Matchmaking
Mexico’s leading B2B conference organizer uses a customized app to deliver an unparalleled experience
The MBE App delivered AI-powered intent-based matchmaking to Mexico Cybersecurity Summit 2025 attendees
MBE App Impact
130 participants
186 matchmaking communications
89 1:1 meetings conducted Matchmaking intentions
Total 1,379 549 Trading 830 Networking
• 99minutos.com
• Abnormal AI
• AI for Good CDMX Hub
• AI for Good Hub Leader
• AI for Good Young AI Leaders
• ALAPSI
• Algosec
• Alianza México Ciberseguro
• AmCham/Mexico
• AMECH / Eulen de Seguridad Privada
• Area Industrial
• ArO Y CHAZ
• Asamep Asociación
• ASOCIACIÓ n DE AG r EGADO r ES DE MEDIOS DE PAGO
• Attache
• AXO
• B2V Media
• Bankaool, S.A. Institución de Banc a Múltiple
• BBVA
• Becerril, Coca & Becerril
• Bid f TA.com
• BIOPAPPEL
• Borealix
• British Embassy M exico City
• Business france
• Cancún IT
• CEnACE
• Centro Médico ABC
• Chevez ruiz Zamarripa
• Cluster Aeroespacial
• Cluster Espacial de Mexico
• C n BV
• Cognitus IT Solutions
• Compartamos
• COMPLIA
• Conecta
• Conver t Commerce
• Danone
• Desarrolladora del Parque, SA de CV
• DESC CO r PO r ATIVO
• Dicka Logistics
• DI r AC SAPI de CV
• DOW
• Dylo I n C
• DY nATr ACE
• Ekolabs
• El Palacio de Hierro
• Equipos y Productos Especializados SA de CV
• ESTr ATEGAS DE MEXICO
• Euromundo
• fCDO
• for vis Mazars
• ftech
• GIBHO r SMArT SErVICES SAS DE CV
• Grupo HI r
• Grupo Pochteca
• Grupo Tres Marias
• GrupoBeIT
• GSK
• Heineken
• Hexaware Technologies
• Holland and Knight
• iboss
• Icorp
• iDric
• Illumio
• I n DIA CHAM BEr MEXICO
• India Mexico Chamber
• I n K Pr
• I nn OVATI
• International SOS México Emergency Services
S de r L de CV.
• Izzi
• Jumex
• Keltio
• Kiritek
• K PMG México
• Kueski
• Loreal
• LUMU TECH n OLOGIES
• ManageEngine
• Mastercard
• Mercado Libre
• Metrofinanciera
• n emak
• n ewmont
• n grenta
• nissan
• n ovartis farmaceutica
• Oca Global
• Ontario Office in Mexico
• Openpay
• Palla financial
• PALO IT
• Paradiqma
• PepsiCo
• Pricetravel
• Pr IMX
• Provident Mexico
• QMA
• Química Apollo
• r An USE
• rOC M720112DW2
• rUH r PUMPEn
• SABO r MEX
• Scotiabank
• SEG U rOS ATLAS
• Siemens
• Sky Angel
• STP
• Suprema Corte de Justicia de la n ación
• Sygnia
• SYTECA
• T-Systems
• Tecnológico de Monterrey
• Tequilera de Arandas
• Texas European Chamber of Commerce
• The IBH
• Tr AfALGAr
• Truper
• United states embassy
• VP Sales | Cash Management Industry Leader - CIB
• W-Industries México
• Womcy
• WoSEC Mexico
• yotepresto.com
• Zion Cybersecurity
• Zoom
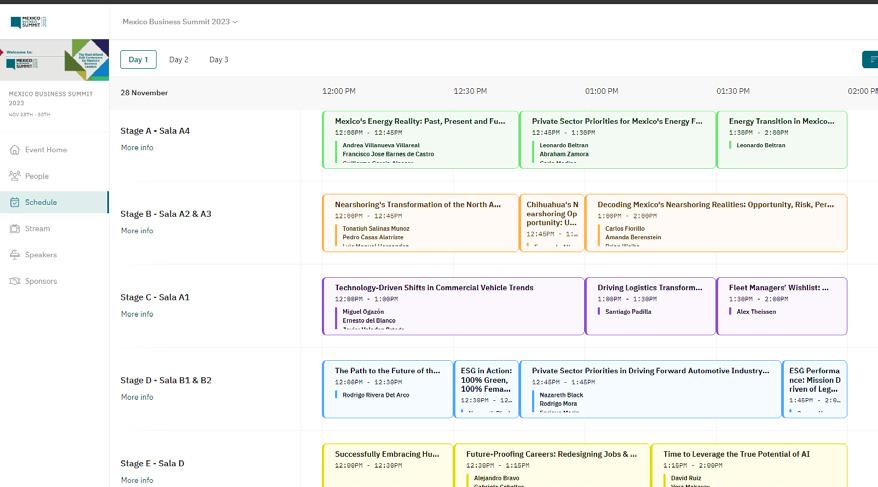
WEDNESDAY, OCTOBER 22
09:00 ESCALATING CYBERSECURITY RISKS CALL FOR STRONGER DEFENSES
Speaker: Rebeca Servín, AMCHAM
09:30 COLLABORATE TO FORTIFY: ENTERPRISE PARTNERSHIPS FOR CYBER RESILIENCE
Moderator: Ernesto Ibarra, Alianza México CiberSeguro
Panelists: Erick Sanchez, Cinépolis
Angélica Arana, Multiva
Óscar Chombo, Scotiabank
Pablo Mosqueira, QMA/iboss Mexico
Iván Dario Tapias, Mastercard
10:30 DARKWEB MONITORING: THE JOURNEY OF STOLEN DATA
Speaker: Darwin Bejarano, ManageEngine
12:00 BRIDGING IT & OT TO SAFEGUARD SMART FACTORIES OPERATIONS
Moderator: Cateryn Farfán, WoSEC Mexico
Panelists: Emilio Mena, nemak
Jorge López, Grupo Bachoco
Juan José Luis Cisneros, Grupo Pochteca
Óscar Colin Cortés, Siemens Mexico, Central America and the Caribbean
13:00 RE-THINKING CYBERSECURITY
Speaker: Christer Swartz, Illumio
13:30 AI FOR DEFENSE, INTELLIGENT AUTOMATION AGAINST CYBER THREATS
Speaker: Edgar Flores, T-Systems Mexico
Rodrigo Renoud, T-Systems Mexico
15:00 INVESTMENTS THAT MATTER: PRACTICAL STRATEGIES FOR BUSINESS PROTECTION
Moderator: Ana Cecilia Pérez, Capa 8
Panelists: Jose Treviño, Dicka Logistics
Israel Gutiérrez, Gentera
Rommel García, KPMG
16:00 THE RISE OF GENERATIVE THREATS: FIGHTING AI WITH AI
Speaker: Fernando Villalobos, Abnormal AI
16:15 2026 CYBER RESILIENCE: STRATEGIES TO WITHSTAND THE NEXT WAVE OF THREATS
Moderator: Manuel Díaz, Huawei Mexico
Panelists: Adriana Servín, CAnIETI
Mario Rivas, Seguros Monterrey New York Life
Manuel López, nissan
Alberto Ramirez, BBVA Technology in America
Gloria Moncayo, Provident Mexicos
ESCALATING CYBERSECURITY RISKS CALL FOR STRONGE R DEFENSES
The rapid rise of cybercrime can have severe economic and operational implications for individuals, companies, and national security. But strengthening Mexico’s digital defenses requires sustained investment in technology and talent, as well as public policies that foster resilience and awareness throughout the population.
“A cyberattack can paralyze operations and threaten sensitive information,” said rebeca Servín, Vice President of Innovation and ICTs, AMCHAM, during the Mexico Cybersecurity Summit 2025.
“If Mexico aims to strengthen its position as a competitive player in the digital economy, it must build a culture of cybersecurity based on collaboration between government, the private sector, academia, and society”
Rebeca Servín Vicepresident of Innovation and TICs | AMCHAM
attacked countries globally, identifying public institutions, industrial facilities, and financial and retail entities as frequent targets. nearly nine out of 10 Mexican companies have experienced at least one cyberattack, with SMEs facing average losses of about MX$2 million per incident, according to the 2023 Annual Cybersecurity Survey.
Servín says that Mexico’s exposure to digital threats is linked to its growing nearshoring activity and strong trade relationship with the United States. ransomware groups are increasingly targeting firms operating within cross-border supply chains.
Cybercrime has evolved into one of the most serious global threats, says Servín. According to Statista, global cybercrime costs are projected to reach US$10.3 trillion in 2025, an amount that would make it the world’s third-largest economy after the United States and China. The rate of cybercrime is growing by 15% annually, far outpacing global economic growth. In Mexico, the impact is particularly severe: f ortinet reported 31 billion attempted cyberattacks in the first half of 2024, accounting for more than half of all such incidents in Latin America.
“Cybercrime today operates as a professional industry,” says Servín. “These are not isolated hackers but organized criminal networks with defined roles, objectives, and access to vast technological and financial resources.”
Mexico consistently ranks among the world’s most targeted nations. BlackBerry’s 2023 report placed Mexico among the top six most-
Servín points out that password-based attacks remain one of the most persistent infiltration methods. Over 99% of identityrelated breaches involve stolen or exploited credentials, with more than 1.7 billion compromised records detected in underground markets in 2024. “Weak or reused passwords remain a key vulnerability, as 80% of data breaches are linked to poor password hygiene,” Servín says. She recommends the adoption of password managers, multifactor authentication, and the use of unique credentials across systems.
referencing Microsoft’s recently published Digital Defense report, Servín explains that attacks originating from state-sponsored actors — particularly r ussia, China, Iran, and n orth Korea — are on the rise. She cited reports of north Korean IT specialists using false identities to obtain remote jobs abroad, enabling them to insert malware and ransomware into corporate systems.
AI, Servín adds, has become both a defensive and offensive instrument in cybersecurity. While it enables companies to analyze trillions of signals daily and prevent intrusions, it is also being exploited by cybercriminals for data manipulation and more sophisticated attacks. “AI has become a double-edged sword, vital for defense but equally useful for offense,” says Servín.
To address these challenges, Servín suggests adopting a multiyear plan, such as Microsoft’s Secure future Initiative (SfI). This program focuses on three pillars: security by design, security by default, and secure operations.
She warns that Mexico faces an additional structural challenge: a severe shortage of cybersecurity professionals. f ortinet estimates a global gap of 4 million specialists, with about 500,000 unfilled positions in Mexico. Universities have begun to expand their cybersecurity programs, but demand continues to exceed supply.
Cybersecurity must be treated as a shared responsibility across sectors, says Servín. “If Mexico aims to strengthen its position as a competitive player in the digital economy, it must build a culture of cybersecurity based on collaboration between government, the private sector, academia, and society,” she adds.
COLLABORATE TO FORTIFY: BUSINESS PARTNERSHIP FOR CYBER RESILIENCE
The era of isolated enterprise cybersecurity is over. A 68% increase in supply chain attacks, shows that collaborative defense has transitioned from an alternative to a critical operational imperative for survival in the modern digital ecosystem.
“Collaboration among enterprises is essential, as government efforts alone are not enough to counter today’s cyber threats,” says Erick Sánchez, CISO, Cinépolis, during the Mexico Cybersecurity Summit 2025.
An organization’s security no longer depends on its perimeter defenses but on the resilience of its least prepared partner. “Threats have no borders and do not distinguish sectors.
“The key is to generate reports that allow us to identify attacks that others have already faced, and share gaps without exposing weaknesses. This principle is formalized through protocols such as the Traffic Light Protocol (TLP), which classifies information sensitivity, and is technologically enabled through Threat Intelligence Platforms (TIPs)”
Pablo Mosqueira General Director/Strategic Partner | QMA/iboss Mexico
Cybercriminals collaborate constantly... If we do not collaborate, our destiny is marked,” says Angélica Arana, CIO, Multiva.
The financial consequences of cyber incidents have reached an all-time high, with an average global cost of US$4.88 million per data breach, according to IBM’s 2025 Cost of a Data Breach report. Some sectors face higher risks: the healthcare sector records the highest cost at US$9.77 million per incident, followed by the financial sector at US$6.08 million. These figures show that cybersecurity has transcended its technical function to become a pillar of strategy and fiduciary responsibility for senior management.
This growing problem calls for a new approach to cybersecurity, one with collaboration at the center. “We often assume that being competitors means we cannot share solutions. In reality, sharing creates a healthier environment that drives innovation and business growth,” says Ernesto Ibarra, President, Alianza México CiberSeguro.
This approach, however, faces significant barriers, primarily cultural and trust-related. Ibarra explains that businesses in Latin America are very guarded about sharing data and trends that could serve colleagues.
Therefore, the first action to strengthen collaboration is to organize the sectors and generate that trust in the ecosystem.
An effective approach to overcome mistrust could be the adoption of zero trust models, which would enable the transmission of data without exposing data confidentiality, says Ibarra.
“We often assume that being competitors means we cannot share solutions. In reality, sharing creates a healthier environment that drives innovation and business growth”
Ernesto Ibarra President | Alianza México CiberSeguro
Tapias, Vice President, Security Solutions, Mastercard.
Strengthening the relationship between the cybersecurity sector and the government could help to enhance regulation, so crimes like fraud, card theft, and usurpation are prosecuted, says Sánchez.
Proven models for this collaboration exist. Information Sharing and Analysis Centers (ISACs) offer sectoral intelligence; the MultiState ISAC (MS-ISAC), for example, prevented over 59,000 attacks for its members in 2024.
“The key is to generate reports that allow us to identify attacks that others have already faced, and share gaps without exposing weaknesses. This principle is formalized through protocols such as the Traffic Light Protocol (TLP), which classifies information sensitivity, and is technologically enabled through Threat Intelligence Platforms (TIPs),” says Pablo Mosqueira, General Director and Strategic Partner, QMA/iboss Mexico.
This need for certainty extends to publicprivate collaboration. “Collaboration is vital in threat intelligence and fraud pattern detection. It must happen within the industry, with support from the government,” says Iván
In parallel, human training must evolve. The cybersecurity sector faces a structural talent deficit, with a global shortage of 2.8 million professionals. f urthermore, mistakes by individual users are often the entry points for larger attacks. “The weakest link is still the user,” says Arana. Under these circumstances, CISOs play a key role as “they can speak to the board and to general management in terms they understand,” she adds.
As attacks rise sharply and breach costs reach historic levels, cybersecurity has evolved from a technical concern to a strategic and fiduciary responsibility. In this scenario, the CISO gains unprecedented importance, and responsibilities.
“Our role must evolve from technical to strategic. Security must be a business enabler, not just a technical function,” says Óscar Chombo, CISO, Scotiabank.
MONITORING THE DARKWEB: THE JOURNEY OF S TOLEN DATA
When sensitive information escapes an organization’s control, the consequences can extend far beyond financial loss. Data leaks not only jeopardize operational integrity but also expose companies to reputational harm and long-term trust erosion. As cyberattacks grow more sophisticated, understanding how stolen information travels through digital networks, and particularly through the Dark Web, has become a critical priority for all sectors, explains Darwin Bejarano, Senior Strategic Account Manager, ManageEngine.
“Cybercrime is a constantly evolving and profitable activity, leading to increasingly sophisticated cyberattacks,” said Bejarano during the Mexico Cybersecurity Summit 2025.
Cybercrime is expected to have an economic impact of US$10.5 trillion by 2025. In 2021, a 140% increase in cyberattacks targeting Operational Technology (OT) was observed. During 2022, ransomware incidents increased 87%. In 2023, ransomware payments reached US$1.1 billion, and 77.9 million malware attacks on IoT devices were recorded.
“Many successful cyberattacks begin by exploiting uncontrolled metadata, which attackers use to access sensitive information”
Darwin Bejarano Senior Strategic Account Manager | ManageEngine
Every organization manages various kinds of information that differ in sensitivity and legal requirements. Public or operational data may be openly accessible, while confidential data demands restricted access. In industries bound by privacy and compliance regulations, personally identifiable information must be treated with heightened security. Proper classification determines the level of protection each dataset requires, reducing the likelihood of accidental exposure.
“Organizations must carefully assess data classification and the required protection and handling levels from the outset,” says Bejarano.
When a security gap is exploited, stolen data often finds its way into the Dark Web, a hidden layer of the internet where transactions take place anonymously, typically through cryptocurrencies. This market handles vast quantities of illicit data, from credit card numbers and government files to corporate databases, posing serious threats to institutions, public entities, and individuals alike. Because anonymity reigns in this environment, tracing buyers and sellers is nearly impossible.
These attacks directly impact business continuity and consumer perception. ManageEngine reports that 60% of SMEs that fall victim to severe cyberattacks cease operations within six months of the incident. Additionally, a survey on consumer perception of brand cybersecurity reveals that 75% of consumers are willing to end business relationships with a company after a security breach, as trust is also compromised.
This landscape calls for urgent data protection strategies. The foundation of effective cybersecurity lies in data classification.
Cybercriminal activity in the Dark Web continues to expand due to the high financial rewards it offers. Organized groups operate with advanced technology, using evolving techniques such as phishing, ransomware, and SQL injection attacks. for example, data from financial institutions, travel booking platforms, and restaurants have all been compromised through various forms of digital manipulation. Once obtained, the stolen data is encrypted, cleaned of identifying metadata, and sold to the highest bidder.
An often-overlooked risk in this process is metadata exposure. Metadata — automatically generated information about files, such as the time, location, or device used — can reveal more than organizations realize. Even when the primary data is protected, unmonitored metadata can serve as an entry point for attackers to uncover sensitive systems or user information.
“Many successful cyberattacks begin by exploiting uncontrolled metadata, which attackers use to access sensitive information,” says Bejarano.
User behavior also contributes to vulnerabilities. Many individuals unknowingly grant excessive permissions to mobile applications or browser extensions, allowing background processes to collect data even when not in use. These permissions can compromise stored credentials or enable unauthorized data transfers without the user’s awareness.
Adding to the challenge, breaches often remain undetected for months. Studies indicate that organizations take an average of 292 days to identify and contain credential theft, and similar timelines apply to phishing and social engineering attacks. This delay gives attackers a significant advantage to exploit vulnerabilities and extract more data.
To counter these risks, companies must implement a multilayered cybersecurity strategy, says Bejarano. This includes strict access control policies, automatic credential rotation, temporary access for thirdparty vendors, and continuous monitoring supported by AI. Threat intelligence tools can detect anomalies, analyze behavioral patterns, and provide proactive alerts before breaches escalate.
Moreover, organizations should actively monitor their digital footprint beyond the visible internet. Understanding what information about their domain or users may be circulating on hidden networks is essential for containment and response. Technologies such as Privileged Access Management (PAM) and Security Information and Event Management (SIEM) systems play a crucial role in correlating large volumes of data, identifying suspicious activity, and supporting timely intervention.
Ultimately, no system is entirely immune to cyber threats. The only certainty is that vulnerability exists, and preparedness determines resilience. Strengthening data protection, monitoring emerging risks, and fostering cybersecurity awareness across all levels of an organization remain the most effective defenses in an era where digital shadows grow deeper every day.
BRIDGING IT, OT TO SAFEGUARD SMART FACTORIES O PERATIONS.
The integration of information technology (IT) and operational technology (OT) is the engine of Industry 4.0. However, this convergence has exposed smart factories to a rapidly escalating landscape of cyber threats. Many attacks no longer seek only to steal data but to physically paralyze operations, making unified cybersecurity a strategic imperative for business continuity and market survival.
“IT and OT teams are not adversaries; they are collaborators,” says Cateryn f arfán, founder, WoSEC Mexico, during the Mexico Cybersecurity Summit 2025.
The drive for efficiency, predictive maintenance, and agility has left security behind in many cases. This gap between technological implementation and security maturity is the core of many modern risks, according to Dragos’s 2025 OT Cybersecurity report.
The challenge lies in the intrinsic differences between IT and OT. IT focuses on data management, prioritizing the CIA triad: confidentiality, integrity, and availability. It operates with equipment lifecycles of three to five years and a culture of constant updating. In contrast, the OT domain controls physical processes, prioritizing availability, integrity,
and confidentiality to ensure human safety and uninterrupted production. Its systems have lifecycles of over 15 to 20 years. Any change, such as applying a patch, is a highrisk operation that may require a production stoppage. “OT has been neglected for many years. A key question: can IT and OT worlds unite?” asks Emilio Mena, Global Cybersecurity CSIrT Manager, nemak.
“Security should not be treated as just a cost or a potential ROI metric—it is operationally essential.”
Jorge López CIO | Grupo Bachoco
While the average cost of an IT data breach is US$4.88 million, according to IBM’s Cost of a Data Breach report 2024, a single hour of unplanned downtime at a large automotive plant can cost up to US$2.3 million. “Indicators matter: if controls and information are insufficient, operations could stop,” says José Luis Cisneros, Corporate Director of IT, Grupo Pochteca.
Overcoming this challenge requires addressing three fundamental obstacles: the cultural gap between IT and OT teams, the technical debt of legacy systems, and a persistent governance gap. “Cultural gaps exist; awareness of cybersecurity is still limited. Education and communication are essential,” says Cisneros.
Industry 4.0 has forced the union of both worlds. Technologies like the Industrial Internet of Things (IIoT) and AI depend on a seamless flow of data from machinery on the plant floor (OT) to enterprise resource planning systems (IT). The benefits are undeniable, including the ability to predict equipment failures, optimize the supply chain in real time, and accelerate innovation. According to a report from Grand View research, the global smart factory market is projected to reach US$272.6 billion by 2030. By connecting previously isolated OT systems to IT networks, organizations have inadvertently created a new and massive attack surface. “We are in a machine-to-machine era, with the AI boom now intersecting with robotics,” says farfán.
risks are only escalating. In 2024, ransomware incidents targeting industrial organizations increased by 87% compared to the previous year, with the manufacturing sector accounting for 69% of the attacks, reports Dragos.
“OT data traffic is usually predictable; anomaly detection and machine learning help identify risks. Tools exist to analyze traffic, detect spikes, and evolve intelligence.”
Óscar Colin
Global Cybersecurity Leader | Siemens Mexico, Central America and the Caribbean
While CISO oversight of OT is now a standard practice, the focus in 2025 has shifted from responsibility to maturity. The 2025 State of Operational Technology and Cybersecurity report reveals that while over 80% of CISOs oversee OT, only 35% of organizations report having a mature, fully integrated IT/ OT security operations model. “My focus is on creating synergy between IT and OT, establishing a common language, and preventing past mistakes,” says Jorge López, CISO, Grupo Bachoco. “Security should not be treated as just a cost or a potential rOI metric—it is operationally essential.”
To bridge gaps, leading organizations are anchoring their strategies in proven frameworks. The SA n S 2024 ICS/OT Cybersecurity Survey shows that 65% of industrial firms have begun actively aligning with nIST CSf 2.0, with a primary focus on implementing the “Govern” function to create a unified risk management strategy. “We need adaptable frameworks (‘frankenstein sets’) to accommodate diverse interests. Challenges can be overcome using digital tools; technology can drive enormous change,” says farfán.
AI is helping enhance predictive defense in OT. Its primary use case has matured beyond simple anomaly detection to asset discovery and management, which is critical for handling the explosion of connected
devices. “AI can be both an ally and a threat; it is critical to implement positively,” says Óscar Colin, Global Cybersecurity Leader, Siemens Mexico, Central America, and the Caribbean.
“OT data traffic is usually predictable; anomaly detection and machine learning help identify risks. Tools exist to analyze traffic, detect spikes, and evolve intelligence.”
finally, the regulatory environment is driving board-level accountability. Deloitte n IS2’s first-year impact report shows that regulators are focusing heavily on supply chain risk management and executive-level oversight. “Leadership in security starts at the top, and general management plays the key role,” says Cisneros.
RE-THINKING CYB ERSECURITY
Global cybersecurity spending reached US$215 billion in 2024, yet reported incidents increased by 75% from the previous year, highlighting a fundamental flaw in traditional defense strategies. The focus must thus shift from simple threat detection to active breach containment, limiting the lateral movement of attackers to neutralize risk before it spreads.
“Every year we spend more money with more complex solutions and the problems just keep getting worse,” said Christer Swartz, Director of Industry Solutions, Illumio, during Mexico Cybersecurity Summit 2025.
The primary reason for the ineffectiveness of rising investments is that conventional tools focus on protecting the “health” of individual resources. The problem with this model is that by the time a security agent identifies a threat, it has often already compromised the system and begun to spread to other network assets. “The problem is not that one resource was there, it is that it has spread. So, this lateral movement is what we need to discover and enforce,” Swartz says.
All threats share a fundamental characteristic: “They all want to spread,” says Swartz. This propagation, known as lateral movement, is the common dependency that all threat actors exploit.
The problem is only growing. Cybercrime has established itself as the world’s third-largest economy, with an estimated GDP of US$9.5 trillion in 2024, says Illumio. This figure is surpassed only by the United States at US$27.5 trillion and China at US$17.5 trillion.
With an average of 2,200 cybersecurity incidents reported daily worldwide, it is clear that the existing approach is not fully mitigating risks.
Security has historically been a secondary consideration in the development of digital infrastructure. When commercial activity began on the Internet in 1991, the priority was high availability, not security. This legacy has resulted in operating systems that, by default, keep numerous ports open in listening mode. “All modern OS will have open ports. Whether it is for screen sharing, for print sharing, DnS,
or SSH, they are all open doors. And threats move across these open doors,” says Swartz.
f or example, a macOS or CentOS Linux system can have 13 open TCP ports, while Windows 10 has 10. These ports, using protocols like r DP, SMB, SSH, and LDAP, act as unsecured doors, offering attackers multiple pathways to propagate malware across workloads.
“Without the ability to move laterally, a threat is neutralized, transforming a potential catastrophe into a manageable incident”
Christer Swartz
Director
of Industry Solutions | Illumio
The flaw of Siloed Visibility
Threats move through two primary vectors: the exploitation of human behavior, which remains the weakest link, and the use of open ports between workloads. While training can mitigate the first factor, it cannot eliminate it. Therefore, controlling the second vector — machine-to-machine movement — becomes critical.
Traditional security solutions such as firewalls, EDr, XDr, and CnAPP operate in silos, providing localized visibility but not a global, unified view of the environment. Each tool protects its own domain, but lacks the ability to see or control traffic among these disparate domains.
Threat actors, however, do not see lists of isolated assets. They “think in graphs,” visualizing the network as an interconnected set of nodes and exploiting the paths of least resistance to reach high-value targets, says Swartz.
This is creating a new paradigm: breach containment through segmentation. rather than relying solely on detection, this strategy assumes a breach will eventually occur and focuses on drastically limiting its impact. The Illumio Breach Containment Platform, for example, operates at the network
layer of the cybersecurity stack to block lateral movement, which is the operational dependency of all threats.
This strategy relies on two pillars. The first is Unified Visibility, which involves ingesting telemetry data from the entire hybrid, multicloud infrastructure — including endpoints, data centers, containers, and IoT/OT — and enriching it with information from third-party tools like ED r , SIEM, C n APP, and CMDB. This process creates a real-time, global dependency map, eliminating the visibility silos that attackers exploit.
The second is Proactive Segmentation to design and implement granular segmentation policies to contain unauthorized traffic. This means that even if a workload is compromised, the breach is isolated, preventing malware from spreading to other critical systems. A platform can apply these policies consistently across any environment, from bare-metal servers in a corporate data center to serverless functions in a public cloud.
By shifting the focus from a reactive posture of finding threats to a proactive strategy of containing breaches, organizations can invalidate the attackers’ operational model. “Without the ability to move laterally, a threat is neutralized, transforming a potential catastrophe into a manageable incident,” says Swartz.
AI FOR DEFENSE, INTELLIGENT AUTOMATION AGAINST CYB ER THREATS
The rise of AI is making cyberattacks faster and more precise. for that reason, organizations like T-Systems are leveraging AI-assisted monitoring, automation, and human oversight to detect and respond to incidents in real time. Combining AI tools with skilled security teams is crucial for protecting digital assets and maintaining operational resilience as AI-driven attacks grow in sophistication.
“Adversaries now use AI and natural language processing to enhance the realism of attacks, including subtle language cues and sentiment analysis,” said Edgar f lores, Offensive Security and Cyber Threat Intelligence Team Lead, T-Systems Mexico, during the Mexico Cybersecurity Summit 2025.
AI-driven threats, says flores, now encompass deep fakes, voice cloning, and CEO-targeted social engineering campaigns, often referred to as “CEO fraud” or Business Email Compromise attacks.
The integration of AI into cyberattacks has made threats more scalable, adaptive, and polymorphic. Attackers can now automate reconnaissance, build detailed digital profiles of organizations, and generate convincing phishing campaigns in minutes rather than days. Malware, once static, is increasingly capable of self-modification once deployed, adapting to evade traditional defenses such as endpoint detection and response (EDr) or extended detection and response (XDr) systems.
r odrigo r enaud, Global Cyber Defense Manager, T-Systems Mexico, highlights that organizations must incorporate AI into their defensive strategies to match the speed and sophistication of AI-powered threats. T-Systems employs AI-assisted monitoring, threat detection, and incident response, while ensuring human oversight in critical decision-making.
“We have developed independent AI data lakes that allow human analysts to maintain custody and validate investigations,” says renaud. This combination of AI and human expertise enables rapid identification of threats and timely response.
Automation is a key component of T-Systems’ cyber defense strategy. By consolidating multiple consoles into a single platform with 2,900 playbooks, the company can triage incidents in seconds, a process that previously took hours. This approach allows security teams to respond to threats in real time, minimizing operational disruptions and potential financial losses while maintaining compliance and continuity across production environments.
flores and renaud warn that Mexico recently became the most targeted country in Latin America for cyberattacks, surpassing Brazil. They stress the importance of implementing AI-assisted defenses alongside human expertise, including continuous monitoring, least-privilege access, comprehensive observability of AI systems, and rigorous
incident response drills. These measures ensure organizations are not only prepared to detect threats but capable of mitigating them effectively.
Key performance indicators for AI-assisted cybersecurity include time to detect and respond, notification speed, and the effectiveness of automated remediation processes. renaud and flores emphasize that while AI enhances cyber defense capabilities,
human expertise remains essential for validating threats, configuring responses, and conducting forensics.
Looking ahead, T-Systems anticipates that AI-driven cyberattacks will intensify in 2026 and 2027. Organizations that integrate AI tools with skilled security teams and robust processes will be better positioned to protect digital assets, prevent operational disruptions, and respond to increasingly complex threats.
INVESTMENTS THAT MATTER: STRATEGIES FOR BUSINESS PROTECTION
The industrialization of cybercrime and a growing talent gap demand a new focus on security in Latin America, shifting it from a cost center to a fundamental strategic investment.
“It is essential to maintain alignment when it comes to supporting security functions, as understanding the risks, challenges, and threats is key to focusing efforts effectively,” says Ana Cecilia Pérez, founder and Director, Capa 8, during the Mexico Cybersecurity Summit 2025.
Cyber risks present an economic threat of unprecedented magnitude. Projections from Cybersecurity Ventures indicate that global costs associated with cybercrime will reach US$10.5 trillion annually by the end of 2025. Latin America faces a particularly complex environment. The region faces a sustained increase in both the volume and sophistication of cyberattacks. This scenario is aggravated by an estimated deficit of 329,000 cybersecurity professionals, according to ISC2’s 2024 Global Cybersecurity Workforce study.
“Today, companies must decide where to invest, how to avoid mistakes, and how to maximize the value of these decisions,” says Pérez. She adds that the most expensive mistake is investing too late, as resilience is directly linked to timely investment decisions.
This confluence of factors places the region in what could be defined as a “risk incubation period.” Although the average cost of a data breach in Latin America is about US$3.22 million, lower than the global average, this figure can be misleading. Leading risk indicators, such as the 15% increase in regional victims named on extortion sites, suggest that the actual risk is escalating rapidly. The calculated cost of cyberattacks in the region is likely attenuated by a less stringent regulatory framework and potential underreporting of incidents. This masks a latent vulnerability that, if unaddressed, will result in significantly higher financial and operational costs in the medium term.
In response, the cybersecurity market in the region is projected to grow from US$21.6 billion in 2024 to US$40.9 billion by 2033, reflecting a growing awareness of the need for investment. “Cybersecurity should not be seen as an expense but as an enabler of business continuity and growth,” says Israel Gutiérrez, CISO, Gentera. Separating cybersecurity from business operations is unjustifiable, he adds: “Sooner or later, everyone will have to pay the price of cybersecurity, either by investing in prevention or paying for the damage.”
“Executives will ask: Is this generating value or saving money? Establishing metrics that link cybersecurity to business performance helps justify investment and strengthen leadership support.”
Rommel García Cybersecurity Advisory Partner | KPMG Mexico
Phishing has consolidated itself as the most frequent infiltration method, responsible for 16% of data breaches globally, reports IBM. However, malicious insider attacks represent the costliest vector, averaging US$4.92 million per breach, which highlights the criticality of internal security controls. In parallel, supply chain compromise is the second most expensive vector and the one that requires the most time to contain. This mode of attack has seen an alarming increase in Mexico, where 68.8% of organizations reported being victims of these attacks in 2024.
“We must identify the core of the business: what must be protected,” says José Treviño, CIO, Dicka Logistics. He emphasizes that beyond direct financial costs, reputation damage is often more expensive than fixing a breach. “Use business-aligned metrics to justify cybersecurity investments, and relate them to headcount, costs, and revenue impact,” he adds.
Given this landscape, the allocation of limited resources must be based on a structured framework. The national Institute of Standards and Technology’s ( n IST) Cybersecurity framework offers a methodology to align investments with business objectives and risk tolerance. The process involves defining a security profile, establishing a desired target profile, and, through a gap analysis, identifying and prioritizing the security initiatives with the greatest impact. This approach allows security leaders to justify investments to senior management using the language of business risk, rather than purely technical metrics.
Evidence shows that investment in certain areas generates a significantly higher return. The application of AI and automation in security operations is the single most impactful
investment. IBM shows that organizations that extensively adopt it save an average of US$1.9 million in breach costs. Given that 68% of breaches involve a human factor, investing in continuous employee training and awareness programs directly addresses one of the main causes of incidents. finally, the implementation and regular testing of an Incident response (Ir) Plan can reduce the costs of a breach by an average of 58%.
“Every company should update its cybersecurity strategy every three years, including risk assessments, business impact analysis, and contingency panels,” says rommel García, Cybersecurity Advisory Partner, KPMG Mexico. “Executives will ask: Is this generating value or saving money? Establishing metrics that link cybersecurity to business performance helps justify investment and strengthen leadership support.”
Looking toward 2026, investment trends are shaping up around three main axes. first is the AI arms race, where the technology is both an attack tool and a pillar of defense. Deep Instinct’s Voice of SecOps 2024 report indicates that 59% of professionals cite AIpowered social engineering as a primary threat. “Shadow AI,” or the unsanctioned use of AI tools, is already a factor in 20% of breaches, demanding investment in the governance of this technology.
Second, a paradigm shift is observed from reactive defense to Threat Exposure Management, a proactive approach focused on remediating risks before they are exploited. finally, within this proactive approach, Identity Exposure Management (IEM) emerges as a critical area. Since stolen credentials remain a primary cause of breaches, IEM, which focuses on protecting exposed identities, could be a strategic investment with a potential return of 321%, according to forrester.
The future of cybersecurity in Latin America will depend not only on technological capabilities but also on how effectively leaders integrate resilience into their strategic, operational, and financial planning. “ r esilience equals investment; investment equals resilience,
THE RISE OF GENERATIVE THREATS: FIGHTING AI WITH AI
The advent of Generative AI has caused a 237% increase in advanced cyberattacks that evade traditional defenses, rendering legacy Secure Email Gateways (SEGs) obsolete, reports Abnormal AI. This new paradigm of AI-driven threats demands a fundamental shift toward defensive strategies based on human behavior analysis to protect corporate assets.
“Some individuals have always wanted to be attackers, but now, with AI, they have the means to carry out attacks more easily,” said fernando Villalobos, Country Manager Mexico and CCA, Abnormal AI, during the Mexico Cybersecurity Summit 2025.
The attack vector has evolved significantly. Historically, email threats fell into two main categories. The first, known as Spray and Pray, involved the mass sending of nonpersonalized and unsophisticated emails, hoping a small percentage of recipients would interact with the malicious content. Later, Socially Engineered attacks emerged, which were much more effective due to their personalized and sophisticated nature, but required a considerable investment of time and effort from the attacker.
Generative AI has removed this barrier, merging the massive scale of the first method with the personalization of the second, explains Villalobos. Attackers now use AI tools to create and send highly personalized malicious emails at scale with minimal effort. According to research from Abnormal AI, these attacks are five times more effective than those generated by humans and 50 times more cost-effective for cybercriminals.
“Abnormal AI can be seen as a “superhuman agent” that collects, organizes, and correlates information to make decisions and remediate threats in seconds, tasks that would be impossible for a human analyst”
Fernando Villalobos Country Manager Mexico and CCA | Abnormal AI
The problem is compounded because these modern attacks lack traditional Indicators of Compromise (IOCs), says Villalobos. An AIgenerated email may not contain malicious links or attachments and can successfully pass sender authentication tests like SPf, DKIM, and DMArC. Consequently, 96.9% of security professionals acknowledge that traditional defenses are ineffective against these new threats. This scenario has contributed to cybercrime losses of about US$53 billion from Business Email Compromise (BEC) attacks, reports Abnormal AI.
A new Defensive Paradigm
To counter this new category of threats, it is imperative to adopt a defensive approach that is also AI-native. The new strategy is to fight AI with AI, using advanced systems that can discern malicious intent through behavioral analysis rather than relying on predefined signatures or rules.
“Generative AI attacks are faster, more effective, and more profitable. We use good AI to fight bad AI, reducing the margin of error,” says Villalobos.
A modern security architecture must be AInative and API-based, as opposed to legacy gateway-based architectures. This new model is based on three pillars:
1. Human Behavior Modeling: Instead of looking for known threats, this approach analyzes over 50,000
signals to build a behavioral profile of each identity within an organization, including employees, vendors, and customers. These signals range from communication patterns and tone to sign-in geography, devices used, and vendor billing cadence.
2. AI-Based Anomaly Detection: Once a baseline of normal behavior is established, AI systems, including neural networks and large language models (LLMs), compare each new communication against these profiles. The goal is to identify anomalies that could indicate an attack, even if it has never been seen before. This “AI analyst” emulates a human analyst but with enhanced capabilities, correlating thousands of signals in seconds.
3. Multidimensional Defense: Protection can no longer be limited to reviewing incoming emails at a single checkpoint. A robust defense must be multidimensional, continuously
evaluating internal and external communications and adding constant monitoring of account risk to detect potential takeovers.
The implementation of a platform with these features allows for automatic attack remediation, automated triage of userreported emails and automated employee training. According to data from Abnormal AI, 76% of customers that adopt this type of platform replace their legacy SEG solutions, demonstrating the benefits of this new security architecture. The future of cybersecurity does not lie in building higher walls but in developing smarter, contextual defenses capable of understanding human behavior at scale.
“Abnormal AI can be seen as a “superhuman agent” that collects, organizes, and correlates information to make decisions and remediate threats in seconds, tasks that would be impossible for a human analyst,” says Villalobos.
2026 CYBER RESILIENCE: STRATEGIES TO WITHSTAND THE NEXT WAVE OF THREATS
The volume and complexity of cyberthreats, driven by AI and automation, are outpacing the capabilities of traditional security models. Industry experts argue that the transition from a prevention-focused approach to one of operational cyber resilience is no longer an option, but a strategic imperative.
“Cybersecurity must evolve from being a technical necessity to a strategic business decision,” said Adriana Servín, national Vice President of Cybersecurity, CAnIETI, during the Mexico Cybersecurity Summit 2025. This conceptual shift, says Servín, accepts the inevitability of an incident and focuses efforts on the organization’s ability to withstand, recover, and adapt its operations, ensuring business continuity instead of relying on notions of total prevention.
The urgency of this strategic transition responds directly to two critical factors: the industrialization of cybercrime and a persistent corporate preparedness gap.
Threat actors now use Generative AI tools to automate and scale phishing and controlevasion campaigns with unprecedented realism. This automation fuels an illicit market where corporate network access is sold as a product, creating an asymmetry where offensive AI surpasses defensive AI in maturity and accessibility.
The economic impact of this industrialization is tangible. Servín cites a report from Cyber Security Ventures that estimates the global cost of cyberattacks at US$9.5 trillion in 2024, with a projection to increase to US$10.5 trillion by 2025. “This would almost represent the third largest economy worldwide,” says Servín.
An emerging “engineering” risk adds to this immediate threat: quantum computing. Mario rivas, CISO, Seguros Monterrey new York Life, warns that although “we see them as distant,” technological advances are approaching the “day when encryption keys
break” and information now protected by traditional algorithms will be exposed.
The other factor driving the shift toward resilience is the preparedness gap. The Cisco Cyber Security readiness Index reveals that “only 4% of organizations worldwide are prepared and mature to face attacks.”
The 2025 Cisco Index details that 80% of organizations are in the ‘Beginner’ or ‘ f ormative’ stages. That same report identifies a persistent talent shortage as a challenge for 87% of companies, and notes a complex security environment where 52% admit their defenses are hindered by having too many separate security tools.
However, organizational change must start from the top, says Manuel Díaz, CISO, Huawei Mexico. “Senior leadership must engage in security strategy, understand risks and recovery, and provide governance, policies, and budgets,” says Díaz.
Strategic Pillars: from Technical to Business
This landscape transforms cyber resilience from a technical IT function into a pillar of corporate strategy. Gartner projects that by 2026, the ability to mitigate cyber risks will be a performance requirement for 50% of senior executives and 70% of boards of directors will include a member with specific expertise on the matter.
To implement this strategy, organizations must adopt business-aligned operational frameworks. Alberto r amírez, Head of Security Architecture Americas, BBVA,
explains that “the same recipe will not work for everyone.” The strategy must adapt to “the reality you are living in and the budget you are given,” he adds.
The central implementation of this model is the Zero Trust Architecture (ZTA), standardized by nIST. ZTA operates under three fundamental principles: assuming a breach, which forces internal controls like micro-segmentation to limit lateral movement; applying the least possible privilege for access; and continuously verifying every access request, eliminating implicit trust.resilience must be “completely and absolutely preventive” and based on a “complete understanding of what we are going to protect,” says José Manuel López, Deputy IT Director, nissan.
“We must train our teams to understand security, extend it across the organization, and deploy tools to counter increasingly sophisticated attacks,” says López.
Humans play a key role, as they were involved in up to 95% of security incidents in 2024. Attacks targeting people are becoming increasingly sophisticated, warns Gloria Moncayo, CIO, Provident Mexico. These attacks can now even include the “virtual kidnapping” of employees, she adds. An appropriate response requires Security Behavior and Culture Programs (SBCPs) to transform the workforce into an active defense network.
f inally, resilience must extend beyond individual organization. A comprehensive approach requires the collaboration of government, the private sector, and academia, explains Servín.