
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 05 | May 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 05 | May 2025 www.irjet.net p-ISSN: 2395-0072
Shubham Tukaram Andhale1 , Saurabh Sandip Vaidya2 , Mangesh Balasaheb Kakade3 , Prof.Shital. Y. Mandlik4
123Under Graduate Student, Jaihind College of Engineering, Kuran, Pune 4Professor, Jaihind College of Engineering, Kuran, Pune
Abstract - In today’s digital healthcare environment, safeguarding sensitive patient information is a critical challenge, especially with the growing use of wireless networksfordatatransmission.Thispaperpresentsasecure and efficient healthcare data management system that integratesSmartCardtechnology,QRcodeencryption,and Aadhar-basedauthenticationtoensureprivacy,accessibility, and rapid information exchange. The proposed system allows medical professionals to access encrypted patient records by scanning QR codes linked to smart cards, with identityverificationbackedbyAadharcredentials.Datais protected using robust encryption techniques like AES, ensuringconfidentialityduringwirelesscommunication.The systemisdesignedtosupportdiverseapplicationssuchas emergency services, remote consultations, prescription verification, and insurance processing. It also addresses technicalchallengeslikehardwarecompatibility,securedata synchronization, and user-friendly authentication. The developed platform uses Java, JSP, and MySQL, and was tested successfully through unit, integration, and systemlevel testing. With its scalable design and potential for integration with biometric systems and cloud-based services, this solution offers a future-ready approach to digitalhealthcaredatasecurity
KeyWords: Medical Data Privacy, Data Security, Wireless Networks, Smart Card Technology, QR CodeIntegration, Aadhar Card Authentication
With the increasing digitization of healthcare services, protecting patient data has become a critical concern. Traditional systems often lack strong security, making medical records vulnerable to unauthorized access and misuse especially over wireless networks. This paper presentsasecurehealthcaredatamanagementsystemthat combines Smart Cards, QR code encryption, and Aadharbased authentication to ensure data privacy and secure access.
The system allows authorized users to access encrypted patientinformationthroughQRcodeslinkedtosmartcards, withstrong encryptionand identityverification.Designed for use in hospitals, emergency services, and remote healthcare,thesystemimprovesbothsecurityandefficiency.
Built using Java, JSP, and MySQL, the platform offers a
scalablesolutionwithfuturepotentialforcloudintegration, biometricauthentication,andAI-basedmonitoring.
Zhao, Y., & Zhang, L.[1] Proposed a secure medical data sharing scheme that effectively utilizes smartcardsandQRcodestoenhancedataprivacyin wirelessnetworks
Khan, M. A., & Ali, S.[2] Developed a privacypreservingdata-sharingframeworkthatleveragesQR codesandsmartcardtechnology to secure healthcareinformation.
Patel, S., & Desai, A.[3] Introducedasmart card authenticationmethodthatsignificantly improves thesecurityofmedicalrecords transmittedover wirelessnetworks.
Li & Wang[4] Presentedasmartcard-based approach thatsuccessfullyenhancesthesecurity of wireless medicaldatatransmission.
Chen, Y., & Liu, T.[5] Proposedasecureaccesscontrol mechanismformedicaldatausing smart cards withinwirelesshealthnetworks.
Ashealthcaredataincreasinglymovesonline,theriskofdata breaches and unauthorized access has become a major concern especially over wireless networks. Existing systems often lack strong encryption and reliable authentication methods. This project is motivated by the needtocreateasecureandaccessiblesolutionthatprotects sensitive medical data. By using Smart Cards, QR code encryption, and Aadhar verification, the system aims to ensuredataprivacy,quickaccess,andtrustworthyidentity verificationinbothurbanandruralhealthcareenvironments.
With the growing use of digital platforms and wireless networksinhealthcare,ensuringthesecurityandprivacyof patientdatahasbecomeacriticalchallenge.Manyexisting

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 05 | May 2025 www.irjet.net p-ISSN: 2395-0072
systems depend on weak password-based authentication and lack encryption, making them vulnerable to unauthorizedaccess,databreaches,andidentitytheft.These issues are especially concerning in emergency situations, remote consultations, and rural healthcare setups, where secureandfastaccesstomedicalrecordsisvital.Therefore, there is a need for a system that provides strong authentication, encrypted data sharing, and user-friendly accesswhileensuringpatientconfidentiality.
5. Objectives
1. Toenhancethesecurityandprivacyofmedicaldata using Smart Cards, encrypted QR codes, and Aadhar-basedauthentication.
2. To enable fast, secure, and authorized access to patientrecordsoverwirelessnetworks.
3. To improve healthcare efficiency, especially in emergenciesandruralareas,throughuser-friendly andscalabletechnology.
6. Scope of project
1. Remote Healthcare Services: Provide online consultations, appointment scheduling, and prescriptionmanagementto enhance patient accesstohealthcareremotely.
2. PatientandDoctorInteraction:Enablesecure communicationbetweendoctorsandpatients through video consultations, chat, and realtimeupdatesonhealthdata.
3. Medical Records Management: Develop a centralizedsystemtostoreandmanagepatient healthrecords,ensuringeasyaccessfor both patientsandhealthcareproviders.
4. DataSecurityandPrivacy:Ensurerobustdata security measures to protect patient information, complying with healthcare regulationsandstandards.
7. Advantages
1.Easy Access – Patientscanconsultdoctorsfrom anywhere,anytime.
2.Saves Time & Money – Reduces travel and waitingtimefortreatment.
3.DigitalRecords – Centralizedmedicaldatahelps infasterandaccuratediagnosis.
4.Real-Time Monitoring – Trackspatienthealth usingwearabledevices.
5.ImprovedCommunication –Smoothinteraction betweendoctorsandpatients.
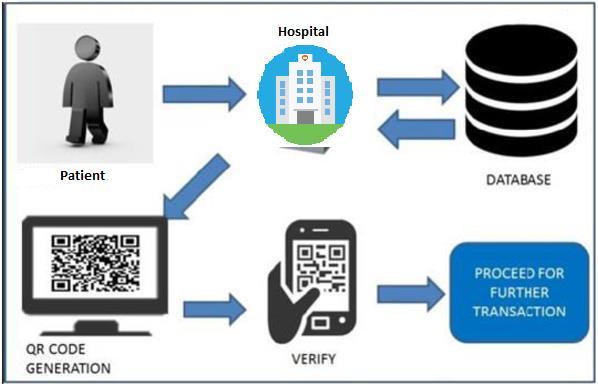


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 05 | May 2025 www.irjet.net p-ISSN: 2395-0072
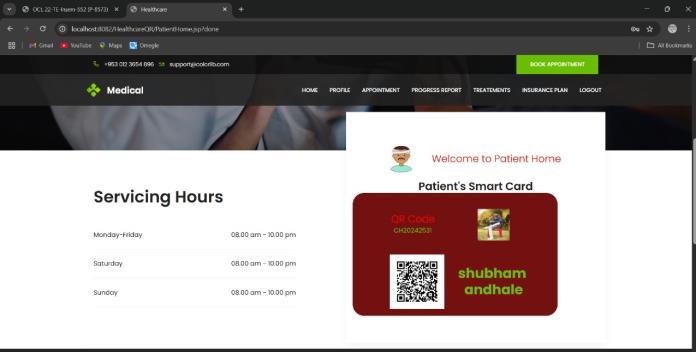
Thee-healthcaresystemplaysacrucialroleintransforming traditional healthcare by offering efficient, accessible, and cost-effective medical services. Through features such as onlineconsultations,centralizedmedicalrecords,andrealtimehealthmonitoring,thesystembridgesthegapbetween patients and healthcare providers. It not only improves patient care and reduces waiting times but also helps in bettermanagementofhospitalresources.Byensuringdata security and user-friendly interfaces, this system can be effectivelyadoptedin bothurbanandrural areas.Overall, theprojectaimstocreateareliableplatformthatenhances the quality of healthcare services while promoting digital healthinnovation.
[1]S.Wan,Y.Lu,X.Yan,W.Ding,andH.Liu,“Highcapability embedding ways that of qr code error correction,” in InternationalWirelessInternetConference,2016,pp.70–79.
[2]X.Yan,S.Guan,andX.Niu,“Researchonthepotentialof error-correctingcodes-basedinformationconcealment,”in Iihmsp’08 International Conference on Intelligent information concealment and multimedia Signal method, 2008,pp.1158–1161.
[3] J. Weir and W. Yan, “A comprehensive study of visual cryptography,” in: Transactions on DHMS V, LNCS 6010, Springer-Verlag.Berlin,Heidelberg:Springer,2010,pp.70–105.
[4]Z.Wang,G.R.Arce,andG.DiCrescenzo,“Halftonevisual cryptographyviaerrordiffusion,”IEEETrans.Inf.Forensics Security.,vol.4,no.3,pp.383–396,2009.
[5]X.Yan,X.Liu,andC.-N.Yang,“Aninflatedthresholdvisual secretsharingsupportedrandomgrids,”Journalofyourtime amountImagemethod,vol.14,no.1,pp.61–73,Jan2018.
[6]X.Yan,S.Wang,andX.Niu,“Thresholdconstructionfrom specificcasesinvisual cryptographywhereasnotthepart enlargement,”Signalmethod,vol.105,pp.389–398,2014.
[7] G. Wang, F. Liu, W. Q. Yan, “2D Barcodes for visual cryptography,”MultimediaToolsandApplications,vol.2,pp. 1-19,2016.
[8]C.N.Yang,J.K.Liao,F.H.Wu,etal.,“DevelopingVisual Cryptography for Authentication on Smartphones,” IndustrialIoTTechnologiesandApplications,vol.173,pp. 189-200,2016.
[9]W.Song,Y.Lu,X.Yan,etal.,“Visualsecretsharingscheme for (k, n) threshold based on QR code with multiple decryptions,”JournalofReal-TimeImage-Processing,pp.116,2017.
[10]YW.Chow,WSusilo,GYang,etal.,“ExploitingtheError Correction Mechanism in QR Codes for Secret Sharing,” InformationSecurityandPrivacy,pp.409-425,2016.