Women

Harkins
(Security) Ethicist Proving ROI for Network Detection and Response NEW FEATURE Detecting Data Leaks from Use of ChatGPT New SEC Rules: Are You Ready? Q3, 2023 - ISSUE 01
Integrity Matters Malcolm
The
in Cyber
We're Following
by the Light
Cobalt Strike with ExtraHop Reveal(x)
Who
Blinded
Detecting
Integrity Matters, Malcolm Harkins: The (Security) Ethicist
Security Leaders Face Increasing Pressure to Downplay Cybersecurity Risks
by Grant Gross
Detect Data Leaks from Employee Use of ChatGPT
Protect Your Business from Generative AI Risks
by Meridith Levinson
Proving ROI for Network Detection and Response
How ExtraHop NDR Customers See 193% ROI from Reveal(x) 360
by Ferris Anwar
New SEC Rules: Are You Ready?
CISO Perspectives on Proposed SEC Cybersecurity Rules
by Paul Ditty
Women in Cyber: Who We're Following.
These Women Are Making Huge Contributions to Cybersecurity
by Grant Gross
Blinded by the Light
Detecting Cobalt Strike with ExtraHop Reveal(x)
 by Edward Wu, Jonathan Wrolstad and Ben Higgins
by Edward Wu, Jonathan Wrolstad and Ben Higgins
01
CONTENTS
FROM THE CEO
Security leaders are known for their integrity. They stand up for the truth, for what they believe is right, even if it comes at great personal cost. It’s a leadership trait I admire and try to hold myself to every day. It’s not always easy, but it’s the best way to build trust. Trust that’s vital to the success of any organization.

That’s why we made integrity the cover story for this inaugural issue of The CISO Review. We’re honored to share, on the pages that follow, a cautionary perspective on ethics and integrity from longtime CISO Malcolm Harkins. Malcolm believes security leaders are under more pressure than ever to compromise their integrity, and he reminds us all why integrity matters.
We’re also honored to share perspectives about the SEC’s new cyber risk governance and incident reporting rules from Jerry Perullo, the former CISO of Intercontinental Exchange and the New York Stock Exchange, and other security executives. The new SEC rules demonstrate the regulatory body’s commitment to building trust by providing investors with the truth about publicly traded companies’ cyber risk exposure.
Speaking of risk exposure, ExtraHop recently released a new capability designed to help organizations understand the scope of employee use of ChatGPT. You can read about it in this issue of The CISO Review.
We hope these stories–all curated from the ExtraHop blog–inspire you to lead a security culture based on seeking the truth about cyber risk and acting with integrity to build trust.
Patrick J. Dennis CEO, ExtraHop
 Peiter “Mudge” Zatko. Alex Stamos. Chris and Brian Krebs. Jen Easterly. Runa Sandvik.
Peiter “Mudge” Zatko. Alex Stamos. Chris and Brian Krebs. Jen Easterly. Runa Sandvik.
PJD
02
Integrity Matters
Malcolm Harkins: The (Security) Ethicist
 by Grant Gross
by Grant Gross
CISOs are always under pressure.
They’re under pressure to prevent data breaches and if one slips past, they usually take the fall for it.
They’re under pressure to keep their organizations secure without impeding business growth. They’re under pressure to keep costs down.
And now, with the SEC’s proposed enhancements to its cyber risk and incident disclosure rules, CISOs may face a new kind of pressure: pressure to downplay the cyber risks their organizations face.
Malcolm Harkins, the Chief Trust and Security Officer for Epiphany Systems (and former Intel CISO), says security leaders have faced this pressure for some time. In 2020, he surveyed more than 100 CISOs and found that 76% had felt pressure to under-report a cyber incident.
Harkins says this pressure is problematic for a number of reasons. For one, it can force CISOs to compromise their integrity and code of ethics. And succumbing to this pressure can have disastrous personal consequences for security leaders, not to mention far-reaching implications for their organizations, and even for customers who may be affected by an eventual data breach.
03
76% had felt pressure to under-report a cyber incident.
Don't Succumb. Speak the Truth.
However, there are a million, or perhaps 3 million, reasons not to capitulate, and instead, to speak the truth about cyber risk. Recently, the SEC reached a $3 million settlement with Blackbaud, a data management company, over charges that it misled investors about a 2020 ransomware attack. This appears to be the first SEC settlement related to a ransomware breach, although other companies have paid smaller fines for failing to report other types of breaches.
Blackbaud originally announced that attackers did not gain access to customer bank account data or Social Security numbers, and the SEC accused the company of not correcting those statements after its IT team found otherwise. The company also did not mention the breach in its next quarterly report to the SEC.
Harkins noted the settlement on LinkedIn, advising his peers to “make sure how you report risk is as accurate as possible and seek appropriate counsel if your organization seeks to modify (hintdilute) how the risks you are responsible for managing are characterized.”
Integrity Matters
For several years, Harkins has been on a mission to raise awareness about, and encourage, CISOs’ strong code of integrity. He encourages his peers to speak up when they face pressure to underplay cyber incidents–a disconcerting trend he doesn’t see subsiding.

When he’s shared the results of his 2020 survey with peers, he says he’s had “so many agree that they have experienced this pressure, so anecdotally, I think the numbers are relatively consistent.”
In an RSA Conference webcast from 2020, “Integrity Matters, and Things that Matter Aren’t Easy,” Harkins and other security professionals talked about ethical pressures on CISOs. He and three other security professionals “acknowledged that we could anticipate when the pressure was likely to arise—we could smell it, feel it like a sixth sense—and came to the conclusion that we need to trust and use our instincts to address ethical dilemmas earlier, to create enough space so that the right questions can be asked and the best solutions created,” he wrote at the time.
CISOs need to work with trusted peers to gain perspective on these dilemmas, he added.
“Ethical decision-making is a requirement of leadership, a deliberate commitment,” he wrote. “It is supposed to feel uncomfortable, and if it does not, then you are not doing it the right way.” </>
04
Reveal(x) Detects Data Leaks from Employee Use of ChatGPT
 by Meridith Levinson
by Meridith Levinson
Ever since OpenAI released ChatGPT on November 30, 2022, use of AI as a service (AIaaS), including generative AI tools, has skyrocketed. Within five days of launching, ChatGPT exceeded 1 million users. Two months later, it had 100 million users. By March, it boasted 1 billion. By comparison, it took TikTok eight years to reach 1 billion users.

It’s no wonder these tools have been, in large part, such a runaway success, what with the productivity improvements they promise (and deliver) for professionals across a range of occupations, from software development to pharmaceutical research.
And even though these tools are not well understood, many large enterprises that see the enormous potential of generative AI and AIaaS are committing significant resources to use it. According to Gartner® Research, Garter’s 2023 CIO and Technology Executive Survey showed that “nine out of 10 respondents (92%) ranked AI as the technology their organizations were most likely to implement by 2025.”
The downside? Beyond the ethical concerns, organizations using AIaaS tools have learned some hard lessons about data leaks and intellectual property (IP) risk after employees shared proprietary information with these public tools. What those employees using AI to accelerate code reviews and new drug discovery may not have realized is that they’re effectively putting confidential data in the public domain: once they share proprietary information with an AIaaS, the service continues to use it to process other people’s requests–in some cases, indefinitely, depending on the terms of the AIaaS provider.
05
The immediate IP risk centers on users logging into the websites and APIs of these generative AI solutions and sharing proprietary data. However, this risk increases as local deployments of these systems flourish and people start connecting them to each other. Once an AI service is determining what data to share with other AIs, the human oversight element that currently makes that determination is lost. The AI service is unlikely to understand the impact and potential consequences of sharing data it has access to and may not notify its human handlers that data has been shared outside of the organization.
Thus, the risk of IP loss and leakage of customer data has made it imperative for organizations to understand the scope of generative AI use across their businesses. Until now, organizations haven’t had an easy way to audit employee use and potential misuse of these tools.
Data Protection From Rogue AI Use and Accidental Misuse
Earlier this week, ExtraHop released a new capability that helps organizations understand their potential risk exposure from employee use of OpenAI ChatGPT.
ExtraHop Reveal(x) provides customers with visibility into the devices and users on their networks that are connecting to OpenAI domains. This capability is essential as organizations move quickly to adopt policies governing the use of large language models and generative AI tools, since it will give organizations a mechanism to audit compliance with those policies. We are taking this step as part of a larger security platform approach, incorporating the AIaaS monitoring with our existing, industry-leading network detection and response (NDR) capabilities.
By tracking which devices are connecting to OpenAI domains, identifying the users associated with those devices and the amount of data those devices are sending to those domains, Reveal(x) enables organizations to assess the risk associated with their users' ongoing use of AI services.
06
...the risk of IP loss and leakage of customer data has made it imperative for organizations to understand the scope of generative AI use across their businesses.
In addition, because Reveal(x) shows the amount of data being sent to and received from OpenAI domains, security leaders can evaluate what falls within an acceptable range and what indicates potential IP loss. For example, simple user queries to a chatbot should fall within a range of bytes to kilobytes. If security teams see MBs of data flowing to these domains, that volume may signify employees are sending proprietary data with their query.
Organizations will be able to identify the type of data and individual files that employees are sending to OpenAI domains if the traffic in question is not encrypted and Reveal(x) is able to identify related data exfiltration and data staging detections.
Reveal(x) is able to provide this deep visibility and real-time detection because we use network packets as the primary data source for monitoring and analysis. Using a real-time stream processor, Reveal(x) transforms unstructured packets into structured wire data and analyzes payloads and content from OSI Layer 2–7 for complete network visibility. From device discovery to behavioral analysis, network telemetry is the immutable source of truth for understanding an organization’s hybrid environment. Logs can tell you that two devices talked to each other, but Reveal(x) provides rich context about the communication.
At ExtraHop, we can’t underscore the importance of this capability as organizations grapple with the popularity and proliferation of AIaaS and the data leakage risk associated with it.
ExtraHop believes the productivity benefits of these tools outweigh the data exposure risks, provided organizations understand how these services will use their data (and how long they’ll retain it), and provided organizations not only implement policies governing use of these services but also have a control like Reveal(x) in place that allows them to assess policy compliance and spot risks in real time. </>
07
How ExtraHop NDR Customers See from Reveal(x) 360 193% ROI
by Ferris Anwar
Advanced threats have security teams under pressure to dramatically improve detection and response times, yet defenders have a limited number of new strategies and workflows they can use to proactively hunt for threats. Investing in new tools can help, but along with the pursuit of big returns, comes potentially high cost and risk.

To help organizations evaluate the potential return on investment from security technology, ExtraHop recently commissioned Forrester Consulting to conduct a Total Economic Impact™ Study of our cloudbased network detection and response solution (NDR), Reveal(x) 360.
As part of the study, Forrester interviewed Reveal(x) 360 customers, then aggregated quantitative and qualitative data on Reveal(x) 360 costs, benefits and risks from those interviews and other research sources to create a composite organization. From there, Forrester formed a financial model to represent the costs, risks and benefits incurred by adopting the technology, which forms the basis of their study.
The result is a thoroughly constructed, independently vetted, and unbiased look into the actual economic impact of a particular technology to help security leaders make informed purchasing decisions. In the case of ExtraHop Reveal(x) 360, Forrester determined that customers realized 193% ROI over three years.
Forrester TEI studies are important tools for organizations who need an accessible and unbiased way to evaluate the risk of new technology solutions, and Forrester has been successfully utilizing the TEI methodology for over two decades.
08
How to Evaluate ROI with Forrester Data
To offer a realistic assessment of potential value, the ExtraHop Reveal(x) 360 customers represented in the Forrester TEI study were diverse: They included large enterprises and different industries. Because security technology ROI can depend on a variety of factors including integration, end-user adoption, training, and organization size, the actual ROI companies receive may vary, but IT leaders can use Forrester TEI as a framework to help assess ROI and risk prior to adoption.
To help organizations gauge potential ROI, we'll break down Forrester's assessment in two key areas of cybersecurity: threat detection and remediation, and tool consolidation.
Assessing Potential NDR ROI Threat Detection and Resolution
To calculate the ROI, assess what toolsets your organization currently uses for network security and performance. Many organizations rely on a combination of perimeter solutions like firewalls and intrusion detection systems (IDS), agent-based detection from endpoint detection and response (EDR), log-based security information and event management (SIEM) systems, and basic packet capture (PCAP) tools for network visibility.
One commonly reported challenge associated with using all of these tools is too much data without context. This slows detection and response times, which can be extremely costly and adds risk. To assign a dollar value to response times for current toolsets, Forrester considers how many threats an organization detects and resolves, the time it takes, and the average hourly wage of IT staff.
To break down the math further, the Forrester TEI study assumes that the composite organization detects 40 threats per month, but larger or highly targeted industries including healthcare may see higher numbers. To get your own estimate of costs, multiply the average number of threats per month by the average number of hours it takes to detect threats, plus the hours it takes to remediate them. Next, factor in IT staffing costs to create this simple formula:
([Threats
x Detection Time] + [Threats x Remediation Time]) (Hourly Rate) = Current Cost
According to the TEI study, an organization saves 2.5 hours on detection, and 7 hours on remediation after adopting Reveal(x) 360, so by subtracting those assumed hours from your current averages and re-running the numbers, you'll have your assumed cost savings.
We should note, this calculation doesn't factor in false positives. The Forrester TEI study addresses this as a common issue, quoting one ExtraHop customer as saying, "We used to get thousands of alerts per day with no context, and we couldn't dig through them all because there were so many.
09
And of the ones we did look at, a lot of them were false positives. We're now getting closer to 150 alerts per day, and these are more targeted, so we can detect an issue faster and take action."
False positives are a huge waste of time and resources. For organizations considering NDR, we recommend assessing the number of false alerts the NDR solution produces and the time it takes to respond, multiplied by the average rate for a security analyst to get a sense of pre-adoption costs.
Tool Consolidation
The second way security teams see returns from NDR, and ExtraHop Reveal(x) 360 specifically, is in tool consolidation. Organizations interviewed by Forrester have used this strategy to realize six- and seven-figure savings. According to one IT leader, "we were able to decommission a few homegrown solutions and some network analytics sensors. We're also looking to retire some tools our operations team uses for visibility over the next year. This could lead to savings in the millions."
Among the common tool sets used as part of a network security strategy, some of these are arguably essential. SIEM and EDR, for example, are considered to be a part of the SOC visibility triad, along with NDR, and all three solutions can be integrated as part of a best-in-class XDR strategy.
To assess the value of tool consolidation, the math is fairly straightforward: Subtract the annual expense of decommissioned tools from the cost of NDR adoption. That said, the full number of tool sets that can be retired may not be fully understood until after adoption, but to offer a sense of how others have streamlined their tech stack, it helps to understand the two most commonly decommissioned tools:
Packet Capture (PCAP)
PCAP provides raw, detailed network data that is essential for visibility. It provides an unevadable source of truth, which is why many organizations use PCAP tools to store and analyze this rich dataset. In addition, PCAP data aids HIPAA and Executive Order 14028 compliance, among others.
PCAP on its own is extremely detailed, which means security teams have a vast amount of data to wade through for investigation or forensics. Not all NDR solutions work off of real-time, linerate packet data, but those that do (like ExtraHop) can easily replace PCAP. Packet data from NDR provides security teams with the context they need to detect threats and allows them to pinpoint the root cause right down to the packet level in a few clicks.
Intrusion Detection Systems (IDS)
IDS has been around in some form or another since the 1990s. Traditionally it uses signature-based detections to spot intrusions using known patterns. Among industry compliance standards, IDS is mentioned specifically in PCI DSS, making it another security staple.
10
However, IDS is a notorious source of false positives. In addition, its reliance on signature-based detection alone limits its capabilities and makes it easy for attackers to evade. In contrast, NDR can combine behavior-based and rules-based detections to spot more threats with more accuracy. This supports compliance, reduces SecOps workloads, and eliminates the need for legacy intrusion detection platforms.
A support analyst interviewed by Forrester explained how NDR allowed them to retire their legacy IDS solution: "We were able to consolidate tooling. Particularly, we were able to get rid of our IDS/ IPS solution once implementing our ExtraHop solution because it wasn't able to do as much for us as ExtraHop can in terms of pinpointing network and security issues."
Other Quantifiable and Unquantifiable Benefits
NDR as a Shared IT Resource
While NDR is primarily considered a security tool, the Forrester TEI study also addresses the benefits for the broader IT organization, including in resolving network performance and downtime. As a source of potential costs, Forrester's downtime calculations factor in remediation time, the number of endusers affected, and even lost revenue.
Cost savings from reduced end-user downtime are an example of a key unquantified benefit identified by Forrester: "Expanding usage to different teams." By sharing resources across security, compliance, and network optimization teams, NDR customers can see more value from a single tool. These benefits extend into improved communication, and even decision-making by leadership, according to Forrester.
One director of security explained the benefits of data sharing to Forrester: "Having a tool where we can all communicate has been key. If I see a threat, I am now able to communicate not only with the people who will be fixing it but also with management to say, 'This is my proof, this is what we're going after, this is what we're trying to lock down.' Reveal(x) 360 has been great for security maturity."
Visibility to Stop More Breaches
The biggest unquantified risk in our eyes is in network visibility. By adding coverage into cloud workloads, encrypted protocols, and all connected devices, NDR adopters are able to improve security hygiene and reduce their risk of a breach. As one technical director interviewed for the study explained, "The Reveal(x) 360 platform gathers a lot of information for us instantly. And with the ability to put our behavioral models and our intelligence models directly into the system and customize the risk scores that the system produces, we can much more quickly respond to things that we see as a greater degree of risk than without it. This definitely recused the deeper and more collateral damage that could occur and probably saves us millions." </>
11

Stay ahead of attackers. Stay Informed. Visit the ExtraHop blog to stay up to date on all things cybersecurity. extrahop.com/blog
CISO Perspectives on Proposed SEC Cybersecurity Rules
CISOs from NYSE, TransUnion, and SunLife weigh in on SEC incident reporting and cyber risk governance
by Paul Ditty
Last March, the U.S. Securities and Exchange Commission (SEC) proposed a series of rules to "enhance and standardize" publicly traded companies' disclosures about cyber incidents and their practices for managing and governing cybersecurity risk.
In their official document, the SEC proposes that registered companies adhere to the following:
• Disclose information on material cybersecurity incidents in their 8-K filings within four business days of identifying the incident's impact as material.
• Provide updates in their quarterly and annual reports (10-Qs and 10-Ks) on material cybersecurity incidents they previously disclosed in 8-Ks.
• Notify the SEC when previously undisclosed, immaterial cybersecurity incidents become material.
• Describe their policies and procedures for identifying and managing cybersecurity risks, including whether they have a CISO (or someone in an equivalent role), reporting relationships for the CISO, and whether they consider cybersecurity as part of their business strategy, financial planning, and capital allocation practices.

• Describe their boards of directors' and senior management team's expertise in assessing, managing and governing cybersecurity risk and in implementing cybersecurity policies, procedures and strategies.
The rule changes are intended to bring consistency to the way SEC registrants report on cyber risks and incidents, and to provide investors with information they can use to better assess an organization's overall risk profile. However, they've become a source of concern for both C-level leaders and corporate directors, not to mention a wellspring for debate. For cybersecurity practitioners, the central question is whether the proposed rules–which go into effect on April 1, 2023–will ultimately improve or undermine an organization's cybersecurity posture.
CISOs' views on the impact of the SEC's proposal vary. Some welcome it. Others urge caution. Here, we present highlights from public comments that several prominent CISOs filed with the SEC or posted to their LinkedIn profiles. We're grateful to these CISOs for the time they spent drafting these comments and for sharing their informed and experienced perspectives in the public interest.
13
What CISOs Are Saying About the SEC Cyber Rules

Jerry Perullo, the esteemed former CISO of IntercontinentalExchange (parent company of the New York Stock Exchange), lauded the SEC's proposed rules for their focus on driving "the right outcomes while avoiding over-prescription." In his detailed public comments, he offered reasonable and nuanced suggestions for implementing the incident disclosure and governance rules in a way that wouldn't arm threat actors with new details on registrants' vulnerabilities or specific security practices. He also advised the SEC to improve its examples of incidents that would merit disclosure and urged them to provide clarity on gray areas, like whether organizations would need to disclose a ransomware attack they successfully contained to a single or limited number of computers.
"The Commission has done well to focus on material cybersecurity incidents. Other authorities have flirted with the notion of incidents that merely present the potential of jeopardy, panicking industries recognizing a potentially limitless expanse of reportable events. Materiality has been core to the Commission's remit since the Securities Act of 1934, and it is wise to extend this notion—which preserves signal-to-noise ratio for the investing public—to cybersecurity." –Jerry Perullo, former CISO, IntercontinentalExchange
In his forceful public comments, Bill Shields, Executive Vice President and CISO at TransUnion, echoed concerns shared by many of his peers when he urged the SEC to better define "materiality" and give registrants more than four days after determining materiality to report an incident.
"That turnaround is simply too short to collect and present the necessary information accurately and will inevitably lead to mistakes that do the opposite of what the rule intends—disclosures will misdirect the Commission and investors, rather than provide clarity." –Bill Shields, EVP and CISO, TransUnion
Shields also cautioned the SEC against forcing companies to disclose too much information related to active and ongoing security investigations. "The interest of investors in transparency cannot override the need to effectively resolve an issue and prevent its recurrence, which itself is in the interest of not just one company's shareholders but the shareholders of any other company that may be under a similar threat."
14
Abhay Raman, SVP and CISO for Toronto, Ontario-based Sun Life Financial, noted the rigorous regulatory obligations around cyber risk management and incident reporting that publicly traded Canadian companies are required to meet, some of which are similar in spirit to the SEC's proposed rules and some of which go beyond. Due to Canadian regulatory authorities' strict requirements, Raman advised the SEC to continue allowing eligible Canadian foreign private issuers to follow their own domestic disclosure standards and documents to satisfy SEC requirements and to make compliance with SEC rules voluntary for Canadian filers.
"Not doing so," he wrote in his public comments, "would subject Canadian companies to additional incident reporting regimes that would distract critical resources with fulfilling reporting obligations rather than focusing on addressing a cybersecurity incident."
"We encourage the SEC to work closely with Canadian regulators to resolve any concerns with existing cybersecurity reporting regimes before imposing additional reporting requirements. Crossborder regulatory cooperation is a powerful tool to support regulators seeking to fulfill their mandate while also minimizing disruption to businesses." –Abhay Raman, SVP and CISO, SunLife Financial
Andrew Heighington, CISO at Visit.org and former information security leader at Bank of America, JP Morgan Chase, and the U.S. Department of Defense, researched the cyber governance practices of the fastest growing Fortune 1000 companies in 2022 to get a feel for their readiness to comply with the SEC's proposed rules. Among his findings:
• Only 36% met three of the SEC's criteria for cyber risk governance.
• 42% don't have a publicly named CISO or equivalent.
• 38% don't have a board committee designated to govern cyber risk.
"The lack of foundational cyber governance and leadership at many of these companies means it's highly unlikely there is agreement on the company's financial exposure to cyber risk, how much cyber risk the company is willing to accept, transfer, and reduce, what will constitute a material cyber incident to the business and trigger SEC reporting, and what cyber trends are emerging that the C-suite and Board need to be aware of as they craft their business strategy." –Andrew Heighington, CISO, Visit.org
It's so important for CISOs to weigh in on these rules since they'll be responsible for putting in place many of the systems, processes, policies and practices to enable their organizations to comply. The CISO community is fortunate to have such a deep bench of mission-driven practitioners. </>

15 CISO Perspectives on Proposed SEC Cybersecurity Rules (continued)
These Women Are Making Huge Contributions to Cybersecurity

On International Women’s Day, ExtraHop Salutes Several Women Who Are Making a Huge Mark on the Cybersecurity Industry
by Grant Gross
This year’s theme of the United Nations’ International Women’s Day, celebrated on March 8, is “DigitALL: Innovation and technology for gender equality.”
“From the earliest days of computing to the present age of virtual reality and artificial intelligence, women have made untold contributions to the digital world in which we increasingly live,” the U.N. says. “Their accomplishments have been against all odds, in a field that has historically neither welcomed nor appreciated them.”
Women made up less than 30 percent of the workforce in cybersecurity, according to an (ISC)2 cybersecurity workforce report, released in 2022. Thirty percent of the cybersecurity workforce under age 30 are women, but that number falls as the ages of workers go up, with only 12 percent of women making up cybersecurity workers ages 50 to 59.
All that said, many women have made–and continue to make–their mark in the cybersecurity industry. On this International Women's Day, we'd like to recognize a few women in the field who we’ve long followed and admired, for their significant contributions to the industry, their outspokenness, and for breaking glass ceilings. This list highlights just a small number of the many women we admire who are making a huge impact in the cybersecurity industry.
16
Marene Allison
recently retired as CISO at Johnson and Johnson. She’s a former FBI special agent and a graduate of the West Point Military Academy. She posts regularly on LinkedIn about cybersecurity topics and work issues. We salute Marene for her service and significant accomplishments.

Beth
Anne Bygum
is senior vice president, chief security and compliance officer at Acxiom and former senior director of information security strategy and portfolio management at McKesson, a health IT and pharmaceutical company. She’s active on LinkedIn.



Leslie Carhart
who uses they/them as personal pronouns, is director of incident response at cybersecurity company Dragos and a retired member of the U.S. Air Force Reserves. They post on Mastodon at @hacks4pancakes@ infosec.exchange, with a focus on infosec.
Emily
Crose
is principal industrial pentester at Dragos and a former U.S. intelligence officer. You can find her at @hexadecim8 on Twitter. She’s been tweeting recently about her new comic book series, “Our Lady Maven,” politics, and Elon Musk’s takeover of Twitter. She also shares knowledgeable tweets about information security.

Deneen DeFiore
is vice president and CISO at United Airlines and former senior vice president and global chief information and product security officer at GE Aviation. She’s active on LinkedIn and also on Twitter at @deneendefiore. She tweets about United Airlines, cybersecurity, women in cybersecurity, and the Santa Fe Saints college baseball team.
17
Jen Easterly
is director of the U.S. Cybersecurity and Infrastructure Security Agency and former head of firm resilience and the Fusion Resilience Center at Morgan Stanley. She’s also worked in the White House and at the National Security Agency. She’s active on LinkedIn and tweets at @CISAJen, where she gives advice on ways people and organizations can protect themselves against cybercriminals.
Renee Guttmann
is founder and principal of cybersecurity consulting firm Cisohive. She’s also former CISO at Campbell Soup Company, Royal Caribbean Cruises, Optiv, and Coca-Cola, and Time Warner. She’s active on LinkedIn and in the industry, where she frequently comments on cybersecurity topics.


Jadee Hanson
is CISO and CIO at cybersecurity provider Code 42. She has also served as senior director of information security at Target and as manager of enterprise risk services at Deloitte. She’s active on LinkedIn, where she often posts encouraging comments about the achievements of other people working in cybersecurity.



Meredith Harper
is senior vice president and CISO at financial services company Synchrony and a member of the board of directors at Berry Global Group. She previously served as vice president and CISO at Eli Lilly and Company and is passionate about increasing the numbers of women and minorities in tech and infosec. Listen to the Resilient podcast she did with Deborah Golden, Principal and U.S. Cyber and Strategic Risk Leader at Deloitte.
Siobhan MacDermott
is a partner at The Consello Group, a financial services advisory and strategic investing platform. She’s also served as CISO at Utilidata, an energy equipment and digital solutions company, and as global cyber public policy executive at Bank of America. She’s at @GlobalSiobhan on Twitter, where she talks about news and cultural issues, as well as cybersecurity.
18
Katie Moussouris
is founder and CEO of security company Luta Security and a creator of the bug bounty program at Microsoft. She also helped create the bug bounty program at the U.S. Department of Defense. She tweets at @k8em0, where she posts about cybersecurity (not surprisingly), women’s issues, and the intersection of the two, along with a host of other fascinating topics. She’s an advocate for pay equity and has been using her Twitter account this month to draw attention to women’s contributions to business, technology, law, politics and other disciplines. She’s also active on Mastodon. If you’re not following her, you need to.

Wendy Nather
serves as Head of Advisory CISOs at Cisco and previously held a similar position with Duo Security, which was acquired by Cisco in 2018. She worked for many years in the financial services industry as an information security director, and is known for coining the term “security poverty line” while serving as a research director with 451 Research.



Vanessa Pegueros
is on the boards of Forterra, the Northwest chapter of the National Association of Corporate Directors (NACD), Presidio, LivePerson and Boeing Employee Federal Credit Union (BECU). She previously served on the board of directors for Carbon Black and served as chief trust and security officer at OneLogin. Like Meredith Harper, Vanessa was also a guest on the Deloitte Resilient podcast, talking about mental health and burnout in cybersecurity.
</>
® FOLLOW ON
DETECTING COBALT STRIKE
with ExtraHop Reveal(x)
by Edward Wu, Jonathan Wrolstad, and Ben Higgins
In November 2022, members of the ExtraHop Detections Research and Data Science teams picked up on a device in an organization’s network environment that was making suspicious outbound connections to a confirmed Cobalt Strike command and control (C2) server.

Cobalt Strike is a legitimate penetration testing and attack simulation platform used by red teams, but over the past three to four years threat actors including Cozy Bear and the Conti, Black Basta, and Royal ransomware gangs have used it as a tool in their arsenal. Specifically, they deploy Cobalt Strike to establish communications with a C2 server once they’ve gained access to an organization’s environment. Attacks leveraging Cobalt Strike frequently foreshadow ransomware.
The C2 communications that we detected in early November using the ExtraHop Reveal(x) network detection and response (NDR) platform, combined with other data and threat intelligence sources, strongly suggested that a malicious actor had breached the organization’s perimeter defenses and was potentially looking to take a number of actions, including network reconnaissance, lateral movement, and credential theft–with the possible intent to deploy ransomware and/or exfiltrate data.
In this threat analysis report, we share our findings and detection methodology to help cybersecurity practitioners identify Cobalt Strike in their environments. We also describe how we discovered the malicious activity using ExtraHop Reveal(x), and we explain the benefits and impact of detecting this attack in its early stages.
20
Threat Analyisis:
The Detection
On November 9, 2022, an ExtraHop Reveal(x) sensor monitoring an organization’s network picked up on unusual traffic patterns coming from an internal device (later identified as an employee laptop) that was making suspicious outbound connections to an external device with the IP address 194.165.16.90.
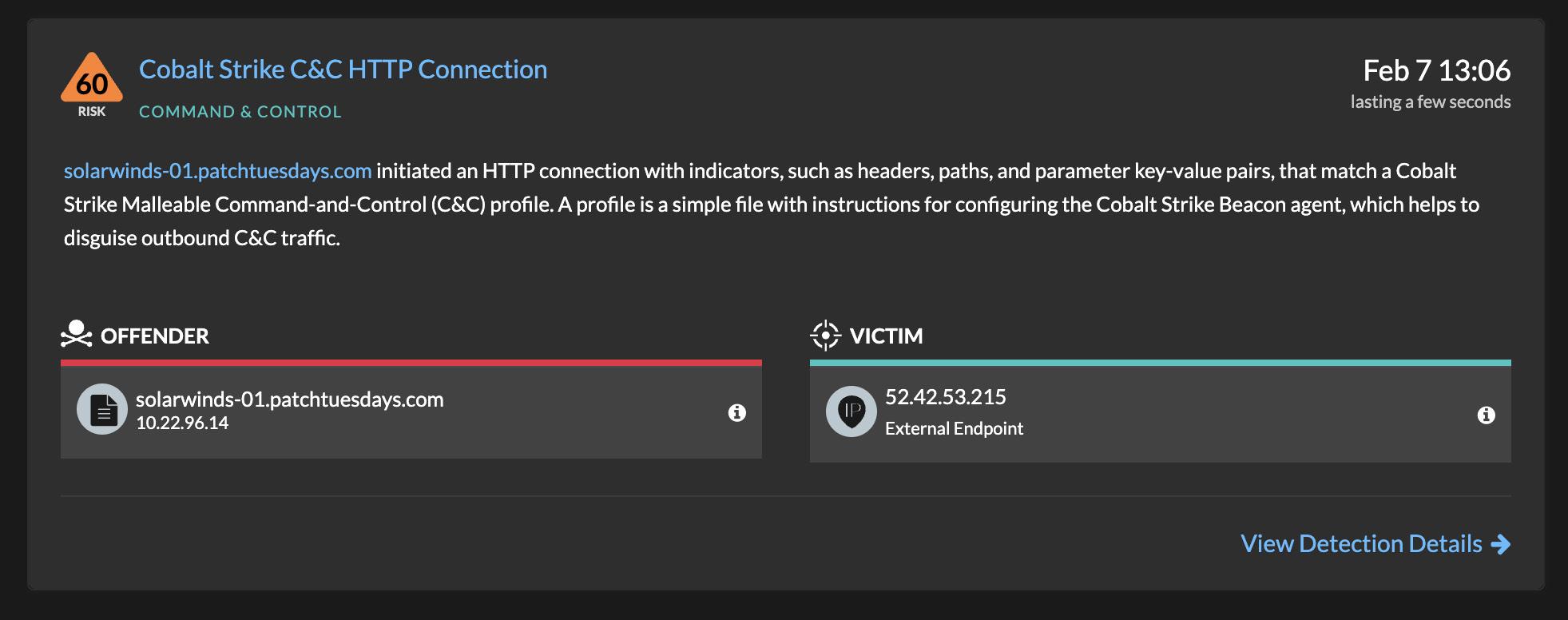

According to Censys, the external device had ports 22 (SSH), 53 (DNS), and 80, 443, 8080, and 8888 (all plain text HTTP) open. We noted that ports 80 and 8080, which usually communicate over plain text HTTP, were in this case using HTTPS to communicate with the internal device on the organization’s network, which was unusual.
The most convincing evidence came from our proprietary fingerprinting method, which the ExtraHop Threat Research team runs constantly against the internet and which flagged the external IP address as suspicious. Our fingerprinting method for detecting Cobalt Strike C2 servers probed ports 80, 443, 8080, and 8888, and all came back with a positive result. Furthermore, we knew the external IP address was hosting a Cobalt Strike C2 server because one of our researchers was able to download a beacon from it. Our beacon analysis suggested the downloads did not come from a legitimate, licensed copy of Cobalt Strike. Had the beacons come from a legitimate copy of the software, it would have been a stronger indication of red team usage, but in this case, because the beacons appeared to come from an unlicensed copy, it increased the likelihood that a malicious actor was using these tools rather than a red team.
21
The automated detection from Reveal(x), combined with our own active probing as well as internal and external threat intelligence sources, indicated the IP address belonged to an external device hosting a Cobalt Strike C2 server, and therefore, signaled a high-fidelity alert about a potentially very serious and fast-moving attack.
The Attack Chain
ExtraHop contacted the organization about the detection, and the organization was then able to identify how the threat actor gained initial access: an end user who was logged into the organization’s network via a VPN received a phishing email with an HTML file. The end user clicked on the file, which triggered a malicious executable–several strong signals indicated it was likely Qakbot–to immediately download on the user’s machine. Qakbot (also known as Quakbot and QBot) allows attackers to conduct network reconnaissance, move laterally, and deliver payloads such as Cobalt Strike and Conti, ProLock and Egregor Ransomware. In this case, Qakbot led to the delivery of Cobalt Strike, which then established a link to a C2 server the very next day, signaling an attack that was likely to progress rapidly and likely to conclude with ransomware.
22
1
End user receives a phishing email with a malicious HTML file attached.
2
End user clicks file and it downloads onto their laptop.
3
Malicious file installs Cobalt Strike beacon on end user’s computer.
4
Cobalt Strike beacon begins communicating with an external device with the IP address 194.165.16.90.
5
ExtraHop Reveal(x) sensor picks up unusual traffic patterns coming from end user’s laptop.
6 MALICIOUS ACTIVITY DETECTED
ExtraHop confirms communication to a Cobalt Strike C2 server.
MITRE ATT&CK Tactics and Techniques Used in This Attack
It is important to note that there were a number of significant security controls these sophisticated, stealthy attack tools managed to circumvent:
• VPN
• Firewall
• Intrusion Detection System (IDS)
• Email security
• Anti-virus software
The visibility that ExtraHop Reveal(x) provided into full network activity allowed us to quickly detect malicious behavior. The early detection then allowed the organization to stop an attack that was likely to progress rapidly and conclude with ransomware and/or data exfiltration scenarios.
Tactic
TA0001: Initial Access
TA00011: Command and Control
Technique/Sub-Technique
T1566: Phishing
T1071.001: Application Layer Protocols: Web Protocols
TA00011: Command and Control
TA0003: Persistence
TA0005: Defense Evasion
TA00011: Command and Control
T1071.004: Application Layer Protocols: DNS
T1197: BITS Jobs
TA00011: Command and Control
TA00011: Command and Control
T1132.001: Data Encoding: Standard Encoding
T1001.003: Data Obfuscation: Protocol Protocol Impersonation
T1568.002: Dynamic Resolution: Domain Generation Algorithms
TA00011: Command and Control T1572: Protocol Tunneling
TA00011: Command and Control
T1573.001: Encrypted Channel: Symmetric Cryptography
TA0007: Discovery
TA0008: Lateral Movement
TA0007: Discovery
TA0011: Command and Control
T1046: Network Service Discovery
T1210: Exploitation of Remote Services
T1135: Network Share Discovery
T1095: Non-Application Layer Protocol
23
Containment and Remediation
When the organization became aware of the outgoing connections, its security team took a number of steps to contain and remediate the compromise, including disconnecting the affected device from the internet, changing account passwords and access control credentials, quarantining the device from the network, and removing the malware. The security team then assessed the scope of the compromise, eliminated the attacker’s presence, blocked access, closed attack vectors, and updated and augmented security controls to prevent similar future compromises. The organization also continued to use ExtraHop Reveal(x) to monitor the network for suspicious behavior.
Evasive Malware Requires Powerful Network Detection
Cobalt Strike has become a powerful adversarial tool because it delivers a full range of post-exploit capabilities via a single, integrated system and also because it employs so many techniques to evade detection. For example, Cobalt Strike can imitate the HTTP protocol for C2 communication while hiding the actual data in either an HTTP header, URI parameter, the transaction body, or appending it to the URI. Cobalt Strike can break large data sets into smaller chunks so as not to trigger data loss prevention systems during exfiltration. Cobalt Strike can encrypt task commands, shell code, configuration data, and data being sent to a C2 server. It can use custom C2 protocols that can be encapsulated in HTTP, HTTPs, and DNS, even as those custom protocols use their standard assigned ports, and it can do much, much more.
That’s why attacks leveraging Cobalt Strike tend to be serious. It’s also why organizations need NDR. Only NDR–and more specifically, Reveal(x) 360–can detect the highly covert, super subversive, network-level techniques attackers use to fly under the radar. We build behavior-based detections for Cobalt Strike and other tools that catch the most subtle activities.
Even if it’s your last line of defense against sophisticated threat actors, ExtraHop Reveal(x) can still help you detect their attacks before IDS, AV, EDR and SIEM and before they lead to business impact.
AUTHORS:
Edward Wu, Former Senior Principal Scientist, ExtraHop
Jonathan Wrolstad, Senior Manager, Engineering and Threat Intelligence, ExtraHop
Ben Higgins, Software Architect, ExtraHop
</> 24
Reveal(x)
Network Detection & Response
Reveal the Unknown. Unmask the Attack.


 by Edward Wu, Jonathan Wrolstad and Ben Higgins
by Edward Wu, Jonathan Wrolstad and Ben Higgins

 Peiter “Mudge” Zatko. Alex Stamos. Chris and Brian Krebs. Jen Easterly. Runa Sandvik.
Peiter “Mudge” Zatko. Alex Stamos. Chris and Brian Krebs. Jen Easterly. Runa Sandvik.

 by Grant Gross
by Grant Gross
 by Meridith Levinson
by Meridith Levinson
























