offices: Boost operational efficiency and employee convenience.
Residential Communities: Provide residents with a smooth, app-enabled parking solution.
Each implementation is customised to the site’s infrastructure and operational needs, ensuring a perfect fit with minimal disruption.
Having proven its capabilities across multiple deployments in Dubai, Limitless Parking is now scaling up its operations throughout the UAE and the wider Middle East region. From airports and malls to residential compounds and smart city projects, the company is in active discussions with government entities and private developers alike.
“We’re not just a vendor,” Hediya emphasised. “We’re a technology partner helping cities evolve.”
This includes exploring integration with municipal smart city platforms, enabling real-time data exchange between parking systems, traffic management, public transport and emergency services.
In a region that’s rapidly embracing digital transformation, Limitless Parking stands out not only for its technology but for its vision. It is a company that recognises a daily frustration and turns it into an opportunity — one that benefits individuals, businesses and cities alike.
With Mohamed Hediya at the helm, Limitless is more than a parking company. It’s a catalyst for smarter cities, a driver of urban efficiency and a leader in the mobility revolution.
As the Middle East charts its path toward sustainable urban futures, Limitless Parking is already there — scanning the road ahead, unlocking the gate and showing the way forward.
limitlessparking.com

Dr Víctor Mateu, Chief Researcher of the Cryptography Research Center at the Technology Innovation Institute, considers what the HQC Standard means for the future of cryptography
The US National Institute of Standards and Technology (NIST), which has been working on finding algorithms to withstand cyberattacks that could come from quantum computers, recently selected HQC, a cryptographic algorithm built on code-based security, as its fifth and latest post-quantum cryptography (PQC) standard, a critical milestone for the global cryptographic community.
The rise of quantum computing poses a fundamental challenge to today’s
public-key cryptographic systems. Algorithms currently safeguarding global digital infrastructure, from banking transactions to healthcare information, could one day be rendered obsolete by sufficiently advanced quantum machines. That’s why the standardisation of quantum-resistant algorithms has become one of the most consequential undertakings in cybersecurity today. That urgency is what makes NIST’s selection of HQC so significant.
As the world prepares for the era of quantum computing, one of the building blocks of secure communication is the Key Encapsulation Mechanism (KEM), a method used to safely exchange encryption keys between two parties.
HQC, short for Hamming Quasi-Cyclic, is a promising KEM that takes a different approach from most early post-quantum standards. Many of the standards selected by NIST rely heavily on latticebased mathematical techniques, which

secure data using complex geometric structures called lattices. But HQC relies on a fundamentally different approach focused on error-correcting code-based cryptography.
Code-based cryptography is built on the challenge of decoding scrambled messages, a technique widely used in data storage and satellite communications. HQC’s resilience stems from mature, well-studied principles, now tailored for post-quantum security, which makes it more trustworthy.
The inclusion of HQC by NIST marks a deliberate step toward algorithmic diversity. It mitigates systemic risks that might arise if vulnerabilities were discovered in any single family of cryptographic assumptions. This diversification offers a way to build a more resilient and secure global cryptographic ecosystem.
Protecting communications against quantum attacks is one of the most urgent challenges of our time. Creating secure algorithms is only half the battle, trying
to break them is the other. That’s why investment in cryptanalysis is just as important as innovation.
This dual focus on design and validation reflects a core belief, at the Technology Innovation Institute (TII) and within the broader community, that the resilience of future cryptographic standards will rest on both creativity and on scrutiny.
Standards like HQC are born from rigorous peer review, iterative improvement and a global, collective effort grounded in transparency. For example, HQC was initially developed by a group of researchers coming from several French universities including the University of Limoges and University of Toulon as well as from research centres such as TII.
As quantum computing evolves from theoretical possibility to practical reality, the cryptographic community must continue to act with both urgency and caution.
The adoption of HQC is a milestone. But it is not an endpoint.

As quantum technology progresses, our cryptographic defenses must evolve. Standardisation should remain a living process, shaped by ongoing research, open collaboration and continual scrutiny.
Standards matter because they shape the future of secure communication. Finding the right standards has become central to the mission to help guide a safer digital world in the face of quantum uncertainty.
tii.ae


Hardened PoE Switches & Fiber Media Converters
• Deploy IP devices at remote locations with or without local power
• Supports up to 90W per port
• Rapid battery charging provides extended power backup
• 115/230VAC or 277VAC input
• Manage and reset devices remotely with LINQ™ Network Power Management
• Lifetime warranty


Jeff Zindel, Vice President of Cybersecurity Programs, Parsons, looks at how integrated cybersecurity is essential for smart cities
With more than half of the world’s population now living in urban areas, ensuring cities function efficiently, securely and sustainably for those who live and work within their boundaries has never been more critical. Smart city initiatives, once considered aspirational, are now being heralded by policymakers at all levels, across all regions. Smart cities are increasingly being viewed as
a pathway to economic diversification, improved communication and connectivity, reduced resource waste and lower carbon emissions.
Countries in the Middle East, particularly Saudi Arabia, the UAE and Qatar, are gaining global attention for their futuristic smart city developments, which are built with advanced infrastructure and technology integration
leveraging the Internet of Things (IoT) and artificial intelligence (AI). Current and past successes, coupled with visionary leadership, are attracting foreign investment and top talent, creating powerful models of privatepublic collaboration. These smart cities are transforming infrastructure into more connected, efficient, responsive, sustainable and user-friendly systems.

The interconnected nature of smart cities makes cybersecurity a priority. Historically, design and cybersecurity existed in silos, with cybersecurity typically treated as an afterthought. In the context of smart cities, that approach is untenable. Failing to incorporate cybersecurity into the design phase creates substantial risks. Vulnerabilities in interconnected smart transportation systems, public safety networks, energy grids, smart buildings and water and wastewater systems, can be exploited leading to potentially catastrophic consequences. These risks include operational disruption, safety risks,
cascading failures across interconnected systems, substantial financial losses, loss of foreign investment, reputational damage, data breaches and privacy violations.
Given these profound implications, why is it vital to integrate cybersecurity during the design phase? Retrofitting security after project development and commissioning is costly, disruptive and often impractical. Consider a smart energy project: attempting to retrofit cybersecurity into operational facilities and systems after deployment – across network architecture, control systems, edge devices, substations and other assets – can result in major service disruptions. Moreover, the
expense to retrofit the infrastructure post construction can be exponential; far greater than the cost of integrating cybersecurity during the design phase. Workarounds may not fully address cybersecurity vulnerabilities or provide the visibility and information required to effectively monitor and protect the assets and systems. By contrast, incorporating a cybersecurity strategy and programme into smart city design and planning from the outset, covering security architecture, controls and governance, delivers both resilience and long-term efficiency.
Key measures aligned with each country’s standards and regulations should include:
Continuous risk assessments for critical infrastructure.
Secure architecture with network segmentation.
Data protection and privacy-by-design.
Supply chain security with forensic verification of hardware and software. Centralised asset inventories with automated discovery of connected devices.
Universal zero trust privileged access for all access points and stakeholders. Cybersecurity performance and compliance management.
Establishment of a Security Operations Centre (SOC) monitoring IT, OT, IoT and cloud infrastructure.
Together, these proactive measures provide multiple layers of security that reduce long-term risk, mitigate costs and strengthen resilience, especially as cyber threats to digital infrastructure evolve in scale and sophistication.
The rapid adoption of digital technologies is accelerating the digitisation of smart city systems, expanding the attack surface and heightening the need for robust cybersecurity. The UAE Cyber Security Council recently reported they are countering more than 200,000 cyber-attacks per day, with the government sector accounting for 30% of the attacks. The financial stakes are rising in the GCC, the average cost of a cyber incident has reached $6.9 million – substantially higher than the global average of $4.2 million.
Compounding the challenge, cyberattacks are becoming more sophisticated. Addressing this threat landscape requires continuous monitoring
“Retrofitting
of digital infrastructure to identify vulnerabilities and threats, ensure compliance and respond to indicators of compromise and cyber incidents. True resilience, however, must be built in from the start. Embedding cybersecurity at the design phase helps best prepare smart city systems to withstand and adapt to emerging threats before going live.
AI adoption in smart cities is accelerating under a do-it-now mindset, where speed often outpaces governance. However, research from IBM and the Ponemon Institute warns that ungoverned AI systems are not only more likely to be breached but also have significantly greater cost implications when they are. Poorly secured AI systems can be manipulated by malicious actors, leading to misinformation or even control and disruption of critical infrastructure. To reduce these risks, AI systems in smart cities must be protected by a multilayered security framework emphasising access control, data privacy and robust governance.
At the same time, AI should be leveraged as a defensive cybersecurity capability, playing a significant role in ongoing vulnerability management and advanced threat detection and response. With the right guardrails, AI can strengthen resilience rather than become a source of new vulnerabilities.
The safety and resilience of smart cities depends on securing their complex vendor and contractor ecosystems, because even a single weak link in the supply chain can lead to severe compromise. According to the World Economic Forum’s Global Cybersecurity Outlook 2025, 54% of large organisations view supply chain challenges as the greatest barrier to achieving cyber
resilience. Mitigating supply chain risks must begin at the smart city design stage, before systems are procured or deployed.
Key actions include:
Establishing and enforcing a supply chain risk management (SCRM) policy that requires vendors and contractors to undergo rigorous security due diligence.
Analysing hardware and software to detect vulnerabilities and hidden risks. Implementing zero trust privileged access for all vendors and contractors throughout design, construction, operations and maintenance.
Collectively, these measures protect against counterfeit components, outdated equipment and unauthorised access –critical for the security, reliability and resilience of smart cities.
Smart cities generate massive volumes of data governed by both local and international laws and regulations. In the GCC, cybersecurity compliance requirements are especially stringent, where safeguarding critical infrastructure is treated as a matter of national security.
Compliance is no longer a boxchecking exercise; it has become a cornerstone of effective cyber risk management. Modern compliance management tools automate tracking, audits and reporting – strengthening security posture and operational efficiency while lowering OPEX. Embedding compliance into the design phase further enhances oversight, reduces vulnerabilities and limits exposure to financial and reputational risk.
Proactive integration not only strengthens resilience against increasingly

sophisticated cyber threats, but it also enhances efficiency, quality, productivity and reliability.
Resilient smart cities require: Cybersecurity-first design principles grounded in proactive strategies and governance.
Supply chain risk management beyond compliance.
Responsible AI governance. Continuous monitoring and compliance systems.
Cybersecurity must be a key criterion in selecting engineering partners, so they can deliver a cyber-secure digital ecosystem that enables frictionless data sharing across sectors, authorities and citizens.
It should not be an afterthought or retrofit. Cybersecurity must be an integral part of smart city design, shaping not only how cities function, but how they thrive in an increasingly digital, interconnected and high-risk world.
parsons.com






The Middle East’s AI ambitions face a security reality check, according to Dario Perfettibile, VP, Kiteworks
As the UAE pours billions into becoming a top 10 AI nation by 2031 and Saudi Arabia anchors its Vision 2030 on artificial intelligence, a dangerous gap has emerged. The region’s organisations have achieved an impressive 85% AI adoption rate, according to new research from Wiz. But here’s the catch: 86% of these same organisations can’t see where their data goes once it enters AI systems.
The race to lead in AI has created a paradox: the faster organisations deploy AI, the larger their security blind spots
become. In a region where business runs on relationships and trust, these vulnerabilities threaten the entire digital transformation agenda.
Racing towards an AI future
The Middle East’s AI adoption isn’t following the typical technology curve. Where cloud computing took years to gain trust, AI went from experiment to essential in just 18 months. Saudi Arabia’s NEOM project integrates AI into its foundational infrastructure. Qatar’s financial sector
uses AI for everything from fraud detection to customer service. Kuwait and Bahrain have launched national AI strategies that touch every sector from healthcare to logistics.
The numbers tell the acceleration story. Self-hosted AI adoption in the region jumped from 42% to 75% in a single year. Organisations aren’t just using pre-built AI services — they’re running sophisticated models within their own cloud environments. Meanwhile, 67% of regional cloud

“AI went from experiment to essential in just 18 months”
environments now use OpenAI or Azure OpenAI SDKs, up from 53% last year.
Competition demands innovation. Digital transformation initiatives that once focused on moving to the cloud now centre entirely on AI capabilities.
But speed has a price. A Kiteworks report reveals that only 17% of organisations can automatically prevent confidential data from flowing into AI systems. The other 83% rely on employee training, warning messages – or nothing at all. When humans are the only barrier between sensitive data and AI platforms, breaches become inevitable.
January 2025 should have been a celebration for DeepSeek adopters. Usage of the AI platform more than doubled across Middle Eastern organisations, with companies integrating it into everything from customer service to data analysis. Then Wiz researchers made a discovery that changed everything.
DeepSeek’s infrastructure leaked over one million lines of log streams containing confidential information from organisations worldwide. The exposed database didn’t just reveal usage patterns — it provided complete database control access to potential attackers. Any organisation that had connected DeepSeek to their systems had potentially exposed sensitive data.
Think about what this means practically. A government agency in Riyadh using DeepSeek for citizen services. A Kuwaiti bank analysing transaction patterns. A healthcare provider in Abu Dhabi processing patient records. All of them potentially exposed through a single vulnerability in a platform they trusted.
The timing made it worse. Organisations were rapidly onboarding DeepSeek precisely when it had
fundamental security flaws. They were essentially inviting a compromised system into their most sensitive operations. And because most organisations can’t track their AI data flows, many still don’t know what they exposed.
This isn’t a story about one bad platform. It’s a preview of what happens when AI adoption outpaces security implementation. Today it’s DeepSeek. Tomorrow it could be any of the dozens of AI platforms that regional organisations are rushing to adopt.
Traditional security tools excel at monitoring networks, tracking file access, and watching application behaviour. But AI operates differently. When an employee copies a financial report into ChatGPT to summarise it, no file transfer occurs. When a developer pastes code into an AI assistant, no network anomaly appears. The most sensitive data movements have become invisible.
The problem compounds through what researchers call “permission cascade”. Here’s how it typically unfolds: An employee in a Dubai financial firm connects an AI tool to their Google Workspace account. The AI needs broad permissions to function effectively, so the employee grants access to their drives, calendars and emails. But corporate Google accounts include access to shared drives, archived projects and organisational resources that the employee rarely touches.
Suddenly, an AI platform has access to years of accumulated corporate data. Market research. Strategic plans. Customer databases. The permissions persist even after the employee stops using the AI tool. Multiply this by hundreds of employees across an organisation, and the exposure becomes staggering.
Infrastructure vulnerabilities add another layer of risk. The CVE-20240132 vulnerability affected NVIDIA GPU containers across 35% of cloud environments. For a region betting heavily on AI infrastructure, this means a single vulnerability can compromise a significant portion of national AI capabilities. GPU-based processing isn’t optional for serious AI workloads — it’s essential. When the foundation cracks, everything built on top becomes unstable.
The immediate financial impact is sobering. AI-related breaches cost 28% more than conventional incidents, according to industry analysis. But the true cost for Middle Eastern organisations extends far beyond immediate damages.
Consider competitive intelligence risks. When a Saudi petrochemical company’s proprietary process data gets analysed by a shared AI model, that information doesn’t disappear. It potentially influences the model’s training, making traces of that intelligence available to competitors using the same platform. In industries where competitive advantage depends on closely guarded expertise, this invisible leakage can destroy market positions.
A recent report by Varonis found over 225,000 compromised AI credentials available on dark web marketplaces. For a region where business relationships build on decades of trust, a single leaked credential can unravel partnerships, damage reputations and close doors that took years to open.
Then there’s the compliance time bomb. US agencies issued 59 new AI regulations in 2024. The EU AI Act adds another layer of requirements. Middle Eastern organisations with international operations face a maze of overlapping regulations. AI systems deployed hastily last year must now meet standards that didn’t exist when they were implemented. The resulting compliance debt threatens to derail digital transformation initiatives before they deliver value.
Regional talent sees these vulnerabilities too. The best AI engineers and data scientists want to work for organisations that take security seriously. When breaches make headlines, recruitment becomes harder – and retention becomes expensive.
that actually work
Forward-thinking organisations across the region are proving that secure AI deployment is possible without sacrificing innovation. Their approaches share common elements that any organisation can implement.
Zero-trust AI architectures lead the way. A major UAE bank routes all AI interactions through controlled gateways in their cloud infrastructure. Employees get the productivity benefits of AI tools, but data never leaves the bank’s security perimeter. Every query is logged, monitored and analysed for potential exposure.
Integration beats isolation. Rather than treating AI security as a new challenge requiring new tools, successful organisations incorporate AI controls into existing security frameworks. They extend their cloud access policies to cover AI platforms, include AI data flows in their compliance monitoring, and train their incident response teams on AIspecific threats.
Automation scales where human oversight fails. With AI adoption at 85% and growing, manual reviews and approval processes can’t keep pace. Leading organisations implement automated controls that detect new AI integrations, assess permission requests in real-time and flag suspicious data movements before they become breaches.
Middle Eastern organisations don’t need to choose between innovation and security. The same engineering excellence that builds skyscrapers in the desert and creates cities from sand can build AI systems that are both powerful and protected. The question isn’t whether AI will transform business in the region — that’s already happening. The question is whether organisations will take control of that transformation or let it control them.
Smart organisations are doing three things. They’re mapping every AI tool their employees use, implementing automated AI data gateways to control on data flows, and treating AI security as part of their existing cloud infrastructure rather than a separate problem. These aren’t complex solutions. They’re practical steps that recognise a simple truth: in the race to AI leadership, the winners won’t
75%
Self-hosted AI adoption in the region jumped from 42% to 75% in a single year
be those who move fastest, but those who move wisely.
The opportunity remains enormous. The Middle East stands poised to demonstrate that rapid AI adoption and robust security aren’t opposing forces — they’re complementary requirements for sustainable success. In a region that has always understood the value of strong foundations, it’s time to apply that wisdom to our digital future. kiteworks.com

In a bid to streamline its emergency services, the Ministry of Interior in Iraq evaluated solutions that could unify diverse technologies under one resilient system, ultimately selecting Hytera for its proven expertise and comprehensive platform CASE STUDY
The Ministry of Interior in Iraq is the government body responsible for overseeing a number of agencies, including the Emergency Response Unit, Iraqi Police, Highway Patrol and Traffic Department. It needed to overhaul its fragmented emergency response system in Baghdad to combat ongoing security challenges.

The city of Baghdad has long faced security challenges due to political instability, terrorism and the aftermath of the ongoing conflict in Iraq. In the past the emergency response system was highly fragmented with as many as 26 different emergency numbers in use leading to confusion for citizens about what number to call. This splintered approach caused delays in response times and hindered effective resource allocation.
In addition, for the operators and responders, the biggest pain point was the delay and inefficiency in allocating resources. With different agencies using separate systems and incompatible communication tools, information often did not flow quickly enough, leading to slower response times on the ground.
To overcome these challenges the MoI wanted to enhance the overall efficiency and resilience of Baghdad’s emergency response services to provide its citizens with a safer environment.
To achieve this, the MoI required a new command and control system able to integrate all the emergency calls ranging from fires, security issues, crimes and traffic incidents and manage them through one unified platform. In addition to emergency call handling and dispatch, the platform also needed to be able to integrate different two-way radio standards used by the emergency services, including DMR and TETRA, as well as other technologies such as CCTV and live video feeds from vehicles and body worn cameras.
Hytera’s SmartOne solution was deployed in the MoI’s 911 command and control centre to integrate all the different emergency call requests and dispatching activities for the various types of first responder agencies. The 911 call centre features 300 operator seats, supports case intake and creation and dispatches cases using DMR and TETRA two-way radio networks.
Additionally, the centre is connected to CCTV cameras and body cameras to provide live video feeds of incidents, which helps to facilitate a faster, more informed response. The system also includes call recording and statistical analysis capabilities for continuous improvement and training purposes.
The technology brings together several modules in order to meet operational goals. For example, the call taking and handling module efficiently manages emergency calls, records incidents, and forwards them to the appropriate response units.
The integration of computer-technology integration (CTI) and computer-aided dispatch (CAD) ensures timely, accurate and standardised responses from call handlers and dispatchers.
The visual command system module is designed to optimise patrol planning and monitoring. By helping to anticipate potential problems, this module can reduce the number of incidences and improve public safety. It also facilitates performance evaluations and enhances the management of personnel.
The incident analysis module uses data mining and advanced analytics to help personnel make informed decisions by offering incident reports, trend analysis and proactive warning features.
Finally, the mobile police application connects frontline officers’ communication devices to the central command centre, facilitating real-time updates and reducing administrative burdens, which ultimately improves field operations.
The system is built on a micro-service architecture to provide a more stable and scalable command and control solution. It allows the platform to run modular services independently, making the system easier to scale, more resilient to faults and better able to handle large volumes of emergency calls.

Hytera Communications Corporation Limited is a leading global provider of professional communications technologies and solutions. With voice, video and data capabilities, it provides faster, safer and more versatile connectivity for business and mission critical users. Hytera continuously invests in technology development and application innovation, and is committed to promoting more open communication standards.
As a result of centralising all emergency requests, fragmentation has been eliminated which has improved coordination between police, fire and medical services. Combining these services into a single platform has resulted in fewer delays and quicker response times, as well as giving citizens greater clarity when seeking help.
There has also been an improved efficiency in resource allocation, as the system provides dispatchers with realtime visibility of available resources, enabling them to assign the appropriate personnel, vehicles or units to an emergency.
Faster response times have been achieved thanks to the new system. It can automatically generate case numbers and files, relieving personnel of admin tasks; dispatchers can also quickly locate callers and allocate resources, which saves lives by reducing response times. The integration of CCTV and body camera systems further accelerates the decisionmaking process by delivering real-time visuals of the incident.
This integration is also enhancing situational awareness, which in turn empowers authorities to make informed decisions based on live video feeds and statistical analysis.
Finally, the MoI is now able to operate using data to aid decision making. The system’s ability to record calls and analyse trends helps the Ministry
continually assess and improve the effectiveness of the emergency response. This data-driven approach ensures the system adapts to evolving needs and challenges.
The new system has not only improved the situation for those working within the emergency services but has also served to elevate the reputation of the MoI and increase the trust in authorities. With a successful implementation, public confidence has been built in emergency services.
The system not only met its objectives but far exceeded them. On the very first day of its launch, it successfully received and processed approximately 70,000 calls demonstrating its robust capability. The project can now serve as a model for other conflict-affected areas seeking to improve their emergency response capabilities.
Powered by Hytera’s SmartOne platform, the MoI deployed the 911 Command and Control Center with 300 operator seats, supporting call intake, CAD/CTI, GISbased visual command, CCTV and body camera integration, patrol management, incident analysis and a mobile police app. These features centralised all emergency requests, reduced response times and improved coordination.
hytera.com

Genetec takes a closer look at AI-powered video analytics –could this be a force multiplier for retail security and operations?
Nearly one-quarter of American adults have shoplifted, according to a LendingTree survey. However, only 48% of these shoplifters have been caught in the act, highlighting a growing need for security solutions that can proactively identify suspicious behaviour, such as someone standing near a clothing rack for too long.
Whether it’s spotting a potential shoplifter before they leave the store, identifying hazards like spills in an aisle, or tracking patterns in customer flow to adjust staffing, AI-powered video analytics can help retailers respond to incidents faster, reduce false alarms and gain insights that improve security, operations and the customer experience.
AI vs. IA: Clarifying the terminology
While they may seem similar, AI and Intelligent Automation (IA) play different interconnected roles in providing benefits to the retail industry.
AI involves teaching technology to spot patterns, make decisions and carry out tasks by feeding it information. For example, an AI-powered video security system can identify and flag suspicious activity to a security team, freeing up time they would have otherwise spent watching multiple hours of video.
IA, on the other hand, uses AI and takes it a step further by including human decision-making, so the security team can choose the best next steps.
Empowering loss prevention teams with AI-enabled technology
Retail loss prevention teams face mounting challenges, from ORC to internal theft. Strengthening processes and deploying advanced monitoring systems can help retailers become more resilient against threats.
Key benefits of AI-powered video analytics include: Reducing friction for loss prevention teams
Retailers accumulate vast amounts of video footage every day, but manually sifting through it is time-consuming and inefficient. By using AI-enabled features of their video management
or physical security system to analyse video streams, loss prevention teams can identify potential issues faster and focus on actual risks instead of monitoring multiple cameras at once. For example, automated alerts can notify operators of potential threats, such as individuals lingering in high-value areas. Once flagged, management can review the incidents and decide if further monitoring or intervention is needed. This proactive approach reduces false alarms and allows teams to respond swiftly to credible threats.
Accelerating investigations
Manual video reviews after an incident can stretch for hours or even days.
AI-powered video analytics can help streamline this process with forensic search functions. Investigators can use natural language prompts such as “woman in a red jacket” or “white truck near entrance” to easily locate relevant footage within a specific time frame. This rapid access to evidence not only aids internal investigations but also streamlines collaboration with law enforcement. Once the footage is located, loss prevention teams can securely share evidence with law enforcement using a digital evidence management system (DEMS).
Detecting vehicle license plates ORC often involves repeat offenders operating across multiple stores in a region. In this case, an automatic license plate recognition (ALPR) solution enables retailers to track

vehicle plates linked to previous incidents. For example, when a flagged vehicle enters a property, staff receive immediate alerts, and the information can be shared with law enforcement and nearby participating retailers. This collaboration strengthens defences against ORC and helps retailers build stronger cases against offenders.
Many people enjoy going into a store, whether it’s to see and touch a product before buying it (46%) or to take it home right away (40%), according to a PwC survey. By showing when stores are busiest, how shoppers move through the aisles, and where staff are most needed, AI-powered video analytics can give retailers the information they need to create experiences that match what customers want.
Here are four ways retailers can improve the customer experience by deploying AI-powered video analytics:
1. Understanding traffic patterns By using AI to analyse data from in-store cameras, retailers can get a clearer picture of how customers move through the space. This helps identify high-traffic areas, optimise store layouts and ensure essential items are within easy reach. For instance, a retailer can use these insights to determine the best placement for seasonal or clearance items, ultimately creating a smoother and more enjoyable customer experience.
2. Improving marketing and promotions
Video data can be used to monitor customer movement and help evaluate the effectiveness of product displays and promotional campaigns. By correlating customer behaviour with sales data, retailers can determine which displays convert browsers into buyers. Additionally, comparing traffic patterns before, during and after a promotion can provide valuable insights into what strategies work best for attracting and retaining customers.
3. Keeping shelves stocked and stores clean
Video analytics can help detect when stock is low or displays are disorganised. In this case, automated alerts can notify staff when restocking is needed or when a display has been disrupted, ensuring products are always available and the store stays presentable.
4. Managing checkout lines and customer service
Video analytics can detect long lines at registers and alert staff, prompting the opening of additional registers to ensure the customer experience is not negatively impacted. Similarly, by monitoring store zones, staff can be notified when a customer appears to need assistance, helping to close more sales and provide a personalised experience.
Retailers are increasingly using AI for large-scale data analysis and automation, aiming to maximise security investments and support loss prevention teams. However, AI is not a one-size-fits-all solution, and its success depends on thoughtful planning and human oversight. Some key considerations include: Data privacy: Retailers must prioritise the protection of customer data by following strict data protection regulations and implementing strong security measures. Access to sensitive information should be carefully controlled to prevent misuse. Transparency and fairness: AI models should be rigorously tested to ensure fair, unbiased outcomes. Retailers should choose vendors that rigorously test AI models to minimise bias and ensure accurate, explainable results. Human decision-making: While AI can process information faster than any human, final decisions – especially those involving security – should involve human judgment. AI serves as a tool to inform and support decisionmaking, not replace it.
To fully benefit from AI advancements, retailers should consider physical security platforms with built-in AI capabilities. In these modern systems, AI isn’t a separate add-on; it’s embedded into the software, quietly powering key functions like video analytics.
Ultimately, the key to success lies in blending innovative technology with a thoughtful, human-centered approach. By doing so, retailers can protect their assets and create a shopping environment that’s both safe and enjoyable for customers.
genetec.com

Meet Barco CTRL, the innovative, scalable software platform for control rooms. A solution that simplifies workflows, deployment, and serviceability. With ‘Simplicity, Scalability and Security’ as the key principles, Barco CTRL allows users to securely connect to their sources, from any location. And interact with the content on any video wall or operator desk.




Jack Fletcher, Senior Director, Technology Advisory, FTI Consulting, shares his thoughts on the use of AI in the workplace and the implication it can have on data security, while our Ambassadors share their thoughts on the same topic
AI tools such as ChatGPT have become ubiquitous and are being used for anything from developing the perfect holiday itinerary to writing tricky work emails. The rapid use of AI is also radically changing how we work, and a range of companies have successfully deployed inhouse AI tools which are having positive impacts on productivity and organisation. However, the use of unapproved ‘shadow AI’ in work environments presents an array of data and security risks that can seriously undermine the compliance posture of an organisation and expose valuable commercial and sensitive information.
A key tenet of many data privacy regulations concerns data reuse and transparency, and central to this is the idea that personal data should not be
used for a secondary purpose that was not communicated to the individual when the personal data was provided and/ or consent to use the data was granted. Similarly, data privacy regulations often impose restrictions on where personal data can be sent, while certain AI tools may rely upon data storage in countries with poor standards of data protection and security, which may bring your organisation into contravention with data protection and security regulations if protected information has been input into an AI tool.
There is also a myriad of security risks associated with the use of AI tools. While sophisticated and more reputable AI tools may deploy strong security controls, this does not prevent sensitive or commercially sensitive information,
including intellectual property, from being leaked or mishandled. To compound this issue, the ability of security teams to actively monitor and prevent against this form of data exfiltration is made difficult if the use does not take place on a company device and is performed using shadow AI.
So, what can be done? Like with many compliance initiatives, the emphasis should be on encouraging positive behavioural shifts by training employees on the risk of using shadow AI tools and reminding employees of the core principles of key policies such as acceptable use policies. Where possible, employees should be steered towards in-house AI tools and encouraged to use corporate devices for all corporate activities.


“The increasing adoption of AI tools offers significant rewards, such as improved efficiency and advanced data analysis. However, it also presents complex security and privacy risks, including potential exposure of sensitive information and difficulties in erasing data due to AI’s immutable nature. As AI systems process vast amounts of data, ensuring secure handling throughout each stage of the AI lifecycle is critical to prevent breaches and unauthorised access.
“With increased querying, the attack surface expands, further elevating security concerns. Additionally, achieving true impartiality remains elusive, as models are influenced by their training data and embedded values, which can inadvertently reinforce biases. To mitigate these risks, organisations must adopt comprehensive security protocols, effective data governance frameworks and bias mitigation strategies. Responsible management of AI’s security and privacy challenges is essential for harnessing its full potential while maintaining trust and compliance.”
Ian Keller
Global information technology expert
“AI is becoming deeply embedded in enterprise environments, driving automation, real-time decisionmaking and operational efficiency. But for security professionals, this shift introduces a new layer of complexity. Each interaction with an AI system — whether through prompt, output, or log — creates a data artifact that may persist beyond user intent. Unlike conventional software, AI systems process vast, unstructured datasets, often without clear data lineage or retention boundaries. This creates challenges around auditability, confidentiality and exposure management.

“The recent NYT v. OpenAI case illustrates how AI data can quickly move from operational asset to legal evidence. Deleted chats were ordered preserved, raising red flags about whether “ephemeral” truly means temporary. For CISOs, DPOs and CAIOs, this signals the need for stronger controls over AI access, logging and privacy disclosures.
“AI’s benefits are real — but only if matched with security practices that address data retention, model behaviour and legal risk. As AI adoption accelerates, organisations must embed privacy and security by design, ensure transparency in data usage, and define clear accountability across the AI lifecycle. Ignoring these risks now may mean dealing with regulatory or legal fallout later.”
Betania Allo Cyber Policy & Law Expert
“As AI tools become increasingly integrated into modern security and business environments, the dual challenge of maximising value while safeguarding data grows more complex.

“AI’s ability to process and analyse vast amounts of data enables enhanced decisionmaking, predictive security and operational efficiency. However, this capability also introduces new vulnerabilities. Sensitive data fed into AI systems — whether for training or real-time decisionmaking — must be protected across its entire lifecycle, from collection and storage to processing and output.
“The use of third-party AI platforms raises further concerns about data residency, unauthorised access and compliance with data protection regulations. Furthermore, algorithmic bias remains a pressing issue, potentially compromising fairness and trust in AI-driven decisions.
“From a security leader’s perspective, it is essential to balance innovation with responsibility. Embedding security and privacy into AI design (‘secure by design’) and implementing robust governance frameworks are critical steps. Ultimately, the successful deployment of AI tools depends not only on their technical capabilities, but also on our commitment to protecting the data they rely on.”
Turki Almalki Security Facilities & Vigilance Manager at Riyadh Air
“In order to use AI responsibly, organisations must have policies that outline the rules for AI use and in particular protection of data and client’s data. The objective is to ensure that we harness the power of AI, whilst promoting the responsible use of AI to protect values, data and intellectual property. This is of upmost importance when utilising public or third-party AI tools.

“Basic rules to be followed when using AI systems include, for instance: Don’t input any data or personal information into AI systems; be mindful of generated personal information; be transparent when people may be impacted and don’t use AI systems for purposes that people would not reasonably expect (e.g. obtain participants’ consent for call recording); confirm accuracy: all outputs must be proofread, validated and fact checked to ensure accuracy and reliability before being published or used; and respect third party intellectual property (IP) rights. We must not plagiarise or violate third party IP rights.
“The above will help mitigate risks associated with the use of public or third-party AI systems.”
Andrew Long Principal Consultant – Security Risk Management, WSP

rapiscan.com
The new IDIS Edge AI Plus Camera range takes security and safety to a new level of efficiency for real-time monitoring and incident review

Supercharge your security and safety operations with the IDIS Edge AI Plus Camera range. It features IDIS A-Cut Monitoring and IDIS Deep Learning Analytics (IDLA) Pro event functions - including crowd detection, abandoned object, removed object and fall detection. These new functions enable faster investigations and response times thanks to automatic image cropping, intuitive attribute searches, and advanced automated alerts, as standard.

Johnson Controls is powering the future of building technology – we meet the newly appointed General Manager, Emerging Markets, Tony Nasr, to find out how
As a global leader in smart, healthy and sustainable buildings, Johnson Controls has been at the forefront of innovation for nearly 140 years. From the invention of the electric room thermostat in 1885 to its groundbreaking work in creating autonomous buildings, the company’s long legacy is a testament to its commitment to transforming the environments where people live, work and thrive.
Ahead of Intersec Saudi Arabia, we sit down with Tony Nasr, the company’s General Manager for Emerging Markets. Drawing on his extensive background in the security sector, Tony provides a fascinating look at how Johnson Controls is meeting the unique challenges and opportunities of the rapidly growing Middle East market. In our conversation, he explores the company’s strategic investments in the region, the power of integrated solutions, and the importance of key accreditations in the security market.
Can you tell us a bit about your professional journey and what drew you to your current role at Johnson Controls?
I joined Johnson Controls earlier this year in the position of General Manager, Emerging Markets.
Throughout my career I’ve held several senior positions and have built up extensive experience within the security sector, mainly from within global businesses.
What excited me about the role with Johnson Controls was the opportunity for me to bring my extensive knowledge of the region and my security and building management experience to the role.
I believe I bring key strengths to the role, including relationship building and strategic business planning; skills that are important to such a diverse region.
In a crowded market, what would you say is the key differentiator that sets Johnson Controls apart from other firms in the security sector?
Johnson Controls is a large global company with a vast product portfolio of leading brands and is currently celebrating its 140th anniversary of innovation.
What sets us apart is our experience in offering integrated solutions. Customers know that with our long heritage and products we can supply their security, fire and building management solutions. We firmly believe in the benefits of integration and purchasing from one supplier – we want to make it easy for our customers to work with us and our experience and product range support this.
The Middle East is a dynamic and fast-growing market. How is Johnson Controls investing in the region to support this growth and better serve its customers?
One of the many reasons I chose to work for Johnson Controls is the strong reputation of the local team. They are skilled in what they do and are adept at understanding the customer’s needs.
Other areas we’re investing in is our newly refurbished training centre. We want to support our consultant and integrator customers as best we can, so we offer training to suit the customer completely free of charge.
You’ll see us at many of the industry leading events within the region. Apart from attending Intersec Saudi with our security and fire portfolio, visitors will have the opportunity to learn more about our wider product ranges, including Controls and we will also be at Intersec Dubai in January.
Both are strategically important shows for us, and we very much enjoy the opportunity to meet new and existing customers at these events.
With a diverse portfolio, which key vertical markets in the Middle East do you see the most potential in, and how does Johnson Controls’ experience specifically serve those sectors?
Our products and expertise span many verticals, but we have a particular interest in government, hospitality, data centres and the aviation industry.
We can draw on global experience, particularly working with national brands and complex government protocols. Our American Dynamics range of video equipment achieved SIRA accreditation. This was very important to us and means that our equipment is tried and trusted in complex situations.
You mention the SIRA accreditation, which is a significant achievement in the region. What does this accreditation mean for your customers, and why is it so important for the security market in Dubai and beyond?
Achieving SIRA for our American Dynamics video range from Dubai’s Security Industry Regulatory Agency (SIRA) underscores the company’s commitment to delivering cutting-edge security solutions that meet the highest standards.


“What sets us apart is our experience in offering integrated solutions”
SIRA’s rigorous testing process ensures that products comply with stringent regulations and possess the necessary features and functions to safeguard businesses across Dubai’s diverse sectors.
Johnson Controls is known for its integrated product range. Could you elaborate on how your security products work together to offer a more cohesive solution than standalone systems?
We are firm believers in the power of integration and are proud of our industry-leading brands and reputation.
There is much value in products that work together and that can be managed from one software platform. Our OpenBlue platform is a smart building ecosystem that combines a secured and scalable open data platform with AI powered applications to deliver impactful business value across the entire building life cycle.
Intersec Saudi Arabia is a key event for the industry. What will Johnson Controls be showcasing this year, and what can visitors expect to see at your stand?
This year we’re showcasing our Zettler and Fireclass fire detection range and our Access Control and Video Surveillance systems. Visitors will see live demonstrations in real-time and have the opportunity to speak with our product experts. johnsoncontrols.com



Discover the future of security with Johnson Controls at Stand 2-B16, where innovation meets intelligence. The company will be showcasing its cutting-edge access control, and video surveillance solutions designed to elevate safety and streamline operations.
Explore IStar G2 – the simplest way to elevate your security with the software house iSTAR Ultra 2nd generation family of Open MQTT cyber hardened access controllers for up to 32 readers.
Experience C•CURE 3.10 IQ – the latest upgrade in unified security intelligence, delivering smarter insights and enhanced situational awareness.
See Edge AI in Action – the powerful video surveillance system that brings real-time analytics and intelligent monitoring to the edge.
The team from Johnson Controls will be on hand during Intersec Saudi Arabia to answer visitors’ questions, demonstrate its industry-leading technology innovations and showcase how its security solutions can elevate, streamline and achieve results.
Intersec Saudi Arabia, 29 September to 1 October 2025 at the Riyadh International Convention and Exhibition Centre (RICEC)

Building Safer, Smarter Cities: Our integrated security platforms combine access
INNOVATIVE INTELLIGENCE
Intelligent access control readers, AI-powered cameras, and IoT analytics optimise operations, enhance safety, and support sustainability— delivering preventative security that anticipates risks and acts before issues arise.
INTEGRATED SECURITY
Access control, video surveillance, perimeter protection, and cybersecurity—united in a single platform with end-to-end encryption and layered defence. From single sites to smart cities, we deliver uncompromising enterprise protection at every scale.
BECAUSE AT JOHNSON CONTROLS, WE BELIEVE ADVANCED SECURITY PROTECTION SHOULD NEVER BE OUT OF REACH.

Jason Lane-Sellers, Director of Fraud and Identity, LexisNexis® Risk Solutions, shares the hidden threats posed by fraud in the travel industry
Fraud in the digital age poses significant challenges across sectors. The travel industry, with its early adoption of ecommerce channels and reliance on high-value transactions, loyalty programmes and customer trust, is a prime target, especially in light of new tactics that exploit vulnerabilities early in the customer journey.
How can businesses stay one step ahead of tech-savvy fraudsters? The answer lies in a perfect blend of innovative technologies and industry-wide collaboration.
The travel industry has long been a lucrative target for fraudsters and with many operators being early adopters of digital commerce, the sector has long been open to a wide range of vulnerabilities that require strong risk mitigation tools.
I recently had the pleasure of discussing this topic with Gustavo Tonti, Head of Fraud at Destinia – an online travel agency specialising in hotel and international travel bookings – who has
been leading the fight against fraud in the travel industry for more than 20 years.
Tonti says that while traditional scams like stolen credit cards or fake booking sites are as prevalent as ever, tech-enabled approaches such as device spoofing and synthetic identities are making them more difficult to detect. However, fraudsters are not limited to traditional scams. Many have migrated to new routes like loyalty programmes, exploiting weaknesses in security. Tonti explained: “Fraudsters today are not just seeking stolen payment
“The broader challenge for travel companies is how to effectively defend against such a wide range of threats that include account takeover and first-party fraud?”
details. Many now exploit generous promotional offers, sign-up bonuses, or vulnerabilities in loyalty schemes. These often lack the robust security measures found in other parts of the customer journey.”
The broader challenge for travel companies is how to effectively defend against such a wide range of threats that include account takeover and firstparty fraud?
Chargebacks and cancelled bookings remain a visible fraud consequence, but the indirect costs can be equally harmful. Allocating resources to fraud detection tools, staff training and manual transaction reviews puts significant strain on operational budgets.
The most recent LexisNexis® True Cost of Fraud™ Study for the EMEA region reported the actual cost of a fraud loss to a retail business to be upwards of three times the value of the original fraud, resulting from investigating and managing the case.
Another significant consequence occurs when authentic transactions are incorrectly flagged as fraudulent, leading to customer frustration and operational challenges. Tonti elaborated: “If we unfairly block a frequent traveller, they may not only abandon their current booking, but lose trust in our brand, sending them straight into the arms of competitors.”
In an age where social media can instantly amplify a customer complaint to an extensive public

audience, this can quickly escalate to reputational damage, too.
In response, travel companies are leveraging behavioural biometrics, machine learning and bot detection.
Tonti said: “Behavioural biometrics learns from the typical signals generated when a genuine customer interacts with their device, then compares those to subsequent login events to determine if it’s the genuine customer logging in. This has become indispensable as a means to distinguish between legitimate customers and fraudsters, especially in cases such as international bookings where there’s a lack of other customer information available to make a clear assessment.”
Companies like Destinia are also exploring AI-driven real-time assistance and open-source intelligence (OSINT) tools to enhance fraud detection and resolve false positives. Tonti added: “Technology is our first line of defence, but collaboration across the industry is equally vital.”
Fraud in the travel industry is multifaceted – it crosses borders and involves complex stakeholders, such as airlines, online travel agencies, banks and payment platforms. Tackling it requires collective effort.
Tonti reflected on a recent example in which a €16,000 fraudulent booking was intercepted in Dubai. “By leveraging OSINT skills and building connections within the fraud prevention network, we
ultimately protected the cardholder from further damage.”
However, Tonti warned that “to truly stay ahead of fraudsters, regulations must evolve alongside technology and networks, such as allowing behavioural biometrics into permissible evidence for contested transactions.”
Existing regulations make it hard for companies to challenge cases of customers disputing legitimate transactions. Here, too, advanced technologies can help.
Analysing underlying device behaviour involves comparing current transactions with a user’s typical activity patterns. This can help identify whether the user interaction is genuine or potentially fraudulent.
Tonti added: “Behavioural intelligence is about bringing the hidden to the surface, which not only helps prevent financial losses but can also protect reputation by demonstrating accountability and commitment to fair practices.”
If not executed with clarity, complex security protocols can lead to cart abandonment and destroy customer trust and loyalty. “Transparency in the checkout process is critical,” Tonti noted. “Customers should never feel confused or intimidated. Clear communication can alleviate fears and reduce the risk of abandoned transactions.”
For businesses operating in a global market, understanding cultural differences in payment expectations is equally important. Tailoring your customer journey, such as adapting 3D Secure and identity verification requirements to be sensitive to regional and cultural norms, ensures customers feel respected and supported.
risk.lexisnexis.com
From protecting students and staff day-to-day, to streamlining school operations. ICT’s customisable solutions provide built-in access control, intrusion detection, mobile credentials, and extensive integrations. Beyond security, ICT Protege helps you optimise operations so most resources can be spent on education. Secure your success with ICT.

Is she old enough? How often was he here this month? When and where did she enter? Does he appear in videos recorded last week?
Premier face recognition technology for real-time video surveillance, recorded video investigation, crowd detection, and anonymous people analytics www.cognitec.com | sales@cognitec.com Is he on a watch list for banned persons?






Mazen Adnan Dohaji, Vice President & General Manager, IMETA, Exabeam, shares his thoughts on achieving smarter, more scalable SOC strategies in the Middle East with agentic AI
Organisations in the Middle East are rapidly exploring new space when it comes to AI in cybersecurity. As demand for greater efficiency and automation in the security operations centre (SOC) increases, business leaders are looking for solutions that ease workload burdens while proactively fighting threats. This is where agentic AI comes in.
As the region pushes forward with national initiatives including Saudi Vision 2030 and the UAE National Strategy for AI 2031, the conversation is shifting from assistive AI to agentic AI. With the AI agent market expected to reach $2.2 billion by 2030 across the Middle East and Africa, according to Grand View Research, there’s no doubt around the increasing
appetite for and value in autonomous AI systems across the region.
The question is no longer whether AI belongs in the SOC, but can AI deliver results that matter? Security leaders need agentic AI solutions that can take their organisation’s security approach from reactive to proactive by pinpointing gaps, fine-tuning strategies, and justifying investments.
Overpromised capabilities, undelivered value
While there is massive promise and potential around agentic AI in cybersecurity, too many tools lack integration with security operations workflows and still require constant
tuning and interfaces to learn. Most teams are still reactive, chasing false positives, and struggling to respond fast enough.
The challenge lies in deploying agentic AI that doesn’t just collect data but turns it into actionable strategies that Chief Information Security Officers (CISOs) and their teams can operationalise.
Currently, SOC teams across the Middle East are facing several critical challenges that impact their overall efficiency, including:
1. Lengthy threat investigations. Analysts often lose valuable time manually correlating events and building timelines. Many teams still struggle to respond to incidents in less than an hour. For organisations
“The challenge lies in deploying agentic AI that doesn’t just collect data but turns it into actionable strategies”

in the Middle East, this is leading to increased mean time to detect (MTTD) and respond (MTTR).
2. The security talent shortage. According to the ISC2 2024 Workforce Study, the global cybersecurity workforce gap has reached 4.8 million. Across the Middle East, this talent shortage is exacerbated by the region’s rapid digital transformation and the increasing sophistication of cyber threats. This leaves SOCs overextended and understaffed, increasing the risk of threats going unnoticed.
3. AI-powered threats. Attackers are using AI to scale and accelerate attacks faster than traditional detection methods can manage. These AI-powered attacks allow threat actors to automate, customise and evolve their methods in real time. In turn, this increases pressure on analysts as they grapple with unfamiliar threat tactics.
4. Static dashboards. Traditional cybersecurity tools don’t recommend next steps or guide SOC teams on vulnerabilities or areas to improve.
As a result, CISOs are often left piecing together reports from disparate tools or manually chasing metrics from their teams.
At the same time, today’s CISOs are business leaders, responsible for more than just minimising risk. They’re expected to make smart investments, support strategic transformation, protect sensitive data and users, and clearly demonstrate how security operations support their organisation’s growth. The combination of these factors introduces serious vulnerabilities that leave organisations exposed to breaches and increases the mounting pressure on CISOs. Agentic AI changes this by delivering business-ready insights from operational data in real time and presenting them in a way business leaders can understand and utilise.
To keep pace with the Middle East’s everevolving threat landscape, organisations need agentic AI that goes beyond basic task automation and chatbot-style interactions. They need solutions that can interpret data, prioritise threats, streamline investigations and help security leaders continuously improve their security posture.
Agentic AI addresses this by perceiving problems, interpreting context and initiating or recommending next steps. It’s not limited by static rules or rigid playbooks. Instead, it can reason across datasets, adapt to new input and stay aligned with organisation’s policies.
In the SOC, where every second matters, AI-powered automation enables faster, more accurate decisions. CISOs in the Middle East capture new value through:
• Increased advisory insights: With the right agentic AI that supports cybersecurity strategy, CISOs benefit from a proactive solution that turns security data into business-relevant terms, proving value of investments and leadership decisions. SOC teams are supported by measurable insights, recommended targeted improvements and automatically generated databacked roadmaps.
• Improved security maturity: Through agentic AI, CISOs can improve their
organisation’s overall security maturity by uncovering issues like missing log sources, misconfigurations and ineffective threat detection content that weakens security posture. They gain the tools to simulate adjustments or additional security capabilities and benchmark security posture daily.
• Enhanced threat detection, investigation and response (TDIR): Agentic AI is not only augmenting strategic planning and reporting processes, but it also acts as a barrier to stop cyberattacks from infiltrating sensitive data. Agentic AI uses behavioural analytics and adaptive learning to detect deviations from baselines, uncover stealthy techniques, and prioritise high-risk events with contextual risk scoring. This is especially helpful in fighting AI-powered threats.
• Reduced analyst burnout: Agentic AI is capable of analysing every step of a cyberattack, from identifying a vulnerability, to solving the issue, and then producing logs and insights on how to protect SOC operations in the future. With this, security teams can streamline their workloads by offloading repetitive tasks like data parsing and case summarisation. This frees analysts to focus on highervalue work.
AI agents built into the foundation of security operation workflows offer a new way forward for CISOs in the Middle East. More than just copilots bolted on to outdated infrastructure, they can serve as force multipliers — extending SOC capacity while enhancing decisionmaking. Whether it’s a review of the organisation’s security posture, creating executive-level reports that show the SOC’s true value, or an analysis of detections, automation from AI agents can simplify both strategic and routine tasks helping security teams work smarter and faster.
The benefits that agentic AI brings to the region will be key to strengthening operations, protecting against cyberattacks, and guiding future-ready security strategies.
exabeam.com
Trusted for unmatched reliability, global certification, and intelligent fire safety design.

Reduce false alarms with precision detection
Lower lifetime cost without compromising performance
Designed and manufactured in Japan, the UK, and the USA
Networking capabilities for complex and scalable projects

0.001% manufacturer failure ratee
Simple installation and low maintenance design

We Do Fire. Better.
International network of trusted installers
Trusted globally by leading developers and consultants



Contact our Middle East team today to specify Hochiki devices for your next project. Visit www.hochikieurope.com/middleeast or email sales@hochiki.ae



When I established Frontier Pitts Middle East, I was inspired by the company’s global reputation as a trusted leader in perimeter security. What motivated me most was its commitment to innovation, proven performance, and raising standards in environments where safety is critical. From the very beginning, my mission has been clear: to bring reliability, transparency, and education into a security market that often lacked alignment and awareness.
Overcoming Challenges in a Competitive Market
The early days were far from easy. Establishing credibility in a competitive, price-driven environment was an uphill battle. Many clients were accustomed to low-cost, non-compliant solutions and unfamiliar with international crash-rated standards. The turning point came when I stopped positioning us as just equipment suppliers and instead became knowledge partners by organizing workshops, technical presentations, and live demonstrations to show the real value of crash-rated solutions. Slowly but surely, trust followed.
The Madina Munawara Mosque Milestone (KSA)
One defining milestone was the Madina Munawara Mosque Hostile Vehicle Mitigation project. This was a deeply sensitive assignment, requiring a balance of security, cultural respect, and accessibility for millions of worshippers. Successfully delivering this solution elevated our reputation, proving that we could combine technical excellence with cultural awareness to protect some of the region’s most important landmarks.
“In the security sector, reliability ensures that equipment, procedures, and people function as intended, providing trust in critical moments.”
Since those early days, we have grown into a team of more than 14 professionals, expanding from small perimeter installations to complex, high-profile security solutions across the UAE and GCC. Beyond physical protection, our impact extends into raising awareness, mentoring young professionals, and supporting internships that prepare the next generation of security leaders. This combination of engineering excellence, local presence, and thought leadership is what makes us unique in the industry.
As a leader, I have always believed in collaboration and empowerment. Our team culture is built on accountability, problemsolving, and innovation, qualities that allow us to adapt to emerging challenges, from EV impact threats to cyber-resilience in HVM systems. Mentors and colleagues across the UK and Middle East have been instrumental in this journey, and my wife has been my greatest partner, offering unwavering support and encouragement as I navigated complex projects across the region. This reminds me that strong relationships are as vital as strong engineering.
Values that Define Our Work
At the heart of my work are the values of trust, integrity, and excellence. These are not just words; they shape every decision, from transparent communication to meticulous testing and compliance with international standards such as IWA14, PAS68, and ISO. What sets Frontier Pitts Middle East apart is our ability to deliver tailored, high-performance solutions that do not just protect people and assets but also respect the cultural and operational realities of the region.
Today, I am most proud that Frontier Pitts Middle East is trusted to protect critical infrastructure across the UAE and GCC, including airports, government buildings, cultural sites, and commercial hubs. Looking ahead, my vision is to strengthen our role as the region’s leading manufacturer of perimeter security, harnessing advanced technologies such as AI monitoring, cyber-resilient systems, and smart access control to keep communities safe.
Why should customers choose Frontier Pitts Middle East? Because reliability is our foundation. In the security sector, reliability ensures that equipment, procedures, and people function as intended, providing trust in critical moments. Every barrier, bollard, or system we deliver is built on that promise.
12 – 14 January 2026
Dubai World Trade Centre
The world’s premier event for Security, Safety and Fire Protection.
50,000+
Visitors
1,300+
Exhibitors 61 Exhibiting Countries 140+ Visiting Countries

ENQUIRE TO EXHIBIT

Security Middle East magazine spoke with Trevor , Director of Middle East Sales and Kassem Saad, Sales Manager for Saudi Arabia at March Networks, about how intelligent video is shaping the Kingdom’s rapidly growing hospitality sector
Q: March Networks is best known for serving Fortune 500 banks and retailers. How does that experience translate into hospitality, especially in Saudi Arabia?
: Our reputation is built on delivering scalable, flexible solutions for some of the world’s largest banks and retail chains. We’ve perfected enterprise deployments across thousands of sites, where compliance, security and efficiency must all work seamlessly.
That expertise applies directly to hospitality. International hotel groups face similar challenges – scale, brand standards and complex operations. We already work with luxury hotel brands like Marriott, Hilton and IHG, so we bring proven hospitality credentials.
Saudi Arabia makes this especially relevant. Vision 2030 is driving a hospitality boom with new resorts, hotels and entertainment destinations. Our track record with global enterprises positions us to help operators here build secure, intelligent and future-ready environments.
Q: What role does video surveillance play in this transformation?
Traditionally, video meant monitoring. Today, with AI and analytics, it means intelligence. Our platform integrates with hotel systems – property management, POS, access control and RFID – so that every event, from a guest check-in to a restaurant transaction, can be linked to video. Operators gain both security and actionable insight in
Q: How does that translate into the guest
Guests expect personalisation. With licence plate recognition and facial
recognition, hotels can identify VIPs the moment they arrive, tailor services and discreetly manage risks. People-counting analytics help optimise staffing and lobby flow, ensuring guests feel recognised, safe and well cared for.
Q: What kind of traction does March Networks already have in Saudi Arabia?
Kassem: We’re proud to be vendorapproved by three Public Investment Fund (PIF) entities, including Red Sea Global. We also partner with system integrators specialising in hospitality to ensure local expertise. With our technology already recognised by leading international hotel groups, properties in the Kingdom can move forward with speed and confidence.
Q: Security is still at the core of hospitality. How do your solutions support that?
Trevor: Our analytics detect loitering, overcrowding or suspicious behaviour in real time. We integrate access control with guest data for tighter protection, and audit logs simplify investigations and compliance reporting. It gives security teams the tools to act fast and meet regulatory standards.
Q: Beyond security, hotels are under pressure to operate more efficiently. How does video help?
Kassem: Video analytics also drive efficiency. Integrated with building management systems, they automate lighting and HVAC for energy savings. In restaurants and retail outlets, POS integration detects fraud and verifies transactions. And at construction sites for mega projects, our surveillance safeguards assets and worker safety.

Q: What about cloud adoption and cybersecurity – two hot topics in the Kingdom?
Trevor: Some operators still prefer on-premise, but others are ready for cloud. Our Cloud Suite enables centralised video management across multiple properties, with analytics accessible anywhere. On cybersecurity, our CyberSuite delivers system health monitoring, asset reporting and regular updates. Protecting guest data is as critical as protecting physical property – and some of the world’s largest most complex banks trust our cybersecurity.
Q: Why should Saudi hospitality leaders choose March Networks?
Kassem: Because we combine international credibility with local presence. Globally, we’re trusted by over 2,000 financial institutions and retailers. Locally, we’re investing in partnerships, people and projects in Saudi Arabia. We’re here to support the Kingdom’s hospitality ambitions with intelligence, security and innovation.
Contact: Kassem Saad, Sales Manager –Saudi Arabia ksaad@marchnetworks.com marchnetworks.com

Hadi Jaafarawi, Regional VP – Middle East & Africa at Qualys, makes the case for a Risk Operations Centre and the ability to finally control the relationship between value and risk management

Risk is a way of life. As it is for individuals, so it is for businesses. Enterprises across the Middle East have in recent years had to deal, either directly or indirectly, with a series of global shocks — a health crisis, followed by a recession, followed by inflation, intermingled with shift after shift in consumer expectations. In response, the nation’s businesses have had to leverage whatever technical tools were available to satisfy consumers, regulators and investors.
Today, staying solvent and relevant requires a balancing act that inevitably leads to conversations about risk management. Business stakeholders want as little risk as possible, but in trying to formulate a real-world action list, it quickly becomes obvious that you can’t eliminate all risk. The Risk Operations Centre (ROC) has arisen to formally orchestrate this challenging process of managing risk at scale — helping businesses understand what risk they need to eliminate or mitigate, and what risk needs to be accepted or transferred. Let’s start by defining our terms. We might think of risk as a way to describe an ecosystem of uncertainties where at least some of the outcomes are undesirable. Even in that limited view, the number of uncertainties and the severity of the outcomes are themselves subject to uncertainty. And what about the negative outcomes that result from unpredictable events? In practical terms, the organisation must seek to detect all possible scenarios and sources of harm, and to do so repeatedly, in the course of its risk management journey.
Our challenge is therefore to measure risk — to somehow quantify the likelihood of future setbacks. We need metrics that express a reduction in uncertainty given certain conditions and subsequent actions. As we try to do so, we must define what ‘elimination of risk’ means to us. What risk managers really need to do is to set boundaries of acceptability. In cyber insurance, for example, we find the concept of risk tolerance where verifiable levels of risk are compared to some preset limit that is contractually defined.
“Our challenge is therefore to measure risk — to somehow quantify the likelihood of future setbacks”
Besides just monitoring and measuring risk, the ROC is also a hub for continuously orchestrating the mitigation and remedying of risk to align with a predefined tolerance level. And since every modern business is a digital business, we are talking, in large part, about cyber risk. At this point, we should note the differences between the ROC and the Security Operations Centre (SOC). The SOC gathers and acts on security alerts while the ROC uses SOC data to provide all stakeholders, from the CFO to the lead compliance officer, with actionable information that allows them to manage risk collaboratively.
In my experience, the ROC is often established by the CISO, who will aggregate information on risk into a data lake. This requires building a comprehensive digital asset register and a full-stack vulnerability list and then integrating multiple threat-intelligence feeds. It also necessitates the invention of controls to compensate for risks that cannot be immediately fixed and coming up with ways to use the new stack to automate mitigation and remediation. This is no easy task. While it is difficult to gauge precise figures for the Middle East, a 2021 global estimate from Panaseer suggests the average organisation may be using as many as 76 security tools. Regional CISOs may find themselves in the ironic position of having to incorporate past security investments into their current risk profile.
As the CISO moves forward with their creation of an ROC, they will find that event-oriented data from the SOC can only act as a foundation for risk measurement. High-volume, rapidly accumulated SOC data lacks the requisite business
context to be useful in its raw form to risk managers. The ROC’s job is to provide visually rich, context-sensitive information that supports sophisticated analysis of potential sources of harm and enables effective responses. Hence, the ROC is all about protecting value and minimising loss.
One of the unfortunate realities of business risk is that it tends to increase with success. Each enterprise has a ‘risk surface’ — or how much it stands to lose. The ROC is responsible for monitoring this surface and continually managing the business’ exposure to potential loss. We can already see enterprises embracing the ROC concept. In the fourth quarter of 2024, KPMG Lower Gulf launched what it calls a “risk hub” in the UAE, built around a Governance, Risk and Compliance (GRC) service. In the coming months, we are likely to see more moves like this across the nation, as ROCs become focal points for addressing challenges faced by the modern UAE business.
Approaches to the construction of ROCs are still in their infancy, but if each company assesses its own realities against its goals and puts the right authority in the hands of the right teams, progress could be rapid. Collaboration between CISOs, CFOs and compliance officers will be of particular importance, as will partnerships with peers and vendors. As cybersecurity risk grows in intensity, quantification will be of great help in the mitigation battle. The ROC will be pivotal in bringing the right data and know-how together to shield the enterprise from the worst its adversaries can throw at it.
qualys.com
The greatest threat to international security is in the palm of your hand. Fortunately Braniff Enterprises is here to help

Across the Middle East, a remarkable transformation is underway. Ambitious national visions from Saudi Vision 2030 to the UAE’s Centennial 2071 plan are charting a course away from hydrocarbon dependency and towards diversified, knowledge-based economies. This future is being built on a foundation of digital innovation, global investment and strategic international partnerships. However, as we construct these gleaming towers of progress, we must ask: how secure is their digital foundation?
Securing mobile devices has never been a higher priority. Privileged and confidential information exchanged on mobile devices is more at risk than ever before, with the added complexity of securing high value data without sacrificing necessary smartphone utilities.
Traditional solutions have proven inadequate. Commercially available smartphones, while powerful, are built for consumer convenience, not for the rigorous security demands of national leadership. App-based encryption offers a partial shield but fails to protect the device’s underlying operating system, leaving the device vulnerable to compromise.
Today’s smartphone users demand perfection in device utility. The ability to use mobile apps for email, instant messaging, calling and video calling, word processing and social media is the bare minimum. In addition to this minimum standard, photos, videos, location-based services and comprehensive mobile services including global talk/text and Internet access are essential. A singular device which meets
consumer demands and enterprise security standards has not been available in the MENA region until now.
The ESP-OS platform provides the ultimate blend of security, privacy and utility for enterprise, government and ultra-high-net-worth individuals with valuable information to protect. Standardised yet highly customisable, the ESP-OS platform defines mobile security at scale or at home.
Key features of ESP-OS include:
1. AI-enhanced Protection: Active Malware Scanning & Exploit Protection Active scanning and protection against the leading mobile security and privacy threats (ex: NSO Pegasus).
2. Secure App Containers and Storage
Use all your favorite apps, securely (ex: WhatsApp, Outlook).
3. End-to-End Encryption
AES-256-XTS and AES-256-CTS, enhanced by hardware-based security features. This system ensures that data is encrypted both at rest and in transit.
4. Device Identity Spoofing*
*Note: IMEI spoofing requires specialised hardware and may not be legal for civilian use in your region. This capability will only be provided to authorised customers.
5. Multi-Profile and Multi-SIM
Split your device into 31 different unique phones with their own applications, authentication
(unique encryption keys) and even phone numbers / eSIMs. Using multiple eSIMs, you have access to local data and a local phone number worldwide.
6. Remote Wipe and Duress Capabilities
Securely wipe the device remotely by sending a secret code via text or IM. Input a ‘duress password’ (if forced to divulge your password) on authentication to securely wipe the device before loading the OS. Either method renders your data unrecoverable.
7. Self-Destructing Profiles
Use a self-destructing profile for any supported ESP-OS function. Upon exiting the profile, all data will be securely wiped and is unrecoverable.
8. Fully Custom Operating System Design Available
Customise your devices at the OS-level for the most sensitive workloads and granular use cases.
9. Enterprise Support
And more…
Revolutionise your approach to secure mobility: sme@braniffenterprisesllc.com




and what UAE businesses must do to protect themselves, according to Danny Jenkins, CEO and co-founder of ThreatLocker®
As a nation rapidly embracing AI, cloud computing and digitalisation, the UAE is undergoing a significant transformation. But as innovation accelerates, so too do cyber threats, many of which now use artificial intelligence (AI), particularly generative AI. The result? A rise in sophisticated attacks leveraging AI. According to a Cisco study, 93% of organisations in the UAE faced AIrelated incidents in 2024. Similarly, the UAE Cyber Security Council oversaw a growing trend in AI-driven threats at the beginning of 2025.
What was once the domain of highly skilled individuals with deep technical knowledge is no longer the case. Today, with the rise of generative AI tools – such as large language models, AI-powered code generators and synthetic voice systems – almost anyone can launch a sophisticated cyberattack. AI can generate polymorphic code on demand, including scripts capable of evading traditional antivirus detection by not matching known malware signatures.
This dramatically lowers the barrier to entry, expanding the pool of potential
attackers – including those with limited technical skills but malicious intent or financial incentive. This shift introduces unprecedented risk, demanding a fundamental change in how UAE organisations defend their systems.
Tapping into hackers’ mindsets
Hackers are not bound by rules; they think opportunistically, scanning for any weak point that offers an easy way in. Attackers take advantage of decentralised IT environments, shadow IT and the
assumption of internal trust that still underpins many corporate networks.
For UAE businesses, this means even a single misconfigured setting, untrusted application, or outdated system can become the entry point for a costly breach.
Cybercriminals often aim to exploit the fast-paced adoption of cloud and digital services in the region, seeking gaps in visibility and trust. To remain ahead, UAE businesses must proactively secure their environments. By blocking unknown or unauthorised software and simulating real-world attacks such as penetration testing and red teaming, companies can uncover blind spots before attackers do.
In this evolving threat environment, traditional detection-based tools – such as antivirus software and behavioural monitoring – are increasingly ineffective. Threats can now be customised in realtime and delivered using legitimate, signed applications or obfuscated payloads.
UAE businesses must adopt a Zero Trust security model. Embracing a Zero Trust framework aligns with the UAE’s National Cybersecurity Strategy and supports compliance with local standards such as the Information Assurance Standards (IAS) and DIFC data regulations. This approach rejects the outdated assumption that anything inside the perimeter is trustworthy. Instead, it is built on the principle of “never trust, always verify”, and mandates that nothing runs or communicates unless it has been explicitly authorised.
Even the best-prepared environments must assume compromise is possible. That’s why 24/7 monitoring, alert triage and rapid incident response remain critical components of a modern cybersecurity strategy. Whether handled in-house or through a managed detection and response (MDR) provider, UAE companies must act on alerts immediately.
Automated actions – such as disabling administrator tools, isolating systems from the network or revoking access to sensitive data – can contain threats while human analysts investigate. This combination of prevention and real-time response dramatically reduces dwell time and limits the scope of breaches.
1. Controlling application execution
UAE organisations must restrict which software is allowed to run – not just traditional executables, but also scripts, libraries and portable tools. Only explicitly authorised applications should be permitted, preventing unknown or newly compiled code from executing. Companies should audit or restrict browser extensions due to their elevated permissions.
2. Limiting application behaviour
Even trusted applications can be exploited. Their behaviour should be tightly controlled, preventing unnecessary internet access, file access, registry access, or inter-process communication. For example, a PDF reader should not initiate outbound connections or modify system settings.
3. Managing administrative privileges
Excessive privileges make lateral movement and persistence easier for attackers. Accounts with administrative rights should be limited, monitored and regularly audited. Dormant accounts must be removed from privileged groups to reduce attack surfaces.
4. Network security
Host-level network control is critical. By default, all inbound ports should remain closed for workstations, only opening dynamically for explicitly authorised traffic. Outbound traffic from servers should be tightly regulated, as many breaches rely on outbound communication to Command and Control (C&C) servers.
5. Data protection
Organisations must isolate and protect sensitive data, particularly backups. It is also critical to block unauthorised access, modification or exfiltration even from otherwise trusted applications or users. Controls on portable storage should enforce encryption and restrict usage.
6. Web content control
Filtering internet access prevents exposure to malicious content and limits shadow IT risks. Blocking categories like advertising networks, unapproved cloud services and unauthorised AI tools reduces exposure to emerging threats.
7. Consistent patching
No security model is complete without timely updates. Operating systems, applications and even portable tools like SSH clients must be patched regularly to eliminate known vulnerabilities that could be exploited in an attack.
The rise of generative AI has permanently changed the threat landscape globally. For a country like the UAE that is committed to digital transformation and innovation, it becomes even more critical to protect themselves from AI-powered attacks. The tools available to attackers are more powerful, accessible and scalable than ever before. Businesses must stop assuming that good intentions or basic antivirus protection will keep them safe.
A Zero Trust strategy, built on strict enforcement of least privilege and
application control, offers a proactive defence suited for today’s AI-powered threats. It accepts that human error and software vulnerabilities are inevitable, and builds a layered defence to minimise their impact.
By controlling what runs, what it does, and who can access what, UAE companies can reduce their exposure and shrink the attacker’s opportunity window. In the age of generative AI, that may be the most powerful security tool we have.
threatlocker.com



As emergency, defence and security sectors worldwide adapt to evolving communication landscapes, the shift from traditional digital radio services like TETRA to advanced broadband networks capable of Mission Critical Services (MCX) is gaining momentum. This transition, driven by the need for enhanced multimedia, robust data support and greater operational efficiency, demands a new generation of mobile technology. Stepping into this space, Zebra Technologies recently introduced its FR55 first responder mobile computer, designed to support frontline operations during this crucial period of change. The FR55 is engineered to meet the dynamic requirements of modern emergency response. It offers comprehensive broadband capabilities, supporting 4G/LTE and 5G connectivity as services gradually migrate to these networks. A key feature is its MCX integration, ensuring interoperability
with existing narrowband systems like TETRA, DMR and TETRAPOL. This means agencies can transition at their own pace while maintaining essential communication links. Airbus Agnet solution, integrated into the FR55, further enhances its MCX capabilities, providing access to voice, data, live video and location services with encryption.
Beyond core connectivity, the device incorporates WiFi 6E and Bluetooth v5.3 for secure network access, alongside Evolved Multimedia Broadcast Multicast Services (eMBMS) to ensure reliable support in high-density environments such as large public gatherings. A top-mounted emergency duress button provides a rapid call for assistance. According to Oliver Ledgard, Public Safety Strategy Director for EMEA at Zebra Technologies, the FR55 was designed around the direct needs of frontline workers, addressing issues like bandwidth limitations and spectrum


availability to facilitate secure multimedia communication and advanced data handling.
Underpinning the FR55 capabilities is a Qualcomm processor, offering robust performance and long-term OS support up to Android 18. This future-ready design allows the device to handle multiple applications simultaneously, process data efficiently and provide secure geolocation, with future potential for AI and augmented reality applications. zebra.com






INNOVATING TO PROTECT SAUDI PROGRESS

We are honoured and delighted to welcome you to Intersec Saudi Arabia 2025, taking place from 29 September to 1 October 2025 at the Riyadh International Convention and Exhibition Centre (RICEC)
Held under the patronage of His Royal Highness Prince Abdulaziz bin Saud bin Naif bin Abdulaziz Al Saud, Minister of Interior, and in association with the General Directorate of Civil Defense, this year’s edition marks an important milestone in the event’s journey and continued contribution to the Kingdom’s safety and security ecosystem.
After a record-breaking edition in 2024, this year’s show reflects even greater momentum. Over 370 exhibitors from more than 35 countries will showcase over 1,000 brands across seven halls and a dedicated outdoor area. With exhibition space now totalling 30,000 sqm, and more than 27,000 visitors expected, Intersec Saudi Arabia 2025 continues to grow in both scale and impact.
The show presents a comprehensive showcase across five product sectors:
Commercial & Perimeter Security, Homeland Security & Policing, Fire & Rescue, Safety & Health, and Cybersecurity, and features rich learning and engagement opportunities. Our CPD-certified content theatres include the Future Security Summit (Powered by ASIS International Middle East) and the Fire Protection & Technology Summit, each offering deep insights into the critical topics shaping our industries.
We are especially pleased to highlight the Majlis at Intersec Saudi Arabia, which play a central role in hosting official delegations and key government entities, providing a dedicated space for high-level dialogue and meaningful engagement, as well as the return of the Intersec Saudi Arabia Premium Club, which offers enhanced networking and hospitality experiences for key buyers and decision-makers.
On behalf of the team at Messe Frankfurt Middle East and our organising partners at 1st Arabia, I would like to extend our sincere thanks to all our exhibitors, speakers and visitors for their invaluable support.
We look forward to welcoming you in Riyadh as we shape a safer, smarter and more secure future together.
Warm regards,

Riham Sedik
Exhibition Director
Intersec Saudi Arabia
Messe Frankfurt Middle East
With the Middle East security market on a strong upward trajectory, Saudi Arabia stands at the forefront of this transformation. As national development accelerates, driven by ambitious GIGA projects and cutting-edge smart city initiatives, the need for modernised, future-ready security solutions has never been more urgent. This growing security ecosystem spans government facilities, transportation networks, healthcare systems and commercial developments, creating unprecedented opportunities for innovation and strategic partnerships
across the Kingdom. The future-focused and innovation-led Future Security Summit features two days of content delivered by visionary leaders, uniting global thought leaders, policymakers, innovators and industry professionals to explore the technologies, partnerships and policies reshaping regional security. Key themes:
Sustainability in Security: Strategies for Large-Scale, Long-Term Protection
Cyber-Physical Security: Safeguarding Critical Infrastructure Against Converging Threats
Regional & Global Security
Cooperation: Building Stronger
International Partnerships
Security in Smart Cities: Designing Resilient Urban Environments

Mega-Event Security Excellence: Mastering the Complexities of LargeScale Public Gatherings
Securing Transportation Infrastructure:
Ensuring Safety Across Complex Mobility Networks
AI in Security: Harnessing Artificial Intelligence for Predictive and Proactive Protection
11:00 Registration & Networking
11:10 Opening Remarks Conference Chairperson
11:15 Keynote Address/ Keynote Speech by Patron
11:30 Panel Discussion
Beyond Borders: Regional and Global Security Cooperation in a Shifting Geopolitical Climate
12:10 Presentation
Cybercrime in the Age of Convergence: People, Promises, and Policies at the Crossroads of Reality and Digital Threats
12:35 Panel Discussion
Mega-Event Protection Excellence: Mastering the Security Challenges for Large-Scale Gatherings
13:15 Presentation
Next-Generation Border Security
13:40 Presentation
The Era of the White Swan: Are You Truly Prepared for the Inevitable?
14:05 Presentation
Open Standards: A Foundation for Smarter, Safer Cities
14:35 Panel Discussion
Security Operations Centers (SOCs): Designing for Emerging Threats
15:00 Presentation
Designing Cities for Safety: Embedding CPTED and Security in Urban Master Planning
15:25 Panel Discussion
Experience meets Energy: Reimagining Security Talent
16:00 Panel Discussion
Giga-Projects Security: Specialised Protection Frameworks for Sustainable Development
16:40 Panel Discussion
Women in Security: Building an Inclusive Security Workforce for the Future
17:20 Presentation
Saudi Arabia’s $20 Billion AI Strategy: Security Implications and Opportunities
17:40 Closing Remarks & Day 1 Summary

11:00 Registration & Networking
11:15 Recap of Day 1 by Konstantin Turuntcev, Managing Partner | Event Concept Consultancy QFZ LLC
11:30 Keynote Address
Security & Risk Management: Lessons from the Field
11:50 Ethical AI Focus
Ethical AI for a Secure Future: Balancing Innovation and Responsibility in Security Applications
12:10 Presentation
Overview of Optimum Recovery and Social Contribution
12:30 Presentation
Cyber-Secure Transformation: Balancing Innovation, Risk and Resilience
12:50 Healthcare and Utility Focus Fireside Chat
Security Command: Lessons in Crisis-Driven Innovation
13:20 Tourism Focus Presentation
Securing the Tourism Renaissance: Integrated Physical Security Solutions for the Hospitality Sector
13:40 Aviation Focus Presentation
Elevating National Airspace Security: Strengthening Aviation Resilience Across an Expanding Network
14:05 Entertainment Focus Fireside Chat
Designing for Experience and Safety: Embedding Security into the DNA of Modern Entertainment Venues
14:20 Transport Focus Presentation/ Fireside Chat
Protecting Transport Infrastructure: Physical Security Strategies for Smart Mobility Systems
14:40 Presentation
Beyond CCTV and Firewalls: Designing National Security in an Age of Hybrid Threats
15:05 Presentation
Rethinking Security Through Context, Culture and Capacity
15:25 Presentation
The Threat Assessment Process in The Built Environment
15:45 Presentation
Converging Worlds: Integrating OT Security into Saudi Arabia’s Critical Infrastructure Defense Strategy
16:05 Presentation
Building a Culture of Safety: Public Awareness and Empowerment in the UAE
16:20 Energy, Mining & Manufacturing Focus
Securing the Next Generation of Critical Infrastructure
16:40 Presentation
Industrial Resilience in Action: Security Strategies for Energy, Mining, and Manufacturing
17:00 Closing Remarks & Day 2 Summary

STUART MCHUTCHON
Deputy Director, National Security & Resilience | TAG International

ENG. MOHAMMED SALEH
Security Engineering Director | SIRA

RAJEH ALSUBEIA
Director - Emergency Preparedness & Planning | Ministry of Environment, Water and Agriculture, Kingdom of Saudi Arabia

ABDUL AZIZ S. AL SHAFI,
VP Cybersecurity | Aramco

Safety & Security Director | Ministry of Finance

Safety & Security Director | King Salman Park Foundation

Country Manager and Chief of Center of Excellence | United Nations Office on Drugs and Crime (UNODC)

THAMER ANWAR NOORI
Director, Industrial Security & Safety | Royal Commission for Jubail and Yanbu

Senior Manager - Investigations Unit, Security, Environment & Sustainability Operations | Red Sea Global
30,000SQM of exhibition space

TAWFEEQ ALSADOON
Group Head of Security | Red Sea Global

Digital Transformation Director, Resorts Holding

LT. COL. DR. HAMAD KHALIFA AL NUAIMI
Head of Telecommunications Division - Information Technology Center | Abu Dhabi Police
1,000+ top brands to explore 27,000+ industry peers to network

ADNAN ALGHAMDI
Aviation Security Advisor | General Authority of Civil Aviation (GACA)

Senior Vice President, Safety, Security & Sustainability | Maaden

Head of the UNODC Regional Center for Combating Cybercrime | United Nations Office on Drugs and Crime (UNODC)

Corporate Security Head | Government Confidential

KHALID BUALI
VP - Industrial Security | Aramco

Head of the Security Management Department & Acting Head of the Police Sciences Department | Naif Arab University for Security Sciences

Hochiki, a global leader in life safety technology with over 100 years of manufacturing heritage, will be present at Intersec Saudi Arabia 2025 on Stand

Rapiscan is an industry leader in security checkpoint technology, providing screening systems to help borders, ports, airports, military, high-threat locations and law enforcement combat terrorism, smuggling and trade fraud. Its broad array of scanning systems leverages X-ray inspection, optical inspection and radiation detection technologies to address each customer’s unique security application requirements. Customers can further enhance inspection capabilities and operational efficiencies with its analyst assist tools and data integration platform to automate manual processes, control workflows and deliver targeted, actionable intelligence. Visit Rapiscan at Intersec Saudi Arabia where it will demonstrate a range of its checkpoint security technology, including facial recognition, vehicle classification, vehicle and baggage X-ray screening, undervehicle inspection, metal detection and more. Rapiscan’s commitment to quality and innovation ensures its solutions help customers find threats and contraband with ease and confidence. rapiscan.com
5-E09. Its Japan-designed systems — fully certified to UL, FM, and EN standards — are engineered for uncompromising performance and reliability in high-risk environments. From critical infrastructure to commercial developments, Hochiki’s addressable fire detection and emergency lighting solutions provide intelligent control, flexible configuration and effortless scalability.
Gallagher Security is poised to demonstrate its cutting-edge security solutions at Intersec Saudi Arabia 2025, reaffirming its dedication to enhancing safety through advanced technology. Attendees can look forward to detailed demonstrations of Gallagher’s Perimeter Security solutions, meticulously designed to protect critical boundaries with robust monitoring capabilities.
The Access Control system will showcase seamless entry management, offering organisations a streamlined approach to securing premises. In addition, Gallagher will unveil AccessNow, a user-friendly mobile access solution that enhances convenience and flexibility for employees and management.
Highlighting the importance of integrated security management, Gallagher will also feature OneLink, a platform that unifies all security functions, providing operators with a comprehensive view and control of their security landscape.
Furthermore, Gallagher is excited to showcase its latest advancements in security technology through integrated collaborations with its esteemed partners, including Idemia, Commend, Penguin Solutions, Garrett and Torus. Together, they will illustrate how these seamless integrations elevate overall security and safety solutions. security.gallagher.com
With a reputation for precision engineering and long-term resilience, Hochiki supports the security sector with robust, high-integrity systems built to meet international and regional demands. Visit the expert team at Stand 5-E09 and explore solutions trusted across the globe.
hochiki.ae

Intelligent Security Systems (ISS) stands at the forefront of AI-driven video analytics innovation. At the heart of its offerings is the SecurOS® platform, an end-toend solution renowned for its seamless integration with most third-party security systems. The state-of-the-art solutions leverage the latest advancements in video intelligence technology, encompassing the SecurOS® VMS, SecurOS® Auto, SecurOS® Cargo, SecurOS® Tracking Kit and the SecurOS® UVSS, which has recently been manufactured in Saudi Arabia.
At Intersec Saudi Arabia, ISS will unveil two groundbreaking solutions: the SecurOS® ITS, an AI-powered platform designed to enhance traffic monitoring and streamline transportation infrastructure management by addressing accidents and moving violations; and the SecurOS® Stadium, a suite of AI-powered solutions for sports events meticulously engineered to meet the security requirements of the FIFA World Cup Saudi 2034. issivs.me

HID is a global leader in trusted identity solutions, with over 30 years of experience enabling secure access to physical and digital spaces, safe
At the 2025 Intersec Saudi Arabia Show, CommPort Technologies will be demonstrating advanced field-proven under vehicle inspection systems (UVIS) with image scanning technology

Zenitel will be elevating cyber-secure communications at Intersec Saudi Arabia 2025.
Building on its debut at Intersec Saudi Arabia in 2024, Zenitel returns in 2025 to showcase its advanced Intercom, Public Address & Voice Alarm (PAVA), IP Speaker and Unified Critical Communication solutions.
A highlight is the VIPEDIA/Integra PAVA system — the industry’s first
transactions and seamless travel. Headquartered in Austin, Texas, and part of ASSA ABLOY, HID operates in 100+ countries, including the Middle East and Africa since 2010. With expertise in Physical Access Control Solutions, HID helps governments, organisations and institutions protect assets, streamline operations and enhance user experiences. Visit the HID stand, 1-B24, to see the latest facial recognition readers, ecofriendly credentials, class-leading Mobile solutions including Wallet integrations and more. hidglobal.com

Integrated Control Technology (ICT) will be exhibiting on its distribution partner’s stand Mobius, 3 C12.
for eliminating bottlenecks at ports, borders, airports and other high-volume vehicle inspection needs. As the original authority and industry leader for specialised UVIS, the company will be at stand 4.B10. Offering best-ofbreed products since 1998, CommPort continues to bring high performance and field-proven UVIS technology with the CPAS and HH-300 product lines. The sales team and technical engineers will be on site to answer any needs for special requirements on your next UVIS systems. cpuvis.com
Gaurav Mahajan, Sales Director Middle East and Africa, will be demonstrating ICT enterprise access control platform and its range of readers, expanders and input modules, physical and mobile credentials. Scalable and open, Protege GX platform unifies access control and intrusion detection, and interfaces with many thirdparty systems to improve security and operational efficiency. Its integration with lift manufacturers, including Kone Office Flow helps manage people flow through multistorey buildings. Access security can be tightened with its integration with Suprema and Idemia biometrics readers, and VMS platforms such as Milestone XProtect. ict.co
voice alarm system compliant with IEC 62443-4-2 cybersecurity standards. Security by design is central to Zenitel’s philosophy, embedding encryption, authentication and zero-trust principles into every product. Attendees will meet Zenitel’s Middle East team, reinforcing the company’s commitment to secure, mission-critical communications in the region. zenitel.com


Q: Progress has made clear its deepening commitment to KSA. What tangible initiatives signal this isn’t just market entry — but long-term partnership?
A: Our presence in the Kingdom is not defined by systems — it is defined by integration. We have embedded ourselves within the fabric of Saudi operations, aligning every solution with the Kingdom’s regulatory standards, cultural context and operational rhythms. This means designing solutions that don’t just function — they resonate.
Q: How does Progress’s solutions directly advance KSA’s digital transformation agenda?
A: Digital transformation without secure, intelligent physical infrastructure is incomplete. At Progress, we don’t merely deploy technology — we construct integrated, resilient secure ecosystems. Our platforms enable real-time situational awareness across critical sites, turning fragmented systems into unified, adaptive networks. We deliver protection that anticipates — not reacts. This is not digitisation. It is the foundation of sovereign security: where technology empowers operators to act with precision, confidence and foresight — exactly as Vision 2030 demands.
Q: Vision 2030 hinges on mega-projects, economic diversification and quality of life. How do your solutions enable these pillars?
A: Our decades of experience delivering security for the region’s most complex projects — from global financial hubs to critical infrastructure and large-scale industrial zones — provides a proven, scalable methodology for mega-projects.

Our diverse sector track record in energy, transport and finance means we understand unique operational challenges and can apply best practices to avoid pitfalls.
Furthermore, our strategic partnerships with leading international partners give us direct access to global innovation and supply chain certainty, ensuring best-inclass, reliable solutions.
Ultimately, we provide more than security; we provide the certainty of a partner with a documented history of regional success, built to support the ambition of Vision 2030.
Q: Collaboration is key. Who are your most impactful partners in KSA, and how are you co-creating the future?
A: True national progress is never outsourced — it is co-owned. We partner
with operators across the public and private sectors not as integrators, but as stewards of their mission. Our solutions are designed into workflows, not bolted onto them. We embed ourselves within governance structures, so security becomes an intrinsic part of daily operation. But our most vital partnership is with the people of Saudi Arabia. We invest in local talent — training engineers, analysts and operators to master, manage and evolve our solutions. This is not about deploying technology — it is about empowering a generation to safeguard the Kingdom’s future.
Learn more about the transformative alliance that has been forged between IFPO and PSSA
In a world where safety and security are paramount, empowering the professionals behind the scenes has never been more crucial. The Professional Security and Safety Alliance (PSSA) and the International Foundation for Protection Officers (IFPO) have joined hands in a purpose-driven alliance: to uplift, educate and certify security professionals at all levels, locally and globally. Since the inception of our collaboration, IFPO and PSSA have worked tirelessly to ensure that security professionals, especially frontline personnel, have access to meaningful development opportunities. From certification programmes to recognition ceremonies, our initiatives are grounded in real-world impact.
In the early phases of our partnership, we launched a landmark webinar session moderated by Nadeem Iqbal, the Regional Director of IFPO MENASA, where the mission and offerings of IFPO were highlighted. The session drew participation from a wide crosssection of the security industry, including field officers, managers and aspiring supervisors. This was followed by an interactive Q&A session, creating a safe space for professionals to explore how IFPO programmes could support their growth.
As part of our ongoing commitment to support learning and certification, IFPO offered 25 free Certified Protection Officer (CPO) and 25 Certified Security Supervision and Management (CSSM) courses for PSSA members in 2025. This generous gesture underscores our belief that financial limitations should never stand in the way of progress. Already, 10 CSSM seats have been filled, and we are seeing the real-time impact these programmes are making on the careers and confidence of those enrolled.

Beyond education, we recognised the importance of celebrating and awarding those who serve tirelessly. Through our joint efforts, we organised several platforms where security officers and professionals were honoured. These recognition events were more than just ceremonies; they were a validation of the vital role played by security personnel and a reminder to the broader industry that every effort counts.
However, our impact has not been limited to certifications. Through this alliance, numerous events have been held that serve as transformational platforms, not only celebrating achievements but nurturing growth. These events are designed to build soft skills, leadership qualities, communication abilities and professional confidence among security personnel.
As we look ahead, the partnership between PSSA and IFPO is more than a collaboration, it’s a shared mission to uplift, inspire and professionalise the security workforce.
Together, we have opened doors to learning, recognition and growth for individuals who often work behind the scenes, yet play a vital role in our safety. These efforts have not just built skills, they have sparked confidence, pride and purpose across the industry.
This journey is defined not by what we have done, but by the lives transformed and the belief it has reignited in so many. And as this alliance continues to grow, one thing is clear: the future of the security profession is brighter, stronger and more respected than ever before.
pssa.global

Ali Laribi, CISSP, CPP, CISM, Founder & IT/ OT
Advisor, Fortress
Can you tell us about your journey in security.
My journey in the security field started with the IT network, operational and technical IT/OT cybersecurity from 2008 to 2013 after obtaining my MEng in Industrial computing in 2007. This was followed by a focus more on physical security between 2013 and 2018, where I obtained the CPP certification from ASIS in 2018. Recognising the growing importance of cybersecurity, I returned more towards cybersecurity and further deepened my knowledge by obtaining CISM certification in 2019 and CISSP certification in 2022 and multiple other certifications in IT and OT cybersecurity.
Currently, I am dedicated to promoting the convergence of cybersecurity and physical security, understanding that a holistic approach is essential for effective risk management in today’s complex security landscape.
What do you see as the biggest challenges in aligning physical security and cybersecurity governance in today’s organisations?
One of the biggest challenges is the siloed nature of physical and cybersecurity teams. They often operate independently, which can certainly lead to security gaps. What’s more, the rapid evolution of threats means that both teams have to constantly update their strategies, and often there is no unified strategy. Consistent communication and a unified governance framework are essential, but often difficult to achieve due to differing priorities and perspectives.
How do you ensure effective collaboration between physical and cybersecurity teams to address the threats?
The main objective of security convergence is not to merge two security departments into one, but to
develop a strategy that brings the two departments together to ensure that they are ready to work in a unified way to prevent and manage threats and provide the organisation with a complete and coherent vision of its overall security. This collaborative environment enables knowledge to be shared, resources to be optimised, risks to be reduced, responsiveness to threats to be improved and a holistic view of security to be guaranteed. The implementation of integrated security management systems can help bridge the gap between the two teams. A culture of shared responsibility and clear channels of communication are essential if risks are to be managed effectively.
What emerging trends in physical security and cybersecurity governance are reshaping the industry, particularly in the Middle East?
In the Middle East, several trends are reshaping the region’s security landscape. One important development is the proliferation of smart cities and other mega-projects in several sectors that rely on advanced physical and electronic security technologies and equipment that is connected and certainly exposed to cyber risks. In addition, IOT/IIOT devices are increasingly integrated into critical infrastructures, enabling improved monitoring and management, but also exposing them to vulnerabilities. Organisations are increasingly recognising the need for a unified approach to security that encompasses both physical and cyber security to effectively address these complexities
What advice would you give to organisations striving to build a robust and unified security governance framework?
Converging security functions and promoting communication, coordination

and collaboration requires an inclusive culture. By creating an approach tailored to its structure, priorities and level of capability, any organisation can pursue the convergence approach. You will find below three integrated phases to security convergence that can overcome those barriers (recommended by CISA US) and provide a flexible framework for developing a holistic security strategy that aligns security activities with business priorities and objectives:
• Communication: Effective security convergence begins with fostering open communication across teams. This involves forming a convergence team, clarifying leadership roles, and securing executive support. By enabling cross-functional information sharing, organisations can break silos and establish a foundation for collaboration.
• Coordination: In this phase, organisations formalise convergence efforts by defining roles, mapping critical assets vulnerable to cyberphysical threats and conducting vulnerability assessments. A gap analysis is used to identify discrepancies and prioritise areas requiring improvement, creating a structured approach to addressing risks.
• Collaboration: Collaboration focuses on implementing solutions and aligning strategies. The convergence team prioritises improvements, develops joint risk-reduction policies, and ensures all efforts align with business objectives. This phase embeds convergence into the organisation’s operations, fostering resilience and adaptability to emerging threats.


