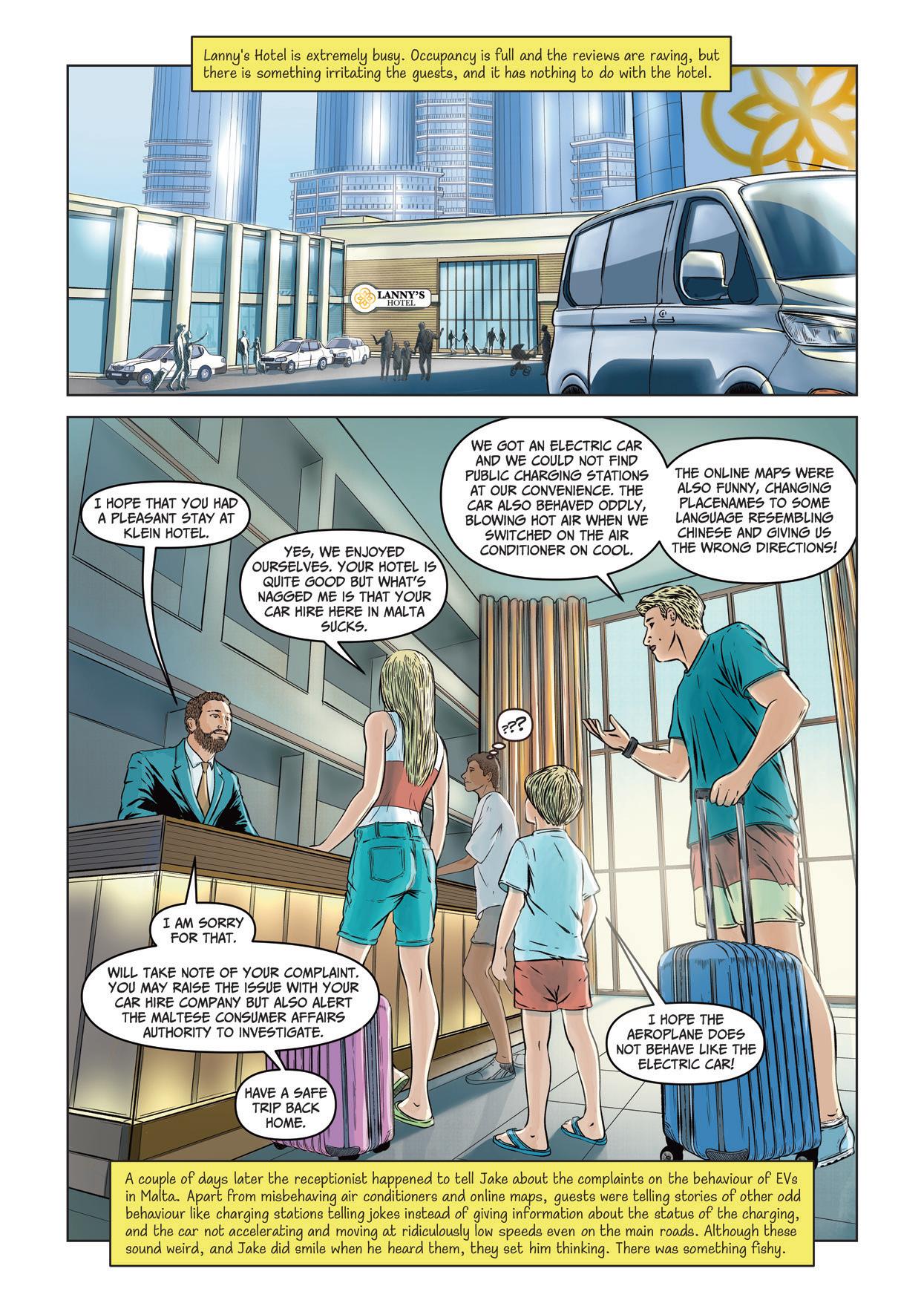
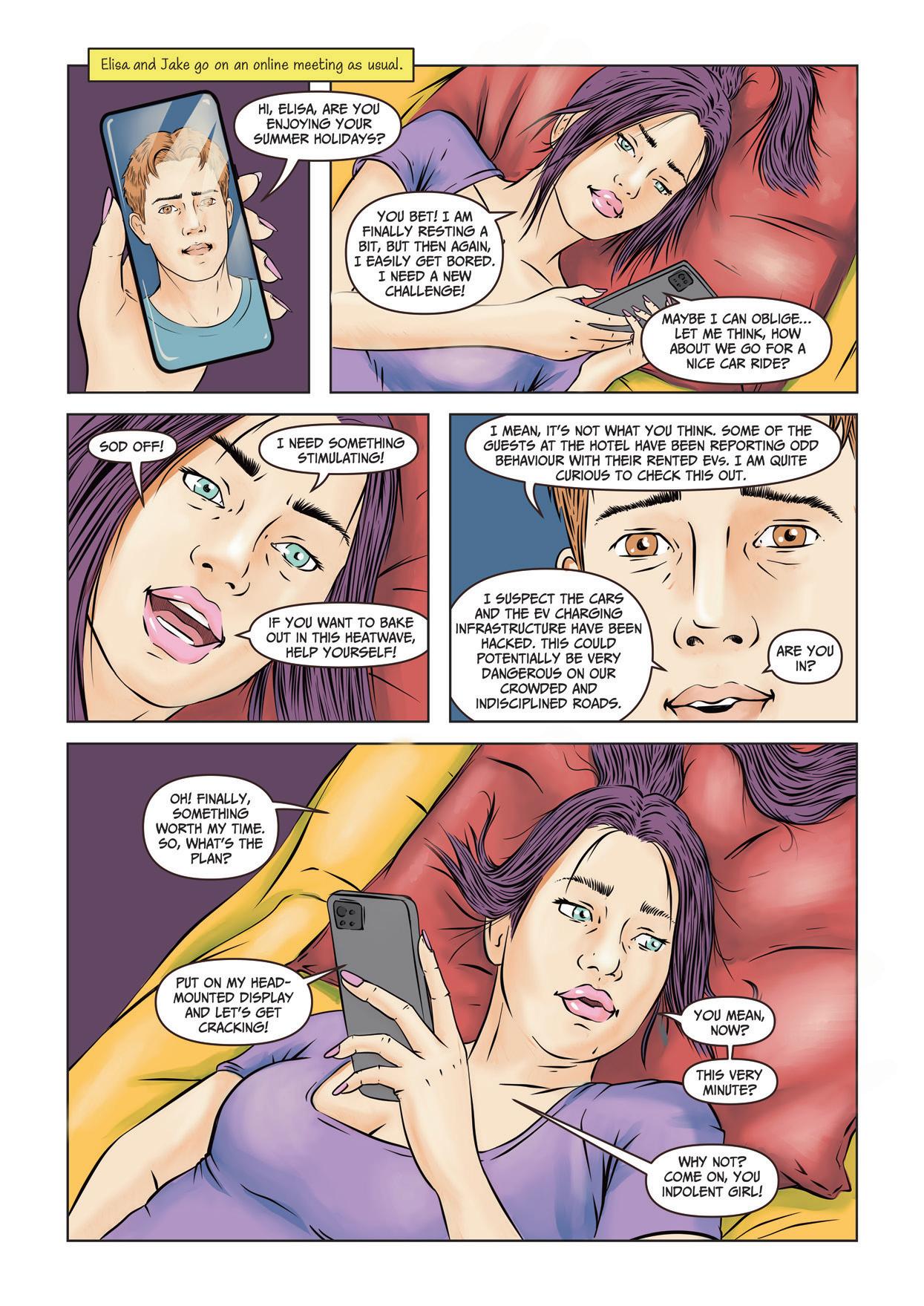
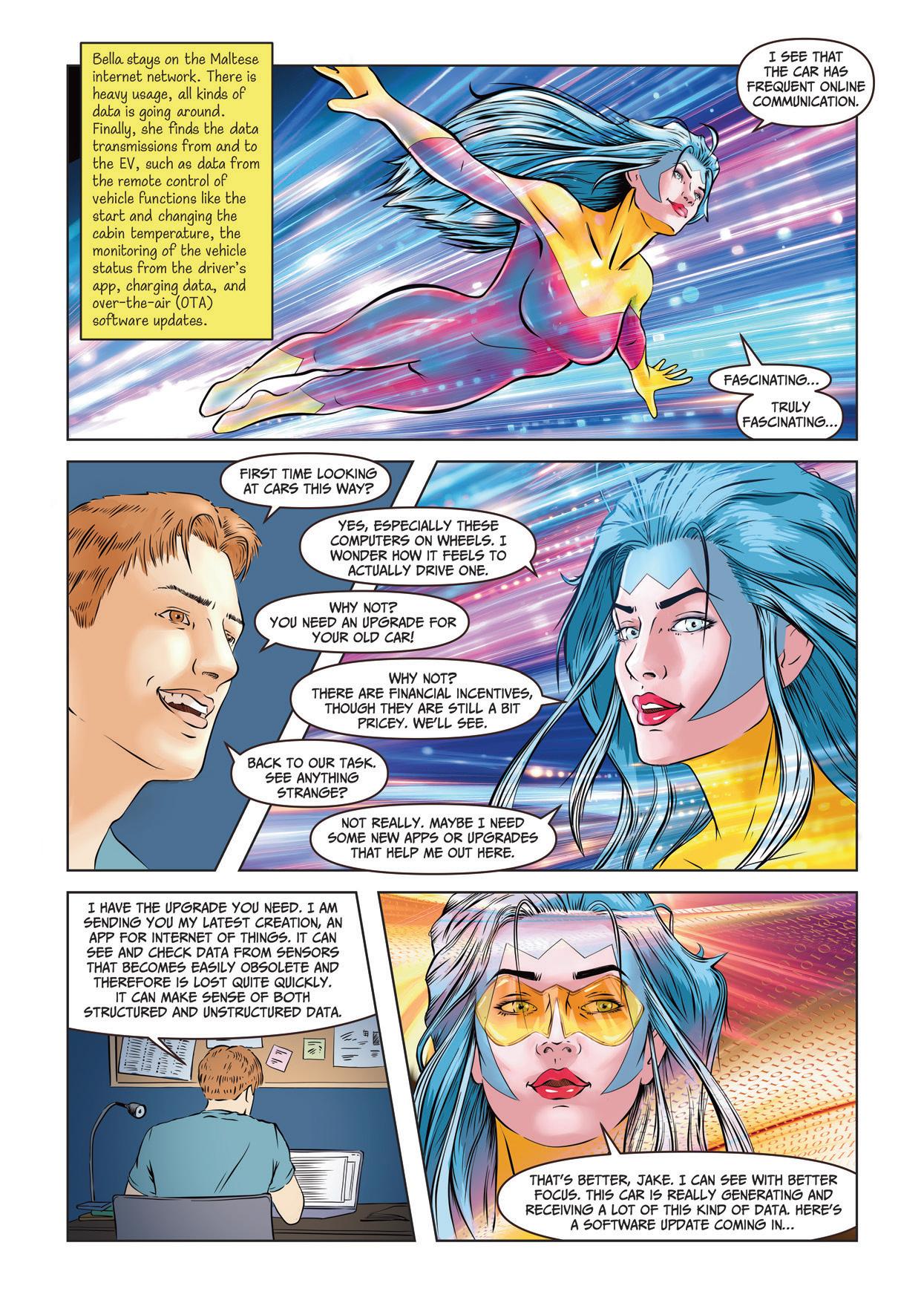
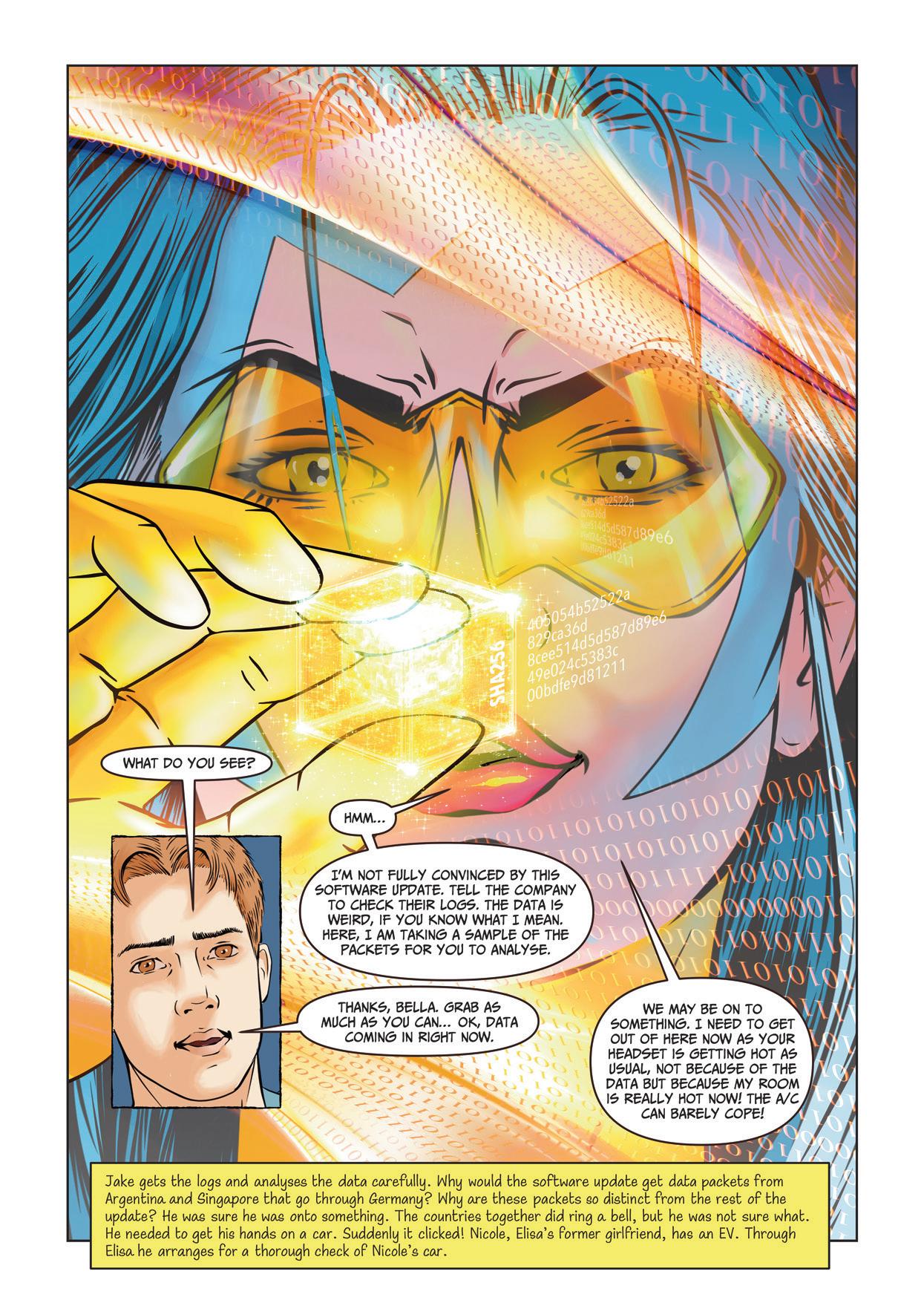
Episode 4 AN AMAZING LEAP FORWARD
Created by Robert Caruana (artist) and Martin G. Debattista (writer)
Editor Trevor Sammut
Proofreading Christopher Giordano
Publisher Malta Digital Innovation Authority (MDIA) in collaboration with Tech.mt
Printed in Malta (EU) Print It Ltd
ISBN printed 978-9918-0-1123-0
ISBN PDF (digital) 978-9918-0-1124-7
Copyright © 2025 Robert Caruana and Martin G. Debattista
All Rights Reserved
The story, all names, characters, and incidents portrayed in this production are fictitious. No identification with actual persons (living or deceased) is intended or should be inferred.
This publication is intended for an audience aged 11 years and older.
Particular attention has been given to ensure that all the content of this comic is correct and up to date as on date of issue. While every care has been taken during production, the publisher does not accept any liability for errors that may have occurred.
Contact Information
MDIA
Twenty20 Business Centre, Triq l-Intornjatur, Zone 3, Central Business District, Birkirkara, CBD 3050
Malta
Email: info@mdia.gov.mt
Telephone: +356 2182 8800
This publication is provided free of charge and is not for sale.
maltaverians.mt
The project of publishing a series of comics focused on digital innovation technology aims to emphasize the importance of expanding teens’ knowledge in this rapidly evolving field. These comics will be distributed among students studying Computing and IT to enhance their understanding of the latest technologies and potentially guide them towards their future careers. It will be available in a digital format online as well. By incorporating engaging visuals and storylines, the comics will pique the interest of young readers and promote a deeper comprehension of innovative technologies that are shaping our world. In addition, the inclusion of a glossary within the publications will further clarify technological terms and concepts, making the material more accessible and informative.
Intelligent, passionate, loyal
Jake + bright mind + small
responsible citizens, trusted computing devices
Phishers, hackers, spammers etc.
Tech whisperer – somehow inanimate technologies seem to understand what
Effortlessly produces software like
Created by Elisa Bonello to navigate through electronic data
Real Name: Unkown. Could never be verified
Alias: Professor Borgon Phase
Occupation: All we know is that he is a brilliant Maltese scientist
Special abilities: Controlling mastermind behind large-scale tech developments including the Phasecoin digital currency
Nobody knows much else about him.
GLOSSARY OF TECHNICAL TERMS
TERM DEFINITION
Artificial Intelligence (AI)
Automated Transportation Systems
Backdoor
DDOS (Distributed Denial of Service)
AI includes systems designed to perform tasks that typically require human intelligence, such as learning, problem-solving and decision-making. In the context of transportation, AI can optimize traffic flow, predict accidents and even power self-driving cars. Defining Artificial Intelligence (AI) is inherently challenging because the concept encompasses a broad, evolving range of technologies, capabilities, applications and philosophical definitions of ‘intelligence’ itself.
These systems involve vehicles that can operate independently, without constant human control. This includes self-driving cars, autonomous trucks and driverless public transport.
A backdoor is a secret way into a computer system that allows unauthorised access. It’s like a hidden entrance that bypasses normal security measures or is left ‘open’ to let in the ‘attacker’ who might have implanted the backdoor into a system.
A DDoS attack is a cyberattack where multiple devices (often controlled by hackers) overwhelm a target system with traffic, making it unavailable to legitimate users. For example, it can be a massive flood of data from co-ordinated sources that generate it with the aim to crash a website, rendering it unavailable.
Digital Footprint Your digital footprint is the trail of data you leave behind while using digital devices. This includes your browsing history, social media activity, online purchases and more.
Electric Vehicles (EVs)
Ecosystem
Internet of Things (IoT)
Man-in-the-Middle Attack
These are vehicles powered entirely or partially by electricity, using batteries or fuel cells instead of conventional internal combustion engines. EVs include fully electric cars, plug-in hybrids and some hydrogen fuel cell vehicles, offering reduced greenhouse gas emissions, lower operating costs and quieter operation compared to traditional vehicles.
In the context of EVs an ecosystem refers to the interconnected network of infrastructure and services that support EV adoption. This includes charging stations, government policies and the overall energy grid.
The IoT refers to a series of devices, typically embedded with sensors, software and other technologies that enable them to collect and exchange data via network. Devices of this kind can include smart home devices, modern home appliances, wearable tech and even connected cars.
This type of cyberattack involves an attacker intercepting communication between two parties and potentially altering or stealing information. It’s like someone eavesdropping on a conversation.
Malware Strain Malware is any type of malicious software designed to cause harm, directly or indirectly. A “strain” refers to a specific version or variant of malware with possibly unique characteristics and behaviours.
Road Transport Network
Rootkit
Self-Driving Cars
This refers to the interconnected system of roads, highways and other infrastructure used for road travel. It’s essentially the framework for road transportation within a region or country.
A rootkit is a type of malicious software designed to gain unauthorized access to a computer system while hiding its presence. It allows attackers to control the system, steal data or execute harmful actions without detection. Rootkits often exploit vulnerabilities to infiltrate systems and can be challenging to detect and remove, posing significant security risks.
Self-driving cars are vehicles equipped with sensors, cameras and AI that can operate autonomously, without human intervention.
SHA-256 SHA-256 Secure Hash Algorithm (256-bit) is a cryptographic hash function that converts input data into a fixed 256-bit (32-byte) hash value, regardless of the input size. It is widely used in data integrity verification, digital signatures and blockchain technologies due to its strong security and resistance to collisions or reverse engineering.
RIPEMD-160 is another example of a cryptographic hash function, that produces a 160bit fingerprint of data for integrity and security purposes.
Hash functions like RIPEMD-160 and SHA-256 are absolutely critical to today’s digital security. They underpin blockchain transactions, password storage, digital signatures, file integrity checks, and virtually every encryption system, making them one of the silent gatekeepers of trust in the online world.
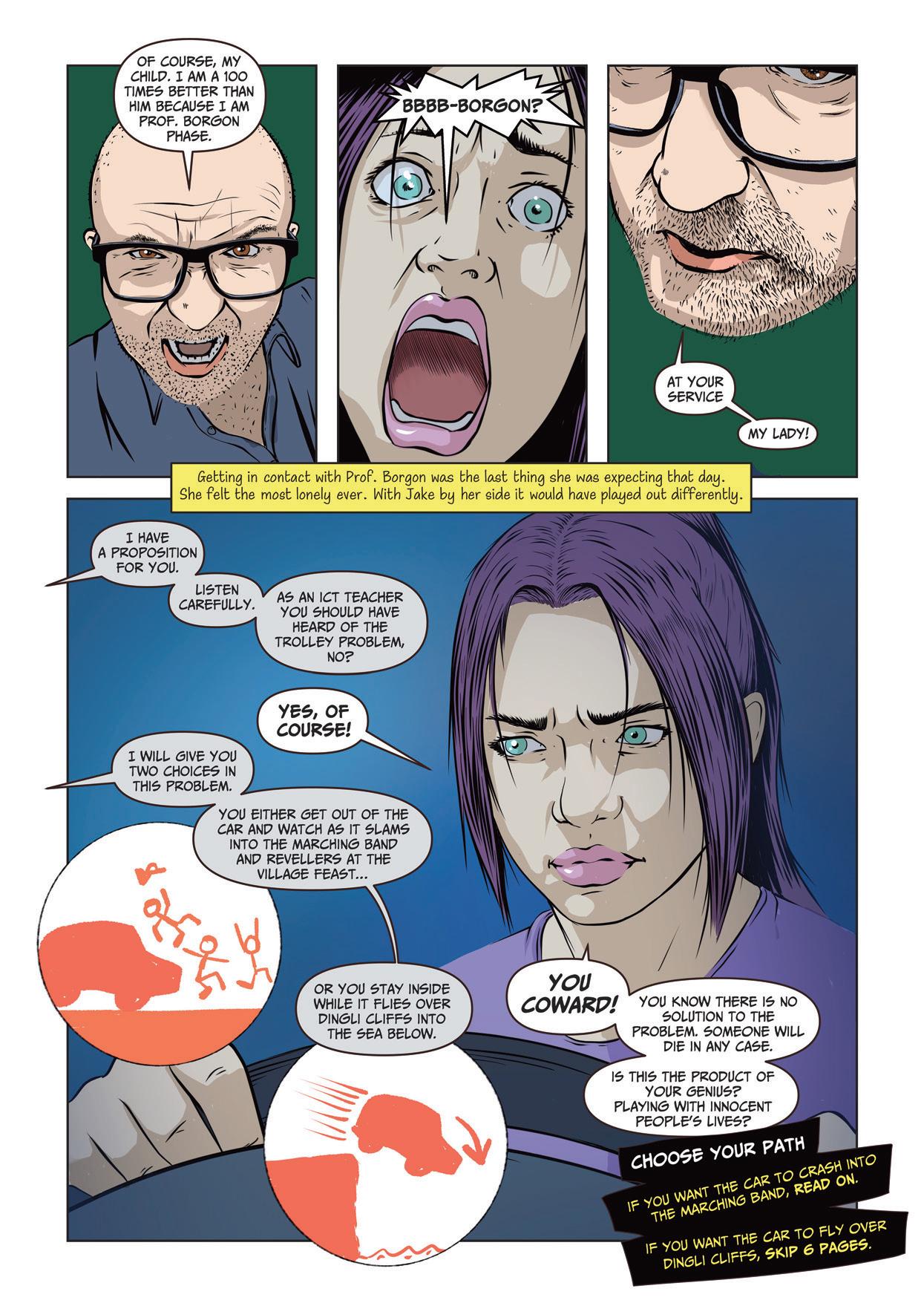
The Trolley Problem
Vehicle-to-Everything (V2X) Technologies
A philosophical thought experiment in ethics that presents a moral dilemma: should you divert a runaway trolley onto a track where it will kill one person to save several others on its current path? It explores the conflict between utilitarianism (maximizing overall good) and deontological ethics (adhering to rules or duties), highlighting the complexity of moral decision-making.
V2X technologies enable communication between vehicles and other entities on the road, such as other vehicles, infrastructure (traffic lights, road signs) and pedestrians. This can improve safety, traffic flow and overall efficiency.