
CELL PHONE PRIVACY AND UNWANTED ACCESS
Waratchaya Luangphairin (June) | Lara Radovanovic | Zahid Rahman
TABLE OF CONTENTS
1.Introduction
2.Different Types of Mobile Privacy Threats
3.Signs of Compromise
a. What to Do Next
4. Limiting App Access
Screenshots & Step-by-Step Help For iOS
a. Disable App Tracking
b. Turn off Ad Personalization
c. Disable Safari Tracking
d. Disable iCloud & Siri Tracking For Android
a. Disable App Tracking
b. Turn off Ad Personalization
c. Delete Current Advertising ID
d. Turn off Web & App Activity
e. Turn off Usage & Diagnostics
5. Securing Your Phone
6. Good Habits
Introduction
In today’s digital world, mobile phones are more than just phones. They are our personal secretaries. They manage our schedules, store our health and insurance information, act as our bank and workstations, and encapsulate our entire social lives through apps, photos, videos, and voice messages. Even our thoughts, plans, and sometimes passwords are kept in note apps making our phones both our diaries and our digital identities. With this kind of access, it is no surprise that mobile devices make prime targets for cyber threats. A private and secure device is defined as being “free from the danger or risk of an asset loss or data loss” [1]. What are the chances that your phone is safe?
This informational report discusses cell phone privacy and how to prevent unwanted access, or in other words, when “a person gains logical or physical access without permission to a network system, application, data, or other resource [2]. You will be walked through the different types of threats, how to recognize signs of compromise, and most importantly, what steps you can take to protect your device and data from the many risks that disguise as convenience.
With real-world examples, reputable statistics, and a step-by-by-step guide for both iOS and Android devices, this report serves to help mobile users of all levels stay informed and in control.
Different Types of Mobile Privacy Threats
A.Phishing and Mishing (Mobile Phishing)
Phishing is when an attacker impersonates a trusted, legitimate entity to trick potential victims into giving sensitive information. Similarly, mishing is phishing that happens exclusively on cell phones. This type of tactic often utilizes SMS text messaging apps (smishing), voice calls (vishing), emails, QR codes (quishing), and fake websites [3].
As of 2024, 82% of phishing scams happen on cell phones [4], and 76% of phishing sites now use a secure protocol known as HTTPS. Traditionally, users were taught to trust "S” in HTTPS, as it stands for “secure”. Today, even malicious websites can use HTTPS as it only encrypts the connection and not the content of the site itself. Phishing pages can still look legitimate while being dangerous.
Owned by Google and requiring HTTPS by default, the .dev domain is often trusted by users visiting the site. In 2023, 40% of phishing sites used the .dev domain. [4]
Example: A user receives a text claiming to be from their bank, warning them of suspicious activity putting their account on temporary hold. In the text, the bank urges the user to click a link that will reactivate their account. This link asks the user to confirm their credentials, leading to a successful login credential harvest.
B. Downloading Malicious Apps:
Malicious apps often disguise themselves as helpful but once installed, they can steal your data, sell your data, spy on you, or download more malware.
A breakdown per category showed that malicious apps often come in the form of photo editors (42.6%), business utilities (14.1%), phone utilities (15.4%), games (11.7), VPNs (11.7), and lifestyle apps (4.4%) [5].
60% of iOS apps and 43% of Android apps are vulnerable to leaking personally identifiable information (PII) [4].
Example: To edit a photo for social media, a user decided to download a seemingly harmless photo editor app. Unbeknownst to the user, this app has secretly installed spyware, gaining access to the camera without the user’s consent [6].
C. Unsecured Wi-Fi
Public Wi-Fi networks, like the ones in coffee shops, airports, or hotels, often have no encryption. Data sent over them can be intercepted by anyone within the vicinity. Attackers can employ a man-in-the-middle (MITM) attack to eavesdrop, steal login credentials, or inject malware onto those devices. Because public networks are easy to access and usually unsecured, they’re a common target for cybercriminals.
According to Forbes, 40% of respondents who used public Wi-fi had their information compromised [7].
Example: An employee on a business trip connects to “free airport Wi-Fi" that happens to be a fake Wi-Fi network set up by a hacker to steal email and social media credentials [8].
D. Outdated Operating Systems
Outdated Operating systems are prone to critical security vulnerabilities that their updated counterparts are not. When an operating system gets updated, the former vulnerabilities are publicly documented. Attackers can easily reference these documentations to exploit outdated devices, making them easier targets [9].
61.2% of Android devices and 49.2% of iOS devices run on outdated operating systems during any given 12-month period [4].
Example: A user keeps postponing system updates, thinking they’re time-consuming. Consequently, this delay leaves a known vulnerability unpatched. An attacker exploits it remotely to install spyware, allowing them to monitor the device without the user ever clicking on a link or opening an app.
E.Excessive App Permissions
Mobile apps require permissions to perform tasks such as access to photos, contacts, location, microphone, and camera. For example, Some apps ask for way more access than they need. If not careful, users could be granting third-party apps permission to collect, share, or even sell personal data without realizing it. Once an app has permission, it doesn’t need to hack your phone; it already has the access it needs. [10].
Commonly Exploited Permissions:
Camera: Given camera permission, photos or video can be taken without consent.
Microphone: Granting microphone access could enable an app to record conversations or build advertising profiles. [11].
Location: Enabling location while using an app could reveal your home address, workplace, daily stops, and information that can be sold or used for advertising, stalking, burglary, or adverse purposes. [11].
Storage: Granting storage access could allow the app to access personal files, photos, and downloads, which can be extracted or sold to third parties.
Contact list: Sharing your contact list with certain apps could lead to targeted advertising or data being sold to third parties.
Bluetooth: Enabling Bluetooth may open the door to wireless exploitation or device tracking.
Before granting an application permission, consider its function. Do not give an app permission outside of its scope of use.
3.Signs of Compromise
If your mobile device is behaving unusually, it could be a sign of compromise.
Common symptoms include:
Unrecognizable downloads, messages, purchases, etc. [12].
Applications randomly open on their own [12,14].
Diminished battery capacity [12].
Device slows down [12].
Applications crashing [12].
Pop-ups [12,14].
Unexplained data usage
New apps
Mysterious outgoing calls
What to Do Next
Take immediate action if you suspect your phone is hacked:
1.Delete suspicious apps [13].
2.Check your accounts [13].
3.Update login credentials [13,14].
4 Alert contacts
5.When in doubt (as a last resort) factory reset.
4. Limiting App Access
A recent report lists that 69% of users’ digital media time is actually spent on mobile phones only [15]. A widespread, and continuous use launched mobile devices as the primary platform for personal data collection subsequently used in targeted ads. Targeted ads pose serious privacy risks and concerns such as third-party tracking [16]. Even though mobile users still use browsers to access different websites, applications (apps) are gradually replacing browser function. Most mobile applications contain at least one ad library that enables targeted advertising [16]. The instructions below provide a guide for disabling tracking across apps.
Screenshots & Step-by-Step Help:
In this section we will walk through the different types of ways you can make your phone secure. We will cover both iOS and Android.
For iOS
A. Disable App Tracking
B. Turn off Ad Personalization
C. Disable Safari Tracking
D. Disable iCloud & Siri
Suggestions
For Android
E. Disable App Tracking
F. Turn off Ad Personalization
G. Delete Current Advertising ID
H. Disable Web and App Activity
I. Turn off Usage & Diagnostics
For iOS
A. Disable App Tracking
1.Open the Settings app. Tap the settings icon on your home screen.
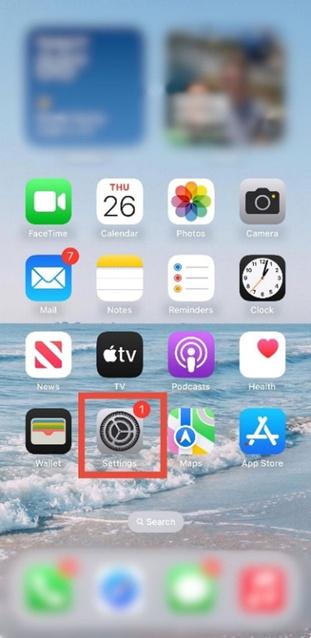
2. Go to Privacy & Security. In settings, scroll down and tap Privacy & Security.
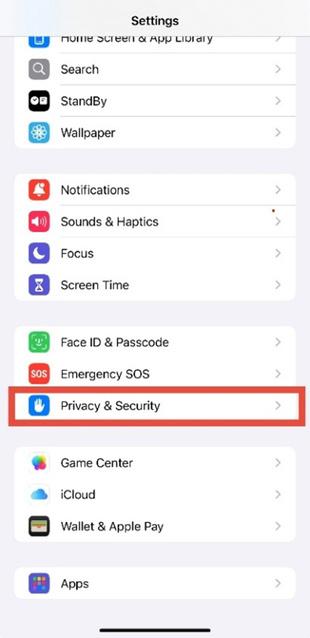
3. Select Tracking
Under Privacy & Security, tap Tracking.
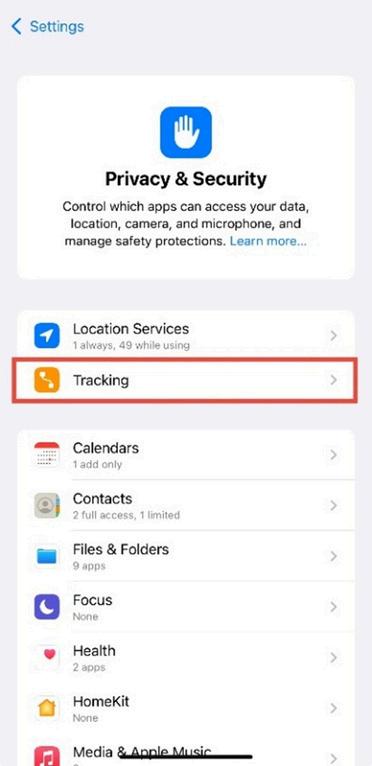
Figure 1 3: Privacy & Security menu with the “Tracking” option visible
4. Disable Allow Apps to Request to Track.
Toggle it off to automatically deny tracking requests from new apps.
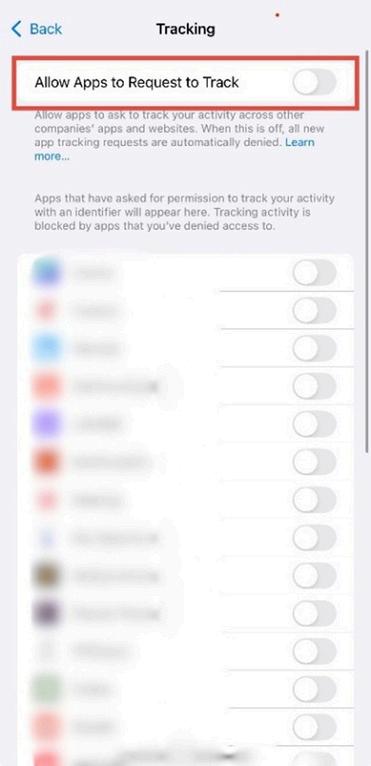
Figure 1 4: Tracking settings showing “Allow Apps to Request to Track” turned off (switch turns grey
B. Turn off Ad Personalization
1.Open the Settings app. Tap the settings icon on your home screen.

2. Go to Privacy & Security. In settings, scroll down and tap Privacy & Security.

3. Select Apple Advertising. In the Privacy and Security menu, scroll down and tap Apple Advertising.
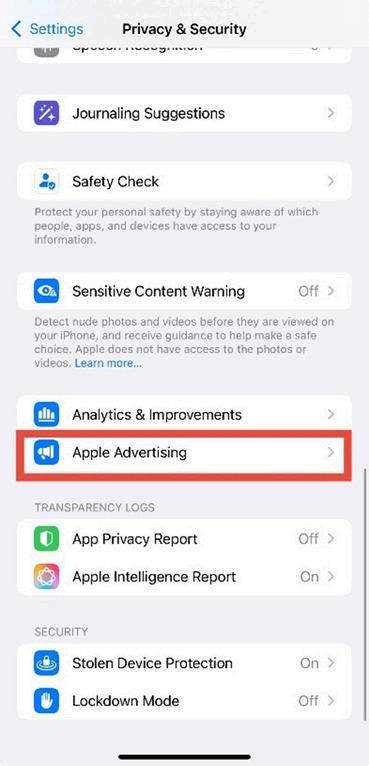
Figure 2.3: Privacy & Security menu showing “Apple Advertising.”
4. Turn off Personalized Ads. Toggle Personalized Ads to the OFF position (gray).
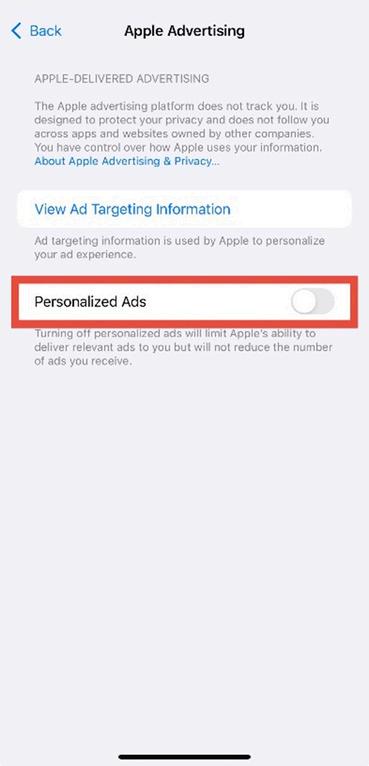
Figure 2.4: Apple Advertising settings with “Personalized Ads” disabled (switch turns grey).
C. Disable Safari Tracking
1. Open the Settings app.
Tap the settings icon on your home screen.
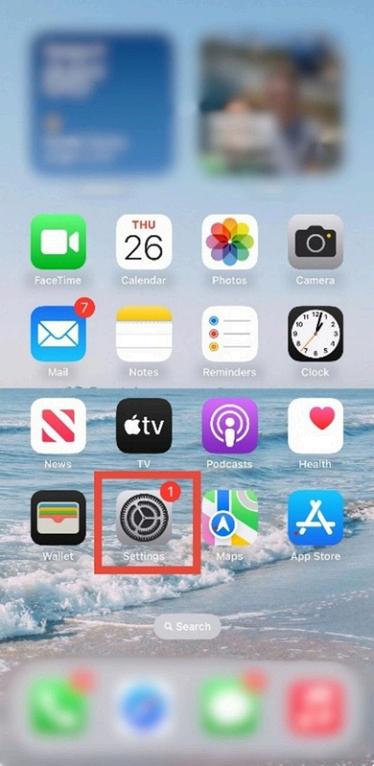
Figure 3 1: iPhone home screen with the Settings app highlighted
4. Access Apps Tap Apps.
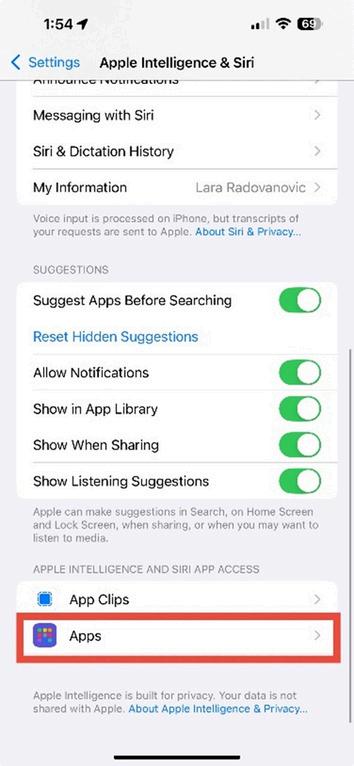
Figure 3 2: Settings menu showing “Apps ”
3. Find Safari In Apps, tap Safari.
4. Enable Privacy Settings. Toggle the following options to ON (green).
Prevent Cross Site Tracking Hide IP Address
Figure 3.3: Apps list with “Safari” selected.
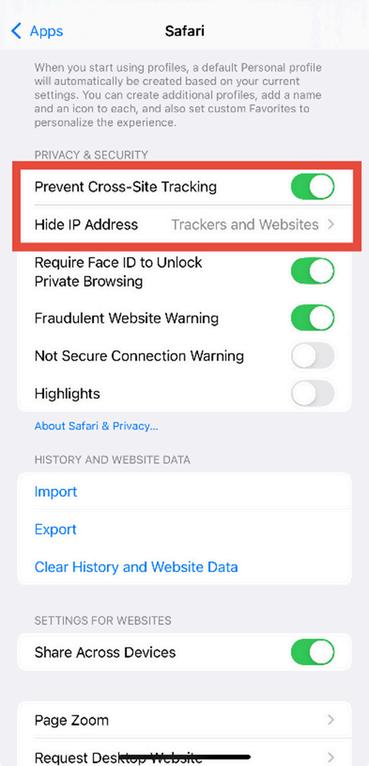
Figure 3.4: Safari settings showing tracking protections toggled on (switches turn green).
5. Disable Seach and Suggestion Tracking.
Scroll down and turn off the following:
Search Engine Suggestions Safari Suggestions
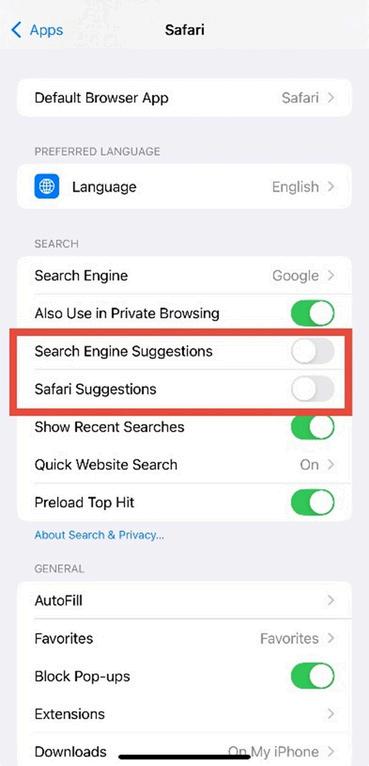
Figure 3.5: Safari settings with “Search Engine Suggestions” and “Safari Suggestions” turned off (switch turns grey).
6. Go to Advanced Settings. Scroll to the bottom and tap Advanced.
Figure 3.6: Safari settings scrolled to the bottom with “Advanced” selected.
7. Block all cookies (optional)
In Advanced, toggle Block All Cookies to ON. Note: This may break certain websites or logins.
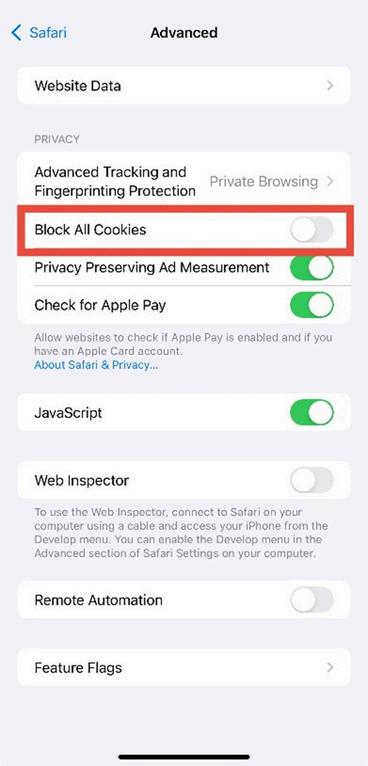
Figure 3 7: Advanced Safari settings showing the “Block All Cookies” toggle. To block, turn on (switch will turn green)
D. Disable iCloud & Siri Tracking
1 Open the Settings app. Tap the “Settings” icon on your home screen.

Figure 4.1: iPhone home screen with the Settings app highlighted.
2. Go to Privacy & Security In settings, scroll down and tap Apple Intelligence & Siri
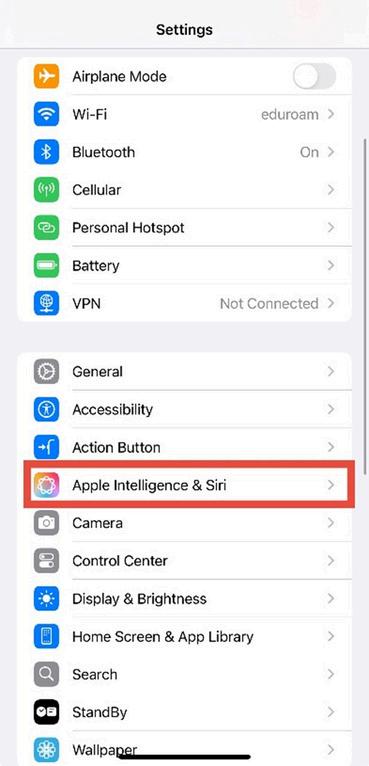
Figure 4.2: Settings menu showing the “Apple Intelligence & Siri” option.
3. Go to Apps
Under Apple Intelligence & Siri, scroll down and tap Apps.
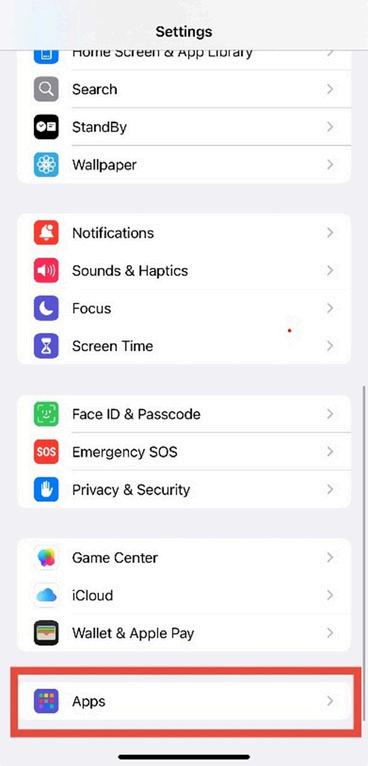
Figure 4.3: Apple Intelligence & Siri menu showing the “Apps” option under app access settings
4. Select an app, and toggle “Learn from this App” off.
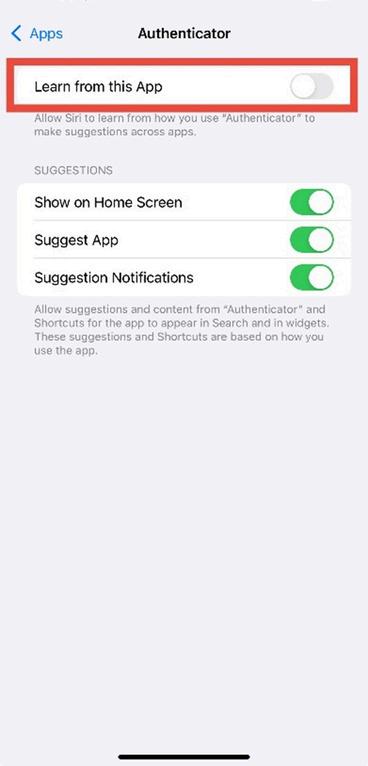
Figure 4.4: Individual app settings with “Learn from this App” toggled off (switch turns grey)
For Android
E.
Disable App Tracking
1 Open Chrome
Tap the profile icon located in the top right corner of the browser.
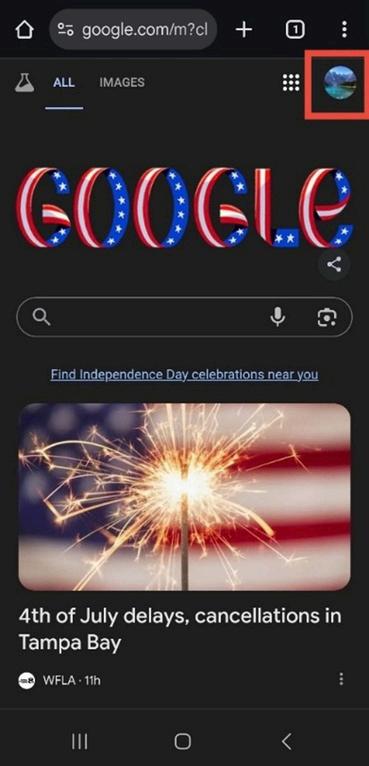
2. From the menu, go to Settings. Scroll down and tap privacy and security.
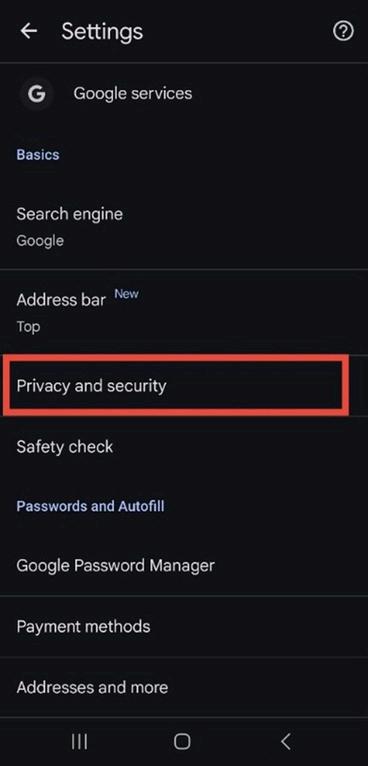
3. Under the Privacy section, select “Send a ‘Do Not Track’ request.”
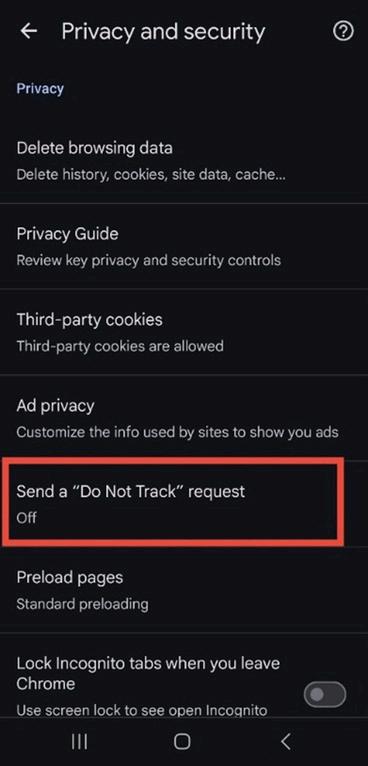
Figure 5 3: Privacy and Security settings in Chrome showing the “Send a ‘Do Not Track’ request” option
4. Toggle the switch to turn it on. This will send website requests asking not to track your browsing activity.
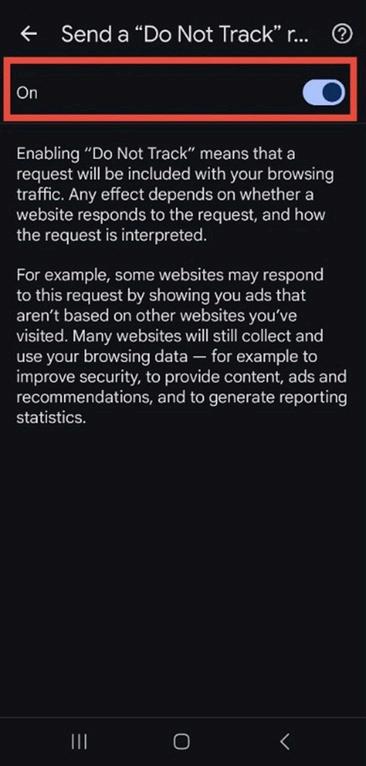
Figure 5 4: Do Not Track settings screen with the toggle switch turned on (switch turns blue)
F. Turn off Ad Personalization
1.Open the app drawer. Swipe up or open the app drawer icon to view all apps.
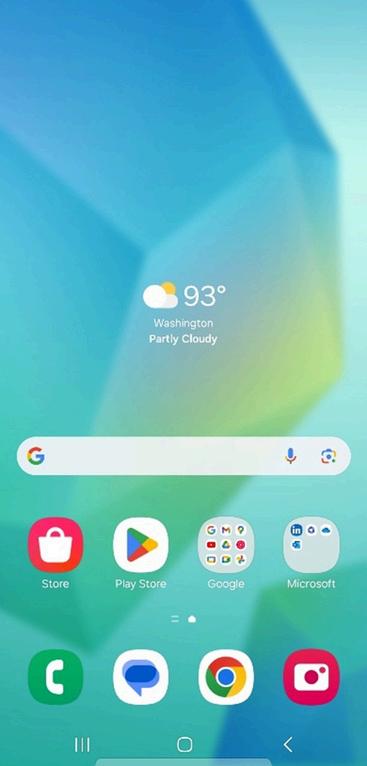
2. Go to Settings. Tap Settings from the app list.

3. Access your Google account Tap your profile icon or name to open your Google Account dashboard.
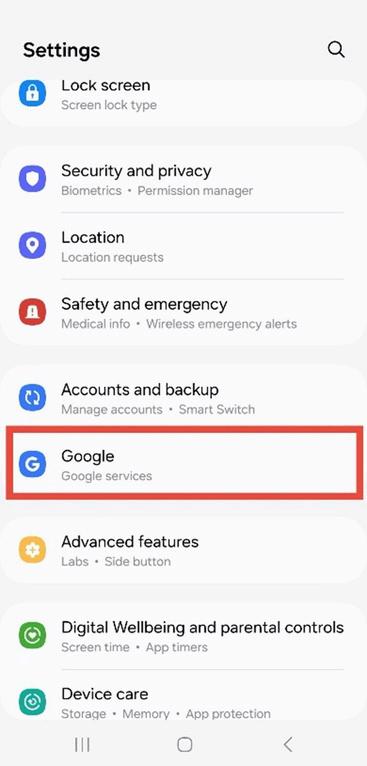
Figure 6 3: System Settings menu showing the “Google” option under Accounts and Backup
4. Open the Data & Privacy tab Tap on profile icon again to access Data & privacy.
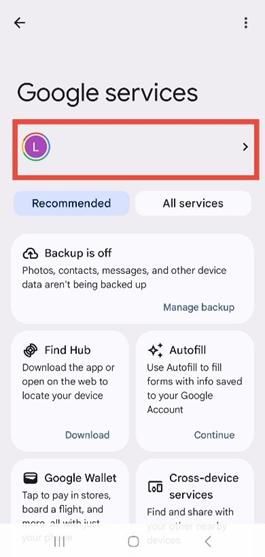
Figure 6 4: Google Services page displaying the user profile icon and recommended service cards
5. Scroll to the “Personalized Ads” section.
Tap My Ad Center and turn off Personalized Ads.
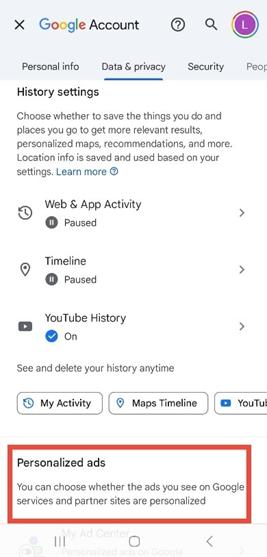
Figure 6 5: Google Account dashboard under the “Data & privacy” tab with the “Personalized ads” section visible
6. Disable Search Personalization
Scroll to Search personalization and toggle it Off.
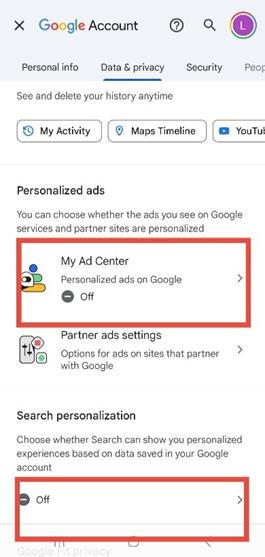
Figure 6 6: Google Account settings showing “My Ad Center” and “Search personalization” toggled off
G. Delete Current Advertising ID
7. Open the app drawer. Swipe up or open the app drawer icon to view all apps.

8. Go to Settings. Tap Settings from the app list.

9. Select Google. In settings, tap “Google.”

Figure 7 3: System Settings menu showing the “Google” option highlighted
10. Navigate to Ads. Under All Services option located in the top right corner, scroll down to select Ads.
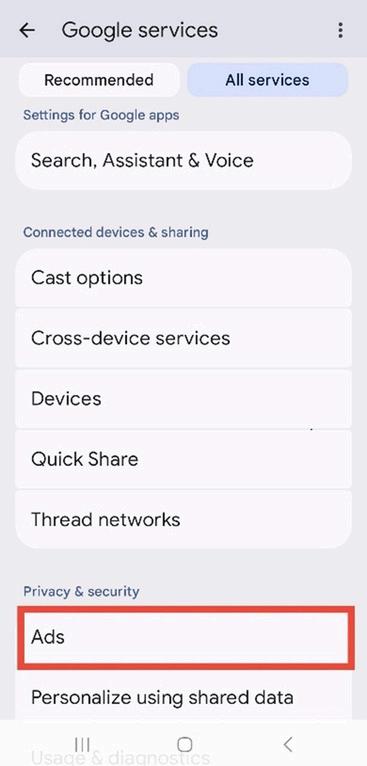
Figure 7.4: Google Services settings under “All services” with the “Ads” option highlighted.
11. In Ads, tap “Delete advertising ID.”
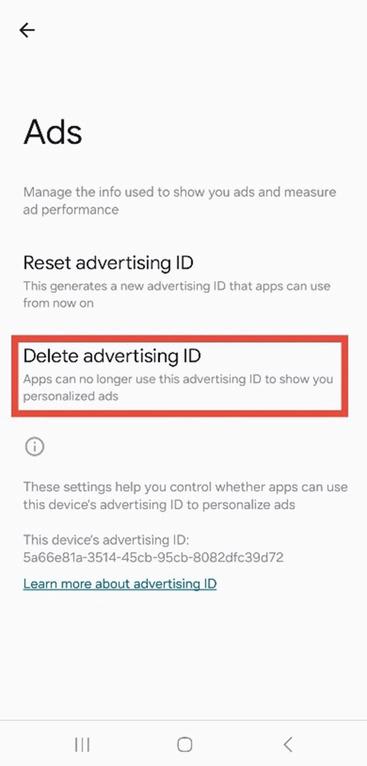
Figure 7 5: Google Ads settings showing the “Delete advertising ID” option
12. Delete Advertising ID and confirm deletion.
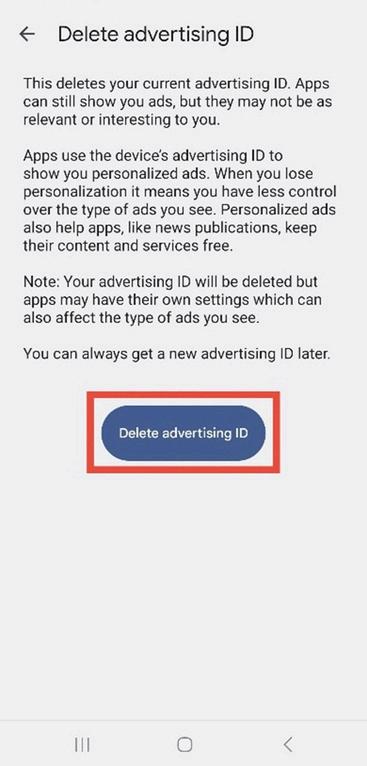
Figure 7.6: Confirmation screen for deleting the advertising ID with a blue “Delete advertising ID” button
H. Turn off Web & App Activity
1. Open the app drawer. Swipe up or open the app drawer icon to view all apps.

8 3: System Settings menu showing the “Google” option highlighted
2. Go to Settings. Tap Settings from the app list.

8 4: Google Services screen with user profile icon visible for accessing account management
3. In Settings, tap Google.

Figure 8 3: System Settings menu showing the “Google” option highlighted
4. Tap your Google account profile at the top, then select “Manage your Google Account.”

Figure 8.4: Google Services screen with user profile icon visible for accessing account management.
5. Navigate to Data & Privacy In your account settings, swipe to the Data & Privacy tab.
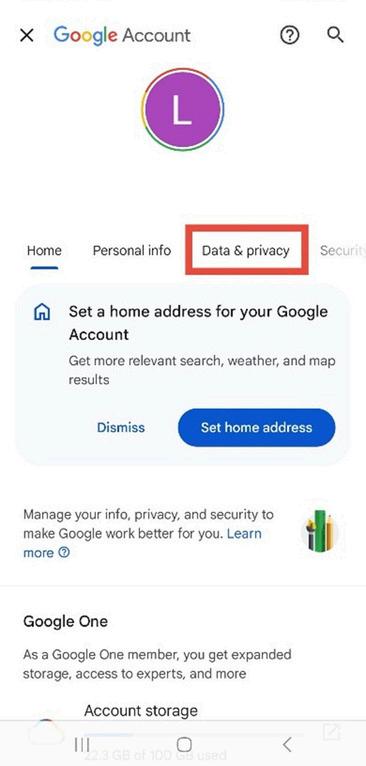
Figure 8 5: Google Account settings page with the “Data & privacy” tab highlighted
6. Turn off the following options: Web & App Activity Timeline
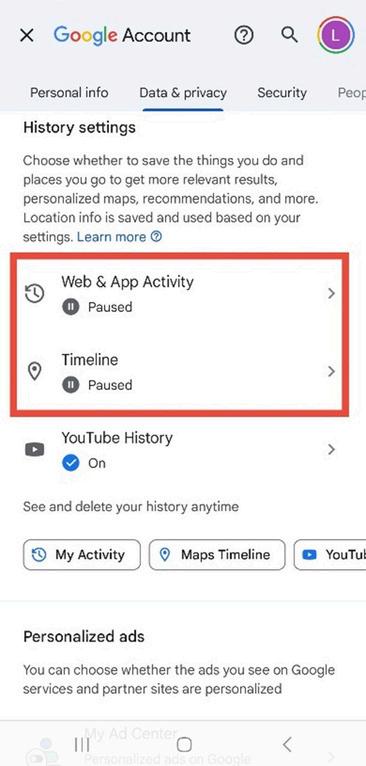
Figure 8.6: Account activity settings showing “Web & App Activity” and “Timeline” paused.
I. Turn off Usage & Diagnostics
1.Open the app drawer. Swipe up or open the app drawer icon to view all apps.

2. Go to Settings. Tap Settings from the app list.

3. Select Google. In settings, tap “Google.”

Figure 9 3: System Settings menu showing the “Google” option highlighted
4. Open Usage & Diagnostics and Turn It Off.
Scroll down and tap Usage & Diagnostics, then toggle the switch off to stop sending device data.
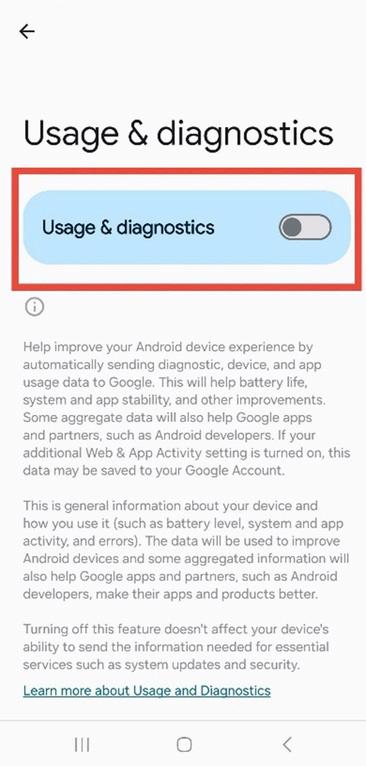
Figure 9 4: Usage & diagnostics settings with data sharing toggle turned off (switch turns grey)
5. Securing Your Phone
Most of these privacy protections can be set up right in your phone settings or within individual apps. Taking just a few minutes to adjust these options can make a significant difference in keeping your data private, especially in public spaces, or if your phone is ever lost or stolen.
A. Prevent Shoulder Surfing
Shoulder surfing is the act of secretly observing someone’s screen to steal sensitive information like passwords, PINS, etc [17]. To reduce shoulder surfing and unwanted access, implement the following measures:
Buy a privacy screen
Blocks side glances on public transportation or in crowded areas [18].
Mask lock screen notifications
Keeps sensitive content (e.g., texts or app alerts) hidden when the phone is face-up [19].
Set a short auto-lock timer
Ensures the phone locks itself quickly when idle and unattended, minimizing the window of opportunity for unauthorized access [19].
Lock sensitive apps with a passcode or Face ID
Biometric authentication such as FaceID or fingerprint adds a layer of security unique to you that’s harder to replicate [19].
B. Manage Location Permissions
Your location can reveal a lot about you. Where you live, work, or have your daily routines. Many apps ask for it even when they don’t need it. Here's how to stay in control:
Deny location access to non-essential apps
For example, mobile games typically do not need your location [20].
Enable “Ask Every Time” for occasional-use apps
Useful for delivery or ride-share apps that only need access when placing an order [21].
Allow continuous location only for critical apps
Apps like Maps or Find My Device may require ongoing access for accurate functionality [21].
Use “Approximate Location” when possible
Appropriate for weather apps and similar tools that only need general area information [21].
C. Disable Passive Listening
Many phones listen for wake words like “Hey Siri” or “Hey Google” by default, which means the mic is always on. To cut back on unnecessary listening:
Disable “Hey Siri” or “Hey Google”
Stops always-listening mics from triggering mid-conversation [19, 22].
Restrict microphone and camera access
Only allow access to apps with a clear, justifiable need.
Limit photo permissions to selected images
Instead of gaining fill library access, select only the images you wish to share.
D. App Permission Hygiene
Apps often ask for more access than they really need. Being strict here can protect you from oversharing information.
Block contact access for unnecessary apps
For instance, a flashlight or calculator app, should not request access to your contacts.
Select “Ask App Not to Track” (iOS) or “Disable Ad Personalization” (Android)
Prevents shopping applications from profiling activity across other applications.
Turn off personalized ads
Stops targeted ads based on recent searches and app history [22].
E. Limit Background Activity
Some applications and features remain on even when not in use, impacting both privacy and battery life.
Turn off Bluetooth when not in use
Avoids auto-connections and reduces tracking risks [23].
Disable background app refresh
Restricts apps from pulling data while idle, preserving battery and privacy [24].
F. Strengthen Overall Security
These final settings tie everything together and give your phone a strong security foundation. Enable two-factor authentication in your apps
Provides an important additional layer of protection beyond passwords.
Use a password manager
Stores complex passwords securely and discourages reuse or weak credentials [25].
Delete sensitive info from notes apps
Avoid storing sensitive information in unencrypted locations such as notes.
Activate lost device tracking and remote wipe options
Allows you to locate or securely erase your phone if lost or stolen [26].
Update your phone’s software promptly
Regular software updates and patches close security holes cybercriminals may exploit.
6. Good Habits
Practicing good digital habits helps maintain privacy and security over time, even when there is no immediate threat present. The following practices provided below will help increase your mobile safety and data protection:
Be picky about downloads: Only download apps from the official app store. Safe applications have high ratings by users, lots of downloads, and a known reputable developer. Pay attention to who the developer of the application is. Trustworthy developers usually have multiple apps with consistent branding and regular updates. Look for official names and pay attention to bad clones. Don’t install anything from sketchy links or random texts [23].
Use Wi-Fi with caution: Public Wi-Fi is convenient, but don’t log into sensitive accounts unless you’re using a trusted VPN or secure mobile data.
Watch your accounts: Turn on login alerts when possible and avoid reusing the same password everywhere. If one gets leaked, it limits the damage.
Back things up: Turn on automatic cloud backups for your photos and files. That way, if your phone gets lost or stolen, you won’t lose everything.
Clean up regularly: Delete apps you don’t use anymore and double-check app permissions, especially after big software updates.
Keep up with the news: Follow at least one solid tech news account or newsletter. Staying in the loop helps you spot new threats before they hit.
Works Cited
[1] Ibm (2025, June 10) What is mobile security? IBM https://www ibm com/think/topics/mobilesecurity
[2] Editor, C. C. (n.d.). Unauthorized access - glossary: CSRC. CSRC Content Editor. https://csrc.nist.gov/glossary/term/unauthorized access
[3] Spoofing and phishing | Federal Bureau of Investigation (n d ) https://www fbi gov/how-we-canhelp-you/scams-and-safety/common-frauds-and-scams/spoofing-and-phishing
[4] Zimperium (2025) 2025 global mobile threat Report pdf https://lp.zimperium.com/hubfs/Reports/2025%20Global%20Mobile%20Threat%20Report.pdf
[5] Agranovich, D., & Victory, R. (2022, October 7). Protecting people from malicious account compromise apps. Meta Newsroom. https://about.fb.com/news/2022/10/protecting-people-frommalicious-account-compromise-apps/
[6] Meyer, B (2025, April 28) These camera apps with billions of downloads might be stealing your data and infecting you with malware https://cybernews com/security/popular-camera-apps-steal-datainfect-malware/
[7] Forbes Magazine. (2024, October 15). The real risks of public wi-fi: Key statistics and usage data. Forbes. https://www.forbes.com/advisor/business/public-wifi-risks/
[8] Williams, K (2024, October 21) Why it’s time to take warnings about using public wi-fi, in places like airports, seriously CNBC https://www cnbc com/2024/09/29/its-time-to-take-warnings-about-usingairport-public-wi-fi-seriously html
[9] Love, B., Abbas, M. M., Ginther, S., & Flora, J. D. (2024, May 24). What are the cybersecurity risks associated with outdated software and operating systems?. Easy2Patch. https://www.easy2patch.com/blog/cybersecurity-risks-outdated-software-systems
[10] Manage application permissions for privacy and security: CISA Cybersecurity and Infrastructure Security Agency CISA (n d ) https://www cisa gov/resources-tools/training/manage-applicationpermissions-privacy-and-security
[11] What app permissions you should avoid giving. Nord Security. (n.d.). https://nordsecurity.com/blog/app-permissions-you-should-avoid-giving [12] J., H. (2024, October 3). Phone security: How to protect your phone from hackers. Prey. https://preyproject com/blog/phone-security-20-ways-to-secure-your-mobile-phone [13] Birchall, M (2025, March 27) What to dial to see if your phone is hacked: 9 useful codes Norton https://us norton com/blog/mobile/what-to-dial-to-see-if-your-phone-is-hacked [14] Ilevičius, P. (2023, January 12). How to know if your phone is hacked - 5 signs | nordvpn. NordVPN. https://nordvpn.com/blog/how-to-tell-if-your-phone-is-hacked/ [15] Ahuja, S. (2020, December 4). 45 digital and targeted advertising statistics. Grenis Media. https://www grenismedia com/blog/45-digital-and-targeted-advertising-statistics/ [16] Ullah, I , Boreli, R , & Kanhere, S S (2022, December 24) Privacy in targeted advertising on mobile devices: A survey International journal of information security https://pmc.ncbi.nlm.nih.gov/articles/PMC9789888/ [17] McAfee. (2024, January 4). What is shoulder surfing? https://www.mcafee.com/learn/what-isshoulder-surfing/ [18] Joshua, C (2025, May 6) Shoulder surfing: What it is and how to keep Prying eyes away LifeLock Official Site https://lifelock norton com/learn/identity-theft-resources/what-is-shoulder-surfing? srsltid=AfmBOorEpKaTCRowIzSatHcPUlM5q6iGQ68CBUkckmcDWWOBSnCxezzV
Works Cited
[19] National Security Agency | mobile device best practices (2020, October 20) https://media.defense.gov/2021/Sep/16/2002855921/-1/-1/0/MOBILE DEVICE BEST PRACTICES FIN AL V3%20-%20COPY.PDF
[20] Howell, G., Franklin, J. M., Shritapan, V., Souppaya, M., & Scarfone, K. (2023, May). Guidelines for managing the security of mobile devices in the 1] Ibm (2025, June 10) What is mobile security? IBM https://www ibm com/think/topics/mobile-security
[21] Chan, K (2025, February 6) One tech tip: How to block your phone from tracking your location AP News. https://apnews.com/article/tech-tip-disabling-phone-tracking33f6dedaa4c6f587a4049bceb87daadc
[22] (OCR), O. for C. R. (2022, June 29). Protecting the privacy and security of your health information when using your personal cell phone or tablet HHS gov https://www hhs gov/hipaa/forprofessionals/privacy/guidance/cell-phone-hipaa/index html
[23] CISA (2024, December 18) Mobile Communications Best Practice guidance https://www.cisa.gov/sites/default/files/2024-12/guidance-mobile-communications-best-practices.pdf
[24] Homeland Security | Office of Emergency Communications. (n.d.). Mobile device adoption best practices. CISA. 1] Ibm. (2025, June 10). What is mobile security?. IBM. https://www ibm com/think/topics/mobile-security
[25] Boeckl, K , Grayson, N , Howell, G , Lefkovitz, N , Ajmo, J , Eugene Craft, R , McGinnis, M , Sandlin, K , Slivina, O , Snyder, J , & Ward, P (2023, September) NIST Special Publication 1800-22 - Mobile device security. nist.gov. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.1800-22.pdf
[26] Arizona State University. (n.d.). Telecommuting, mobile and Travel Safety. Telecommuting, Mobile and Travel Safety | Get Protected. https://getprotected.asu.edu/policy-practices/telecommutingmobile-and-travel-safety
