
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Sejal
Pawar1 , Sumaiyya Shaikh2 , Shreya Patil3, Prof. Dr.K.P. Paradeshi4
1234Research Scholar, Dept. of Electronics & Computer Science Engineering, Padmabhooshan Vasantraodada Patil Institute of Technology, Budhgaon, Maharashtra, India
Abstract: - In the era of digital transformation, the integration of biometric fingerprint authentication with cloud computing is revolutionizing public service delivery,particularlyinthefieldsoflawenforcementand identity verification. This research presents a cloudbased system designed to facilitate the online registration of First Information Reports (FIRs) and streamline passport verification using fingerprint biometrics. The proposed system enables citizens to securely authenticate their identities and file FIRs remotely,therebyminimizingtheneedforphysicalvisits to police stations and reducing the risk of fraudulent entries. Additionally, it incorporates fingerprint-based verification into the passport issuance process, allowing for accurate and real-time criminal background checks through a centralized cloud database. The use of Automated Fingerprint Identification Systems (AFIS) significantly enhances the speed and accuracy of individual identification. The platform ensures high availability, robust security, and seamless accessibility for authorized personnel across various locations. Furthermore, this study addresses key challenges related to data privacy, system interoperability, and scalability. The proposed solution promotes greater transparency, operational efficiency, and public trust in safety and identityverificationsystems.
Keywords— Biometric Authentication, FIR Registration, Passport Verification, Cloud Computing, AFIS.
The evolution of biometric technologies, particularly fingerprint recognition systems, has significantly transformed the operations of law enforcement and forensic services. Due to their inherent uniqueness and lifelong consistency, fingerprint biometrics have become afoundationalelementinmoderncriminal identification practices. When integrated with digital infrastructures, these systems enable precise and rapid individual recognition leading to faster case resolutions, more effective identification of repeat offenders, and enhancedtrackingofunidentifiedsuspects.
The widespread deployment of Automated Fingerprint Identification Systems (AFIS) has notably improved the speed and accuracy of matching biometric data against large-scale criminal databases. This has strengthened the capacity of investigative agencies across various legal and securitysectors,reinforcingtheirabilitytomanagecomplex identificationtasksefficiently.
Despitethesetechnological advancements,numerous public service mechanisms particularly in developing and underresourced areas still depend on manual, paper- based processes.Theseoutdatedmethodsoftenleadtooperational inefficiencies, inconsistencies in data handling, and susceptibility to human error. Key public services, such as lodging a First Information Report (FIR) or undergoing passport verification, generally necessitate in-person attendance at government offices. Such requirements not only cause delays and limit accessibility especially for residents in remote or rural regions but also expose the system to potential fraud due to weak or absent identity verificationprotocols.
This study presents an innovative approach aimed at addressingtheselimitationsbydesigningandimplementing a cloud-based digital system for FIR registration and passport verification secured through fingerprint biometric authentication. The primary objective of the proposed solution is to enable citizens to file FIRs remotely via a secure web interface, thereby eliminating the need for physical presence at police stations. To ensure authenticity, fingerprintscanningisemployedasareliablemethodofuser authentication, significantly reducing the likelihood of impersonationorsubmissionoffalsereports.Inconjunction with FIR registration, the same fingerprint data is utilized during the passport verification phase. This allows the system to cross-reference an individual's biometric data with centralized law enforcement records, facilitating accurate and timely background checks before passport issuance. The use of a unified fingerprint database ensures that both police and immigration authorities can access synchronized, real-time information across geographically distributedlocations.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
By leveraging cloud computing, the platform supports a centralized and scalable architecture capable of handling large volumes of sensitive data with high availability, resilience, and robust security protocols. The integration of fingerprint biometrics with cloud-based infrastructure not only streamlines operational workflows but also strengthens system transparency, accountability, and traceability.
This research contributes a practical framework for enhancing the efficiency and credibility of essential governmentservices.Theproposedmodelfostersgreater publictrustandestablishesafoundationformoresecure, transparent,andcitizen-centricpublicsafetyandidentity verification systems. Through this unified digital infrastructure, the project aims to bridge systemic gaps and promote improved interaction between citizens and state institutions thereby advancing the overall effectiveness of law enforcement and immigration processes.
Fingerprint biometric systems have increasingly emerged as vital tools in law enforcement, offering enhanced capabilities for criminal record management and suspect identification. Various methodologies have been proposed and implemented to improve the accuracy, reliability, and efficiency of these systems, particularly in crime investigation and public safety infrastructures.
In the work presented by [1], a fingerprint-based verification system developed for the Nigerian Police Force aims to modernize criminal record handling. Built using Apache, PHP, and Java technologies, the system provides secure data storage and facilitates accurate suspect identification, thereby automating traditional manual processes and improving investigative efficiency. Similarly,
[2] introduces the concept of an Automated Fingerprint Identification System (AFIS), which significantly accelerates and simplifies the identification process. By utilizing contactless scanning and advanced matching algorithms, AFIS offers high-speed, non-intrusive recognitionacrosslarge-scaledatabases.
Abroadoverviewpresentedin[3]outlinesthebenefits and limitations of fingerprint-based biometric systems. Challenges such as spoofing attacks and image degradation over time are addressed, with the authors recommending the implementation of liveness detection andencryptiontechniquestobolstersystemsecurity.The study in [4] proposes a cost-effective fingerprint-based crime investigation platform that enhances the recognition of low-quality prints using binarization, segmentation,andFastFourierTransform(FFT)methods.
Further developments in matching algorithms are examinedin[5],whereimprovedfingerprintidentificationis achieved through image enhancement, feature extraction, and pattern recognition techniques. Thesestrategies are particularly effective in handling poor- quality fingerprint images. In [6], an advanced biometric verification system is proposed, focusing on reducinghumanerrorandincreasing verificationaccuracyinforensicoperations.
A noteworthy contribution in [7] applies convolutional neuralnetworks(CNNs)tofingerprintrecognition,achieving a high accuracy rate of 97% in forensic identification and crime prediction. This system incorporates secure cloud storage and liveness detection, with future enhancements aimedatsupportingmultimodalbiometricauthentication.An Internet of Things (IoT)-based crime record management solutionis introduced in [8],which digitizesFIRsubmission and secures access through fingerprint authentication. This system also employs cloud- based storage for real-time record retrieval, reducing the time required for handling criminalcases.
Theapproachin[9]centersaroundacomputerizedcrime file management system designed to enhance efficiency in FIRhandlingandcriminal datamaintenance.Plannedfuture enhancements include the integration of fingerprint authentication.Inarelatedstudy,[10]proposes a three-tier web-based biometricsystemusingHTML, PHP, and XAMPP, which improves the security and accuracy of crime record management.
A centralized model for criminal record coordination is described in [11], enabling structured interaction among stakeholderssuchaspolicedepartmentsandjudicialbodies. The model simplifies the management of records through centralized processing. In [12], a secure and scalable fingerprint verification system is built using HTML, JavaScript, and PHP. This solution, tested in a local environment,demonstratespotentialfordeploymentinrealtimelawenforcementapplications.
Collaborative data sharing throughfingerprint biometrics is the focus of [13], where the authors highlight improved data accuracy and inter-agency coordination. A multimodal biometric framework integrating fingerprint, facial, palm vein, and iris recognition technologies is presented in [14], developed using Visual C# and MySQL, with the goal of achieving robust suspect identification under varying conditions.
The system discussed in [15] adopts a Rapid Application Development (RAD) model for anonymous crime reporting and real-time communication with police authorities. This approach emphasizes user engagement and fast iterative development. An online FIR filing platform is proposed in [16], featuring automatic routing, attachment of photographic evidence, and real-time tracking, developed usingJava,MySQL,andJSP.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
A more comprehensive solution is offered in [17] through the Crime Management System (CMS), which integrates multilingual support and a user-friendly interface for centralized handling of complaints, criminal profiles, and case histories. Finally, the study in [18]
explores a crime detection and prevention system that utilizes data mining algorithms and AES encryption. The platform includes features such as women’s safety alerts and crime hotspot prediction, providing a forwardlookingperspectiveonproactivecrimeprevention.
The hardware implementation of this system is based on an IoT-enabled biometric authentication architecture, centeredaroundtheESP8266Wi-FimoduleandtheR307 fingerprint sensor. The setup begins with a regulated power supply that delivers the required voltage, typically 3.3V or 5V, to power both the microcontroller andthefingerprintmodule.
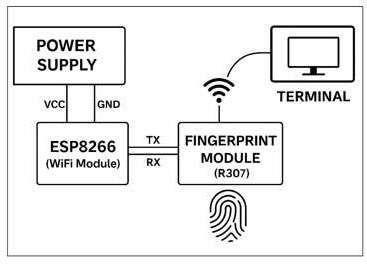
Fig -1:Blockdiagramofcomponentsmountedon PCB
The ESP8266 serves as the central processing and communication unit, responsible for managing data exchange between the biometric sensor and an external terminal or server over a wireless network. The R307 fingerprint sensor performs the core biometric function of acquiring fingerprint images and comparing them against pre-stored templates in its internal memory to determineamatch.CommunicationbetweentheESP8266 andthefingerprintmodule is carriedoutvia serial UART protocol, allowing the microcontroller to receive match results in real time. Once the authentication result is obtained,theESP8266 transmits this data wirelessly toa connectedendpointsuchasawebserver,clouddatabase, or desktop application. The receiving terminal then logs,displays, or further processes the data, enabling use cases such as access control, attendance monitoring, orintegrationwith criminal identification systems. This
design effectively leverages biometric security in combination with wireless IoT communication to provide real-time,remoteoperabilityandmonitoring.
The compact, low-power configuration of the hardware, along with its internet connectivity, makes it suitable for deployment in field applications where centralized access andreal-timedecision-makingarerequired.
The methodology adopted in this project is based on modular design principles and agile development practices, aimingtocreateasecure,scalable,anduser-friendlysystem for FIR registration and passport verification using biometric authentication. The process begins with an authorizedadministratororheadofficerwhoholdselevated access rights to configure system parameters, initiate case entries, and monitor biometric verification results. This is particularly important when cross-referencing with centralized criminal databases to validate applicants. If no criminalhistoryisdetected,thesystempermitscontinuation of the application process; however, if a match is found, the process is halted and legal authorities are alerted. Technologically,thesystemisimplementedusingafull-stack architecture.ThefrontendisbuiltwithReactandTypeScript forrobust,maintainableinterfaces,styledwithTailwindCSS to ensure responsive design, and developed using Vite for faster builds and hot module replacement. The backend is poweredbyNode.jsandExpress.js,whichhandleserver-side logic and API routing, while PostgreSQL serves as the relationaldatabasestoringencryptedrecordsincludinguser data,biometricinformation,FIRlogs,andsystemactivity.For biometriccapture,theR307 fingerprint sensor is integrated with a NodeMCU ESP8266 microcontroller, mounted on a customPCBand enclosed in a durable casing for real-world deployment.Thesystemcapturesbothfingerprintandfacial data, ensuring dual-layer authentication fingerprints offer tamper-proof identification, while facial recognition preventsimpersonation.Thisdual-modalapproachnot only enhances security but also reduces false acceptance and rejection rates. The hardware setup has been rigorously tested under varying environmental conditions to ensure operational stability and accuracy. For new users, biometric and personal information is securely registered; for returning users, live biometric data is matched with stored templatesto authenticate identity.All data is encrypted and storedinacloud-hostedPostgreSQLdatabase,allowinghigh availability, scalability, and real-time access for authorized personnel across locations. The platform supports dynamic record updates, which are revalidated and stored upon modification.A built-indata analysisphasescans records to detect potential matches or patterns, particularly useful for identifying repeat offenders or links between cases. Security is reinforced through Role-Based Access Control (RBAC),wheredifferentuserrolessuchas

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
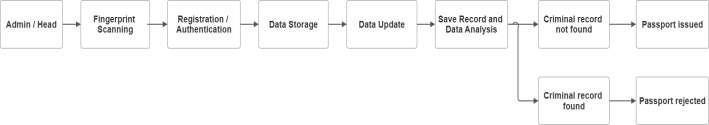
-2: Workflow Diagram of Passport Verificationand FIR Registration Process Using BiometricAuthentication
constables and PSIs are assigned permissions according to their responsibilities. Additional safeguards include real-time form validation, input sanitization, encrypted API communication, and compliance with data protection standards. The system is deployed on cloud platforms such as Firebase or Vercel, offering disaster recovery, synchronization, and scalability. In essence, this methodology provides a technologically robust and practical solution for enhancing public safety workflows by enabling secure biometric verification, efficientdatamanagement,andimprovedcoordination acrosslawenforcementunits.
T T he software flowchart outlines the operational design of a biometric-based criminal registration and verification system, aimed at streamlining both the registration of criminal records and the verification processforpassportissuance.Thesystemprovidestwo distinct user roles: Admin Login for constables and ReaderViewLoginforhigherauthoritiessuchasPSIor Head officers. Upon starting, users are directed to a dashboard where they select their access level. In the Admin flow, constables can register new criminal information by capturing fingerprints and entering personal details. If the fingerprint is successfully captured, the user can proceed to edit, delete, or add criminal data through a controlled interface. After updatingthedatabase,recordsaresavedandvalidated toensuresuccessfulregistration.Therecordscanthen be managed or modified through the system's management interface. On the other hand, the Reader Viewflowisprimarilyusedforverificationpurposes.A fingerprint scan is performed, and if successfully collected,thesystemchecksforamatchinthecriminal database. Ifa match is found, the passport is issued.If not,thepassportisdenied,andtheregistrationprocess is initiated for new data entry. The newly captured dataissavedanddisplayedinastructuredformat for record management. Both flows conclude with a logout operation, ensuring secure session termination. his role-based, fingerprint-driven system enhances data integrity, improves user accountability,andsupportssecuredecision-making in both criminal registration and identity verification processes
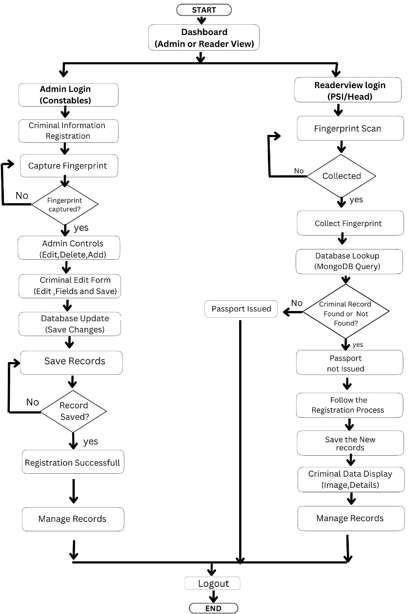
Fig -3: Role-Based System Workflow for Admin andReaderViewsinFIRandPassportVerification Process.

The following images showcase the practical implementation and working interface of our CloudBased Unique Online Police FIR Registration and Passport Verification System using Fingerprint Authentication.Eachinterfacehasbeendesignedtofulfill a specific functionality, ensuring a seamless and secure workflowforthepoliceandverificationdepartments.
-4:Admin/ConstableLoginPageofFIRSystem
This login interface is exclusively designed for Admins and Constables who possess authorized credentials to access theFIR System. Only users with a valid username and password can log in, ensuring secure entry into the platform.
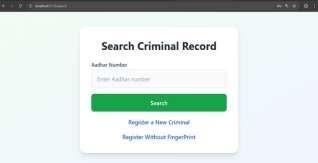
The system includes an input field for entering a 12digit Aadhaar number, which serves as a unique ID to search for an individual’s criminal record. Aadhaar is issuedtoIndianresidentsandactsasthemainidentifier in this process. After entering the number, clicking the green “Search” button retrieves any linked criminal recordsbyaccessingthebackenddatabase.Theinterface also offers options to manage records. The “Register a NewCriminal”featureallowsuserstoaddanewentryto the criminal database. The “Register Without Fingerprint” option is useful when biometric data is unavailable, such as in cases of unclearfingerprintsor a faulty scanner. These options enhance the system’s usability andadaptability.
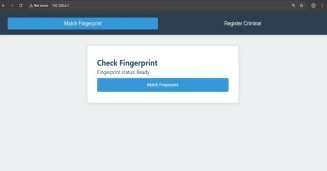
The "Check Fingerprint" button at the center initiates the scanning of a person’s fingerprint using a biometric device. Once scanned, the system automatically compares the fingerprint with those stored in the criminal database to identifytheindividualandretrievetheirrecordifamatchis found. The left panel features a "Match Fingerprint" option that allows users, such as police officers, to manually verify fingerprints against existing data. The "Register Criminal" option at the top indicates that the system also supports registering new suspects, helping to maintain accurate recordsandquicklyidentifyrepeatoffenders.
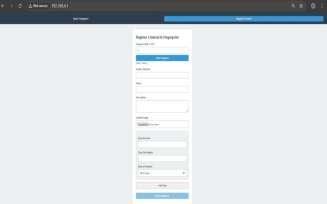
The "Register Criminal & Fingerprint" page is designed forlawenforcementtoinputandstoreacriminal'spersonal and biometric information. It includes fields for the individual's full name, a description of their crime (such as theft or robbery), and their 12-digit Aadhaar number to ensure proper identity linkage. The interfaceprovides two mainfunctions:"ScanFingerprint"tocapturebiometricdata using a fingerprint scanner, and "Register Criminal" to save allenteredinformationintothecriminaldatabaseforfuture referenceandidentification.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
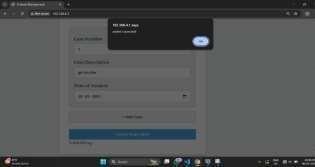
Fig -8: SuccessfulRegistrationAlert
This image illustrates a confirmation alert that appears after a case is successfully submitted in the system.TheformincludesfieldssuchasCase Number, Case Description, Date of Incident, and Place of Crime. After filling out the information and submitting the form, a "Submitting..." message is displayed, followed by a successalertpop-uponthe right, confirming that thecasehasbeenrecordedinthesystem.
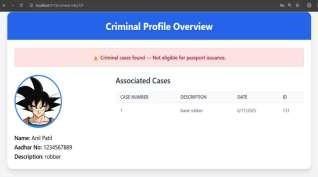
The figure displays the Criminal Profile Overview pageofanindividual,showingherphoto,basicdetails, and Aadhaar number. The system indicates that there are no criminal records associated with her/his, confirminghereligibilityforpassportissuance.
6. Conclusion
The cloud-based unique online police FIR registration and passport verification system using fingerprint authentication offers a modern, secure, and efficient approach to publicsafety and identity verification. By integrating biometricauthentication, the system ensures accurate identification reduces the chances of impersonation, and maintains the integrity of FIRs and passport applications. The centralized cloud infrastructure allows police
departments across the country to access and update criminal records in real time, promoting transparency, faster response, and better coordination among authorities. This system simplifies the FIR registration process for citizens while enhancing accountability within the police department. It also streamlines passport verification by enabling rapid background checks using fingerprint data, saving time and reducing manual workload.Overall,theprojectdemonstrateshow the use of biometric and cloud technologiescanstrengthen national security,improvepublicservicedelivery, and support the broadervisionofadigitallyempoweredIndia.
[1] Nnadimma, C.E. (2018). Design and implementation of an online crime reporting system. Dissertation, SchoolofPostgraduateStudies,UniversityofLagos.
[2] Jamal,F.,Barrow,M.,Alam,M.J.,&Mustafa,N.(2019). Unique model of criminal record management system in the perspective of Somalia. JOIV International Journal of Inform.Vis., 3, 332–336.
[3] Macleod, R. (2019). Crime and criminals in the North-West Territories 1873–1905. In: The NorthWest Mounted Police and Law Enforcement, 1873–1905(pp.114–130).UniversityofTorontoPress.
[4] Ganiron Jr, T.U., Chen, J.S., & Dela Cruz, R. (2019, June). Development of an online crime management &reportingsystem.
[5] Ristroph,A.(2018).Thethinbluelinefromcrime to punishment. Journal of Criminal Law and Criminology,108(2),305–334.
[6] Alrwisan, A., Ross, J., & Williams, D. (2011). Medication incidents reported to an online incident reporting system. European Journal of Clinical Pharmacology, 67(5), 527–532. https://doi.org/10.1007/s00228-010-0986-z
[7] Amer, M., Bari, D. M. A., & Khare, D. A. (2022). Fingerprint image identification for crime detection. International Journal for Advanced Research in Science and Technology, 12(10), ISSN2457–0362.
[8] Criminal Records Ohio Information System [Online].Available:http://ww.society.ezinemark.co m/criminalrec ordsohioinformationsystem171e851d4ae.html [Accessed:18April2019].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
[9] ArchanaM.,etal.OnlineCrimeReportingSystem. International Journal of Advanced Networking andApplications(IJANA).
[10] Dr. Nilakshi Jain & Siddharth Agarwal. (2017). Crime File System. International Journal of Advanced Research, Ideas and Innovations in Technology,3(1).
[11] Shweta Gaur & V.A. Shah. (2012, October). Biometric Recognition Techniques: A Review. International Journal of Advanced Research in Electrical, Electronics, and Instrumentation Engineering,1(4).
[12] Anil K. Jain & Ajay Kumar. (2010). Biometrics of Next Generation: An Overview – Second GenerationBiometrics.Springer.
[13] Tatale, S., & Sakhare, S. Intellectual Crime Recognition System. IOSR Journal of Computer Science (IOSR-JCE), e-ISSN: 2278-0661, p- ISSN: 2278-8727,pp.40–45.
[14] Amuji, H.O., Chukwuemeka, E., & Ogbuagu, E.M. (2019). Optimal Classifier for Fraud Detection in Telecommunication Industry. Open JournalofOptimization,8,15–31.
[15] Anil K. Jain & Arun Ross. (2015). Bridging the gap: from biometrics to forensics. Philosophical Transactions: Biological Sciences, 370(1674), 110.
[16] Arua,A.I.,Chigbu,P.E.,Chukwu,W.I.E.,Ezekwem, C.C.,&Okafor,F.C.(2000).AdvancedStatisticsfor Higher Education. The Academic Publishers, Nsukka,Nigeria,pp.82–91.
[17] Laufer, B. (1917). Concerning the History of Finger-Prints. American Association for the AdvancementofScience.
[18] Criminal Records Ohio Information System (2011). Retrieved from: http://society.ezinemark.com/criminalrecordsOhio-information-system171e851d4ae.html