
AFTER 41 YEARS OF PUBLISHING



AFTER 41 YEARS OF PUBLISHING

At exedee we put our energy and expertise into enabling your organisation to manage process automation and digitalisation with ease … and with >99% accuracy.
Recognise any of these common business problems? We can solve them for you!
Problem #1 Problems managing inbound documents – manual data entry & processing delays and issues
Problem #2 Accounts Payable / supplier invoice processing delays and approval issues
Problem #3 Issues and challenges turning paper documents into accurately scanned files
Problem #4 Digital filing - issues trying to find specific documents in a collection of scanned files
Problem #5 Issues managing and monitoring contracts
Problem #6 Issues centralising all customer information so that everyone can find and use it
Problem #7 Conflicting & duplicate data issues in your business information
Let us show you how our eSolutions work easily, effortlessly and exactly – to solve your business problems and streamline your records and information management processes.
EDITOR: Peta Sweeney
Information and Content Specialist
Email: editor.iq@rimpa.com.au
Post: Editor, iQ Magazine
1/43 Township Drive
Burleigh Waters Qld 4220
DESIGN: Amanda Hargreaves
Graphic Designer (Freelance)
Email: olecreativeagency@gmail.com
Stock images: Shutterstock
ADVERTISING
Peta Sweeney
peta.sweeney@rimpa.com.au
EDITORIAL COMMITTEE
Stephanie Ciempka (ACT)
Peta Sweeney (QLD)
Matt O’Mara (NZ)
David Pryde (NZ)
Philip Taylor (QLD)
Roger Buhlert (VIC)
CONTRIBUTIONS & EDITORIAL ENQUIRIES
Articles, reports, reviews, news releases, Letters to the Editor, and content suggestions are welcomed by the Editor, whose contact details are above.
COPYRIGHT & REPRODUCTION OF MATERIAL
Copyright in articles contained in iQ is vested in their authors. Most editorial material which appears in iQ may be reproduced in other publications with permission gained through iQ’s Editor.
ANNUAL SUBSCRIPTIONS
iQ DIGITAL ANNUAL SUBSCRIPTION
$49.50 incl GST ($) per annum for 2 issues RIMPA Global | Phone: 1800 242 611 International Phone: +61 7 32102171 To subscribe head to www.rimpa.com.au
iQ ONLINE ARCHIVE
Copies of articles published in iQ since 1984 are available at the Members Only section of the RIMPA Global website, in the iQ Article Archive. The Members Only section of the website can be accessed with RIMPA Global membership.
DISCLAIMERS
Acceptance of contributions and advertisements including inserts does not imply endorsement by RIMPA Global or the publishers. Unless otherwise stated, views and opinions expressed in iQ are those of individual contributors, and are not the views or opinions of the Editor or RIMPA.



BONITA KENNEDY LIFE ARIM, CERIM, CHAIR OF THE BOARD RIMPA GLOBAL

ANNE CORNISH LIFE MRIM CEO RIMPA GLOBAL
After thoughtful deliberation, the Board of RIMPA Global has made the decision to retire our long-standing industry journal, iQ. This decision was not made lightly. For many years, iQ has been a trusted companion to our profession—capturing milestones, sharing ideas, and showcasing the voices that have shaped the world of records and information management.
However, like the profession it served, our methods of engagement must evolve. Member feedback and engagement data have made it clear: the way our community consumes content is changing. You’ve told us you want insights that are more timely, accessible, and adaptable to your working lives. In response, we are embracing new formats that allow us to deliver expert insight and professional updates more frequently and in more interactive ways. In addition, producing iQ in its traditional format has become increasingly costly— both financially and environmentally. As a member-driven association, we have a responsibility to manage our resources wisely and to reduce our environmental footprint wherever possible. By transitioning away from print-based publishing, we are supporting a more sustainable future aligned with our values. From here, our focus will shift to a dynamic mix of digital content—including fortnightly newsletters, webinars, expertled blogs, and curated online experiences. These formats not only allow us to reach more members, more often, but also reflect the cost-effective, responsive, and inclusive model we need to sustain into the future. We know that iQ has held a special place in our members’ professional journey. To honour its legacy, we will archive past editions online, preserving the knowledge, creativity, and leadership that have filled its pages.
Looking ahead, we remain as committed as ever to supporting and elevating the profession. You can expect continued access to highquality content, thought leadership, and engagement opportunities— delivered in ways that are more agile, audience-focused, and future-ready. For our valued partners and advertisers, we’re also excited to offer a fresh suite of digital opportunities, including:
• Targeted placements in our highengagement email newsletters
• Sponsored thought leadership and content partnerships
• Webinars and panel event sponsorships
• Customised digital campaign solutions We understand that change can be
You can expect continued access to high-quality content, thought leadership, and engagement opportunities—delivered in ways that are more agile, audience-focused, and future-ready.
challenging, but we believe the time is right. As we close this chapter, we do so with immense gratitude and pride. Thank you—for reading, contributing, supporting, and believing in IQ. Your support has helped us inform, challenge, and inspire thousands of professionals over the years. We look forward to shaping the next phase of our professional community with you.
Bonita Kennedy Life ARIM, CERIM – Chair of the Board
Anne Cornish Life MRIM - CEO
As we prepare this final edition of IQ, I find myself reflecting on the remarkable journey this publication has taken—through decades of industry shifts, professional advancement and shared knowledge.
Since its first issue, iQ has stood as a trusted voice, a critical resource and a reflection of our profession’s depth, diversity and resilience. Over the years, we’ve explored emerging technologies, legislative change, strategic challenges and day-to-day practice. We’ve welcomed the voices of new professionals and honoured the wisdom of seasoned leaders. Our contributors, reviewers, readers and advertisers have formed a community built on shared purpose and mutual respect. To each of you: thank you. The decision to cease publication was not made lightly. Like many of you, we’ve seen the ways in which our profession is adapting—leaning into real-time communication, embracing digital platforms, seeking content that is more interactive, on-demand and diverse in form. This final edition is not the end of the conversation, but rather a transition to new ways of engaging with the ideas and issues that matter most.
Our contributors, reviewers, readers and advertisers have formed a community built on shared purpose and mutual respect. To each of you: thank you.
In this edition, you’ll find reflections on where we’ve been and where the profession is heading. We’ve gathered voices from long-time contributors and first-time authors and curated some of the most impactful pieces for you. It’s a celebration of both legacy and future. While this may be the final printed page, the work we do—as information and records professionals—continues to matter deeply. The need for strong, ethical and future-ready information leadership is greater than ever. Thank you for being part of this story. It’s been a privilege to share it with you.
Peta Sweeney Life FRIM, CXRIM – Editor























The Council of Australasian Archives and Records Authorities have recommitted to the aims of the International Council on Archives Tandanya-Adelaide Declaration on its fifth anniversary.
The Declaration calls on archives to ‘…re-imagine the meaning of archives, to embrace Indigenous world views and to decolonise archival principles with Indigenous knowledge methods’. To mark this occasion, CAARA has released a video titled "CAARA Members Recommit to the Aims of the Tandanya-Adelaide Declaration."
CAARA’s First Nations Special Interest Group established in 2020 includes representation from eight Australian states and territories, National Archives of Australia and Te Rua Mahara o te Kawanatanga, Archives New Zealand. CAARA organisations are unified in their support for First Nations peoples, providing resources and services to our First Nations peoples and communities across Australia and New Zealand.
We support the creation of ethical spaces of encounter, respect, negotiation and collaboration and we are committed to opening up our archives. CAARA First Nations Special Interest Group.
CAARA Australian jurisdictions are working on cross-jurisdictional support for the Healing Foundation’s Principles for nationally consistent approaches to accessing Stolen Generations records.
A guide for Victorian public offices is now available.
Managing Records in Microsoft 365: A guide for Victorian public offices was developed by Microsoft 365 (M365) expert Andrew Warland to assist Victorian Government agencies in the management of records created and captured across the M365 environment.
Whether your agency is implementing or currently managing an existing M365 environment, this guidance will be a useful resource in understanding the recordkeeping capabilities and limitations of M365. This guidance will also help records managers and others to start developing a good understanding of the M365 environment. From its admin centre structure, who should have which assigned roles and responsibilities, where records are captured and stored, to recordkeeping configurations, retention policy recommendations and information architecture approaches. It covers all areas of M365 that creates and manages records including, but not limited to, SharePoint, Exchange (for emails), Teams, Purview (for compliance activities) and Entra (for access arrangements and grouping). By utilising this guidance, agencies can work towards meeting their recordkeeping requirements and compliance with PROV’s PROS 19/05 Create Capture and Control Standard and other standards and specifications. You can find this guidance on our website, as well as a new Microsoft M365 topic page for further advice. Visit prov.vic.gov.au/about-us/ourblog/managing-records-m365


ACA Pacific is a leading distributor of Document Scanners, Capture Software and Information Management solutions, designed to fast track your path to Digital Transformation. As the distributor for Kodak Alaris Scanners and Software, ABBYY solutions, Contex & Colortrac Wide-Format Scanners and GetSignature eSign solution, we can digitise just about any size and type of document, making it easy to store, share and manage business ready information. Deliver powerful benefits and real-world value to any job function and organisation.
Locations: Melbourne, Sydney, Brisbane, Perth, Auckland Ph: 1300 761 199 | E: imagingsales@acapacific.com.au | W: acapacific.com.au

Collaborate with confidence. AvePoint provides the most advanced platform for SaaS and data management to optime SaaS operations and secure collaboration. More than 8 million cloud users rely on our full suite of solutions including records & information management to make them more productive, compliant and secure. Locations: Sydney, Melbourne Ph: 03 3535 3200 | E: au_sales@avepoint.com | W: avepoint.com
Compu-Stor is a family-owned Australian business specialising in information and records management solutions and services. From document, media & data storage to digital scanning, business process automation and consulting services, Compu-Stor provides a wide range of solutions using the latest technologies & methodologies to deliver secure & efficient services. Through its Digital Transformation Solutions, Compu-Stor helps maximise the accessibility of information within organisations. Compu-Stor works with its customers to provide costeffective solutions tailored to their needs. Locations: Across Australia Ph: 1300 559 778 |E: sales@compu-stor.com.au | W: compu-stor.com.au

We see ourselves as your strategic business partner, not just another supplier. As the cost of running your business continues to rise and your customer’s preferred source of communication becomes digital, we have developed innovative solutions to help you adapt efficiently and effectively, not only in today’s environment but for the future. We recognise it is no longer viable to be just ‘another supplier’. Our focus is to truly understand your business challenges and strategic direction so we can support you as a trusted business partner.
Ph: 0481 009 779 | E: john.cox.ez@fujifilm.com | W: www.fujifilm.com/fbdms

Grace ensures business information is managed as the high-value asset it is, throughout its lifecycle — Capture, Control, Storage, Access, and Secure Disposal. Established in 1911, Grace operates a national network of 28 branches across every capital city and major regional centre, each equipped to provide best-in-class secure physical records and specialist digital information management solutions. Partnering with Grace ensures information is expertly managed, whilst our digital specialists provide tailored transformation pathways to increase digital maturity. Locations: Across Australia Ph: 1800 057 567 | E: GIM-sales@grace.com.au | W: grace.com.au/information

iCognition is an Australian SME and the trusted advisor of choice to our clients for enterprise-wide information management and governance, consultancy and solutions implementation. We provide IMG services and software to government, not-forprofit, education and private sector enterprises across Australia and overseas. iCognition’s goal is to ensure enterprises maximise the value of their information, while minimising cost and risk. Locations: Canberra, Sydney, Adelaide and Brisbane Ph: 0434 364 517 | E: Nicholas.Fripp@icognition.com.au | W: icognition.com.au

CorpMem Business Solutions specialises in the MAGIQ Documents EDRMS and provides a wide range of services focused on improving your business by increasing the Return on Investment (ROI) made to deliver records management. InfoVantage is our flagship software designed to create a Records and Information Management Knowledge Platform that leverages off and integrates into whatever corporate EDRMS you have implemented. CorpMem converts their clients’ corporate memory into a knowledge asset. Location: Caloundra Ph: (07) 5438 0635 | E: hello@corpmem.com.au | W: corpmem.com.au
EzeScan is one of Australia’s most popular production capture applications and software of choice for many Records and Information Managers. Solutions range from centralised production records capture, highly automated forms and invoice processing to decentralised enterprise digitisation platforms which uniquely align business processes with digitisation standards, compliance and governance requirements. Contact: Demos Gougoulas, Director Sales & Marketing | 1300 393 722

Ignite has been assisting public and private sector organisations with talent services since 1984. We provide Specialist Recruitment (IT, Federal Government, Business Support & Engineering), On Demand (IT managed services) and Talent Solutions (RPO, Training, recruitment campaigns & talent management services). For four decades, we’ve been igniting the potential of people and have built a reputation as Australia’s trusted talent advisor. Locations: Sydney, Western Sydney, Canberra, Melbourne, Perth Ph: 02 9250 8000 | E: Catherine.hill@igniteco.com | W: igniteco.com


Information Proficiency is a Records and Information Management specialist providing a full range of services and software. We cover everything IM; from strategy to daily operational processing practitioners, full managed services, technical support and helpdesk, training, software development, data migration, system design and implementations. We work with many IM products including MS365, e-signature, workflow, scanning, reporting and analytics. We also develop a range of productivity tools and connectors. We work hard to understand your requirements and implement solutions to match. Services available in all states and territories. Locations: Perth, Western Australia Ph: 08 6230 2213 | E: info@infoproficiency.com.au | W: infoproficiency.com.au

Make your business process more efficient and exact! Are process inefficiencies and data inaccuracies weighing your team down and causing errors? Do you currently achieve a data extraction accuracy of over 99%? Are you under pressure to improve outcomes while reducing costs and processing time? Are you looking for an easy, effective, and proven solution? Get the exact business process automation eSolution for your needs, with a team of dedicated experts supporting you. Talk to the Exedee team today! Ph: 1800 144 325 (Melb) | W: www.exedee.com
At FYB our customer promise is to provide secure, easy to use, leading edge technological solutions, to enable organisations to harness the power of their information so they can provide excellent services to the community. We’ve stayed true to our core beliefs—to deliver the best information governance, systems and solutions to our customers.
Ph: 1800 392 392 | E: info@fyb.com.au | W: fyb.com.au


Iron Mountain Incorporated (NYSE: IRM), founded in 1951, is the global leader for storage and information management services. Trusted by more than 225,000 organisations around the world, and with a real estate network of more than 85 million square feet across more than 1,400 facilities in over 50 countries, Iron Mountain stores and protects billions of valued assets, including critical business information, highly sensitive data, and cultural and historical artefacts. Ph: 02 9582 0122 | E: anita.pete@ironmountain.com | W: ironmountain.com
iFerret is a turnkey enterprise search solution developed by iPLATINUM that works like "google" over your corporate data. iFerret enables you to find information quickly across your enterprise. Location: Sydney, Melbourne Ph: 02 8986 9454 | E: info@iplatinum.com.au | W: iplatinum.com.au

Leadership Through Data provide Microsoft 365 focused information and records management training that has been developed by information and records managers to Australian and New Zealand Records Standards. Our core offerings are designed to help Information and Records Managers make sense of Microsoft 365 so that strategy and policy can be developed with a true and accurate understanding of the platform’s capability. Our SharePoint Foundation offering helps with understanding the core of M365 before providing education in specific aspects – Records Management, Information Protection and Privacy Management, and Information Architecture. E: jacqueline@leadershipthroughdata.co.uk | W: leadershipthroughdata.co.uk


TIMG (The Information Management Group) has been in the Information Management business for more than 20 years. We are known as a company that solves Information Management problems and, as such, we remain committed to providing innovative, smart and cost-effective information management solutions for our clients. As the digital world rapidly evolves, we remain committed to helping clients accurately store, track, access, retrieve and cull data. Some of the services we offer include document conversion and digitisation (including scanning, printing and data capture), document storage and archiving solutions, sentencing, secure document destruction, Ph: (02) 9305 9596 | E: info@timg.com | W: timg.com

Objective Corporation - Powering digital transformation with trusted information. With a strong heritage in Enterprise Content Management, regulation and compliance, Objective extends governance capability throughout the modern workplace; across information, processes and collaborative workspaces with governance solutions that work with Objective ECM, Micro Focus Content Manager and Microsoft 365. Through a seamless user experience, people can access the information they need to make decisions or provide advice from wherever they choose to work. Locations: Australia: Sydney, Wollongong, Canberra, Brisbane, Melbourne, Adelaide, Perth; New Zealand: Wellington, Palmerston North Ph: 02 9955 2288 | E: enquiries@objective.com | W: objective.com.au

OpenText, The Information Company™, enables organisations to gain insight through market leading information management solutions, powered by OpenText Cloud Editions. OpenText is one of the world’s largest global software providers, delivering mission critical technology to empower 125,000 customers across 180 countries. We believe that companies of all sizes can be smarter by bringing information and automation together and delivering smarter outcomes by helping customers BUILD, AUTOMATE, CONNECT, SECURE, PREDICT and ACT. Ph: 02 9026 3400 | W: opentext.com
Since 1989, Professional Advantage has excelled as a top IT solutions provider and Microsoft Solutions Partner in Australia, specializing in modern work, cloud, security, financial management, and business intelligence for various sectors. As an exclusive iWorkplace/ Information Leadership Partner, we leverage Microsoft 365 for effective digital workspaces, information management, and data governance. Our skilled team, boasting a high NPS and long client relationships, operates across 7 offices in 3 countries, serving over 1000 clients globally. Ph: 1800 126 499 | E: enquiries@pa.com.au | W: www.pa.com.au
Founded in 2009, RecordPoint is a global leader in cloud-based information management and governance services. Our adaptable layer of intelligence offers complete insight and control over all in-place data, records, and content, enabling organisations to increase compliance and reduce costs. RecordPoint enables regulated companies and government agencies to reduce risk, achieve greater operational efficiency, and drive collaboration and innovation. Ph: 02 8006 9730 | E: salesapac@recordpoint.com | W: recordpoint.com

Votar Partner's number one priority is our clients. Working independently of all software and IT vendors, we offer our proven and specialised expertise to empower our clients to achieve their goals. Our subject matter experts can help you develop and implement practical initiatives across each stage of the information management lifecycle, ensuring that your records and information management practices support and enable business improvements, and remain relevant.
Ph: (03) 9895 9600 | E: votar@votar.com.au | W: votar.com.au


WyldLynx – We take your business personally. WyldLynx provides Information Management, Governance solutions and services using a unique blend of cutting-edge technology, real world experience and proven industry principles. This allows Organisations to manage their Information, Security, Privacy and Compliance across enterprise systems with reduced risk, complexity, and cost. WyldLynx has a reputation for delivering value through long term relationships built on trust, shared vision, and a continual investment in relevant innovation. Locations: Brisbane Ph: 1300 995 369 | E: contact@wyldlynx.com.au | W: wyldlynx.com.au
A market leader in Records and Information Management, ZircoDATA provides secure document storage and records lifecycle solutions from information governance and digital conversion through to storage, translation services and destruction. With world class Record Centres nationally, we deliver superior service and solutions that reduce risk and inefficiencies, securely protecting and managing our customers’ records and information 24 hours a day, every day of the year. Locations: HQ Braeside, Victoria Ph: 13 ZIRCO (13 94 72) | E: services@zircodata.com.au | W: zircodata.com.au


Records Solutions is an Australian-owned company, founded in 1994. Created BY Information Managers FOR Information Managers, our team provide records and information management solutions to the industry. As a software neutral vendor, our only concern when working with you is what is best for you. With a Quality Management System developed in accordance with AS/NZS ISO 9001:2016, we aim to assist you in achieving the best outcome for your project. Locations: Brisbane Ph: 1300 253 060 | E: admin@rs.net.au | W: rs.net.au



The Kenyan Archives and Records Management Association (KARMA), in collaboration with RIMPA Global, has officially launched its KARMA Talent Development Program (KDTP) - a two-year pilot initiative designed to build capability and foster leadership in Kenya’s records and information management sector.
The program connects ten early-career Kenyan professionals with ten experienced RIMPA mentors.
Running from February 2025 to November 2026, the initiative offers monthly mentoring, professional development, and project support, with the aim of strengthening local capacity and promoting international collaboration.
“This pilot program is a significant step in supporting the global growth of our profession,” said Anne Cornish, CEO of RIMPA Global.
“We’re proud to be working alongside KARMA to help shape the next generation of information leaders in Kenya.”
The program officially kicked off with the release of introductory videos, enabling mentees and mentors to connect and begin defining their goals and mentoring plans. With flexibility built in, the initiative caters to each participant’s development needs while providing structure and consistency.
RIMPA Global extends its sincere thanks to the following mentors:
- Adelle Ford ARIM
- Dr Bethany Sinclair-Giardini MRIM
- David Robinson
- Joy Siller Life ARIM
- Justin Coleman
- Leanne Dunne
“The KTDP is a dream realized for Kenya’s information management community—many thanks to RIMPA for your steadfast partnership in turning this vision into reality and for investing in the next generation of information leaders.””
- Meryl Bourke Life MRIM
- Nancy Taia Life MRIM
- Nicole Thorne-Vicatos MRIM
- Sandra Ennor ARIM

Let’s face it – information management has never been more important than it is today. As we all deal with tougher regulations and the endless flood of data, organisations desperately need skilled professionals who can make sense of it all.
That’s why we’re excited to announce our new Certification Program – designed to help you take your career to the next level.
RIMPA Global is proud to announce the launch of our comprehensive Certification Program—a milestone in our ongoing commitment to advancing the profession and supporting practitioners in their career development.
A New Benchmark of Professional Excellence
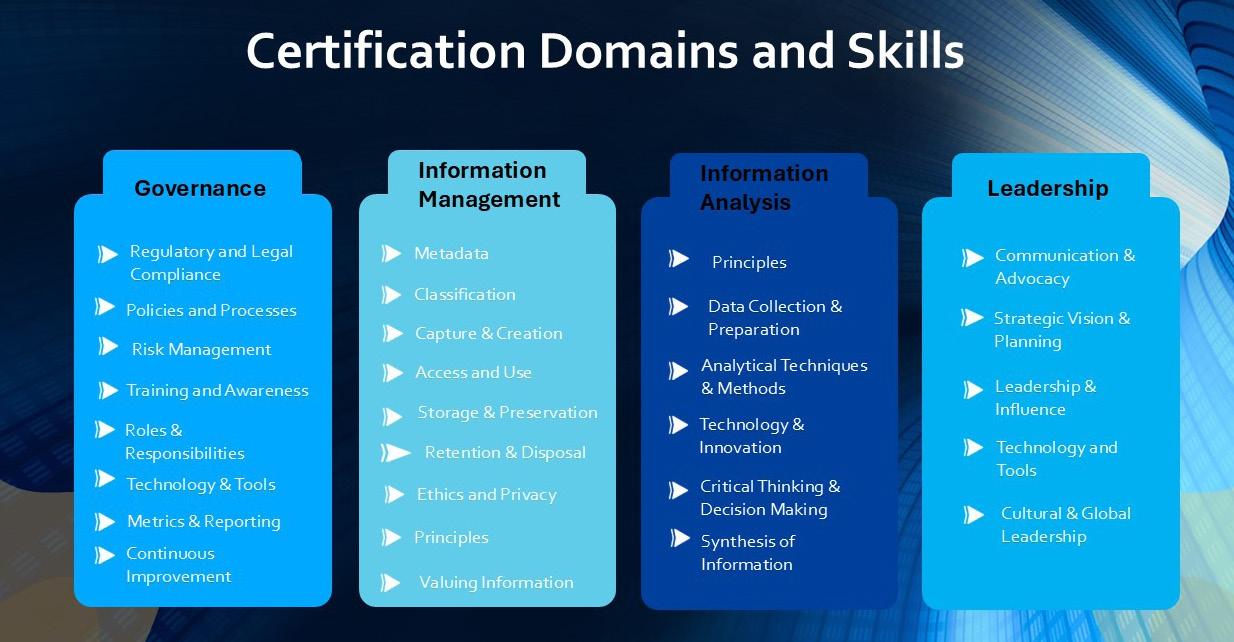
The RIMPA Global Certification Program was developed through extensive research and member consultation, this program establishes a clear framework for validating the capabilities of information management professionals across four key domains. See Figure 1: Domain Capabilities Framework.
This comprehensive framework doesn’t just acknowledge technical proficiency; it recognises the multifaceted nature of modern information management roles that increasingly demand business acumen, strategic thinking and leadership capabilities alongside traditional information handling skills.
Three Levels of Professional Excellence
We’ve created three certification tiers that recognise your growing skills and experience. Whether you’re newer to the field or a seasoned veteran, there’s a certification level that fits where you are in your career journey.
Experienced Level (CERIM)
This entry-level certification acknowledges practitioners who have demonstrated fundamental capabilities across all four domains. At this level, professionals can:
• Explain governance principles to internal customers
• Apply basic information management concepts and lifecycle knowledge
• Support analysis processes with fundamental techniques
• Develop foundational leadership skills in information management
Skilled Level (CSRIM)
The intermediate certification recognises practitioners with robust expertise and practical experience. These professionals demonstrate:
• Proficiency in implementing governance frameworks
• Strong ability to implement systems and manage information-related risks
• Skills in applying analysis techniques to solve real-world problems
• Capability to lead IM teams and align practices with organisational goals
The highest tier of certification distinguishes practitioners who demonstrate exceptional mastery. These professionals exhibit:
• Expertise in strategic governance leadership and policy development
• Advanced capabilities in strategic planning and driving IM innovations
• Leadership in information analysis methodology development
• Influence on organisational and industry-level IM strategies
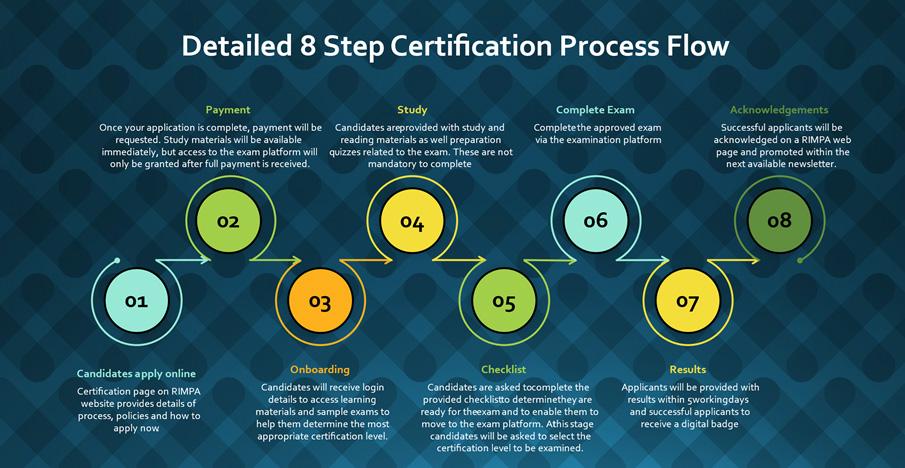
The Certification Process: Accessible and Rigorous RIMPA Global has partnered with Robinson Ryan, a respected assessment provider who also supports DAMA certifications, to deliver a certification process that is both accessible and maintains high standards of integrity. The certification journey follows these steps: The examination is structured to assess realworld application of knowledge rather than mere theoretical understanding. For the Experienced level, a 60% pass mark is required, while Skilled and Expert levels require 70% and 80% respectively, reflecting the increasing depth of capability expected at each tier. See Figure 2: Certification Journey.
We also recognise the accomplishments of our existing professional members and have established a straightforward transition pathway.
All current professional members (at 1 April 2025) can opt into the new certification program for just $25 (including GST), receiving a complimentary three-year certification aligned with their current membership status:
• Associate Members (ARIM) will transition to Experienced Certification (CERIM)
• Chartered Members (MRIM) will transition to Skilled Certification (CSRIM)
• Fellows (FRIM) will transition to Expert Certification (CXRIM)
This transition opportunity has been extended until the end of August 2025, providing enough time for current professional members to gain certification without undergoing the examination process.
Certification is valid for three years, after which renewal is a streamlined process involving a shorter 30-minute examination focused on current trends in the field. Practitioners seeking to upgrade to a higher certification level can do so at any time by paying the upgrade fee and completing the certification process for their desired level. The certification program encourages continuous professional development, ensuring that RIMPAcertified practitioners remain at the forefront of evolving information management practices and technologies.
In today’s competitive job market, having recognised credentials can make all the difference – both for you and your employer.
RIMPA Global has established a transparent fee structure that reflects the value of certification while remaining accessible to practitioners at all career stages. The fee structure varies based on certification level and RIMPA membership status, with special pricing available for practitioners in developing information management countries. While the investment required may vary, all practitioners can expect returns in terms of professional recognition, career opportunities, and personal development. For those looking to upgrade their certification level, upgrade fees apply, and if successful a further three-year certification period will commence.
Why bother getting certified? In today’s competitive job market, having recognised credentials can make all the difference – both for you and your employer.
• Verified Expertise: Certification provides independent validation of your skills and knowledge, differentiating you in a competitive job market.
• Career Advancement: Certified professionals often enjoy enhanced career opportunities and greater mobility across sectors.
• Professional Development: The certification process itself encourages continuous learning and skills enhancement.
• Industry Recognition: A digital badge and certificate demonstrate your commitment to professional excellence.
For Employers:
• Quality Assurance: Certification helps identify candidates with verified capabilities in critical information management functions.
• Risk Mitigation: Certified practitioners bring standardised knowledge of compliance requirements and best practices.
• Return on Investment: Organisations benefit from the improved performance and strategic thinking that certified professionals bring to information management challenges.
• Competitive Advantage: Teams with certified professionals are better positioned to leverage information as a strategic asset.
RIMPA’s next step is to actively promote the certification program to external stakeholders, particularly those involved in recruitment and workforce planning. Our goal is to clearly communicate that certification is a reliable indicator of capability, and we will be mapping certification levels to commonly advertised roles in the industry. This will allow employers to better match their job requirements with certified professionals.
Integrity and Accessibility at the Core
The RIMPA Global Certification Program has been designed with integrity and accessibility as guiding principles:
• Independent Assessment: Partnership with a third-party examination provider ensures objective evaluation of capabilities.
• Reasonable Accommodations: The program provides appropriate adjustments for practitioners with documented needs, ensuring equitable access to certification.
• Transparent Appeals Process: A clear process exists for addressing examination concerns or other certification issues.
• Ethical Framework: All certified practitioners commit to upholding RIMPA Global’s professional standards and code of conduct.
Make your expertise official and join a network of recognised professionals who are shaping the future of our industry.

The Journey to Certification: Years in the Making The development of this certification program represents the culmination of extensive work by dedicated RIMPA Global staff and members:
• In late 2022, a Status Upgrade Review Working Group was established to create more streamlined pathways for members seeking professional status.
• This group’s comprehensive report, submitted to the Board in May 2023, contained 21 recommendations informed by research and member feedback.
• The Status Implementation Working Group formed in August 2023 then worked diligently to implement these recommendations, focusing on creating a modern, transparent upgrade process and future-proof certification program.
• Between January and April 2025, RIMPA Global and Robinson Ryan collaborated to develop exam questions, create policies and rules, and establish the technical platform for the certification process.
• In February 2025, the RIMPA Global Board endorsed the revised status upgrade and certification model. This thorough, member-driven approach ensures that the certification program truly reflects the needs of the profession and establishes a meaningful standard of excellence.
Ready to take the plunge? We’re inviting all RIMPA members and information management pros to get on board with certification. It’s your chance to make your expertise official and join a network of recognised professionals who are shaping the future of our industry.
Whether you’re an experienced practitioner looking to formalise your expertise or newer to the field and seeking to establish your professional credentials, the RIMPA Global Certification Program offers a pathway to recognition that aligns with your career aspirations.
Congratulations to the professional members who took advantage of the transition period and secured their certification at the transitional rate. From 1 July 2025 all practitioners seeking certification will need to complete the full certification process, including examination.
For practitioners who aren’t yet RIMPA Global members, certification is available to you but it is an ideal time to join the RIMPA community to receive the discounted price and gaining access to not only the certification program but also the wealth of resources, networks, and professional development opportunities that RIMPA Global membership provides.
RIMPA Global will be sharing detailed information about the certification application process for new applicants and the pathway for upgrading certification levels. We will also be hosting information sessions to answer questions and guide practitioners through this exciting new program.
The RIMPA Global Certification Program marks a significant evolution in our profession’s journey. By establishing clear standards of professional excellence and providing a structured pathway for recognition, we are not just acknowledging the capabilities of today’s information management practitioners—we are helping shape the future of our profession.

BY MATT O’MARA FRIM, CXRIM
In October 2024, I had the incredible privilege of attending ARMA International’s InfoCon conference in Houston, Texas – all thanks to the generous RIMPA scholarship.
Valued at $8,000, this scholarship covers flights, accommodation, and full registration to one of the world’s premier conferences for information professionals. It’s an opportunity that I can honestly say has been a career highlight – and one that I’d encourage every RIMPA member to consider applying for.
If you’re even thinking about applying for the RIMPA scholarship, do it. The opportunity to attend InfoCon provides far more than just a ticket to a conference –it’s a platform to grow professionally, connect globally, and bring fresh insights home.
Held at the vast George R. Brown Convention Center, ARMA InfoCon 2024 drew over 900 attendees from across the globe. Houston – known as “Space City” and home to NASA’s Johnson Space Center – was a fascinating backdrop. Arriving to 31-degree heat from a cool New Plymouth spring was just the beginning of an experience packed with professional insight, thought leadership, and genuine connection.
One of the most surprising and fascinating aspects of Houston is its extensive underground tunnel system. Spanning over six miles (9.7km) and connecting 95 city blocks, this climate-controlled network lies approximately 20 feet (6 metres) beneath the bustling streets of downtown . It’s not only the largest collection of underground tunnels without a subway in the United States but also a vital part of the city’s infrastructure . Originally developed in the 1930s to link two movie theaters, the tunnel system has evolved into a subterranean cityscape . Today, it connects office towers, hotels, banks, corporate and government offices, restaurants, retail stores, and even the Houston Theater District . The tunnels house over 500 businesses, including numerous dining options and shops, serving thousands of downtown workers and visitors each day . Navigating the tunnel system is made easy with colorcoded maps and wayfinding tools throughout . Access points are primarily located within connected buildings, with only a couple offering direct street-level entry . The tunnels are typically open to the public on weekdays from 6:00 a.m. to 6:00 p.m., providing a convenient and comfortable way to traverse downtown Houston.
For visitors attending events like ARMA InfoCon, the tunnel system offers a unique and efficient means to explore the city, connect with fellow professionals, and experience the vibrant culture that thrives beneath Houston’s surface.
InfoCon’s speaker lineup was nothing short of outstanding. One standout was astronomer Dr. Phil Plait, who drew compelling parallels between space data and the future of information management. His talk was both intellectually exciting and deeply relevant to the data-driven world we work in.
John Montel, CIO at the U.S. Department of the Interior, reinforced the value of strategic thinking, executive engagement, and investing in education and training – particularly during digital transitions. Other sessions provided deep dives into Microsoft Purview, SharePoint, and Copilot, reflecting the sector’s growing emphasis on managing records in place using cloud-based tools. Information governance was a recurring theme, with practical insights into enhancing governance practices using emerging technologies – a hot topic across our industry.
Beyond the impressive sessions, the real power of InfoCon lies in the connections you make. Meeting peers from around the U.S. and the world – and discovering that many of our challenges are shared – was both validating and inspiring. The social events built into the program were just as valuable, offering casual opportunities to share experiences, ideas, and solutions. And yes, everything really is bigger in the States – from the convention center to the meals!

Winning the RIMPA scholarship didn’t just open the door to a world-class event; it opened my eyes to the global nature of our profession. Whether it’s the adoption of AI, transitioning from paper to digital, or navigating hybrid environments, the core challenges are often universal. Being at InfoCon allowed me to engage directly with thought leaders, discover new tools and methods, and return with actionable knowledge to benefit my own work – and, I hope, to share with the wider RIMPA community.
If you’re even thinking about applying for the RIMPA scholarship, do it. The opportunity to attend InfoCon provides far more than just a ticket to a conference – it’s a platform to grow professionally, connect globally, and bring fresh insights home. Attending InfoCon also offers RIMPA a valuable lens into how other associations operate, what’s coming next in our field, and how we can learn from international best practice. Finally, I want to extend a heartfelt thank you to RIMPA and the scholarship selection committee. Being chosen was a true honour – one I’ll never forget and an absolute career highlight.
BY DAVID ROBINSON AND STEPHEN CLARKE MRIM, CSRIM, RIMPA GLOBAL AMBASSADOR

Has Information Management improved over the last 40 years? Are the various decision makers in organisations making better decisions based on complete record sets in 2025 compared to 1985? These are the questions we’ve pondered over as a profession with traditional Information Management (IM) thinking and disciplines being diluted through deprofessionalisation of the industry, reduction in further educational qualifications and theoretical knowledge, with many experienced IM staff, with indepth knowledge of paper based and digital systems now steadily leaving the profession is it time to think differently on how we can help our organisations to improve decision making by providing more complete and accurate records through both new human and machine modes of practice.
While the digital age began earlier than the 1980’s it was still in its ‘toddler’ stage in the average office
setting in the 80’s. Paper based records and manual processes to manage them ruled the day. Large postal bags of mail, date stamping, handwritten inwards mail registers, library cards to manage file locations and photocopies of correspondence if more than one staff member needed to know about the correspondence that day was what was going on. Organisations who were at the cutting edge were converting archived records onto microfilm and had a mainframe computer to mark file locations by staff initials and were installing the facsimile machines (original electronic transmission) but didn’t have many places to send facsimiles to yet. Looking back at this time we would generally say that staff had a high level of awareness of their responsibility to retain a copy of outwards correspondence on the official file as well as making (handwritten) notes to record significant meetings or telephone conversations. Personal computers, mobile phones etc were expensive and limited in functionality and not really in the office yet. In conclusion,
the limited choice of medium to create and capture records into the official recordkeeping system did, in the majority of cases work and the decision makers in organisations made decisions based on complete sets of business records. The rise of personal computers and internet really saw the digital revolution explode from the 1990’s.
Most IM teams in 2025 are struggling daily to manage records what are received centrally. Outside of official systems records can be in any application with often scant regard for whether they fully integrated, or not, with centralised or ‘authorised’ corporate systems. Social media has been with us since the early 2000’s in a business context and still is mostly outside of these official systems. Specialist teams in ‘Digital or Data’ have formed and we’re hearing that traditionally IM teams are being merged into these new teams whose management may, at best have a token knowledge of records disposal, naming conventions,

business classification etc.
Technology remains at the forefront of the modern office. IT budgets are huge and ever expanding on the promise of delivering greater and greater efficiencies, yet it only drives contextual records further apart. We had the concept of ‘big data’ a few years ago which made all manner of claims, yet we now are told part of this could be redundant, obsolete trivial (ROT) data. Artificial Intelligence (AI) being the latest technology to emerge promising to remove repetitive, repeatable tasks from employees. We’ve also seen a sidelining of records management as we moved into the 2000s between information management and data governance, and perception that records management only applies to information, not data. A common phrase is a ‘Tradesperson is only as good as their tools’ however in a modern organisation its been the tools that have let employees to create and store records all over a modern workspace. Employees exit an organisation and either leave records in personal accounts, or worse delete everything. Central
recordkeeping resources are too thin on the ground to be able to meaningfully capture what is needed. It doesn’t help that organisations compound this issue with the cognitive dissonance of a ‘keep everything’, with the periodic ‘delete/overwrite everything’ approach, based on format, or system, regardless of the business value of the records.
Since the 1980s, the creation and capture of records has undergone significant conceptual evolution, yet professional practice has not consistently kept pace with theoretical development. Foundational models such as the records lifecycle and the records continuum have offered foundational frameworks for understanding the management of information from creation to eventual disposal or preservation. These models, however, are heavily predicated on the assumption that staff actively create records in a deliberate and structured manner, in the first place, and consistently
capture them into designated official systems. In practice, this assumption often proves flawed. The reality of everyday organisational behaviour shows us that many records of evidential or business value are either not being created at all, for example, critical decisions made informally and never documented beyond a whiteboard or, when they are created, are not captured in a manner that supports long-term findability or reuse, (e.g. thermal image printouts), or with inadequate naming conventions, minimal metadata, and/or poor contextualisation mean that even when records do enter formal systems, they remain difficult to retrieve and interpret. This disconnect between theory and practice highlights a fundamental challenge for the profession: without renewed emphasis on the conditions and behaviours underpinning record creation and capture, especially in increasingly decentralised and digital work environments, the value of even the most sophisticated theoretical models’ risk being undermined by poor implementation on the ground.
"Digital practice has blurred these boundaries, everyone with a PC became their own (usually untrained) de facto records manager."

In our workplaces we have witnessed the shift in practice, as the creation and capture of records has transformed from a paperbased paradigm, where records were a tangible physical artefact, to a complex, digital environment in which records are fluid, distributed, and often ephemeral. In the paper world, recordkeeping was a more deliberate and observable act; documents were physically filed, formally registered, and controlled within structured systems. Digital practice, however, has blurred these boundaries, everyone with a PC became their own (usually untrained) de facto records manager.
The act of record creation is now embedded within everyday business processes and applications, emails, chat messages, collaborative documents, and transactional systems, making the distinction between a high value and lowvalue records less visible and more difficult to manage without deliberate intervention. This shift has necessitated a re-examination of traditional recordkeeping concepts and has exposed the limitations of relying on staff to consciously and consistently create and capture records into official systems.

Over the latter half of the twentieth century Philip Coolidge Brooks’ original 1940s records lifecycle model[1] dominated records management practice and conceptualised recordkeeping as a linear sequence, from creation, active use, semi-active storage, to eventual archives or destruction. While appropriate in the context of physical records, this model proves increasingly inadequate in digital environments, where records are continually reused, revised, repurposed, and remain active across multiple business contexts and systems. In response, the records continuum model has emerged as a more dynamic and integrated conceptual framework. Various records management thinkers and authors arrived at the continuum solution, but Frank Upward’s model is generally considered to be the foundation of modern recordkeeping theory[2] The Continuum theory acknowledges that records can exist
simultaneously in multiple states, being both current and archival, both business and evidential, depending on their use and interpretation across time and space. However, this model too assumes that records are being consciously created and managed from the outset. The disconnect between theory and organisational reality remains a persistent challenge. Both the lifecycle and continuum approaches are built on the foundational premise that records will be captured at or near the point of creation into a designated, controlled environment. Staff frequently bypass formal systems due to perceived complexity, time pressures, or lack of awareness. Records are generated but left stranded on desktops, shared drives, or within transient communication tools. The practicalities of modern work environments, and reliance on decentralised digital collaboration, mean that records are often not consciously identified, let alone consistently managed.
Compounding this issue is the poor application of naming conventions and metadata standards. Even when staff do attempt to capture records, inadequate or inconsistent naming makes information retrieval difficult. Without structured metadata or contextual tagging, records become effectively invisible within repositories, undermining their long-term accessibility and usability. Information professionals frequently encounter systems bloated with poorly titled documents, lacking version control or contextual clarity, which significantly hampers enterprise search and discovery functions. This is further exacerbated by human error and misfiling, and a failure to capture file or store records at all, e.g. records sitting in individual email inboxes, or spread amongst several. In the digital era, where documentation can, and should, be seamlessly embedded into business processes, the failure to generate records at the point of transaction or decision represents a significant gap in governance maturity. Even when records are created, they are frequently not captured with adequate metadata, rendering them contextually opaque and
disconnected from the broader business information landscape. Metadata, whether system-generated or user-applied is essential to make records findable, relatable, and useful over time. Without it, the intrinsic value of a record is diminished, and its potential to support business, legal, and historical needs is compromised. This gap between record creation and meaningful capture highlights the urgent need to refocus professional practice from implementing a single technological platform towards automation, supported by behavioural and cultural change.
A renewed emphasis on embedding recordkeeping into business workflows, supported by automation, intuitive interfaces, and behavioural design, is critical.
Overall, the digital transition has challenged many of the assumptions that underpinned traditional records management. The profession must now move beyond outdated models and adapt its practices to fit real-world organisational behaviour. A renewed emphasis on embedding recordkeeping into business workflows, supported by automation, intuitive interfaces, and behavioural design, is critical. Recordkeeping must also be reframed not merely as compliance, but as an enabler of business performance, transparency, and knowledge continuity in a complex and evolving information landscape.
If you’re out at a social gathering and there are people you don’t know its inevitable that you’ll be asked ‘so, what do you do for work?’ and in response you have to go into details to explain what IM which usually results in a puzzled expression. Why is it that colleagues in other corporate functions such as Accounting, Communications or Human Resources are readily understood and not ours?
It maybe the time for IM to give up and better describe the value of our corporate function delivers. So next time you get that question say something like ‘I help my work make evidence- based decisions’ instead. Isn’t that the real reason why employees make and access records to check information and/ or use them to make business decisions? Ok, we may retrieve a nice report we created occasionally just to admire it but why don’t we just let go of describing what we do and just tell them what the outcome is ‘evidence-based decision making.’
Management apathy to support good recordkeeping existed in 1985 and is mostly still present today. While we like to think that we have their support, in truth its more real to start from the point that we don’t. Having worked through the rise of the digital age and the decline of paper as a records medium the explosion of data and digital tools has seen an ‘unchecked’ loss of central control and accessibility to most records. Employees still make business decisions whether they have full or limited access to records.
Looking back now from 2025 there seems to be a shortage of a key ingredient for a success, when implementing new technology platforms, in the lack of focus on the human element of addressing employee psychology. This is usually limited to training staff to use the new technology or providing educational IM initiatives. For example, employees arrive at the training session, delivered online and many just do their regular work while the Trainer delivers the material because the participants aren’t fully invested and engaged, which isn’t the Trainor’s fault. Its largely due to a poor workplace culture that believes records aren’t important. Organisational psychology, which is the study of human behaviour in business that focuses on applying psychology principles to improve workplace effectiveness and employee well-being[3] needs to be fully engaged to truly empower the workforce. Traditionally this is done from the top down in an organisation from Management, Human Resources or Change

Transformation teams however by also engaging this from the bottom up as well with psychology tools such as ‘job crafting’[4] an organisation can meet halfway to rapidly change workplace culture. Addressing this as a first priority to build a good recordkeeping workplace culture is a must. While technology plays its part, its still too heavily relied upon as the focal element at the expense of the people factor being organisational psychology.
Humans can change behaviour when fully engaged and motivated with belief in the outcome. Our parklands used to be practical useable with dog owners not picking up their pooch’s waste and people used to place all household waste into a single landfill bin. Enough people changed and believed in a better way and now environmental outcomes are vastly improved. Changing the workplace culture to ‘move the dial’ from a poor recordkeeping culture to good one is possible too. Psychology and specifically organisational psychology has the means to influence a good recordkeeping culture for most employee’s behaviour but it is more a marathon than a sprint. Job crafting is one proven method that can open employee thinking around self, task
Job
crafting is one
proven
method that can open employee thinking around self, task or relations to allow them to redesign their work to make it more meaningful to them and their team. This increases their satisfaction, commitment and enjoyment of their job. But it can’t just come from top-down thinking, so we need to engage lowerlevel employees and build up towards the top to make significant change. or relations to allow them to redesign their work to make it more meaningful to them and their team. This increases their satisfaction, commitment and enjoyment of their job. But it can’t just come from top-down thinking, so we need to engage lower-level employees and build up towards the top to make significant change.
While 1985 recordkeeping had limited technology by today’s standard with records mostly on paper and microfilm media and over a century of repeated work practice to ‘keep a copy’ now appear to be quite comprehensive compared to 2025. In 1985 though we were just told that it’s done this way and we mostly did it. The record creation ‘digital genie’ escaped the bottle in the 1990’s and is still loose today. So, the challenge now for us as a profession is do we still have the fight to take on the apathy towards us and present an improved applied model of recordkeeping to our organisation and individual employees? One that helps re-capture the ‘digital genie’ and return them to the bottle of comprehensive compliant recordkeeping?
So, in conclusion, over the past four decades, the evolution from paperbased to digital work environments has dramatically changed the nature of records creation and capture, yet Information Management practice has struggled to keep pace. While traditional models like the lifecycle and continuum provided structured approaches to managing information, they were built on assumptions that no longer hold true in decentralised, digital workplaces where records are inconsistently created, poorly contextualised,

"To build a sustainable IM culture, organisations must move beyond technical solutions and invest in workplace culture change, engaging staff at all levels."

and often never captured at all. Technology has enabled data proliferation but undermined recordkeeping coherence, with critical business decisions increasingly undocumented or lost in fragmented systems. This disconnect demands a fundamental shift, from systems-based IM thinking to human-centred, behavioural approaches that focus on the psychology of recordkeeping. To build a sustainable IM culture, organisations must move beyond technical solutions and invest in workplace culture change, engaging staff at all levels, embedding IM into workflows, and reframing recordkeeping not as a ‘tick-box’ exercise, but as a vital enabler of evidence-based decision making. Just as society changed its behaviours to improve environmental outcomes, so too can workplace behaviours shift, if the profession embraces organisational psychology as the key to revitalising modern recordkeeping practice.

Stephen Clarke MRIM, CSRIM, RIMPA Global Ambassador and J. Eddis Linton Award winner 2012, is an Information Management and AI Consultant. Stephen has had many senior roles in Information and Data Management, been a Chief Data Officer, and the Chief Archivist of Archives New Zealand, a career highlight of 20 years as senior NZ Public Sector. Stephen has been a strong advocate of standards for many years working with Standards Australia and NZ since 2007,and for ISO since 2010, and has co-developed standards such ISO 15489, ISO 13028, ISO 16175, and the ISO 30300 series.

REFERENCES
David Robinson - With more than 38 years of experience in the records / information management industry, David has worked in all levels of government to guide agencies to make the most out of their information assets. David is responsible for the redevelopment of the information management program at City of Greater Geelong and has led implementations of information management solutions at government agencies. With a passion for job crafting, storytelling and all things historical David is making it fun again to work in information management.
[1] Brooks, Philip Coolidge. “The Selection of Records for Preservation.” American Archivist 3, no. 4 (October 1940): 221–234.
[2] Upward, Frank, Sue McKemmish, and Barbara Reed. 2011. “Archivists and Changing Social and Information Spaces: A Continuum Approach to Recordkeeping and Archiving in Online Cultures”. Archivaria 72 (December), 197-237. https://archivaria.ca/ index.php/archivaria/article/view/13364
[3] ChatGPT
[4] Vol 40 – Issue 3 – November 2024 issue of iQ - The RIMPA Quarterly Magazine of the Records and Information Management Practitioners Alliance.

BY GUY HOLMES
In a somewhat startling projection, researchers and analysts are warning that by as early as 2026, the world may face a shortage of high-quality data to train artificial intelligence (AI) systems.
The engines of today’s AI, particularly large language models (LLMs) like ChatGPT, Claude, and Gemini depend on an evergrowing diet of text, images, audio, and video to become smarter, faster, and more capable. But this well is beginning to run dry.
This prediction is not a dystopian fantasy, it’s a wake-up call. As the data that has traditionally powered AI becomes exhausted, organisations must prepare for a new era where private, proprietary, and internal data becomes the fuel that drives AI innovation. And this transition offers significant opportunities for organisations ready to embrace it. Most of today’s large AI models are trained on publicly available data: websites, books, open-source code, forums, social media, news articles, and more. While vast, this corpus has limits. Much of the high-quality content has already been absorbed into existing models, and growing legal and ethical concerns are restricting further harvesting. At the same time, what’s left online tends to be either redundant or low in informational value. As a result, the utility of public data is diminishing, and the ability to continue scaling models using this approach is reaching its limit.
Yes, new data is always being created on the internet, but the models are now keeping pace with this creation. New photos on Instagram that are used to train AI image generation models took years to ingest and be integrated into the systems of today, but now these systems like ChatGPT are absorbing this data and information almost as fast as it is created. What the world does not realise is that prior to the cloud existing almost all data worth keeping was recorded onto backup tapes. The cloud is the fundamental bedrock that has allowed AI to grow at the rate it is now growing – as it provides the compute and storage that allows these massive models to scale and continue to grow. But prior to the cloud, the data created by corporates was largely written to offline technology meaning the AI models and cloud have never seen a large part of our world’s historical content. This challenge, however, presents a powerful new opportunity. Every organisation sits on a reservoir of internal data that has typically been used for record-keeping, compliance, or reporting. This includes everything from documents and spreadsheets to emails, call transcripts, PDFs, and images. Unlike public data, this internal information is deeply specific to the organisation.
It reflects its customers, its processes, its language, and its knowledge, making it incredibly valuable for the next phase of AI development. Using internal data to train or finetune AI models isn’t just a technical upgrade — it’s a strategic move. It enables the creation of custom applications that truly understand the nuances of your organisation. For example, a legal firm might create
Using internal data to train or fine-tune AI models isn’t just a technical upgrade — it’s a strategic move.
an AI tool capable of summarising case notes in its own format, while a manufacturing company could use historical data to forecast maintenance needs or optimise supply chains. Even something as straightforward as an internal chatbot trained on company policies can reduce the burden on HR and operations teams. But making this data usable for AI requires more than just uploading it to a model. Most enterprise data isn’t AI-ready. It’s scattered across silos, stored in outdated formats, or buried under layers of confidentiality.
The first step is understanding what data exists and where it lives. That means conducting an internal audit, identifying key information assets, and bringing structure to chaos. This might include scanning paper documents, extracting data from PDFs, consolidating emails, or tagging files with metadata to improve discoverability. Once this groundwork is done, security and governance take centre stage. Organisations must ensure that data privacy, legal compliance, and access controls are embedded into the AI development process. Sensitive data needs to be handled with care, especially where customer information, employee records, or financial details are involved. This is where good data governance practices, long championed by information managers, become vital enablers of innovation.
Organisations should also consider the long-term lifecycle of their information. Archiving strategies that have traditionally focused on regulatory retention can now be reimagined through the lens of usability. It’s no longer just about storing documents for years; it’s about structuring them in a way that AI systems can extract value over time. Metadata becomes a crucial asset, not just a tag. The ability to understand when, why, and how a document was created and in what context becomes essential to training AI that can reason, reference, and act.


With internal data cleaned, secured, and structured, organisations can begin to explore how to combine it with publicly available sources in a meaningful and safe way. This hybrid approach, when done right, yields powerful results. Public data can offer general context, definitions, industry benchmarks, and reference materials, while internal data delivers the specificity needed for precision. Together, they allow AI to respond intelligently and appropriately to queries that require both background knowledge and contextual awareness.
One effective technique for this is called Retrieval-Augmented Generation, or RAG. Instead of retraining a model from scratch, RAG allows AI to access relevant internal documents at the moment of a query. So when someone asks a question, the system finds the most applicable documents and uses them to inform its answer all without permanently absorbing sensitive data into the model. It’s secure, scalable, and effective. Some organisations may choose to fine-tune a model directly on their internal data. When taking this
approach, they should consider techniques such as masking sensitive fields or using synthetic data to avoid exposing confidential information. Whichever path is chosen, it’s important that the AI infrastructure is deployed in a way that meets data residency, privacy, and cybersecurity requirements. This could mean using private cloud environments, keeping the AI systems on-premises, or adopting zero-trust frameworks.
Adopting AI doesn’t mean replacing people, it really means amplifying the impact of the people.
Building these systems often involves a multidisciplinary effort. It requires collaboration between IT teams, records managers, legal counsel, and business stakeholders. The AI initiative should not be driven solely by technologists. It must be grounded in a deep understanding of the business goals, user needs, and regulatory context in which the data lives. It’s in this collaborative space that records professionals and
information managers play a vital role, ensuring that data quality and information integrity are upheld as AI development progresses. The rewards of leveraging internal data for AI are far-reaching. Decision-making becomes faster and more accurate as AI surfaces insights from across the organisation. Productivity improves as routine tasks like summarising documents to generating reports that can all be handled by machines. Customer experiences become more personalised and responsive, driven by an understanding of past interactions and behaviours. Perhaps most importantly, this shift transforms data from a passive archive into an active, strategic resource. Imagine your AI model knowing everything about your organisation form its inception, it is an incredibly powerful notion, and one that is now becoming reality. There are cultural benefits too. When employees see their knowledge and workflows reflected in AI tools, they become more engaged in the technology. Data quality improves, digital skills grow, and innovation becomes part of everyday work.
The organisation begins to develop what might be called an “AI-ready culture” — one that embraces change and continually looks for better ways to use information.
Adopting AI doesn’t mean replacing people, it really means amplifying the impact of the people. It allows skilled professionals to focus on critical thinking, creativity, and relationshipbuilding, while the AI handles the grunt work. For example, a policy analyst might use an AI tool to scan thousands of pages of regulatory text and surface relevant passages, freeing up time for interpretation and strategy. A customer service representative could access a dynamic knowledge base trained on previous cases to resolve inquiries more quickly and accurately.
• Enhanced decision-making
• Automation of repetitive tasks
• Increased employee satisfaction
• Competitive differentiation and barriers to entry
• Improved and personalised customer experiences
That said, the journey isn’t without its challenges. Integrating legacy systems, aligning stakeholders, and developing the right mix of skills can take time. There may be resistance from staff concerned about automation or overwhelmed by new tools. And while costs can be managed with the right planning, there will be an upfront investment in infrastructure, training, and data preparation.
Addressing these challenges requires thoughtful change management. Staff need to understand not just the technology, but the vision behind it. Communication, training, and transparency are essential. Leaders must demonstrate how AI will support people, not sideline them, and create opportunities for staff to participate in shaping how the technology is introduced. This collaborative approach builds trust and leads to better outcomes.
But for those willing to make the leap, the results speak for themselves.
Proprietary AI models grounded in internal knowledge are not only

more useful, they’re also harder for competitors to replicate. They give organisations a durable advantage in markets that are becoming more data-driven and automated every year. In time, these models could even become licensable assets themselves, opening up new revenue streams or partnership opportunities. For professionals in records and information management, this moment represents both a shift and an opportunity. The principles of good information governance — accuracy, integrity, accessibility, retention — are now central to AI success. The ability to classify data, ensure compliance, manage metadata, and track usage has never been more relevant. Information professionals are uniquely positioned to lead in this space, helping to bridge the gap between compliance, operations, and innovation.
As AI capabilities grow, so too will the demand for well-curated, explainable data. Regulators and customers alike will expect transparency and accountability from AI systems. This means that organisations will need clear documentation of how data was collected, processed, and used in model training or augmentation. Records professionals, with their long-standing expertise in documentation, auditability, and lifecycle management, are essential to meeting these expectations. In the past, data was something we kept “just in case.” It was a safeguard, a record, a box to tick. But the role
of data is changing. In the AI era, data becomes an engine — a source of power that fuels growth, insight, and transformation. And as the supply of usable public data begins to dwindle, internal information will become the most valuable asset many organisations have. Now is the time to prepare. Audit your data. Protect it. Organise it. Activate it. Because the future of AI won’t just be trained on the internet. It will be trained on you and your own personal and corporate data.

Guy Holmes is the Founder and CEO of Tape Ark, a company revolutionising legacy tape data access and migration. With a background in geophysics and decades in the oil and gas sector, Guy launched Tape Ark to modernise outdated, costly storage practices. A passionate advocate for Artificial Intelligence, he sees Tape Ark as a bridge between legacy data and AI-driven analytics. He shares insights on his podcast Tape Ark 3D: Deep Diving into Data. Guy holds degrees in Geophysics and Technology Management, and is a graduate of the Australian Institute of Company Directors. He has a proven track record in growing start-ups and turnaround ventures across tech and information management sectors.
BY IAN HICKS
Ian Hicks draws from his master’s in Archive and Records Management dissertation to explore what emotions users feel while handling original documents and how important these are to their experience and how these compare to looking at digital copies.
Acknowledgement: This article appears with permission of ARA (UK and Ireland) and the author. The article was first published in the ARC Magazine, No. 398 May-June 2024.


Our fundamental purpose as archivists (and archive conservators) is to preserve the documents (and in some cases objects) that record the history of our communities, preserving the original facts and information. We do this so people can call on this information now and in the future for a multitude of purposes and reasons.
The recent furore round the proposal by the Ministry of Justice to destroy original documents, in favour of a digital only approach, broached to a wider public the pros and cons of digitisation and why preserving originals is important from a technical ‘fail-safe’ perspective. Few of those putting forward consultations on the matter looked at the impact on users –particularly the loss of ‘wonder’ and emotional affect when literally holding history in their own hands. My research focusses specifically on this aspect of user experience – and who do we preserve archives for if not our users? The research for my masters was certainly not the first in the heritage sector where there have been several studies exploring user emotions. I found, however, that there had been little work on the role that emotions play when conducting historical research with original manuscripts, apart from a study conducted by Anastasia Varnalis-Weigle in 2016, ‘A Comparative Study of User Experience between Physical Objects and Their Digital Surrogates.’
For my research, I audio-recorded interviews of 50 visitors to the archives and local studies at the Wiltshire & Swindon History Centre (WSHC) while they handled original documents and viewed digital copies. The participants were asked to explore three documents - an eighteenth-century will from our probate collection. This collection has been digitised and is available on Ancestry.co.uk (we do not produce the originals anymore); this was chosen because wills are heavily favoured by genealogists – who account for a high proportion of our users, and also because the document is small and looks like it was handwritten by the testator and signed by him.
See Photograph A: The will of Edward Bodman, WSHC, MS P5/1725/3.

The second document is a rolled map, dated 1841, in which the participant had to unroll to view it. This gave them an element of exploring and discovery. Again, this document has been digitised and is available on a website called ‘Know Your Place: Wiltshire’ (we do not produce the originals anymore).
See Photograph B: 1841 Tithe Map of Hankerton, Wiltshire, WSHC, MS T/A Hankerton.
The third and final document was a letter from Elizabeth I. This document was chosen, because it was written and signed by a well-known historical figure, who the participants, it was hoped, could connect with. It was intended to provoke an emotional response, which the will or map could not provide – an emotional response being unlikely due to the non-family nature of the document. It also has two small wax seals with fabric embedded in the wax. This allowed the participant to engage with other intrinsic values of documents that digital copies could not otherwise provide.
See Photograph C: Queen Elizabeth I letter, undated, WSHC 1946/4/2K/1.
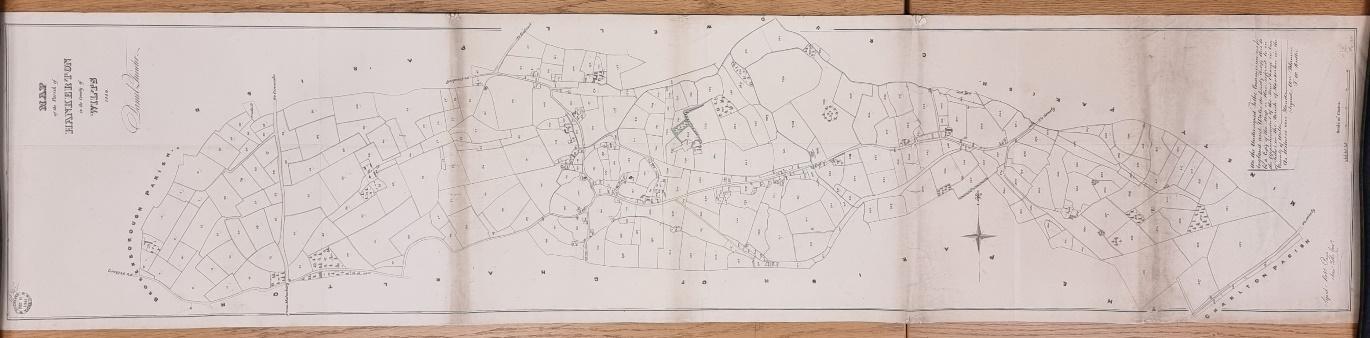




The letter has two small wax seals, with material interwoven into the wax. The material, probably silk, was originally used to seal the letter. It would have been tightly wrapped around the letter, with the seals pressed into the silk in two places to secure it. What we can see today is the frayed ends where the silk was cut. Participants took great interest in these and made numerous visual and tangible observational comments while handling the analogue.
While comparing the analogue to the digital copy, one noted that ‘I spent a bit more time looking at the seals, as they are 3D. You don’t really get anything from the screen.’ This observation is important to note when digitising collections since not all properties are transferable. These include texture, structure, scent, watermarks, weight, how the document was folded, method of binding and seals and their construction.
See Photograph D: Detail of the wax seal with interwoven material attached to the letter, WSHC, MS 1946/4/2K/1
NUMINOUS -WHAT IS IT AND WHY DOES IT MATTER?
Numinous is a word that has gained in popularity to describe a transcendent experience provoked by being in the presence of something ‘special’. Originally associated with religious experience it has been used by Catherine Cameron and John Gatewood, [Catherine Cameron and John Gatewood, ‘Seeking Numinous Experiences in the Unremembered Past’, Ethnography, Vol. 42, No. 1, (2003), pp. 57–71, p. 57] to describe visitor experiences while visiting historic sites, describing visitors who ‘Desire… to transcend the present and engage with the past in a highly personal way’. Having found no comparable study for this experience in archives I looked to fill the gap and use this term to describe this highly profound, subjective emotion.
I identified four emotional themes of numinous as:
• Wonderment: The profound feeling of importance, an emotion equal to surprise linked with curiosity and intellectual exploration. Wonderment, through curiosity, provides the motivation for questioning and wondering, ‘What if?’
• Through the experience of curiosity, visitors are more likely to make return visits to the archives to further their research.
• Fascination: The Oxford English Dictionary
describes fascination as ‘The state of being enthralled or intrigued by, or extremely interested in, something or someone.’ One participant was so captivated by the analogue letter that they had to be reminded to look at the digital, and remarked, ‘I felt some emotion. Very much so, to the extent that I didn’t even think until you had said that I had to look at the screen, I wouldn’t have. It’s quite amazing’.
• Empathy: in my study this was the least felt of all the numinous affects. Only three participants made remarks of an empathetic nature. Two, while handling the will; one noted, ‘A certain sadness when I picked it up. They’re obviously very poor’; and one while handling the map. This low comment rate expressed by participants could reflect the lack of emotional attachment that would occur if users had a strong family connection to the manuscripts. More research is needed in this area.
Spatiotemporal: Anastasia Varnalis-Weigle [Anastasia Varnalis-Weigle, (2016), ‘A Comparative Study of User Experience between Physical Objects and Their Digital Surrogates’, pp 4, 20, p4 [LINK https://elischolar.library. yale.edu/cgi/viewcontent.cgi?article=1019&context=jcas] describes spatiotemporal as ‘Transporting the user into a specific time or place in history’. A total of 15 participants’ remarks were identified as spatiotemporal themed.

One of the most profound of these was while handling the letter, in which the participant stated, ‘I got this thing, this feeling, oh my God, you know, Elizabeth I, when I was sat there looking at it, Elizabeth the 1st would have been sat here looking at exactly this and I also got a bit of a feeling of presence. A sense of history. Sense of it having been written by a great historical figure.’ Participants only remarked on these four numinous emotional themes while handling the analogue documents and not while viewing the digital copies.
Preserving the facts of history is also vital and many people using digital documentation will be happy to have their questions answered in that way – with no need for an emotional connection. In my research I found that 30 percent of participants preferred the digital copy, and 23 comments revealed no emotional narrative. These comments were pragmatic, unambiguous, unemotional and practical.
For this group of users, information-seeking was the core goal. These participants did not indicate they were looking for or wanted an emotional experience; their behaviour was based on finding what information could be gleaned from the digital copies.
One participant remarked, ‘Some people will say that it’s lovely to handle and all this, that, and the other. But from the point of view of getting the content information, the digital is perfectly acceptable.’



ABOUT THE AUTHOR
In my study 15 percent of participants preferred to use both digital and analogue sources. I termed this ‘holistic-seeking behaviour’. This suggested that for this group the emotional and informational experiences were equally important.
Whilst ‘inspiration’ wasn’t one of my ‘numinous’ themes, one participant, an artist, was visiting to look for art inspiration from the archives.
At the start of her interview, she asked if she could make notes about the documents on her sketch pad using her pencils. While she looked at the documents, she sketched little doodles – two of which are represented below (see Figure 1).
“I feel it’s important to see and to be able to handle the originals. But that maybe digital has a place alongside that because maybe it prevents overhandling of the originals.”
Her note-making style was in the form of drawing different parts of the documents. She summed up her experience by saying, “For me, as an artist, I’m interested in the physicality of the object, handling the original. I could miss something with the digital.”
Digitisation has many advantages, for instance, greater access by placing digital images on the internet. It also helps to preserve original documents and objects by limiting handling, in our case at the WSHC we do not produce from the probate and tithe map collections, although these are two large and heavily used collections This has drastically reduced the wear and tear on the documents.
Several participants remarked about preservation; one said, “I feel it’s important to see and to be able to handle the originals. But that maybe digital has a place alongside that because maybe it prevents overhandling of the originals.”; and “I appreciate that some of the things should not be brought out. If you’ve got a good [digital] picture, there’s no need to have it out.” Nevertheless, this research has discovered that some ‘object-ness’ qualities do not transfer to the digital environment. These include the finer details of documents, such as seals, and the emotional experience that some users seek when doing their historical research.
When considering the need to preserve originals, we should factor in the experience of our users, as well as the technical considerations that go alongside the digitisation debate.

BY ANDREA MCINTOSH
The pace of change, the demands of the end users, the complexity of business processes, and the introduction of technological innovations are challenging the ability to integrate records management requirements into organisational needs.
It is likely that many readers will agree with this assessment.
My background in information technology and systems development has provided valuable experience for today’s workplace information management environment. Additionally, working on projects with dedicated business analysts has helped me develop skills in this area on top of formal training. Over time, this skill set has contributed to successful records management outcomes and the enhancement of the records and information management brand within organisations.
Information management is gaining attention from C-suite leaders, driven by factors such as the exponential growth in data, associated risks, and business drivers for information automation and artificial intelligence use. This increased attention necessitates a more strategic approach in defining records management requirements, aligning them with business strategies, collaborating with stakeholders, and managing their needs to support both business objectives and compliance requirements.
In a world where projects compete for prioritisation with limited capacity and resources, business analysis techniques facilitate a stronger presence during prioritisation decisions. Using business analysis tools can effectively represent information management needs and help ensure successful project delivery.
BUSINESS ANALYSIS PLAYS A PIVOTAL ROLE IN BRIDGING THE GAP BETWEEN IM, IT AND THE ORGANISATIONAL STRATEGIES.
Not all organisations have a dedicated Business Analyst, so information management professionals must develop business analysis skills to effectively contribute to projects.
This article will guide you through a phased approach to business analysis using three well-known techniques. These techniques represent a subset of the six fundamental knowledge areas essential for effective business analysis.


They are frequently employed across projects of diverse scales. These activities are interrelated and generally follow the specific sequence outlined in Figure 1. Business analysis is an important aspect of successfully implementing change within an organisation. It facilitates change by supporting information management, ensuring that initiatives comply with compliance strategies and lifecycle management requirements. Additionally, it aims to deliver value to stakeholders and align with the broader strategies of the organisation (see Figure 2).
A stakeholder is anyone whose support is essential for the organisation’s existence. In information management, this refers to those who create, consume, or rely on data, information, and records to achieve organisational goals. Stakeholder analysis identifies project stakeholders, their concerns, business processes, and how the project will affect them. At a project’s start, thorough stakeholder analysis, we can outline key needs, ensure understanding of expectations, and maintain good communication. We also take a risk lens with our stakeholders looking at the impact they can have on the achievement of our project goals and desired outcomes.
The ultimate output of stakeholder analysis is to engage and satisfy them in a way that supports the project and contributes positively to the project success. This output also has the knock-on effect of building strong relationships which in turn influence future opportunities. There are several steps in the stakeholder analysis we undertake.
In this step we are recognising and listing all individuals and groups that can significantly impact or be affected by the project. We need to consider both internal and external stakeholders. What we need to be mindful of is this list of stakeholders can become dynamic over the life of the project and as such will require ongoing management and updates. In an information management initiative as an example the stakeholder list may change based on the area of the organisation or the business process being affected during different phases of the project. There are a number of different methods we can employ for this step including:
• Brainstorming sessions: Project team members generate a list of stakeholders based on their knowledge and expertise.
• Document review: Reviewing existing documentation such as organisation charts, business process documentation or previous project records.
• Surveys and interviews: Seeking input from individuals to capture perspectives and at times uncover stakeholders we may not have previously considered.
Assessment of stakeholder interest
In this step we are ensuring the project goal and outcomes has good alignment with the interest and diverse needs of our stakeholders. It is in this step that we gain insight into the expectations they hold and the values and goals they each bring into the project.
Information management is gaining attention from C-suite leaders, driven by factors such as the exponential growth in data, associated risks, and business drivers for information automation and artificial intelligence use.
By understanding this we can tailor our communication and project approach which in turn contributes to overall project success.
There are a number of components for assessment here:
• Identify stakeholder’s goals: One of the greatest outcomes in understanding our stakeholder’s goals is that it builds trust and fosters collaboration through goal alignment.
• Analyse concerns and priorities: By taking time to analyse concerns and priorities we can ensure we a conscious of these in the planning and they can be proactively managed.
• Assessment of attitudes toward the project: Attitudes including enthusiasm and scepticism can have a big impact on engagement; by understanding this we are able to focus the attention where it is required.
• Determination or communication preferences: It is critical for communication success that we meet the communication preference of both individuals and groups in our stakeholder mix. If the preference is group meetings over email updates, we need to plan and adapt for this.
• Consideration of any cultural considerations: There may be cultural considerations that could impact perspectives and engagement. Understanding these assists in delivering the project in a way that is sensitive any cultural needs.
The methods employed in identifying stakeholders can be repeated here and we can also use additional methods such as focus groups and a review of previous interactions.
Another critical aspect of assessing stakeholder interest, particularly in a project of long duration, is a mechanism for feedback. This will encourage our stakeholders to express thoughts and raise concerns.
Evaluation of stakeholder influence
In this step we map the level of impact and influence the stakeholders have over the project and assists in the decision-making process.
It allows us to prioritise efforts and resources and gives us a good understanding of the management of our stakeholders.
What we are considering in this step is:
• Decision making authority
• Control over resources
• Expertise and knowledge
• Alliances and relationships
• Past influence
Prioritisation of stakeholders
The steps above give us the information we need to rank or categorise our stakeholders based on the level of importance and influence as well as potential impact on the project or project decisions.
All stakeholders are not created equal, and we need to be mindful of this in the approach to them throughout the project in terms of attention, communication, risk and effort.
A trusted method for mapping stakeholders is the power/ interest matrix. This simple tool helps us plot our stakeholders against the power and influence
they have over the project and allows us to proactively focus prioritisation and manage engagement with them. This grid is represented in Figure 3. Let’s take a real-world example. In an information management project that moves information and records out of a dedicated EDRMS and into a SharePoint environment and consider the following stakeholders:
• Project sponsor – High Power and High Interest, this is typically the most powerful stakeholder and decision maker and managing them closely is critical to project success
• Organisational customer – Low Power and Low Interest, these stakeholders typically are not impacted directly by the project however they will require monitoring particularly if the way they access information changes.
• Senior Leadership – High Power and Low Interest, they certainly hold the power to change the direction and provide funding and resources for the project but would be less interested in being deeply involved in the project
Now that we understand who our stakeholders are we can move forward to gathering the

requirements for our project.
Requirements gathering is a crucial step in ensuring our project delivery moves us from the current state to the future state with all requirements met. In some cases it also informs and documents where we cannot meet requirements and the decisions surrounding the balance of meeting these versus the risk of not meeting them, this is important in information management projects from a compliance or standards perspective and in my experience has allowed me the support to let things go knowing I had my issues heard, documented and escalated prior to the end decision.
There are four general classifications of requirements we need to consider:
• Business requirements: Statements of goals objectives and outcomes for the project or the change that has been initiated
• Stakeholder requirements: This covers the needs of the stakeholders that must be met for their business requirements.
• Solution requirements: There are two types of solution requirements covered in this area functional (what the solution should do) and non-functional (how the solution should perform). Solution requirements cover the technical capabilities and features. A key point here is that we are not designing the full solution or getting into deep technical areas.
• Transition requirements: These are the requirements that are often overlooked in projects yet are critical in bridging the gap between current and future state ensuring the solution is successfully adopted, training and skills assessment are aspects of this class of requirements. Often requirements gathered during this process are used for the procurement process as a measurement of a solutions ability to meet the requirements and therefore become a decision framework for vendor or partner selection.
There are two key skills deployed when working with stakeholders when discussing requirements
and using these is important to ensure the solution success is balanced with effort.
Challenging “because we always have” thinking.
We need to encourage critical thinking and where possible back it up with data and insights to demonstrate the need for change. Often training our stakeholders on the potential solution can shift perspectives, this may also include highlighting success stories from similar organisations who have deployed the solution.
Leading from the top with a culture of continuous improvement is important here too, as is making space for open discussion where stakeholders are all encouraged to share ideas and explore alternatives.
One method often used here is the MoSCoW method where we categorise requirements into:
• Must have: Essential requirements critical for business process, compliance and project success. Without these being met the project will fail or introduce unmanageable risk.
• Should have: Important, but not critical. They add value to the business process and should be included if possible.
• Could have: These are desirable requirements and are nice to include if resources, budget and other project constraints allow.
• Won’t have: The least critical requirements sit here and are often excluded in the final delivery. They may be considered for future phases of work.
Process modelling is often done in tandem with requirements gathering as part of the current state and desired future state decisions.
It provides a visual representation of the organisational business processes and assists in the understanding of these, particularly for project team members where the business process is not part of their normal business as usual work.
One of the outputs from the business modelling process is the identification of areas for

"All stakeholders are not created equal, and we need to be mindful of this in the approach to them throughout the project in terms of attention, communication, risk and effort."
"...the skills of a business analyst are indispensable in modern records management programmes."

improvement with the solution the project delivers in mind. An example of this in an M365 solution could be the deployment of an approval process using out of the box SharePoint tools. When it comes to process modelling we can achieve the following:
• Clarify the sequence of activities in the process
• Identification of where information is generated and consumed
• Identification of participants in the business process
• Clearly identify trigger events
• Map crossover between business processes (this is critical for ensuring the requirements of both process are not weighted in isolation)
• Documents the result of the business process
There are several different ways to document the business process from a simple flow diagram through to a full process model using the Business Process Model and Notation (BPMN) standard. How you document your model will depend on the complexity of the project and also will need to consider the stakeholder requirements.
If you are in an organisation that does not have a high level of business process modelling already, it is an opportunity for you to add value to the organisation by undertaking this as part of your work in information management initiatives.
What is common between all forms of business process modelling is these key elements:
• Activity: The individual step that forms part of the business process.
• Event: What initiates the activity sequence it could be as simple as an email received.
• Directional Flow: This is the path that indicates the logical sequence of the workflow.
• Decision Point: This is the point in the process that the direction splits into two or more directions. Often this is represented by a YES or NO marker.
• Link: This is where we show connections to other business processes, in some cases an activity at a high level may include a link to where that activity is decomposed into a sub-process.
• Role: This is the person, or the group of people involved in the process. In a process model we always refer this to the organisational role rather than an actual name.
If you would like to read more about Business Process Modelling and Notation follow the link below.
https://www.omg.org/spec/BPMN
In conclusion, the skills of a business analyst are indispensable in modern records management programmes. What I have discussed here is just a small touch on three skills which have provided great success in my career to date and really enhanced the buy in to the initiatives I presented over the years to build maturity and improve the way we manage the function and deliverables.
I look forward to seeing you at RIMPA 25 where you can learn more about the Leadership Through Data EMPOWER framework which contains many more opportunities to build leadership skills.

Andrea is Principal Consultant at Leadership Through Data. What sets her apart is the ability to create an atmosphere where learning and project delivery becomes a joyous journey. Interactions with Andrea are highly rated and she brings a unique blend of expertise, humour, and genuine care to every interaction including what you will be presented with today. Andrea has a rich history of professional experience in both government administration and the private sector in a mix of technical development and leadership. She has led and been a key project team member in several large project deliveries and this experience is something she is always willing to share empowering individuals and organisations to achieve their full potential along the way.

BY SHARON IPSEN

In school, there’s a myth many of us are taught; that success is a ladder, a straightforward climb you can only make one way, with no detours. Life, as most people find out, is quite different. You can find yourself going in all sorts of directions, or even making a jump on to an entirely new ladder from the one you started on.
That’s exactly what I did when I made the leap from records and information management to cyber security. In this article, I’ll share a bit about my story, many different career opportunities in cyber security for IM and other professionals, and how you can position yourself to get a start in the field.
MY CYBER SECURITY STORY (AND THE TAP ON MY SHOULDER)
After less than 10 years, I was a leader in information management at my organisation, and a certified member of RIMPA. However, I yearned for new career challenges and opportunities, so I did a bit of soul searching. I had gone back to university to study IT with the idea of becoming an IM Systems Specialist, but I had realised this was not going to give me the opportunities that I craved. Eventually, I heard a niggly little voice that gave me the answer. Not from in my head, but from the desk beside me.
“You should look into cyber security,” my husband said, who shares a home office with me, and happens to work for a tech education company.
“I talk to cyber security professionals all the time, and I think it’d be something you’d love.”
“Really? How do you mean?” I asked.
“There’s a whole field of cyber security called GRC: Governance, Risk, and Compliance. That’s literally what you talk about every day.”
At first, I had doubts. I didn’t feel like what my preconceptions had taught me a cyber security professional was—someone with lots of technical, hands-on experience, and had spent time on a tech support desk. But the more I investigated it and the more I talked to my colleagues and friends in security, the more I realised he was right: GRC sounded exactly like the things I already thought about as an IM professional. From there, I started studying, got myself a mentor, and eventually got my start as a Cyber and Information Security Manager. My transferable skills from IM were a large part of this.
CYBER SECURITY IS BROADER THAN PEOPLE REALISE
The story of the niggling voice---that person who taps you on the shoulder and tells you that you’d be good in cyber security---is actually very common. Cyber security is a broad profession, but just like me, most people start out with a very narrow idea of what a cyber security professional is, one that they can’t see themselves as. Because of that, they talk themselves out of considering it as a career option, until someone in the field—a colleague, a roommate, a friend, or a spouse--taps them on the shoulder and lets them know it’s a real possibility. So, consider this your shoulder tap. I’m passing it forward, letting you know that cyber security is indeed something you can consider a future in.

It’s actually very exciting to realise that cyber security isn’t just a single ladder, but a wide range of entire career paths you can pursue, many of which you already have transferable skills for. Here’s some of the pathways you might want to learn about:
1. Security Analyst
Are you great at noticing suspicious things, thinking critically, and have good attention to detail? You might thrive as a Security Analyst. Analysts review alerts to detect if they’re suspicious or not and investigate and respond to threats. If you’ve got great communication, teamwork, and time management skills, these are also a plus.
2. Pen Tester / Red Team Operator
Are you the sort of person who likes to challenge yourself, and can put yourself in the shoes of someone trying to break a system? Pen testers use ethical hacking techniques to simulate attacks on a system, to flag weaknesses and vulnerabilities. That way, these issues can be fixed before the real bad guys can exploit them.
3. Incident Response / Forensics
Are you calm in a crisis, have great attention to detail, communications skills, and can think about a sequence of events? It might be worth looking into incident response
and forensics. These specialists are like the firefighters of an organisation, jumping in to identify and analyse a cyberattack, then shut it down. Afterwards, they figure out how the attack happened in the first place.
4. Security Architect
Are you great at systems thinking, problem solving, and are a bit creative? You might thrive as a security architect. They plan the overall security of enterprise systems, turning complex problems into simple, elegant solutions. By making sure assets, data, and systems are well fortified, this minimizes the risk to the organisation.
5. Governance, Risk, and Compliance (GRC) Specialist
Can you memorize a wide range of compliance and legal requirements, have a great nose for risk, can think holistically and communicate effectively? Then GRC might be of interest to you! In this role, you make sure an organisation meets the relevant standards regarding security, reducing risk through the process, and making sure the organisation is audit ready.
6. Threat Hunter
Do you love researching, have an analytical mind, and are always thinking about what’s on the horizon? Being a threat hunter, also known as threat intelligence, might be up your alley. You research cybercriminals, hacking methods, and threats to help prepare against attacks.

7. Cloud Security Specialists
Do you love learning about new platforms and services, have a head for systems thinking, and are highly adaptable? Working in cloud security might be for you. Cloud infrastructure is a large and vital part of most modern organisations, and so there are plenty of jobs for people who specialise in defending this.
8. Security Software Developer
Do you relish the problem-solving process, are tech savvy, and have a creative streak? These are the top traits of security software developers, who help create computer applications that protect systems and networks. They design, test, implement, and manage problems that defend against malicious activity.
9. Security Awareness and Education Practitioner
Do you have excellent communication skills and empathy, have a knack for public speaking, and are a life-long continuous learner? There are many roles that use these skills to help educate people about cyber security but all of them share a passion for teaching folks to be cyber security heroes.
HOW TO GET YOUR START IN CYBER SECURITY
As stated earlier, there’s not one surefire ladder to climb. However, there are a list of things you can do to improve your odds. Note that different fields of cyber security tend to have different requirements, so I’d research the specific area you’re looking at as well as consulting this list.
1. Embrace your love of learning
I love learning, and it turns out it is one of the best traits you can have in cyber security (or really, any field of technology).
Every day in security, there’s a new threat to learn about, or a tool or technique to combat it. The threat landscape is always changing so it is important to keep on top of things.
Rather than be daunted by this, look at it is an opportunity to continue to grow, develop and have exciting ever-changing opportunities.
Some of the resources I use to keep informed and continue my education are:
• Dark Reading
• Krebs on Security
• ASD
• The Hacker News
• Schneider on Security
• Ars Technica
• ISC2
• Pluralsight
• LinkedIn learning
2. Get some certifications
Certifications are a great way to get a taste for whether you’ll like cyber security in a structured way, while learning the fundamentals and getting a credential at the end. As such, I’d highly recommend getting a foundational certificate, and then exploring specialist credentials from there.
ISC2, a cyber security professional association, has a wonderful entry-level certification called Certified in Cyber Security (CC). The course material gives a great overview on cyber security to help you discover where your passion lies.
"Every day in security, there’s a new threat to learn about, or a tool or technique to combat it. The threat landscape is always changing so it is important to keep on top of things.
Rather than be daunted by this, look at it is an opportunity to continue to grow, develop and have exciting ever-changing opportunities."

I followed this up with the Certified Information System Security Professional (CISSP) course which is a security leadership and operations certification. There are many different certifications that are relevant to different security fields so make sure to do research on what is relevant to the pathway you are interested in.
3. Find yourself a mentor in cyber security
I can’t emphasise how much it helps to have a mentor in the field. It’s not a requirement, but it does go a long way. A great mentor will help you determine the skills you need to work on to build your career and share their experiences within the field.
I have been very lucky within my career to have found fantastic mentors in both information management and cyber security to help me grow my career. I can honestly say that I wouldn’t have gotten as far as I have, as quickly as I have, without their amazing guidance. Organise to meet with them regularly and learn as much as you can.
4. Seek career opportunities within your current organization
It’s a lot easier to move into cyber security within your current organisation if you’re not currently in cyber security, than to try and step into an entirely new field in a different organisation. The first good way to do this is to let your cyber security team know you’re interested in cyber security and seek opportunities to work collaboratively with them. Ask yourself how you could make your existing processes more secure. Look at your existing systems and processes and ask, “How would I break that?”, “How is that at risk?” or “How would that fail effectively?”
Become the cyber security champion in your area, and this will help create an intermediate step between your current career and your future one.
Secondly, keep your ear to the ground with any roles that might come up internally. Ask what would be needed for you to get these roles and then spend your time learning to fill these gaps.
Hopefully you’ve come away from this article with a good idea of some of the career opportunities available to you in cyber security, and a list of steps you can take to get a start in the field. Cyber security is a rewarding career where there’s always something exciting to learn, so if any of the above seems exciting to you, I’d highly recommend checking it out.
At the very least, you’ll start and learn a little bit more about cyber security, and this will help you out in your everyday role regardless of if you pursue it as a career.

Sharon is an Information Management professional, innovation and tech enthusiast. Former Information Manager at the Victorian Electoral Commission and current SharePoint Collaboration Consultant at the Department of Transport & Planning, Sharon is always looking for learning opportunities and to try new ways of working.
BY CHRIS FOLEY

CASE STUDY
Physical records are forever, not just for Christmas is a refashioning of an old proverb. The current Digital Age has driven all organisations to re-evaluate their business processes and information lifecycle management practices; however, physical information does not disappear simply because the technology has changed. Indeed, physical information is an oftenneglected information format which incurs significant annual costs whilst offering ambiguous value and crippling hidden risks. This article will explore the efforts of The Salvation Army in Australia to climb its Mount Everest of archive boxes before the mountain consumes it.
BACKGROUND: THE ORGANISATION
The Salvation Army (TSA) is an international Christian movement committed to giving hope where it is needed most. Within Australia, it provides services to people in need irrespective of demography, ethnicity, and religion. These services include aged care services, alcohol and other drug services, emergency relief, employment services, family and domestic violence, financial aid, and homelessness services.[1] In the financial year ending June 2024, we assisted more than 250,000 people, provided $24.3 million in financial assistance, and delivered 1.1 million nights of accommodation across all our programs.[2]
This commitment to service delivery translates to a staggering volume of information that we capture and store about our clients, our people, and our assets. Indeed, it was unknown how much physical information that we possessed until the project commenced – with more than 30,000 archive boxes in commercial storage vendors alone, and the equivalent of a further 10,000 or more boxes stored onsite across all our physical locations. However, storage of physical information is not a neutral undertaking. It comes with significant financial costs and regulatory concerns.
TSA depends on its revenue sources to fund its services – derived from a mix of donations, government funding, and the income from its businesses such as the ubiquitous Salvos Stores. However, the costs associated with delivering these services are increasing with the current cost of living crisis in Australia, whilst simultaneously our funding sources are shrinking due to the same cost of living pressures. Therefore, TSA is reevaluating its costs and re-prioritising how its finite funds are spent. The costs of storing, accessing, and managing physical information, however, can be a difficult expense to quantify. Some elements of the total costs are knowable – such as the costs incurred with the commercial records management storage vendors. However, there are also hidden costs with respect to managing physical information. Such hidden costs include:
Personnel costs associated with information stored with the commercial vendors – inclusive of their time spent preparing archive boxes for transfer, maintenance of the boxes in storage (monitoring the life cycle of the boxes and processing of invoices), and searching for information that may reside in physical archive boxes.
Storage and personnel costs associated with physical information not stored with a commercial vendor. TSA in Australia operates from hundreds of locations – ranging in size from shop fronts to residential aged care centres, and to warehouses. Anecdotal feedback suggests that physical information exists across all our locations. However, where TSA directly owns a location, then the costs associated with storing physical information are not factored into the costs of operating that site.
TSA captures, stores, and uses significant volumes of personally identifiable information (PII). This information can take the form of identity documents, financial information, and case records.
Our actions with respect to such information, however, must be consistent with the current Australian legal framework governing PII –such as the Privacy Act 1988 (Cth), the associated 13 Australian privacy principles[3], and legislation governing medical and health information.
The Privacy principles specify:
• What is personal and personal sensitive information.
• The obligations applying to organisations regarding the capture, use, and disclosure of personal information.
• What rights pertain to individuals with respect to their personal information stored by organisations. Historically, TSA has captured PII in physical formats such as documents, photographs, audio, and film. However, for much of this information, unfortunately, we do not have a good understanding of what we have and where it is located. Therefore, hanging over our heads
"The costs of storing, accessing, and managing physical information, however, can be a difficult expense to quantify."
is the possibility of a notifiable data breech[4] with respect to physical information. If such was to happen, it might be difficult to understand what information has been disclosed and to whom.
The implications of a physical data breech may include:
• Potential harm to the individuals whose information has been disclosed.
• Significant reputational damage to TSA within the Australian community, and
• Significant legal and financial penalties incurred by TSA.
Between 2023 and 2025, we completed preliminary steps for tackling our Mount Everest of archive boxes, including:
• Creation of my position (the Data and IM Lead) to drive internal awareness and promote a proactive agenda.
• Creation of internal policies and procedures, such as an Information Retention and Disposal Standard. As a non-government entity, the
onus rests with TSA to establish its own information and disposal regime. Yet, as an organisation operating across numerous regulated industries, we have many obligations incumbent upon us.
• Building and strengthening of internal stakeholder relationships. A key initiative has been the establishment of internal data and information forums with a diverse internal membership (department heads, system owners, and administrative support personnel) to assure the maturation of our information governance culture.
• Selection of a single commercial storage vendor (Grace Records Management) with whom we will store our physical information.
• Analysing how many archive boxes we possess. This was an unknown figure before I started.
The overarching aims of the Physical Offsite Storage project are:
1. To provide transparency over what we store and where we store it.
2. Reduce our PII risks with respect to physical information storage.
3. Reduce costs and volumes of items stored, and
4. Provide an effective internal customer service experience with regards to the storage and retrieval of physical information.
To ensure that such aims are intelligible and can elicit buy-in from stakeholders, I have scoped the project as a series of 6-monthly goal periods.
For the six months ending 30 June 2025, we will:
5. Consolidate our holdings with five storage vendors into one (we closed our relationship with a sixth vendor already in 2024).
6. Assess the expiry of retention requirements for physical items stored with our legacy vendors and destroy time expired items.
7. Assess the considerable physical holdings residing at a TSA warehouse located in inner Melbourne. Time-expired items will be destroyed, and the remainder will be transferred to Grace.
8. Encourage departments to initiate physical archiving activities.
9. Implement a customer service experience with the Grace ‘Gateway’ online portal for selected TSA personnel.
For the six months ending 31 December 2025, we will:
10. Extend our disposal assessments to include the Grace holdings.
11. Creation of a staging area for archive box consignments at the warehouse located in inner Melbourne.
12. Provide support to over 300 local ‘corps’ (our local churches, through which much of our services are delivered) as they assess their inactive physical information repositories.
13. Initiate data quality improvement actions with respect to box inventory metadata.
14.Continue to encourage departments to initiate physical archiving activities.
15. Extend the customer service experience with the delivery of an internal inventory search tool and a customer request system (to be accessible by both ‘power’ users and ‘casual’ users).
Our backlog goals include:
16. Investigation of the use of selfstorage vendors for the possible storage of physical information. TSA has lease arrangements with many such vendors Australia-wide, however, there is no central visibility over what is being stored.
17. Ensuring that disposal actions occur as an annual activity.
A project touching virtually the whole organisation cannot be completed alone. Therefore, I needed to define my stakeholder roles and responsibilities:
•An executive sponsor to champion the project at the highest levels. During the project, my function was transferred from the Governance portfolio to IT. I have been fortunate that both executive heads have been firm supporters of the project.
•A line manager who actively promotes the project with his counterparts across the organisation. As with many organisations, the informal crossdepartmental networks at TSA are essential to building awareness and buy-in for any initiative.
•Departmental contacts (at both the managerial and the worker levels) who are willing to engage with the project and drive change and action within their spheres.
•Project resources available to deliver the project. In practice, much of the work devolves to me. However, I have been able to utilise TSA’s practice of engaging volunteers, and I have been fortunate to recruit several individuals who bring enthusiasm and much needed skills to the project.

Project success is dependent upon getting our building blocks right, maintaining and strengthening our internal and external stakeholder relationships, matching scope to available resourcing, and delivering tangible outcomes within 6-monthly time frames sufficient to satisfy the stakeholders
Throughout the preliminary stages, and the execution of the current 6-month goal period, the learnings have been constant. Sometimes, harsh realities have forced flexibility with respect to project approach, scope, and timelines.
Key learnings include:
Resourcing: I cannot complete the project on my own; the volume of work is too great. Therefore, at the time of writing, I am investigating options to expand my team further.
Vendor Relationships: Grace, as our partner, has been engaged to coordinate the transfer of some thousands of archive boxes from each of the legacy vendors.

Scope: The project scope quickly ballooned from consolidating the holdings of the various commercial storage vendors to something much bigger. Therefore, the adoption of 6-month goal periods has provided focus and prioritisation to the project.
Policy Framework: Maintenance of an internal policy framework has been essential. Our Retention and Disposal Standard is constantly evolving in response to increased understandings about what records we capture and how long we retain them.
Stakeholder relationships: Such relationships have been rich and generous, usually helpful, and occasionally frustrating. However, without such relationships, the project cannot succeed.
TSA’s Physical Offsite Storage project will address a commonly overlooked component of our information eco-systems within the Digital Age –our physical information holdings. However, the project is not a trivial undertaking; we are dealing with many thousands of archive boxes, diverse business processes across the country, and the mitigation of significant cost and PII risks.
Project success is dependent upon getting our building blocks right, maintaining and strengthening our internal and external stakeholder relationships, matching scope to available resourcing, and delivering tangible outcomes within 6-monthly time frames sufficient to satisfy the stakeholders.
As at authoring this article, the first 6-month goal period is underway. I hope to report by the end of 2025 that we have destroyed more boxes than we have transferred to Grace.
OAIC: Office of the Australian Information Commissioner. Personnel: Within TSA, all our people are known as ‘personnel’ – inclusive of Officers, employees, contractors, volunteers, and local church members.
TSA: The Salvation Army.


Chris Foley is an experienced information management professional. His 25-year career in IM has spanned both public and private sectors. As the Data and IM Lead at The Salvation Army, his role is to drive an information governance culture so that the organisation can stay true to its mission of service in the Australian community. Additionally, Chris holds postgraduate degrees in Education, History, and Information Management.
BY SUSAN TASIC-CLARK
You know the saying - 'When you only have a hammer, every problem is a nail.'
In content governance, not all information is equal. Some of it is dynamic – being written, edited, shared, consumed, re-drafted and published – in the prime of it’s active life. Some of it is highvalue based on use and purpose. However for government agencies the country over, many records are final and rarely viewed or accessedconsidered inactive prior to disposal. In the vast expanse of content holdings you control, you are faced with many governance challenges. You are likely to have volumes of items that are unclassified, may be a duplicate, may contain PII, may not have a meaningful title. Not everything is a record. Most organisations have unused content but you’re stuck in a quandary. You can’t dispose of content when it isn’t classified, and you shouldn’t delete items when you’re not sure if they are records. Putting all of this information in your records management system (RMS) would quickly outstrip the purpose it was built for and the cost would be astronomical. So what can you do? To treat your information and records based on value to the business and need for compliance, you fit yourself out with the right tools for the job.
Your RMS works beautifully for active records. Your people work with your RMS, your processes are built around it and the change cost would be huge. For new records, records in high demand, recent records and records that need to change before becoming final, RMS is the right place for them.
Where should inactive records, or business complete records be retained? And which records are business complete and ready for preservation anyway?
The definition for business complete records is set by your organisation’s policy direction. Deciding appropriate criteria and timing for preservation treatment once records are inactive is nuanced for many organisations. If you’re not editing the documents or their metadata, you don’t need to change them later, they aren’t being accessed or viewed; they are very likely inactive or business complete. You might need to view, export or hold them for a legal, audit or FOI use case; but otherwise they might be ready for preservation.
An Information Archive can pair with your RMS to give you the solution to your compliance and retention needs, with a simple approach to managing your records going forward.
Why is Information Archive a better tool for those aging records? Let’s dig in a little.
Once records have been around for awhile the tacit business context for them is lost. The people who worked with them originally have gone, the business processes have changed, the policies they ran under have been superseded. Metadata on records provides some clues to their content. But knowing where something is, what it’s called and a records classification are the very beginning of understanding. Are these records relevant to your enquiry? Enter AI.
Take the example of an archived legal case. The metadata of the case tells us some information about it – name, reference number, closed date etc. If I want to really understand what that case was about, I can do a search, look at the metadata, and read 300 documents. Or, I can use the conversational AI interface to do some work for me –summarise what the case was about, tell me the key facts, answer specific questions, create graphs on data in the content… you get the idea. We keep records to understand how we came to decisions and why we made them. When the tacit knowledge of those records is gone, a conversational AI helps us to follow the thread through records for the decisions we seek to understand. Using a conversational AI interface is therefore most essential for understanding archived records.
In 2023, Gartner said your information estate would triple by 20251. For a government agency, that means a landslide of new records is already here, and you need a solution to handle records that can scale out - as you cross your first 100TB, your first half a petabyte, your first petabyte. Expecting your RMS to meet even half of that load without adequate planning is heading for disaster. Luckily, Information Archive is a proven application that can effortlessly grow to accommodate those needs. Where you have large
sized records like security footage, drone videos, large photos, and video recordings that you have to keep, you can take a simple approach to manage them. You have the option to route those records through a classifying service to your Information Archive. This offers an immediate compliance win and a long-term answer to control large volumes of business complete records that don’t always make it into the RMS because of their size and file type.
Storing records in a secure and compliant archive only meets one aspect of digital preservation. There is little point in keeping the information in the archive if it isn’t accessible or usable over time - be that 30 years or permanently. To ensure digital permanence and bypass risks from storage hardware aging, you can deploy Information Archive to your cloud hyperscaler of choice, or consume it as SaaS. With cloud deployment, yours or ours, you automatically benefit from high-quality infrastructure that is maintained and regularly upgraded. Preservation concerns that come with managing aging storage media, and the risk of data loss from bit rot, are a thing of the past.
At the start of this article we were thinking about how an information landscape includes documents where the classification, risk, PII and actual subject are unknown. For prolific, rogue and uncontrolled record stores like network file shares, cloud buckets, OneDrive stores, SharePoint sites, you need to understand the inherent risk and classification of records before you can decide what to do with them.
Our Core Data Discovery & Risk Insights can provide clarity on record content and their hidden risks. When you’ve decided what to do, the tool follows your instructions to take the actions you need. Some records have medical data, PII, credit card information – so you can classify and move them to the RMS or your Information Archive. Duplicates and ROT can be deleted.
To keep your governance tools smart, choose SaaS. No hardware to buy, upgrades to pay for, new staff to employ, DR to manage or cyber vulnerabilities to identify and remediate. Quarterly software updates means you can harness all of the benefits of advancement – this is especially important when generative AI is changing at breakneck pace.
When all is said and done, records are kept to meet legislative criteria. Using the right governance tools for the job at hand means you can deliver on your responsibilities. And that’s what every hard-working information manager wants, to put the tools down, and to have done a good job.

Susan Tasic-Clark is a Senior Manager in the OpenText Presales ANZ group. Her key focus is in ensuring that OpenText customers are making strategic decisions with explorations in AI innovation, across integrated platforms between critical technology stacks. With recent challenges facing organisations in heightened information security risks and advancement in artificial intelligence driven applications, IT landscape options have changed dramatically. Susan is contributing to organisational thought leadership to ensure that our customer’s investments in technology provides ROI and will meet the needs of tomorrow’s business.
[1] Gartner: Top trends in enterprise data storage 2023 Published 29 June 2023 — ID G00789370 — 22 min read By Analyst(s): Chandra Mukhyala, Julia Palmer, Jeff Vogel
BY ERIN SMYLIE AND TONY PERRY
Series Summary: When we talk about directions and the latest trends in information and data management, we often focus on the here and now without necessarily looking at the historical influences that have helped us in our journey. This series of research papers and subsequent presentations will take us back in time to delve into aspects of our past and discuss the attitudes and approaches that may have impacted on the advancements of today. It is only through the advancement in collaboration, research and technology that we have been able to uncover the approaches of the past to help steer our journey of the future.
Compilation Date: February – March 2025
For better or worse, censorship of taboo information is about control. Be it digitally or physically, we now have the luxury of archiving information in an orderly fashion, enhancing our ability to analyse data effectively and in a controlled environment. Was this always the case? From time immemorial people have found ways to censor that which threatens the status quo. Although we have the luxury of using digital methods for managing records and censoring information that allows us to retain the bulk of the content, we are faced with such an abundance of digital and physical information that it can feel like an impossible challenge to feel as though we have full control.
The ancients had a similar, yet all too different problem:
Consider the challenge of doing so in an era in which much of the content in need of silencing was through word of mouth alone, leaving behind no physical record. Still, censorship remained, only in other forms.
The democracy of ancient Greece (particularly Athens) allowed for a lot of self-expression, provided it did not undermine the values of Greece at the time. When this boundary was crossed (often by historians and writers) they would be tried for their crimes, and, not uncommonly, exiled. Anaxagoras, for instance, was a philosopher that was charged with impiety and exiled from Athens to Lampsacus c.450BCE for his theory that the sun and the moon were, in fact, made of rock and were not the works of gods.

If being exiled was not enough of a punishment, then those who dared to speak against the established ways of life and were considered a threat to the future of Greek culture would be put to death. Bring your mind to the execution of the ancient Greek philosopher Socrates in 399BCE-the consequence of accusations of having disrespected the gods whilst also introducing new ones, as well as his efforts to corrupt the minds of the younger generations. Or did he? Although his name and philosophy are familiar to many, he himself is not thought to have written any of the texts that we attribute to him. Rather, these accounts were written by his pupil, Plato. This is a consistent problem students of ancient history run into: the uncertainty of authorship which, consequently, makes it impossible to come to specific conclusions. This execution is a prime example. It is possible that Plato had glorified Socrates, minimising his crimes and manipulating the ways in which future generations perceived the philosopher. Should this be the case, then we can argue that this is a form of censorship in its own right. Another issue with ancient texts is that we are unable to rely solely on physical files due to wide-spread illiteracy. Alternatively, one of the key sources of information surrounding taboo, political affairs, and social values were theatrical plays. Even then, these were not without their fair share of censorship. Should a play include a scene of battle, it was to be performed off stage, while the chorus (a collection of people on stage that sang and told the story) explained the gruesome details of the scene. Actors were to wear masks, portraying the concept of the person they are playing rather than a direct representation, especially if they were portraying authorities or deities in an unfashionable light. It should also be known that it was not considered appropriate for women to watch too many tragedies at once, the thought being that their constitution could not handle too many emotions in one sitting. This, it can be argued, is another form of censorship, although rather than removing the confronting content of the plays themselves, they would remove the women entirely.
Another issue with ancient texts is that we are unable to rely solely on physical files due to wide-spread illiteracy. Alternatively, one of the key sources of information surrounding taboo, political affairs, and social values were theatrical plays. Even then, these were not without their fair share of censorship.
Upon reflection, it can be concluded that a significant part of censorship of taboo information in antiquity saw the removal of the person, be it by exile or death, rather than the redaction of specific written passages.
Upon reflection, it can be concluded that a significant part of censorship of taboo information in antiquity saw the removal of the person, be it by exile or death, rather than the redaction of specific written passages. Time moved on, and with it came new social norms. Amongst other things, religious movements created more strict expectations on what was deemed appropriate in relation to romance, sexuality, and marriage. As such, explicit content was often at the forefront of taboo information redaction. In fact, there were often specific locations in libraries dedicated to keeping said content away from prying eyes.
The Bodleian Library in Oxford, United Kingdom was no exception to this. In fact, from the year 1882 the shelves of the notorious library kept a collection of books locked away from public consumption known as the Phi Collection. If the spine of a book was stamped with a Phi symbol (Φ), this told those in the know that the contents of the book were explicit and unacceptable, housing over 2000 literary texts.

They were kept from students and the public alike, whilst also ensuring that there was no interference with the texts themselves. Despite this, the collection itself did not suffer much outrage, nor were the texts intended for destruction. Rather, it can be inferred that library upheld a standard of preservation even for texts that threatened societal sanctity, prioritising the preservation of information (Houston, 2015), pp1-15. Amongst these forbidden books sat some of the most iconic pieces of literature we continue to familiarise ourselves with today, including the first edition of ‘The Picture of Dorian Gray’ by Oscar Wilde. Many people are familiar with the iconic tale of a young man who so greatly wishes that he could retain his youthful beauty, watching in horror and regret as his wish came true and the portrait he’d had painted aged and warped before his eyes in his stead. However, how many know that the version of that book we are so familiar with is not the original, and is in fact a highly censored text that omits themes of homosexuality? The keepers of the Phi Collection certainly knew. The text was deemed inappropriate for public consumption, but by today’s standards the text is incredibly tame: “It is quite true,” Basil confesses, “that I have worshipped you with far more romance of feeling than a man should give to another friend... Somehow I have never loved a woman” (p144, Wilde; Frankel). What we may learn from this is that when we, as modern consumers, read the word ‘explicit,’ we hold it not to a different standard (indeed, the people of the past were just as passionate about their societal standards as we are) but to a different meaning. As such, we expect much more vulgarity than a text of this kind offers, the preservation of these texts giving insight into the transition of values over time.
Wildes’ homosexual subtexts were certainly not the first to shock the public into censoring his work. Throughout his career that spanned from the mid-1500s to the early 1600s, William Shakespeare produced a number of sonnets that are still regarded as some of the most important pieces of English literature to this day.
Decades after Shakespeare’s death, in the year 1640, a seemingly disapproving John Benson republished the sonnets after changing the pronouns from masculine to feminine in order to adhere to current laws and accepted behaviours. Classic sonnets: iconic verses, all censored to avoid the confronting romanticisation of one man’s love for another. “A man in hue, all hues in his controlling...for a woman wert thou first created” the speaker of Sonnet 20 declares, for example. Despite the original texts being restored and made public a century later, these censored versions of the sonnets remain the most commonly used in education and leisurely reading. It is here we see how censorship of the past has ingrained itself into our current perceptions of history and culture. It is important to remember that there was no particular word for homosexuality when Shakespeare was writing his sonnets, but that did not stop it from being a crime at the time, and as such the censorship of the texts were, in a sense, the bodies to receive the punishment so the writer could survive.
Human nature conditions us to prioritise and protect that which we hold to great importance. When weather or warfare threatened the preservation of texts, history has told us that there was, in fact, a hierarchy and an order in which books were to be protected. This tells us a lot about what people valued during various lifetimes, or perhaps how authoritative influences represented the masses that may actually have felt differently. Even so, it is worth wondering, if texts such as these were truly so unforgiveable and threatening to former ways of life, why would the people of the past not just simply destroy the books?
Sometimes, that’s exactly what people did. Libraries and archives would often prioritise preservation over destruction, finding the value in learning even from that which they don’t agree with whilst also maintaining the texts for future scholars. Sometimes, though, the weight of the words within the texts posed too much of a risk to the established way of life and subsequently had to be destroyed.

"The privilege we have as modern media consumers is that we can look back on events such as these and think, with blissful ignorance, that we have come a long way and will not be threatened by such vigorous censorship. It is vital that we remember, however, that taboo topics are ever-changing and the value to which censorship is held has never faltered. In fact, it is arguably more prevalent now than ever."
The privilege we have as modern media consumers is that we can look back on events such as these and think, with blissful ignorance, that we have come a long way and will not be threatened by such vigorous censorship.
In 1933, members of the German Student Union collected books containing anything that contradicted the ideologies of the Nazi Party. This is known as the Nazi Saurberung, and consisted largely of books pertaining to socialism and Jewish culture.
Once these texts were found, they were then thrown onto pits of fire in a public display of authority over people, but also over information. Information is identity, so by destroying texts relating to a particular group of people, they were also eradicating legacy.
One of the most frequented collections of Jewish materials in the Bodleian Library is the ‘Copenhagen Collection,’ a series of Hebrew books that were under threat of siege and destruction amidst the Nazi invasion of Holland. This collection was first moved to a Jewish school, but as the threat of prosecution became more severe, the books were later moved to a Dutch school for safe keeping.
The survival of most of these books (a couple having been obtained and destroyed) shows the collaborative efforts and sacrifices made to preserve written records of culture. The surviving books are labelled with a stamp attributed to the Offenbach Archival Depot, allowing us to trace, analyse, and further preserve the texts of this collection (Ovenden, 2020).
There were also more subtle yet less conventional approaches to hiding information from the public. Lee (2020) recounts a conversation in which he shows a photo of an armchair to the owner of a furniture store. Innocent though this may seem, the truth is that the reason for such interest in this chair is because, stuffed inside and sewn into the cushions were documents related to the Nazi party. Although this method is unorthodox and impossible to control, Lee’s recount of this conversation proved that there was little surprising in this (p17), and that sensitive information would be censored by any means necessary. Censored, and yet right under our noses.
The
survival of most of these books (a couple having been obtained and destroyed) shows the collaborative efforts and sacrifices made to preserve written records of
culture.
The privilege we have as modern media consumers is that we can look back on events such as these and think, with blissful ignorance, that we have come a long way and will not be threatened by such vigorous censorship. It is vital that we remember, however, that taboo topics are ever-changing and the value to which censorship is held has never faltered. In fact, it is arguably more prevalent now than ever. Social media is an integral part of our lives, and in many ways, we have become blind to just how frequently we are faced with censorship. Online posts may limit interaction to those in specific groups; images are blurred and labelled with a warning before the user can decide if they want to see the contents; specific words are flagged and can cause the post to be taken down. Amongst the blatant taboo and strict censorship, there exist topics that don’t require as much action yet are still found in wide-spread conversations of distaste or even outrage. With the advancement of Artificial Intelligence (AI), there is a growing concern about how integrated (and, indeed, threatening) it is becoming with human life.
Colloquially, one of the biggest concerns of this regard is the increased use of AI to create pieces of art, sparking heated philosophical questions as to whether anything not created by people, shaped as we are by our experiences and emotions, could truly be considered art.
Social media apps such as TikTok and Instagram are major platforms for those dubbed ‘AI artists;’ a title that is often criticised as being an oxymoron and exists solely to make ‘easy money’ by laundering art with no ‘meaning’ or ‘soul.’ Similarly, AI artists are accused of plagiarising man-made works of art, given that AI learns from pre-existing references. Many may look at this topic and consider it to be a waste of time and not of much importance. What we must remember, though, is that social media often influences real life more than real life influences media, and as such offline social interactions become framed by what has been widely deemed appropriate according to anonymous netizens. This becomes more of an issue when major companies implement the use of AI art, as the implication is that the employment of people in creative industries is being threatened by a mechanism the public has little respect for and is viewed as simply a way of saving money. In this way, the censorship comes more in the form of trying to deny allegations of the use of AI in art or promotional materials in order to preserve the reputation of the artist/company as opposed to the actual content.
How can we possibly accurately archive work that is attributed to no particular person, place, time, or medium? Art has always been a platform on which people can express their personalities and religious/ socio-political passions, and as such has always been a significant point of contention when the content matter contradicts the current social standards.
Titians’ painting Venus of Urbino (1534) faced considerable backlash for the seductive pose of Venus combined with the humanising details of a loving marriage (the small dog sitting at the end of the bed that, it is implied, is shared, while the maids tend to their business in the background).
Sexualising Venus in a way that seemingly sought to represent all married women was considered wildly inappropriate, and yet not strictly hidden. Even so, this work of art remains highly regarded for both its boldness and its skill. Today, we still consider stark nudity and sexualisation to be vulgar and inappropriate but are considerably more forgiving of artistic expression in the name of sexual empowerment than people of the past would have been.
What we must remember, though, is that social media often influences
real life more than real life influences media, and as such offline social interactions become framed by what
has been widely deemed appropriate according to anonymous netizens.
That being said, there are many responsibilities that come with this topic, such as creating content warnings and appropriate censorship, but most importantly, consent. The more AI learned from its surroundings and exposure to all forms of culture, the visual and audio quality improved and became strikingly life-like. While many people online chose to utilise this to make jovial videos or political statements, others took a more sinister approach and used this newfound skill to create explicit content using the faces and/or voices of celebrities, causing considerable threats to their careers, reputations, and privacy.
Although social media platforms tend to remove videos or images of such nature fairly quickly, often banning the person responsible for a period of time, it is safe to assume that this is more of an attempt to adhere to guidelines rather than to enact significant action against this behaviour. It is not unfathomable, nor unreasonable, that future attempts at sabotaging others in this way will become a criminal offence. We may reflect on the past and the lengths that were taken to control and censor forbidden information but also ought to relish in the freedom we have to express ourselves creatively, politically, and socially that we experience now and in the future.

Erin Smylie – Information Management Consultant for Paragon Information Management Services Australia Pty Ltd, a graduate from La Trobe University with a Bachelor of Arts in Chinese Languages and Culture and Classics and Ancient History, and a member of the Golden Key International Honour Society.

Tony Perry – Director of information and data management consulting company
Paragon Information Management Services
Australia Pty Ltd and long term information management specialist with over 30 years of experience having worked across multiple international regions including the UK, Europe, Norway, US, Canada, Middle East, India New Zealand and Australia and industries including oil and gas, mining, aeronautical, and the arts within both private and government sectors.
BIBLIOGRAPHY
• Lee, D 2020, The SS Officers Armchair, Vintage p17
• Houston, L 2015, Towards a History of the Phi Collection, 1882-1945, pp1-15, Hertford College, University of Oxford.
• Ovenden, R 2020, Burning the Books: A History of Knowledge Under Attack, John Murray (Publishers) p138
• Shakespeare, W 2020, eds. Edmondson, E, Wells, S, Sonnet 20, Cambridge University Press p145
• Wilde, O 2012, eds. Frankel, N, The Uncensored Picture of Dorian Gray, The Belknap Press of Harvard University Press p144
BY JESSE WILKINS
What if your organization’s entire records team won the lottery today and quit? What would happen to your records program? How long would it take your organisation to rebuild the team from scratch?
If you had a records management playbook in place, your newly hired team could hit the ground running!
Acknowledgement: This article appears with permission of ARMA International and was first published in the ARMA Magazine, September 26, 2022.
In sports, a playbook describes the “plays” a team executes to accomplish its goals and objectives—generally, winning a game or match. Plays are tailored to specific circumstances: the team’s personnel and capabilities, the opponent’s capabilities, and the specifics of the in-game situation. Some plays just do not come up very often, while others are executed regularly throughout the game. Some plays only come up at the end of a period of play or towards the end of the game. And once the game is over, the coaching staff reviews the plays and the team’s execution of them and makes changes to get ready for the next match.

Similarly, a business playbook describes the plays that a particular organisation, department, or work process executes to accomplish its goals and objectives. Larger or more mature organisations might have multiple playbooks, while smaller or less mature organisations might have everything in a single playbook.
In this article, we will focus on the records management playbook— the list of plays that a records program will execute on an ongoing basis. Different records programs will operate at different levels of maturity, so some programs will include more plays in their playbook than others. Similarly, different organisations have different cultures, and the playbook needs to reflect those realities as well.
So how is this different from a standard operating procedures (SOP) manual?
The playbook is like an SOP in that it lists the things to be done and some detail about how to do them.
But plays go beyond just the tasks and activities required to include things like metrics, references, and key players.
It also includes cultural values and mechanisms for making decisions when the play is not so clear-cut. We will look at the structure of the playbook and the plays in more detail later in this article.
It is also the case that in many organisations, SOPs were written years or even decades ago. Because they tend to be scattered around the organisation, they are not maintained well; and because of that, there is often a significant divergence between what the SOP says in describing a process and how that process actually gets done. Again, the playbook can provide value by having everything in one place and in a readily maintainable format. Through a playbook, the organisation can:
• Identify and implement best practices and standards
• Ensure that operational practices are consistent, repeatable, and standardized to the extent possible
• Ensure resources and priorities are aligned to common goals
• Train new employees to perform within the guidelines, become a part of the desired culture, and develop shared values
• Ensure that important expertise, on which their business results depend, does not walk out the door when employees are unavailable, transition to a different role, or leave the company
The records management playbook’s objective is to provide best practices for the records program, not to substitute for management and leadership. It is critical to balance the importance of standards and guidelines with the value of local management discretion and individual employee creativity[1].
Another way to look at the records management playbook is that it contains what someone would need to know to execute the various tasks required to sustain the records management program over the course of thirty, sixty, or ninety days—even up to a year. What are the things you do, create, monitor, or report regularly? What are the questions you answer every day or every week?
These should be in your playbook.
The playbook is a living document. As the team develops new processes, they should be turned into plays and added to the playbook. As the team updates, streamlines, or adds processes to reflect changes in the organisation, its technology, or legal or regulatory requirements, the team should also update the plays in the playbook. The playbook thus becomes the sole source of truth for all things involved with and related to your records program.
At the same time, the playbook should reflect the reality of what is done and how it is done. It makes no sense to write a play about disposing of legacy emails if legacy emails are not in fact being disposed of.
In other words, it is not a list of best practices and the ideal world if time and resources were no object. Rather, your playbook should be accurate as to what you are currently doing, and as your program matures, those changes should be reflected in the playbook. It is also not a list of how some other organisation does things. A different organisation, even in the same industry and jurisdiction and similarly sized, will have a different level of maturity, different organisational culture, and different personalities involved. It might be helpful to look at another organisation’s records management playbook for ideas and completeness, but you should not try to implement its playbook as-is in your organisation.
This also means that plays should include some amount of flexibility, because things change, and sometimes the circumstances require that a play be executed differently. Inflexible adherence to whatever is described in a particular play may miss something and will tend to encourage employees to ignore it. Again, with effective leadership and management, this sort of flexibility should not be a major issue.

The playbook is a living document. As the team develops new processes, they should be turned into plays and added to the playbook. As the team updates, streamlines, or adds processes to reflect changes in the organization, its technology, or legal or regulatory requirements, the team should also update the plays in the playbook.
Depending on how you build and publish your playbook, it may make more sense to link to your supporting documentation—the detailed procedures, checklists, flowcharts, standards, and anything else that supports a particular play.
Similarly, it is helpful to distinguish between plays that are executed on some sort of a regular basis, with projects which may be executed much less frequently. For example, how often will you change recordkeeping applications? You probably don’t need a “Select and Implement New Recordkeeping Application” play in your playbook. You need a process to follow, to be sure, but that is not a play.
The benefits of having and using a records management playbook include[1]:
• Organisation: The playbook includes all the information your records management team needs to operate successfully, in one organized and easy-to-access place.
• Efficiency: The team can save time when they have questions about workflows or procedures because the answers are in the playbook. They can follow the steps outlined in the document rather than searching through numerous files, locations, and resources to find information. And if it is digital, and why wouldn’t it be, supporting resources can be linked directly within the play.
• Work quality: The playbook includes references, standards, checklists, and templates that align with the organisation’s existing policy and quality frameworks. Work output will become better and more consistent as a result.
• Employee training: A playbook makes it easier to onboard new team members and roles and helps them get up to speed quickly.
• Independence: Employees can refer to the playbook instead of asking their managers for help for those plays that are included in the playbook. Similarly, supervisors can trust their employees to do quality and accurate work without constant management because they have a playbook for guidance.
The records management playbook is intended to be self-contained; that said, there is a tradeoff between being comprehensive and being unwieldy, especially for an organisation with a mature records management program. In that case, it makes sense to focus only on the plays, and move the other elements listed below into supporting documentation. It may even be worth breaking the playbook into two or more parts—for example, records management processes and records program processes. Depending on how you build and publish your playbook, it may make more sense to link to your supporting documentation—the detailed procedures, checklists, flowcharts, standards, and anything else that supports a particular play.
The playbook will have three distinct parts: the introduction, the actual plays, and any appendices.
This entire part should be brief—no more than a page or two for each section, and shorter is better. Some organisations leave this section out entirely and make this content available as a separate, supporting document. The introduction, if included, should set the stage for the playbook. It could include any of the following sections. Introduction to the playbook. Much of this is included in the first section of this article.
Introduction to the records management program. This should introduce your records management program: its purpose and how it supports organisational outcomes.
It should also outline any unique aspects of how your records management program works within your organisation—for example, unusual administrative or reporting requirements. Again, will often vary for different jurisdictions or industries. Organisational context. This helps to orient new staff to the organisation and the plays in the playbook. This section would include:
• Organisational mission: What does your organisation do, and what does its legal and operational environment look like? These can help those reading the playbook to have some additional context over why the plays are the way they are. For example, a law firm’s records program must deal with client records, while a government agency’s may have to deal with Freedom of Information or open records-type requirements.
• Organisational culture: Is your organisational culture more focused on reducing and managing risk, or on accepting reasonable risks that are relatively low impact? Do you encourage people to be creative, or to follow directions closely? Again, these can shape the granularity and level of detail in your plays.
• Definition of roles and responsibilities:

These are the roles involved in the execution of the records management program, directly and indirectly, and who would be included on a RACI (responsible, accountable, consult, inform) chart. A large and mature records management program might include the following individual roles: director of records management, records manager(s), records analysts, and/or records coordinators. It might also include some sort of a steering committee. A smaller or less mature records management program might have a single person, with a non-records related title, or even be a part-time role. Indirect roles might include those with which records management team members need to collaborate, such as IT, or whose approval is required under certain circumstances such as Legal signing off on policy changes.
There are hundreds of potential records management plays that could be included in a records management playbook, and there are certainly many more that would be unique to jurisdictions and industries. But as
noted earlier, the playbook should contain the plays that the organisation actually executes. It should not include such an exhaustive list of plays, many of which are not in place or even contemplated yet. For a more mature records management program, it may make sense to group plays into categories, so they are easier to access and manage. Here are some broad categories of records management plays—but there are a couple of points to keep in mind. First, each of the categories below may include several to many individual plays. Second, some of these categories may not seem specific to the records program, but the individual plays would. For example, plays under the decommissioning legacy systems category would focus on records appraisal, disposition of legacy records and information, and so forth. Finally, this list does not include any standard management or project management plays, which are also necessary and may be part of the records management program, such as budgeting, defining business requirements,
marketing and championing records management, records management system administration, and so forth.
Potential categories of records management plays for the playbook:
• Capturing and filing records
• Digitizing paper records
• Responding to requests for records
• Conducting records, information, system, and process inventories
• Developing metadata and classifications schemes
• Maintaining the records retention schedule
• Applying retention and disposition
• Reviewing and updating governance documents
• Migrating records
• Decommissioning legacy systems and user information stores
• Remediation of redundant, outdated, and trivial information
• Evaluating systems for records management capabilities
• Change management
• Assessing and auditing the records management program.


Depending on your organisation and approach, you might also include “records management-adjacent” plays such as privacy and data protection, e-discovery, archives, or document control.
Appendices can include anything that would be helpful to those using the playbook to sustain the records management program. For example, if your organisation has conducted a maturity assessment, such as the one aligned to the ARMA Information Governance Implementation Model, the results could be included as an appendix. We mentioned earlier the possibility of including a full RACI chart with contact information as an appendix. A full list of references and resources might be helpful as well—not just organisation-specific resources like policies and procedures, but also things like industry standards and reference works. A glossary and list of acronyms and abbreviations may also be of value.
Each play should include several standard elements. This makes it easy to maintain them and to add new plays over time. Name. This is the name of the play and should take the form of “verb-noun,” e.g., “Send Boxes to Offsite Storage.” Make sure that the name accurately describes the play using your organisation’s terms.
Purpose. Why is this play in the playbook? What is the business value of executing this play?
Description. The overall description of what is required to execute the play. This should include enough information for someone new to be able to follow the steps in the play but should not necessarily be a fiftynine-step checklist—rather, it should describe the intended outcomes. If there is a fifty-nine-step checklist, we can link to that in the references below. Players or responsibilities. The play should identify the primary role responsible for executing the play. Since different plays will have different players, I like adding a mini-RACI chart for each play, and then rolling up all the individual RACIs into a full RACI chart either at the start of the playbook or as an appendix. It is up to you whether to include a point of contact—for maintenance purposes, it may be easier to include contact information as part of the full RACI chart if you create one.
Cadence. This refers to both the frequency of the execution of a play as well as the actual timing. For example, your “Send Boxes to Offsite Storage” play might be done every month, but only once a month, and only at the end of the month. References. List all the things that can support the efficient and successful execution of a play: policies, procedures, guidelines, checklists, templates, standards, job aids, etc. If you can link to these so they are immediately available, even better; some ideas follow in the section on building the playbook. Metrics. As the old management truism states, “if you can’t measure it, you can’t manage it.” Every play should have at least one metric that is relevant to how and why it is executed and that aligns to the overall goals of the organisation. These should be quantifiable to the extent possible, and if you can get a financially quantifiable metric, that is even better. Here is an example of an actual playbook play in Figure 1
The actual process of building a playbook is fairly straightforward. The two key challenges are in determining what plays to include and what platform to build it on.
As noted throughout, the plays in your records management playbook should include only those that you execute regularly. But responsibilities and documentation are often scattered across roles and information stores. First, start by reviewing any existing documentation of your records management processes— SOPs, flowcharts, procedures, etc.
Next, review any reports or other paperwork that you generate on a regular basis. These will often help to inform the metrics as well.
You should also review any existing job aids—checklists, glossaries/ lists of terms or acronyms, naming convention cheat sheets, and so forth. Do not overlook the records policy and retention schedule—while
these are the source of a few plays themselves, the retention schedule in particular often documents other records management-related tasks that result in the creation of records.
Look at job descriptions for the roles on the records management team—but make sure to compare them to the work that the members of the team are doing. Performance reviews can offer value as well, by identifying current expectations and priorities and potential gaps. Finally, if you are just starting this process, a note of caution. Records management textbooks are a rich source of information, but they could lead you to developing and including many plays that you are just not doing. This can call the value of the playbook into question.
Playbooks can be built as Word-type documents, as spreadsheets, or as PowerPoint-type presentations. There are tools designed for playbooks and similar types of authoring. A wiki can be a great way to build a playbook— each play is its own article, with links to related plays and to all the references and supporting materials. But the platform and its attendant capabilities do not matter as much as the answers to these questions:
• What platform is easiest to access and use for those who will be using the playbook?
• What platform is easiest for the team to maintain the playbook? If users cannot use it, or if the team cannot maintain it, it will become shelfware just like the traditional SOP manual.
You! Well, you and any other subject matter experts who can describe the plays and their individual components. Again, in smaller organisations or records management programs this might be the single person running the program; in a larger organisation or with a broader playbook, you will need to identify the right people to weigh in. You will certainly also want to reach out to anyone identified as having a records management responsibility (e.g., through the RACI chart) who is not a formal member of the records management team.

We have stressed throughout this article that the playbook is a living document that needs regular care and feeding to remain relevant and useful. Change is a constant; changes to technology, changes to legal or regulatory requirements, and changes to how the organisation does business all require that the playbook be regularly reviewed and updated. In fact, reviewing the playbook should be a play in your playbook! When the team finds out about a change that will impact a play, someone should be assigned to update the play with a timeline. Similarly, if the team determines a need for a new play, it should be assigned and scheduled. For example, developing a retention schedule the first time is a project. But reviewing and maintaining it are plays; once the retention schedule is finalized, those plays should be defined and added to the playbook.
The playbook is a great way to take your program to the next level. It takes some work up front to ensure that it is complete and accurately reflects the way your program works today, but once you have it, you will never look back!
References [1] https://www.indeed.com/career-advice/careerdevelopment/what-is-a-playbook-in-business

Jesse Wilkins, CIPP/ US, IGP, CRM/ CIGO, ICE-CCP, is the President and Principal Consultant for Athro Consulting, a records and information management consulting firm. Contact him at jesse.wilkins@athroconsulting.com

Emails are no longer the primary business information source for local and central Government organisations. RIMPA’s Diamond Sponsor, Exedee are extremely excited to announce to RIMPA members the introduction of our new eCom Management service.
BACK 10 YEARS…
In 2015 Exedee designed and introduced (our then brand new) service for auto-triage and management of incoming emails – it was called oMail. Back then, emails accounted for approximately 85-90% of all incoming Council correspondence, with the rest being scanned paper mail. oMail then and now included the following functions:
• Electronic triage - with no manual intervention to receive scanned paper mail and emails plus attachments and electronically identify their subject matter (including for each attachment type)
• Auto-register them into the Council’s document management system
• Identify missing NAR and Property data in the Council’s own data provided to oMail for use in matching the incoming mail and email items to the Council’s data
… FAST FORWARD TO 2025
Email triage and then auto-registration into a document management system is no longer enough as an isolated service.
Emails now account for less than 60% of communications in many Councils (and in other local, federal and central Government organisation).
To continue to preserve the document management system as the Single Source of Truth, there are additional information records that need to be captured and registered into the document management system -- as well as being shared with, or exported to other internal computer systems such as job/customer management systems.
These include:
• Webforms
• Transcripts of online meetings
• Recordings of online meetings
• 3rd party data and images from systems that record the Public’s reporting of local issues like rubbish in the street, hazards, potholes etc (including photo evidence and geographic location data)
• 3rd party data from electronic monitoring systems
• Emails and attachments as well as our original email processing services that are now also required for this much bigger group of information records:
• Electronic triage
• Auto-registration into the Council’s document management system
• Identify missing NAR and Property data in the Council’s own data provided to oMail for use in matching the incoming mail and email items to the Council’s own data. The collection of information types that need to be obtained and automatically registered into a document management system has therefore significantly increased – meaning that our Council customers now require us to provide a significantly expanded range of business information receipt and registration services. To meet today’s requirements, Exedee have substantially enhanced our original oMail functionality via the design and development of our new eCom service, as part of our comprehensive suite of eSolutions.


In the dynamic records and information management landscape, it is crucial that you can trust any data that is imported during your business automation processes. We can deliver 99% accuracy to you.
Exedee software is driven by the “power of e” – we make anything to do with digitisation of records and business information processing easy, effortless, exact and efficient.
Efficiently digitalises tens of thousands of documents in a short time
Effective governance demonstrated through complete and accurate metadata
Ensures you stay in control of information with a single source of truth for each document and a reliable search index
Enables increase in document transparency, accessibility and data quality
We put our energy and expertise into enabling all types of organisations to manage process automation and digitisation with ease – and with 99% accuracy.
Talk to the Exedee team of experts today, and find out how we can help you.
Visit www.exedee.com and register your interest.

DR BETHANY SINCLAIR-GIARDINI MRIM, CXRIM, MAISA, RIMPA LOCAL AMBASSADOR
There has never been a more critical moment for Information Management to take centre stage. Over the past decade, the world has undergone a sweeping digital transformation, evolving into a landscape dominated by technology.
theAmongst voices, the competing opinions, all the comments in the chat, one thing was crystal clear: stagnation was not an option. The moment had arrived for Information Management professionals to rise to the occasion, embracing this new era with both open arms and open minds.
Yet, despite this seismic shift, many individuals continue to engage in the outdated practice of stamping hard copy letters, diligently scanning them, and laboriously registering them into an Electronic Document and Records Management System (EDRMS). As the world around us becomes increasingly digital, one cannot help but wonder why so many remain entrenched in these antiquated methods. This is a question that frequently occupies my thoughts and sparks discussions with colleagues, yet the answers remain elusive, never quite clear-cut. Recently, a post on LinkedIn jogged my memory, bringing to mind the Moloko song “The Time is Now.” For those of us immersed in the field of Information Management, there truly has never been a more opportune moment to step forward, to elevate our roles out of the shadows of the proverbial basement once and for all. The time is genuinely now and let me elucidate why.
For those who attended the IAW Round Table Debate on AI on the 20th of March, you would have heard compelling discussions from eminent figures about the formidable challenges and abundant opportunities that AI is ushering into our profession. During the event, a poll vividly illustrated the mixed emotions of excitement and apprehension that attendees felt, and rightfully so. AI has been a buzzword for years now, lingering in the background of technological advancements. It’s no longer a novelty; yet its influence is just beginning to seep into our organizations, with some experiencing this influx like a powerful surge akin to the mighty Niagara Falls.
As AI swiftly integrates into the realm of Information Management, the imperative for us to adapt and evolve has never been more pronounced. Traditional methods of handling data and documents are rapidly becoming relics of the past, overshadowed by the dazzling potential for efficiency and innovation that AI promises to deliver.
As I sat in on that Round Table Debate, experts passionately discussed the sweeping implications of AI in our profession. The potential for unparalleled growth and advancement hung thick in the air like an electric charge, yet so too did the looming specter of the unknown. What sweeping changes would AI usher in? How might it revolutionise the way we work, think, and interact with the vast sea of information?
Amongst the voices, the competing opinions, all the comments in the chat, one thing was crystal clear: stagnation was not an option. The moment had arrived for Information Management professionals to rise to the occasion, embracing this new era with both open arms and open minds. The tantalising opportunity to mould the future lay right at our fingertips, waiting to be seized. Because if we hesitated, if we faltered, someone else would step in to claim it, and we would inevitably be left on the sidelines. Again.
I say again, as I observe a considerable number of Information Technology (IT) professionals immersed in the tasks of configuring complex systems, managing data retention, applying intricate layers of metadata, and constructing detailed information architectures. These diligent professionals are employed by organisations that also have a dedicated Information Management (IM) team. However, the IM team often finds themselves without a voice or presence at this critical table of decision-making. Job advertisements have begun to surface, enticingly labelled as ‘Information Architect.’
As AI swiftly integrates into the realm of Information Management, the imperative for us to adapt and evolve has never been more pronounced.
We absolutely need to be prepared for the future. We must rise to the occasion and ensure our contributions are acknowledged. It is essential to be recognised for our expertise in our fields and the unique value we bring to the table.
Yet, upon closer inspection, these roles essentially blend responsibilities from both IT and IM domains, with a predominant focus on IM. These positions require individuals to possess a solid foundation in information security knowledge and experience, typically centred around the Essential 8 framework and the Information Security Manual. The tasks outlined in these job descriptions fall squarely within our area of expertise. So, what exactly is transpiring here? Are we a profession on the brink of crisis, or have we merely wandered off course for a brief moment? We absolutely need to be prepared for the future. We must rise to the occasion and ensure our contributions are acknowledged. It is essential to be recognised for our expertise in our fields and the unique value we bring to the table.
In an era where organisations are keen to adopt AI technologies and establish comprehensive big data governance frameworks, data platforms, and a slew of other enticing initiatives, many tend to overlook the crucial need for impeccable records governance. This is firmly within our wheelhouse.
We stand on the threshold of a groundbreaking era in Information Management, where the lines dividing traditional records management and stateof-the-art technology are increasingly becoming indistinct. Our profession finds itself undeniably at a pivotal crossroads. The conventional methods of handling information fall short in the face of swift and relentless technological progress.
This has been the reality for some time now, yet I feel that the profession remains somewhat tone-deaf to these transformative changes. I speak to many IM staff, and they just do not work close enough with their IT and procurement colleagues, to make any real difference, when it comes to the procuring of these technologies. They normally end up being turned on, lots of public records go in there, but nobody looks after them with a records lens. The IM Team only see themselves as having responsibility for records in the EDRMS …. how does that work if there are lots of other systems also containing records? Who is looking after them?
A firm I collaborated with recently was on the brink of launching a substantial procurement initiative in both the records and data domains, potentially moving towards experimenting with AI large language models. When I engaged with their Executive team, I emphasised that they were on the verge of venturing into uncharted territory and that it was imperative to proceed with both eyes wide open.
I took a deep breath and stood up in that boardroom, meeting the eyes of each executive sitting around the table. “You are on a precipice,” I repeated, my voice steady and firm. “The choices you make now will shape the future of your organisation, determining whether you thrive or fall behind in terms of data privacy and information security. This relies on a strong records governance program, and you cannot leverage AI without it.”
"We stand on the threshold of a groundbreaking era in Information Management, where the lines dividing traditional records management and state-of-the-art technology are increasingly becoming indistinct. "
"The choices you make now will shape the future of your organisation, determining whether you thrive or fall behind in terms of data privacy and information security. This relies on a strong records governance program, and you cannot leverage AI without it."
It was an interesting moment, watching an Exec. team look at each other, understanding exactly what moment in time they were at. There was a time for ensuring better records governance, to ensure clean data, privacy taken seriously and information security policies that wrapped around information assets in the best possible way. They recognised this and pressed the pause button for 12-18 months on their procurement. This is a prime example of where IT, Data and Procurement can all run off ahead like the Charge of the Light Brigade, and it was up to me - the IM Consultant - to just ensure they were moving ahead in the right way.
Another example is from a local government agency who had procured a new system, had three legacy systems to shut down, and a huge data migration piece on their hands. Not only was the new system scoring very low on compliance (just over 60% PROV compliance and 70% VPDSF compliant), but they had no metadata to aid the migration and system decommissioning process. Legacy systems that had no recordkeeping governance or recordkeeping metadata contained within them. All digital landfills containing over a decade of data, with no disposal ever having been carried out. This situation was due to the IM team believing that they were only responsible for the records in the EDRMS. This is something I see so very often, like with every customer I work with. It scares me that there are so many IM teams not seeing the validity in applying the retention and disposal schedules across all the data holdings. I don’t know whether it’s due to a communication breakdown between IT, Procurement and IM, or historically, IT just turned on systems without giving a thought to anyone actually managing the data contained therein.

to an information security audience really illustrated how there was radio silence between IT and IM teams in most organisations. This has to change.
This is the topic of my paper at RIMPA Live later this year and I can’t wait to share some insights and really unpick this topic and carry out some real time root cause analysis with the audience.
Reading between the lines, you should now know that if you come to my session, be prepared to get involved! Information management professionals need to step up and see that they play a crucial role in today’s data-driven world.
I recently attended an information security conference and gave a paper on digital disposal and information assets. The audience were all Chief Information Security Officers and other persons who sit in extremely big chairs. It made for an interesting presentation when I began to look at enterprise security architectures from the viewpoint of the information asset.
I felt like I had stumbled into one of those film sets where the tumbleweed goes rolling down the old main street and nobody wants to step out the saloon bar into the firing line. Looking at system configuration and security architectures is something that, as a digital archivist, I have always done.
To up their game, gain a voice, and make a significant impact, they can focus on several key areas:
• Continuous Learning and Skill Development: The field of information management is constantly evolving with new technologies and methodologies. Professionals should stay updated with the latest trends, tools, and best practices. This includes gaining proficiency in data analytics, machine learning, and artificial intelligence. This also should include a transition from traditional IM approaches and embracing new digital ways of working. This includes digital disposal, assisting to configure systems, building up strong metadata profiles and decent user-friendly taxonomies and ontologies.
• Networking and Collaboration: Building a strong professional network can open doors to new opportunities and collaborations. Attending industry conferences, joining professional organisations, and participating in online forums can help information management professionals stay connected with peers and thought leaders. Collaboration with other departments within their organisation can also enhance their visibility and influence. Anybody who knows me knows that I am consistently on the RIMPA Community Forum. It is a key component within my own networking plan. It helps me build my “Bethany brand.”
• Advocating for IM to be involved with Decision Making: Information management professionals should position themselves as subject matter experts because that is what we are! By demonstrating the value of accurate and timely information, they can influence strategic decisions and drive business outcomes. This is in our wheelhouse and is ours for the taking so reach out your hands and take it!
• Developing Strong Communication Skills: Effective communication is essential for information management professionals to convey the importance of their work. This includes both written and verbal communication, as well as the ability to create compelling visualisations that tell a story with information, records and data. Let’s get better at telling our stories and showing our value.
• Embracing Innovation and Change: The ability

to adapt to new technologies and processes is critical. Information management professionals should be open to experimenting with new tools and approaches and be willing to lead change initiatives within their organisations. This proactive approach can help them stay ahead of the curve and demonstrate their value as innovators. We are the original agents of change - let’s do this!
Good records governance lies at the heart of any project, business decision, or technological investment. We ensure that information is accurate, accessible, and secure, forming the backbone of effective decision-making and strategic planning. Information management (IM) professionals play a pivotal role in this process, and it’s time for them to step up, hear their own voices, and make themselves heard. By advocating for robust records governance, IM professionals can drive significant improvements in organisational efficiency, compliance, and risk management. They must embrace the moment, leveraging their expertise to influence key stakeholders and champion the importance of well-managed information. As a profession, we need to see our value, lead by example, and ensure that good records governance is recognised as a key ingredient moving forward, wherever you work. Give up yourself unto the moment, the Time is Now!
Dr. Bethany Sinclair-Giardini is a dedicated RIMPA Ambassador based in Victoria, and having spent the last few years consulting, this year she is embarking on an exciting career transition to join Technology One. In her new role, she will focus on the Enterprise Content Management module, overseeing system design, configuration, and client training. Bethany is also a member of the Australian Information Security Association & The SABSA Institute, as well as holding a doctorate in archives and manuscripts. Many in the community may recognise her from the RIMPA Community Forum, where she is a vibrant and enthusiastic contributor.





For decades, the IQ has captured the voice and vision of our professional community. From feature articles and case studies to interviews and editorials, it has been a platform for thought leadership, connection, and progress.
As we turn the page on this chapter, we reflect with deep appreciation on the contributors, editors, advertisers, and readers who brought the journal to life.
This digital archive preserves the rich history and contributions of our profession. We invite you to browse past issues, revisit favourite articles, and celebrate the evolution of our field.
While this last edition marks the end of an era, it also opens the door to more timely, accessible, and dynamic ways to deliver the content that matters to you.
From expanded newsletters and member spotlights to expert-led webinars and interactive campaigns, you’ll now see content that is:
• Delivered more frequently
• Easier to access and share
• Better aligned with member interests
• More cost-effective to produce and sustain
We remain deeply committed to keeping you informed, connected, and inspired—and to honouring the legacy of the journal as we evolve into this next chapter.
The inaugural issue of InfoRMAA Quarterly emerges from the typewriter, capturing the essence of records management in the paperbased office era. Fresh insights from Queensland’s first national conference at Greenmount set the foundation for decades of professional discourse.
1990
Federal Council revolutionizes the journal’s approach by appointing a powerhouse editorial trio—Judith Ellis, Philip Taylor, and Bill Williams—ending the state-by-state rotation and establishing a consistent editorial voice that would guide the publication for years to come.
1996
As the information world transforms, so does the journal. Articles tackle emerging challenges like email management, internet records, and early EDRMS implementation—chronicling a profession boldly stepping into the digital unknown.
2003
Following a sobering Audit Office report on widespread non-compliance, the journal becomes a platform for professional accountability. Contributors call for higher standards, sparking conversations that would redefine industry expectations.
2005
In the aftermath of global catastrophes—the Boxing Day tsunami, terrorist attacks, and natural disasters—a groundbreaking issue on disaster recovery sets a new benchmark for the journal’s relevance and influence in crisis response planning.

Mirroring the association’s evolution to RIMPA, the journal transforms into “IQ – The RIM Quarterly,” sporting a fresh design and accessible approach that welcomes practitioners across all experience levels.
2017
A pivotal shift occurs as content increasingly positions records managers as strategic partners rather than custodians. Articles champion information value, security expertise, and executive-level contributions— elevating the profession’s perceived impact.
2020
As the world locks down, the journal steps up with timely insights on remote work practices, digital continuity strategies, and information security in crisis—becoming an essential resource during unprecedented global disruption.
2025
The journal closes its final chapter with this commemorative edition, celebrating four decades of professional evolution, countless contributors, and the enduring impact of a publication that both chronicled and shaped the information management profession.
Developing A BCS For Ministry Of Premier And Cabinet WA (1999, Vol. 15 No. 3)
Bridging the gap between abstract theory and practical application, this article brought theoretical concepts into day-to-day practice at Western Australia’s highest government office. The article generated the journal’s most passionate Letters to the Editor in its publication history.
I Spy… Managing The Archives Of The NZ Security Intelligence Service (2009, Vol. 25 No. 3)
This rare exposé peels back the curtain on New Zealand’s Security Intelligence Service, revealing the delicate balance between national security and civil liberties. Diving into the ‘neither confirm nor deny’ policy, the article explores how culture shapes everything from information declassification to privacy protections. Far from dry policy analysis, it offered readers an unprecedented look into one of NZ’s most enigmatic institutions.
The AI Edition (2019, Vol. 35 No. 1)
One of the most downloaded issues, a forwardlooking perspective on how AI is reshaping our field. Thought-provoking articles examined the promise and the practical implications of AI including emerging trends, ethical considerations and the evolving relationship between human judgment and machine learning. Still being accessed today.
Of Lifelong Rights In Childhood Recordkeeping In Out-Of-Homecare (2022, Vol. 38 No. 2)
This article resonated deeply with professionals and care leavers alike, fostering a broader discourse on ethical, inclusive recordkeeping practices, participatory rights and the recognition of identity, memory, and accountability of children and adults who have experienced out-of-home care.












Celebrating 40 Years of the iQ Magazine
Most shared article | 2009, Vol. 15 No. 3







Forget the Aston Martin and the Walther PPK. Spying is all about keeping records – on people like us. In a rare insight into the recordkeeping practices of a national security and intelligence service, this article, by officers of New Zealand’s SIS, reveals how the agency administers secret dossiers, old and new, and how it addresses information requests.


The New Zealand Security Service was established on 28 November, 1956, assuming functions that at different periods since 1919 had been exercised by the New Zealand Police and the Security Intelligence Bureau.
Most of these organisations’ records*, including reports and assessments relating to groups and individuals that had been of security interest at various times, and administrative and operational files, were inherited by the new organisation.
From early 1957, records were created by the New Zealand Security Service which, on 11 September 1969, became the New Zealand Security Intelligence Service (NZSIS).
The great majority of these records are “classified”; that is, they carry a national security classification: “Restricted”, “Confidential”, “Secret”, or “Top Secret”, and are consequently subject to strict controls regarding storage, handling and release.
Like other security and intelligence organisations, the NZSIS has always faced intense public interest in the information it holds. The need to safeguard security and privacy has often meant that requests for information have been declined, as provided for in the Official Information Act 1982 (OIA) and the Privacy Act 1993. This has led to some criticism of the Service.
On the other hand, the nature of some of the information released by the Service has also been criticised, usually by those seemingly unable to view material in its correct historical context.
Historical context is important because information collection priorities have altered over the years, as the nature and perceptions of threats to security have changed. From a post 9/11 perspective, for example, the significance of the Soviet bloc – the Service’s focus for decades – is not readily apparent.
The nature of reporting and filing has also changed. Comparatively few people are or were in the past actively investigated by the NZSIS or its predecessors. In earlier times, though, it was common for all those who had come to notice, even in some minor way and even although they were not under active investigation or of security concern, to be identified and all references to them, both public and in classified reporting, to be assiduously placed on a personal file.
These old files may also contain sensitive personal details about convictions, health, and adoptions that would not be reported today.
There is a further class of records – the vetting files – which result from the statutory responsibility of the NZSIS to make enquiries about people – usually government employees – to provide advice concerning their suitability to be granted a security clearance.
Such enquiries for security clearance vetting purposes are undertaken with the formal agreement of the person concerned. The resulting vetting files are generally of no historical value, and are mostly outside the scope of this discussion.
Statutory acceSS regimeS
Many requests for access to personal information held by the Service were received following the passing of the OIA in 1982. Since 1993, the Privacy Act has provided for access to this type of information. Both security and privacy constitute grounds for
Records Held by the NZSIS
• The focus of security service recordkeeping has changed over the years as threats to national security have changed.
• FOI has been perceived at NZSIS as a way for adversaries to ‘out’ security agents.
• The Service today feels that citizens have a right to privacy, and this and security needs have to be balanced.

withholding information; the OIA and the Privacy Act also provide that in certain circumstances a person requesting information can be given notice that the agency neither confirms nor denies the existence or non-existence of information.
Initially, those seeking access to personal information were provided by the Service with a brief summary of anything that was held on file. It soon became apparent that a concerted information collection and pooling plan had been instituted by some activists who wished to identify the Service’s sources of information, including “agents”.
Agents, in security intelligence parlance, are not regular employees, but those who work under direction in target organisations to collect information secretly. This is often at personal risk, and the NZSIS is under a legal and moral obligation to protect their identity.
Confronted by these attempts to expose its agents, from November 1983, the Service generally invoked Section 10 of the OIA and declined to confirm or deny whether or not any relevant information was held.
Where appropriate, the “neither confirm nor deny” approach is still followed, but in recent years the NZSIS has often been able to be more forthcoming. In numerous cases, applicants have been given copies of reports or summaries of personal information held on them – or, as often as not, they have been informed that no information is held about them.
There has also been interest in information held about organisations and people other than the applicants. Significant amounts of information in these categories have been released under the OIA from NZSIS custody to writers – averaging twice a year since 1993. Some recipients have been family historians, and books have not always followed, but the Service’s contribution has now been acknowledged by a dozen authors.
NZSiS archiveS Policy
In 2000, at the request of the Rt Hon Helen Clark, Prime Minister and Minister in Charge of the NZSIS, the Service began to formulate an archives policy to aid the proactive and systematic public release of records in NZSIS custody.
After extensive consultation, with views canvassed from the Chief Archivist, the Chief Ombudsman and the Privacy Commissioner, and appropriate members of their respective

offices, and the Inspector-General of Intelligence and Security, the policy was launched by Helen Clark in November 2003.
A summary of the policy, which has a guideline withholding period of fifty years before transfer to Archives New Zealand, appears on the NZSIS website and is reproduced below.
In June 2005, the Minister in Charge, under the provisions of Section 22(1)(d) of the Public Records Act 2005, renewed a certificate deferring for ten years (five years in respect of records over fifty years old) the transfer of NZSIS records to Archives New Zealand. This recognises the practical issues and difficulties involved in preparing Service records for transfer.
Security aNd Privacy iSSueS
Unique security and privacy concerns arise when security intelligence records are considered for release. Among the most significant is the obligation to protect the identity of agents who provided information to the NZSIS and its predecessors. This is not dissimilar to the long-standing conventions in the news media relating to the protection of sources of information.
Another is the requirement to obtain, prior to release, permission from the originators of classified information. In practical terms the consequences of this requirement are usually more evident when considering information provided by overseas intelligence services, as discussed below. These imperatives are recognised by legislation.
There is a view that the records of overseas intelligence services are an open book. This is far from being the case. The requirements to protect the identity of agents, other sources of information, and serving and retired staff, and to maintain the secrecy of certain operations, are universally recognised.
By the nature of its work, a security intelligence organisation often collects privacy-sensitive information. The NZSIS will not generally release sensitive information unless the subject consents, or an appropriate period has passed – when such material may be made available only to the person, or the close family of the person, who is in the record – or the information is already in the public arena.
The Service regards private citizens as being entitled to expect greater privacy than public figures, and considers that time diminishes privacy concerns.
Except where security concerns impinge (as with the identity of NZSIS staff members and agents), the preference of the Service is to leave decisions about privacy matters to Archives New Zealand staff, who have greater familiarity with those issues.
declaSSificatioN
Declassification is the process whereby national security classifications, and the concomitant restrictions on storage, handling and release, are removed under appropriate authority. Declassification, a pre-requisite for public release, is usually a laborious task requiring the page-by-page examination of documents. Sensitive information must be identified, and the originator’s views obtained on the information’s suitability for release.
Where records are locally-generated, they can usually readily be assessed and a decision quickly obtained on whether to release or withhold them. However, declassification can be very time-consuming when the information is of overseas origin. Archival matters are not a priority for security intelligence services, and obtaining release permission from overseas liaison partners can be a lengthy process.
Information that cannot be made public is excised from the release copy, which is annotated to record the excision and the grounds for it. Experience has shown that care must be taken when excising sensitive material. For example, former Communist Party members have proved adept at identifying old comrades
years later despite concealment of their names; blacked-out text can be electronically reconstituted; and what has been deleted may correctly be deduced based on the context and the size of the gap.
Where the information that is releasable is not representative of Service holdings and would create a false impression, it is generally issued with a clarificatory statement. Where information cannot be released in full, for example because it is too recent, a summary may be provided.
receNt activity
In April 2007, the NZSIS recruited an experienced declassifier to prepare Service records for public release by transfer to Archives New Zealand. The first records to be transferred, Special Branch files relating to the 1951 waterfront dispute, became available to the public at Archives New Zealand on 27 March 2008.
A significant group of NZSIS papers relating to Dr William Ball Sutch, who in 1975 was tried and acquitted of charges under the Official Secrets Act 1951, was released under the OIA in May 2008.
Concurrently, the Chief Ombudsman and the Director of Security made public an annex to a report written in 1976 by the then Chief Ombudsman, Sir Guy Powles. The release of this formerly Top Secret annex is consonant with an important principle of the NZSIS’s archives policy: that the Service will deal impartially with information, regardless of whether it reflects unfavourably on the Service or shows the Service in a good light.
In fact, the methods employed by the Service in its investigation of Dr Sutch were sharply criticised by Sir Guy.
Not unexpectedly, the recent releases have prompted many requests for access to personal information held by the NZSIS.

Public views are being canvassed by the Service to determine what records are of most interest, and individuals who have requested information and are the subject of early personal files are being invited to give their views on the disposal of the records concerning them. To date, they have invariably wished to see them preserved and eventually transferred to Archives New Zealand.
The NZSIS is indebted to Archives New Zealand for undertaking a series of appraisals of records held by the Service. Vetting records were appraised in 2003, subject files earlier this year, and personal files are now being assessed.
The outcome is a set of disposal schedules identifying significant categories for preservation and enabling the destruction of other records. Very few vetting files will be kept, but it is envisaged that many other records will be preserved.
lookiNg ahead
A number of files relating to the Second World War and early Cold War period have been identified as being of high public interest. After any security or privacy issues have been dealt with, these will be the next records to be transferred to Archives New Zealand.
As the Service’s small declassification team must give priority to Privacy Act and OIA requests, it is not possible to give a precise timetable for the transfer of these files. ‡ The Service remains nonetheless committed to the progressive declassification and public release, through transfer to Archives New Zealand, of records of historical interest that are no longer of administrative value.

The New Zealand Security Intelligence Service (NZSIS) is subject to New Zealand’s archives legislation and will maintain and preserve as long as required to proper standards all records of security and historic value in its custody.
These are mainly in paper or electronic form but also include photographic, audio and video material. Many records will eventually become available for public access, but there will be sufficiently compelling reasons to withhold some from public access indefinitely, subject to periodic review.
Where possible, records appraised as having long-term value will be transferred to Archives New Zealand (ANZ). The NZSIS will deal impartially with information, regardless of whether it reflects unfavourably on the Service or shows the Service in a good light.
The archives policy does not provide guidance on responding to requests made under the Official Information Act 1982 and the Privacy Act 1993. Each request made under the statutory access regimes will be assessed on an individual basis and the Service will act in the spirit of these statutes taking into account security and privacy considerations.
criteria for PreServatioN
Records in the following categories will be preserved:
• History of the Service including structure, objectives and important papers relating to administration;
• Major intelligence cases;
• Significant individuals;
• Important issues of the day;
• Advice to ministers;
• Relations with Parliamentary, judicial and quasi-judicial authorities;
• Relations with other agencies;
• Period pieces (reports which capture the essence of the period concerned);
• Representative 1% cross-section of personal and subject files;
• All indices, hard copy and electronic;
• Vetting records of historically significant people;
• Precedent-setting vettings;
• Vettings reviewed at request of candidates;
• Service staff; and
• Any other records approved for preservation by the Chief Archivist.
criteria for disposal (ie, Preservation or destruction)
– Disposal must comply with legislative requirements. There will be no destruction of records without a current authority approved by the Chief Archivist.
handling Procedures: disposal
– Significant files will be retained intact.
– Any original papers meeting preservation criteria will be retained from files scheduled for destruction.
– All vetting files outside preservation criteria will be destroyed in toto
Withholding Periods
– Security concerns will always remain paramount.
– Privacy issues will also be taken into account.
– These considerations may preclude release at any time.
– Where there is a high level of public interest, the withholding period may be reduced.
– Access decisions, especially for older records, will be subject to periodic review.
Withheld Shorter-term
– Subject files: release 50 years after creation.
– Personal files: release 120 years after the birth of the subject or 50 years after the death of the subject, whichever is later.



To include:
• Some files on target organisations and personalities and Service administration;
• Some information relating to technical intercept operations; and
• Material from overseas liaison services where the originator’s permission to release it has been obtained.
Withheld longer-term
– Information on NZSIS staff members in general: release 100 years after death, unless the member or next-of-kin gives approval for prior disclosure.
– Note: generally limited to name, dates of service and outline of responsibilities; privacy-sensitive material not releasable.
– Some files on target personalities: release 100 years after death.
– Information on technical operations: some may be released 100 years after creation.
Withheld indefinitely
– Information disclosing the existence of an interception warrant.
– Material that could identify sensitive sources of information or agents.
– Information the release of which would constitute a threat to security, be a breach of confidence, or could endanger a person.
– Liaison service material, until the originator gives permission for its release.
– Some material relating to sensitive operational techniques or targetting.
custody
– Classified information will remain in the custody of the Service.
– Declassified material, that has been appraised as having long-term value, will generally be transferred to ANZ.
– Supervised access to selected archives at NZSIS Headquarters may be negotiated on a case-by-case basis.
guidelines for release
Security Significance
Declassification is essential before public release. Information will not be released which may reveal:
• the existence of an interception warrant;
• sources of information or the identity of agents;
‡ NZSiS archiveS releaSe Programme 2008 – 2009
• Anti-Conscription Organisations
• New Zealand Peace Council
• Communist Party of New Zealand
• Society for Closer Relations with Russia
• other assistance available to the Service;
• operational techniques still used by the Service;
• current or planned Service operations; or
• liaison service information where the originator has not given permission to release it.
Confidentiality
Confidentiality obligations to liaison services and other organisations and individuals must be observed.
Privacy
Private citizens are entitled to expect greater privacy than public figures, and sensitive information will not generally be released unless the subject consents, the information is already in the public arena, or an appropriate period has passed.
The Service will be guided by relevant legislation and practice. Time will diminish privacy concerns.
handling Procedures: release Security is paramount.

All material to be released must be:
• expurgated of any references that might compromise security;
• formally declassified; and
• annotated to indicate where deletions have been made and why.
Original records must:
• be kept intact;
• record any release of the document; and
• identify any deletions or excisions made on the version released.
Material being declassified should be made available to all except that some personal information may be releasable only to the person, or the close family of the person, who is in record.
The Service will endeavour to process material as requested by the public, and, as resources permit, other records judged to be of the most interest to the public.
This article was written by New Zealand Security & Intelligence Service archives staff. It is an offence under New Zealand law to name any member of the NZSIS, or their associates, other than the Director. The article was approved for publication by the Director, Dr Warren Tucker.
• Further information about the NZSIS is available on the Service website: www.nzsis@govt.nz This article first appeared in the 2008 edition of Archifacts, the occasional journal of the Archives & Records Association of New Zealand, (ARANZ), and is published by iQ with permission.

BY BARBARA REED & SUE MCKEMMISH
The Board of Directors have endorsed the Charter of Lifelong Rights in Childhood Recordkeeping in Outof-Home Care*. In this, RIMPA are aligned with a range of professional recordkeeping bodies and regulators, with Commissioners of Children and Young People, along with service provider organisations in the sector.
The Charter represents an ambitious agenda to put recordkeeping into a prominent position as one of the interventions needed to support children’s rights, with a particular focus on children in Out-of-Home Care. The lifelong role of recordkeeping as a means of empowering people who are experiencing, or who have experienced, Out-of-Home Care in Australia has been brought to professional attention again and again. While recordkeeping professionals have been responsive through advocacy, submissions and engagement with affected communities, the role of recordkeeping has, to date, failed to become a priority in how organisations respond. Yet we know through countless inquiries, investigations, and reports at both state and national level, that records are essential for an individual’s identity formation and memory validation, ability to participate and take action (agency), and to hold organisations to account.
This work has been done in collaboration with those having lived experience in Out-of-Home Care. It is firmly embedded in broader human rights.
The landmark Royal Commission into Institutional Responses to Child Sexual Abuse recognised the importance of recordkeeping of the past, present and future in Volume 8 of its report. Post Royal Commission, recordkeeping has been subsumed into child safe principles, diminishing organisational attention on the critical role of recordkeeping. The Charter is a strategic intervention to elevate the importance of recordkeeping in this context.
In Australia, almost 50,000 children, nearly one in every 100 are in care. And the figures are even more confronting for Indigenous children, who are more than ten times more likely to be in care, relative to their numbers in the broader population. The strategies for child protection are in flux, with ample evidence of failing systems. As a state-based responsibility, individual jurisdictions have recognised the significant problems with the systems, but this is complicated by the embedding of approaches supporting a continuation of an essentially colonial mindset.
The Charter takes a quite different, and very strategic approach. This work has been done in collaboration with those having lived experience in Outof-Home Care. It is firmly embedded in broader human rights. By taking this approach, the Charter seeks to transcend the inevitable stumbling blocks of specific jurisdictional legislation. Rather it positions the child as the centre point, as an individual with inalienable human rights.
To better achieve these rights, the Charter links records - what they say, what they mean and the control of records - to human rights. Based within the framing rights of broad human rights (Participation, Memory, Identity and Accountability), the Charter is informed by key principles of Wellbeing, Cultural Safety and Justice. Within that recordkeeping-specific rights are articulated specifically within our professional sphere of
influence. These recordkeeping rights are grouped into three major categories – participatory and records creation rights, rights in disclosure, access and records expertise, and rights to privacy and safe recordkeeping.
The challenges for recordkeeping professionals committed to observing and implementing the recordkeeping rights are very significant. Each of the three major groups of recordkeeping rights pushes at existing recordkeeping practice. They challenge us to do better, and to do things differently. As such, the Charter is a very ambitious document, positioned as aspirational because it is clear that implementing the rights will be on the professional agenda for many years to come. The impact on people’s lives as we strive to position recordkeeping practice as a tool for change will be profound.
Understanding the significant changes implied in achieving the Charter, the project has also created a range of practical tools based firmly in the reality of organisational current practices. The range of Best Practice Guidelines and Implementation Advice outlines the issues being addressed and discuss practical, achievable steps to commencing the realisation of the Charter Rights. These Implementation Advice themselves challenge the notion of organisation-centric recordkeeping. They address issues that are known to be thorny in implementation and seek to create small steps along a transformational path.
The Charter and all its associated guidance and advice are freely available on the Monash website (monash.edu/it/clrc). The broad range of organisational endorsements positions the Charter as a strategic and aspirational tool with practical guidance to assist in small steps towards implementation. In blue sky thinking, this rights-based approach, clearly linked to human rights, raises tantalising opportunities to rethink organisational practice for all records relating to people.
At this stage, we are working with Indigenous colleagues on a further project to tailor the implementation advice to specifically address the unique needs of Indigenous children and Indigenous service providers.
Emerita Professor Sue McKemmish &
Barbara Reed
Digital Equity and Digital Transformation
Faculty of Information Technology, Monash University
Professor Emerita Sue McKemmish has an international reputation as a celebrated academic, a strong social good advocate, a leader in Records Continuum theorising and a force in recordkeeping and information management. Her recent research focus has been on community-centred, participatory recordkeeping and archiving research relating to rights in records, complemented by ethics of care, in response to advocacy by those with lived experience of Out of Home Care, and First Nations peoples in Australia. Developing inclusive, reflexive research design and practice in partnership with communities has been a critical to part of this research.

Barbara Reed has worked with a range of government, non-government, private and nonprofit organisations, in Australia and internationally. She has previously worked on issues empowering access to records for the Care Leaver Community and the Stolen Generation. Much of her consulting work has been focused on developing recordkeeping practices and competencies, transforming recordkeeping into digital practice, and working with a range of stakeholders to create strategic interventions through standards and best practice guidelines.
* See www.monash.edu/it/clrc.
Thomas Kaufhold Life MRIM, OWL, Editorial Committee
It is with some sadness to hear that the iQ is no longer a viable publication in an environment where people prefer short servings of information in a fast-moving world. However, it is completely understandable that a decision had to be made to close the iQ given the cost of producing it, low readership and reducing revenue to keep it going. It is with some fondness I look back on the humble beginnings of the iQ with simple artwork and format and an avenue where burgeoning authors started their publishing ambitions. There was nothing like it around that tackled the issues and hot topics of the day in managing records.
The iQ evolved to be a very sophisticated magazine which experimented with different formats, content and graphics, and it looked good on the coffee table in printed form. Articles published ranged from newsy/fun bits of information and serious discussions on important topics. I am certain that many people working in the information management industry would have found the information proved useful in their working careers. We can be comforted in the knowledge that the iQ will provide an ongoing rich source of information going back some 40 years waiting for scholars and interested people to dip into. You will find interesting facts on the development of RMAA/RIMPA Global as an organisation, who were involved (movers and shakers) over the years and how the information/ records industry evolved. You will see that much has changed on the technology front but not surprisingly some core issues discussed have not changed.
My thanks and appreciation to the authors, publishers and editors who have put in countless hours over the years.
Let’s Celebrate a fond farewell to the iQ

Peter Smith Life FRIM, OWL
I have always looked forward to receiving the iQ and enjoyed not only the content but also the sensation of its physical presence, and copies have adorned my bookshelves for years.
There is, of course, the temptation to cling to the past and the old ways, however, having been involved with the Association since the 1950’s, I am well aware of the major changes that have taken place throughout the years and the need to embrace them and to move forward and meet new challenges.
So, whilst I am sad to see the demise of the printed copy of the iQ, I also recognise the inevitability of progress, and that time and technology have overtaken the old methods of communication. The future is in the hands of newer, younger and forward-looking members to leave their mark.
Philip Taylor Life MRIM, OWL, First InfoRMAA Co-Editor, Editorial Committee
From its inception in 1984 as it was known, Informaa Quarterly and more recently iQ the journal set out to provide an avenue for the advancement of the profession through the writings of those that know the profession best. Looking back in time our collective efforts seem to be amateurish with articles on basic information management. However, viewed over time iQ was also a window into how the profession developed.
A browse through the years of the journal reveals a gradual sophistication in what was been written. The advent of the computerised information system changed the profession markedly and hence the writings changed from the basic to a more comprehensive view of information management.
iQ provided a means by which members could understand the meaning of the world they work in. There have been many people involved with iQ over the years. Harry Haxton, the then Federal President believed that having a journal of professional writings would enhance the profession and so right was he.
Over the years editors have come and gone each contributing to the journal in their own way. iQ would not exist without the contributions of those that contribute to the journal. Those that devoted the time to writing can be proud of the work that they have made to the information management industry. Collectively, the articles provide an insight into the development of the industry.
On a personal note, I have been involved with iQ from its inception in one way or another as a contributing editor, author and Editorial Committee member.
It has been a great honour to be associated with the journal.
Helen Onopko Life ARIM, Editor – South Australia
Congratulations is in order for RIMPA to have been able to produce iQ and its predecessors for so many decades. The collection tells a rich story, difficult for other professional organisations to rival. It will forever be a valuable component of Australia’s business history, and through it, the origins of Australia’s global leadership in recordkeeping writ large. Congratulations to previous contributors and editors for such professional outcomes with iQ – it’s a high bar with which to close the chapter. Recordkeepers have always been alert to needs for change, and putting iQ to rest is part-sadness, largepart change management. And we’re good at that.


Linda Shave Life FRIM
Author
It is a sad time in history with the announcement on the 15th April 2025 that the Records and Information Management Professionals Australasia (RIMPA) Global Board have made the decision to retire our iQ Journal magazine. This professional magazine has served our Records and Information Management Industry since 1984. The iQ journal magazine has kept us informed, inspired and provided us with a wealth of knowledge, skills and intellect. The iQ journal magazine has been a valuable resource for students around the world.
I myself have been a regular contributor to the iQ magazine since August 2013. My first article was The changing landscape of information and records management and my last article in November 2024 was on the topic of Innovative Technologies Reshaping Information Management. Below is a list of the 44 Articles that I have written for the RIMPA Global iQ magazine from 2013-2024.
As a researcher, author and advocate for continuous learning it has been a pleasure to have been able to contribute to the iQ journal magazine from 2013 until 2024. I hope that my articles have inspired readers not only here in Australia but worldwide.

"No one knows entirely what the future holds. We can however be certain that it will be beyond anything we can imagine today. "
The Roman god Janus was visualised as having two faces: one looking towards the past, the other looking towards the future. The end of the iQ journal magazine takes a backward look at how the records and information management profession got to where it is, the events and influences that have shaped it. Then like Janus, we now look forward to the next chapter, where will the records and information management industry be heading.
In ending, I have taken a quote from one of my many eBooks ‘Digital Content Services Intelligent Information Management for the Fourth Industrial Revolution’. National Library of Australia.
• "No one knows entirely what the future holds. We can however be certain that it will be beyond anything we can imagine today." Linda Shave, June 2017
"The end of the iQ magazine takes a backward look at how the records and information management profession got to where it is, and the events and influences that have shaped it."

Jo Kane Editor
From the moment I stepped into the role of iQ Magazine Editor in 2020, I knew I was taking on more than just a publication — I was taking on a legacy. With its roots stretching back to RIMPA’s inaugural 1984 conference in Coolangatta, iQ has long been a cornerstone of the records and information management profession. We dug into everything from metadata, digital preservation and retention schedules to AI, information governance, compliance, data ethics and leadership. But more than that, we showcased the real people doing the work — our members, their wins, their insights and the realities of managing information in an ever-changing digital world.
A big thanks to the contributors who backed every issue — Linda Shave, Keith Darlington, Craig Grimestad, and so many more — along with the vendors and readers who kept the momentum going.
It’s the end of an era for iQ and while it’s sad to see the magazine retire after so many years, the conversations it sparked and the voices it amplified won’t stop here.
The profession is evolving — and its story will continue to be told in new and powerful ways.
I’m proud to have helped bring iQ to life.































"Our profession has never stood still—and neither has iQ. These covers reflect a living, evolving story shaped by the people, ideas, and challenges that define us. What began as a bold idea grew into a voice for a profession. Thank you to all contributors and sponsors for bringing it to life."
- Judith Ellis, First InfoRMAA Quarterly Co-Editor









































































































































































































































"It has been an honour turning these final pages with you."


As we close this final issue of IQ, we do so with deep gratitude and great pride. For every article submitted, every edition read, and every conversation sparked— we thank you.

To every author whose wisdom, research and passion have graced our pages, thank you!
Your contributions have shaped this publication alongside our industry, inspiring readers, sparking conversations and setting new benchmarks for excellence. Each article represented countless hours of research, reflection and writing --generously shared with your professional community. Your words and the impact they have made will continue to resonate and inspire future generations in our field.
iQ EDITORS
Virginia Bolger
Pam Camden
Shirley Cowcher
Stephen Dando-Collins
Wendy Duggan
Anthony Eccleston
Kenneth Elliot
Judith Ellis
Karen Farrell
Helen Francis
Sue Hill
Marita Hoo
John Hough
Barry Joyce
Joanne Kane
Janet Knight
Dale Kreibig
Richard Leggo
Margaret Medcalf
Heather Miller
Malcolm Nairn
Bill Parr
Nigel Patterson
Ken Ridley
Jim Shepherd
Geoff Smith
Susanne Smith
Mike Steemson
Murry Stewart
Peta Sweeney
Bill Taylor
Philip Taylor
Ross Thompson
Craig Webb
Bill Williams
We remain deeply grateful for your significant role in this journey and look forward to continuing our shared commitment to professional growth and excellence through new channels and collaborations. The journal may be coming to an end, but the work continues. The conversations will carry forward—in conference rooms, online forums, classrooms and across the desks of the next generation of information professionals. If you’ve ever learned something here, questioned something here or felt seen here— then this journal has done its job.
So here’s to every draft, every footnote, every reader.
Thank you for turning the page with us, one issue at a time.
iQ EDITORIAL COMMITTEE
Julie Apps
John Behrens
Roger Buhlert
Stephanie Ciempka
Judith Ellis
Helen Francis
Russell Fraser
Christine Holmes
Ray Holswich
Jo Kane
Thomas Kaufold
Kristen Keley
Margaret Kenna
Tim Newbegin
Matt O’Mara
Margaret Pember
David Pryde
Joy Siller
George Smith
Mike Steemson
Philip Taylor
Ross Thompson
Judy Watts
Dennis Wheeler
Bill Williams


Thank you for memories... and the momentum celebrating 40 years of voices, vision and vital change.