
ISSUE 1


Editor in Chief Cyber News Global
Dear Reader,
Welcome to the Inaugural edition of Cyber News Global, this collaborative publication has been brought together by the UK’s leading Energy Sector Publication OGV Energy and UK Cyber Security Specialists, OSP Group Limited.
A combined wealth of experience, networks and specialists will ensure that CNG becomes a leading platform for the Cyber Sector in the UK, USA and Middle East.

We are delighted to welcome our Editor Elspeth Reilly

A talented writer with a Master of Science focused on Creative Writing from The University of Edinburgh who was also art Director for The University of Edinburgh’s creative writing anthology.
In addition, Elspeth also has a bachelor’s degree in graphic design from the American University where her activities included Vice President of the Graphic Design Club and Poetry Editor of the American Literary Magazine.

As you will see Cyber News Global will be in great hands,
Welcome on board Elspeth we look forward to working with you.
Thomas McCarthy
OSP Group Kenny Dooley
OGV Energy
of cyber threats and risks as they embark on their chosen studies. The UK government has worked tirelessly to establish a standard academic knowledge path to ensure that all UK cyber students are receiving the same level of education. The Cyber Body of Knowledge (CyBOK) sets out the academic guidance that ensures all cyber students receive a structured knowledge path.
OSP Cyber Academy is an approved training provider with National Cyber Security Centre (NCSC) certified training, which reinforces the learning outcomes of their training to a UK national standard.

If you have a contribution of relevant industry news please email Elspeth to editor@cybernewsglobal.com
Behind every single cyber attack there is a beating heart. The bad actor is human. The victim is human. So to combat the threat, we need to understand the human risks, good cyber security is as much a people function as it is a technical function. “ said Malcolm Norman, CISO at Wood.
Arab International Cyber Security Summit
The role of a virtual CISO


Cyber Criminals - Bad, Mad or Sad?
Cyber Leaders of Tomorrow Cyber Empowerment in the Middle East
The Six Serving Men of Cyber Resilience
From Cyber Forces to Cyber Citizens
A new home front - Darktrace
Citizen Developers the next big Cyber Threat?
Inherent Risks From Security to Resilience
Do you Know Your OT from IT? How to Close the Skills Gap News of Growth - OSP Cyber Academy
Cyber Criminals - Bad, Mad or Sad? Cyber Leaders of Tomorrow
Cyber risks are real in the business community. The 2022 Global Risks Report which was released by the World Economic Forum found that 95% of cybersecurity issues are The final thoughts on the journey of this
Have an inspiring day and read on!
5 11 12 14 16 22 25 26 28 32 36 41 44
The views and opinions published within editorials and advertisements in this Cyber News Global Publication are not those of our editor or company. Whilst we have made every effort to ensure
student placements.
Disclaimer:
have worked together with cyber
RGU Marketing
Blair
ACADEMY FORCES WITH WOOD AND TO CHANGE BEHAVIOUR
tremendous collaboration were echoed by former
student,
CYBER
Sandip Patel KC Managing Partner Aliant Chief Legal Advisor at OSP Cyber Academy
12 14 3
NCSC CERTIFIED TRAINING COURSE


This course Provides delegates with the opportunity to explore and discuss cyber risk and resilience and how to provide effective governance, risk management and strategic implementation. This course is for Board members including Executive Managers who need to provide governance and implement strategy for cyber risk, including data protection and resilience.




A co-opted core panel member of the British Standard (BS) 31111 Cyber Risk and Resilience Guidance for Boards and Executive Management. A chapter author for Managing Cybersecurity Risk – Case studies and Solutions. A chapter author for Managing Cybersecurity Risk – How Directors & Corporate Officers can protect their businesses.

CYBER RISK AND RESILIENCE COURSE FOR BOARD, EXECUTIVE AND SENIOR MANAGERS
RESERVE YOUR PLACE BOOK HERE: SCAN ME ALL THIRD PARTY TRADEMARK RIGHTS ACKNOWLEDGED If you require exclusive and tailored training for your team, email your enquiry to training@ospcyberacademy.com THE APMG INTERNATIONAL AND SWIRL DEVICE LOGO IS A TRADE MARK OF THE APM GROUP LIMITED, USED UNDER PERMISSION OF THE APM GROUP LIMITED ALL RIGHTS RESERVED
DELIVERED BY RICHARD PREECE, CHIEF TRAINING OFFICER OSP CYBER ACADEMY








6 – 8 December 2022 Exhibition World Bahrain arab-cybersecurity.com
Cybersecurity
Empowering Global Cooperation in
Organised by
Held under the patronage of HRH Prince Salman bin Hamad Al Khalifa Crown Prince, Deputy Supreme Commander and Prime MinisterThe Kingdom of Bahrain Co-Host Partner
Strategic
Partners Supported by Global Media Partner
Global Cybersecurity Market Share and Value
Global Cybersecurity Market Value ($bn)
Global Cyber Security Market Share
By Industry
› US cyber companies dominate, contributing almost 1/3 of revenue generated in 2022
› The average spend per employee on cybersecurity globally in 2022 is over $40.00
› The market is predicted to grow from $200bn in 2021 to $400 bn in 2026
Revenue in the Cybersecurity market is projected to reach US$146,324m in 2022

The market’s largest segment is IT Services with a projected market volume of US$69,624m in 2022
Revenue is expected to show an annual growth rate (CAGR 2022-2026) of 9.67% , resulting in a market volume of US$211,669m by 2026
The average Spend per Employee in the Cybersecurity market is projected to reach US$42.52 in 2022
In global comparison, most revenue will be generated in the United States (US$58,650m in 2022)
03
arab-cybersecurity.com
0 400 2019 2020 2021 2022 2023 2024 2025 300 200 100 Banking Financial, Insurance IT and Telco Retail Healthcare Government Manufacturing Travel and Transportation Energy Others


AICS Event Overview 04 arab-cybersecurity.com “ The Arab International Cybersecurity Summit correlates with the objectives and scope of Vision 2030 for the Kingdom of Bahrain’s National Cyber Security Centre, which considers Cyber Security an utmost important topic for our Kingdom and our industries & government entities. The Summit aims to facilitate knowledge sharing on the subject of cyber security, enhance cyber resilience, fight cybercrime and boost innovation, As the increase and acceleration of digitisation brings new cyber threats to our world.
Shaikh Nasser bin Hamad Al Khalifa National Security Advisor Royal Guard Commander 2500+ Attendees 70+ Speakers 70+ Partners & Sponsors An Arab League of Capture the Flag Competition Youth Leader Programs 20+ Startups
About
HH
CEO (Chief Executive Officer) SVP, VP, Directors, Heads, Sr. Manager, Managers CIO (Chief Information Officer) CTO (Chief Technology Officer) DirectorGeneral CSO (Chief Security Officer) CISO (Chief Information Security Officer) CDO (Chief Digital Officer) Defence Information Security Cyber Crime Cyber Security Threat Management Fraud & Risk IT Architecture Strategy Smart Services Digital Transformation e-Gov IoT (Internet of things) AI (Artificial Intelligence) Education Energy & Natural Resources Banking, Finance, Insurance & Real Estate Government Healthcare Legal Manufacturing Media & Broadcasting Telecom Transport (Aviation, Road, Railway) Utilities OEMs Distributors Cyber Sec Channel Partners Application Service Providers (ASPs) ISV IT Consultants System Integrators / VARs Communications/ Electronics Showcase of World Class Technologies and Solutions Job Title Industry Field 08 arab-cybersecurity.com 1000’s of cyber professionals from across the globe with real purchasing power will attend AISC 2022 to source new products, technologies and services along with network and be inspired by global experts and peers. › 3D Secure Authentication › Academic & Research › Anti-Virus › Audit Management › Big Data Security › Business Resiliency › Cloud-Native Security › Compliance Management › Cyber Intelligence Services › Data Centre › Data Loss (Leakage) Prevention (DLP) › Data Masking › Data Recovery › Data Security › Data-At-Rest Encryption › Data-In-Motion/Transit (Network) Encryption & VPN › DDOS Protection › Deception-Based Security › Digital Rights Management › Digital Risk Monitoring › Endpoint Detection & Response (EDR) › Enterprise Fraud Risk Management › Evolved Security Information & Event Management (SIEM) › Extended Detection & Response (XDR) › Firewall Configuration & Management › Human Resource Risk Management › Identity & Access Assurance › Identity & Access Management › Identity Governance › Industrial Security - Industrial Control System (ICS) & Supervisory Control & Data Acquisition (SCADA) Security › Integrated Risk Management › Intrusion Prevention Systems & Intrusion Detection Systems › IT & Security Risk Management › Laboratory / Certification › Legal Services On Cyber Security › Log Monitoring › Malware Detection & Analysis › Mobile Data Protection › Mobile Device Management › Multi-Factor Authentication › Network Access Control › Network Behavior Anomaly Detection (NBAD) › Network Detection & Response › Network Firewall (Includes NextGeneration Firewalls) › Network Masking › Network Monitoring & Forensics › Network Security / Cloud Security › Omnichannel Fraud Prevention › Operational Risk Management › Public Sector Risk Management › Risk & Vulnerability Assessment › Secure Access Service Edge › Secure File Transfer › Secure Internet Gateway › Secure Web Gateway › Security Orchestration & Automation › Third-Party Risk Management › Threat Detection & Response / Security Automation › Transport Access Control › Unified Threat Management › User & Entity Behavior Analytics (UEBA) › Web Application Firewall › Wireless Intrusion Detection System Our Exhibitors Technologies, Solutions and Products showcased at AISC 2022























ONCA TECHNOLOGIES www.oncatech.com Virtual CISO & Cyber Security Experts IT Support & Monitoring ISO 9001 & 27001 Compliance Risk Management Training Campaigns GDPR Compliance Business Optimisation & Data Analysis Digital Solutions Support & Guidance Security Gap Analysis System Organisation 10
THE ROLE OF A vCISO
With businesses steadily moving towards digital data storage, the increasing quantity of sensitive information held online is resulting in a heightened risk of cyber attacks.
Over 80% of UK organisations fell victim to a successful cyber attack in 2021/22, and as these attacks become both more sophisticated and more prevalent, comprehensive threat protection is absolutely vital to safeguard organisations. The role of a Chief Information Security Officer (CISO) has never been more in demand, and in turn, virtual CISOs (vCISO) are becoming a popular choice for many businesses.

Similar to a CISO, a vCISO is a cyber security expert responsible for managing an organisation’s information security, to protect its data and technology and ensure it meets its compliance obligations. The key difference is that a vCISO does so on a consultancy basis rather than as a full-time employee.


WHAT ARE THE BENEFITS OF A vCISO?
Expertise and experience

Like any CISO, a vCISO has the specialist technical expertise and up-to-date knowledge required to identify cyber vulnerabilities and implement security measures to address them.
As a consultant, a vCISO will also have a diverse breadth of experience gained from working across a range of industries with a variety of security programs. This can allow them to advise on best practice through a much wider lens, offering insight from several different perspectives.
Cost
When you consider the cost to an organisation of a successful cyber attack, the value of robust cyber security becomes clear. An attack including the breach of any personal data, for instance, can invoke a fine of up to 4% of an organisation’s global annual turnover.
Nevertheless, despite the risk of a lapse in cyber security, some businesses simply won’t have the budget available to invest in a full-time CISO.
vCISOs deliver reliable protection whilst also providing the flexibility to scale their service offering up or down according to an organisation’s requirements and budget. By utilising a vCISO, businesses only pay for the work they need, which can often be a more cost-effective solution than hiring a full-time CISO. For example, if a business only requires support with developing specific security solutions or performing risk assessments, rather than implementation and management of a full information security strategy, then commissioning a vCISO on a short-term contractual basis is the sensible option.
Flexibility
Given their capacity to take on both long- and shortterm contracts, vCISOs can be appointed to manage smaller-scale projects or immediate security requirements whilst organisations assess their longer-term CISO requirements. The vCISO can then work in tandem with the business to decide whether their role is expanded, or whether an in-house CISO is the most appropriate solution.
Similarly, vCISOs are often engaged to bridge a gap during the transition phase between an outgoing and incoming in-house CISO. Bringing an experienced vCISO on board is a much speedier process than hiring and bedding in a full-time CISO, and in some cases a vCISO can even support the recruitment process, helping to select and induct the right candidate.




A growing importance
At Onca Technologies we offer a full vCISO service, working both alongside in-house CISOs and on a standalone basis to provide tailored solutions - from security gap analysis to training campaigns, to GDPR compliance, to designing, implementing and managing bespoke information security strategies.

With digitalisation only on the rise, both CISOs and vCISOs will find demand for their services continuing to increase over the coming months and years. Cyber criminals certainly won’t rest on their laurels, so it will be more important than ever for all cyber security professionals to stay on the front foot when it comes to this evolving threat landscape; ensuring that whether outsourced or in-house, we’re providing the comprehensive and reliable protection that businesses need.

www.oncatech.com ONCA 11
Sandip Patel KC
Cyber Criminals - Bad, Mad or Sad?

As a baby barrister, I was assured that criminals were bad, mad or sad. Much later when I became involved in prosecuting major cybercrime cases, I discovered that most defendants did not fall into any one neat category and that their motivations and goals were often quite nuanced.
There was aka JiLsi who ran Dark Market, a global online bazaar for criminals dealing in drugs, guns and anything criminal, from a London internet café. In the virtual world, JiLsi was a god while in real life, he was a lonely and non-descript young man who I later learned in Misha Glenny’s book “Dark Market” also had a drug problem.
Then there was young Glenn Mangham who from his bedroom successfully hacked Facebook, stole their source code and caused an international stir sparking fears that Facebook was the target of industrial espionage. His actions were “the most extensive and grave” case of social media hacking ever to have come before a British court. His motive, however, was not greed but intellectual challenge. How he managed to infiltrate Facebook confounded some of the best brains at the Serious and Organised Crime Agency (SOCA) and well remember Glenn giving our experts a tutorial when questioned. Glenn was an ingenious young man who had previously breached Yahoo, but no one believed him.

There were the Hacktivists under the banner of Anonymous and their notorious operations. One was Operation Payback when in 2011 Anonymous launched an attack on the media giant Sony and they took down the PlayStation Network and other related PlayStation Websites.
There was Operation Yukon which targeted Pay Pal and Visa among others. Other victims included the FBI, CIA, UK Ministry of Defence and even SOCA when they intercepted a “secure” call between them and US law enforcement.
LulzSec, a splinter group, involved a Jake Davis aka Topiary. They carried out a retaliatory attack on HBGary, a US defence and security company with sensitive US government contracts, posting tens of thousands of sensitive documents including emails on the internet. The breach resulted in Congressional hearings and collapse of the firm. Jake was instrumental in the attack. Jake just 18 years’ old, was arrested in the Shetland islands of Scotland where he lived on his own. He was taken to London by a private jet, and experience which he described as the “best day of his life.” Police confiscated a laptop and a 100-gigabyte hard drive that had 16 different virtual machines. The hard drive also contained details relating to attacks and hundreds of thousands of email addresses and passwords. Jake is now a security


researcher, disclosing bugs to corporations as a part of their bounty programs.
Finally, there was young Seth aka Narko who started hacking at 14. When 16, he carried out attacks which impacted major internet exchanges around the world and was described by the Times newspaper as the “cyber-attacks which almost broke the internet.” The massive DDoS attack targeted junk mail tracker Spamhaus, knocking it offline. The company requested help from anti-DDoS specialist Cloudflare, which escalated the attacks. At its peak the attack was channelling 300 gigabits of traffic every second to Spamhaus servers, and the sheer scale of it began to impact on LINX – the London Internet Exchange. This in turn began to slow international internet traffic due to the volume of requests. On arrest, his computer showed multiple global active virtual machines. Data extraction took 36hrs. He had 43 IP addresses and rented servers in countries without mutual assistance. He used multiple online identities. There was 1 million lines of chat evidence. Seth was also a “gun for hire” who took down sites on demand. He had more than £72,000 in a UK bank account and kept multiple Bitcoin accounts. Seth made £10,000 in a good month.

I quickly learned that investigating and prosecuting cybercrime brings unique challenges which are not encountered in most traditional crime investigations including multiple jurisdictional issues, expertise, technology, new investigation workflows and of course, attribution, namely, proving the person in the dock is the virtual perpetrator.

 Glenn Mangham
Jake Davis aka Topiary
Seth aka Narko
Renukanth S. aka JiLsi
Glenn Mangham
Jake Davis aka Topiary
Seth aka Narko
Renukanth S. aka JiLsi
cybernewsglobal.com 12
Managing Partner Aliant Chief Legal Advisor at OSP Cyber Academy


DON'T BE THE NEXT VICTIM! AN AVERAGE SECURITY BREACH WILL COST YOUR BUSINESS... £4.3m UNLIMITED REPUTATIONAL DAMAGE FINANCIALLY 326 DAYS TO DETECT AND CONTAIN AFTER LISTENING TO THE FBI, CIA AND OTHERS, POP OVER TO THE CELERITY STAND FOR A CHAT REGARDING SIMULATED CYBER ATTACK AND HOW WE CAN SUPPORT YOUR CONTINUOUSLY EVOLVING CYBER STRATEGY www.celerity-uk.com
OSP Cyber Academy, Wood, and Robert Gordon University (RGU) have joined forces to help shape the cyber leaders of tomorrow.

At a recent initiative launch at RGU’s school of Computing in Aberdeen, Wood’s Chief Information Security Officer, Malcolm Norman, endorsed the cyber awareness initiative between OSP Cyber Academy and RGU Cyber Faculty. The training initiative has been generously funded by Wood which provides vital cyber awareness induction training to every cyber student within RGU.
“ RGU has a long history of graduate employment, being one of the UK’s leading vocational institutions. In order to maintain this standard, the relationship that RGU has with companies is vital — none more so than with Wood; this relationship is so important for RGU, as

the students that gain placement, feed back their experiences into their chosen faculties, which enables RGU to shape and develop their courses. The more input that RGU can have from industry the better. There are benefits on both sides — very much a reciprocal relationship — working with industry enables RGU students to be better equipped when graduates are looking for employment. Preparing the cyber students is a perfect example of that collaboration with OSP Cyber Academy and Wood, one that RGU is very grateful for. ” said Chris McDermott, a lecturer of Computing Science and Cyber Security with a passion for human factors education.
The emphasis of this initiative is to ensure that all new cyber students have an awareness
OSP CYBER ACADEMY JOIN FORCES WITH WOOD AND RGU TO CHANGE CYBER BEHAVIOUR cybernewsglobal.com 14
of cyber threats and risks as they embark on their chosen studies. The UK government has worked tirelessly to establish a standard academic knowledge path to ensure that all UK cyber students are receiving the same level of education. The Cyber Body of Knowledge (CyBOK) sets out the academic guidance that ensures all cyber students receive a structured knowledge path.
OSP Cyber Academy is an approved training provider with National Cyber Security Centre (NCSC) certified training, which reinforces the learning outcomes of their training to a UK national standard.

“ Behind every single cyber attack there is a beating heart. The bad actor is human. The victim is human. So to combat the threat, we need to understand the human risks, good cyber security is as much a people function as it is a technical function. “ said Malcolm Norman, CISO at Wood.

Cyber risks are real in the business community. The 2022 Global Risks Report which was released by the World Economic Forum found that 95% of cybersecurity issues are attributed to human error.
Without awareness or education on cybersecurity, businesses are susceptible to attack as those unaware of cyber risks are the most likely to be targeted and exploited. The same cyber risks and vulnerabilities exist for academia, especially when students are first embarking on their studies with no initial level of cyber awareness.

The final thoughts on the journey of this tremendous collaboration were echoed by former RGU Marketing student, Blair Wallace. Blair joined OSP Cyber Academy on a placement 4 years ago and is now shaping his own career path within the business community:


have worked together with cyber student placements.
“ With 5.6 million companies in UK at risk of cyber attack, there is a huge shortage of capability to meet the cyber demands required to ensure that our businesses and people are safe when online. With less than 1 in 9 business in the UK providing cyber awareness training for their staff, there is a huge shortfall in cyber education. There is a large chunk of the business community that is not raising awareness. It’s so important that every business leader should be looking to raise cyber awareness amongst their staff. For me, cyber security awareness training is essential for anyone going into the business world and for their own online safety. This is where OSP Cyber Academy can provide that critical real-life training, awareness, and education needed. ” These were just some of the thoughts of former Police Chief Inspector and now Chief Operating Officer at OSP Cyber Academy, Irene Coyle.
“ Marketing and management was my chosen degree course which is very much people orientated. People outside of cyber security would think that cyber is all about technology, numbers on a screen and servers, and to a degree that is true however cyber is very much a human factor. People just don’t realise until they are in the cyber industry, not until they have experienced a cyber attack or a data breach, which happens a lot more than you would think. It’s then that they begin to understand just how much relates to the human factor. It’s just as important to educate your workforce as it is to focus on your technology and hardware, that is something that has become so apparent to me working with so many of the clients here at OSP Cyber Academy. ” Blair is now a vital member of the OSP team, providing support as the business and digital marketing lead.
Collaborations like this do not have all the answers; unfortunately, there is NO silver bullet to solve all of the challenges that the cyber security industry faces. One thing that is critical is education and awareness, which every company should provide for its workforce to ensure that they have the opportunity to identify a risk before it escalates into something catastrophic.
This is not the first collaboration between Wood and RGU, and the wider business community, as for a number of years they
“The Wood Business Information Security Team learn as much from the students that join the cyber team on placement as the students do from Wood. We get enormous benefit from the curiosity of the students who join Wood with an academic stimulus and learning. In return, Wood layer on to that practical experience, which is vital context for the students’ future development. It’s a win-win situation for us all.” said Malcolm Norman..
The key message is
that if we all work together to educate and raise awareness, we can make genuine change as we endeavour towards our collective goal of a positive cyberculture.
15
Irene Coyle, Chief Operating Officer, OSP Cyber Academy
“Within our garden close I saw thee—I was guide for both—a little child, along with my mother, plucking dewy apples. My eleventh year finished, the next had just greeted me; from the ground I could now reach the frail boughs. As I saw, how I was lost! How a fatal frenzy swept me away!”
Many of us have come to the field of cybersecurity from diverse educational backgrounds and professional experiences. As a former classics major in college, I loved reading original texts in Latin, Classical and Koine Greek, and then translating them into English, French and German. The above lines are long held to be Voltaire’s favorite lines in Latin: “from the ground I could now reach the frail boughs”—this line, with its stunning syllables of interposition, embodies the promise of moving from callow childhood into adolescence, the alacrity of self-empowerment.
meaningful progress in diversifying the workforce will happen. Inclusion is the foundation, and from it, diversity will expand. That’s our focus and we’re honored to have such a thriving global community of over 6.3k members, 54 professional affiliates and 214 student chapters keeping the momentum and advancement opportunities for women in cybersecurity going strong.” WiCyS has now grown to have representation in over 70 countries in under a decade.
Lynn Dohm is the Executive Director of WiCyS, with more than 25 years of organizational and leadership experience. Dohm has successfully collaborated with businesses, nonprofits and NSF-funded grants and helped produce outcomes that aligned with their cybersecurity business goals.


As the Arab International Cybersecurity Summit begins on December 6th, 2022, we take the time to honor the success, sustained contributions, and advancement of women in the Middle East in cybersecurity, notably through Women in Cybersecurity Middle East (WiCSME) organization. The WiCSME launched in 2018 through the vision and effort of founding members Abeer Khedr, CISO of the National Bank of Egypt, and Dr. Reem Faraj Al-Shammari, CISO of the Kuwait Oil Company, starting as a WhatsApp group with 20 members. The organization grew 1400% in the first year of its inception, and now has supporting members in the UAE, Egypt, Kuwait, Oman, Saudi Arabia, Jordan, Qatar, the United Kingdom, India, New Zealand and Ukraine. The WiCSME trajectory of growth remains strong into 2023, and its continued collaboration with global nonprofits, including Women in Cybersecurity (WiCyS), evidences a substantial trajectory toward the growth of women in the cybersecurity arena in all roles.


In a recent conversation with Lynn Dohm, Executive Director of WiCys, Dohm noted “at WiCyS, we continually start the conversation to recruit, retain and advance women in cybersecurity with the power of inclusion. Cultivating a culture of inclusion is where

The theme of cybersecurity culture, specifically with women as anchors for its genesis and collaboration, continues through the work of Christiane Wuillamie, OBE: “Cybersecurity needs women more than ever. Women are natural collaborators, which makes their contribution(s) to building culture in cybersecurity an essential part of the cyber ecosystem.”
Ecosytem. Culture. Cybersecurity continues to foster opportunities to collaborate, allowing us to go beyond conventional thinking and define what will be next. As women both entering and thriving in the cybersecurity arena, it is our responsibility to both carefully curate and support this curation of culture.
As we look out from the Exhibition World Bahrain Center, we see skyscrapers that rise as sablethroated music and harmonize with the desert sky. We find and embrace our collective industry knowledge and strength, which stretches across many continents-it is a roborant force that cannot be suppressed.

I invite you to connect, and to embrace building this cybersecurity ecosystem as our responsibility. Looking back at Vergil’s guidance--all of its branches, across all continents, will indeed, be tangible.
Do not be afraid to stretch and aim as high as you can. We’ll find our wings on the way down, together.
Christiane Wuillamie, OBE, is an expert in shaping technology, security, business systems and cultural change to help companies across the globe solve complex business challenges.

Wuillamie has won many awards, notably an OBE for her services to business and tireless support of SMEs. Recently Wuillamie has participated in a book on Responsible Leadership sponsored by the United Nations, which will be released on November 30th, 2022 (launched in Geneva on December 16th and in London on January 20th).
Margaret Morton is a solution-oriented information security senior leader who combines extensive industry knowledge with solid program and change management skills to drive global enterprise-wide security and governance strategies. She served on the Founding Board of WiCyS from its funding stage and has delivered impactful security initiatives for AmLaw 25 law firms, two Federal agencies, and leading investment banks. Morton is currently contracted to the Office of the CISO at a French international banking group, also the largest cooperative financial institution in the world. In her spare time she is thrilled to support “FLYGIRLS” a forthcoming, dramatic television limited series that will feature true stories and previously unseen footage of the legendary Women Airforce Service Pilots of World War II (of which her Aunt was a service member).
cybernewsglobal.com 16
Vergil’s eighth Eclogue (tr. H. Rushton Fairclough)
The Home of Cyber
Dedicated to raising the standard of professionalism in Information Security and Cybersecurity. The Chartered Institute of Information Security (CIISec) was formed in 2006 to advance the professionalism of Information Security practitioners and thereby the professionalism of the industry.

CIISec is the only pure-play Cyber and Information Security institution to have been granted Royal Charter status and we currently represent over 20,000 individuals in the industry.
Our frameworks, in particular CIISec’s Skills Framework, have been developed in conjunction with industry, government and academia and are aligned with and recognised by other accreditation bodies.
The CIISec Skills Framework is widely accepted as the de-facto standard for measuring the competency of Information and Cyber Security professionals. To find out more about the Institute, or membership of the Institute, then please contact membership@ciisec.org or visit our website - www.ciisec.org
17






















ITAREPO O N A L TECHNOLOGY CYBERAWAREN E S S ENILNO O T C Y B E R A W A R E N E S S O S P C Y B E R A C A D E M Y O S P C Y B E R A C A D E M Y JBUS E C T ACCESSREQUE S T (SAR)COURSE O ENILN S A R C O U R S E HTAP W A Y TO INFORMAT ION SECURITY M O D SELU O S P C Y B E R A C A D E M Y D A T A B R E A C H HTAP W A Y TO INFORMAT ION SECURITY M O D SELU O S P C Y B E R A C A D E M Y M O B I L E D E V I C E S E C U R I T Y HTAP W A Y TO INFORMAT ION SECURITY M O D SELU O S P C Y B E R A C A D E M Y C Y B E R S E C U R E A T H O M E HTAP W A Y TO INFORMAT ION SECURITY M O D SELU O S P C Y B E R A C A D E M Y P A S S W O R D S & A C C E S S M A N A G E M E N T HTAP W A Y TO INFORMAT ION SECURITY M O D SELU O S P C Y B E R A C A D E M Y P H I S H I N G & S O C I A L E N G I N E E R I N G HTAP W A Y TO INFORMAT ION SECURITY M O D SELU O S P C Y B E R A C A D E M Y R A N S O M W A R E & M A L W A R E IN ASSOCIATION WITH ALL THIRD PARTY TRADEMARK RIGHTS ACKNOWLEDGED NCSC CERTIFIED ELEARNING COURSES OTHER ELEARNING COURSES NCSC CERTIFIED CLASSROOM / VIRTUAL COURSES THE APMG INTERNATIONAL AND SWIRL DEVICE LOGO IS A TRADE MARK OF THE APM GROUP LIMITED, USED UNDER PERMISSION OF THE APM GROUP LIMITED ALL RIGHTS RESERVED

19





End-to-end services covering every challenge throughout your cyber security journey.
cybercx.com.au






Phriendly Phishing is a cyber security awareness and phishing simulation training solution that educates and empowers your organisation and employees to help mitigate security attacks. We train not trick through empathetic learning that is customised to each learner's journey The platform is fully automated, digitally delivered and is localised with relevant and engaging content of all cyber attacks begin with Phishing emails 91% UK's average cost of a data breach in 2022 £4.4M Safeguard your Organisation with Phriendly Phishing. of all security issues are caused by human error 95% Save time with peace of mind Automated system and responsive & local support team Mitigate huge financial and reputational loss. £4 4M is UK's average cost of a data breach in 2022 Easily track staff performance and create long-lasting behavioural change Delivering value and measurable outcomes W: phriendlyphishing.com/uk E: info@phriendlyphishing.com T: 0800 0488 195 Get in touch today
The Six Serving Men of Resilience and Why it is a Strategic Endeavour
Richard Preece Chief Training Officer OSP Cyber Academy

Why and What.
All good strategy starts with a diagnosis of the challenge, or “what is going on here?” This diagnosis should seek to identify the critical aspects of what can appear to be an overwhelming complex reality, with lots of fluff, fear, uncertainty and doubt (FUD), and buzz phrases. Alas this article may be a bit guilty too!
By taking a more systems thinking approach (see figure below), which looks below the surface of events, it is possible to identify patterns and trends, some of which may be hard trends (will happen), whilst others may be soft trends (may happen). Looking further below the surface, systems structure becomes more apparent, including how the different parts are related and what influences the patterns. Finally, by challenging mental models and worldviews, values, assumptions, and the beliefs that shape the system can be identified.

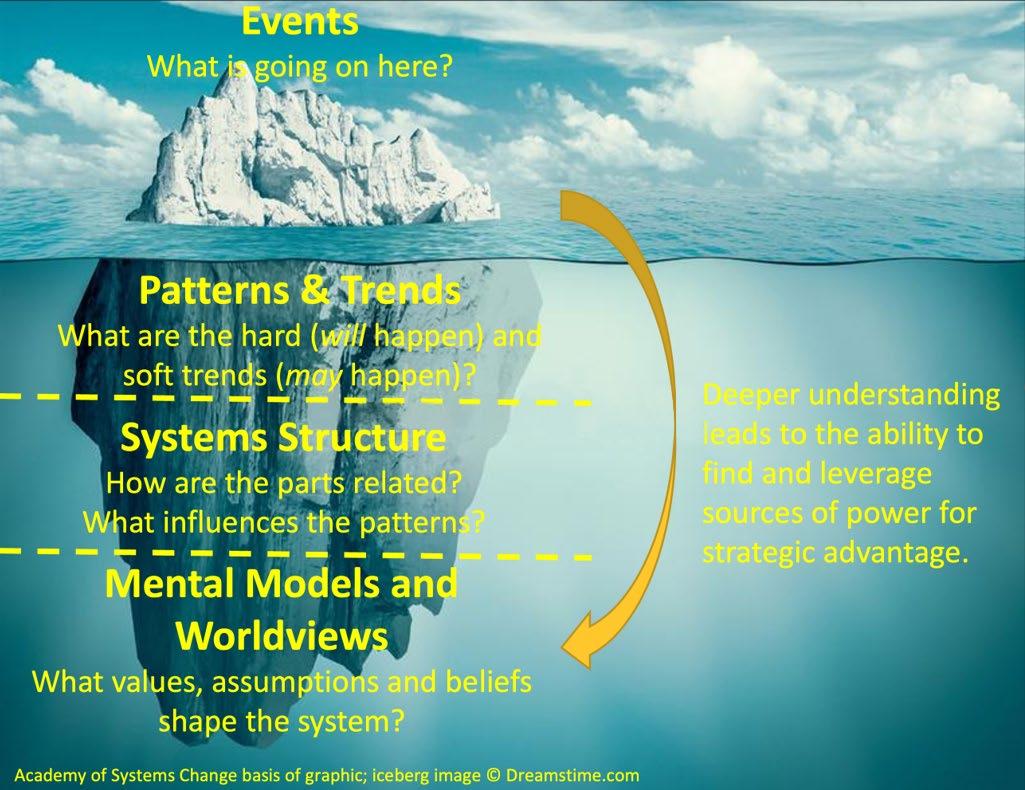
The deeper the understanding that this diagnosis is, the greater the ability to find and leverage strategic advantage as the basis of strategy.
From a resilience perspective, there are perhaps five overlapping mega disruptive forces, which are creating a polycrisis in the 2020s. These disruptive forces overlap and influence eachother and may be summarised as:
• Geo-political tensions between collaboration, competition, confrontation and conflict;
• Climate change, adaptation and the energy transition, leading to changing resources, connections and dependencies;
• Demographic and culture changes as the population grows, with different age ratios and immigration flows;
• Democratic and financial mis-alignment with rising debt, inequality, vulnerability and economic risk, leading to a new but unclear socio-economic model in the West; and
• Digitalization with exponential growth in use and value of data, technology, innovation, opportunity and risk.
Individually each disruptive force should drive the imperative for greater resilience and a strategic approach, not just at the organizational level, but internationally, nationally and the personal level. When combined, they make the case to not just to have a manged capability that satisfies regulators and other authorities. But provides clear focus on delivering organizational essential outcomes and understanding the potential impacts upon not just your organization, but on customers, other stakeholders and the environment.
Once this diagnosis of the challenge to your organization is understood, then a goal seeking strategy, to guide the overall approach to cope with the disruptive forces and to overcome obstacles to achieving your resilience goal, within your organization’s wider strategy.
Board members and executives are busy people. They are constantly bombarded with this, that and the other, all of which claim they must be the priority! One of these bombardments is that resilience, sometimes with a specific prefix of business, organizational, cyber, operational, etc, is a priority and is a board issue.
The reality is resilience needs to be considered strategically and embedded into strategy. All good strategy involves choices. So the first choice and strategic decision, is recognise and to treat resilience as an enabling goal. A goal that can enable your organization to be more agile in seizing of opportunities, whilst mitigating the risks that may impact your organization and stakeholders.
So let’s take a simple six serving men approach of why, what, who, when, where and how resilience can be addressed by boards and executives to integrate resilience into strategy and implement it (95% of strategy!).
“I had six honest serving men. They taught me all I knew. Their names were: Where, What, When, Why, How and Who.”
Rudyard Kipling, The Elephant’s Child
cybernewsglobal.com 22
Who, What, When.
How.
Diagnosing the challenge and identifying the strategy approach is important, but only 5% of strategy. Implementation through a set of coherent actions to deliver a resilience capability is 95% of the strategy. Further, due to the complexity and dynamic changing context, this will need to become a constant endeavour from board room to server room and across the organization and its wider eco-system.
To assist with this a strategy based upon stable, certain, simple and clear (SCSC) objectives, can provide the mechanism to deliver coherent actions to develop resilience capability across the organization. These objectives should be underpinned by principles (outputs and outcomes to achieve) with supporting guidance and indicators of good practice to interpret and apply the principles to context. Whilst specific standards may be appropriate for well-defined use cases.

The sum of this strategic approach enables topdown governance to set the overall strategy and provide oversight, with supporting accountabilities and responsibilities. But also enables bottom-up de-centralised decision-making, empowered by a unifying purpose and framework. This purpose and framework can create stable structures and processes, but with a dynamic agile capability that can anticipate opportunities and mitigate risks and inevitable disruptions.
The evidence is clear that in the sort of polycrisis environment displaying characteristics of volatility, uncertainty, complexity and uncertainty (VUCA) this mixture of top-down strategy and bottom-up implementation with effective governance, is most likely to deliver success.
This does not undermine compliance-based approaches, but does overcome one of the most common obstacles, that of bureaucratic excesses of adherence and the associated risk adverse escalation of decision-making which stifles organizational dynamism.

Ultimately this is about culture and in particular the knowledge, skills, attitudes and behaviours (KSAB), that are both explicit and implicit in the organization.
This requires leadership and commitment from boards and executives, to make clear that resilience, in whatever form (business, organizational, cyber, operational) it is focused upon, is a strategic goal. That it requires integrating capability into the organization, that because of the insights based upon the diagnosis, it is necessary for fulfilling the purpose, wider strategy and essential outcomes of the organization.
Finally to communicate that this is an endeavour that will be resourced and invested in. That it will ultimately lead to both continuous improvement and innovation, that exploits the disruptive opportunities, whilst mitigating the harms and risks of disruptive 2020s.
As with all cultural change, this starts with developing people, through awareness, education, training and on-going support. This KSAB is the foundation for empowered and motivated people ready to act through a set of coherent actions to deliver a resilience capability and strategic goal.
Don’t be the next boardroom cyber victim!
23
From Cyber Forces to Cyber Citizens
A future facing approach to digital skills
As the world moves out of lockdown and back to a ‘new normal’, digital dependency grows ever greater.
Sally Walker, Human Leadership in a Digital World
Sally Walker spent 25 years in the national security community, 16 years of which were in the senior civil service in various crisis management and military support roles.
A civilian graduate of the Higher Command and Staff Course at Shrivenham, her final job in government was to design and deliver the National Cyber Force, as Director Cyber for GCHQ and in full partnership with Ministry of Defence. She also had joint responsibility for the National Offensive Cyber Programme, led many aspects of the UK’s partnership with US Cyber Command, and was GCHQ’s diversity champion for over a decade.
She is currently a board chair in local UK government and a non-executive Director for her “new tribe”, WithYouWithMe, while also working with a portfolio of clients from all sectors of society.


The lifeblood of society is internet connected
Digital systems and data underpin the very foundations of our society.
The world of communication – estimated 7 billion smart phones on the planet – integral to everyday life. Shopping, family connections, business meetings, and supplementary schooling –, all conducted in the digital environment.
The operating systems that live depend on: power, water, transport, health. The beating heart of the world, controlled remotely, often built for a different threat landscape.
Automated human assistants monitoring and sense making, bringing the world ever closer and ever faster; tracking data, people, money, deliveries around the globe and to the doorstep. All done using technology so sophisticated it was restricted to military use and only recently has been made available to all.
Data, networks, the internet of things. Volume, velocity, variety, and constantly under threat.
“Critical national infrastructure”, once the bastion of must protect and have to defend, has become a sprawling, complex mass of vulnerability and interdependency (in the UK the CNI spans 13 infrastructure sectors and includes “all facilities, systems, sites, information, people, networks and processes for a country to function and upon which daily life depends” ).
As in any other walk of life, where there is dependency, there is opportunity to project power or exploit.
Insider information or intelligence. Breaches of confidentiality to obtain data at scale.
Financial benefit. Exploitation of vulnerability and dependency (ransomware)

Command and control. Exploiting the integrity of technology to dominate geography, physical assets or people.
Functioning societies require trusted sources of power, water, finance, emergency response, healthcare… The cyber war isn’t to stop a ‘digital pearl harbour’ – but it is about keeping the lights on, everywhere, now and tomorrow. Contesting the dark side of tech; including legitimate use of harmful techniques back against those that would otherwise do society harm. Often o ut of sight and out of mind – but no less important for that.
and timely information and on trusted capabilities and logistics chains. All of us depend on each of us, to have a safe and secure digital world.
And yet, still, there is a vast and growing skills gap. Nations are chronically short of digitally skilled personnel. Nation states have built their cyber forces, and their cyber centres need cyber citizens.
Citizens don’t have to be sophisticated in their skills or specialists in their roles to add value to the collective digital health of a system or society. The most basic of training or cultural awareness can assist in recruiting and deploying new personnel to the front line of the digital world – not just to defence, or to cyber specialist functions, but to banks, schools, energy companies, transport logicians, manufacturers, medical research centres. The people exist, as the 160k strong IT army of Ukraine is showing. Mobilising citizens can be done, with a sense of purpose and self-belief.
The solution is part technology. Secure by default, trusted at its core. Better designed and managed to be alert to the potential for unauthorised use, or deliberate misuse. Digital data and digital infrastructure is a nervous system to the globe; confidentiality, integrity, and availability is vital to the functioning of a healthy modern society.

But according to just one global investigation into data breaches , more than 80% of the problem is human. Cyber isn’t (just) tech, and cyber security isn’t for the IT department to fix. Humans are error prone, with instincts honed over millennia for a different threat and a different world. A front-line operator in the digital battlefield becomes anyone who depends on accurate
Providing practical, low cost and high-quality training to all citizens builds depth in national strategic resilience and enable a whole of nation approach to cyber security, even cyber conflict. Scalable platforms already exist to provide the training.
Dealing with the digital skills shortage requires the brain power of all of society. The specialists are vital (those who can read and write – or code) – but for most, the challenge is developing digital literacy with a difference –the ability to read, write, and think. People with knowledge have become experts on yesterday’s problems; people with curiosity and motivation will solve tomorrow’s challenges. Thinking differently is the cyber superpower.
The brains, the training platforms, and the ability to assess potential are all out there. Government, industry, and education institutes must do better and double the talent pipeline for digital skills. And they can.
cybernewsglobal.com 24
WithYouWithMe: Future-facing skills, data led employment
All Brains
By discovering a pipeline of talent that no one else sees, WithYouWithMe is revolutionising employment. The digital skills shortage will only be fixed by building talent from overlooked communities. Those without the ‘right’ educations, or the right experience, or the right connections. We need to help people understand what they can do, not focus on what they can’t (or have not – yet).

With Aptitude
Schools, universities, and employers have heard the digital skills challenge as moving from reading and writing, to reading, writing, and coding.
Certainly, demand for coders outstrips supply. But everyone will use technology ; – not everyone will build it. The biggest education gap is in reading, writing, and thinking (and coding).

The solution? Assessment processes too often test what is known, not how a student will cope with the unknown. Aptitude, problem solving, ability to work collaboratively on new and innovative challenges – these are the super powers of the 21st century workforce.
And Attitude and Skill
The WYWM platform upskills people (many for free) in technology-based roles based on aptitude testing and intense hands-on training. Then, working with clients, WYWM identify requirements of existing workforce requirements, allocating program graduates with the right complementary skills into those vacant roles. It’s a win win.


Fixing it Fast
Scalable technical infrastructure enables rapid end to end recruiting, identifying, training, and mobilising of citizen cyber talent. Informed innovation of HR processes, being data driven in decision making, ensuring we recruit, recycle, and retain people? Using tech and data innovatively, and providing an immediate solution to bringing people in, and on, at pace and scale.
The opportunity to solve the digital skills gap requires a whole nation approach; it requires bold decisions by Defence, Government, and industry leaders; and it requires a wholesale change to the approach to human talent. Digital platforms are the scale solution across education and training to recruitment and retention of skilled personnel – and the answer exists for all.

For more information visit withyouwithme.com 25
A NEW HOME FRONT
Cyber warfare is increasingly being conducted outside of centralized military or government efforts. In Ukraine, without direct government supervision, thousands of private individuals and organizations are involving themselves in the cyber-war against Russia. Yurii Shchyhol is head of Ukraine’s State Service of Special Communications and Information Protection. Speaking to Politico, he commends a group of “more than 270,000 volunteers who are selfcoordinating their efforts and who can decide, plan, and execute any strikes on the Russian cyber infrastructure without Ukraine getting involved in any shape or form.”
‘Hacktivists’ have existed since the 1990s, but the term seems ill-suited to the scale and approach Shchyhol is describing. They might instead be labelled an auxiliary cyber force, playing a supportive role in a larger military effort. Shchyhol himself calls them “an army”.
OPEN-SOURCE WARFARE
In the modern cyber landscape, anyone with a computer and a basic skill set can contribute to a war.


Depending on who and perhaps where you are, this fact is inspiring, concerning, or a little of both. The challenge of distinguishing between official nation-state attacks and hacktivists raises certain issues, making it possible, for instance, for nation-states to conduct devastating attacks against critical national infrastructure from behind a mask of proxy criminal organizations. The ties between nation states and these
organizations may be suspected, but any accusations are rarely confirmed.
The converse problem is seen when idealistic individual actors launch provocative attacks with the potential to stoke tensions between nation states. Recent DDoS and defacement attacks against Taiwanese government sites and businesses are largely being attributed to Chinese hacktivists, but with the perpetrators unidentified, these attacks remain a concerning question mark and do little to ameliorate sharply rising tensions. A spokesperson for Taiwan’s ruling party has already said in a statement that these attacks are “unilaterally raising the situation in the Taiwan Strait.” Official Taiwanese websites, like that of the Presidential Office, the Ministry of National Defense, and a municipal Environment Protection Bureau have all been targeted, the latter defaced with five Chinese national flags.
A spate of similar defacements preceded Russia’s February invasion of Ukraine, with more than a dozen Ukrainian national websites made to display threats like, “be afraid and expect the worst”. Once again, the perpetrators of this attack remained unconfirmed, with Ukrainian government institutions accusing the Russian Federation, and Russia denying all involvement. The degree to which modern war efforts can be influenced by – or concealed behind – individual threat actors is a new and disconcerting symptom of the modern cyber landscape. There are, however, more official ways in which cyber warfare has moved beyond government and military organizations as well.
CALLING IN A PRIVATE CAVALRY
Just 15 months after it was opened by President Volodymyr Zelensky, the UA30 Cyber Center in Ukraine lies largely empty. It is located in an unsafe part of the war-torn country, and its operations have had to be moved elsewhere. In the time between its opening and Russia’s invasion in February, however, the center was able to host more than 100 cyber security training sessions. These sessions, which involved realistic cyber-attack simulations, hackathons, and other competitions, were attended by some military operators, but also by large numbers of civilian contractors and private sector representatives. Their attendance was part of an intentional and significant effort to involve the private sector in Ukraine’s cyber defense efforts.
Shchyhol explains, “a lot of private sector IT cyber security experts are either directly serving in the Armed Forces of Ukraine or my State Service or otherwise are indirectly involved in fighting against cyber-attacks.” This is the realization of the UA30 Cyber Center’s aim: using crucial assistance and expertise from the private sector in national cyber-defense efforts, and bolstering the security of those organizations on which Ukraine’s critical national infrastructure depends. As we have seen with attacks against Ukrainian telecom and internet providers, organizations operating the infrastructure which underpins a population’s daily life are often the first – and most appealing – targets for attackers looking to create disorder within a nation.
cybernewsglobal.com 26
The part we all play in a modern cyber war
It is not only Ukraine’s own private sector which is lending a hand. International organizations like SpaceX and Amazon have contributed to Ukraine’s efforts by providing technology and infrastructure, as well as their own expertise and services. In its report on Early Lessons from the Cyber War, Microsoft suggests that “defense against a military invasion now requires for most countries the ability to disperse and distribute digital operations and data assets across borders and into other countries”. With cloud services provided by Amazon, Microsoft and others, and data now hosted across Europe, Ukraine is managing to do just that. Like its army of guerrilla cyber-fighters, the involvement of private organizations is dispersing and bolstering Ukraine’s war effort.
THE NEW HOME FRONT
Beyond these direct contributions, however, Shchyhol also notes those private sector organizations supporting the cyber-war “indirectly”. These indirect efforts have been a focus of US government statements on cyber security since the beginning of the conflict. A statement from President Biden in March read, “I urge our private sector partners to harden your cyber defenses immediately”, a message which has been repeated and reinforced by CISA.
The great responsibility which private organizations have for critical national infrastructure has been highlighted in attacks like that on Colonial Pipeline last year, but organizations in every industry can offer opportunities for nation-state attackers. When

more organizations are sufficiently prepared for cyber-attacks, the nation as a whole becomes stronger.
In its report, Microsoft calls for “a common strategy” to thwart modern cyber-threats, which includes the need for greater public and private collaboration and advances in digital technology, Artificial Intelligence (AI), and data. By adopting stronger defenses, and employing well-suited emerging AI technologies, organizations can accelerate the detection and prevention of threats, and contribute to national security in the face of constantly developing international cyber-threats.

When cyber-attackers are provided with funding, coordination, and thorough threat security intelligence, they can create scores of never-before-seen attacks, which circumvent pre-established security rules and avoid detection. As attackers develop their approach, so must defenders - not just by employing the latest technologies, but by embracing the changes in defensive strategy which those technologies enable.
Defenders need to pivot away from focusing on patterns and predictions, and concentrate on understanding the landscapes and ‘normal’ operations of their digital environments. With this approach they can harden attack paths, visualize their internet-facing attack surface, detect the smallest deviations from ‘normal’, and disrupt attackers before damage is done. For private sector organizations, auxiliary cyber forces, and hacktivists alike, focusing on defensive rather than offensive action will be the surest way to win the battle and the war.
ABOUT THE AUTHOR
Marcus Fowler
CEO Federal, Darktrace
As SVP of Strategic Engagements and Threats, Marcus works closely with senior security leaders across industries on cyber security strategy and business resilience, including across Darktrace’s Federal Division. Marcus focuses his research and analysis around emerging and next generation cyber threats, trends, and conflicts. Prior to joining Darktrace in 2019, Marcus spent 15 years at the Central Intelligence Agency developing global cyber operations and technical strategies. He has led cyber efforts with various US Intelligence Community elements and global partners. Prior to serving at the CIA, Marcus was an off icer in the United States Marine Corps. Marcus has an engineering degree from the United States Naval Academy and a Masters’ Degree in International Security Studies from The Fletcher School. He also completed Harvard Business School’s Executive Education Advanced Management Program.

risk and harden security with the
Cyber
Loop. Find out more at darktrace.com 27
Marcus Fowler
Reduce
Darktrace
AI
WHAT IS A CITIZEN DEVELOPER?
A 2020 Gartner survey shows that 41% of employees outside of an IT role fit a description called business technologists — those who customise or build applications, automation and technology solutions for work. Citizen development is the practice of enabling a community of like-minded business technologists using shared No-Code and LowCode tools to create automation and apps in a safe and scalable way.
Historically if you required applications or software built, you needed to rely upon Professional Developers. This is all changing, Modern software platforms permit Citizen Developers to build advanced software systems and applications without the reliance on Professional Developers. These new software platforms are delivering a 20-50x improvement over the entire SDLC - Software development lifecycle enabling smaller teams and reducing costs.
CITIZEN DEVELOPMENT IS A KEY ENABLER OF D IGITAL TRANSFORMATION
Business units increasingly control their own application development efforts, in which Citizen Developers are playing a crucial role. Application and software engineering leaders must help define and guide Citizen Development to maximize mutual benefits for business and IT.
The Citizen Developer is often a domain expert and understands the data they want to capture, process, transform and report against. By allowing Citizen Developers to create the apps they need, with advanced software platforms, timescales and costs are dramatically reduced
versus traditional software development approaches with Professional Developers.
Professional Developers normally work within a team of people that exist to create the apps that are required for the end users to utilise. There is usually some formal specification created that requires a detailed description of the process required alongside crosstraining of the Professional Developer to help them to understand the needs of the end user, the domain expert. This is often where projects fail, the clarity around requirements. The miscommunication between the end user, Project Manager, Business Analysts, Database Designers, BI Analysts, Front End & Back End developers, Testers & DevOps teams standing up the final application before production.
Citizen Developers using the latest Super Apps and No-Code Low-Code Platforms significantly reduce timescales and costs when compared to traditional software development using Professional Developers.
However, this isn’t the end of the Professional Developer. Citizen Developers can be selfsufficient whilst supported by Professional Developers and IT teams. Professional Developers can focus on the more complex challenges and processes, further enabling the Citizen Developers to be able to do more faster and together provide a better overall service to the business operations of the organisation.
TAAP provides a No-Code Platform to help Professional and Citizen Developers to work together more effectively, working as Fusion Teams. These are small targeted focused and efficient groups of individuals with complementary skills that together are helping organisations of every size become agile enterprises.

CYBER THREAT FROM CITIZEN AND LOW CODE DEVELOPERS

Cyber and Low-Code developers will have access to your corporate data. Without appropriate Guard Rails and adequate Governance, how will you police the activities of these individuals?
There is an inherent inertia built into the speed at which software is created and developed with traditional Pro Code development resources. It’s slow and requires a higher degree of governance and DevOps management to build, test and deploy applications.
With Citizen Developers and Low Code Developers, you can create applications at the speed of thought and with just an idea, a few hours later you have an app. What if the app developers’ motivation is less than honest? How can you determine and access what is legitimate data flow vs business-sensitive information streaming into the cloud?

PROJECT MANAGEMENT INSTITUTE CITIZEN DEVELOPER PROGRAMME

The PMI is a not-for-profit organisation which has picked up on the challenges of Citizen Development. They recognise the benefits of No-Code and the importance of good governance. Cyber is often considered a security blanket around the systems and processes that have been created, stopping outside attacks. With this next stage in the evolution of the software applications development industry, Cyber needs to be considered across the board to help eliminate insider attacks and/or the loss of corporate data.
CITIZEN & CYBER FUTURE
It’s here to stay and its adoption is accelerating. Just make sure you apply solid cyber principles to how you embrace this technology and ensure that its application is a positive incremental benefit and not a ticking bomb.
TAAP - The Agile Application Platform Find out more at ontaap.com ARE CITIZEN DEVELOPERS THE NEXT BIG CYBER
cybernewsglobal.com 28
Gartner predict in 2023 that there will be four times the number of Citizen Developers than Professional Developers. How will this change the Cyber Threat landscape?
THREAT?


For a demonstration, free trial or initial consultation with one of our cyber security experts, contact us at systal.co.uk/contact © Copyright 2022 Systal Technology Solutions Limited 1,000+ Leading Industry Experts 200,000 Managed assets in 93 countries 35 Global Locations Securing Your Digital and Physical World Systal provides a holistic security solution for our corporate clients, bridging the gap between the digital and physical worlds to manage cyber security risks. Systal is a specialist technology integrator and managed services provider dedicated to global enterprise infrastructure management. We pride ourselves on our ability to deliver dynamic, innovative, tailored solutions to meet any business aspirations or challenges. Why Systal?





cybernewsglobal.com CYBER SECURITY CONSULTANCY FOR INDUSTRIAL AUTOMATION AND CONTROL SYSTEMS IACS Consulting LTD, Balmoral Business Park Building 1, Aberdeen AB12 3JG info@iacsconsulting.com 01224 460212 UNDERSTANDING AND MITIGATING YOUR OPERATIONAL TECHNOLOGY SECURITY RISKS www iacsconsulting com ASSESSMENT | COMPLIANCE | SUSTAINMENT











ALL YOU CAN BUILD Drive digital transformation with power at your fingertips using TAAP’s No-Code Platform Get in contact to find out more! www.ontaap.com +44 345 230 9787 sales@ontaap.com Mobile & enterprise scale applications No-Code application cyber resilience A mature, proven No-Code Platform Deployed across over 56 industries and 110 verticals Reporting & analytics 20-50x improvement across SDLC
Years before I studied law, I had trained as a climbing instructor. I cannot travel to Scotland and sit in the shadows of her mountain ranges to discuss resilience without acknowledging that as long as humans endeavoured to undertake anything worthwhile, it has always been a balancing act between making progress and protecting your people and your assets.

It is not the case that we simply do not undertake these challenges, of course we do. This is how 47 years ago in September 1975 a British team successfully scaled the South West face of Everest.
Chris Bonington’s team succeeded not because they were immune to the dangers. They’d had an unsuccessful attempt three years earlier. They succeeded because the leader and his team had carefully assessed a myriad of factors, including the conditions they were facing, the team he had assembled, what assets and skills those individuals brought to the team, the equipment & supplies they would need to give them a reasonable prospect of success.
INHERENT RISKS From Security to Resilience

Wise words from Cyber Woman of the Year
Rois Ni Thuama Phd Head of Cyber Governance Red Sift

The weather turned inclement, the team’s best ice-climber Tut Braithwaite laid the route for the the five that eventually summited. It was a win for the whole team.
Their ability to endure and withstand testing conditions wasn’t born of ignoring what they might face, adopting a devil-may-care attitude and throwing caution to the wind. Their success rested on being completely honest about what they might face. They knew the risks, they prepared, and then they struck off. Resilience is born in the preparation phase.
INHERENT RISKS
The starting point for any undertaking whether its climbing Ben Nevis, or operating in a digital landscape replete with bad actors poised to hold you to ransom or steal your commercially sensitive data, requires leaders that can fully appreciate the inherent risks associated with it. In order to lead, it requires optimism. But optimism is not blind faith, optimism is what is left after a realistic risk assessment.
Being prepared for the expected conditions, whilst also making plans to address and cope with changing circumstances should those conditions change or deteriorate, are material to withstanding and enduring shocks. This is resilience. We have been assessing risks and calculating our prospects for success since time immemorial. It should give us enormous confidence that none of this is new, we are simply applying what we have learned to a digital threat landscape which is becoming more dangerous for businesses of all sizes.
In order to prepare to meet the conditions, every mountain leader will keep an eye on credible sources to keep up to date with the latest weather report and mountain conditions. Every leader in business should be looking to credible, trusted, independent sources to cut through the noise.
Not only are independent sources like the National Cyber Security Centre (NCSC), National Institute of Standards in Technology (NIST) the best sources of information otherwise unavailable in the private sector, but relying on institutions offers a safe haven.
cybernewsglobal.com 32
In the unlikely event that the guidance or information turns out to be imprecise, relying on credible sources offers a shield, a mechanism for defensibility in the face of litigation.
FROM SECURITY TO RESILIENCE
In recent years the cybersecurity sector has seen a shift in the language, moving away from the concept of security to resilience. There is good reason for this and broadly the sector welcomes this move.
In the past we have all been guilty of oversimplifying our language to land a message to a broader audience. But this drive to simplify means that many non-technical stakeholders expect that a firm that has implemented sound cybersecurity measures will, in fact, be cyber secure. Of course, that is not the case. Because that omits the painful truth: Motivated actors can always find a way to breach even the most robust cyber security measures.
In the aftermath of an event, meaningful conversations are more challenging as nontechnical stakeholders who have suffered
losses struggle to understand how a business that had implemented sound security measures was simultaneously vulnerable to an attack and was not, as they believed, cyber secure.
TRANSPARENCY
Discussing the concept of resilience up front rather than security is a more transparent way to describe what it is that businesses do. Putting resilience front and foremost as the overarching business imperative puts all stakeholders on notice of what it is that the leadership values. In this way, leaders set out their vision for the firm, not one of excessive optimism relying on the notion of security. Instead it is a vision firmly rooted in reality and it acknowledges that conditions can change. It sets out the firm’s position, that it can withstand and endure the shocks because it is has considered them and it is prepared.
VALUE PRESERVATION
Making progress or to put it in corporate terms value creation is one thing, but in today’s world
defending and protecting those gains is a necessary part of any business’ resilience discussion.
If we consider the legal obligation on directors’ ‘to promote the success of the company’ then it is clear that value preservation becomes elevated to a corporate imperative. A company cannot succeed if it cannot endure conditions that it ought reasonably to have prepared for.

CONCLUDING REMARKS
The mountains are unforgiving of those who are ill-prepared and rely on excessive optimism as a strategy, as are businesses. This not a case for pessimism. This is a case for preparation, where resilience is born.

Find out more at redsift.com
 Products on the Red Sift Platform work together to block outbound phishing attacks, analyze the security of inbound emails, and provide domain impersonation defense for company-wide threat protection.
Products on the Red Sift Platform work together to block outbound phishing attacks, analyze the security of inbound emails, and provide domain impersonation defense for company-wide threat protection.
33
Achieve cyber resilience in a hostile digital environment
Geopoli�cal events of 2022 have made the UK’s na�onal security and its cri�cal energy sector, including power and water u�li�es, a major cause for concern. Our energy industry is now a prominent target for poli�cally mo�vated state-sponsored cybercriminals who want to reduce energy supply in Europe and disrupt the market.

The global threat landscape is rapidly changing, with increasingly sophis�cated, financially mo�vated criminal groups regularly adjus�ng their tac�cs to evade defences and hold energy companies to ransom. Ransomware a�acks are now a serious threat for everyone.
Today, no single en�ty can work alone to protect its assets, resources, customers and reputa�on from harm. Governments, the private sector, cyber security companies and technology developers must adopt a coordinated approach to defend the energy industry’s key infrastructure.
Helping defend businesses around the world
At Quorum Cyber, we partner with our customers to focus on outcomes and results, while reducing the total cost of ownership to deliver a clear return on investment. We’re proud to help more than 150 organisa�ons, including in the energy and oil & gas sectors, in Europe, North America, the Middle East, Asia and Australia thrive despite opera�ng in an unpredictable digital landscape.

Being a Microso� Gold Partner and member of the Microso� Intelligent Security Associa�on (MISA) has led us to be one of the fastest growing cyber security companies in the UK. We provide managed, professional and consul�ng services, as well as offering penetra�on tes�ng, phishing simula�on and red teaming exper�se to ul�mately enhance security maturity.
Managed services around the clock
If you need a seamless extension to your IT or security team, then our Microso� Sen�nel Security Opera�ons Centre and Managed Detec�on & Response (SOC & MDR) service is perfect for you. Operated by experts equipped with Microso�’s market-leading security technologies, they monitor your whole environment, detect any poten�al threats and respond rapidly 24/7, 365 days of the year. All our customers can see any incidents and how we’re managing them in real �me through our dedicated customer portal, Clarity.
With our premium service, Managed XDR, we provide comprehensive security across your en�re IT estate, combining the strengths of Microso�’s two families of Defenders – Microso� 365 Defender and Microso� Defender for Cloud – plus Microso� Sen�nel into one single service.
incident
Our CREST Cyber Security Incident Response (CSIR) service is ready to assist you to manage an incident at any �me, day or night. Services include Incident Response Preparedness, Emergency Incident Response and Incident Response Retainer to help you wherever you are on your cyber security journey.
Threat intelligence is a crucial part of our team’s toolkit as we stay on top of new threats around the clock. Our professionals are experienced cybercrime expert witnesses who enable law enforcement agencies to drive successful prosecu�ons.
We also offer an emergency service designed for anyone experiencing a crippling incident or an impending cyber-a�ack. Our Tac�cal Security Opera�ons Centre (TSOC) quickly moves organisa�ons from a vulnerable state to a safe posi�on so they can recover and get back to business as safely as possible.
Come and meet our team today to discuss how we can help you. You can find out more at www.quorumcyber.com or contact us at info@quorumcyber.com
cybernewsglobal.com
Helping you win before, during and after a security
#wefightbullies
Helping you design, build and deliver a robust cyber security strategy
We are a membership organisation for Scotland’s digital technology industry. We underpin a thriving community which brings together the ambition, talent and expertise across our industry to grow Scotland’s digital economy.
Our membership includes technology businesses across a wide range of sectors, in addition to universities, the public sector, financial services, energy industries and specialist providers.

By becoming a member you will:
Raise your profile
Gain exposure to key audiences, highlight your capabilities to our expansive network of members and cluster tech companies in Scotland and beyond. From speaker and sponsorship opportunities, to access to our extensive community via our social platforms and bulletin, we will enable you to be heard in every corner of our industry.
Expand your network
Receive introductions within our network of over 1000 Scottish technology companies. Access valuable ecosystems through our Cyber and Data clusters. Attend our events for free or at a discounted rate, for the opportunity to network with our community.
Strengthen your business
Access new funding calls and procurement opportunities that we highlight to our membership. Receive business support such as HR and legal advice to help you on your journey as you grow.
Be part of the conversation
ScotlandIS will keep you apprised of the latest industry trends, insights and research. Join Specialist Groups such as our Software Engineering Leaders Forum and Marketing Meetups to explore challenges with peers and the potential to work together. Our steering groups such as Policy, Cross-Sector, and Diversity & Inclusion, will help you stay informed and shape the future of Scotland’s tech sector.

35
Maybe the ship or yacht you’re working with has experienced some kind of cyber-attack, or you’ve fallen victim to malware or ransomware, or had your social media accounts hacked. In this hyper-connected world that we all live in, it’s all too easy for us to fall into the cyber criminals’ traps.

We, as people, are the first line of defence against any cyberattack – unfortunately, 95% of all security breaches are caused by human error, mainly by email, and primarily by phishing.
Hackers can compromise data and systems with relative ease, and on a regular basis. The main

reason continues to be a lack of cyber security awareness – people utilise poor practices which expose data, leaving it unprotected and vulnerable to theft and breaches.
Being aware of this and treating emails with a little extra suspicion won’t hurt.
But that’s just the IT… what about the OT…. that’s the technology that makes things actually happen. Industrial Control Systems, for example, SCADA, etc. Chances are if you’re working on a ship, you’re especially likely to come across OT because it’s the tech that makes the ship move, navigate, and countless other things that assist humans.
WHY IS OT IMPORTANT?
Often the OT systems and the IT systems are integrated without any thought of consequences; many devices that shouldn’t have access to the Internet or other such networks, wrongly have this access – this creates a huge problem.
Imagine a scenario where fuel and ballast systems could be hacked, tricking the vessel to thinking it was off balance – the propulsion would stop. This disruption could be used to then commit piracy or to cause environment issues that then become health and safety issues, potentially endangering lives.
Such disruption could easily target the power generators on board or other systems which are critical to life support. This disruption and danger to life can stem from a simple phishing email: if the devices receiving the phishing email are not protected and if the network said devices are linked to, isn’t configured properly to protect the systems – a process called network segmentation.

DO YOU KNOW YOUR OT FROM IT? With cybercrime becoming a growing global issue, can you afford not to be cyber aware, and, what does it even mean to be cyber aware? cybernewsglobal.com 36
THE “INSIDER THREAT”
With the increasing connectivity and vendor requirements to connect remotely to the systems on board – an Internet connection is required to connect to systems remotely. Anything connected to the Internet, thus, presents a risk that it could be attacked. But the risk of attack also comes from within, on the local ship’s local networks.
More and more cyber-attacks and incidents come from within, either maliciously by a disgruntled crew member, for example, or by pure accident. The automation and digitisation of many of these systems create paperless bridge environments. As such, there is an increasing dependence on monitors and screens, and subsequently, an unwitting reliance that these systems are infallible to attack. Well configured systems aside, the strongest defence system against a cyberattack is quite often, the human factor. Cyber awareness is crucial, and awareness that breaching an OT system can have far more devastating effects than a breached IT system is crucial, as well.
AWARENESS IS THE KEY
A high percentage of security breaches are attributed to human error, and consequentially, it’s an unfortunate truth that the crew or workforce are often the weakest link in cyber security. Bearing this in mind, developing a cyber security culture on a vessel or in the workplace is a very effective method for

reducing the likelihood of a successful attack. All crew members should be aware of the dangers and know what to look out for.
When it comes to the operation of a ship or a vessel, it’s vital that all crew members understand the technology that they are working with, either directly or indirectly. Moreover, they and should be aware of the dangers and know what to look out for so that they can make informed decisions – currently, there are developing legislation and regulations which seek to mandate this, but we shouldn’t, and can’t afford to, wait.
Preventative security decisions cannot be underestimated, they are critical in ensuring safe and resilient vessels, operations, and business continuity.
Knowing the environment that you are working and living in is a must. Equally important is knowing the basics about your environment’s systems, and about how those systems can and should be secured.
There is a difference between IT and OT, but these systems might be connected, meaning that the worst can and often, inevitably, does happen. Cyber awareness and knowledge can help mitigate attacks: by separating the IT and OT functions, putting safeguards in place, and keeping systems updated and configured precisely will help.
All of this is just the basics, and the importance of thorough training in this area cannot be underestimated.
Pelion Consulting is a cyber security company that serves primarily the maritime and yachting sector. We pride ourselves on specialising in providing cyber security to superyachts and work closely with international organisations to prevent cyber-crime. By closely following the latest technological developments in the industry we ensure that our knowledge of maritime cyber security is always at the cutting edge.

For more information contact Richard Hodder at Pelion Consulting: rh@pelion-consulting.com

Find out more at www.pelion-consulting.com 37
OPERATIONAL TECHNOLOGY (OT)

CYBER SECURITY STAFF AWARENESS COURSE
Digitisation relies on secure communications to ensure a protected exchange of data between Operational Technology (OT) and Information Technology (IT).

The aim of this course is to provide you with a introduction to Operational Technology (OT) Security and to reduce the likelihood of a cyber attack through reprogramming or training the wetware (us).
The average user struggles to understand the difference between OT and IT and their importance OSP Cyber Academy has worked hard to seek the advice of the very best proven practitioners and partners at Cyberprism to provide some first hand experience of baseline cyber awareness.

I recommend this course to all who want to protect themselves and others, in a practical and realistic way.
Malcolm Warr
OBE, Chairman of CNI Scotland
PURCHASE YOUR COURSE HERE:

SCAN ME
CONTACT US - EMAIL: TRAINING@OSPCYBERACADEMY.COM
CyberPrism
Take control of your Operational Technology

CyberPrism provides Software as a Service, underpinned by industry - leading technical practitioners and professional services, to protect Operational Technology, chiefly within the Energy, Maritime and Government sectors. We are dedicated to producing cost-effective, client-specific solutions to safeguard your OT.


Our Platform reduces the resources required to re-establish safety and security in the face of current threats. Incorporating OT - compatible network visibility, alerting, incident response, and protection of devices and systems; it is low-risk, using tried and tested technology, and compatible with any OEM’s equipment. Human experience and judgement are key to the Platform, which is backed by our proven expertise, borne of decades spent protecting Critical National Infrastructure. We reduce the scale of the task and allow people to do what they do best: take control.

Guard
CyberMonitor
CyberSupport
Guard protects OT from malware ingress and provides ‘smart segregation’ within industrial networks It facilitates secure two-way communication and allows critical industrial and safety processes to continue Guard can also protect legacy, unsupported and un-patchable devices from attack.

CyberMonitor is a Security Orchestration Automated Response (SOAR) software solution. It monitors and manages IT and OT networks, generates alerts and tracks compliance. Built on innovative data comparison software, which allows it to ingest and compare data from any source, it works with any OEM’s equipment.

CyberPrism provides a complete range of cyber security services and solutions Our products and services provide key elements of the NIST cyber security protocol: Identify – Protect – Detect –Respond – Recover.

Phone: +44 020
Cyberprism cyberprism.net
7873 2414 Email: contact@cyberprism.net
DARE TO BECOME
When asked, most people believe they are only using 60% of their potential. Does this sound like you and your team?
At Compass for Life, we believe everyone has the potential to be the best version of themselves.
Our aim is to unlock this potential and transform every team working with us into becoming high performing, resilient and confident individuals.
Using evidence based psychological research, Compass for Life brings together the best aspects of leadership training and performance coaching into a simple, concise, and effective framework.
To find out more about our leadership training courses, you can reach our team on HELLO@COMPASSFORLIFE.CO.UK

WE DARE YOU TO BECOME THE BEST YOU CAN POSSIBLY BE
WHAT DOES IT TAKE TO BE A SUCCESSFUL LEADER IN TODAY’S UNPREDICTABLE AND CHALLENGING TIMES?
ARE ALL YOUR EMPLOYEES FULLY ALIGNED AND ENGAGED WITH YOUR COMPANY STRATEGY
HOW CLEAR IS YOUR COMPANY’S VISION
ARE YOU AND YOUR LEADERSHIP TEAMS PERFORMING AT THE HIGHEST LEVEL
CYBER LIFE
From Classroom to Boardroom,
How to Close the Skills Gap
Rebecca Keen, Managing Director - Keen People Ltd

One of the most critical aspects of any business is their cyber security. Cyber-attacks are increasing at an alarming rate and with catastrophic and expensive consequences. Cyber-crime costs the UK economy £27 billion every year, and globally $600 billion, which is a rise of 0.8 percent. According to Gartner, the demand for cyber security professionals at all levels will exceed by 260% from previous years. As a specialist tech and cyber security recruitment agency, this shortage has become a day-to-day discussion for us at Keen People, and we are consistently evaluating and looking for ways as to how we can address orhow we can close the skillis gap.
From classroom to boardroom: cyber security is a topic discussed at all levels. Executives, and managers, through to technical staff — every employee has and other employees, all have a part to play in keeping our businesses safe. Cyber criminals do not discriminate and are not always the bad guys on the streets —, cyber-attacks can and do sometimes come from within your own business network.
There are many issues that arise from the cyber security skills gap which and presents us with a few challenges and problems to solve. Firstly, the demand for talent has increased as the use of technology has grown and become more complex within businesses. Companies require a much wider range of cyber skills now than they ever did before. Cybersecurity Ventures reports that the number of unfilled cyber jobs worldwide grew to 350% in 2021, from 1 million to 3.5 million vacancies. They also predict that in five years the same number of jobs will still be open.
The talent pool in cyber security lacks diversity. A recent study by ISC2 suggests that only 25% of the global cyber security workforce is femaleare women. EWith ethnic minorityies
representation is also being reported as significantly underrepresented. There is some hope on the horizon though:, this research also suggests that millennials entering the tech space provide much more diversity in teams, which better represents the world around us. For example, 45% of women in cyber now are millennials, compared to 33% of men, proving that outreach and awareness is slowly working towards bridging the diversity gap within cyber.
Retention of cyber security professionals is another issue which has recently seen a huge increase recently. A survey by Trellix found
the recruitment, we repeatedly see all too often organisations with requiring an almost unachievable wish list of skills, certifications, and years of experience required that they would be a struggle to find all in one person. To help close this gap, companies can look toshould prioritise the skills required and be more flexible with their desired years of experience. A condensed wish list will to enable more young people or and graduates a chance to enter the profession thus bringing more people to the cyber skills table. Training and upskilling the within their own organisation can also be a cost-effective way to gain the skills required, however, this does come with its own challenges.
It is widely accepted that the cyber security skills gap exists and will continue to be a consistent issue, with the emergence of new technology and the ever-changing threat landscape which moves so rapidly. Therefore, the demand for cyber skills will always be greater than the talent pool. This imbalance will persist until we start seeing young people or and fresh graduates are , securing roles within companies.
that over one third of cyber professionals want to change careers. The With more demands on the employee’s time and the expectations to keep up with the ever-changing threat landscape demands more of the employee’s time — it is no wonder that people are looking to move sectors or industries for a more balanced and stress-free life.
As a cyber security recruitment agency who’s whose business is built around the supply of tech and cyber security professionals, we know all too well how costly and time consuming the recruitment process of these particular skills and people can be —, especially when you are managing the process in house. Even when outsourcing

There is no quick or easy fix for reducing the cyber security skills shortage, but however, we all must take responsibility towards in bridging that the gap in whatever ways that we can. Whilst we have seen a positive shift in attitudes across the world, and and with more womenfemales and people from all backgrounds choosing the cyber pathway, it still is far from wherewe are still far from where we need to be in order to keep our businesses safe.
We need to see more of these underrepresented individuals given opportunities in the boardroom. Only then we will see a more diverse set of skills to address the cyber security agenda.
41
For more information about Keen People Recruitment visit:
keenpeople.co.uk
One of the most critical aspects of any business is their cyber security.

43
Exciting News of Growth Potential for OSP Cyber Academy
OSP Cyber Academy have been selected as a ‘Grow’ member of the Cyber Runway, a fast-track innovation programme for cyber entrepreneurs and startups.


Cyber Runway, which is the UK’s largest cyber accelerator, is delivered by Plexal with support from Deloitte and the Centre for Secure Information Technologies. It’s funded by the Department for Digital, Culture, Media and Sport (DCMS).
Julia Lopez, Cyber Security Minister at the Department for Digital, Culture, Media & Sport, said: “Our thriving cyber security sector is worth more than £10 billion and attracts some of the world’s best talent. “We fund programmes like Cyber Runway to help startups successfully scale in this thriving sector. If you’re a cyber professional looking for mentoring and masterclasses to help your business grow, then this exciting opportunity is for you.”
Cyber Runway has already supported 107 entrepreneurs with its first cohort. Grow members saw a 20% increase in revenue, an 8% increase in investment and a 22% increase in headcount over the course of the programme.
Saj Huq, Chief Commercial Officer at Plexal, comments: “The economic and geopolitical necessity for a thriving cyber security ecosystem has never been greater. As the UK’s largest cyber accelerator, Cyber Runway provides a uniquely scaled platform for growth at the heart of the UK’s innovation ecosystem, that is designed to support bold, ambitious and diverse founders to realise their potential. We encourage any startup that is serious about their growth to apply and collaborate with us.”

The Cyber Runway provides OSP Cyber Academy with the opportunity to shape the growth strategy for their company. The ethos behind this Cyber Runway programme is that cyber innovation thrives when teams are diverse, and that everyone who joins the sector and wants to grow their business, should have access to the right support.
Irene Coyle, Chief Operating Officer, OSP Cyber Academy said “we are delighted to have been selected as a cohort member for this years DCMS Programme on the Cyber Runway Grow’. This opportunity will allow OSP access to the critical support mechanism that has enabled previous grow companies to be successful within their own sector.”

For more information on the Cyber Runway programme visit: plexel.com/cyber-runway-cohort-two
 Julia Lopez
Cyber Security Minister at the Department for Digital, Culture, Media & Sport
Saj Huq
Chief Commercial Officer at Plexal
Irene Coyle Chief Operating Officer at OSP Cyber Academy
Julia Lopez
Cyber Security Minister at the Department for Digital, Culture, Media & Sport
Saj Huq
Chief Commercial Officer at Plexal
Irene Coyle Chief Operating Officer at OSP Cyber Academy
cybernewsglobal.com 44



MARITIME CYBER BASELINE


IASME Maritime Cyber Baseline scheme is an affordable and practical way for shipping operators and vessel owners to improve their cyber security to reduce the likelihood of a cyber-attack disrupting their day-to-day operations. Maritime Cyber Baseline certification enables a path to compliance with the IMO Maritime Cyber Risk Management guidelines and is open to vessels of all sizes and classifications, including yachts, commercial, passenger ships and merchant vessels.

How the scheme works
1. Complete the verified-assessment, which involves answering a series of easy-to-understand questions, using IASME’s secure online platform.
2. An IASME Assessor will assess your vessel to review systems and processes and verify the answers provided in step 1.
3. Once the assessment is fully completed and verified, your vessel will be officially certified.
If you require any further assistance, you can get advice from an IASME Certification Body - these knowledgeable maritime cyber security experts can help make the required changes to systems and processes to ensure they meet compliance. They can also help you with the certification process itself.
For more information, please contact Craig Wooldridge via craig.wooldridge@iasme.co.uk
About IASME Consortium


IASME work alongside a network of over 280 Certification Bodies across the UK and Crown Dependencies to help certify organisations of all sizes in both cyber security and counter fraud. IASME is committed to helping businesses improve their cyber security, risk management and good governance through an effective and accessible range of certifications, including IASME Cyber Assurance, IoT Cyber Assurance and Counter Fraud Fundamentals. IASME is also the National Cyber Security Centre’s Cyber Essentials Partner, responsible for the delivery of the scheme.
The Maritime Cyber Baseline scheme has been developed by IASME with guidance and maritime cyber expertise from Infosec Partners Limited.
E N T
MA R I T IM E CYB E R R ISK M AN A GE M
The Royal Institution of Naval Architects (RINA) have endorsed and supported the development of the Maritime Cyber Baseline.
Wyche Innovation Centre, Wal wyn Rd, Malver n WR13 6PL Tel: 0330 088 2752
Learning
Students learn in state-of-the-art facilities acquiring skills in areas such as web, database and network security, penetration testing, ethical hacking, digital forensics and human factors in security. In addition to their degree, graduates also acquire knowledge and skills towards industryapproved external professional certifications in networking and security (Cisco and ECCouncil).
Placement
During their studies students have the opportunity to complete a one-year industry placement. This strong link with industry has contributed to RGU being named the top modern university in Scotland for graduate prospects (Guardian University Guide 2022).

Accreditation

Our security and networking courses are accredited by the British Computer Society for CITP. In addition, our MSc Cybersecurity course is NCSC (GCHQ) certified.

Industry Collaboration

The school works very closely with industry to shape our courses and engage in collaborative research.
For more information about possible avenues of collaboration or placement opportunities contact: Dr Christopher McDermott.
47
Entry Requirements +44 (0) 1224 262700 soc-enquiries@rgu.ac.uk The School of Computing aims to shape future industry -sought skills in Computer Science, Cybersecurity, Computer Networks, Digital Media, Data Science and Intelligent Information Systems. Our courses provide innovative, practical and research-led teaching, designed to meet current and future industry needs.
Course Highlights
• Degree Link: Study at college and then articulate into third year at RGU • Graduate Apprenticeships: Earn a degree while working in industry • Courses accredited by British Computer Society (BCS) • NCSC accredited Cybersecurity course • Accredited Cisco Academy For
info
-security Cybersecurity contact:
School of Computing Full/Part Time On Campus/Hybrid Accredited courses Research –led learning Practical Learning Excellent Facilities Strong Industry Links Placement Widening access to Higher Education Cybersecurity BSc|PgCert|PgDip|MSc|PhD
more
please visit www.rgu.ac.uk/cyber
Dr Christopher McDermott (c.d.mcdermott@rgu.ac.uk)
ALL DECK!
We've been navigating the cyber skills gap now for at least a decade and recent estimates still put the number of unfilled positions across the globe as high as 3 million.
Capture the Talent say evidence is pointing towards practical, hands-on training and assessment methods to tap into new pools of talent Let's look at why that is
WHY PRACTICAL TRAINING?
Classroom-style training is fine, and if you have a tutor who can add a bit of pizzazz, then you might stay interested for longer than 30 minutes But as humans, we ' re not wired for sitting still and listening for long periods of time
Incorporating practical, hands-on training as part of a course is imperative if we expect students to retain information, especially in an industry where having the theory rarely prepares you for the reality of the role
HOW CAN CTF EVENTS HELP?


Capture the Flag events are a great way of testing the practical and professional skills of many people in a single sitting
We support businesses in identifying internal training needs and finding the right talent for unfilled positions using CTFs covering various disciplines, including soft skills.
Learn more
CAPTURETHETALENT.CO.UK


DON'T CERTIFICATIONS DO THIS?!
We're glad you asked! Certifications are great some of them anyway However, a lot of certs focus too much on the theory and not enough on the actual doing.
Security isn't a multiple choice occupation, so why are we testing people with multiple choice exams? Doesn't make sense to us
That's why all of our training incorporates practical exercises to ensure students can test out the theory
IN PERSON OR VIRTUAL TRAINING?
VIRTUAL TRAINING

Virtual training is great if you ' re looking for something that's lower cost, self-paced and convenient It's fab for individual students and those on a budget
IN-PERSON TRAINING
In-person training is proven to help you retain more information. It's best for groups with a common goal, those wanting a deep dive into a particular subject, and businesses who need their team to be at the top of their game
CAPTURE THE FLAG
CTFs are great for assessing training needs within a business and identifying team strengths to inform hiring strategies
We also run CTFs to support mass recruitment for businesses - they are all tailor made, ensuring they are relevant to your tech stack, technologies and team

CTF / CYBER E SKILLS COACH
Created by local authorities as a shared resource for the sector, we have a successful track record of delivering transformation and service improvement programs in the UK. By doing so, we have delivered more than £1bn of savings for our clients.
iese.org.uk

Onca Technologies Ltd provides IT advice and support, as well as technological and business solutions for companies of all sizes. Specialising in enterprise computing, data security and analysis, system analysis and design and business process optimisation, we provide optimal bespoke solutions according to our clients’ needs & requirements.


oncatech.com

An


The Agile Application Platform

ontaap.com
Pelion Consulting is a cyber security company that serves primarily the maritime and yachting sector. We pride ourselves on specialising in providing cyber security to superyachts and work closely with international organisations to prevent cyber-crime.


www.pelion-consulting.com
Risk-based cyber security. Right first time.
Design a cyber security programme that fits your risk profile.
crmg-consult.com

Access
Enjoy
Join the CNG Community today!
your own company directory page on the CNG
Build
website.
social
Get your company news shared via the website, app, newsletter and
media platforms.
regular online networking events.
free job advertising on the CNG jobs board.
application platform to build and run software for – Citizen Developers and No-Code App Builders – Pro Code Developers – Small, Medium and Agile Enterprises.
49
SCAN THE QR CODE!
cyberscotlandweek.com/get-involved For more information visit our website: @CyberScotlandWk @cyber-scotland-week @CyberScotlandWeek 27th February - 5th March 2023 Get involved in CyberScotland Week 2023 by hosting an event and sharing your cyber expertise! CyberScotland Week, now in its fifth year, draws together in-person and online events across Scotland designed to improve organisations' and individuals' cyber awareness and resilience.



























































your cyber
FIT FOR PURPOSE? Sooner or later, you will let malware in. They only need to get it right ONCE.
for Local Public Services From education & training, to detection, protection & response, we are the one-stop-shop for your cyber essentials. www.iese.org.uk/cyber-centre-of-excellence | enquiries@iese.org.uk An entirely new layer of cyber protection. Created by the sector, for the sector. Military grade defence, at high street prices. A unique combination of skills and solutions. Expert services that you can trust. Protecting your local community.
Are
defences
Cyber Centre of Excellence



















































 Glenn Mangham
Jake Davis aka Topiary
Seth aka Narko
Renukanth S. aka JiLsi
Glenn Mangham
Jake Davis aka Topiary
Seth aka Narko
Renukanth S. aka JiLsi











































































 Products on the Red Sift Platform work together to block outbound phishing attacks, analyze the security of inbound emails, and provide domain impersonation defense for company-wide threat protection.
Products on the Red Sift Platform work together to block outbound phishing attacks, analyze the security of inbound emails, and provide domain impersonation defense for company-wide threat protection.


























 Julia Lopez
Cyber Security Minister at the Department for Digital, Culture, Media & Sport
Saj Huq
Chief Commercial Officer at Plexal
Irene Coyle Chief Operating Officer at OSP Cyber Academy
Julia Lopez
Cyber Security Minister at the Department for Digital, Culture, Media & Sport
Saj Huq
Chief Commercial Officer at Plexal
Irene Coyle Chief Operating Officer at OSP Cyber Academy
























































