
ISSUE 2


Editor in Chief
Dear Reader, Welcome to Cyber News Global, this collaborative publication has been brought together by the UK’s leading Energy Sector Publication OGV Energy and UK Cyber Security Specialists, OSP Group Limited.
A combined wealth of experience, networks and specialists will ensure that CNG becomes a leading platform for the Cyber Sector in the UK, USA and Middle East.
Our Editor Elspeth Reilly is a talented writer with a Master of Science focused on Creative Writing from The University of Edinburgh who was also art Director for The University of Edinburgh’s creative writing anthology.


In addition, Elspeth also has a bachelor’s degree in graphic design from the American University where her activities included Vice President of the Graphic Design Club and Poetry Editor of the American Literary Magazine.
Thomas McCarthy
CEO, Cyber News Global

Kenny Dooley
Director, OGV Energy
If you have a contribution of relevant industry news please email Elspeth to editor@cybernewsglobal.com
Have an inspiring day and read on!
Cyber Centre of Excellence is Lauched
Cyber Risk and Resilience
OSP Cyber Academy join forces with Robert Gordon University
Protecting Operational Technology

By Martin Smith, MD of CyberPrism
Police Scotland Youth Volunteers
Become Cyber Aware Warriors
Same Fraud Playbook - Corporate Governance
Rois Ni Thuama Phd, Head of Cyber Governance, Red Sift
Resilience Decision Making
By Floyd Woodrow MBE
Compliance in an Ever-Evolving Cyber Threat Landscape

By Jonathan Sproule MBCS CISM CCSP CISSP
Human-Centred Security
By Chris McDermott, Lecturer, Human-Centred Security Research, RGU
Meet the Tesla Hacker Interview with David Colombo

Cybersecurity University Challenge - CNG
How to Hire a Hacker
By Amy Stokes-Waters, CCO, Capture the Talent
Enduring Cyber Resilience
By Malcolm Warr OBE, Chairman of CNI Scotland
Managing the Human Element of the Security Chain

By Dr Fene Osakwe, Global Cyber Security Leader - Best-Selling Author

Women in Cyber Security
Increasing women participation in Cyber Security
Dr Andrew Larner, Chief Executive

6 14 16 20 22 26 30 32 35 37 41 43 44 46 48
Cyber News Global
6 37 46 Contents Cyber Centre of Excellence is launched
20
THE TESLA HACKER
the
of the security chain
Operational
3
MEET
Managing
human element
Protecting
Technology
cyberscotlandweek.com/get-involved For more information visit our website: @CyberScotlandWk @cyber-scotland-week @CyberScotlandWeek 27th February - 5th March 2023 Get involved in CyberScotland Week 2023 by hosting an event and sharing your cyber expertise! CyberScotland Week, now in its fifth year, draws together in-person and online events across Scotland designed to improve organisations' and individuals' cyber awareness and resilience.
Supply Chain Security






‘the weakest link in the supply chain’




Supply Chain Security Course – This course is aimed at staff who deal with third parties within their organisation’s supply chain. With this training you will improve awareness of the supply chain cyber risk and help to implement good practice.




This course includes:




• Understand the cyber risks to your supply chain



• Understand how to establish and maintain control of your supply chain

• How to check your arrangements for confidence in your supply chain

• Recognise how to encourage continuous improvement and build trust with suppliers.
This course makes recommendations based on NCSC best practice, implementing these recommendations will take time, but the investment will be worthwhile. It will improve your overall resilience, reduce the number of business disruptions you suffer and the damage they cause.


It will also help you demonstrate compliance with GDPR, the new Data Protection Act. Ultimately, these measures may help you win new contracts, because of the trust you have sought in the security of your supply chain.


The views and opinions published within editorials and advertisements in Cyber News Global are not those of our editor or company. Whilst we have made every effort to ensure the legitimacy of the content, Cyber News Global cannot accept any responsibility for errors and mistakes. CONTRIBUTORS OUR PARTNERS Editorial editor@cybernewsglobal.com Advertising marketing@cybernewsglobal.com Design Ben Mckay, OGV Energy Events & Partnerships ceo@cybernewsglobal.com VIEW our media pack at www.cybernewsglobal.com or scan de QR code ADVERTISE WITH US
Disclaimer:
SCAN QR CODE ospcyberacademy.com
Cyber Centre of Excellence is launched
iESE is proud to announce the launch of the Cyber Centre of Excellence (CCOE) which is being showcased for the first time at the District Councils Network (DCN) annual conference in February. We believe the creation of the CCOE, which will represent a collaboration by UK public bodies underpinned by an Advisory Forum made up of some of the UK’s best brains in cyber security, will help drive forward major advances in the level of cyber protection in our local authorities and the UK public sector.
With our vision of making the UK the safest place to live, work and play online, the creation of the CCOE brings together the most knowledgeable and well-respected people in the industry to understand the cyber threats we face and how to address them. Through this expertise and member collaboration we aim to stay abreast and ahead of the growing and ever-present threat, offering peace of mind to the UK public sector.
We aim to make military grade support, products, training and advice available to the public sector by understanding what best-of-breed protection is and making this knowledge and these innovations available to procure simply at high street prices through our collective purchasing power. Essentially, the CCOE will offer a one-stop-shop to assist members throughout their cyber security journey from implementation and beyond. It does not aim to replace other organisations, such as the National Cyber Security Centre (NCSC), but aims to give practical guidance on implementing cyber security advice and standards and will also be well placed to assist if things go wrong.

You can read more about the CCOE on pages 3, 4 and 5 of this issue. To find out more about the CCOE, please go to www.ccoe.org.uk or contact us directly at enquiries@iese.org.uk
Local authorities urged to get involved with the CCOE
LOCAL AUTHORITIES AND OTHER PUBLIC BODIES ARE BEING URGED TO GET INVOLVED WITH THE NEWLY-FORMED CYBER CENTRE OF EXCELLENCE (CCOE) WHICH WAS SHOWCASED FOR THE FIRST TIME AT THE DISTRICT COUNCILS NETWORK (DCN) ANNUAL CONFERENCE IN FEBRUARY.
The CCOE will offer access to training, advice, products and services backed up by a group of advisers who will keep the CCOE abreast of cyber threat and up to date with new innovations. Any products and services offered under the umbrella of the CCOE will be tried and tested for the public sector. The initiative aims to offer military-grade protection at high-street prices through utilising iESE’s connections and collective purchasing power.
Dr Andrew Larner, Chief Executive at iESE, said: “At the moment there is a perfect storm where the complexity and frequency of attacks on local government are increasing. The innovation in the attacker is huge but our response as a sector isn’t. We know that there are gaps in our defences, especially in terms of operational technology, and we are working on plugging those gaps before they become a major issue. We need to make this business as usual and not frightening. The CCOE will sit at the forefront of best practice and act as a one-stop-shop to ensure local authorities and other public bodies are as secure as possible in this everchanging environment.”
Development of the CCOE has been led by an Advisory Forum of some of the most knowledgeable people in cyber security the country, including prominent legal experts, ex-military and ex-police personnel who have worked and continue to work in protecting the security of the country. “By synthesising and continually synthesising their knowledge and through member collaboration we will increase our ability to stay ahead of the game. If you want protection that is five years ahead in the opinion of those who protect the national security of the country, then get involved,” Dr Larner added.
Council leader shares cyber learning


IESE HOSTED A STAND AT THE RECENT ARAB INTERNATIONAL CYBERSECURITY EXHIBITION AND CONFERENCE IN BAHRAIN WHERE THE CENTRAL THEME WAS EMPOWERING GLOBAL COOPERATION IN CYBER SECURITY.
Councillor David Tutt, leader of Eastbourne Borough Council and Chairman of iESE attended alongside Dr Andrew Larner, Chief Executive at iESE. Cllr Tutt said there were some key messages he had taken away from the conference regarding local government. First was the need to raise awareness of the level of risk being faced and for the sector to stay regularly updated about new and emerging threats. Secondly, he said the conference highlighted that collaboration would be key in future on both a global and national level.
“What we need globally is to collaborate on the things that have gone wrong. Organisations tend to close ranks when something happens – we don’t want to say we’ve been attacked or that we paid a ransom or what the consequences were. We need to share that information if we want to protect each other. A key takeaway for me from the conference is that there is an enormous need for universal standards across the industry and adoption of those on a global basis,” he explained.
Cllr Tutt said a demonstration by an ethical hacker on a Tesla car showed how people with a little bit of know-how can cause issues for malicious purposes, fun or financial gain. “The UK local government has 10,000 cyberattacks a day. We have seen the impact on some local authorities, and it is not just the financial impact, although that is immense and runs into millions, it is the loss of data and personal information of residents getting out into a wider domain and the impact of not being able to run your services for your residents or not being able to run payroll for your staff,” he explained.
Cllr Tutt said the conference had further opened his eyes to the level of risk faced by UK public authorities. However, he added that he remained hopeful for the future due to the creation of the Cyber Centre of Excellence (CCOE) and its commitment to helping protect local authorities and the public sector from cyber risks.
i
@LaverdaJota
Cyber Centre of Excellence cybernewsglobal.com 6
Dr Andrew Larner, Chief Executive
Keeping your organisation secure
The Cyber Centre of Excellence (CCOE) is an initiative aimed at all local authorities and UK public bodies to help them stay abreast of cyber threats and give them access to easy-to-procure military-grade protection at high street prices through collective purchasing power. It will be able to assist with the full remit of what an organisation needs to do and know to stay as cyber secure as possible.
We know that navigating an ever-changing cyber security landscape is difficult for local authority leaders with many competing priorities and limited budgets. That is why the cyber security industry is coming together to create the CCOE – an initiative underpinned by an Advisory Forum of world class experts to help you navigate cyber security for your organisation.
The CCOE is a place for organisations to collaborate and share knowledge of threats. It will also act as a one-stop-shop to help those involved in cyber protection understand what their unique risks are and how to best tackle them.

Kurtis Toy CISSP, Managing Director of Onca Technologies, is a Virtual Chief Information Security Officer (vCISO) who has been appointed as the Convenor of the CCOE. He has been working alongside iESE to develop the Cyber Centre of Excellence (CCOE) and ensure the Advisory Forum represents the range of skills needed for a cyber and data secure organisation. Here, he outlines some of the current threats facing local authorities and terms commonly used in the cyber security landscape:
Phishing
‘Phishing’ describes an unwanted email that might contain dangerous content or have a hidden agenda. This could be in the form of a hyperlink or URL that redirects to a malicious site or downloads an attachment with hidden malicious content.
Multi Factor Authentication (MFA)
When logging in, we use at least one factor to identify ourselves, such as a password or PIN, through a smartphone or a secure USB key, or via a fingerprint or facial recognition. Multi-factor Authentication uses at least two of these methods to log in, helping prevent password compromise.
Zero Trust
‘Zero Trust’ is a term a used for both security models and network architectures. In both
cases, the main concept is “never trust, always verify”. This means all devices, access or identities should not be trusted by default, even if they were previously trusted or are connecting through a known network or location. Zero Trust is often implemented to promote strong verification processes that are continually re- examined and re-established and provide minimum access privileges.
Zero Day
Although this sounds the same as Zero Trust, it is not directly related to Zero Trust security or architecture models. A ‘Zero Day’ vulnerability is a security flaw that has been discovered but there is no security patch for it yet. Once discovered, Zero Day flaws are often exploited very quickly so it becomes a race against time for the software provider to develop and distribute a security patch.
Layered Approach
A ‘Layered Approach’ is a term often used within information security. Whilst it sounds like this means one tier of security being layered on top of another, it really means multiple solutions should be put into effect to defend against the same or similar issues. The idea is to build a suite of defences to act as contingency plans for one another and should include security tactics for people, processes, and technology. The best approach is to have a failover for every avenue possible and review your security controls on an ongoing and regular basis.
Ransomware
Ransomware is a type of malware, malicious software, that blocks access to the victim’s data and threatens to keep it unavailable or even delete it unless the victim pays a ransom to the attacker. This is a very common type of attack so it’s highly important to take every possible precaution against them. Defences against ransomware include: adequate training for all staff, including scenario training; technological defences such as antimalware, email protections and even AI; ensuring backups are maintained and immutable (see below);
updating software regularly to ensure patches for Zero Day vulnerabilities are in place and implementing robust access control policies.
Breach
A cyber security breach is an incident resulting in the unauthorised access of computer data, applications, networks, or devices which results in information being accessed without authorisation. A breach can cost a company a large amount of money, not just in shoring up defences to prevent further breaches but also for potentially stolen intellectual property or critical company data. If the breach also includes personal data, the ICO (Information Commissioner’s Office) must be informed within 72 hours of the organisation becoming aware of the breach. Fines may be issued under the GDPR if adequate protections for personal data were not in place.
Nation State Threats
Cyberattacks of this nature are initiated and sponsored by countries or geopolitical groups and are referred to as Nation State Threats, which aim to disrupt infrastructure, business, government and military. These types of attack can be particularly difficult to identify as the attackers often shift blame to cyber gangs, other foreign entities or hacktivist groups.
IoT and OT
IoT denotes the Internet of Things and includes technologies such as machine learning, machine-to- machine communications, big data, sensor data and other data collected on automated devices.
OT denotes Operational Technology and defines a specific category of hardware or software that functions to monitor and manage the performance and operation of physical devices. OT systems often support critical infrastructure and industrial operations.
Immutable Backups
An immutable backup is a copy of data that cannot be altered, deleted or changed in any way once the back-up has completed, not even by system administrators. This type of back up can be critical when a company needs to recover or restore data after it has been lost or damaged, whether through a cyberattack or a natural disaster.
Cyber Centre of Excellence 7
Meet the CCOE Advisory Forum
The CCOE’s goal is to create an entirely new level of protection in the UK and help the public sector become resilient against cyber threats. A shared service in the best traditions for local public services ensures that we all have the best people, the best technology, and the best protection. Our team have unparalleled experience, having run the UK’s military cyber offence and defence capability, having built the defences of the Bank of England, and also hold clearance to work on national cyber defence infrastructure.
Sitting behind the CCOE is an Advisory Forum of some of the UK’s leading experts in cyber security. This group will keep the CCOE up to date with threats and abreast of new innovations. Here they share their biographies and their thoughts on the CCOE:


Kurtis Toy
Kurtis Toy is a Virtual Chief Information Security Officer (vCISO) who has been appointed as the Convenor of the CCOE. After gaining an MSc in Biology he worked for an oil servicing company where he ended up working in IT. He became responsible for the IT information security in the company, leading to him becoming Global IT coordinator. He then gained an MSc in Information Technology, next becoming Global IT Team Leader before leaving to establish his own company in 2016. Further qualifications he has gained since include becoming a GDPR Foundation and practitioner (Data Protection Officer), ISO 9001 internal auditor training and ISO 27001 lead implementor. He is also a CISSP (Certified Information Systems Security Professional). He describes the CCOE as giving local authorities access to an umbrella of protection akin to a “validated Google of cyber security knowledge”.
Major General Martin Smith
Major General Martin Smith
CB MBE is the Managing Director of CyberPrism, a cyber security company which protects Operational Technology (OT) and IT in the UK and internationally.



Before joining CyberPrism, Major General Smith had a 33-year career in the Royal Marines, becoming Commandant General of the Royal Marines. He commanded the UK’s Amphibious Force and led the UK’s maritime counter terrorism force. He also founded the unit known as 30 Commando Information Exploitation Group. Major General Smith is pleased to be part of the CCOE Advisory Forum. “CyberPrism fills a gap in that there is very little knowledge and experience in operational technology in the marketplace. Playing our part in the CCOE helps fulfil the full range of services
needed by local authorities to address their cyber vulnerabilities. The CCOE is an initiative in which no single company is pretending to be able to do everything. It is a joint force of a range of experts in their own fields which will work for the good of the public sector.”
Dane Clackworthy
Dane Clackworthy is Head of Business Development and Sales at CyberPrism, a cyber security company which protects Operational Technology (OT) and IT in the UK and internationally.

Before joining CyberPrism, he had a 20-year career in the Royal Marines where he gained extensive experience in radio communications and information assurance. His positions included being Yeoman of Signals, the Chief Communication Manager for the UK’s Response Force Task Group. The RFTG was a Very High Readiness force of 1,500 personnel that could deploy worldwide in 5-days. More recently, he was the unit Data Protection Officer, IT Security Officer and was project lead for the aviation CIS infrastructure plan for the Queen Elizabeth-class aircraft carrier.
At CyberPrism, he continues to enjoy relaying technical information between stakeholders in plain language that everyone can understand. “My role in the CCOE will be to keep the forum up to date on best practice in securing OT in a clear concise way that brings real value. There is a general lack of awareness about OT risks. We look forward to helping local authorities and public service organisations take the necessary steps to understand and secure their vulnerabilities.”
Irene Coyle
Irene Coyle is Chief Operating Officer at OSP Cyber Academy, a managed service provider of cyber, information security, data protection training and education programmes. She joined OSP Cyber Academy after a 30-year career in the police force in a variety of roles, including that of Chief Inspector for recruitment within Police Scotland.
During her career in the police force, Coyle held various roles which centred on protecting people’s data, including as Detective Inspector of the Public Protection Unit at Grampian Police. In this position she was Project Manager of the Grampian Police Vulnerable Persons Database, a project which was then rolled out across Scotland. Coyle is also a Data Protection Officer, a NCSC Certified trainer and holds a teaching degree. OSP Cyber Academy has joined with the CCOE to provide member access to its suite of training tools.“To be involved with the CCOE is great. This new group wants to provide the best that it can for local authorities which is admirable. It is not about driving high profit for the experts involved, it’s about driving the cyber resilience capability across communities. I am excited to see where it goes and being part of building cyber resilience across the public sector.”

Thomas McCarthy
Thomas McCarthy is the founder and Managing Director of OSP Cyber Academy. He has previously held various roles in training auditing and safety, including several positions in the energy sector. As someone with a wide range of industry contacts and knowledge, McCarthy has been instrumental in helping to establish the advisory forum for the CCOE. OSP Cyber Academy are a UK Government- certified managed service provider of cyber, information security, data protection training and education programmes. The company has joined with the CCOE to provide its members access to its suite of training tools.
Cyber Centre of Excellence cybernewsglobal.com 8
“In the last five years I have been involved with just about every cyber organisation there is in the UK and overseas. The CCOE is one that has been designed and set up to make a difference and to deliver, as opposed to just talk about delivering. The problem with cyber is that it is an ever- evolving threat landscape and things change so rapidly that the only way you can stay resilient is by keeping up to speed with what is going on. I think the CCOE will do this and has the capability to deliver for all public sector bodies.”

Sandip Patel KC
Sandip Patel has been a Barrister for more than 30 years and was appointed Queen’s Counsel (QC), which is now known as King’s Counsel (KC), more than ten years ago. He became involved in cyber security law after being asked to prosecute several cases for the Crown Prosecution Service. His cases have included that of Glenn Mangham who stole Facebook’s source code from his bedroom in North England using an ordinary desktop computer and Seth Nolan-Mcdonagh, the boy who ‘almost broke the internet’. Patel is also Director of cyber security consultancy Quantum Resilience International and Chief Legal Advisor at OSP Cyber Academy. He is pleased to be involved with the CCOE to contribute knowledge of legal compliance and advise how this might evolve by looking to other countries. However, he warns that legal compliance is the minimum organisations should aim for. “Regulatory compliance is not cyber security in my view. We know the public sector is extremely vulnerable and I am pleased to play a part in helping protect these organisations.”

Niall Burns is one of the founders and Chief Executive Officer at the specialist risk mitigation, business intelligence and loss prevention company Subrosa Group. He started his career in the Royal Marines and then subsequently within UK Special Forces Communications where it was instilled that sensitive information should be delivered in a direct and confidential manner. Subrosa has been helping keep people safe for more than 25 years, including advising clients on keeping data safe. Cyber Security services are now a large part of their remit. Its services include penetration testing of systems, networks, and web applications, identifying vulnerabilities in internal and cloud-based systems, and identifying configuration vulnerabilities. It can also help clients review and assess processes and policies. “Something like the CCOE where you have experts who are not confined by purchasing protocols will be invaluable to the public sector. It will be able to look at the pros and cons and it won’t be handcuffed to say you have to do this, this and this. Use us as the experts to check you are getting fit-for-purpose and quality products because a lot of people are mis-selling out there.”
Rois Ni Thuama
Dr Rois Ni Thuama is Head of cyber governance for Red Sift, one of Europe’s fastestgrowing cybersecurity companies. She works with key clients across a wide market spectrum including governments, legal, finance, and banking, to spread a contemporary understanding of cyber threats, risks, liabilities, and resilience across diverse audiences and stakeholders to drive effective change. In 2022, Dr Ni Thuama was part of the team of cybersecurity experts tasked with the revision of NATO’s cybersecurity curriculum as part of the Partnership for Peace Consortium’s (PfPC) Defence Education Enhancement Program. She also presented on the legal implications at The Impact of Artificial Intelligence on Future Conflicts Conference in Washington D.C. Ni Thuama is also contributing editor with PCPro, focused on significant cyber threats, the latest trends, risk management and building in defensibility for firms. She is also a regular keynote speaker at cyber conferences.

Colin
Colin Jupe is CEO of Assurity Systems, a company which provides advanced cyber security solutions to a variety of sectors including local government. He is also a qualified General Data Protection (GDPR) practitioner and the Managing Director of VXPartners, a company which helps organisations become and remain compliant with UK Data Protection law. Prior to launching Assurity Systems, Jupe held a management consulting role where he predominantly assisted technology companies with marketing and finance strategy and was also formerly Director of a marketing database and data processing company. “UK government and PLC are under attack more than ever and those in charge of local government have enormous pressures extending from budgetary and personnel issues
through to IT. Rich private organisations are poaching all the good cyber-IT professionals which means the public sector must outsource to get access to skills. The cyber protection industry is a vendor-led industry. Who can you trust? How do you know which is the best solution for your organisation? This is a difficult problem and understanding what solutions are good for today and fit for tomorrow is almost impossible without the sort of collaboration offered by the CCOE.”
David Woodfine
David Woodfine is the managing director of Cyber Security Associates (CSA), a company he started with former colleague James Griffiths in 2013. CSA began as a consultancy practice and still offers this trusted advisor service helping clients with aspects of cyber security such as assessments, help gaining certifications, incident response and general cyber road maps and development. CSA also provides 24/7 managed Security Operations Centre (SOC) services to help monitor, prevent, detect, investigate, and respond to cyber threats. Before starting CSA, Woodfine had a career spanning 28 years in the Royal Airforce, where he undertook a range of roles related to cyber security, including holding the position of Commanding Officer of the Ministry of Defence Cyber Defence Unit. “The CCOE is both an information sharing platform and a one-stopshop offering a framework of services so local authorities won’t have to go to twenty vendors, they can just come to a safe pair of hands and know that if they buy something approved by the CCOE then it is world class. We can also share intelligence on threats and lessons learned which will be invaluable to public bodies. Being part of the CCOE may stop any future attacks through monitoring and sharing information and, if the worst does still happen, the CCOE can help with key aspects of recovery and help improve the ongoing cyber security posture.”




Dougie Grant
Dougie Grant is Managing Director Europe & Global Head Incident Management at Nihon Cyber Defence. He started his career in the military and from there moved to the private sector working in IT where he became interested in cyber security. From here, he progressed into law enforcement, spending eight years as the Cyber Lead for the Police Service of Northern Ireland where he started building online investigative capability looking at the online components of crimes. He finished his public sector career in the City of London Police seconded to GCHQ and NCSC where he spent five years as a Senior Coordinator at the National Cyber Security Centre (NCSC). He remains associated to the NCSC as part of its Industry 100 (i100) initiative and holds an MSc in Forensic Computing and Cyber Crime Investigation as well as other certifications. “Opportunistic attacks are one the biggest threats we face. Anyone from the comfort of their living room can scan internet connected systems and networks globally to see if they can get in find vulnerabilities and exploit them to gain access and disrupt them, sometimes with catastrophic impacts. We have got to ensure that everything being acquired or used by the public sector is secure at its core and that is not there yet. If you are going to procure equipment or deploy technology or systems it is essential to understand the risk and threat and impacts of attacks and breaches which is something the CCOE can assist with.”
Niall Burns
Jupe
Cyber Centre of Excellence 9
Councils urged to consider OT risks
Local authorities are being urged to consider operational technology (OT) as part of their cyber security risk landscape, attacks on which could potentially result in serious health and safety incidents.
Operational Technology (OT) refers to technology used to monitor and control processes. Recent years have seen an increase in attacks on OT. The reasons are twofold: firstly, hackers have realised that OT often presents a vulnerable target and, secondly, systems are more integrated than ever before, increasing the likelihood that malware can move between IT systems and connected OT.
In May 2021, the Colonial Pipeline Company in America had to shut off its oil pipeline due to concerns that a ransomware attack on its billing system could spread to its OT network – an example of how an IT attack could compromise OT. While in July 2022, an Iranian steel manufacturer saw a hacktivist group target machinery causing a fire at its plant in an intentional direct attack on OT.
Local authorities might believe that they don’t have OT of any significance, but Major General Martin Smith CB MBE, the Managing Director of CyberPrism, a managed services company which protects Operational Technology (OT) and IT in the UK and internationally, said this is a commonly held misconception. OT that might be at risk of direct or indirect attack could include CCTV systems, traffic light systems, lifts, security-controlled doors, fire control systems, heating, lighting, air conditioning and more. In public services such as the NHS it can include equipment such as hospital scanners.
“There is a whole range of OT that local authorities won’t have addressed. The fact is that most organisations know nothing about their OT, so some form of basic assessment is a good place to start,” explained Major General Smith. “Until about two years ago those out there who wanted to hack into networks knew nothing about operational technology. They are starting to get the idea now as you can see from various attacks, such as the American Colonial pipeline attack. They now understand that attacking OT is good for two reasons. Firstly, it is vulnerable because organisations have not secured it. Secondly, if you can hack into OT, it is not just a case of stealing data, you can cause disruption. From a ransomware point of view, it becomes even more powerful. What if I stop the lift? Tamper with security-controlled doors? There is a considerable health and safety element too.”
Dane Clackworthy, Head of Business Development and Sales at CyberPrism, encouraged local authorities to take stock of their OT and look at how to protect it. “Every organisation knows that they need to secure their IT but not everyone knows about OT. There is a real gap in understanding what OT is and how we can protect it. One of the first steps is knowing what OT the organisation has. If you don’t know what you have, you can’t protect it and that is an inherent vulnerability.”
There is little doubt numbers of OT attacks are increasing. According to a report, OT Security Incidents: 2021 Trends and Analyses, the number of attacks with physical consequences in process and discrete manufacturing industries more than doubled in 2021 compared with 2020. The authors of the report predicted that ransomware-induced OT outages would triple in 2022 over 2021, stating that due to production outages and other physical consequences, attackers are realising that there is a likelihood ransoms would be paid. Stateon-state attacks are also increasing. In 2022, for example, a sophisticated malware attack attempted to destroy the Ukrainian national grid as part of the Russian and Ukraine conflict. One of the key strategies organisations can take is to segregate OT and IT and introduce software which will shut parts of the network off when a threat is detected without stopping the processes from taking place. “Networks are becoming ever more connected together which means that if malware gets into one area it could pass into everything. What you need is a more closed system where you know exactly where the gateway is, and you can segregate the systems effectively,” explained Major General Smith.
Also important are systems for monitoring activity and alerting to threats, while OT cyber security training is essential for staff and board members. One thing is clear, doing nothing is not a safe strategy. “While we might not yet quite be at the point where local authorities are being targeted through OT, attackers don’t have to attack the OT specifically to cause an effect. It could be an IT attack which could filter through to OT and have serious consequences. We know these types of attack will become more prevalent,” Clackworthy warned.
Both Major General Smith and Dane Clackworthy from CyberPrism are part of the Cyber Centre of Excellence (CCOE) Advisory Forum. The company provides consultancy services, such as OT audits, and access to specialised softwareas-a-service to protect OT.
Find out more about Cyberprism: cyberprism.net
Staffs aims to be most protected cyber region
South

Operational Technology (OT) refers to technology used to monitor and control processes. While its applications frequently exist in the manufacturing sector and processes for industries such as oil and gas, it increasingly applies to any physical technology linked to software. An attack on OT can have a direct physical impact on the victim organisation, its staff or its customers. This could result in service failure but could also have related health and safety implications. Here is a brief list of just some OT a local authority may have which should be protected from direct or indirect cyber-attack:
• CCTV
• traffic light systems
• recycling plant processes
• lifts in real estate
• security-controlled doors
• fire control systems
• heating and lighting systems
• air conditioning systems
Cyber Centre of Excellence cybernewsglobal.com 10
South Staffs aims to be most protected cyber region
South Staffordshire District Council is moving further towards its goal of making its geographical area the most protected in the country from cyber-attack.
South Staffordshire implemented AppGuard in 2020 through iESE and its relationship with Assurity Systems, the European distributor of the product. Peter Shakespear, Corporate Director Finance & Resources at South Staffordshire Council, explained that the pilot would subsidise the implementation of AppGuard in one or two of its local parishes for a period. He said he was confident AppGuard would demonstrate its ability to prevent security breaches.
South Staffordshire Council is convinced by the technology having seen many other local authorities hit the headlines in recent years due to attacks which have caused high levels of damage to operations, resulting in high spend in recovery costs and untold reputational damage with customers. “Other local authorities have not had this protection and it has cost them millions of pounds,” said Shakespear, “For our parishes, this gives a solution that is integrated and matched with the district. After the trial we will hopefully have 27 parishes asking: Where do we sign?”
In addition to showing that AppGuard can prevent cyber-attacks, Shakespear said the trial should also demonstrate that the parishes taking part could potentially scale back some of their other protection, allowing some savings to be made.

As part of its objective to make South Staffordshire the geographical area most protected in the country from cyber-attack, the district council is also offering local businesses access to AppGuard at preferential rates through its business place partnership. “It is great to be able to go to a small parish council or a small business and tell them they can have a level of cyber security they never imagined and that we can make that accessible through iESE. Signing up is common sense. For me this isn’t a nice-to-have, this is the reality of the 21st Century. Cyber-attacks are increasing by the day, and we have to be one step ahead. Other solutions on the market are one step behind. It is an absolute essential,” he added.
Brad Collier, an iESE Associate who has been working with South Staffordshire on its implementation of AppGuard, praised the council for its foresight. “iESE set a mission five years ago to make the UK the safest place to live and work in Europe one local authority at a time. South Staffordshire are an innovative council making this a reality. The pilot is going to open the eyes of the parish councils as to how simple it is to protect themselves and their organisation. It is not complicated or expensive. New customers need to spend a short amount of time doing a survey and then installing the licence is a 20- minute process. In less than an hour it is possible to take away the pain that might occur from a targeted cyber-attack that could disrupt your whole business.”
What is AppGuard?
AppGuard is an endpoint cyber security solution which will protect your systems from all threats –even the never-seen-before attack known as ‘zeroday’. Developed in the US defence environment, it has recently become commercially available in the UK and is being offered to local authorities by iESE through a partnership with its European distributors, Assurity Systems Ltd.
AppGuard offers the required step-change in endpoint and server defence because it operates in an entirely different way to traditional solutions. The patented technology monitors everything and trusts nothing, meaning it offers full protection without the need to detect previously known exploits.
iESE has teamed up with Assurity Systems Ltd to bring this exciting, transformational technology to the UK’s local government environment. We have secured highly preferential rates (discounts exceeding 50 per cent) meaning you can benefit from this technology for around £45 per annum per endpoint for a fully-managed solution, including licence fees. A server version is also available and if you need extra monitoring and support, we have also secured preferential rates on Security Operation Centre (SOC) services.
Bringing AppGuard to schools
Another organisation set to trial AppGuard is Gloverspice School, an independent special school situated on a care farm in the Midlands. Headteacher, Lynne Duffy, has become concerned about the risk of cybercrime and the potential impact on students following an attack on a nearby local authority maintained secondary school.
Although her school isn’t large, the headteacher realises cyber-attacks are indiscriminate, highlighting that the school would not be able to afford to pay a ransom. Although the organisation has existing protection, she believes schools are vulnerable due to lack of expertise, time and budgets. “Taking part in a trial is a really good opportunity. I think cybercrime is quite frightening and that local authorities need to do more training with headteachers on cyber security. A lot of the information available is not specific for schools,” she said.
She would like local authorities which subscribe to AppGuard to offer their preferential rates to schools too, including special schools such as her own. “Hopefully local authorities signing up to AppGuard will allow schools in their area to buy into it as well, including those they use for specialist placements. My students’ fees are paid by the local authority so they should be supporting schools like ours as well as those which are local authority maintained,” she added.
Find out more: www.iese.org.uk/appguard
Cyber Centre of Excellence 11
TheCyber Centre of Excellence (CCOE) has teamed up with UK Government-certified cyber security and awareness training provider OSP Cyber Academy to provide access to a wide range of cyber security and data protection training programmes.
Through the CCOE, local authorities and other public sector bodies can access OSP Cyber Academy’s Cyber/Information Security and Data Protection training, which is National Cyber Security Centre (NCSC) certified. Training days, such as the Cyber Risk & Resilience Board & Executive Awareness Course, will be offered in person for executives, while an online system will also be available to allow an organisation’s wider employee population to access various online courses. These will include: OSP’s GDPR Staff Awareness Course, Cyber Security Staff Awareness Course, Phishing and Social Engineering Course and Mobile Device Security Course and the newly developed Supply Chain Cyber Awareness Course.

These courses will help reduce risk, improve cyber resilience and demonstrate compliance
CCOE provides access to NCSC-accredited training
Local authorities are being urged to consider operational technology (OT) as part of their cyber security risk landscape, attacks on which could potentially result in serious health and safety incidents.
with legal requirements. Thomas McCarthy, Managing Director at OSP Cyber Academy, said training and awareness must start at the top of the organisation but that it was also vital this filtered down to the wider employee population for maximum benefit.
One reason is that cyber risk is greatly increased by employee error, such as unwittingly clicking on an unsecure link. Irene Coyle, Chief Operating Officer at OSP Cyber Academy who is one of the company’s training leaders, said education and awareness were important and that this must be continuous due to the rapid and ever-changing nature of cyber threat. “Public authorities are a real target. Cyber attackers are looking to be disruptive and to cause chaos. Having strong policies and training in place can greatly reduce risk exposure.”
However, she said it was vital cyber security and data protection were not viewed as ‘box-ticking’ exercises. Even where senior management can demonstrate compliance, such as by having a data protection policy in place, Coyle highlights that this is not enough – staff have to be aware
Increase diversity to fight cyber crime
Local authorities are being encouraged to look at the diversity of their workforce to help tackle cyber-crime against their organisations.
While there is a moral case for diversity and equality in the workplace, a more diverse and inclusive workforce can also help strengthen your cyber security defences, experts believe.

Sandip Patel KC is a Barrister who is part of the CCOE Advisory Forum. He hopes the CCOE can help local authorities diversify their teams with cyber responsibilities to help give broader insight into cyber-crime in their organisations: “When you go along to cyber conferences the attendees and speakers are 98 per cent male and white and the industry is heavily dominated by ex-military and ex-M15 personnel and law enforcement. There are 7000,000 vacancies in the United States alone in cybersecurity –they can’t all be filled with men with a certain background,” he said.
Patel is optimistic things are starting to change, noting greater evidence women of in key roles. He also believes neurodiversity within cyber teams is important when thinking about the adversary you are facing. “In my experience of prosecuting, those conducting cyber-crime tended to be young men, but they don’t fall into the classical category of a criminal. These are often sophisticated individuals who are often brighter than you –often on a genius level,” he noted.
Irene Coyle, Chief Operating Officer at OSP Cyber Academy, is also on the CCOE Advisory Forum. When working in police recruitment she launched the Positive Action for Women programme which aimed to uncover barriers for women. The programme was successful in
of such policies and why they are important too. “When you can show the relevant policies are in place, that is great and it has ticked the box, but is that policy known by the users of company devices, do they follow it and how do you know that they follow it?,” she asks. “The key thing is education and awareness and that must be continuous. You can have any certification you want but that doesn’t mean you are reducing the vulnerabilities your people may create.”

McCarthy said OSP Cyber Academy was providing training at the highest standard: “We are a NCSC-certified training provider, which is not something any organisation can say. We are the leaders in what we do in cyber protection training and data protection training. We also know the other organisations involved in the CCOE are all equally credible which is what makes it so exciting to be a part of.”
To find out more about OSP Cyber Academy visit: www.ospcyberacademy.com
To book cyber training at discounted rates for local public services, please go to: www.ccoe.org.uk
increasing numbers of female employees, later becoming a programme for all minority groups. Coyle now advocates for diversity in cyber through giving talks and actively challenging companies to tackle the issue.
Coyle believes increasing the talent pool of young people through apprenticeship schemes and work placements is something local authorities should consider. “This might sound ageist, but young people can be more attuned to the cyber landscape. Having a much more diverse workforce in cyber security will allow you to learn from them and try to build your defences better. You don’t know who is behind the mask because cyber- crime is a faceless crime but having a more diverse workforce will help meet the challenges you face.”
A recent report by the National Cyber Security Centre (NCSC) and KPMG, Decrypting Diversity: Diversity and Inclusion in Cyber Security, painted a mixed picture of the cyber security industry. An area where the report calls for further diversity is age, with only one in twenty respondents’ categorising themselves at between 18 and 24 years old. Jonathan Gill, a Partner at KPMG, said the UK needs a thriving cyber security sector to remain safe and prosperous. “Diversity and inclusion are fundamental to this because we need to attract and retain the best talent and foster diversity of thought,” he said.
Cyber Centre of Excellence cybernewsglobal.com 12

Digital Management of Place Cyber Risk and Resilience


For councillors and council officers the management of place for the progress and protection of its people, natural and built environment is central to their purpose. Every council’s area collective sense of place and context is unique. However, one way of thinking about how to progress the management of place in your council is to think about progressing and protecting the 5 Capitals:
• Natural capital
• Social capital
• Human capital
• Built (including digital) capital; and
• Financial capital.
The strategy that individual councils choose to grow and thrive will vary. But part of any effective and efficient strategy and delivery of
its essential services will be the digitalisation of its management of place and the essential services that the council deliver.
However, digitalisation of essential services and wider community stakeholders, creates a paradox, of both opportunities to grow the 5 Capitals, but also dangers of sustaining them. For councillors, whether in cabinet or not, and council officers, what was once something that could be delegated to IT or similar, is now central to strategy and achieving management of the place that they have the privilege to serve.

So, the challenge for councillors and officers is to develop a deeper individual and shared understanding as well as competence of why and how digitalisation can enable the
progress of your place. Whilst protecting your place and making it more cyber resilient to the risks that accompany digitisation.
This starts with councillors and officers understanding more deeply: what is going on here? So that the opportunities of digitisation can be seized, whilst managing the risks. Including understanding the value of information for investment in the 5 Capitals in your place and what must be enabled and protected to achieve your purpose and strategy.
This starts with training to provide the foundations to develop and most importantly implement effective strategy

“We lost everything. We lost connection to our telephone systems, child services and important data dating back decades. It was so catastrophic that it took us about eight months to recover.”
Mary Lanigan, Leader Redcar and Cleveland Borough Council.
Cyber Risk and Resilience cybernewsglobal.com 14
Evidence to Parliamentary National Security Strategy (Joint Committee) hearing 30th January 2023.


At a recent initiative launch at RGU’s school of Computing in Aberdeen, Wood’s Chief Information Security Officer, Malcolm Norman, endorsed the cyber awareness initiative between OSP Cyber Academy and RGU Cyber Faculty. The training initiative has been generously funded by Wood which provides vital cyber awareness induction training to every cyber student within RGU.
“ RGU has a long history of graduate employment, being one of the UK’s leading vocational institutions. In order to maintain this standard, the relationship that RGU has with companies is vital —

none more so than with Wood; this relationship is so important for RGU, as
OSP CYBER ACADEMY
JOIN FORCES WITH WOOD AND RGU TO CHANGE CYBER BEHAVIOUR
the students that gain placement, feed back their experiences into their chosen faculties, which enables RGU to shape and develop their courses. The more input that RGU can have from industry the better. There are benefits on both sides — very much a reciprocal relationship — working with industry enables RGU students to be better equipped when graduates are looking for employment. Preparing the cyber students is a perfect example of that collaboration with OSP Cyber Academy and Wood, one that RGU is very grateful for. ” said Chris McDermott, a lecturer of Computing Science and Cyber Security with a passion for human factors education.
The emphasis of this initiative is to ensure that all new cyber students have an awareness
OSP Cyber Academy, Wood, and Robert Gordon University (RGU) have joined forces to help shape the cyber leaders of tomorrow.
of cyber threats and risks as they embark on their chosen studies. The UK government has worked tirelessly to establish a standard academic knowledge path to ensure that all UK cyber students are receiving the same level of education. The Cyber Body of Knowledge (CyBOK) sets out the academic guidance that ensures all cyber students receive a structured knowledge path.
OSP Cyber Academy is an approved training provider with National Cyber Security Centre (NCSC) certified training, which reinforces the learning outcomes of their training to a UK national standard.

“ Behind every single cyber attack there is a beating heart. The bad actor is human. The victim is human. So to combat the threat, we need to understand the human risks, good cyber security is as much a people function as it is a technical function. “ said Malcolm Norman, CISO at Wood.

Cyber risks are real in the business community. The 2022 Global Risks Report which was released by the World Economic Forum found that 95% of cybersecurity issues are attributed to human error.
Without awareness or education on cybersecurity, businesses are susceptible to attack as those unaware of cyber risks are the most likely to be targeted and exploited. The same cyber risks and vulnerabilities exist for academia, especially when students are first embarking on their studies with no initial level of cyber awareness.

The final thoughts on the journey of this tremendous collaboration were echoed by former RGU Marketing student, Blair Wallace. Blair joined OSP Cyber Academy on a placement 4 years ago and is now shaping his own career path within the business community:

have worked together with cyber student placements.
“ With 5.6 million companies in UK at risk of cyber attack, there is a huge shortage of capability to meet the cyber demands required to ensure that our businesses and people are safe when online. With less than 1 in 9 business in the UK providing cyber awareness training for their staff, there is a huge shortfall in cyber education. There is a large chunk of the business community that is not raising awareness. It’s so important that every business leader should be looking to raise cyber awareness amongst their staff. For me, cyber security awareness training is essential for anyone going into the business world and for their own online safety. This is where OSP Cyber Academy can provide that critical real-life training, awareness, and education needed. ” These were just some of the thoughts of former Police Chief Inspector and now Chief Operating Officer at OSP Cyber Academy, Irene Coyle.
“ Marketing and management was my chosen degree course which is very much people orientated. People outside of cyber security would think that cyber is all about technology, numbers on a screen and servers, and to a degree that is true however cyber is very much a human factor. People just don’t realise until they are in the cyber industry, not until they have experienced a cyber attack or a data breach, which happens a lot more than you would think. It’s then that they begin to understand just how much relates to the human factor. It’s just as important to educate your workforce as it is to focus on your technology and hardware, that is something that has become so apparent to me working with so many of the clients here at OSP Cyber Academy. ” Blair is now a vital member of the OSP team, providing support as the business and digital marketing lead.
Collaborations like this do not have all the answers; unfortunately, there is NO silver bullet to solve all of the challenges that the cyber security industry faces. One thing that is critical is education and awareness, which every company should provide for its workforce to ensure that they have the opportunity to identify a risk before it escalates into something catastrophic.
This is not the first collaboration between Wood and RGU, and the wider business community, as for a number of years they
“The Wood Business Information Security Team learn as much from the students that join the cyber team on placement as the students do from Wood. We get enormous benefit from the curiosity of the students who join Wood with an academic stimulus and learning. In return, Wood layer on to that practical experience, which is vital context for the students’ future development. It’s a win-win situation for us all.” said Malcolm Norman..
The key message is that if we all work together to educate and raise awareness, we can make genuine change as we endeavour towards our collective goal of a positive cyberculture.

OSP Cyber Academy News 17
Irene Coyle, Chief Operating Officer, OSP Cyber Academy
TIME FOR INNOVATION?
The cyber sector is moving faster than ever - if you’re standing still, you’re losing ground to your competitors. Research, development and innovation need to be core to your company’s growth strategy and whether you’re an established player in cybersecurity, an SME or a start-up, Abertay University’s cyberQuarter can support you.
Research and Development
Work with our team of academic experts and researchers from Abertay University’s Division of Cybersecurity on R&D projects to boost your business, taking your services and products to the next level. We treat every project as bespoke and can tailor packages to suit the needs and budgets of our clients.
Plug into the talent pipeline
Take full advantage of working with some of the UK’s top cybersecurity student and graduate talent to engage on the real-world problems facing your business. Challenge the next generation of cyber leaders to make your offer better and to bring fresh ideas and new thinking to the table.

Base yourself in Scotland’s tech city

Join Dundee’s thriving tech and cyber community by locating our new, physically and digitally secure £18m cyberQuarter building, right in the heart of Abertay University’s city centre campus. Whether it’s workspaces, areas for collaboration, seminar rooms (or even access to a cinema) we’ve got all the facilities you’ll need spread across four specially designed floors.
Join the cyberQuarter community
Choose one of our affordable subscription packages to join the cyberQuarter community. In addition to access to use the building for work, events and networking, you’ll join our growing list of partners from the cybersecurity industry, the public sector and academia, tapping into the network of organisations that are driving the agenda for Scottish cyber.

Find out more
Abertay University is a charity registered in Scotland, No: SC016040.
19
Protecting Operational Technology – an Industry View




There is a growing perception that Operational Technology is the next big focus area for cyber security. Certainly, the incidence of attacks seems to be increasing, although reporting is still low. Moreover, World events such as the war in Ukraine and its associated energy conflict have concentrated minds on industrial security as the Global situation becomes less stable, and the boundary between state intervention and criminality becomes increasingly blurred.
The huge potential for ransom, extorsion and economic disruption now seems clearer than ever. The Energy Sector in particular looks like a great target, but it is the indiscriminate nature of many forms of malware which is perhaps most worrying: there is no need to be targeted in order to become a victim and many successful attacks can be seen as a form of collateral damage which was never envisaged by the initiator. These forms of malware can be seen as hybrids of weapons and contagions –analogous to biological warfare in some ways. Add OT security’s implications for safety and the environment, and it is easy to see why it is attracting attention. But what are companies doing about this? What are we seeing as industry, and the Energy Sector in particular, tries to adapt to a changing threat landscape?
Firstly, we need to understand that we are dealing with commercial entities here. Companies exist to create value and sit within complex ecosystems, with multiple threats and a host of conflicting drivers. Government entities are subject to many of the same pressures. Quantifying the risk and consequences of attack, and the benefits of security investment in terms of value and ROI, is difficult. Perhaps the most obvious driver is the operational cost inherent in increased ‘downtime’ due to cyber attack, but many industries are still on the road to truly datadriven operations, may be subject to other factors such as weather in offshore operations, and significant downtime is often seen as a fact of life. Reputation, and the consequences for share price, would be another significant driver, but it is really where this starts to overlap with some form of licence to operate, backed by Government regulation and enforcement, that we are seeing most traction for what can otherwise seem like an intangible issue. Add in safety and the environment, for instance in the Health and Safety Executive’s enforcement of the Network and Information Systems Regulation in the Energy Sector, and we move to a much more tangible imperative.
OT security can be made feasible and cost effective, but it will require considerable collective will to regain the initiative.
So, given increasingly effective industry drivers, what are the issues? We tend to see cyber security as a technical activity, but the first issue we encounter in most situations is governance. Put simply, who is responsible for OT security? It may be that the IT Department has ended up with the lead – either explicitly or by association. Alternatively, the integrator or OEM might be assumed to have this role, or perhaps it is Operations or Engineering. Sometimes different elements have responsibility for different OT networks at a single site – a difficult situation for the Duty Holder to manage, especially where the supply chain introduces extra vulnerabilities. Either way, we would suggest that clarity of roles and responsibilities – and associated resourcing –is a necessary precursor to technical intervention.
On the technical level, from what we see, it is fair to say that there is a lot of work to do. The issues set out above, along with the prevalence of aging equipment connected in ways that weren’t originally intended, and not fully patched or patchable, has left us with a matrix of vulnerabilities: essentially a large and complex attack surface. Key issues would be asset and vulnerability discovery, network visibility and alerting, network segregation and event response – but there are several others, all underpinned by personnel awareness and training, and with an underlying issue to do with insecure network architectures. Having scoped the problem, we seem to have encountered a bow wave of work which runs the risk of pushing OT security from the ‘not understood’ pile to the ‘too difficult’ pile.
How to move forward against this difficult backdrop? Well, wicked problems must be addressed by teams, not individuals. In this case, the team must include operators, license holders, cyber security companies, integrators and the supply chain – to name but a few. Our military background tells us that the most important element in any team is trust, so that is where we must start. Building trust won’t be easy in an attractive industry with many new entrants at various levels of competence and where ‘vendor fatigue’ has taken hold, but it is essential if we are to make progress against increasing threats.
However, even given the right relationships, we simply don’t have enough qualified people and simply increasing the training pipeline won’t generate the right level of industry experience. This is where technology has to come in. Processes such as asset discovery, segregation, alert response, compliance tracking and training need to be increasingly automated: not taking the humans out of the loop, but putting them in control. Trust will be a factor again here –interventions in OT networks must be safe and there is too much loose talk of AI. Legacy systems will need particular attention, especially those that can no longer be patched effectively.
So we are somewhat behind the power curve, but with the right industry drivers, improved governance, trusted teams and the right technology we stand a good chance of turning this around – not without some investment, of course. OT security can be made feasible and cost effective, but it will require considerable collective will to regain the initiative. The good news is that some companies are grasping the nettle in exactly this way: they are the leaders who will show industry the way ahead. Regulatory compliance may be the key driver for OT security at the moment, but we look to the time when it will be overtaken by competitive advantage.
Martin Smith, MD of CyberPrism, looks at the issues facing industry in securing its OT.
Operational Security cybernewsglobal.com 20
Take control of your Operational Technology
CyberPrism provides Software as a Service, underpinned by industry - leading technical professional services, to protect Operational Technology, chiefly within the Energy Government sectors. We are dedicated to producing cost-effective, client-specific your OT.
Take control of your Operational Technology
Take control of your Operational Technology
Software as a Service, underpinned by industry - leading technical practitioners and protect Operational Technology, chiefly within the Energy, Maritime and are dedicated to producing cost-effective, client-specific solutions to safeguard resources required to re-establish safety and security in the face of current compatible network visibility, alerting, incident response, and protection of low-risk, using tried and tested technology, and compatible with any OEM’s experience and judgement are key to the Platform, which is backed by our proven spent protecting Critical National Infrastructure. We reduce the scale of the what they do best: take control.
CyberPrism provides Software as a Service, underpinned by industry - leading technical practitioners and professional services, to protect Operational Technology, chiefly within the Energy, Maritime and Government sectors. We are dedicated to producing cost-effective, client-specific solutions to safeguard your OT.
Our Platform reduces the resources required to re-establish safety and security in threats. Incorporating OT - compatible network visibility, alerting, incident response, devices and systems; it is low-risk, using tried and tested technology, and compatible equipment. Human experience and judgement are key to the Platform, which is expertise, borne of decades spent protecting Critical National Infrastructure. We task and allow people to do what they do best: take control.
CyberPrism provides Software as a Service, underpinned by industry - leading technical practitioners and professional services, to protect Operational Technology, chiefly within the Energy, Maritime and Government sectors. We are dedicated to producing cost-effective, client-specific solutions to safeguard your OT.

from provides within facilitates communication and continue. legacy, patchable
CyberMonitor
Guard
Guard
CyberSupport
Our Platform reduces the resources required to re-establish safety and security in the face of current threats. Incorporating OT - compatible network visibility, alerting, incident response, and protection of devices and systems; it is low-risk, using tried and tested technology, and compatible with any OEM’s equipment. Human experience and judgement are key to the Platform, which is backed by our proven expertise, borne of decades spent protecting Critical National Infrastructure. We reduce the scale of the task and allow people to do what they do best: take control.
Our Platform reduces the resources required to re-establish safety and security in the face of current threats. Incorporating OT - compatible network visibility, alerting, incident response, and protection of devices and systems; it is low-risk, using tried and tested technology, and compatible with any OEM’s equipment. Human experience and judgement are key to the Platform, which is backed by our proven expertise, borne of decades spent protecting Critical National Infrastructure. We reduce the scale of the task and allow people to do what they do best: take control.
CyberMonitor
CyberMonitor
CyberSupport
Guard protects OT from malware ingress and provides ‘smart segregation’ within industrial networks. It facilitates secure two-way communication and allows critical industrial and safety processes to continue Guard can also protect legacy, unsupported and un-patchable devices from attack
CyberMonitor is a Security Orchestration Automated Response (SOAR) software solution. It monitors and manages IT and OT networks, generates alerts and tracks compliance. Built on innovative data comparison software, which allows it to ingest and compare data from any source, it works with any OEM’s equipment.
Guard protects OT from malware ingress and provides ‘smart segregation’ within industrial networks It facilitates secure two-way communication and allows critical industrial and safety processes to continue Guard can also protect legacy, unsupported and un-patchable devices from attack.
cyberprism.net


Guard protects OT from malware ingress and provides ‘smart segregation’ within industrial networks. It facilitates secure two-way communication and allows critical industrial and safety processes to continue. Guard can also protect legacy, unsupported and un-patchable devices from attack.
Guard
CyberMonitor
CyberMonitor is a Security
CyberMonitor is a Security Orchestration Automated Response (SOAR) software solution. It monitors and manages IT and OT networks, generates alerts and tracks compliance. Built on innovative data comparison software, which allows it to ingest and compare data from any source, it works with any OEM’s equipment.
CyberMonitor is a Security Orchestration Automated Response (SOAR) software solution. It monitors and manages IT and OT networks, generates alerts and tracks compliance. Built on innovative data comparison software, which allows it to ingest and compare data from any source, it works with any OEM’s equipment.

CyberPrism provides a complete range of cyber security services and solutions. Our products and services provide key elements of the NIST cyber security protocol: Identify – Protect – Detect –Respond – Recover.
CyberSupport
Orchestration Automated Response (SOAR) software solution. It monitors and manages IT and OT networks, generates alerts and tracks compliance. Built on innovative data comparison software, which allows it to ingest and compare data from any source, it works with any OEM’s equipment.

CyberPrism provides a complete range of cyber security services and solutions. Our products and services provide key elements of the NIST cyber security protocol: Identify – Protect – Detect –Respond – Recover.
CyberPrism provides a complete range of cyber security services and solutions. Our products and services provide key elements of the NIST cyber security protocol: Identify – Protect – Detect –Respond – Recover.

CyberPrism range of and solutions services the NIST Identify Respond

Phone: +44 020 7873 2414
Email: contact@cyberprism.net
CyberPrism
Phone: +44 020 7873 2414 Email: contact@cyberprism.net Cyberprism cyberprism.net CyberPrism
Phone: +44 020 7873 2414 Email: contact@cyberprism.net Cyberprism
CyberPrism
your Technology
Cyberprism
CyberSupport
cyberprism.net
Police Scotland Youth Volunteers
Become Cyber Aware Warriors
Police Scotland Youth Volunteers (PSYV) join forces with Robert Gordon University and OSP Cyber Academy



Around 1000 PSYV’s are being trained in aspects of cyber awareness via an online training portal delivered by OSP Cyber Academy, one of the UK’s leading online cyber training providers. The aim is to help the volunteers understand the threats and risks that they face on a daily basis online and share this knowledge when engaging with family and friends to help protect them.
So who are these Cyber Warriors? PSYV?
There are currently 43 PSYV groups across Scotland and they are represented in each of the 13 Local Policing Divisions, with over 900 young Volunteers and over 200 adult volunteers nationally.

The purpose of the PSYV is to promote a practical understanding of policing amongst young volunteers, encourage the spirit of adventure and good citizenship, support local policing priorities through volunteering in local events and initiatives to raise awareness, give young people a chance

to be heard and to inspire young people to participate positively in their communities.
The PSYV provides young people aged 13 – 18, of all backgrounds, a positive means of engagement with the police through regular training, participation in community safety initiatives and through volunteering in their communities leading to this project being an ideal opportunity to engage about cyber awareness for protection online.

All age groups of PSYVs including adult volunteers will gain the cyber knowledge necessary to support this great initiative, through peer mentoring.
More importantly they will be learning skills to help them educate the most vulnerable in society, with these newfound skills they will then go into the wider community armed with this capability to deliver education and awareness via a thought provoking “Escape Rooms’ styled exercise developed exclusively for this Project by the science and technology faculty at Robert Gordons University.
This is very much the start of the journey with a hope that the success of this programme might gain more valuable support from the Scottish Government who have been instrumental in making this project happen, to date this is the first programme of its kind in the entire UK, so Scotland intend to deliver on its challenge.
Christopher McDermott Lecturer Human-centred Security Robert Gordon University
Irene Coyle Chief Operating Officer OSP Cyber Academy
Representatives and partners from Police Scotland Youth Volunteers, Scottish Government, Scottish Police Authority, Robert Gordon University, OSP Cyber Academy and ScotlandIS attending the official launch.
cybernewsglobal.com 22
We are a membership organisation for Scotland’s digital technology industry. We underpin a thriving community which brings together the ambition, talent and expertise across our industry to grow Scotland’s digital economy.
Our membership includes technology businesses across a wide range of sectors, in addition to universities, the public sector, financial services, energy industries and specialist providers.

By becoming a member you will:
Raise your profile
Gain exposure to key audiences, highlight your capabilities to our expansive network of members and cluster tech companies in Scotland and beyond. From speaker and sponsorship opportunities, to access to our extensive community via our social platforms and bulletin, we will enable you to be heard in every corner of our industry.
Expand your network
Receive introductions within our network of over 1000 Scottish technology companies. Access valuable ecosystems through our Cyber and Data clusters. Attend our events for free or at a discounted rate, for the opportunity to network with our community.
Strengthen your business
Access new funding calls and procurement opportunities that we highlight to our membership. Receive business support such as HR and legal advice to help you on your journey as you grow.
Be part of the conversation
ScotlandIS will keep you apprised of the latest industry trends, insights and research. Join Specialist Groups such as our Software Engineering Leaders Forum and Marketing Meetups to explore challenges with peers and the potential to work together. Our steering groups such as Policy, Cross-Sector, and Diversity & Inclusion, will help you stay informed and shape the future of Scotland’s tech sector.
www.scotlandis.com

23
CYBER ASSURANCE
Do you need to demonstrate your information security commitment and compliance, and assure customers that their information is protected? Or do you need to ensure your supply chain are managing their cyber security risks?
The IASME Cyber Assurance standard is a comprehensive, flexible and affordable cyber security standard. It provides assurance that an organisation has put into place a range of important cyber security, privacy and data protection measures.




Risk based and includes key aspects of security such as:
Incident Response
Asset Management
People Management
Physical Controls
GDPR compliance
The first step along the certification pathway for IASME Cyber Assurance.
Pricing dependant on the size of the organisation.
Involves an independent audit of your processes, procedures and controls conducted by an IASME Certification Body and Assessor.
A legitimate alternative to other alternative standards.
The next step after completing IASME Cyber Assurance Level 1 certification and our highest level of certification.
Pricing quoted independently by a Certification Body.
 Samantha Alexander IASME Cyber Assurance Certification Manager
Samantha Alexander IASME Cyber Assurance Certification Manager

To find out more about IASME Cyber Assurance, and how it can help your organisation, contact our IASME Cyber Assurance Certification Manager via the contact details below.
samantha.alexander@iasme.co.uk
iasme.co.uk/iasme-cyber-assurance/
IASME

Same fraud PLAYBOOK
Wise words from Cyber Woman of the Year
This year we’ve seen three high profile corporate scandals with larger than life CEO’s in the dock facing serious allegations and it is tech companies that are at the centre of all the action: Theranos, Wirecard, and Autonomy. All three CEO’s have been charged with fraud.

The former CEO of Theranos, Elizabeth Holmes has had her day in court, has been found guilty of fraud. In November, a judge sentenced Holmes to 11 years in prison. Holmes touted Theranos as a health technology company, raised US$700 million, featured on Forbes and defrauded a catalogue of wealthy families, as well as a number of prominent statesmen.
The payment processing firm Wirecard’s former CEO Markus Braun languishes in jail after his bail was revoked.
Braun is awaiting trial on charges of fraud, breach of trust and accounting manipulation.
And last but not least, former Autonomy founder & CEO Mike Lynch is on track to be extradited to the US where he faces criminal charges of wire fraud and conspiracy to commit wire fraud. Lynch created Autonomy’s core product: Intelligent Data Operating Layer (IDOL). IDOL is focussed on the analysis of unstructured data. It is a clever bit of kit, that’s not in doubt.
Three previously highly regarded CEO’s are in a whole lot of hot water, awaiting sentencing, awaiting trial and awaiting extradition.
These scandals provide useful fodder for investors generally but tech investors especially to reflect on and to recast what we think we know

about corporate governance and due diligence. Because however deep their pockets, no investor can afford to fund a firm that’s bound to fail in the future or worse is already failing now.
In this article we will explore what investors did right, what made absolutely no difference, what went wrong and what, if anything, might have alerted them to wrongdoing. What could investors do differently in the future and is there one thing that might have alerted investors to wrongdoing within the companies? Let’s start with the theory.
Jurisdiction & investor type

There is a good deal of academic literature on corporate governance models in the UK, the US, and Europe. Typically, the authors will make a case for one of these jurisdictions as a preeminent destination for investors because of oversight, monitoring and/or control of management. As if to demonstrate this is simply not the case, each of these tech businesses was incorporated in a different jurisdiction; Theranos in the United States, Autonomy in England and Wirecard in Germany.
Could Theranos have occurred in Germany? Perhaps. What is abundantly clear is that obviously each jurisdiction is capable of delivering their own class of fraud. While jurisdiction provides no sanctuary, there’s also no immunity for professional investors either.
Oh oh auditors + the value of verification
It is a normal function of any professional team
looking to invest that they would seek to verify statements made by these companies with respect to cash reserves, revenue streams, profitability etc.


Typically, auditors can be relied upon.
Unfortunately, in the matter of Autonomy and Wirecard, this wasn’t the case. Deloitte’s audit of Autonomy enabled Lynch and his Chief Financial Officer to “present a misleading picture of its financial position”.
Similarly, Ernest & Young’s audit of Wirecard’s revenue stream failed to reveal that the apparently highly profitable and cash rich company was neither profitable nor rich. This is deeply discouraging for any investor who would consider auditors a sound and reliable resource. Truth buys trust and if auditors are not capable of getting to the truth, then their reports are of little or no value.
Verifying with independent, trusted experts would have added enormous value. Had Theranos investors checked with professionals, then it is entirely likely that they would have learned that the tech wasn’t possible and avoided substantial losses.
Check the Tech
In the case of Autonomy, checking the tech did not assist in revealing the fraud. The product IDOL worked. In fact, IDOL worked so well that in the summary judgement the judge referenced words attributed to Meg Whitman who became CEO of HP. She said that the it was ‘almost magical’. Tech does not go to heart of the Autonomy fraud which is a plain vanilla key metric and earnings manipulation fraud.
Investors in Wirecard may have had more luck had they checked the tech before pumping in nearly a billion euros into the failing firm. Wirecard was on the face of it a profitable payment processing firm. Their revenues
In a world brimming with shiny new tech and big promises, making important decisions about where to invest can be challenging.
cybernewsglobal.com 26
Rois Ni Thuama Phd Head of Cyber Governance Red Sift
were fabricated. Checking the tech would have revealed data relating to the payment process. The payment process involved a few different actors: the end user, the issuing bank, the merchant and partners. A closer scrutiny of a random set of payments could have followed these ‘payments’ up or down the pipe. Fabricating revenues is one thing. Fabricating users interacting with merchants and issuing banks is beyond the wit of men.
The most egregious tech fraud is undoubtedly Theranos. Their blood testing system amounted to wires in a box. The tech didn’t exist. To test the efficacy of the Edison the investors would only have needed to have had known an answer to a question in advance and sense checked that against the Edison’s response. The lack of imagination and determination by investors to verify the efficacy of this tech makes this a dreary fraud.
The great thing about techie’s is that they want to show you how their kit works. They want to show you all the clever features, and when it works, they want you to play with it. Whether you’re investing in the firm or the technology. Always, kick its tyres. It is the fastest way to determine whether something works.
Hokey Cokey Principles
Both Wirecard and Theranos engaged in tactics which fell well beyond normal business practices including surveillance, doorstepping, intimidation, threats implicit and express against analysts, journalists, and former employees. That is shameful behaviour. It indicates a willingness to cross the line that should have put current and future investors on notice of a failing firm. Integrity and principles aren’t subject to the hokey cokey routine. You’re either in or you’re out. The firm either behaves in a principled manner or it does not.
Another red flag that was missed in both cases: individuals within the firms were promoted well beyond their capabilities into critical business roles while experts and qualified individuals were demoted, demeaned, and defamed — this shows such poor leadership that this alone should concern investors.
The Free Press isn’t Free
Why investors didn’t raise an eyebrow when lawyers for Wirecard and Theranos pursued credible, leading global publications in an effort to silence them is anyone’s guess.
It is to their endless credit that the investigative journalists and editors at both the FT and the Wall Street Journal (WSJ) would not be intimidated into submission. Uncovering these frauds and bringing them to light was only possible because both of these well capitalized publications had the might and the resources to withstand the bullying tactics of criminals.
Don’t let others define the world around you.
Holmes touted Theranos as a health technology company. That’s misleading — the proposal was actually to create medical diagnostic equipment capable of surpassing existing equipment and miniaturising it.
Reframing the proposition might have caused investors to pause. In addition, readers will recall that Holmes had no background in any of the disciplines necessary to take part in, never mind run a medical diagnostics equipment project. If only those investors had checked.
Consider your source
The free press isn’t actually free. Anyone looking to invest in tech should be doing their homework. Had investors, like Softbank put
more weight in the reports from the FT about Wirecard they could have saved themselves 900 million euros. That’s a solid return on investment for a subscription.
Auditors, as we learned, cannot sadly be relied upon, they’re paid by the company and in no way meet the definition of ‘independent’. While large auditing firms hold themselves out as the unrivalled experts, that tune changes when they’re caught up in a fraud — the very thing they’re expected to uncover. At that point they’re only human. More of that humility at the front end and more confidence at the back end of these scandals would help to restore the reputation of some of these players.
Conclusion
Academic theory suggests that optimising for corporate governance makes a difference. The reality is that criminals will work around every system to perpetrate their fraud. Investors cannot afford to be complacent.

Ultimately, what investors did right was to seek to verify the statements made by these firms. Unfortunately, what they did wrong was to rely on sources that weren’t credible and simultaneously dismissed those that were. In order to avoid a similar fate, investors would do well to rely on trusted, independent experts.

However you carve these scandals up, these leaders operated from the same fraud playbook. They overstated performance, recorded bogus revenue, and they trusted that the brazen mocked documents painted a picture of firm value and that no one would bother to check.
For all their differences these scandals relied on the same tactics: dishonesty, deflection, and misdirection — they just had different products.
Corporate Governance 27
Products on the Red Sift Platform work together to block outbound phishing attacks, analyze the security of inbound emails, and provide domain impersonation defense for company-wide threat protection. Find out more at redsift.com






Minimise OT risks, maximise cyber security, and optimise your resources Trusted Partners www.radiflow.com Detect and analyse your specific threats Visualise your OT network Respond to threats with prioritised, ROI-driven mitigation plan Customers globally >150 Deployed sites 8,000+
One of the most important concepts in cybersecurity leadership is resilience decision making. This involves the ability to make quick and effective decisions in the face of uncertainty and rapidly changing circumstances, remaining in the eye of the storm. Research suggests, effective leaders in cybersecurity exhibit a number of key traits, including a willingness to take calculated risks, a focus on strategic thinking and problem-solving, and the ability to stay calm under pressure. In order to do this, leaders must have a clear Super North Star, “an unambiguous statement of intent” about where their organisation is heading and most importantly, does everyone in the organisation say the same thing?

Leaders must have a clear strategy and have thought through the contingencies they may have to enact, understanding how they and their team deal with difficult situations.
My thought process is always as follows:
• What are the facts of the situation?
• What is a creative way to look at the situation?
• What is positive about this situation?
• What are the dangers and risks?
• How do I now feel about his situation as I make the decision?
The best leaders know how to think under pressure because they have rehearsed it.
One of the most important concepts in cybersecurity leadership is RESILIENCE DECISION MAKING
By Floyd Woodrow MBE
The field of cybersecurity is ever-evolving, with new threats and vulnerabilities emerging on a daily basis. As such, it is important for organizations to have effective leaders in place who can guide their teams through the constantly changing landscape.

Managing a diverse workforce
The cybersecurity industry is compiled of a diverse workforce, and successful leaders in this field must know how to work with cognitive diversity. It is clear from studies that people now respond best to leaders who provide them with clear expectations and goals, offer regular feedback and recognition, and provide opportunities for professional growth and development. Leaders who can communicate effectively and provide the necessary support and resources are more likely to have a highly engaged and motivated workforce. This means the ability to adapt your communication style and realise you need to understand the position of your audience.
My personal view is that most people have always needed the above in place for a leader to be effective. That cognitive diversity is essential for organisations to fully reach their potential, and this requires leaders to be able communicate with talented people who can be challenging.
Working from Home
In the wake of the COVID-19 pandemic, remote work has become the norm for many organizations. Leaders in cybersecurity must be able to manage teams in a remote environment, and this requires a different set of skills and strategies.
a great team.
Effective remote leaders are able to set clear expectations and guidelines, communicate frequently and transparently, and provide their teams with the necessary tools and resources to work effectively from home. Leaders who can maintain a strong team culture in a remote environment are more likely to have a highly engaged and productive workforce. However, this does not mean that people should work entirely from home. It is important to acknowledge the importance of human connection and interaction. Humans are social creatures, and we thrive on social interaction and connection. When we are isolated from others, we can experience feelings of loneliness, depression, and anxiety.
To create a brilliant environment, it is essential to design spaces that align with how our bodies and minds naturally function. Providing opportunities for people to move (standing desks, walking meetings). Areas that have natural light and plants alongside fresh air and areas for social interaction.
In my opinion there needs to be a balance to remote working and being in an office. A three day (office) to two day (home) ratio gives the correct balance.
Resilience Decision Making
In this article, I will explore the current concepts of great leadership in cybersecurity including resilience decision making, managing a diverse workforce, working from home, values, and building
cybernewsglobal.com 30
Values

Values are a key component of effective leadership. Leaders who articulate a clear set of values and principles, and who model these values in their own behaviour, are more likely to inspire their teams and earn their respect and loyalty. According to studies, compelling leaders place a high value on integrity, honesty, transparency, and accountability. However, these values should not be laminated and look good on a wall. Are the values in your organsiation explicit and does everyone model the behaviour that is expected? If not, under pressure teams that do not exhibit strong values generally do not perform well.
When did you last check the values in your organisation? Please remember the values you walk past are the values you accept.
Building a Great Team
Finally, effective leaders in cybersecurity must be able to build and maintain a great team. This involves recruiting the right people, providing them with the necessary training and resources, and fostering a strong team culture that has a high support, high challenge mentality is crucial. They prioritise team diversity and inclusion, encourage open communication and collaboration, and provide their teams with opportunities for professional growth and development.
Resilience Decision Making


Does this happen in your organisation. Are you growing the next generation of leader and what is your legacy going to be?

Finally, great leadership is critical to success in the constantly evolving field of cybersecurity. Leaders who exhibit resilience decision making, can work effectively with a diverse workforce, manage remote teams, prioritise values, and build a great team culture are more likely to succeed in this challenging and complex field.
As the industry continues to evolve, it is important for organisations to invest in developing their leaders and fostering a culture of strong leadership at all levels of the organization.
Floyd Woodrow is a leadership expert, entrepreneur who coaches and mentors’ senior leaders from around the world.
His success in business has come after a distinguished military career where he was awarded the Distinguished Conduct Medal for his services in Iraq and an MBE for his services.
Floyd is the chairman of the Quantum Group which is a leading fintech investment incubator. Floyd was recently selected as one of the top 50 fintech entrepreneurs in the UK by the Financial Technologist Magazine.
Floyd also heads a charitable foundation called Compass for Life which delivers educational programmes in schools and colleges across the UK, assisting disadvantaged children with their educational and aspirational needs.
His book “The Warrior, the Strategist and You” is available on amazon.

[ SCAN THE QR CODE ] GET YOU COPY HERE 31
By Jonathan Sproule MBCS CISM CCSP CISSP

Compliance in an Ever-Evolving
Cyber Threat Landscape
Why compliance is crucial to businesses and stakeholders
The world of compliance has often lagged behind the release and adoption of new technologies. Organisations around the world will always seek new ways to stay ahead of the competition and continue to grow to survive. It is a classic case of the tail wagging the dog, or from the ground up.
There can be several drivers for an information security program, which can include regulation, incidents, and reputation. Thankfully, wWhenever you are in an industry which is heavily regulated thankfully you have the hard work of justifying the program already done. This is the stick rather than the carrot of course, however, for long term success and buy-in, the carrot is more fruitful. An important point is that compliance does not necessarily equal security.
I’m sure many readers will understand the definition of compliance, however, to make sure we are on the same page here I think it’s important to cite the definition. This is an important point, because often in the information security world there can be a great deal of confusion and differences of opinion with certain terms e.g. the risk associated.
Complexity in the Compliance Ecosystem
Organisations can struggle with understanding and interpreting regulatory requirements. There can be complexity in this ecosystem with regulations and they can often have an impact on each other and even sometimes overlap requirements from other regulations. The General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) both regulate the use, and protection of personal data, including individuals’ rights to access and control their personal information, as one example. There are some commonalities, but there are also some key differences. Whether you are considered in scope or out of scope of various regulations very much depends on where you and your customers are located. There are of course, various reporting requirements from various regulations too, which increases complexity in the system.
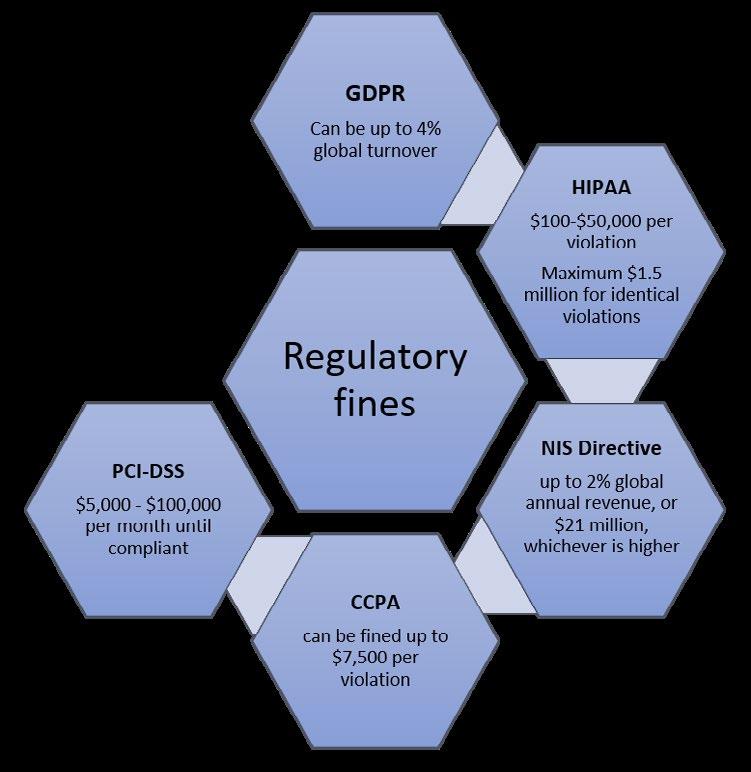
The Impact of not Complying
The impacts of non-compliance can ultimately affect the organisations bottom line. This is something that our business stakeholders will understand in financial terms. When speaking about impacts to business stakeholders we should seek to translate our language into meaningful terms that they understand, and what impact means from a financial perspective.
To communicate the impacts of incidents to business stakeholders, Factor Analysis Information Risk (FAIR) provides a great model for understanding, analysing and quantifying information risk in financial terms. The impacts of incidents and breaches are far more than just being served fines by secondary stakeholders (regulatory bodies). There are other forms of loss that can be realised and should be communicated in your risk analysis:
Producivity loss

Losses that result from an organisation’s inability to deliver its products or services
Response loss
Losses that are associated with managing the event itself
Replacement loss
The costs associated with the replacement of a capital asset or a person
Fines and judgements
Penalties levied against an organisation through civil, criminalcriminal, or contractual actions, usually the result of a Confidentiality related scenario
Competitive advantage
Losses associated with a diminished competitive advantage
Reputational Damage
Losses associated with an external actor’s perception that the value proposition of your organisation has been diminished
Each regulation will have its own enforcement, fines, and penalties for non-compliance, as detailed in figure 1. The severity of the fines will depend on the nature, type of finding, and how it was discovered. Consider if the non-compliance was discovered as part of your audit program, then we could say with a high degree of certainty that this would likely be lower, compared to if it was discovered by an external threat actor in a breach scenario. It is important to note that these fines can vary depending on the specific case, the severity of the violation, and the discretion of the relevant authority, so it’s cost effective if you have an internal audit program. If you don’t have an audit program in place this could serve as a business case for just that, supported by objective data.
Speaking of objectivity - If we look at data relating to data breaches as part of our situational awareness, the global average cost of a data breach is now $4.35M. That’s a fairly sizeable number and would certainly affect the organisational bottom line in terms of profit.
Definition of Compliance
the act of obeying an order, rule, or request
When I think about that definition there are some verbs and adjectives which stand out to me: obeying and rules. Organisations can often get caught up in tick box exercises, and that can happen when talking about compliance, or talking with senior stakeholders who are not traditionally from an information security background. I like the NIST Cybersecurity Framework (CSF), which has been widely adopted in our industry and for good reason; it is outcome driven rather than being a tick box approach and provides useful guidance in the form of information references. This helps to introduce simplicity into a complex environment of regulations and standards.
The cost per stolen record is $164 , which has increased slightly from $161 the previous year. To get good data of course, you need a large sample across horizontals so that we can increase our confidence in the data. It can of course, vary on the cost per stolen record, so you might want to represent that as a distribution instead of being precise.
A measurement is a reduction in uncertainty, and it can be helpful to review industry reports from incidents globally to help inform decisions and incorporate these into risk analysis.
Achieving, and maintaining compliance is crucial in todays interconnected world which is why it’s important to ensure you have a well resourced GRC function. Introduce simplicity in the system to combat the complexity by ensuring you have the resources required; you can’t change the external regulatory landscape, but you can change how easy or difficult it is to adhere to.
Compliance cybernewsglobal.com 32











ALL YOU CAN BUILD Drive digital transformation with power at your fingertips using TAAP’s No-Code Platform Get in contact to find out more! www.ontaap.com 0345 230 9787 sales@ontaap.com Mobile & enterprise scale applications No-Code application cyber resilience A mature, proven No-Code Platform Deployed across over 56 industries and 110 verticals Reporting & analytics 20-50x improvement across SDLC
OPERATIONAL TECHNOLOGY (OT)

CYBER SECURITY STAFF AWARENESS COURSE
Digitisation relies on secure communications to ensure a protected exchange of data between Operational Technology (OT) and Information Technology (IT).

The aim of this course is to provide you with a introduction to Operational Technology (OT) Security and to reduce the likelihood of a cyber attack through reprogramming or training the wetware (us).
The average user struggles to understand the difference between OT and IT and their importance OSP Cyber Academy has worked hard to seek the advice of the very best proven practitioners and partners at Cyberprism to provide some first hand experience of baseline cyber awareness.


I recommend this course to all who want to protect themselves and others, in a practical and realistic way.
Malcolm Warr OBE, Chairman of CNI Scotland

PURCHASE YOUR COURSE HERE: SCAN ME
CONTACT US - EMAIL: TRAINING@OSPCYBERACADEMY.COM
HUMAN-CENTRED SECU R ITY
Welcome
As technology continues to advance, and the number of cyber threats continues to grow, a new approach is clearly required; one that helps organisations to understand and manage psychological vulnerabilities and adopts technology and controls that are designed with human behaviour in mind. In this series, we will explore such a concept and discuss in detail the benefits of adopting this approach.
The conventional method of security focuses on technology and infrastructure, and has been successful in combating certain threats, like viruses and malware. However, its limitations are becoming more evident. Increasingly, security measures are being bypassed by sophisticated cybercriminals that seek to not only exploit vulnerabilities in systems, but also vulnerabilities in human psychology. Human-centred security tackles these limitations by emphasising human factors that cause security risks. By understanding user behaviour and decisions regarding security risks organisations can create solutions that align with user needs and behaviours, reducing potential risks.
Human-centred security also emphasises designing security into solutions, making them ‘secure by design’. This concept emphasises the integration of security measures into the development and design of products, systems, and services, from the earliest stages of planning through to deployment and ongoing maintenance. The goal of security by design is to prevent security risks and vulnerabilities from being introduced in the first place, rather than trying to fix them after the fact. This approach is important because it can help ensure that security is built into the product from the ground up, reducing the likelihood of security breaches and increasing the overall security of the system. Additionally, security by design can
help organisations comply with regulations and standards and reduce the cost and effort of fixing security issues down the line.
A human-centred security approach also requires solutions to be both intuitive and user-friendly to ensure correct and secure usage. User feedback should be considered in the design process, tailoring solutions to meet user needs and preferences. In addition, organisations should equip users with the knowledge and training necessary to make informed security decisions. This involves educating users on potential risks and best practices to embed a “security culture” in the organisation. In this context, a security culture refers to the attitudes, beliefs, and user behaviours that impact an organisation’s security approach. A strong security culture promotes a secure environment and reduces the risk of breaches but requires a commitment from all levels of an organisation, from top management to front-line employees. Additionally, organisations should establish clear policies and procedures for handling security incidents and hold employees accountable for their actions. Furthermore, it’s important to communicate and make security a part of the daily work routine. Regular security training, testing, and drills can help to identify and address potential vulnerabilities, and it can help employees to become more familiar with security best practices. Finally, organisations should establish a reporting mechanism to allow employees to report security incidents and address any concerns they may have.
Human-centred security offers many benefits, including improved security outcomes and user satisfaction. When security solutions align with user behaviour and needs, users are more likely to use them correctly. Additionally, user-
Dr McDermott is an author, educator and researcher in the field of human-centred security. His research focuses on the role of human behaviour in cybersecurity, with a particular emphasis on understanding psychological vulnerabilities leveraged by attackers to influence and exploit humans, and how psychological-related errors can lead to security incidents.

He has published widely on the subject, and is a regular speaker at conferences and other industry events. His teaching focuses on social and human factors in security, security by design, and network security. In addition to his research and teaching, Dr McDermott is a passionate advocate for digital well-being and privacy, regularly writing and giving talks about strategies for leading healthy, safe, and authentic digital lives.
friendly, and understandable security solutions will increase user satisfaction.
In future articles in this series, we will delve deeper into human-centred security, examining some of the concepts discussed above. We will also explore the challenges that organisations may face when adopting a human-centred approach to security, and the strategies they can use to overcome them. Ultimately, the goal of this series is to provide organisations with the knowledge and tools they need to adopt a human-centred approach to security and better protect individuals and businesses in today’s digital landscape.

to the first article in a series on human-centred security; an approach to cybersecurity that focuses on understanding and addressing the human factors that contribute to security risks. Historically, organisations have relied solely on the effectiveness of technical security controls, instead of trying to also understand why people are susceptible to mistakes and manipulation.
Image by rawpixel.com
Chris McDermott Lecturer, Human-Centred Security Research Robert Gordon University
Human-Centred Security 35
Security Service Edge (SSE)

Endpoint Detection and Response (EDR)

Zero Trust Network Access (ZTNA)
Secure Web Gateway (SWG)

Cloud Security Posture Management (CSPM)
WORK FROM ANYWHERE. SECURELY. www.everycloud.co.uk
Malware and Ransomware Protection

Cloud Backup (AWS, Azure, M365)
Email Security
The Future Belongs to The Curious

Cyber News Global Editor-in-Chief, Elspeth Reilly, had the pleasure and honour of sitting down with David Colombo who first gained notoriety as the Tesla Hacker when he ethically, and with the permission of several Tesla vehicle owners around the world, hacked into their car’s systems to demonstrate the holes in Tesla’s cybersecurity measures. Now he travels the world as a consultant, keynote speaker, and as a champion of cybersecurity awareness and education.
What was your main motivation behind your initial investigation into Tesla?

David Colombo: It was only curiosity – that’s what kick started my career in technology. I got my first laptop for my tenth birthday – “how does this work?”. So, curiosity got me started, and it is the same thing that led to the Tesla story.

Because I was thinking about how all these cars are now fully connected. If we go back 80 years, there was no technology in a car — it wasn’t a digital car. Then, we had cars with some interfaces like Wi-Fi, TSM (Trailer Sway Mitigation), and cameras. Now we are connecting those cars to so much more, they’re now connected to other cars, to smart roads, to traffic lights, but all of them also communicate back to the manufacturer.
Traditionally if we look at how cars are being hacked, it’s one car and one hacker that is near that car, attacking local attack surfaces. It got me thinking, why should someone just be near that one car, attack that one car?
If all those cars now constantly communicate back to the manufacturer, someone would be able to [access that communication] route, and they would be able to control multiple cars around the world — completely remotely. So, that was a thought I had in the back of my mind.
That thought led to “how does it work now?”, “How do those cars communicate?”, What interfaces are there?”, “What does the backend infrastructure look like?”
I’m a Tesla fan myself because it’s an iPad on the wheels, right? So, I was just trying to figure out how did all works, I didn’t even think I would find anything — I didn’t even think about hacking anything. I just wanted to understand how the infrastructure works, how the communication works, what it all looks like. Then I came across a few red flags when doing that investigation.
That’s remarkable that this investigation was spurned on purely by curiosity, but it led to this great discovery, a gap in their technology. You mention that everything began on your 10th birthday when you received your first laptop, was this what ignited your interest in cyber? Opening your first laptop opened a whole new world for you?
David Colombo: Exactly. At first it was only coding because I was curious “how does it work?” It’s not magic, its only technology so somehow it must work.
Then, I figured out that I’m growing up in the best time ever because I can leverage technology to learn about how it works. You can just open Google and learn about all these things – I thought that was just wonderful. Then I figured out that everything is code, and so I thought that I better start with coding because that’s how all of these things are built.
So, I really started my tech journey back then with only coding, understanding how it works, then building all of these things: building websites, building apps, and it’s really cool if you’re an eleven-year-old and you can run your own apps and say, “I made this!” That was really fascinating.

My interest in Cybersecurity came two or three years later when I discovered my first vulnerability. I was coding, understanding the basics, and then I came across my first vulnerability, and I was thought “this is super interesting, now I can do things I shouldn’t be able to do.” And on one hand, it’s cool to learn about cybersecurity and hacking and all of these things. But on the other hand, you can already see that cybersecurity is going to be one of the most pressing challenges moving forward when we digitalize our whole lives; starting with smart homes, autonomous cars, even creating infrastructure that is fully digital. So, that really grabbed my attention and my passion; I spent like all my time on it, even though school was the next day — I didn’t care, I would be awake until 4:00 in the morning, sitting in front of my screen, coding and tagging.

WATCH THE INTERVIEW 37
MEET THE TESLA HACKER
You’re incredibly passionate about cybersecurity and technology! I read an article which mentioned that you and your father protested to allow you to attend school for only two days a week, was this so that you could better pursue these passions?
David Colombo: Definitely. So, that was what followed. Now I was into cyber security, I was spending all my time on it. Two, three years in, I was sitting in school in Germany, 10th grade, and I asked myself, “why should I sit here in Latin, if I could be out there helping to protect those organizations?” So, I decided I have to quit school. For me, it wasn’t even a question. What is going to be more important within the next decade? Cybersecurity or Latin, right? “I have to get out of this.” According to German law, you have to go to school until you’re 18.
I was thinking that if there’s a bug in my code, I don’t sit back and relax — I get into it and I fix it. So, I was trying to apply the same principle to my schooling until I found someone at the Chairman Chamber of Commerce who understood what I was saying.

I lived in the middle of nowhere, about 200 people in the town. So, he was driving out there, and it took him like two hours to get there, just to speak with me and to take a look at what I’m doing. Then, we finally got that special permission [which allowed me] to only go to school one or two days a week and use the rest of my time to, to further go ahead with my pursuit of cybersecurity.
It’s very clear that this is your passion, and it’s incredible that you developed it at such a young age. You said earlier that we’re living in a digital world, and it’s only going to get more and more connected —how do you think we should get the younger generation more interested in cybersecurity?


David Colombo: We need to show it to them. That’s that’s the only thing we have to do. Cybersecurity itself, is such a fascinating field. It’s really interesting, and there are so many cool things happening, but not too many people know about them. People always ask me: how do we make the defensive part of cybersecurity cool? Of course, hacking into something is cool, but how do we make the defensive part cool? And I’m thinking, what do you mean make it cool? It is cool. We just need to get it out there and show it to people, right?
For example, if hospitals are getting attacked from cyber threats and we have an incident response team rushing to the hospital defending against the attack and figuring out what happened — we just need to show that all of these exciting things are happening to the younger generations to ignite their interest. Once we are able to ignite it and spark it up, it’s going to be their passion!
Absolutely, it all comes down to education and awareness. You bring up an interesting point about hospitals getting attacked. It’s a great example to shed a light on because being the good guy in that situation is cool, and it is exciting, and it’s great to be able to help people, to step in, and to block those attacks from occurring. We have to demonstrate that cyber resilience is exciting.
David Colombo: Exactly. We also must show these young people who have extraordinary skills where to go, where they can prove themselves — we need to guide them to where they can actually use their skills for good. We need to talk about bounty programs, or about Capture The Flag (CTF) events where they’re able to prove their skills and be in a great community rather than going to the dark side of cyber. If we go back to when I started in cybersecurity, there was not much available. That is something that luckily is changing now. If we take a look at Hacker One and Buck Route and CTF events, these opportunities are happening, but we need to direct people towards them and show them; there are places for them if they have exceptional skills, if they’re interest in the topic, there are ways to test their skills, to prove their skills in an environment where it’s safe and where it’s legal.
cybernewsglobal.com 38
“People always ask me: how do we make the defensive part [of cybersecurity] cool? Of course, hacking into something is cool, but how do we make the defensive part cool? And I’m thinking, what do you mean make it cool? It is cool. We just need to get it out there and show it to people.”
That’s an excellent point — it’s vital to not only create opportunities for people, and especially younger people, to be able to utilise their skills and expertise, but to broadcast them effectively so that people know such opportunities exist. Speaking about the future generations: what do you think personally is future of cyber and how is going to in turn going to affect the cyber threat landscape?
David Colombo: Cyber is definitely going continue to grow as an industry and, with a lot more focus on the cyber-physical things that we are connecting. We are now talking about building Smart Cities. Who’s going to secure them? If you go on LinkedIn right now and you want to find Smart City security engineers — it doesn’t exist yet. We are going to see a lot of automation, but automation can only do so much; it can’t replace a human because cybersecurity is such a complex topic. Because of this, we need a lot more people into the workforce.
We need to start tackling the 3.5 million unfilled cybersecurity positions. It boils down to accessibility.
People don’t see these opportunities and so they don’t get access to them. That’s what we need to change to bring it to the attention of a lot more people, show those pathways, get them into the field. Because every major enterprise is searching for cyber security experts.
I was recently in Germany’s Business newspaper Handelsblatt where there was an article saying that “we are at the breaking point.” In Germany, a lot of organizations are getting hacked and of course, they need to call up cyber security companies to help them recover. But a lot of the time now when that they call up these cyber security companies, these companies tell them “Sorry, we don’t have the capacity to help you.” Which is creating major issues for those organizations in need. So, across the board, whether on the offensive side or on the defensive side, we need experts.
Also, when developing cybersecurity capabilities, something that I always like to point out is that I don’t even have a Tesla myself, so if you have cybersecurity researchers that are really eager to learn automotive cybersecurity, where do they do it?

How many people have the ability to buy a $70,000 car and risk breaking it while doing their research? We need to create environments where we give people access to these systems.

Meet the Tesla Hacker 39
How many people have the ability to buy a $70,000 car and risk breaking it while doing their research?
UNIVERSITY CYBERSECURITY CHALLENGE
The Challenge
Calling all cybersavvy undergraduates to create & cultivate a concept for an app which utilizes AI technology to promote cybersecurity awareness & education.

The Oppor tunity
The 3 finalist teams will be invited to present their concept at the International Cyber Summit on August 31st 2023 in Aberdeen, Scotland — travel & accommodation will be paid for.

Cyber News Global presents the inaugural Cybersecurity University Challenge:

An academic challenge which presents the opportunity to create and cultivate a concept for an app which utilizes AI technology to promote cybersecurity awareness and education to those most vulnerable to cyber risks: the younger generation, and the elderly. We are calling for submissions from undergraduate students currently enrolled in university. Those interested in the challenge will form teams of three and collaborate on the project together.

Initiative
In teams of three develop a concept for an app which utilizes AI technology that promotes cybersecurity awareness and education to those most vulnerable to cyber risks: the younger generation, and the elderly.
Be creative in your problem-solving — How has AI Technology been utilized in similar ventures? Is there an overlooked initiative that could help fill the gaps?
How can we make cybersecurity accessible and digestible to both a younger demographic and the elderly?
How will this app improve cybersecurity awareness, and moreover, how will it inspire education, and leave its users with a better understanding of how to spot and avoid cyber risks?

Deliverables
Due by 24:00 (GMT) May 31st 2023.
• A detailed and data-driven project brief of 3-5 pages
• A wireframe
• A case study
•
•
Opportunity
Following our review of the received submissions — conducted by [insert esteemed judges here] — three teams will be selected as finalists who will be invited to present their concept at the International Cyber Summit on August 31st 2023 in Aberdeen, Scotland — travel & accommodation will be paid for.
The finalists will have ten minutes to present their concept to the panel of judges, who will then make the final decision in the awarding of 1st, 2nd, and 3rd place.
Judging Criteria
Innovative Thinking 30%
UX/Interaction Design 20%
•
•
20%
Data Informed Decisions
10%
Case Study
Cybersecurity University Challenge SIGN UP HERE > 41
CRIMINALS USING THE DARK WEB THINK YOU CAN’T SEE THEM WITH SEARCHLIGHT CYBER, YOU CAN.
GAIN THE ADVANTAGE OVER THREAT ACTORS AND CRIMINALS
Illuminate threats with dark web intelligence


Pre-empt ransomware and cyberattacks
Defend your organization
TRUSTED GLOBALLY BY ENTERPRISE, LAW ENFORCEMENT AGENCIES, AND GOVERNMENTS

TO LEARN MORE, VISIT:

cybernewsglobal.com
C S O o |S c O AICPA SOC aicpa.org/soc4so SLCYBER.IO
HOW TO HIRE A HACKER
SHOWCASING SKILLS
Well, if you ask Quorum Cyber, an Edinburgh-based MSSP, it’s through using a Capture the Flag event to assess the technical capabilities and impact skills of candidates.
For the second year running, Quorum have engaged with training provider Capture the Talent to create a fun and engaging 48-hour event that tests skills across a number of domains including OSINT, Cryptography, Forensics, Web App Hacking, Steganography and more.
CASE STUDY: QUORUM CYBER
BY AMY STOKES-WATERS, CHIEF COMMERCIAL OFFICER, CAPTURE THE TALENT
Cybersecurity skills are in high demand. The industry is booming. Even amid layoffs at tech giants like Google, Amazon, and Microsoft, adverts are flooding social media looking for more tech bods in the security space.

At the same time, we’re seeing an influx of talent reskilling into cyber. Bootcamps are popping up left, right, and centre.
A quick Google search reveals over half a billion results when we type in ‘Learn Cybersecurity’. Content is out there and people are consuming it. Voraciously.
SELECTING THE RIGHT CANDIDATE
This is why matching up talent with the roles we’re hiring for can be extremely difficult. When every candidate we see has their Bachelor’s or Masters in Cybersecurity, certifications coming out of their ears, and a shit hot CV, how can we determine who is the right person to bring on board? How can we be sure they really do have the skills required for the job at hand? How do we know if they’d fit in our team?
Alongside testing technical abilities, the team at Capture the Talent also use an informal group chat setting to get to know the candidates in more depth and monitor how they interact with each other, work together, and communicate.
This allows Quorum to get a rounded view of applicants and identify strengths and weaknesses in a recruitment process that candidates actually enjoy.
COMFORT ZONE
When participating in a recruitment process, we know that candidates often feel stressed and anxious. Feedback so far has shown that a CTF-style recruitment event has lowered stress levels for candidates and has allowed them to have fun.
One candidate, Amy Harvey, explains her thoughts on Quorum’s recruitment process:

“I really enjoyed this CTF, it was brilliant having the opportunity to work on it individually and even better that you were unable to view the scoreboard.
This meant I wasn’t comparing myself against others and solely working at my own pace. It’s definitely been a real confidence booster and shown me what I can truly achieve when I put my mind to it.”
or join the Discord community
THE EVENT IN NUMBERS
40 PLAYERS 40
CHALLENGES
48 HOURS
WHAT THEY WANTED
Quorum wanted a recruitment event that was fun for candidates, cyber-specific, and effective at baselining technical abilities and soft skills of candidates looking to join their graduate scheme.

WHAT THEY GOT
The event went better than we could have hoped for. We turned candidates into a community and the picture we were able to build up on each participants strengths and weaknesses and how they engaged and interacted with others taking part was brilliant and exactly what we were after.
AND HOW IT WENT
From the very first meeting with CTT it was clear that they were experts in their field, really understood what we were after and shaped the event to bring out the best in those taking part, ensuring that they had a great time, whilst showing us what their capabilities were.
FIND OUT MORE
WWW.CAPTURETHETALENT.CO.UK
DISCORD.GG/INFOSEC
A while ago now Keep it Simple –Working Up Enduring Cyber Resilience
On this clay tablet is some of the earliest writing from anywhere in the world. It was made around 3100–3000 BC in southern Iraq and is now in the British Museum. It was used by workers for counting beer.
 By Malcolm Warr OBE, Chairman of CNI Scotland
By Malcolm Warr OBE, Chairman of CNI Scotland
Backthen, it was pretty clear that the devices that provided information and those responsible for managing “technology” were directly connected to those using it. The relationship was simple and straightforward.
Not so nowadays. The average user of technology is bombarded with all sorts of acronyms and strange, mid Atlantic terms. They are assailed with a cacophony of sometimes well-meaning but confusing advice and training regimes. There are dire warnings of the repercussions should technology fails or is infiltrated by cyber invaders. We need to get real. Yes!
There are some very clever adversaries out there who are quite capable of implementing an attack in response to our often-blunted defence posture.
However, too much gobbledegook clouds the issues in responding and deflects practitioners in OT from collaborating effectively with their IT cousins and developing the right relationship with the people who use technology.
As a result, what do many people do to protect themselves?
Almost nothing. Or sometimes the wrong thing. But all is not lost. Many of the dominant cyber adversaries exist within a cult of personality centred on the Leader. The leader sets direction and everyone else executes it. Often repeating patterns by doing exactly what they are told. I have seen examples of this in the security industry and during the Cold War. This form of predictability can be defeated by good training and collective rethinking; intertwined with first class leadership.
In democracies, counter measures can be worked up. Ideas about how to act against both present cyber attacks and help prevent future occurrences can be funnelled by teams and individual contributors. This allows more room for feedback and discussion leading to far better outcomes potentially. There is room for individualism and allowances can be made for human error — and human error plays a critical part.
industries are the most likely to click on links in phishing emails. 45% of employees in banking and finance also admitted to clicking on phishing emails.
Our company’s senior psychologist tells me that new procedures often fail because humans like to get things done but they also fear making mistakes. Many find change difficult — when something stands in the way of progress, humans either concede defeat or circumnavigate the first line of defence. Good aspiration: bad cyber resilience.
Good training and awareness programmes can introduce the tenable cyber threats into employees’ working lives. The best programmes often provide real-time simulations that demonstrate what a threat can look like, and how employees should react. This is partnered with continuous education of the workforce because the threat landscape doesn’t just stop evolving when an employee’s cybersecurity training is done.
According to a study by IBM, human error is the main cause of 95% of cyber security breaches. Therefore, if we can improve human resilience and greater security awareness, the likelihood is that we can reduce cyber driven breaches.
One might assume that involvement in high-tech and high-risk industries, like technology and banking, would bring greater security awareness. However, verified research has shown that this isn’t necessarily the case.
Among the industries that face the most human error are technology companies and financial services. Employees in technology
So where does IT and OT play a part?
If you Google definitions of IT and OT you will get a cat’s cradle of responses.
If you bundle these together, the difference between IT and OT systems is that IT is focused on data and communication, whereas OT is focused on behaviours and outcomes.
However, I have an added a third dimension which is TU. Technology User is defined by lawyers “as someone who uses technology to access and use information or carry out a task that involves the use of digital technology”.

Enduring Cyber Resilience
i cybernewsglobal.com 44
Among the industries that face the most human error are technology companies and financial services.
Enduring Cyber Resilience
All three are linked inextricably.
Over the years, I have led or participated in a number of major transformation programmes and reviewed complex technology projectssome with downstream get well programmes.
In 2020, McKinsey Digital wrote a useful article on a technology-transformation approach that works.
McKinsey reported that technology leaders who have pursued this new approach that is comprehensive enough to account for the myriad inter linkages of modern technology joined at the hip, have shown considerable improvements in business effectiveness and technology resilience.
So where do we go from here?
In 1958 the Royal Navy, set up a transformation programme to train the crews in operating their equipment and give them experience in dealing with every eventuality likely to be met at sea. The McKinsey approach aligns with this transformation.

Starting with a baseline, “Work Up” proceeds with basic safety and awareness training, and progresses through various scenarios to more advanced training on a collective basis involving different “units”.
Common sense plays a big part and it’s accepted from the outset, that all participants can learn from mistakes.
Training is delivered to the same standard whoever, the customer although it can be tailored to meet specific requirements.
It draws heavily on experience gained over 65 years and promotes best practice. It is recognised as a world leader in the international Naval community.
So how do we develop this Work Up in the civilian cyber environment?
The key components are all available in the UK and many other countries. Basic check: setting the requirement, exercising-real and simulated, training and mentoring, feedback leading to revision of an incremental approach.
It just needs to be joined up.
The strengths of this Work Up approach include a less silo relationship between IT and OT Teams and individuals, and across business sectors. People find themselves working more closely together to manage converged technology and the human being plays a central role.
For businesses, a positive flow-on impact of this is reduced development, operational, and support costs and a confidence that any attack on technology systems can be dealt with authoritatively and with practicality.
Source: Getty Images, Jeff J Mitchell
45
Good training and awareness programmes can introduce the tenable cyber threats into employees’ working lives.
Managing the human element of the security chain

The chain here suggests all the various elements of an effective cyber security ecosystem, broadly categorized as “Process”, “Technology”, and “People”. Processes speak to the policies, structure, and procedures that we put in place to ensure that security is appropriately governed. I always advise that these processes be aligned to best practice such as ISO27001, COBIT, NIST. Technology broadly speaks to the systems, devices, technology solutions and tools deployed to prevent, detect, or respond to cyber incidents. Then, there are the “people”: those who execute the strategy, the “people” who write the processes, the “people” who manage the technology, the “people” who have to comply or flout the “processes”, the “people” who are the target of various phishing emails — phishing emails are when attackers send malicious emails designed to trick people into falling for a scam, typically, the intent is to get users to reveal financial information, system credentials, or other such sensitive data.
In fact, according to Verizon’s 2022 data breach incident report: 82% of data breaches involve
a human element, including phishing and the use of stolen credentials. (https://www.verizon. com/business/en-gb/resources/reports/dbir/). This figure is supported by further research conducted by the FBI’s Internet Crime Complaint Center (IC3), whose most recent Internet Crime Report found that phishing — including vishing (fraudulent phone calls), smishing (fraudulent text messages) and pharming (forced redirection to a fraudulent website) — is the most prevalent threat.

So, what are some ways to manage the human threat in your organizations? There are several ways, but I will focus on three in this article.

• Training your users - There is a difference between user awareness (which we do to tick compliance boxes) and training. If we had a small fire incident for example, a user who is “aware” may know where the fire extinguisher is, but they may not save the day if they do not know how to use it to put out the fire. However, the trained user not only knows where the fire extinguisher is, they also know how to use it, in order to put out the fire. Conducting 30-minute-long generic user awareness session or e-learning is a good starting point, but that has to be a part of a more elaborate training calendar for staff of the organization on cyber risk. These trainings must be bespoke and vary for procurement, finance, legal, HR, IT, executive management and so on.
• Understand your users – We talk a lot about asset categorization, which means know what your high value information and low risk assets are within your organization. High value refers to systems that act as a warehouse for sensitive information, information that should it be compromised during a breach would have catastrophic consequences for your

organization. Low value refers to systems that should they be compromised, the impact on the targeted organization would not be major. We need to apply the same concept to people. Who are your most naïve users? Who are your high-risk users, based on empirical data? And in comparison, who are the users with access to your organization’s most sensitive systems? The users who should their credentials be stolen by a malicious user, the consequences for your organization would be severe?
When it comes to cybersecurity education and training, the approach to training a user with access to your organization’s highly sensitive systems cannot be the same as the approach taken when training a user whose access is limited to non-sensitive information. Similarly, if you invest in technology which monitors the activities of your users, the level of observation cannot be the same for these two types of users. Therefore, it is vital that you properly categorize your users.
• Test the users – Simulating various cyber-attack scenarios (aka: an incident response plan) is not something to take for granted or something that can be ‘outgrown’. If you were to suffer a cyber breach today: Do your users know their role? Who should talk to the press? When speaking to the press what should be said and when should it be said? Who is to contain the issue? What is the isolation process? What is the first thing I do if I suspect that I have been hacked? Testing and running real life scenarios, without pre-informing the users being tested, will give you actual figures and data which you can then leverage into improving your cyber program.
Special Feature GET YOUR COPY HERE
“A chain is as strong as its weakest link”. This is a phrase that first appeared in Thomas Reid’s “Essays on the Intellectual Powers of Man,” published in 1786. At this time, there were no conversations about cyber security. Centuries later, it is the term that best describes the overall theme to managing cybersecurity risk.
Dr Fene Osakwe
cybernewsglobal.com 46
Global Cyber Security Leader - Best-Selling Author
The Home of Cyber
Dedicated to raising the standard of professionalism in Information Security and Cybersecurity. The Chartered Institute of Information Security (CIISec) was formed in 2006 to advance the professionalism of Information Security practitioners and thereby the professionalism of the industry.

CIISec is the only pure-play Cyber and Information Security institution to have been granted Royal Charter status and we currently represent over 20,000 individuals in the industry.
Our frameworks, in particular CIISec’s Skills Framework, have been developed in conjunction with industry, government and academia and are aligned with and recognised by other accreditation bodies.
The CIISec Skills Framework is widely accepted as the de-facto standard for measuring the competency of Information and Cyber Security professionals.
To find out more about the Institute, or membership of the Institute, then please contact membership@ciisec.org or visit our website - www.ciisec.org
47
WiCSME’s Journey in the Arab Region: Increasing women participation in Cyber Security
Women in Cyber Security Middle East (WiCSME) was founded in April 2018 as a volunteer group to build a robust, and dependable network of passionate female cyber security professionals in the Middle East and North African (MENA) countries, and eventually, increase the percentage of women in the workforce and encourage more female leadership in cyber security in the region.



The group has grown from 9 founding members to over 2000 members from 23 countries. These members, whilst being on the move, are deeply connected with the regional culture, and societal values, which makes it uniquely family-like.
WiCSME has a number of key capacity building initiatives, all of which were firsts in MENA. WiCSME Annual Conferences reflect on and celebrate the success of these initiatives. These Annual Conferences, began as a virtual event in 2020 and then in 2021 & 2022 as a hybrid with the onsite conferences being held in Saudi Arabia and Oman, respectively.
The WiCSME Annual Conferences are based on 3 key pillars:
1. Create Opportunity for Hands-on Learning through the WiCSME Capture the Flag (CTF) competition.

This is a 24-hour live hacking competition where one of the critical criteria to participate is having at least one female player on the team. From 2020 to 2022, we saw a growth in women’s participation in the CTF. The CTF saw a manifold
increase year on year, beginning with 35% of 380 participants in 2020 to 50% of 790 female CTF players in 2022.
2.Showcase Knowledge through multiple knowledge sessions.
The 2 days Annual conference provides an opportunity for the women in the region to share stage with many internationally successful and inspiring women, thereby not only unveiling the wealth of knowledge held by these regional talents, but also proving the much-needed platform to practice and motivate themselves to continue acting at world class.
3. Acknowledge and celebrate the female cyber jewels through the WiCSME Annual Awards.
It a formal way of recognizing, showcasing and appreciating the unique capabilities and contribution of women in cyber security in their capacities as rising stars, leaders in the field, or contributors to broader communities. Since start of these awards, we have felt a tremendous increase in the confidence of our members, transforming from a follower to a leader; contributing back to the community in their own unique ways.
These speak for the impact that WiCSME is making while recognizing the challenges that we often face in the regional setup. We have experienced historical moments by establishing a platform for our sisters in the region which is fuelled by respect, openness to ideas, constructive feedback and a passion to strive for excellence.
In 2022 we saw WiCSME evolving as a visible contributor in national and international cybersecurity leadership, such as Expo Dubai and United Nation’s OEWG (Open Ended Working Group). It was in the United Nation’s OEWG, where WiCSME leadership, represented by Dr. Reem Al Shammari, first boldly talked about our success so far and the dream of creating a United Nations of women in cybersecurity, creating a sustainable and secure future, for generations to come.
www.womenincybersecurity.me SCAN THE QR CODE cybernewsglobal.com 48
WiCSME continues to break barriers and achieve new records. We are creating history, delivering by example that, with the right minds connecting with the right vision, fuelled by passion, things can change for the better. We are also proud to mention that in this region, we have support of the best allies in the industry:
• various government organizations
• other global women in cyber organizations

• male allies
• many leading cybersecurity event organizers
They believe in WiCSME’s mission and support us as we try to find bigger and better ways of changing the norms of the future. WiCSME
is now an active contributor in many leading cybersecurity events, providing the channel for its members to showcase their expertise and contribution in this industry. In 2022, Middle East saw the highest numbers of female speakers in international events being held in the region, such as RSA Conference and Black Hat middle east.

This is a living proof that WiCSME is a multiplier. The members now have a network and safety net of like-minded women to lean on and grow together. We continue to collaborate with the public and private organizations, government, academia, and community programs. We hope that there will be a day when we will have the United Nations of Women
in Cybersecurity, uniting all the tremendous efforts of all women in cybersecurity groups around the globe to collectively support us in achieving the mission. As with the recent events of layoffs in the tech companies, we, together with other Women in Cybersecurity groups globally, need to work hand in hand to continuously engage, motivate, and inspire the women to stay stronger together, and remain consistently committed to this advocacy.
Women in Cyber Security
49
We were committed to start and now we need to be consistent to finish
SCOTSOFT2023
28.09.2023 Edinburgh
create. innovate. collaborate.
For more than 30 years, leadership and technology have combined at ScotSoft.
Over 1000 guests join us from around the world, not just to learn during the day, but celebrate the incredible young talent emerging from Scotland’s universities.
The day is jam packed with more than 40 speakers across our Developer Conference and Leadership Forum, and topped off with our Young Software Engineer of the Year Awards dinner in the evening.
We’re packed full of visionaries, technologists, business leaders and managers working in digital companies and end user businesses.
Join us and get inspired by our great line up of speakers at the longest running tech focussed conference in Scotland.

join us scotsoft.scot




CYBER SECURITY CONSULTANCY FOR INDUSTRIAL AUTOMATION AND CONTROL SYSTEMS IACS Consulting LTD, Balmoral Business Park Building 1, Aberdeen AB12 3JG info@iacsconsulting.com 01224 460212 UNDERSTANDING AND MITIGATING YOUR OPERATIONAL TECHNOLOGY SECURITY RISKS www iacsconsulting com ASSESSMENT | COMPLIANCE | SUSTAINMENT


























































Are your cyber defences FIT FOR PURPOSE? Sooner or later, you will let malware in. They only need to get it right ONCE. Cyber Centre of Excellence for Local Public Services From education & training, to detection, protection & response, we are the one-stop-shop for your cyber essentials. www.iese.org.uk/cyber-centre-of-excellence | enquiries@iese.org.uk An entirely new layer of cyber protection. Created by the sector, for the sector. Military grade defence, at high street prices. A unique combination of skills and solutions. Expert services that you can trust. Protecting your local community. elearning.ccoe.org.uk/elearning - enquiries@ccoe.org.uk


































































































 Samantha Alexander IASME Cyber Assurance Certification Manager
Samantha Alexander IASME Cyber Assurance Certification Manager

























































 By Malcolm Warr OBE, Chairman of CNI Scotland
By Malcolm Warr OBE, Chairman of CNI Scotland














































