Users can and often do populate Excel spreadsheets with information that is outdated, inconsistent, and full of errors, and with formulas that deviate significantly from company-approved analytical models.
Track changes for regulatory compliance
Evaluate complexity and common errors
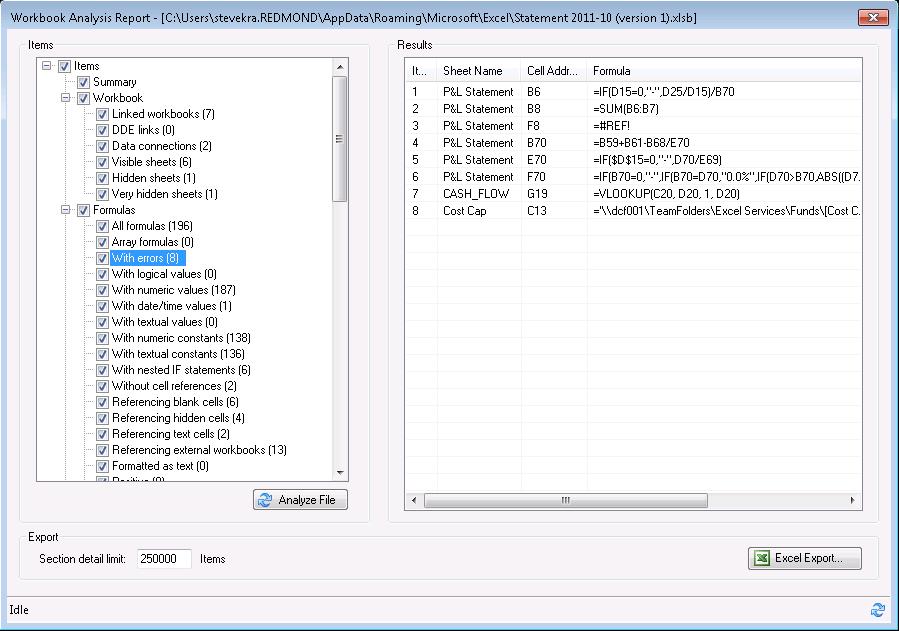
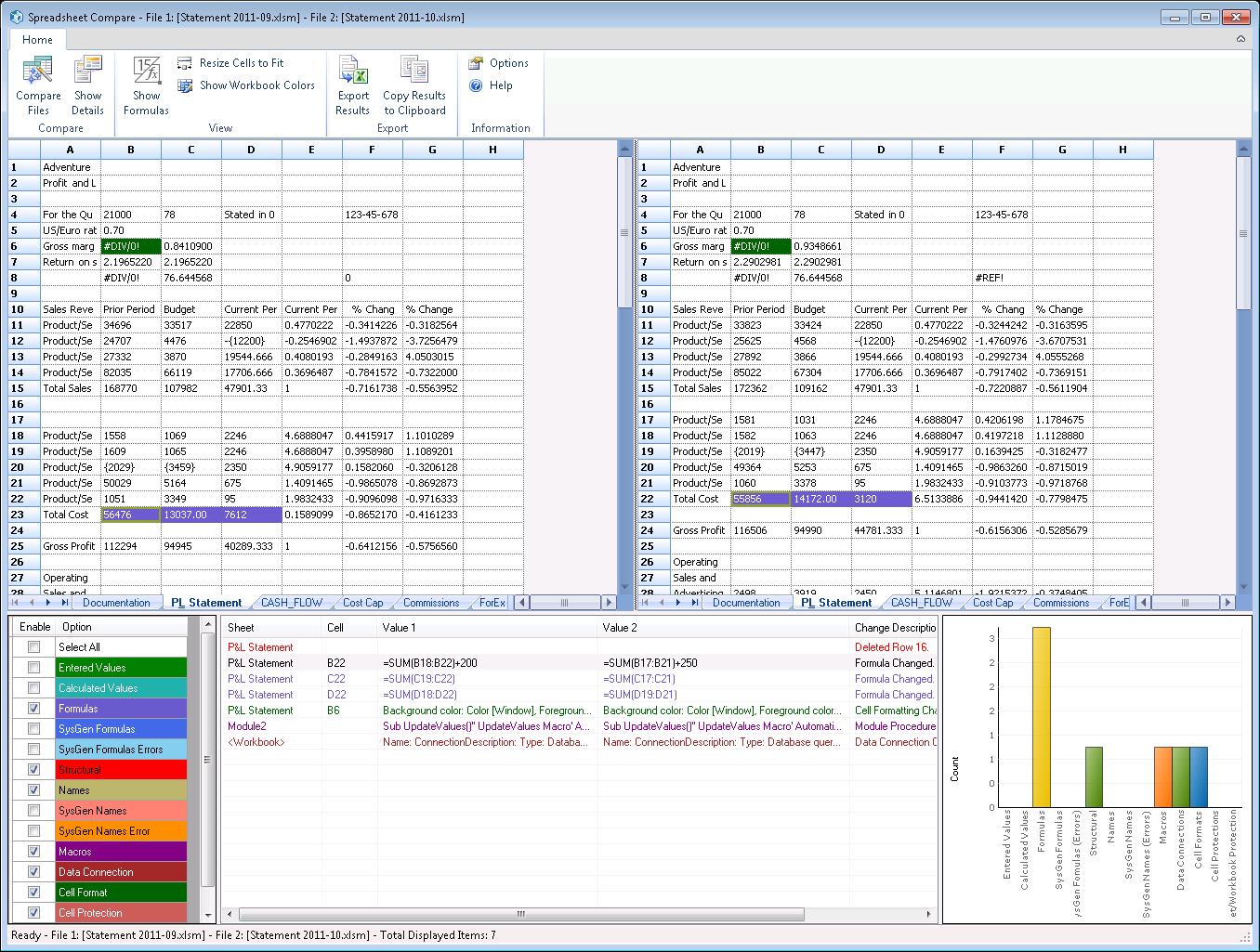

Identify external dependencies & broken links
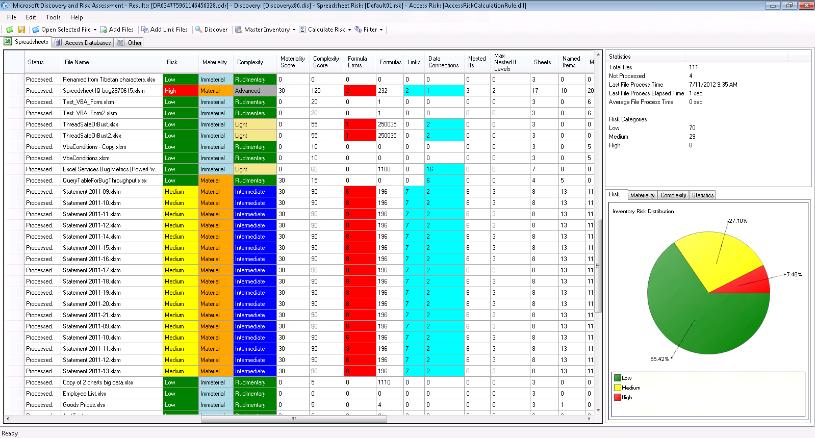
Inventory and assess risk across locations
A PolicyTip notifies you of a policy violation while composing an email


High Business Impact (HBI)
Disclosure would immediately and directly cause considerable material loss.
Examples:
• All data belonging to customer or about the customer
• Authentication/authorization credentials - username/password pairs, PINs, and hardware or software tokens.
• Sensitive PII - government-provisioned identification numbers (tax number, driver’s license), financial transaction authorization information (e.g. credit card information).
Moderate Business Impact (MBI)
Disclosure may indirectly cause limited material loss
Examples:
• PII such as name, address, phone number, fax number, and email address (note that some elements of PII are considered Sensitive PII and must be classified HBI).
• Assets labeled Microsoft Confidential
• Business plans, trade secrets, or financial results.
• Internal employee directory, purchase order data, unreleased product schedules, information on internal websites or file shares.
Low Business Impact (LBI)
Assets not falling into either HBI or MBI are classified as Low Business Impact, and have no formal classification or protection requirements.

- S/MIME /Secure Multipurpose Internet Mail Extensions/

- IRM /Information Rights Management/
Overview of When to Use IRM and S/MIME
Content Sensitivity Sent within the corporate network Sent outside the corporate network
(HBI)
High Business Impact
(MBI)
Moderate Business Impact
(LBI)
Low Business Impact
S/MIME encryption is recommended and IRM is acceptable.
IRM is recommended whenever you are concerned that the content may be inappropriately shared.
S/MIME encryption is required and IRM is acceptable.
S/MIME encryption is required and IRM is recommended.
No content protection or encryption is required. No content protection or encryption is required.
Policy details transparently displayed to end user
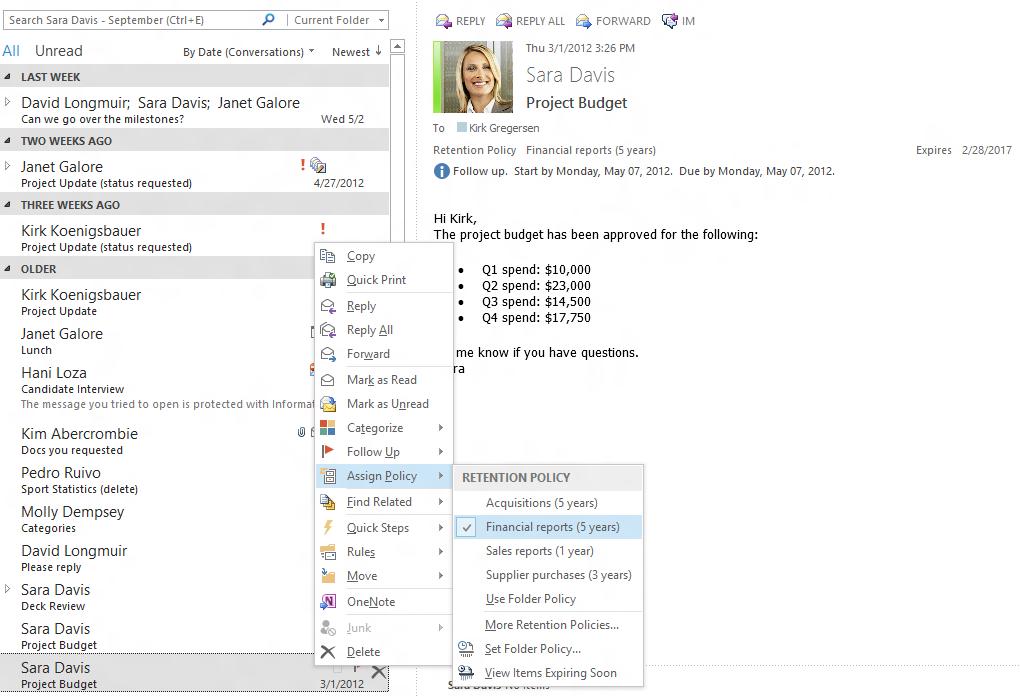
Right click to assign policy to an item, folder or to all your email

Use proximity searches to understand context
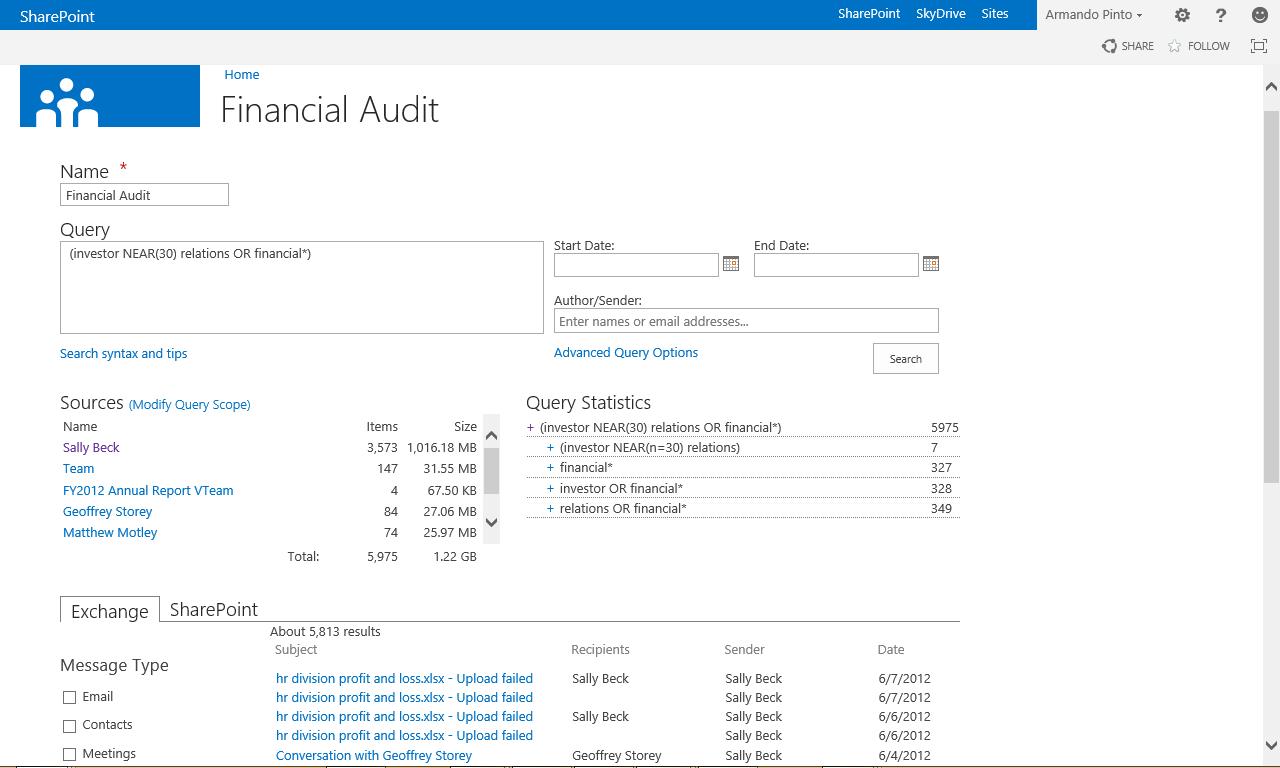
Laser focused refiners to help find the data you need
Query results across Exchange & SharePoint
Fine tune complex queries
Get instant statistics
New Office Telemetry to centrally manage client health, maintain performance, and aid migrations
Granular configuration management support with Active Directory Group Policy
Central management of mobile device settings – PIN, password policies and remote wipe
Full control over client software updating with Office 365 ProPlus
Multi-language support
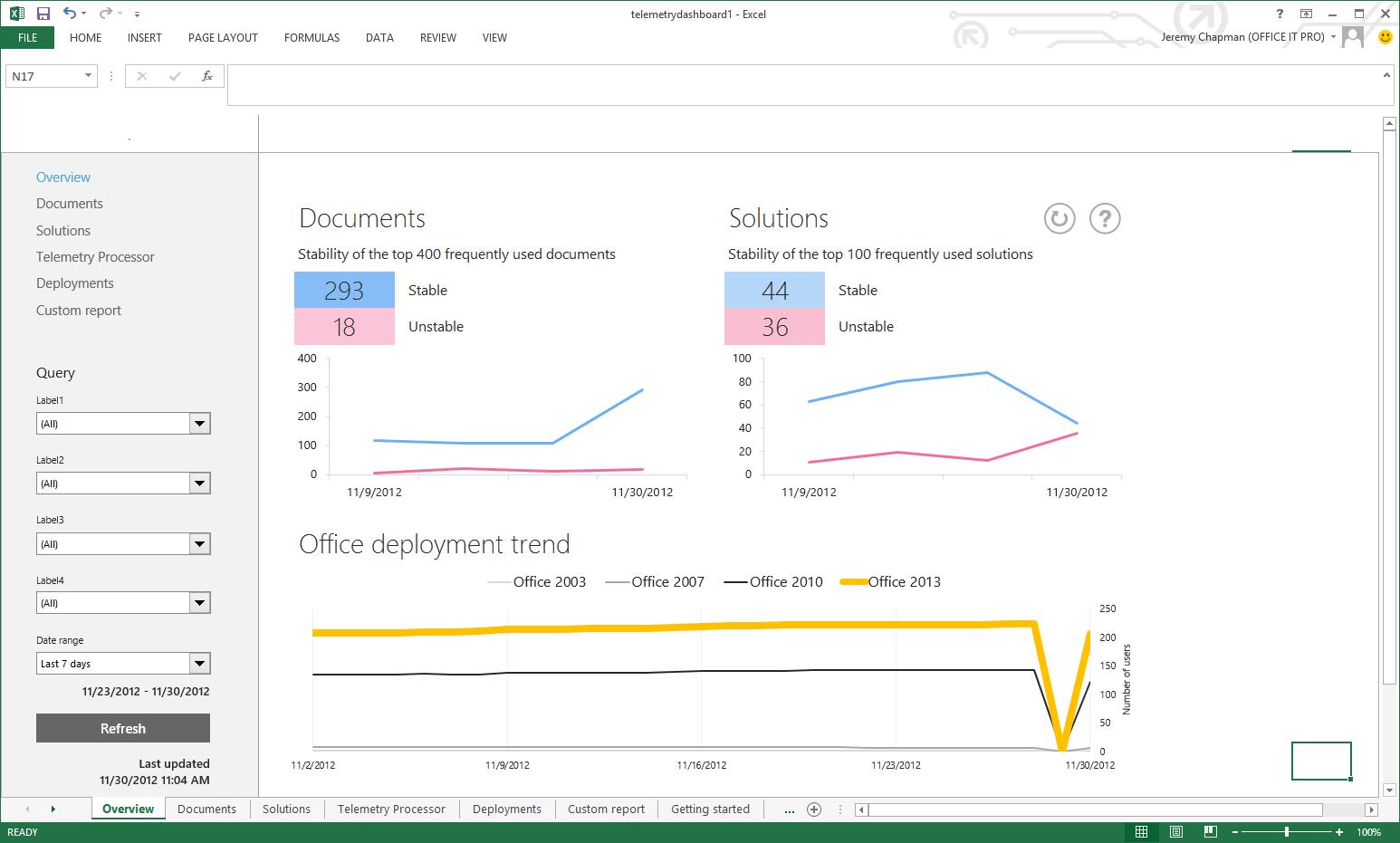
overall health and Office deployment across the organization
View and manage customizations
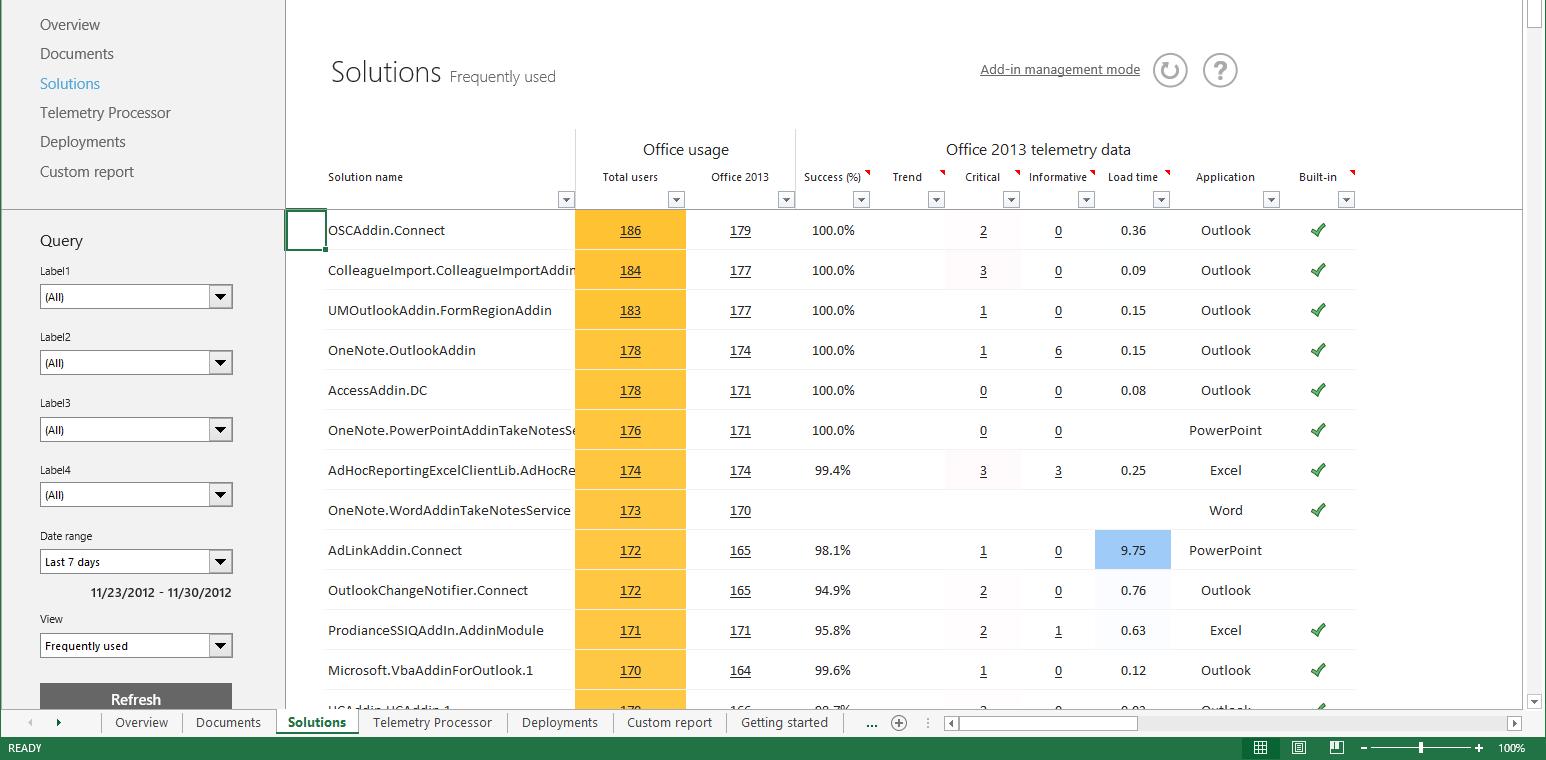
Easily combine data from any source to create fully interactive reports and insights with guided exploration
Visually discover and share insights for collaborative decision making across the organization
Manage self-service BI with control & compliance for end user created assets
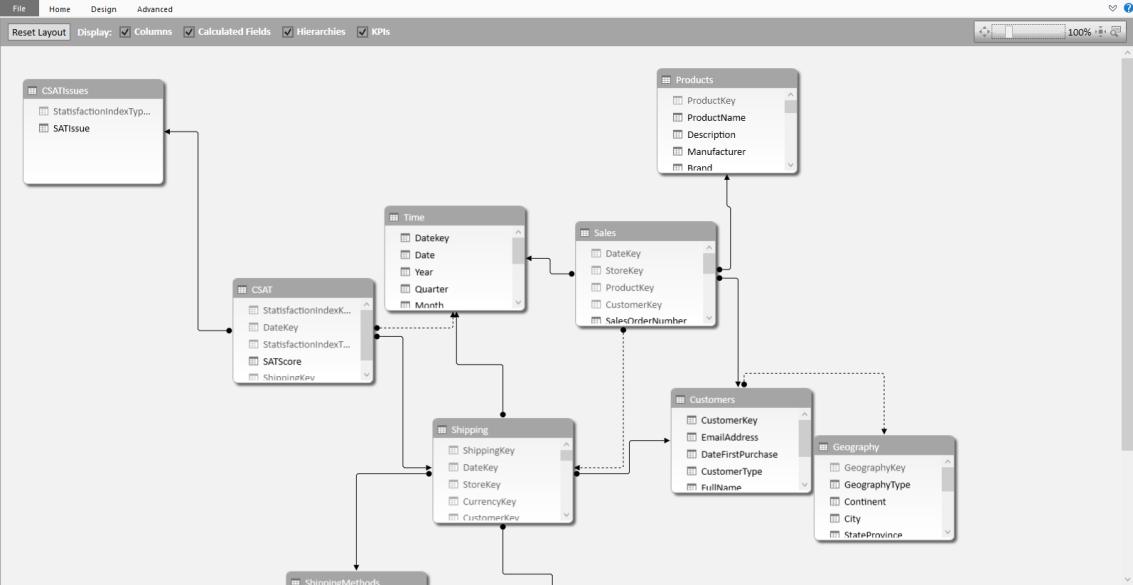
Model analytical requirements from various data sources

Define relationships, hierarchies and KPIs

Visualize your insights with interactive charts
Quickly navigate through your data
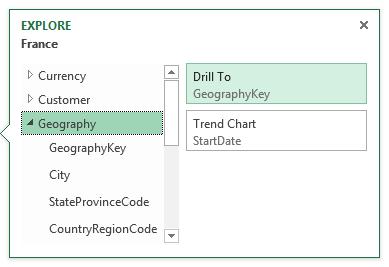

Fine tune your reports with chart and view filters

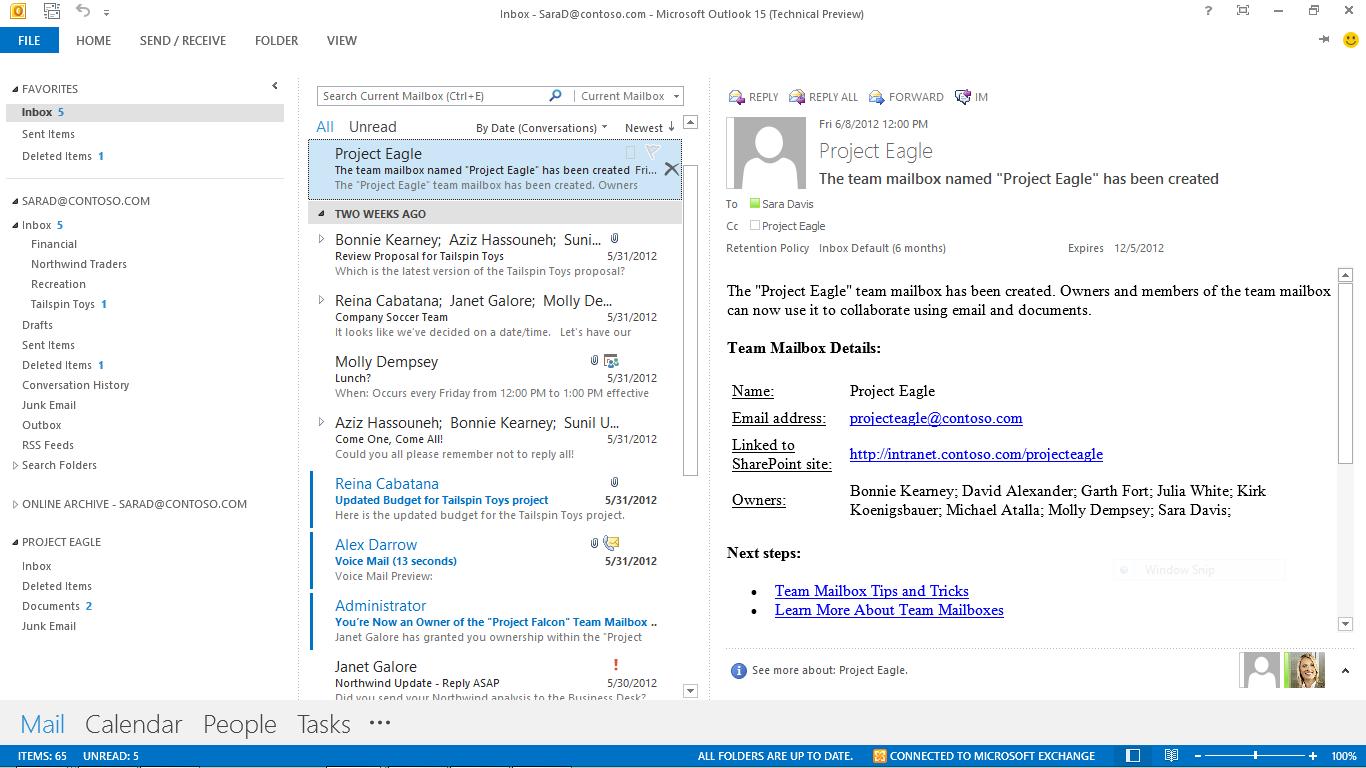
Associates an Exchange mailbox with a SharePoint site Enables users to access SharePoint and Exchange content from Outlook
Team alias keeps communications tracked