
Step 1 to NIS2 compliance
A comprehensive guide to get you started with MFA
1. Introduction 5 2. What’s new in NIS2? 6 2.1 Scope expansion ....................................................................................... 6 2.2 Minimum Cybersecurity Requirements 7 2.3 Sanctions if you do not comply 7 3. Is your organization affected? 8 4. The role of Multi-factor Authentication in NIS2 10 4.1 What is multi-factor authentication (MFA)? 10 4.2 The significance of MFA 10 5. Getting started with multi-factor authentication 12 5.1 Key considerations for evaluating the right solution 12 5.2 How can Nexus help? 13 5.2.1 Versatile and risk-appropriate authentication............................. 14 5.2.2 User self-service for reduced administrative overhead 14 5.2.3 Extensible use-cases 14 5.2.4 NIS2 beyond MFA.......................................................................... 15 6. Summary 16 References 17 Tables and figures 17 About Nexus 17 3
Content
1. Introduction
A significant step toward enhancing the cybersecurity and achieving zero trust for critical infrastructure and digital service providers is the implementation of the revised European Network and Information Security Directive (NIS), known as NIS2. Given the rapidly evolving cybersecurity threats, NIS2 strengthens defenses in the EU.
The NIS2 Directive enhances security mandates and introduces rigorous supervisory measures and enforcement requirements. The updated directive aims to protect critical industries against supply chain vulnerabilities, ransomware attacks, and other cyber threats.
NIS2 distinguishes between essential and important organizations based on the criticality of their services to society and the economy. This differentiation helps tailor compliance requirements to the specific risk profiles and impact levels of these organizations.
All 27 EU member states must integrate the NIS2 Directive into their national laws by October 2024. Non-compliance could result in fines of up to 10 million euros or 2% of annual turnover, with top executives potentially held personally liable.
This guide introduces NIS2 and gives you the insights and actions necessary to embark on your compliance journey. Emphasizing the pivotal role of multifactor authentication (MFA), the guide equips you with the necessary knowledge to fortify your organization against cybersecurity threats in alignment with NIS2 requirements.
5
2.What’s new in NIS2?
NIS2 has introduced considerable updates from its predecessor. In this section we explore these updates.
2.1 Scope expansion
The scope broadens significantly, encompassing a wider range of industries. For example, in Germany, the impact of NIS2 is substantial, with the number of affected entities expected to surge from 1,800 to 29,000. This expansion includes smaller companies and newer industries like Waste Management, ICT, Public, Space, Chemical, and Food. Furthermore, industries included under NIS, notably Health and Digital, also see expanded coverage.
New Industries added under NIS2 scope expansion
OESs (Operators of Essential Services)
Industries originally under the scope of NIS and retained under NIS2 Chemical
DSPs (Digital Service Providers)
Financial
Health
Drinking
Digital
Postal
Manufacturing, Production, and Distribution Food Production, Processing, and Distribution
6 Classification Important Essential Important Type of Organization Industries Waste Water Management ICT Service Management (B2B) Public Administration Space Energy Transport Banking
Table 1.
Market Infrastructures
Water
Infrastructure
and Courier Services
Management
Waste
Manufacturing Research Digital Providers
2.2 Minimum Cybersecurity Requirements
NIS2 introduces new cybersecurity requirements, offering clear guidance to entities across the EU on the measures they must implement to manage risks effectively.
The directive emphasizes that all entities must protect the network, information systems, and the physical environment of those systems. It also promotes adoption of zero trust security approach to promote overall cyber resilience.
The security measures must, at the minimum, include the following:
• the use of multi-factor authentication or continuous authentication solutions, secured voice, video, and text communications, and secured emergency communication systems within the entity, where appropriate
• human resources security, access control policies, and asset management;
• supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers;
• security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure;
• basic cyber hygiene practices and cybersecurity training;
• policies and procedures regarding the use of cryptography and, where appropriate, encryption;
• policies on risk analysis and information system security;
• incident handling;
• business continuity, such as backup management, disaster recovery, and crisis management;
• policies and procedures to assess the effectiveness of cybersecurity risk-management measures;
Source: https://www.nis-2-directive.com/NIS_2_Directive_Article_21.html
2.3 Sanctions if you do not comply
Sanctions for non-compliance with NIS2 can, though, vary by member state, as each EU country is responsible for implementing the directive into its national laws. Sanctions may include financial penalties, administrative fines, and other measures determined by the national regulatory authorities.
Non-compliance could result in fines of up to 10 million euros or 2% of the annual turnover of the company. The severity of sanctions may depend on the nature and extent of the non-compliance. One significant difference from NIS1 is that top executives may be held personally liable for non-compliance.
For the most accurate and up-to-date information on NIS2 and its associated sanctions, it is advisable to refer to the specific national legislation and regulatory authorities in the relevant EU member states or consult legal professionals familiar with cybersecurity regulations in the region.
For comprehensive guidance in, for example, Germany, consult BSI; in France, ANSSI provides detailed information.
The Swedish Civil Contingencies Agency (MSB) offers a valuable summary in their ”Policy Overview - Initiatives at EU Level Affecting Sweden’s Information and Cybersecurity Work.”
7
3. Is your organization affected?
Let us explore whether your organization is affected by the NIS2 directive and how this can be determined.
Your initial focus should not be on whether your organization is important or essential, as many may think. Instead, determine whether your entity is part of the sectors and services affected – the qualification question comes later.
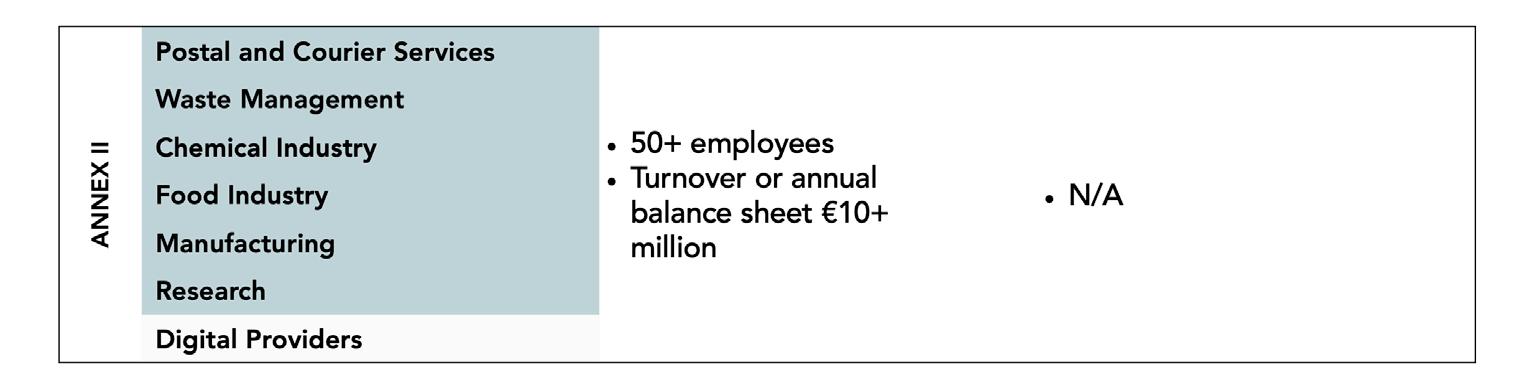
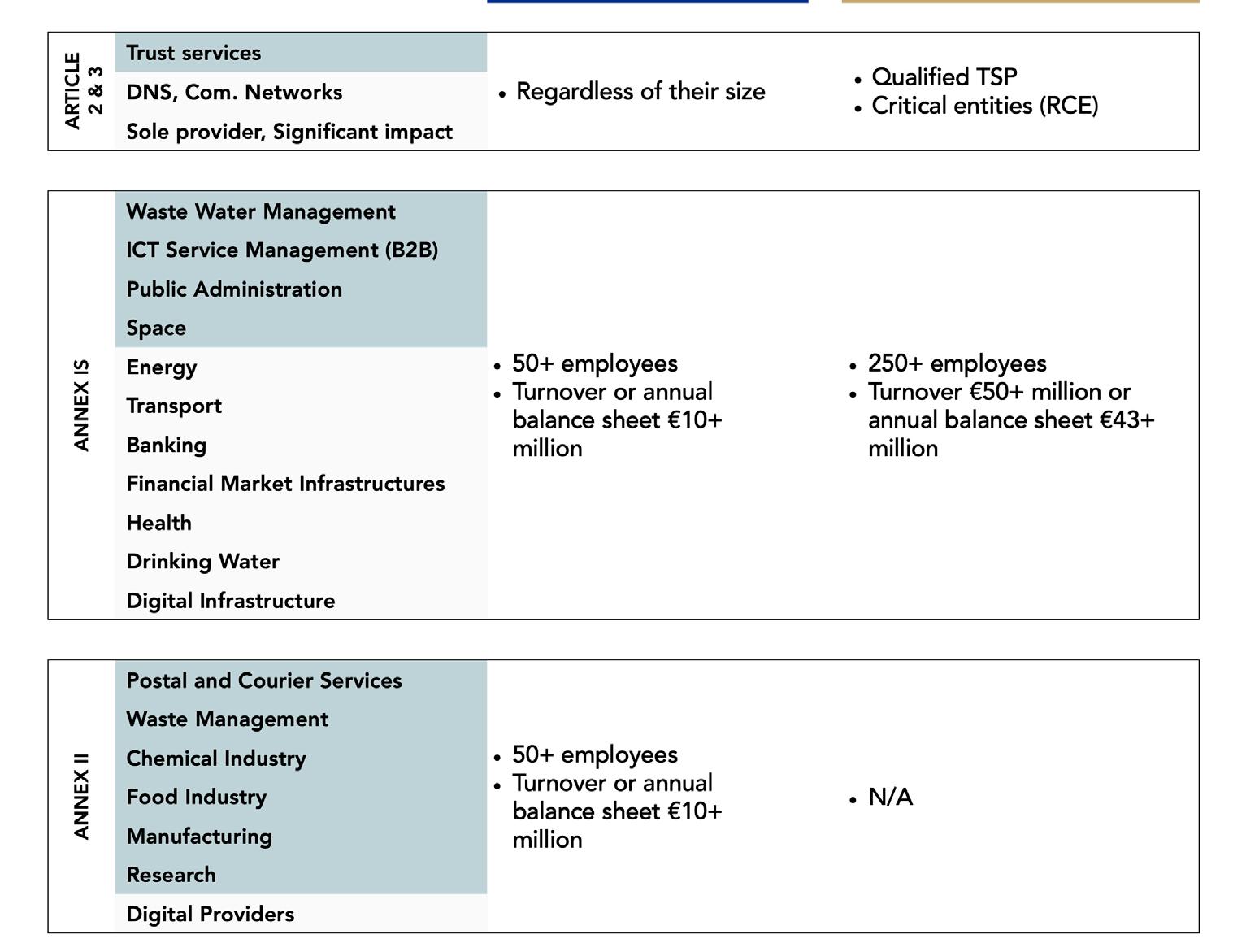
STEP 1: To ascertain if you are affected, check to see if your entity comes under the following parts:
• Article 2,
• Annex I or,
• Annex II.
For example, if you are a Trust Service Provider, your company is part of Article 2. If you are an electricity provider, please see Annex I.
STEP 2: Next, assess whether your organization falls under Important or Essential entities, depending on your sector and size.
• For some specific entities mentioned in Article 3 §1, categorization as Essential is not determined by size but by criticality. For instance, qualified Trust Service Providers and providers of public electronic communications networks are considered essential, regardless of their size.
• For those sectors listed in Annex 1, the distinction between Important and Essential is based on whether the organization has more than 250 employees or an annual turnover exceeding 50 million euros
• If your business operates in one of the sectors outlined in Annex 2, it is considered important if employee count is above 50 or turnover is more than 10 million euros Table 2.

8
The key difference in being classified as Important or Essential lies in each entity’s supervision. If your entity is categorized as Important, it will be audited under an ex-post supervisory authority, triggered by evidence of non-compliance, such as a security breach or alert. In contrast, entities deemed essential face audits under an ad-hoc regime, allowing supervisory authorities to conduct on-site inspections without requiring specific evidence of non-compliance.
As a result, Important entities share the same cybersecurity obligations as Essential entities but benefit from a somewhat less rigorous supervisory authority.

A small company in the Transport sector initially had a turnover of €5 million and 10 employees. It was not subject to NIS2 regulations.
A year later, the company expanded, reaching a turnover of €20 million and had 40 employees. The company would then be categorized as Important under NIS2. While it would have to adhere to all NIS2 obligations, it would not need to be concerned about an unexpected audit from the supervisory authority.
Then, two years later, the company experienced substantial growth, achieving a turnover of €60 million and employing 80 staff members. It would then be classified as essential. Although its obligations under NIS2 would remain unchanged, it should anticipate an on-site audit from the supervisory authority at any time.
What if your entity is not affected?
Even if your organization is not directly impacted by NIS2, prioritizing cybersecurity should be on every organization’s agenda. The dynamic cyber threat landscape poses risks beyond regulatory classifications. In our interconnected digital world, all entities contribute to the overall resilience of critical functions.
Adopting NIS2-aligned cybersecurity measures is forward-thinking. It safeguards against current threats, strengthens competitiveness, and positions your organization strategically in the evolving cybersecurity and regulatory landscapes.
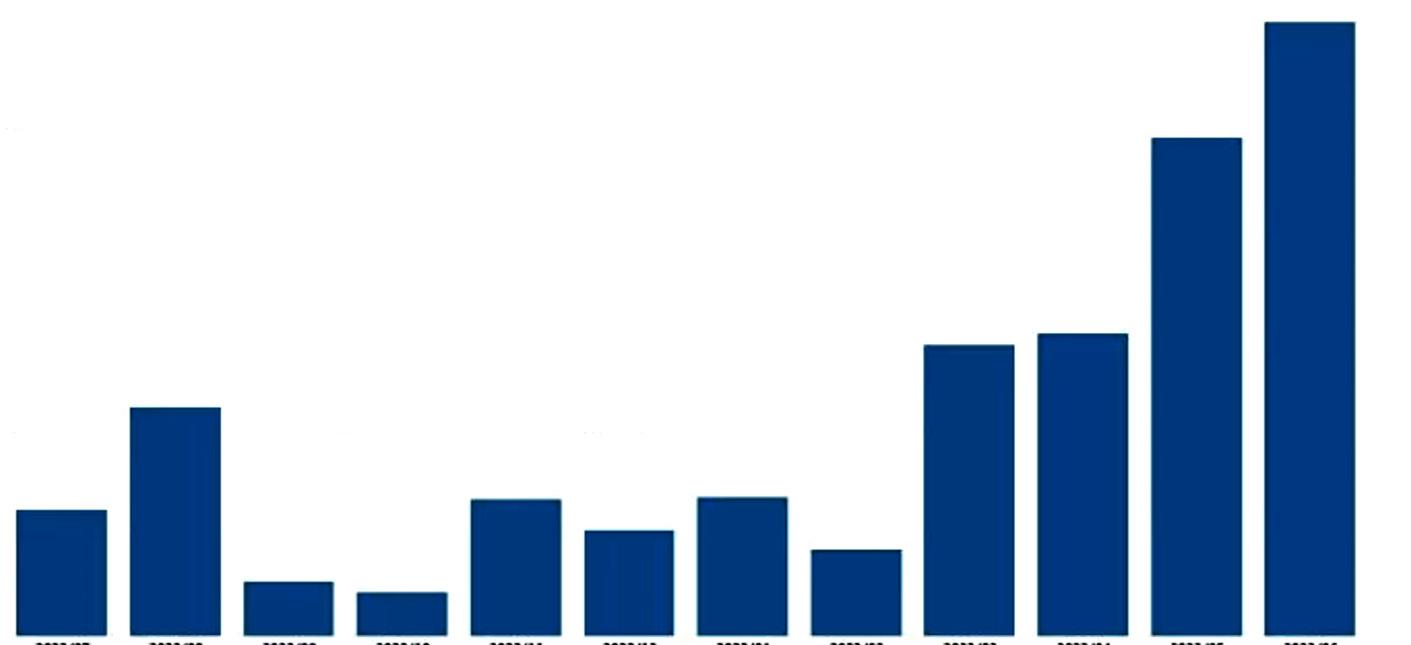
Figure 2. Timeline of EU events
(count of number of observed incidents per month)
600 300 500 200 400 100 0 2022/07 2022/11 2023/03 2022/09 2023/01 2023/05 2022/08 2022/12 2023/04 2022/10 2023/02 2023/06
Figure 1.
9
4. The role of Multi-factor Authentication in NIS2
In the earlier section, Minimum Cybersecurity Requirements, we explored the extensive range of cybersecurity directives outlined in Article 21. Many of these requirements are effectively addressed through the implementation of Multi-Factor Authentication (MFA). Apart from being a part of minimum baseline requirements itself, MFA plays a pivotal role in enforcing various cybersecurity requisites laid down in Article 21, such as:
• Human resources security
• Supply chain security
• Security in network and information systems
• Basic cyber hygiene practices
4.1 What is multi-factor authentication (MFA)?
MFA involves authenticating users with two or more factors. Conventional username-password authentication represents the factor of knowledge or ”something you know” which by itself is weak and prone to compromise.

MFA introduces additional factors such as possession or ”something you have” (e.g., a token, smart card, smartphone) and biometrics or ”something you are” (fingerprint, facial recognition). These factors are paired in a combination such that authenticating without the authorized user’s consent becomes impossible.
Some typical examples of using MFA for strong authentication include smart cards with a PIN (something you have + something you know) or smartphones with facial recognition (something you have + something you are).
4.2 The significance of MFA
Introducing Multi-Factor Authentication (MFA) to your organization can yield numerous advantages beyond mere compliance requirements. By incorporating MFA into your cybersecurity strategy, you not only fortify your defenses against a myriad of threats but also unlock a range of benefits.
1. Enhanced Security: MFA provides an additional layer of security beyond traditional password-based authentication, significantly reducing the risk of unauthorized access. By requiring multiple factors for authentication, MFA makes it exponentially more challenging for malicious actors to gain access to sensitive systems and data, thus enhancing overall security.
10
Figure 3.
2. Mitigation of Credential-Based Attacks: One of the most common cybersecurity threats organizations faces is credential-based attacks, such as phishing and credential stuffing. MFA helps mitigate these threats by adding an extra barrier, even if attackers manage to obtain login credentials through illicit means.
3. Protection of Remote Access: With the rise of remote work and distributed teams, securing remote access to corporate resources has become critical. MFA adds an extra layer of security to remote access solutions, such as VPNs or cloud-based applications, reducing the risk of unauthorized access from external networks.
4. Protection of Human Resources and Assets: MFA contributes to human resources security and asset management, which are essential aspects of cybersecurity governance. By ensuring that only authorized individuals can access sensitive resources, organizations can better protect their valuable assets and intellectual property from unauthorized access or misuse.
5. Improved Supply Chain Security: MFA also plays a crucial role in enhancing supply chain security, as it helps safeguard communication channels and access to shared resources among partners and service providers. By requiring multi-factor authentication for interactions with external entities, organizations can mitigate the risk of supply chain attacks and unauthorized access through compromised accounts.
6. Promotion of Cyber Hygiene Practices: Implementing MFA encourages good cyber hygiene practices among employees and stakeholders. By incorporating additional authentication factors, organizations reinforce the importance of security awareness and responsible access management, fostering a culture of cybersecurity throughout the organization.
7. Regulatory Compliance: While NIS2 mandates MFA for certain entities, other regulations and industry standards also require or recommend its implementation. Compliance with regulations such as GDPR, eIDAS, PCI DSS, PSD2, CER, CRA, HIPAA, and CCPA, often involves the use of MFA to protect sensitive data and ensure regulatory compliance.
8. Cost-Effective Security: While investing in security measures is essential, the cost-effectiveness of these measures is also a consideration. MFA provides a cost-effective way to significantly enhance security, especially compared to the potential financial and reputational damage caused by data breaches or cyberattacks.
9. Alignment with Zero Trust Principles: MFA aligns with the principles of Zero Trust security architecture, which advocates for continuous verification of user identities and devices, regardless of their location or network context. Zero Trust is also a requirement laid down as a part of the NIS2 directive. By adopting MFA as part of a Zero Trust strategy, organizations can establish a more resilient security perimeter and mitigate the risk of insider threats and lateral movement by malicious actors.
11
5. Getting started with multi-factor authentication
Introducing MFA into your organization requires a thoughtful approach to ensure successful adoption and integration. By following a structured process, you can streamline the implementation of MFA and maximize its benefits while minimizing disruption to your operations and user experience.
Below, we outline a series of steps to guide you through the process of getting started with MFA adoption.
ASSESS NEEDS
• Identify the systems, applications, and sensitive data that require enhanced protection
• Consider factors such as user access patterns, remote work scenarios, and regulatory compliance obligations
DEPLOY & MONITOR
• Ensure all systems, applications, and user accounts are properly configured
• Monitor deployment process closely to identify any issues and address them promptly
SELECT THE MFA SOLUTION
• Research solutions based on various factors
• Request demos, conduct Proof of Concept (PoCs), gather feedback
PROVIDE TRAINING & SUPPORT
• Educate users about MFA and address common questions
• Provide user-friendly documentation, tutorials, and troubleshooting guides
START WITH A PILOT
• Consider phased rollouts before full deployment
• Identify any challenges early on, use feedback for improvement
EVALUATE & MONITOR
• Continuously evaluate the effectiveness of your MFA implementation and gather feedback from users, administrators, and stakeholders
• Monitor key metrics such as authentication success rates, user satisfaction levels, security incidents, and compliance status
By following these steps, organizations can effectively kickstart their MFA adoption journey and enhance their security posture while minimizing disruption to user workflows.
5.1 Key considerations for evaluating the right solution
When selecting a Multi-Factor Authentication (MFA) solution for your organization, it is crucial to consider several key factors to ensure that the chosen solution aligns with your security needs, user requirements, and organizational objectives. Here are the key considerations:
1. User Experience: Consider the user experience implications of the MFA solution. Choose a solution that strikes a balance between security and usability, offering seamless and intuitive authentication processes for users. Complex or cumbersome authentication methods may lead to user frustration and resistance to security measures. Avoid the use of additional hardware; instead, leverage options such as virtual smart cards and mobile apps. Using devices and technologies users are already familiar with significantly reduces friction.
1 2 3
4 5 6
12
Table 3.
2. Integration Compatibility: Evaluate the compatibility of the MFA solution with your existing IT infrastructure, applications, and systems. Ensure that the solution can integrate smoothly with your authentication systems, identity management platforms, and cloud services to minimize implementation challenges and maximize interoperability.
3. Adaptive, risk-based authentication: MFA solutions with risk-based authentication, including Single Sign-On (SSO) guarantee strong authentication. This ensures a dynamic security approach that adapts to contextual risk factors, enhancing user authentication while providing a seamless and secure experience across diverse access points.
4. Scalability and Flexibility: Choose an MFA solution that can scale to accommodate your organization’s growth and evolving security requirements. Consider factors such as the ability to support a growing user base, adapt to changing technology trends, and integrate with new applications and services as needed.
5. Administration and Management: Evaluate the administrative capabilities and management features of the MFA solution. Choose a solution that offers centralized management tools for easy deployment, configuration, and monitoring of MFA across your organization. Look for automation features that streamline administrative tasks and reduce manual overhead.
6. Automation: Look for automation features for tasks such as user provisioning and de-provisioning, policy enforcement, and reporting to streamline administrative tasks and reduce manual overhead. By automating routine tasks, organizations can improve operational efficiency, reduce human error, and ensure consistent enforcement of security policies across the enterprise.
7. Vendor Reputation and Support: Research the reputation and track record of the MFA solution vendor. Look for reviews, testimonials, and references from other organizations similar to yours, that have implemented the solution. Evaluate the vendor’s level of customer support, responsiveness to issues, and commitment to ongoing product development and improvement.
By carefully considering these key factors, organizations can select an MFA solution that meets their security requirements, user needs, and operational objectives, enabling them to enhance authentication security while maintaining a positive user experience.
5.2 How can Nexus help?
Multifactor authentication is imperative for high security, but high security should not mean inconvenience for the user, rather the other way around; smooth usage is critical.
Nexus Smart ID is a unique multi-factor authentication solution for organizations to empower their users with trusted authentication that is easy to use, easy to manage, cost-efficient and secure. It allows organizations implement zero trust security policies by granting secure access only to the authorized users - employees, customers, or citizens - to the right digital resources, no matter where users or resources are located.
With Smart ID, organizations can go passwordless and prevent unauthorized access by adopting user-friendly MFA methods with single sign-on (SSO) and identity federation, enabling users to log on just once to reach all managed resources.
13
5.2.1 Versatile and risk-appropriate authentication
Nexus offers several different authentication methods of varying strengths in one flexible and integrated, versatile authentication solution. The benefit of using a platform supporting versatile authentication is that you can select to apply the most appropriate authentication method for each application.
Practically, you can use simple password-based authentication to provide access to less sensitive applications, and more complex authentication to secure access to highly sensitive data. When an already authenticated user requests access to a more sensitive application, you can apply step-up authentication, which requires the user to authenticate again with an additional credential.
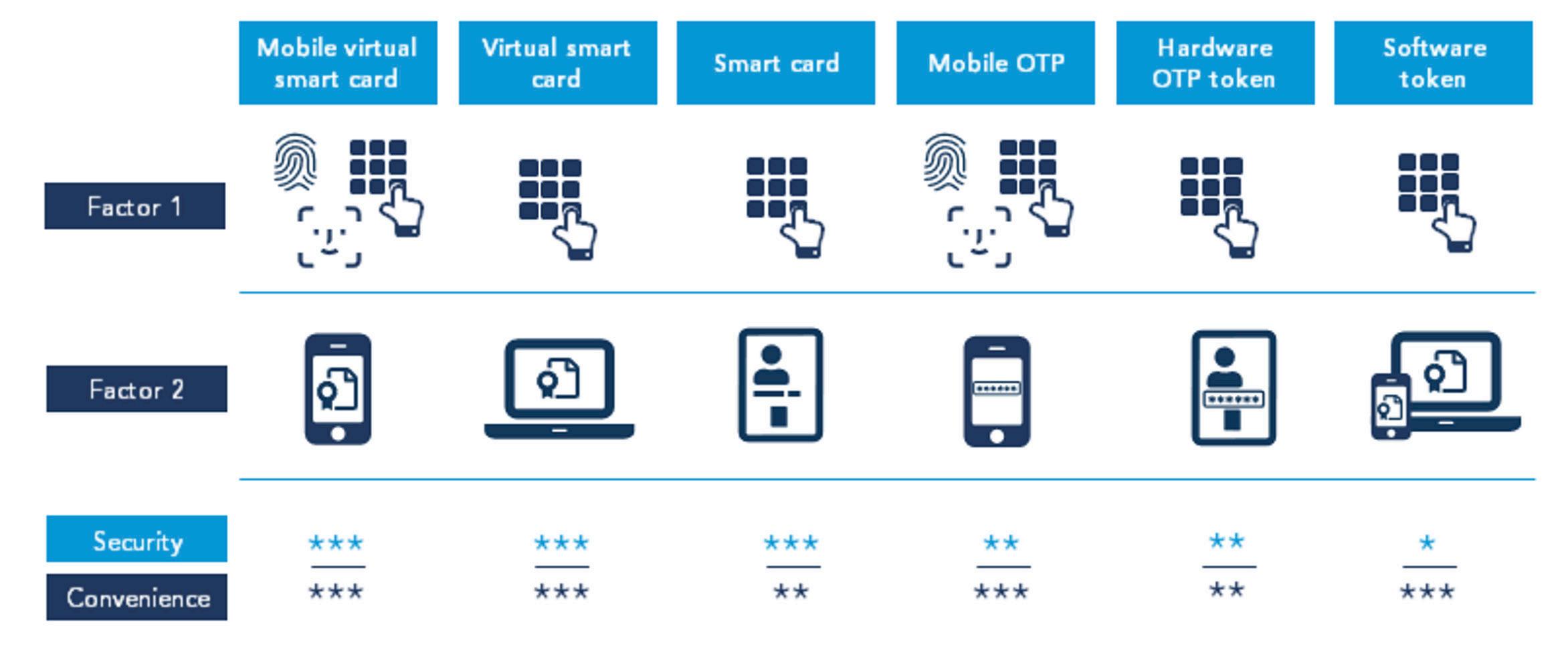
5.2.2 User self-service for reduced administrative overhead
To ensure compliance with standards and regulations and to minimize manual administration, Smart ID enables user authorization based on standardized access rules. These access rules allow formalizing and enforcing the company policies by specifying detailed requirements for users to access resources.
Centralized management combined with user self-service functionality further eases administrative management.
Nexus' solution uses standard protocols and is extendible through a plug-in API (Application Programming Interface). Open standards such as X.509, Open Authentication, RADIUS, LDAP, SAML 2.0, OpenID Connect, and OAuth 2.0 are supported. For applications that do not support any of these standards, integration with Web Services interface is offered.
5.2.3 Extensible use-cases
Nexus Smart ID also enables organizations to provide its users with use-cases beyond MFA. Some examples include,
• Can act as an identity provider against Nexus' services or external services
• Manage secure access to all kinds of digital resources that are installed on-premises or available in the cloud
• Enable digital document signing with non-repudiable signatures for all users
• Roll out email encryption and signing to protect sensitive and confidential corporate email communication
• Authorize access to physical premises and facilities
14
Figure 4.
And that’s not all. The same Smart ID platform can be extended to provision and manage trusted identities for all corporate resources such as applications, software, IT devices such as servers, firewalls, printers, etc., and IoT devices. The holistic platform encompasses a broad range of use cases that empower organizations across industry verticals to adopt an identity-first security approach and achieve Zero Trust.
5.2.4 NIS2 requirements beyond MFA
Moving beyond MFA, NIS2 significantly emphasizes critical aspects such as cryptography, cyber hygiene, and network security. To address these components comprehensively, an organization needs to formulate a clear and company-wide strategy for their public key infrastructure (PKI):
1. Network security: involves monitoring TLS/HTTPS certificates and replacing them before expiration or compromise.
2. Device certificates: The company PKI must manage and issue network security device certificates for secure communication in modern IT devices.
3. Encrypted communication and storage: Demand appropriate encryption certificates.
By implementing a robust PKI solution, organizations can effectively manage and utilize a solid security foundation for strong authentication, email encryption, digital signing, and applications, aligning with the evolving landscape of cybersecurity threats.
Nexus' proven and highly scalable PKI platform offers organizations a comprehensive package for NIS2 compliance. Common Criteria EAL4+ certified, Nexus Smart ID PKI supports a wide range of enrolment protocols and interfaces, such as ACME, SCEP, EST, and CMC, among others. This makes it easily extensible to various use cases while keeping it secure and compliant with global industry standards.
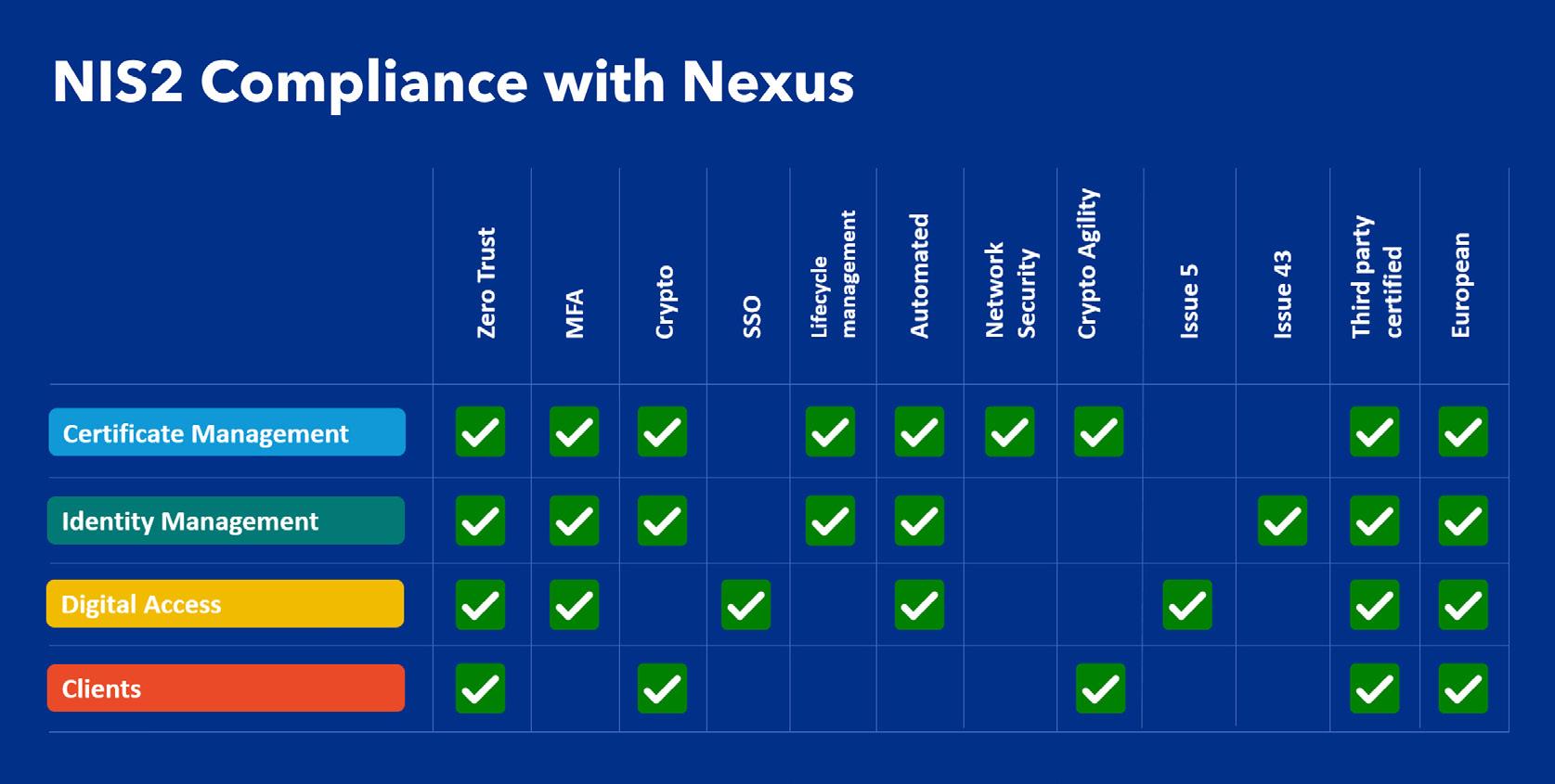
15
Figure 5.
6. Summary
Embracing NIS2-aligned cybersecurity measures is both a compliance necessity and a forward- thinking strategy, providing protection against current threats and strategically positioning organizations amidst evolving cybersecurity and regulatory landscapes. With the directive’s enforcement date, October 17, 2024, fast approaching, the time to act is now.
Password-based authentication has been deemed insecure for years. Organizations cannot afford to risk the immense damage that leaked passwords could entail. Strong multi-factor authentication protects against phishing, password cracking, key logging, and many other types of identity theft. Crucial for meeting minimum NIS2 requirements, MFA addresses various cybersecurity directives, including human resources security, supply chain security, and network security.
MFA also drastically boosts an organization’s overall security posture and takes them a step closer to achieving zero trust, identity-first security approach. This is also emphasized in the NIS2 directive where the Essential and Important entities are expected to embrace a comprehensive set of fundamental cyber hygiene practices, including zero-trust principles.
While NIS2 compliance dictates a broad range of measures, MFA deployment offers organizations a quick win.
With Nexus Smart ID, organizations can empower their users with a secure MFA technology that is easy to use, easy to manage, and cost-effective. Our unique consumer-oriented solution leverages devices such as laptops, tablets, and mobile phones, which makes them easily scalable and easy to use for millions of users.
If you are currently evaluating multi-factor authentication solutions, the checklist below will help you make the right decision. It enumerates the characteristics of an effective solution to ensure that it is convenient enough for broad consumer adoption while keeping costs down and security risks at a minimum.
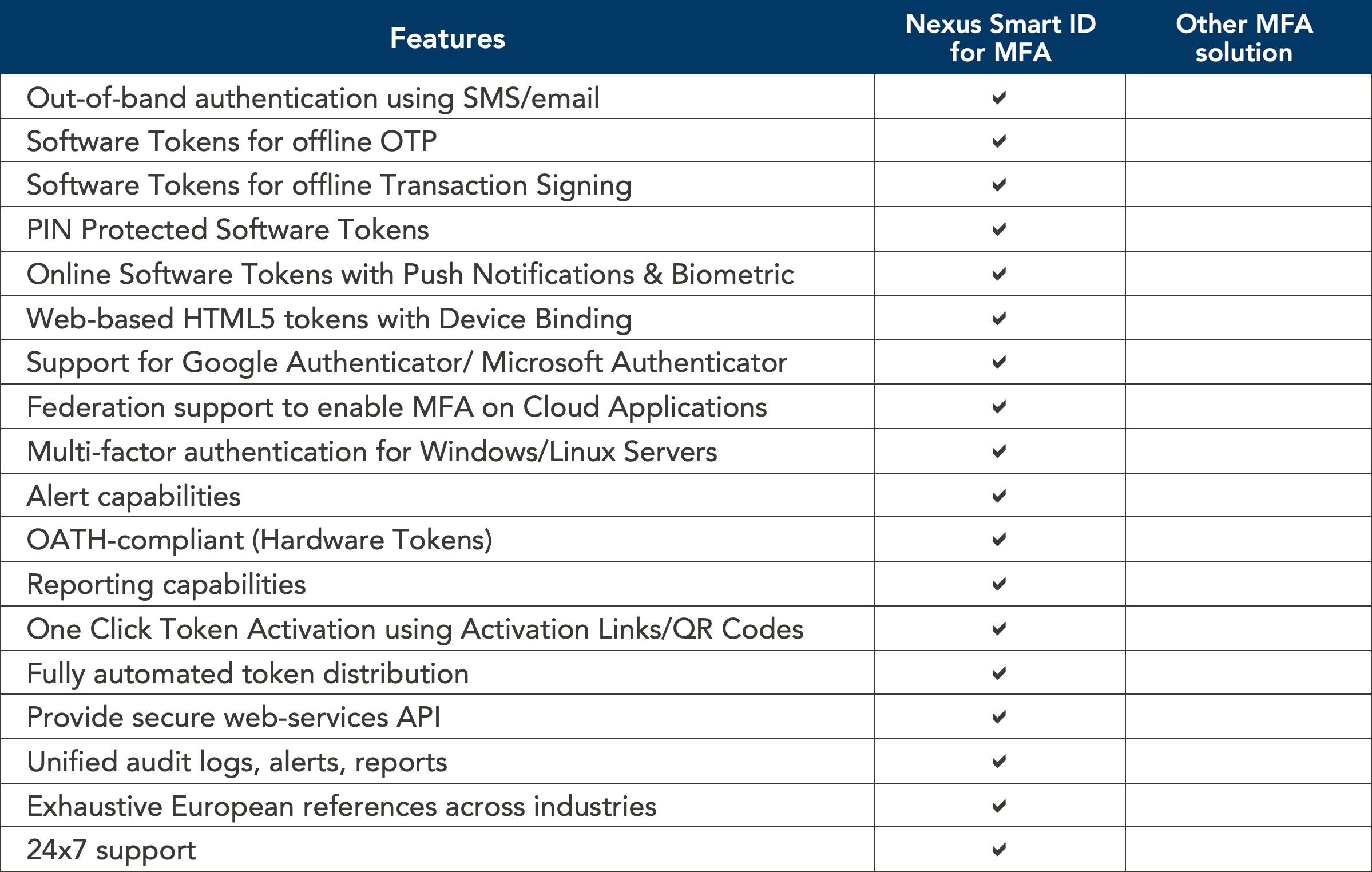
Table 4. 16
References
- The NIS2 Directive: Read the complete directive
- ANSSI Statement: Understanding changes for French businesses and administration
- ANSSI Guide to Becoming Compliant: Explore the cybersecurity guide for small and medium-sized enterprises
- BSI Guide to Becoming Compliant: Access the IT Grundschutz guide for organizations
For detailed guidance specific to each country:
- In Germany, refer to BSI.
- In France, ANSSI provides comprehensive information.
- The Swedish Civil Contingencies Agency (MSB) offers a valuable summary in their document, ”Policy Overview - Initiatives at EU Level Affecting Sweden’s Information and Cybersecurity Work.”
- Preparing for NIS2 - A Checklist for Affected Entities: Explore our checklist for a smooth transition
Tables and figures
Page 6: “Table 1. Industries covered under NIS vs NIS2”
Page 8: “Table 2. Important vs Essential entities categorization”
Page 9, “Figure 1. Illustration: NIS2 applicability based on company size and turnover”
Page 9, “Figure 2. Timeline of EU events (count of observed incidents per month)”
Page 10: “Figure 3. Different authentication factors that contribute toward MFA”
Page 12: “Table 3. Getting started with MFA”
Page 14: “Figure 4. Available MFA options with Nexus Smart ID”
Page 15: “Figure 5. Comprehensive Smart ID package for NIS2 compliance”
Page 16: “Table 4. Nexus Smart ID MFA vs Other MFA solutions: Comparison checklist”
About Nexus
Nexus, a part of the French IN Groupe is a European leader and innovative identity management company. We secure society by enabling trusted identities for people and things.
Our range of security solutions allow organizations to issue and manage trusted identities for the workforce, workplace, and the Internet of Things (IoT) thus, fortifying and safeguarding them against evolving cyber threats. As a European vendor of PKI-based trusted identities, we closely understand and help you to comply with latest regional regulatory requirements, such as NIS2, and adopt an identity-first, Zero Trust security strategy with our proven, scalable, robust, and certified PKI platform.
Let’s embark on the journey toward a secure and resilient cybersecurity future together!
nexusgroup.com
17

” Our commitment to excellence and innovation drives us to build a secure tomorrow with trusted identities ” www.nexusgroup.com











