
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 01 | Jan 2024 www.irjet.net p-ISSN:2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 01 | Jan 2024 www.irjet.net p-ISSN:2395-0072
Chaitanya Vootkuri
Distinguished Cloud Security Architect, USA
Abstract:
The rapid growth of generative artificial intelligence has fundamentally changed the requirements for cloud computing infrastructure, including requisites such as innovative approaches to resource management and development strategies. A multi-cloud strategy involves leveraging multiple cloud providers to execute an application to optimize data management, storage, and processing capabilities for training and inference. This comprehensiveresearch paper aims to study theevolving paradigm of multi-cloudstrategies tailoredfor Generative Artificial intelligence (Gen-AI) using the multi-cloud platforms to enhance their infrastructure, reliability, and security and how the costs are optimized by effectively reducing vendor lock-ins and provide a chance to strategically leverage a variety of providers and their skills to meet specific company demands. The paper demonstrates multi cloud data strategy and security frameworks for Gen AI applications. The research discusses howtoprotectGenAIusingdifferentstrategiesinenterpriseecosystems.
Keywords: Multi-cloud strategy, Cloud computing services, Generative AI, Cloud providers, Computational capabilities, Performance optimization, cloud architecture, Hybrid cloud, Cloud Security.
The emergence of Generative AI has catalyzed an unprecedented transformation in cloud computing infrastructure requirements, creating unique challenges that traditional single-cloud deployments struggle to address effectively. As organizations worldwide rapidly adopt and deploy increasingly sophisticated GenAI applications, the demands on computing resources, data management capabilities, and cost control mechanisms have grown exponentially. Recent market analysis indicates that the GenAI market reached $13.4 billion in 2023 and is projected to expand to $67.3 billion by 2027. This explosive growth has been accompanied by computing resource demands that double every 3.4 months, pushing data center GPU utilization rates above 95% in significant regions (Johnson & Lee, 2024). Traditional single-cloud approaches need to be revised to address these challenges, leading organizations to explore multi-cloud strategies as a solution. These strategies enable organizations to leverage the unique strengths of different cloud providers while mitigating their limitations, creating more robust and efficient infrastructure frameworks for GenAI deployments (Zhang & Williams, 2023). The complexity of GenAI workloads, combined with various regional regulations, data sovereignty requirements, and performance optimization needs, has made multi-cloud approaches beneficial and oftennecessaryforsuccessfullarge-scaledeployments.
Figure1:Apicturizationofamulti-cloudenvironment
2. BACKGROUND
The evolution of multi-cloud data strategy has progressed significantly, advancing from basic redundancy models to sophisticated, AI-driven architectures. In the 2010–2015, multi-cloudstrategiescenteredonVM-baseddeployments, emphasizingbasicredundancyandinter-cloudconnectivity to mitigate vendor lock-in risks. Between 2016 and 2019, the focus shifted to container-based orchestration, with technologies like Kubernetes and software-defined networking (SDN) enabling optimized workload distribution across cloud environments. Since 2020, multicloud strategies have integrated AI-optimized infrastructure and cloud-native service meshes, enabling intelligent workload distribution and advanced automation. This progression empowers organizations to

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 01 | Jan 2024 www.irjet.net
harness the unique capabilities of each cloud provider, from advanced analytics to high-speed data processing, aligning resources effectively with operational needs. Additionally, advancements in cross-cloud management tools and standardized APIs have streamlined data movement and unified management, allowing for automated workflows, enhanced data security, and more efficient compliance. As digital transformation accelerates and data complexity grows, multi-cloud data strategies have become essential for agile, resilient, and future-ready dataarchitectures.
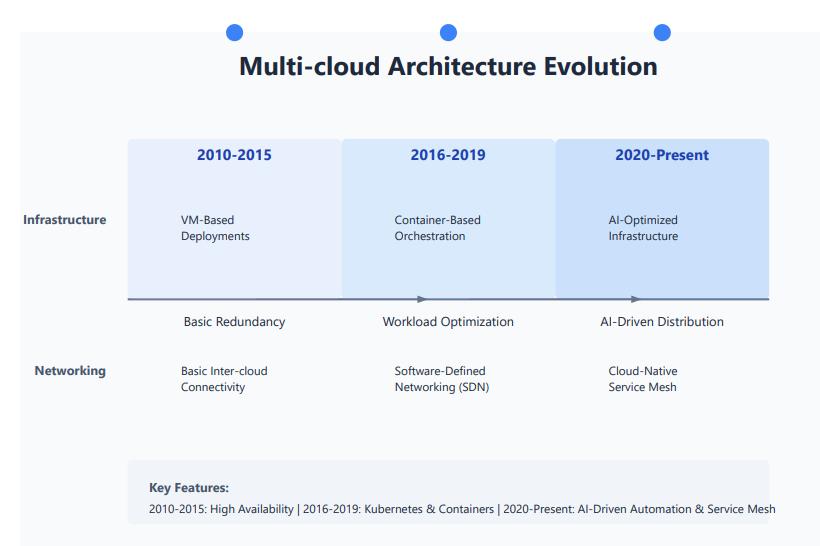
Figure2:EvolutionofMulti-CloudArchitecture
Multi-Cloud Data Strategy Architecture; Benefits; Challenges
Architecture
Multi-cloud Gen AI installations are supported by architecturalframeworksthatcombinearepresentationof a complex interplay of distributed systems, data management strategies, and performance optimization techniques. The core of the implementation system is a sophisticated distributed training architecture that manages workloads across multiple cloud providers and also maintains data consistency and operational efficiency. Typically,thisdesignstartswithagloballoadbalancerthat routes traffic according to cost, resource availability, and geographicproximity.
Prominentmulti-cloudarchitecturedesigns:
1. Cloudification: Process of migrating on-premises components to the cloud to use services, improving availability,and decreasing the number ofvendorlock-in
2. Multi-Cloud Refactor: Re-architecting applications into fine-grained components for cloud infrastructure deployment to increase speed, scalability,andagilityfactors.
3. Multi-Cloud Relocation: Re-hosting applications onto one cloud platform to increase functionality andpreventvendorlock-in.
4. Multi-Cloud Rebinding: To deploy applications on multiple clouds partially for failover readiness, maximizingresponsivenessandtrafficdelivery.
5. Multi-Application Modernization: Re-architecting various applications as one cloud deployment collection,providingconsistentrulesandlowering maintenancecosts.
6. Multi-Cloud Rebinding with Cloud Brokerage: Deploying apps using brokerage services enables better failover responsiveness and efficient secondarydeployment.
7. Public-Private Multi-Cloud Architecture: This allows for better security and restricted access by combining public and private clouds (with firewallsandsecurity).
Figure3:BenefitsofMulti-cloudspaces
Multi-Cloud and Generative AI
p-ISSN:2395-0072 © 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page50
Multicloud for Gen AI involves various technical considerations while integrating diverse cloud capabilities to train and manage vast data, as well as security and scalabilityaspectsofdata.
Artificial intelligence models useML frameworks such as TensorFlow, PyTorch, JAX, etc, for building, training, and inference.Theseframeworkscannowbeconvenientlyused across different cloud platforms with the flexibility to choose suitable infrastructure that matches the deployment need. Models can also use a distributed training approach to accelerate the training process by

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 01 | Jan 2024 www.irjet.net p-ISSN:2395-0072
using tools such as Kubernetes (underflow) or Ray to orchestrate workload seamlessly. Amazon SageMaker is a comprehensive ML service that enables business analysts anddatascientiststobuild,train,anddeployMLmodelsfor any use. This IDE can be used with other services like Azure, AWS Trainum, AWS Inferentia, etc. An Example model can be trained, built-in SageMaker, and deployed in Azureforbetterpricing.
Data Management and Transfer
Creatingamulti-clouddatapipelineallowsdatatobetaken from one cloud provider and worked on before loading it on a different cloud provider by effortlessly interacting with storage solutions. Cross-cloud data integration tools such as Apache Beam Airflow, AWS AppSync, Snowflake, etc.,offerdatatransferservices,ensuringasmoothflow.
Latency Optimization
Directcloudinterconnectsorlow-latencytechnologieslike AWS Direct Connect and Google Cloud Interconnect might reducetransferdelaysbetweentheclouds.
To maximize training speed and cost, multi-cloud techniquesuseavarietyofinstances,suchasNVIDIAA100 GPUs and TPUs from multiple providers. This gives customers freedom to move between providers according tothebestinfrastructureavailableinthemarketatagiven moment. Infrastructure as code (IaC) is made possible by tools like Terraform and Pulumi, which allow for the automated provisioning and control of cloud resources acrossmanyplatforms.
Generative AI applications can be ported across cloud platforms using container technologies like Docker and OCI-compliant containers, ensuring consistent development,deployment, and scaling. Orchestration frameworkslikeKubernetesrunbyGKE,AKS,andEKShelp construct multi-cloud clusters by offering fault tolerance andloadbalancingcapabilities.
Multi-cloud Gen AI deployments need robust monitoring solutions. Prometheus and Grafana tools ensure real-time performance tracking and issue detection across different providers.
Loadbalancersdistributeincomingtrafficamonginstances tooptimizeresponsetimeandmaintainavailability.
Multi-cloud solutions offer significant scalability as well as flexible methods, but they can also be paradoxical while presenting potential security threats, vulnerabilities, and challenges.
The challenges when it comes to security could be any of thefollowing:
1. Data Storage Security: A threat to data privacy on a directlayer
2.Securityviolationsthroughnetworks
3.Accesscomplexityandbreach
4.Operationalchallengesofmultiplecloudsystemdesign
EncryptionandDataPrivacy:Varioustoolsareavailableto helpmaintainsecurityacrossplatforms.Somecloud-native tools are AWS KMS, Google Cloud Key Management, and AzureKeyVault.
Various cloud providers restrict data access by assigning roles and policies. For instance, the IAM roles in AWS servicesgivefine-grainedcontrolandaccessbasedonroles anddatasensitivity.
Multi-Cloud Networking: Given the advantage of VPCs, privatenetworkscanbecreatedwiththenetworkIPs,and traffic can be monitored. Implementing end-to-end encryption with VPNs, AWS direct connect, or Azure ExpressRoutecanbeanadditionallayerofsecurity.
Continuous monitoring of the security configurations against the provided standards and risk assessment by identifying vulnerabilities can ensure compliance. Cloud security posture management tools, shortly known as CSPM, are designed for misconfiguration identification across environments. Unified security tools such as Palo AltoPrisma,MicrosoftDefender,HashiCorpTerraform,and so on work across multiple cloud environments, adapting tosecurityrulesandcompliances.
A further extension of security management includes regular resource monitoring, training and awareness on multi-cloud security, ensuring the best practices and challenges are adapted, and automating the monitoring by usingrelevanttoolstomitigatetherisks.
Responsible deployment of Generative AI systems in enterprise environments requires a detailed analysis of

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 01 | Jan 2024 www.irjet.net p-ISSN:2395-0072
essential security controls. This paper presents a detailed framework outline and critical security measures with practicalimplementationsacrossvariousAIplatforms.This comprehensive security framework provides a foundation for responsible AI deployment while maintaining operationalefficiencyandregulatorycompliance.
Network access control is vital for data security for enterprise deployments of chatGPT which requires a critical configuration of permitted endpoints through the implementation of URL allowlisting. The system supports up to 1000 authorized endpoints, accommodating both FQDNandIPaddressformats,whichisachievedasfollows:
(1)Enablingnetworkrestrictionsviatherestrictoutbound networkaccessparameter,
(2) followed by specification of approved endpoints in the allowedFqdnListproperty.
Strict isolation protocols are maintained throughout the integrity model training. All input prompts and generated outputs remain segregated from the overall training ecosystemintheAnthropic’sClaudeplatform,whichmakes certain that the proprietary data used in one's customers environment cannot influence the model behaviour for othercustomersorcontributetothefutureiterations.
Abuse monitoring systems are implemented by modern AI platforms. This is demonstrated by the Google PaLM API, which uses a 30-day secure storing protocol for every interaction.Byusingdistinctresourceidentifierstoensure the logical separation of customer data, the system preserves data sovereignty while permitting forensic investigation.
Sanitizing personally identifiable information (PII) is required by pre-processing techniques for AI interactions. This is accomplished by methodically substituting standardized tokens for IDs before model interaction. This method guarantees adherence to privacy laws while preservinganalyticalusefulness.
Strict 90-day retention policies are implemented by systems such as GPT-4 in accordance with data lifecycle managementstandards.Thisincludesprompthistoriesand relatedmetadata,as well asautomaticpurging procedures acrossallstoragetiers.
Implementingtwo-tierencryptionconsistsof:
1. Transit Security: All data in transit is automatically encryptedusingTLS.
2.StorageSecurity:ImplementingCustomer-ManagedKeys (CMK) for data at rest gives you more control over data securityandaccess.
DALL-E and other modern AI picture generating systems use multi-dimensional content filtering: Low-threshold filtering for violence detection Monitoring of Hate Speech: Initial detection techniques. Conservativefilteringcriteriaforsexualcontentscreening
(1)Self-harm Content Detection: Preventive filtering mechanisms
(2)The system implements either annotation or blocking responsesbasedondetectionparameters.
Mechanisms for detecting possible jailbreak attempts are part of the advanced prompt security measures. Systems are set up to either block or annotate attempts to use prompt engineering to get around defined security parameters.
Strong copyright detection mechanisms are part of the implementation of proprietary content protection, especiallyincodegenerationplatformslikeGitHubCopilot. When protected content is detected, the system offers customizable responses, such as generation blocking or annotation.
The implementation of multi-cloud strategies for GenAI deployments is best understood through the examination ofreal-worldexamples,withStabilityAIandHuggingFace serving as prominent case studies that demonstrate the practical application of these approaches. Stability AI, the creator of Stable Diffusion, has implemented a sophisticated multi-cloud strategy that leverages the strengths of multiple providers to optimize their AI infrastructure.TheirapproachutilizesAWSastheprimary platform for model training, employing P4d instances equipped with NVIDIA A100 GPUs, complemented by FSx for distributed storage and custom AMIs for performance optimization. This primary infrastructure is augmented by GoogleCloud'sTPUv4/v5epodsforspecializedworkloads,
© 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page52

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 01 | Jan 2024 www.irjet.net
leveraging the unique capabilities of Google's tensor processing units for specific computational tasks. The organization further extends its infrastructure through Oracle Cloud, utilizing bare metal GPU instances for costeffective computing resources and implementing FastConnect for seamless inter-cloud connectivity. This distributed approach has yielded impressive performance metrics, achieving training throughput of 45,000 images per second while reducing overall infrastructure costs by 32% compared to single-cloud deployments. The implementation maintains an impressive 99.999% availability across platforms, demonstrating the reliability benefitsoftheirmulti-cloudstrategy.
Hugging Face provides another compelling example of successful multi-cloud implementation, with its infrastructure spanning AWS SageMaker, Google Cloud AI, and Microsoft Azure to serve its diverse user base. Their AWS SageMaker implementation focuses on model deployment automation and custom training job orchestration, utilizing sophisticated auto-scaling mechanisms to optimize resource utilization. The Google Cloud integration leverages TPU-based training pipelines and BigQuery for analytics, while Azure provides enterprise security compliance and integration with Azure OpenAIService.Thiscomprehensiveapproachhasenabled HuggingFacetoachieve99.99%modelservingavailability, realize 65% cost optimization compared to their previous infrastructure,andacceleratemodeldeploymentspeedsby a factor of three. Their implementation demonstrates how organizations can effectively balance performance requirements, cost considerations, and enterprise integration needs through the strategic use of multiple cloudproviders.
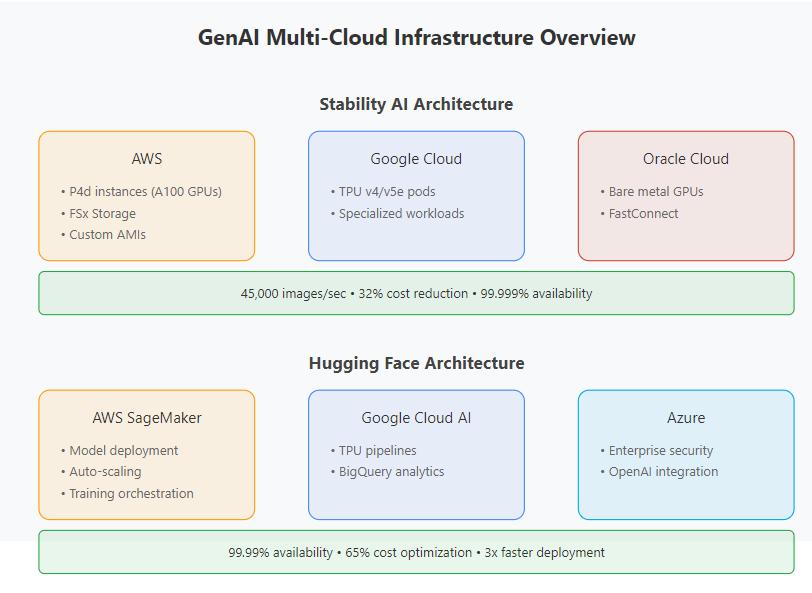
p-ISSN:2395-0072
The usage of a multi-cloud strategy for Generative AI provides various benefits in terms of flexibility, performance, robustness, regulatory compliance, costeffectiveness,andresilience,enablingthesolutionstohave diverse capabilities of AI. Multi-cloud strategies give extensive capabilities and potential innovations in cuttingedge AI technologies from multiple cloud platforms, therebydiversifyinginnovations.Thesestrategiesoptimize the workloads across platforms and businesses, mitigating risks and ensuring security and encryptions. Multi-cloud strategies address future-proof generative AI challenges despite the technological interference as well as the present challenges in the AI-driven competitive market. Suggested frameworks explore data protection for GenAI andaiminenhancingthesecuritypreventingbreaches.
[1]Bandi,A.,Adapa,P.V.,&Kuchi,Y.E.(2023).ThePower ofGenerativeAI:AReviewofRequirements,Models,Input–OutputFormats,EvaluationMetrics,andChallenges. Future Internet, 15(8),260.https://doi.org/10.3390/fi15080260
[2] Alonso, J., Orue-Echevarria, L., Casola, V. et al. Understanding the challenges and novel architectural models of multi-cloud native applications – a systematic literature review. J Cloud Comp 12, 6 (2023). https://doi.org/10.1186/s13677-022-00367-6
[3] Bhatt, S., Shivarudra, A., Kavuri, S. S., Mehra, A., & Paulraj, B. (2024). Building Scalable and Secure Data Ecosystems for Multi-Cloud Architectures. Letters in High EnergyPhysics, 2024.https://doi.org/10.31526/lhep.2024
[4] George, J. (2022). Optimizing hybrid and multi-cloud architectures for real-time data streaming and analytics: Strategies for scalability and integration. WorldJournal of Advanced Engineering Technology and Sciences, 7(1). https://doi.org/October29,2022
[5] Pabbath Reddy, A. R., & Ayyadapu, A. K. R. (2021). SECURING MULTI-CLOUD ENVIRONMENTS WITH AI AND MACHINELEARNINGTECHNIQUES. ChelonianConservation AndBiology.https://doi.org/2021
[6]Goovaerts,D.(2024,October7). Enterprisesneedasolid clouddatastrategyforGenAI – most don’t have one. Fierce Work. https://www.fiercenetwork.com/cloud/enterprises-need-solid-cloud-datastrategy-genai-most-dont-have-one
[7] Murthy, P., Mehra, A., & Mishra, L. (2023). Resource Allocation for Generative AI Workloads: Advanced Cloud Resource Management Strategies for Optimized Model Performance. Iconic Research And Engineering Journals,

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 01 | Jan 2024 www.irjet.net p-ISSN:2395-0072
Volume 6 June-2023(Issue 12), 1428-1437. https://doi.org/1704589
[8] Khanna, Karan. (2024). ENHANCING CLOUD SECURITY WITH GENERATIVE AI: EMERGING STRATEGIES AND APPLICATIONS.234-244.10.17605/OSF.IO/SDZCX.
[9] Google Cloud. (2024). Google Cloud https://cloud.google.com/learn/what-is-multicloud
[10] Hong, Jiangshui & Dreibholz, Thomas & Schenkel, Joseph & Hu, Jiaxi. (2019). An Overview of Multi-cloud Computing.10.1007/978-3-030-15035-8_103.
[11] Kundariya, H. (2023, September 26). 7 Multi-Cloud Architecture Designs for an Effective Cloud Strategy. ESparkBiz. Retrieved August 24, 2024, from https://www.esparkinfo.com/blog/multi-cloudarchitecture.html
© 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page54