
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 10 | Oct 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 10 | Oct 2024 www.irjet.net p-ISSN: 2395-0072
Anurag Singh1 , Prachi Chauhan2
1M.Tech. (CSE) Scholar, B. N. College of Engineering & Technology Lucknow, Uttar Pradesh, India 2Assistant Professor, B. N. College of Engineering & Technology Lucknow, Uttar Pradesh, India
Abstract - Cloudcomputinghasbecomeacriticalpartof modern IT infrastructure, providing scalable and costeffectivesolutionstobusinessesandindividuals.However, with the widespread adoption of cloud services, security concerns have also grown, particularly in multi-cloud environments. This paper aims to analyze the performance of cloud computing in relation to security acrossdifferentcloudenvironments.Wecomparesecurity mechanisms, performance impacts, and vulnerabilities in public, private, hybrid, and community cloud environments. The paper also discusses mitigation strategies, best practices, and future trends in securing cloudenvironments.
Keywords: Cloud Computing, Security, Public Cloud, Private Cloud, Hybrid Cloud, Community Cloud, Virtualization,PerformanceAnalysis,DataBreaches.
Cloudcomputingisaparadigmthatallowsuserstoaccess sharedcomputingresourceson-demandovertheinternet. Ithasrevolutionizedhow businesses handle data storage, processing,and distribution.However,theconvenience of cloud computing comes with security challenges, especially when sensitive data is hosted on third-party platforms.Asmoreorganizationsmigratetheiroperations to the cloud, the importance of evaluating security performance in different cloud environments becomes increasinglycritical.
Theprimaryobjectiveofthisresearchisto:
Analyze the performance impact of various securitymechanismsincloudenvironments.
Evaluate how different cloud environments (public, private, hybrid, and community) handle securitythreats.
Identifycommonvulnerabilitiesandproposebest practicestosecurecloudenvironments.
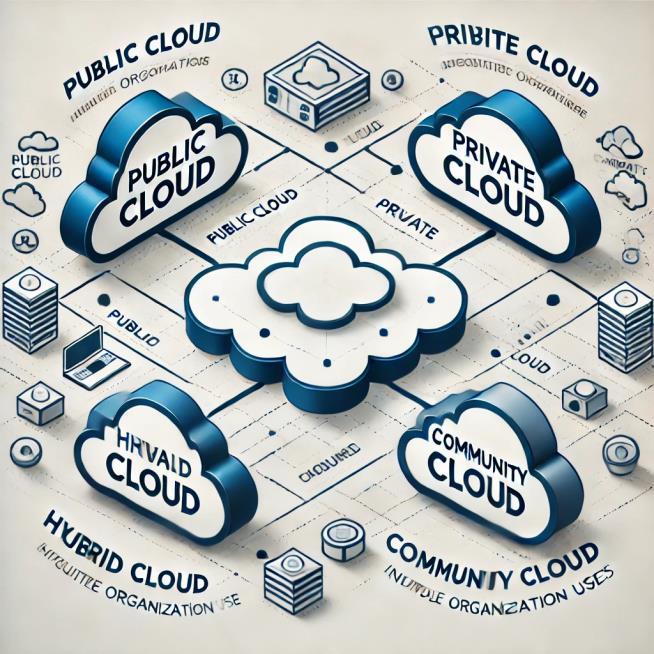
Cloud computing is generally categorized into four environments: public, private, hybrid, and community clouds. The security mechanisms employed in each environment differ based on the level of control the user hasovertheinfrastructure.
Public Cloud:Offeredbythird-partyprovidersto the general public, public clouds (e.g., AWS, Microsoft Azure) offer scalability but present more significant security concerns due to multitenancy.
Private Cloud: Operated solely by an organization, private clouds provide greater control over security but are often more expensive.
Hybrid Cloud: A combination of public and private clouds, allowing sensitive data to be stored privately while leveraging public cloud resources.
Community Cloud: A shared cloud environment for organizations with similar security and complianceneeds.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 10 | Oct 2024 www.irjet.net p-ISSN: 2395-0072
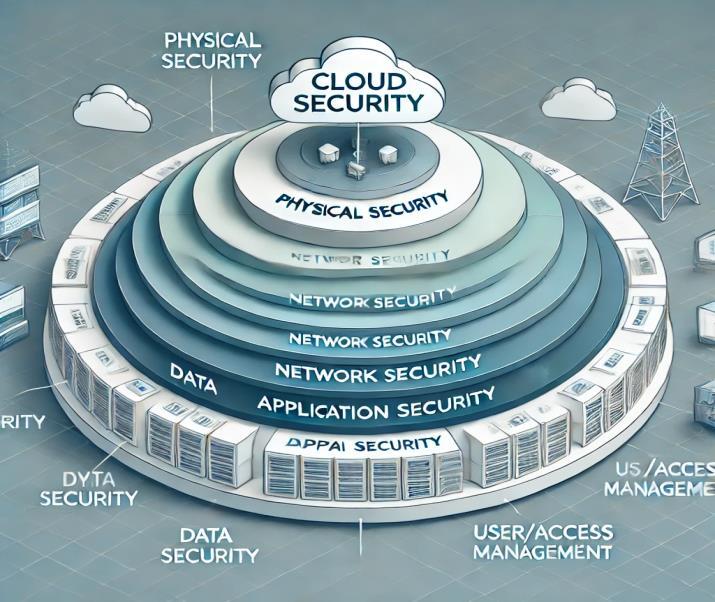
Cloud security involves protecting data, applications, and infrastructure.Keycomponentsinclude:
Data Encryption:Ensuringdataconfidentiality.
Access Control: Managing who can access cloud resources.
Virtualization Security: Protecting the virtual machines and hypervisors that underpin cloud infrastructure.
Several studies have explored the security challenges and performance trade-offs in cloud computing, highlighting thatstrictersecurityprotocolsoftenresultinperformance degradation. However, these trade-offs vary across differentcloudenvironments.
3.1 Data Breaches and Loss
One of the most significant risks associated with cloud computingisdatabreaches.Inpubliccloudenvironments, where resources are shared, there is a higher risk of data leakage.
3.2 DDoS Attacks
Distributed Denial of Service (DDoS) attacks can overwhelm cloud services, particularly in public and hybrid cloud models. The scalability of cloud resources can mitigate some of these attacks, but the security mechanismsmustberobusttowithstandsuchthreats.
3.3 Insider Threats
In private and community clouds, insider threats pose a more severe challenge as trusted employees or administratorscouldmisuseaccessprivileges.
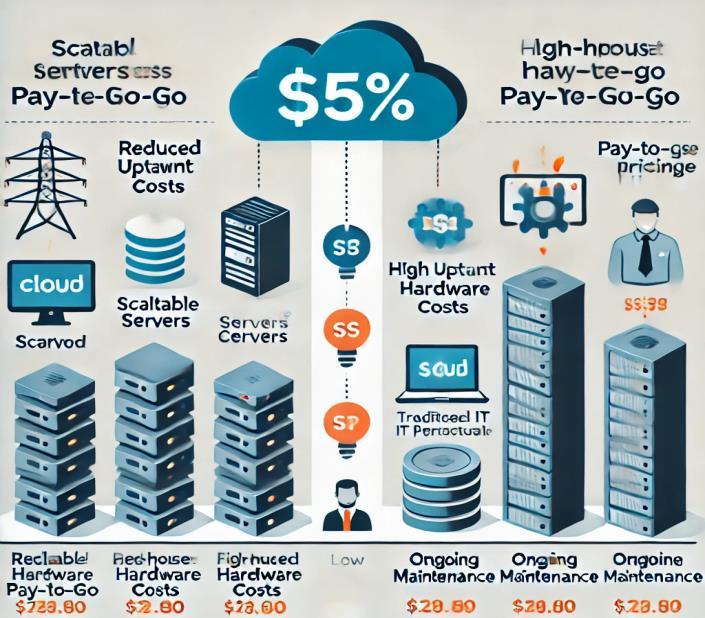
Figure 2: CostComparisonbetweenCloudandTraditional IT
4. Performance Analysis of Security Mechanisms
In this section, we perform a comparative analysis of different security mechanisms deployed in cloud environmentsandtheirimpactonperformance.
4.1 Encryption Overheads
Encryptionisafundamentalsecuritymechanism,ensuring that data remains confidential in transit and at rest. However, encryption can introduce significant performance overheads in terms of CPU usage and data transferspeed.
Table 1:EncryptionOverheadsAcrossDifferentCloud Environments
4.2 Access Control Mechanisms
Access control mechanisms, such as Multi-Factor Authentication (MFA) and Role-Based Access Control (RBAC), can impact system responsiveness. For instance, implementing MFA in a public cloud environment increases login time, while RBAC adds complexity in managingpermissionsbutenhancessecurity.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 10 | Oct 2024 www.irjet.net p-ISSN: 2395-0072
Table 2:AccessControlPerformanceinCloud Environments
IDS tools are essential for monitoring and identifying unauthorized access attempts. However, the effectiveness and resource consumption of IDS tools vary across cloud environments.
Table 3:IDSPerformanceComparisonAcrossCloud Environments
seamless security integration across platforms. Implementing encryption across the private segment and limiting access to public resources reduces exposure to attacks.
Community Cloud
In community cloud environments, organizations share commonsecurityrequirements.Whilethesecloudsoffera balance between cost and control, security mechanisms must cater to multiple stakeholders, potentially complicatingimplementation.
5.1 Public Cloud
Public clouds typically provide a variety of built-in security tools but are also vulnerable to shared resources andmulti-tenancyrisks.EncryptionandIDSarecrucialfor mitigating potential breaches, though performance can sufferwhenthesemechanismsareoverlyrestrictive.
5.2 Private Cloud
Private clouds offer better control over security configurations but require substantial investment in infrastructureandsecuritymanagement.Theperformance impact of stringent security measures like encryption is more tolerable since private clouds often have dedicated resources.
5.3 Hybrid Cloud
Hybrid clouds benefit from the flexibility of both public and private clouds but face the challenge of ensuring
Mitigating Security Performance Challenges
To maintain a balance between performance and security in cloud environments, several best practices can be adopted:
Optimized Encryption: Using optimized encryption algorithms (e.g., AES-128 instead of AES-256) can reduce performance overhead withoutsacrificingsecurity.
Automated Access Control: Implementing automated RBAC systems can reduce the administrative burden and improve response times.
Lightweight IDS Solutions: For environments with limited resources, using lightweight or hybrid IDS systems can help minimize performancedegradation.
7. Future Trends in Cloud Security
Emergingtrendsincloudsecurity,suchasAI-basedthreat detection and Quantum Encryption, promise to enhance securitywithoutnegativelyimpactingperformance.AIcan

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 10 | Oct 2024 www.irjet.net p-ISSN: 2395-0072
help automate intrusion detection, while quantum encryption can offer stronger data protection with reducedcomputationaloverhead.
7.1 AI and Machine Learning in Cloud Security
Machinelearningalgorithmscananalyzelargedatasetsto predict and detect security threats in real-time, reducing relianceontraditional,resource-heavyIDSsolutions.
7.2 Quantum Computing for Encryption
As quantum computing advances, traditional encryption algorithms will become obsolete. Cloud providers are already exploring quantum encryption to future-proof theirsecuritymodels.
8. Conclusions
In conclusion, cloud computing environments face unique challenges when balancing security and performance. Publicclouds,whilescalableandaccessible,tendtosuffer the most from security overheads, while private clouds offer better control but at a higher cost. Hybrid and community clouds provide compromises between these extremes but require careful security management. By adopting optimized security measures, organizations can mitigate performance impacts and secure their cloud environmentseffectively.
9. References
[1] Mell, P., & Grance, T. (2011). TheNISTDefinition of Cloud Computing. National Institute of Standards and Technology. Special Publication 800-145. https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nis tspecialpublication800-145.pdf
[2] Gonzalez, N., Miers, C., Redígolo, F., Simplício, M. A., Carvalho, T., Näslund, M., & Pourzandi, M. (2012). A quantitative analysis of current security concerns and solutions for cloud computing. JournalofCloudComputing:Advances, Systems and Applications, 1(1), 1-18. https://doi.org/10.1186/2192-113X-1-11
[3] Fernandes, D. A. B., Soares, L. F. B., Gomes, J. V., Freire, M. M., & Inácio, P. R. M. (2014). Security issues in cloud environments: A survey. International Journal of Information Security, 13(2), 113-170. https://doi.org/10.1007/s10207-013-0208-7
[4] Zissis, D., & Lekkas, D. (2012).Addressingcloud computing security issues. Future Generation Computer Systems, 28(3), 583-592. https://doi.org/10.1016/j.future.2010.12.006
[5] Subashini, S., & Kavitha, V. (2011). A survey on securityissuesinservicedeliverymodelsofcloud computing. Journal of Network and Computer Applications, 34(1), 1-11. https://doi.org/10.1016/j.jnca.2010.07.006
[6] Aljawarneh, S., Aldwairi, M., & Yassein, M. B. (2017). Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. Journal of Computational Science, 25, 152-160. https://doi.org/10.1016/j.jocs.2017.04.015
[7] Chen, Y., Paxson, V., & Katz, R. H. (2010).What's New About Cloud Computing Security? Electrical Engineering and Computer Sciences University of California Berkeley Technical Report No. UCB/EECS-2010-5. https://www2.eecs.berkeley.edu/Pubs/TechRpts /2010/EECS-2010-5.html
[8] Jansen, W., & Grance, T. (2011). Guidelines on Security and Privacy in Public Cloud Computing. National Institute of Standards and Technology. Special Publication 800-144. https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nis tspecialpublication800-144.pdf
[9] Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities and challenges. Information Sciences, 305, 357-383. https://doi.org/10.1016/j.ins.2015.01.025
[10] Grobauer, B., Walloschek, T., & Stöcker, E. (2011). Understanding cloud computing vulnerabilities. IEEESecurity&Privacy,9(2), 5057.https://doi.org/10.1109/MSP.2010.115
[11] Hashizume, K., Rosado, D. G., FernándezMedina, E., & Fernandez, E. B. (2013). An analysis of security issues for cloud computing. JournalofInternetServicesandApplications,4(1), 5. https://doi.org/10.1186/1869-0238-4-5
[12] Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey of intrusion detectiontechniquesincloud. JournalofNetwork and Computer Applications, 36(1), 42-57. https://doi.org/10.1016/j.jnca.2012.05.003
[13] Pardeep, A., & Sanjay, S. (2020).AComparative Study of Various Cloud Computing Security Issues and Solutions. International Journal of Computer Sciences and Engineering, 8(1), 100108.
https://doi.org/10.26438/ijcse/v8i1.100108
2024, IRJET | Impact Factor value: 8.315 | ISO 9001:2008

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 10 | Oct 2024 www.irjet.net p-ISSN: 2395-0072 © 2024, IRJET | Impact Factor value: 8.315 | ISO 9001:2008
[14] Rittinghouse, J. W., & Ransome, J. F. (2017). CloudComputing:Implementation,Management, and Security. CRC Press. ISBN:978-1498769941
[15]Singh, A., & Chatterjee, K. (2017). Cloud security issues and challenges: A survey. Journal of Network and Computer Applications, 79, 88115. https://doi.org/10.1016/j.jnca.2016.11.027.
| Page