CompTIAPenTest+CertificationAllinOneExam Guide(ExamPT0001)(EbookPDF)

https://ebookmass.com/product/comptia-pentest-certificationall-in-one-exam-guide-exam-pt0-001-ebook-pdf/

Instant digital products (PDF, ePub, MOBI) ready for you
Download now and discover formats that fit your needs...
CompTIA PenTest+ Certification All-in-One Exam Guide (Exam PT0-001) 1st Edition
https://ebookmass.com/product/comptia-pentest-certification-all-inone-exam-guide-exam-pt0-001-1st-edition/
ebookmass.com
CompTIA PenTest+ Certification All-in-One Exam Guide, Second Edition (Exam PT0-002), 2nd Edition Raymond Nutting
https://ebookmass.com/product/comptia-pentest-certification-all-inone-exam-guide-second-edition-exam-pt0-002-2nd-edition-raymondnutting/
ebookmass.com
CompTIA PenTest+ Certification All-in-One Exam Guide, Second Edition (Exam PT0-002), 2nd Edition Heather Linn
https://ebookmass.com/product/comptia-pentest-certification-all-inone-exam-guide-second-edition-exam-pt0-002-2nd-edition-heather-linn/
ebookmass.com
Instructor Manual For Essentials of Negotiation 5th
Edition by Roy Lewicki , Bruce Barry , David Saunders
https://ebookmass.com/product/instructor-manual-for-essentials-ofnegotiation-5th-edition-by-roy-lewicki-bruce-barry-david-saunders/
ebookmass.com




Exploring philosophy: an introductory anthology 6th ed Edition Cahn
https://ebookmass.com/product/exploring-philosophy-an-introductoryanthology-6th-ed-edition-cahn/
ebookmass.com
Italian Verb Drills, 4th Ed 4th Edition Paola Nanni-Tate

https://ebookmass.com/product/italian-verb-drills-4th-ed-4th-editionpaola-nanni-tate/
ebookmass.com
Mapping Violeta Parra’s Cultural Landscapes 1st Edition Patricia Vilches (Eds.)
https://ebookmass.com/product/mapping-violeta-parras-culturallandscapes-1st-edition-patricia-vilches-eds/
ebookmass.com
Improving Public Opinion Surveys Mcgraw
https://ebookmass.com/product/improving-public-opinion-surveys-mcgraw/
ebookmass.com
Psychonauts• psychedelics: A systematic, multilingual, web-crawling exercise Valeria Catalani & John Martin
Corkery & Amira Guirguis & Flavia Napoletano & Davide Arillotta & Caroline Zangani & Alessandro Vento & Fabrizio Schifano
https://ebookmass.com/product/psychonauts-psychedelics-a-systematicmultilingual-web-crawling-exercise-valeria-catalani-john-martincorkery-amira-guirguis-flavia-napoletano-davide-arillotta-carolinezangani/ ebookmass.com




https://ebookmass.com/product/public-relations-cases-9th-editionebook-pdf/
ebookmass.com


CONTENTS
Acknowledgments
Introduction
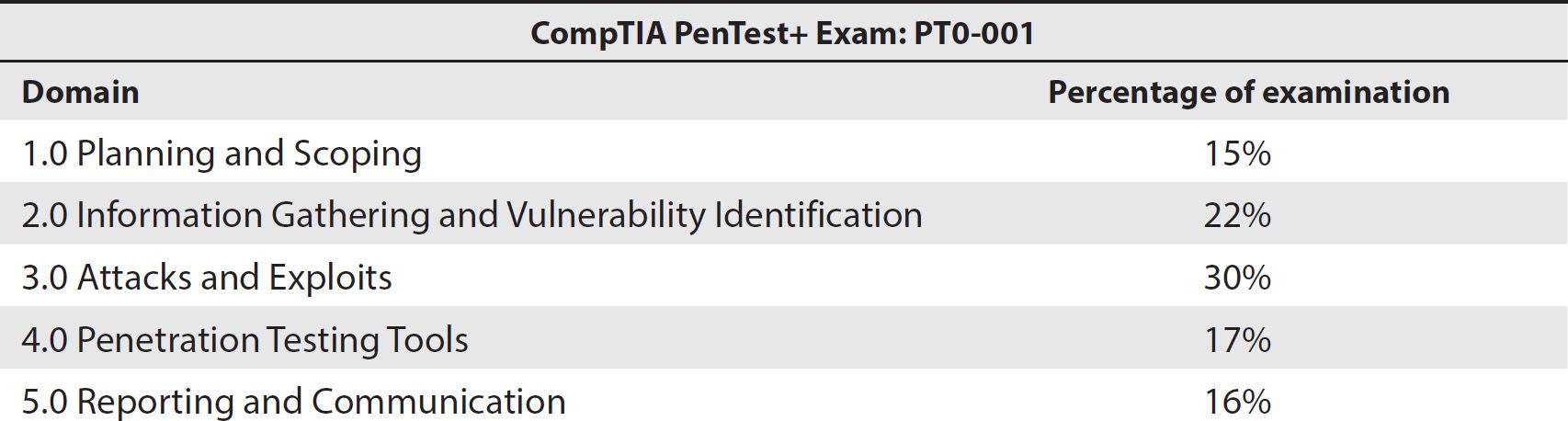
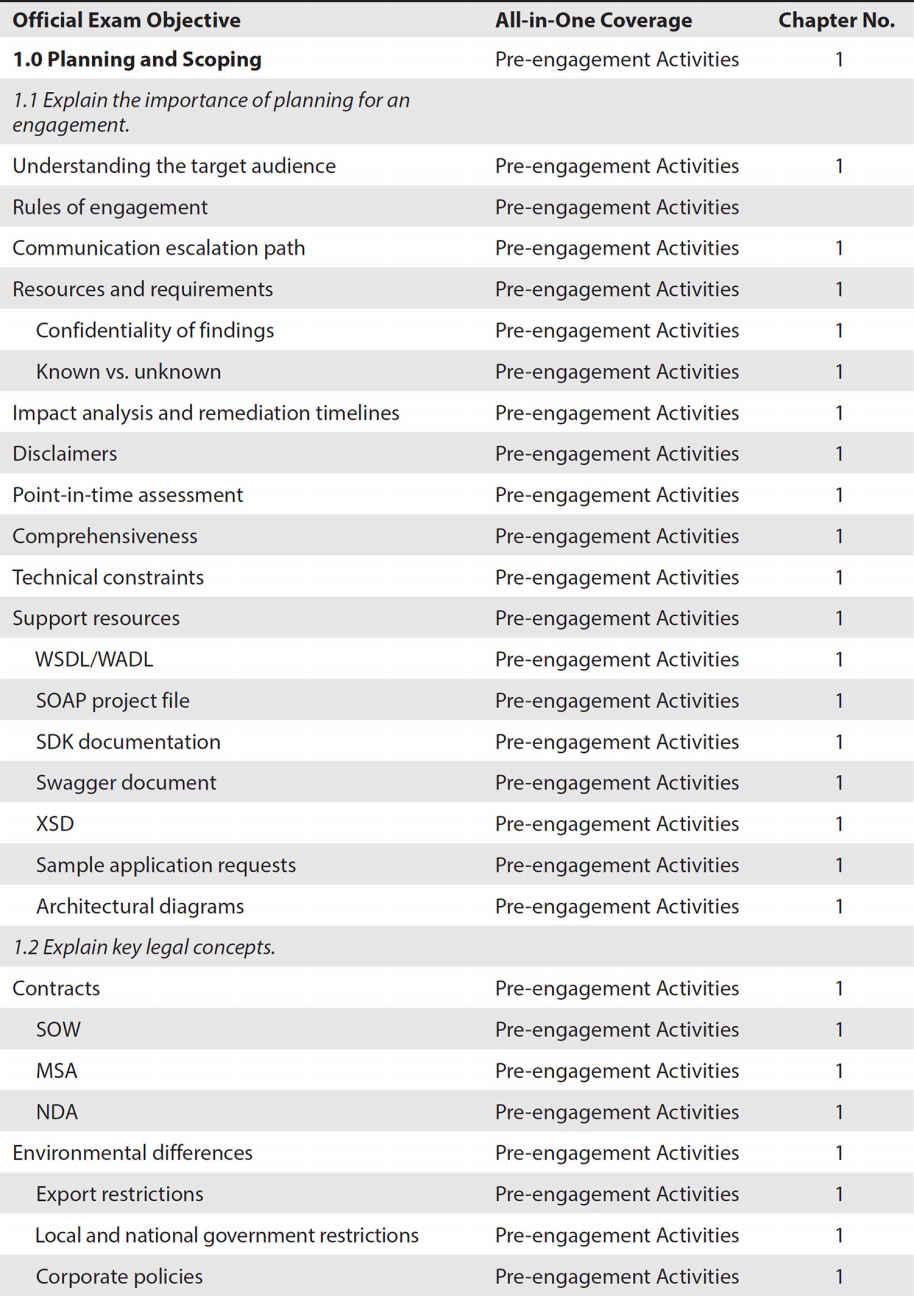
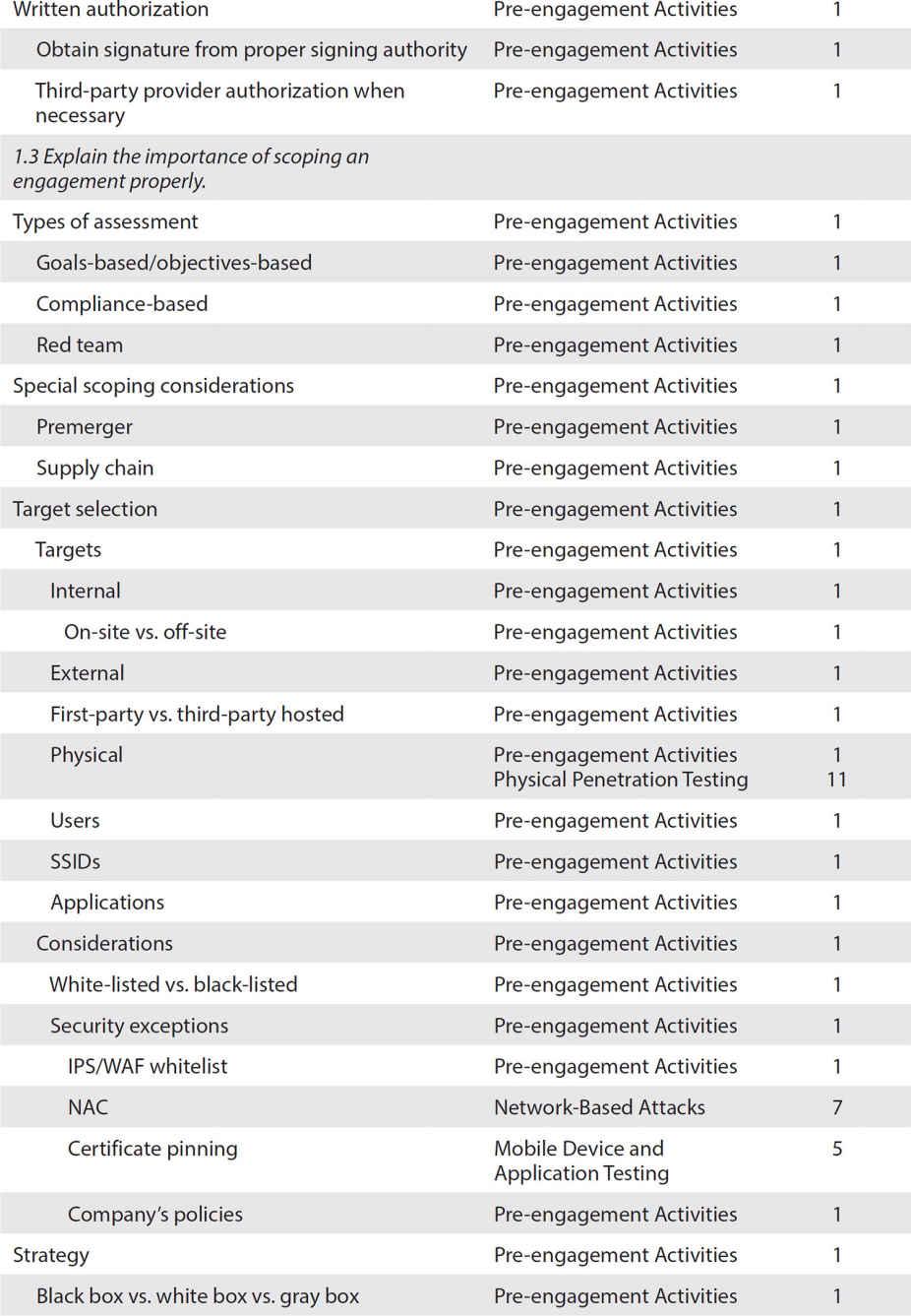
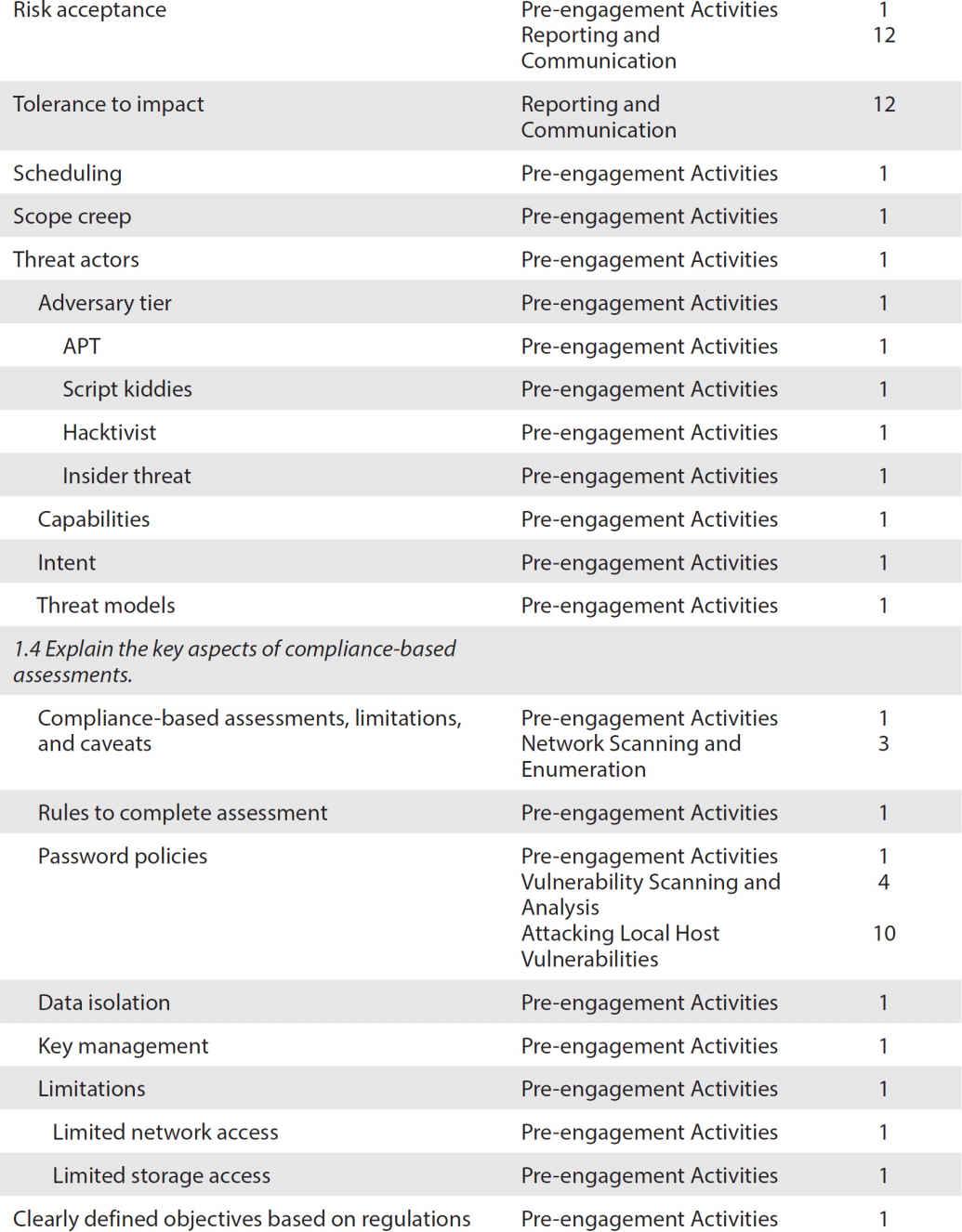
ObjectiveMap: Exam PT0-001
Chapter1Pre-engagement Activities
Target Audience
Impact Analysis
ScopeandMethodology
Typesof Assessment
Threat Modeling
Target Selection
Contractual Agreements
NondisclosureAgreement
Master ServiceAgreement
Statement of Work
Chapter Review
Questions
QuestionsandAnswers
Chapter2GettingtoKnowYour Targets
FootprintingandReconnaissance
InformationGathering
Tools,Methods,andFrameworks
DataMining
SpecializedSearchEngines
DNS,Website,andEmail Footprinting
MetadataAnalysis
Chapter Review
Questions
QuestionsandAnswers
Chapter3NetworkScanningandEnumeration
802.11WirelessStandards
WirelessSpectrum Bands
WirelessModesandTerminology
WirelessTestingEquipment
Popular Antennas
802.11NetworkDiscovery
802.11Frames
WirelessScanning
Host Discovery
PingScan
Port Scanning
Port ScanningMethods
CommonPortsandProtocols
TCPScan
Half-OpenScan
UDPScan
Enumeration
Chapter Review
Questions
QuestionsandAnswers
Chapter4VulnerabilityScanningandAnalysis
ResearchingVulnerabilities
CVE
CWE
CAPEC
ATT&CK
RemoteSecurityScanning
Credentialedvs.NoncredentialedScanning
ComplianceandConfigurationAuditing
Nontraditional Assets
WebandDatabaseScanning
OpenWebApplicationSecurityProject (OWASP)
FingerprintingWebandDatabaseServers
EnumeratingInformation
AuthenticationandAuthorizationTesting
DataValidationTesting
VulnerabilityMapping
Chapter Review
Questions
QuestionsandAnswers
Chapter5MobileDeviceandApplicationTesting
MobileDeviceArchitecture
iPhoneOperatingSystem
AndroidOperatingSystem
MobilePentestingFundamentals
StaticAnalysis
DynamicandRuntimeAnalysis
NetworkAnalysis
Server-SideTesting
iOSApplicationSecurityTesting
SettingUpaniOSTestingEnvironment
JailbreakinganiOSDevice
ConnectingtotheiOSDevice
iOSFunctional TestingandApplicationMapping
AndroidApplicationSecurityTesting
SettingUpanAndroidTestingEnvironment
RootinganAndroidDevice
ConnectingtotheAndroidDevice
AndroidFunctional TestingandApplicationMapping
SoftwareAssuranceTesting
UnderstandingProgrammingLogic
Chapter Review
Questions
QuestionsandAnswers
Chapter6Social Engineering
MotivationTechniques
Social EngineeringAttacks
Phishing
Email-Based
Phone-Based
Countermeasures
Chapter Review
Questions
QuestionsandAnswers
Chapter7Network-BasedAttacks
NameResolutionExploits
DNSSpoofingandCachePoisoning
AttackingLLMNRandNetBIOS
StressTestingApplicationsandProtocols
Denial of ServiceAttacks
ExecutingDDoSAttacks
NetworkPacket Manipulation
AnalyzingandInspectingPackets
ForgeandDecodePackets
Layer-2Attacks
AttackingtheSpanningTreeProtocol
VLANHopping
BypassingNetworkAccessControls
AttackingCommonProtocols
ExploitingSNMPv1
PoorlyConfiguredFileSharing
AbusingSMTP
Chapter Review
Questions
QuestionsandAnswers
Chapter8WirelessandRFAttacks
WirelessEncryptionStandards
SettingUpaWirelessTestingLab
CrackingWEP
Wi-Fi ProtectedAccess(WPA)
CrackingWPS
WirelessAttacksandExploitation
Man-in-the-MiddleAttacks
AttackingBluetooth
Chapter Review
Questions
QuestionsandAnswers
Chapter9WebandDatabaseAttacks
Server-SideAttacks
InjectionAttacks
AttackingAuthenticationandSessionManagement
InclusionAttacks
ExploitingSecurityMisconfigurations
Client-SideAttacks
HTMLInjection
Cross-SiteScripting
Cross-SiteRequest Forgery
Clickjacking
Chapter Review
Questions
QuestionsandAnswers
Chapter10AttackingLocal Host Vulnerabilities
OSVulnerabilities
Postexploitation
GainSituational Awareness
CollectingInformation
Exfiltration
PrivilegeEscalation
LinuxPrivilegeEscalation
WindowsPrivilegeEscalation
ExploitableServices
Buffer Overflows
UnquotedServicePaths
Lateral Movement
Lateral Movement inLinux
Lateral Movement inWindows
MaintainingPersistence
CoveringYour Tracks
ClearingCommandHistory
Timestomping
FileDeletion
Chapter Review
Questions
QuestionsandAnswers
Chapter11Physical PenetrationTesting
KeepingtheHonest PeopleHonest
Environmental Threats
Physical andEnvironmental Protection
Physical LocksandSecurity
Mechanical Locks
BasicToolsandOpeningTechniques
AlarmsandEarlyWarningSystems
Physical DeviceSecurity
ColdBoot Attack
BIOSAttacks
USBKeylogger
Chapter Review
Questions
QuestionsandAnswers
Chapter12ReportingandCommunication
WritingthePentest Report
DraftingtheReport
Postengagement Cleanup
Report Handling
Post-Report DeliveryActivities
Customer Debriefing
Follow-UpActions
CommunicationIsKey
Chapter Review
Questions
QuestionsandAnswers
AppendixAbout theOnlineContent
Glossary
Index