

SCOTSOFT2026
24.09.2026 Edinburgh create. innovate. collaborate.
Join us in Scotland for ScotSoft 2026 with the world’s brightest tech minds to explore the future of digital innovation.
This internationally recognised event offers visionary speakers, cutting-edge insights and unparalleled networking opportunities in one of Europe’s most vibrant tech ecosystems.
“Scotsoft has for many years been the leading technology event in Scotland, The combination of excellence speaks for itself, the interaction of Scottish Cyber capability is exceptional, meeting all manor of industry leaders and future leaders is what sets it apart.”

-Thomas McCarthy, MD, OSP Cyber




Dear Reader
As we head to our 18th edition of Cyber News Global, we will be attending AICS 3rd Edition in Bahrain 2025, the 45th edition, NCSC Bahrain continues build its cyber resilience with continued collaboration with its partner countries within the GCC. With this focus comes great opportunity to collaborate where capability is required, DEFCON will make its first visit to the GCC in collaboration with NCSC Bahrain, AI Village, Cloud Village, ICS Village will be just a few focused areas to build and understand capability.
Capture the flag will be front and centre and the AICS Cyber Escape Room experience will be delivered by UK Cyber Experts OSP Cyber Academy.
Global experts will come together to share knowledge, capability, and experiences to help shape the future of Cyber security and the advancements of AI and Quantum.
Cyber News Global will be there to capture every opportunity that will be presented, we will meet the experts, hear their views and share their ideas, this is the start of something truly extraordinary, we have the entire Bahrain Cyber eco system to thank for such events as AICS, truly a world leading event.
With the advancements in AI and its use being embraced so widely, it’s no surprise that AI Governance has become a critical process to ensure that everyone understands their responsibility when utilising AI to expand their capability.
Quantum computing plans to revolutionise industry like never before, once again the Bahrain NCSC has taken a huge bold leap to host two Quantum Ready Workshops delivered by Cystel Quantum one of the World’s leading authorities in delivering Quantum safely and progressively.
By Stuart Harwood, Head of Business Development at Siker Cyber


So dear readers, don’t loose sleep, know that there is an army of cyber and AI warriors out there looking at the future.

of Cyber Threats in CNI

As critical systems become more integrated and reliant on digital technologies, they become more susceptible to cyberattacks. “The landscape has changed dramatically in the last decade. We are now far more dependent on digital systems, which have attracted adversaries looking to exploit vulnerabilities,
“The interconnectedness of modern systems means that a vulnerability in one part of the supply chain can create cascading risks across the entire infrastructure. Organizations need to be proactive in securing



In addressing these challenges, Stuart emphasizes the importance
“At Siker Cyber, we focus not only on the technological systems themselves but also on equipping personnel with the skills necessary
This workforce development is a key component of Siker Cyber’s comprehensive approach to improving cybersecurity resilience within organizations.One example of this approach in action is a strategic partnership between Siker Cyber and a major energy provider. The goal was to enhance the company’s cybersecurity
“We


Critical National Infrasructure - Stuart Harwood
The Human Side of Cyber security- Ben Owen
The Quantum ReckoningDr Meera Sarma
- Irene Coyle



















Cyber
for Public & Private school students in bahrain

AGENT AGENT AMENA AMENA AGENT AMENA



















AGENT AGENT AMEEN AMEEN AGENT AMEEN























































Courses Produced by osp cyber academy on behalf of NCSC bahrain

Expanding into the Middle East.

OSP Cyber Academy, a globally recognised UK NCSC-accredited leader in cyber security awareness training, have announced a strategic partnership with Bahrain’s National Cyber Security Centre (NCSC) to deliver cyber safety education to 70,000 students across the Kingdom.
The partnership introduces culturally tailored, gamified cyber awareness courses designed to enhance student’s understanding of digital citizenship and cyber security best practices. There are a total of four interactive courses that have been developed to provide dedicated cyber awareness training for 70,000 children, tailored to age groups 6–8, 9–11, 12–14, and 15–17.
The courses feature avatars of both a boy and a girl guiding learners through real-world online safety scenarios set against digital environments inspired by key Bahraini landmarks.
With engaging question prompts and interactive learning, the platform ensures high knowledge retention in a fun and relatable way.


This initiative is launched in collaboration with His Excellency Sheikh Salman bin Mohammed AlKhalifa, CEO of NCSC Bahrain, and builds upon OSP Cyber Academy’s longstanding engagement with the Kingdom.
OSP Cyber Academy hosts the UK pavilion at the Arab International Cyber Security Summit (AICS) in Bahrain every year, and it also achieved a Guinness World Record at the event in 2023 for the ‘Most People to Take an Online Internet Safety Lesson in 24 hours’.
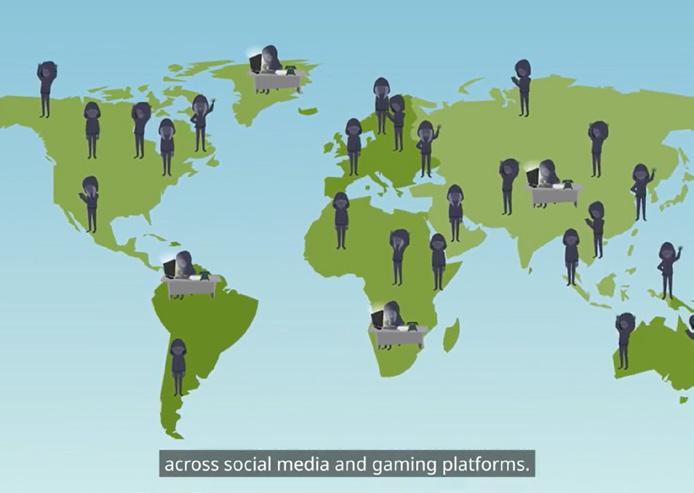
During the challenge, 1550 people from 44 countries completed the lesson in 24 hours, turning the day into the world’s largest ever cyber security training event.
The new school curriculum has been crafted by OSP’s team of expert educators and cyber professionals, many of whom come from policing and teaching backgrounds. Their unique experience ensures that the courses effectively educate children on the threats of the digital world, all while keeping learning engaging through interactive gaming methods.
We are absolutely delighted to announce our new partnership with NCSC Bahrain and to bring our online courses to such an important demographic. Children grow up in a digital world and it is vital they know how to navigate the environment safely. Whether it’s learning, socialising, playing games or interacting with friends, the online world hosts a huge proportion of a child’s life.
OSP Cyber Academy Cyber Awareness Courses Integrated into Bahraini School Curriculum




Gamified training to equip 70,000 students with vital cyber safety skills in partnership with Bahrain’s National Cyber Security Centre We must ensure that children understand the risks that lurk online, have the ability to spot danger and understand security best practices. Our courses have been designed specifically to suit these needs but in a format that is enjoyable for children. The games are interactive, fun, but they also provide guidance for children which will help keep them safe online, said Tommy McCarthy, CEO of OSP Cyber Academy.
This initiative aligns with the Kingdom of Bahrain’s vision of creating a digital society and a secure cyberspace, and it is expected to create new opportunities for educational initiatives and sustainable cyber security policies.
H.E. Sheikh Salman emphasized that the agreement to develop an interactive e-curriculum for school students, as part of this partnership, will play a key role in raising cyber security awareness among future generations from early educational stages.
This initiative supports the resilience of the digital society and establishes a sustainable cyber culture that aligns with national and international priorities for technological empowerment and responsible digital transformation.
We are delighted to be working so closely with NCSC Bahrain and their team to ensure that we deliver exactly what is required, OSP are also looking forward to officially opening our first office in the region in 2026 said Thomas McCarthy CEO and Founder of OSP Group Limited.

THE ARAB
INTERNATIONAL CYBERSECURITY CONFERENCE AND EXHIBITION 2025: ADVANCING CYBER RESILIENCE THROUGH GLOBAL COLLABORATION

Held under the esteemed patronage of His Royal Highness Prince Salman bin Hamad Al Khalifa, the Crown Prince, Deputy Supreme Commander of the Armed Forces, and Prime Minister of Bahrain, and hosted by the National Cyber Security Centre (NCSC), the Arab International Cybersecurity Conference and Exhibition (AICS) 2025 stands as the region’s premier platform for international dialogue, innovation, and capacity building in cybersecurity.

In remarks made on the sidelines of the conference, His Royal Highness Shaikh Nasser bin Hamad Al Khalifa, National Security Advisor, Royal Guard Commander, and Secretary-General of the Supreme Defence Council, affirms that the event reflects Bahrain’s strategic vision to strengthen national and regional cyber resilience.
His Royal Highness emphasizes that the conference and exhibition demonstrate the Kingdom’s commitment to safeguarding its national achievements and advancing digital security under the leadership of His Majesty King Hamad bin Isa Al Khalifa, supported by the government led by His Royal Highness Prince Salman bin Hamad Al Khalifa, the Crown Prince and Prime Minister.
He commends the efforts of the National Cyber Security Centre in transforming the conference into a global platform that unites policymakers, experts, and innovators to enhance cooperation and develop forward-looking solutions to emerging digital challenges.

AICS 2025 features a diverse and dynamic programme of strategic, technical, and educational activities that foster collaboration and inspire innovation across borders. For the first time in the region, DEF CON, one of the world’s most renowned cybersecurity communities, joins the conference with its signature Villages, bringing worldclass expertise, interactive experiences, and real-world technical challenges to Bahrain.
The exhibition floor hosts a broad range of international participation, including several national pavilions. Among them, the British Pavilion takes on a prominent and expanded presence, showcasing the United Kingdom’s leadership in cyber innovation and advanced technologies.
It brings together leading British companies and institutions to share expertise, exchange knowledge, and explore opportunities for collaboration with Bahrain and the wider region. One of the most anticipated highlights is the Cyber Escape Room, presented by OSP Cyber Academy, which offers participants an immersive and handson experience that simulates real-world cyber incidents in a learning-focused environment.
In parallel, the National Cyber Security Centre is collaborating with OSP Cyber Academy on a landmark initiative to develop a comprehensive cybersecurity e-curriculum for schools across Bahrain, encompassing both public and private institutions. The initiative introduces four localized online courses in Arabic and English, each tailored to a specific school level, and designed to promote digital citizenship, online safety, and responsible technology use.
His Excellency Shaikh Salman bin Mohammed Al Khalifa, CEO of the National Cyber Security Centre, notes that this collaboration reflects Bahrain’s commitment to cultivating a resilient digital society through education and international partnership. He adds that the initiative supports the Kingdom’s national vision to empower youth, strengthen cyber awareness, and prepare future generations to thrive securely in an increasingly digital world.
These collective efforts highlight Bahrain’s commitment to building a digitally confident nation that values innovation, invests in education, and strengthens global partnerships to advance cybersecurity for generations to come.
Thomas McCarthy CEO & Founder of OSP Cyber Academy signing agreement with His Excellency Sheikh Salman bin Mohammed AlKhalifa, CEO of NCSC Bahrain, standing Alastair Long His Majesty’s Ambassador to the Kingdom of Bahrain


Building Digital Resilience and Security
Advancing
Cyber Security and Technology Risk Management for a Future
The Future of Trust
Across every industry, the race to modernise technology has outpaced traditional approaches to risk management. Cloud platforms, automation, and artificial intelligence are reshaping how organisations operate and exposing new layers of dependency and risk.
The question facing leaders is no longer whether they can secure their organisations, but how they can sustain trust, resilience, and control in the face of constant change.
We believe the answer lies in people and partnership. For more than 15 years, we’ve supported organisations across financial services, energy, retail, and critical infrastructure to build security capability that endures. Our consultancy approach combines deep technical expertise with an understanding of culture, behaviour, and governance, helping clients move from compliance to confidence.
We don’t just deliver, we build capability. That philosophy sits at the heart of every engagement, ensuring that when our work concludes, our clients are stronger, clearer, and more self-reliant than before.
Develop a Connected Approach to Risk
Effective risk management today extends beyond cyber defence or regulatory alignment. It connects digital risk, operational resilience and technology assurance into a single framework of accountability.

that depends on trust
Organisations are increasingly integrating governance, risk and compliance (GRC) disciplines with cyber strategy to create real-time visibility of threats, dependencies and opportunities. By aligning these capabilities, leaders can make confident, data-led decisions that balance innovation with security.
We see the most mature organisations managing technology risk as a continuous capability rather than a periodic exercise. They understand that visibility and agility are key to maintaining resilience as their ecosystems expand and evolve.
Making Control Environments Work
Many organisations still operate with fragmented control environments, shaped by years of growth, mergers or regulatory change. The result is often complexity, inconsistency and a lack of clarity on control effectiveness.
i-confidential helps clients simplify and operationalise these environments. We focus on controls that are evidence-based, measurable, and linked to tangible business outcomes.
Through rationalisation and automation, we make assurance faster and more reliable, freeing teams to focus on improvement rather than administration.
The result is an integrated control landscape that scales with the business and adapts as risks evolve. It’s the practical application of our philosophy to make security understandable, measurable, and achievable.
Managing Complexity in the Evolving Risk Landscape
Risk today is interconnected. Cyber, operational, third-party and technology risks converge across supply chains and digital ecosystems. No single function can manage this complexity alone.
Modern risk management depends on shared intelligence, data integration and human insight. Technology can highlight correlations and predict emerging vulnerabilities, but it is expert judgment that determines what truly matters.
We have helped organisations develop integrated risk models that combine technical analytics with business interpretation This approach not only improves decision quality, it delivers quantifiable outcomes by directly linking risk exposure to business impact and demonstrating the tangible repercussions of inaction.
The Power of Partnership
Security and resilience is built through collaboration. Whether between regulators and industry bodies, or between organisations and specialist partners, shared expertise accelerates progress and maturity.
i-confidential are a trusted partner to firms, working to translate complex frameworks into practical solutions that combine governance, culture, process and people. Our consultants help organisations build integrated risk management practices that draw on data from across the enterprise and overlay expert analysis to reveal patterns and priorities.
Scan the QR code

Every organisation benefits when cyber and technology risk management are treated as collective responsibilities, not isolated disciplines. Our partnership approach turns knowledge into capability and strategy into sustained confidence in your security posture.
Preparing for Technological Disruption
While today’s priorities focus on regulatory assurance and operational stability, the next decade will demand that organisations adapt rapidly to evolving technologies and updated cryptographic standards.
Rather than waiting for quantum computing to reach maturity, resilient organisations are already investing in cryptographic agility - building the capability to identify, manage and replace algorithms efficiently as threats evolve. This includes understanding where encryption is used, establishing governance for cryptographic assets and ensuring systems are ready to adopt new standards when required.
The same principle applies to evolving technologies such as AI and automation, which raise new questions of accountability, transparency and resilience. By embedding adaptability and governance into their cyber and technology strategies, organisations can confidently work with innovation while protecting the integrity of their systems and data.
Culture, the Foundation of Resilience
No strategy succeeds without culture. Technology alone cannot deliver security - it is people who make risk management effective.
Our experience in regulated environments has shown that culture is the foundation on which resilience depends. When employees understand how their decisions and actions contribute to trust, control and security, resilience becomes embedded.
We work with organisations to build cultures where security is understood, valued, and lived. Through targeted training, leadership engagement, and behavioural insight, we help translate abstract policies into everyday practice

The Road Ahead
As our global cyber and technology community gathers in Bahrain, we should consider that trust is not inherited, it is engineered.
Building trust requires modernising cyber and technology foundations, evolving risk and control frameworks, and nurturing a culture that values resilience as a shared responsibility.
We believe the future of security lies in the connection between governance and innovation, between technology and people, and between organisations that share a commitment to protecting what matters most.
Our Offerings
Our consultancy services help organisations assess, strengthen, execute, and optimise their cyber security and technology risk capabilities, unlocking value and building lasting resilience.
Our services combine deep domain expertise with practical delivery across our four connected pillars:
Assess
We evaluate your current risk and security posture through structured gap analysis, benchmarking, and strategic road-mapping. Our assessments clarify priorities and shape improvement programmes aligned with your business ambitions.
Strengthen
We enhance governance, risk, and control frameworks, develop policies and standards, and ensure alignment with regulatory expectations. Our teams also improve third-party security and build enterprise-wide resilience through effective oversight and compliance.

Execute
We turn strategy into action, implementing control design and testing programmes, delivering targeted security enhancements, and embedding operational services such as Identity and Access Management and Control Testing.
Optimise
We help organisations realise ongoing value from their investments by developing prioritised improvement plans, streamlining assurance processes, defining clear risk metrics, and enabling automation for cyber risk and compliance monitoring.
These offerings are supported by our Specialist Consultancy Team and Flexible Talent Network, giving clients access to experienced practitioners who work alongside their teams to deliver sustainable results.
Our interconnected GRC building blocks — spanning policy, standards, control libraries, process manuals, metrics catalogues, and control testing ensure every service we deliver is measurable, scalable, and designed for long-term success.
To discuss how we can support your cyber security and technology risk objectives, visit www.i-confidential.com or reach out to our team.


Siker Believe learn


Awareness & Training Workforce Development
Empowering engineers, OT professionals, and safety teams with industryleading cyber security knowledge
Our experienced staff will conduct a full Learning Needs Analysis (LNA) or Training Needs Analysis (TNA) Based on the findings we will deliver a suite of training courses to suit all your needs


Siker is a leading cyber security firm specialising in training, consulting, and professional services for industries where security is missioncritical. Since 2013, we have been committed to equipping professionals with the knowledge and skills needed to perform their roles securely, ensuring the protection of Critical National Infrastructure (CNI), Oil & Gas, Nuclear, Government, Water, and Transportation sectors against evolving cyber threats.
Consulting & Compliance
Identifying vulnerabilities, ensuring compliance, assessing against risk frameworks and strengthening security posture.
WHY SIKER?
& IT
Bridging the gap between IT and Operational Technology for comprehensive protection
ining – Practical cyber security education tailored for engineers and safety professionals
c Expertise – Deep understanding of CNI, Oil & Gas, and OT environments









CYBER FZ - LLZ RAKEN, United Arab Emirates

OSP

The Quantum Reckoning: How Hackers Are Already Winning Tomorrow’s War
While executives debate timelines, cybercriminals are positioning themselves for the ultimate heist
The corporate world loves a timeline. When will autonomous vehicles dominate our roads? When will artificial intelligence replace human workers? When will quantum computers revolutionise business? The answer to that last question— somewhere between five and thirty years, depending on whom you ask— has lulled many executives into a dangerous complacency.
This is a critical miscalculation. While quantum computing may seem like a distant concern, the quantum threat is already here, and it’s growing more urgent by the day.
Inside the Hacker’s Quantum Playbook
Cybercriminals have already adapted their strategies for the quantum age, displaying a sophistication that should alarm every corporate leader. Statesponsored hackers and criminal organisations have quietly begun what cybersecurity experts call “harvest now, decrypt later” attacks. They’re systematically collecting encrypted data with a chilling patience, storing it like vintage wine, waiting for the day when quantum computers can crack it open in minutes rather than millennia.
The hacker methodology is disturbingly elegant. Rather than attempting to break current encryption—a futile exercise that would take millions of years—they’re playing the long game.

Intelligence agencies report massive data theft operations where hackers aren’t even attempting immediate decryption.They’re simply stockpiling encrypted databases, communications, and intellectual property, confident that quantum technology will eventually deliver the keys.
The mathematics are stark. Today’s computers would need approximately two million years to break RSA encryption—the cryptographic foundation underlying virtually all digital security, from SSL certificates to VPNs. A commercially viable quantum computer, armed with Shor’s algorithm, could accomplish the same task in minutes. Every email, every financial transaction, every piece of intellectual property currently protected by traditional encryption becomes vulnerable the moment that quantum threshold is crossed.
This represents a fundamental shift in the threat landscape. Hackers have moved from opportunistic attacks to strategic positioning. They’re not just stealing data; they’re investing in future capabilities. The most sophisticated threat actors are already recruiting quantum computing he most sophisticated threat actors are already recruiting quantum computing expertise, establishing partnerships with academic institutions, and developing quantum-enabled attack frameworks.
This isn’t theoretical. The encryption protecting today’s data—your company’s R&D secrets, customer information, strategic plans—is already compromised in principle. The only question is timing.

Dr Meera Sarma


CEO of Cystel , A cybersecurity firm
Modern businesses operate through complex webs of suppliers, partners, and service providers, each representing a potential entry point for quantum-enabled attacks. A single compromised supplier could expose dozens of downstream companies to catastrophic data breaches.
Consider the automotive industry, where a single component manufacturer might supply parts to multiple car brands. If quantum computers can crack the encrypted communications between that supplier and its customers, hackers could potentially access design specifications, manufacturing processes, and strategic plans across the entire automotive ecosystem. The same vulnerability exists in pharmaceuticals, aerospace, financial services, and virtually every other interconnected industry.

The challenge is compounded by the global nature of modern supply chains. Companies may have quantum-safe encryption in their headquarters, but their suppliers in different countries might be operating with outdated cryptographic standards. The weakest link principle means that quantum vulnerabilities anywhere in the supply chain can compromise the entire network.

The operational benefits are equally compelling. Companies using quantum sensing technologies have reported operational efficiencies of up to 80 percent. Aircraft manufacturers are exploring quantum applications to optimise wing design and reduce carbon footprints. Pharmaceutical companies are using quantum computing to accelerate drug discovery, potentially revolutionising how we approach cancer treatment and Alzheimer’s research.
But hackers understand these opportunities too. The same quantum capabilities that can optimise supply chains can also be weaponised to disrupt them. Criminal organisations are positioning themselves to exploit quantum advantages for financial gain, industrial espionage, and geopolitical manipulation. They’re not waiting for commercial quantum computers; they’re preparing to acquire or access them through various means.
Regulatory Reality Check
The regulatory landscape is crystallising rapidly, leaving little room for procrastination. The UK’s National Cyber Security Centre has given organisations a clear directive: prepare now, complete the transition within three years. The U.S. National Institute of Standards and Technology has already published five quantumresistant algorithms, establishing the foundation for post-quantum cryptographic migration.
A quantum-enabled attack on any single point in this network could potentially compromise millions of transactions, customer data, and financial records. The interconnected nature of global finance means that a breach in one institution could cascade across continents within hours.
The Boardroom Awakening
Smart money is already moving, and the implications of inaction are becoming clearer with each passing month. IBM has committed $150 billion to quantum research and development, a figure that should make any chief executive pause. By 2027, more than half of Fortune 500 companies are expected to have adopted quantum technologies at some level. These aren’t speculative investments in distant futures; they’re strategic preparations for imminent realities.
One international bank has already assembled an entire steering committee dedicated to quantum threats. Their reasoning is sound: financial institutions are treasure troves of sensitive data, and the cryptographic methods protecting customer information and trading algorithms are exactly what quantum computers will render obsolete.
These aren’t suggestions; they’re mandates. The European Union’s Digital Operational Resilience Act (DORA) explicitly addresses cryptographic requirements, with quantum resistance becoming a compliance necessity rather than a competitive advantage. Germany’s Federal Office for Information Security has mandated quantum-safe cryptography for public sector and critical infrastructure by 2025.

The message from regulators is unambiguous: the quantum transition isn’t optional, and the timeline isn’t negotiable.
Financial supply chains present particularly attractive targets. Payment processors, banks, and fintech companies all rely on encrypted communications to handle transactions.

The price differential is significant. Early adopters can implement quantum-safe measures systematically, testing and optimising as they go. Late adopters will face crisis-driven implementations, rushed timelines, and the compounding costs of urgency.
The Cost of Inaction
Delaying quantum preparation isn’t just risky; it’s expensive. Every month of inaction increases the eventual cost of migration. Insurance companies are beginning to factor quantum vulnerabilities into their risk assessments, and organisations without quantum-safe measures may soon find themselves uninsurable.
Post-quantum migration isn’t a simple software update. It requires comprehensive cryptographic inventory assessment, risk modelling, and phased implementation across entire technology stacks.
Beyond the Threat
The quantum conversation shouldn’t focus solely on security risks. The technology promises transformative opportunities across sectors.
Quantum computing can optimise supply chains, accelerate materials discovery, and solve complex logistical problems that currently require enormous computational resources.
However, security must come first. Without robust quantum-safe foundations, organisations cannot safely exploit quantum opportunities. The companies building quantum readiness now will be positioned to capitalise on quantum advantages as they emerge.

Industry consortiums are emerging to establish quantum-safe standards across sectors. These collaborative efforts recognise that quantum security is only as strong as the weakest participant in any business ecosystem.
The Geopolitical Dimension
The quantum race has profound geopolitical implications. Nations leading in quantum technology development will hold significant advantages in intelligence gathering, financial manipulation, and strategic communications. Recent power outages affecting multiple countries hint at the potential scale of quantumenabled disruption.
The Practical Path Forward
The good news is that quantum preparation doesn’t require revolutionary changes overnight. The process begins with understanding current cryptographic dependencies— what encryption methods protect which systems, where vulnerabilities exist, and how data flows through the organisation and its supply chain network.
Smart companies are conducting quantum risk assessments, mapping their cryptographic inventory, and developing migration roadmaps that account for supplier relationships and third-party dependencies. They’re implementing hybrid cryptographic approaches, combining traditional and quantum-resistant algorithms to ensure security during the transition period.
The key is crypto-agility—building systems that can adapt to new cryptographic standards as they emerge.
This flexibility will prove invaluable as quantum technologies evolve and new threats emerge. Companies must also extend this agility to their supplier networks, establishing quantumsafe communication protocols and requiring vendors to meet minimum cryptographic standards. Supply chain security requires collaborative approaches. .
The quantum divide could reshape global power dynamics. Countries and companies that fail to prepare may find themselves at the mercy of those that do. This isn’t hyperbole—it’s the logical extension of technological advantage in an interconnected world.
The Time to Act
The quantum timeline isn’t measured in decades; it’s measured in years, possibly months. The corporate leaders who understand this reality are already moving. They’re not waiting for quantum computers to arrive; they’re preparing for the moment when they do.The quantum imperative isn’t about implementing exotic new technologies. It’s about protecting existing business operations, ensuring regulatory compliance, and positioning for future opportunities. The companies that act now will determine their competitive position for the next generation of computing.
The question isn’t whether quantum computing will transform business— it’s whether your organisation will be ready when it does. The clock is ticking, and the time for preparation is now.
Dr. Meera Sarma is CEO of Cystel, a cybersecurity firm offering quantum safe cybersecurity products and services for enterprise and government clients. She has spent over a decade researching hackers, Quantum Computing cyber threats and contributes to the UK Parliamentary Office for Science and Technology.


Quantum Cyber Services
Our services are designed to fit into wherever you are on your cybersecurity and business risk journey.
Our approach allows us to dovetail into your existing cyber programmes and also to step you forward and join up with future transformation without incurring risk gaps and misalignment


Quantum Readiness Workshop All organisational stakeholders must be lenges, risks, and potential ert-led, customized training for : quantum computers and the nd quantum safe cryptography.
nables enterprises to e strategies to safeguard their m computing. A quantum nisations to quantum risk e current state of their s; Identify vulnerable and m quantum threats; develop a cybersecurity
curity transformation is the d quantum cryptography ctices This involves utilizing to enhance the security of nication networks
urity road mapping is a needsss to help identify, select, and o satisfy a set of
t: the creation of a clientmework and an update to the rporate quantum quantum technology into









Email Threat Protection
End Point Detection and Response

Email Encryption

Threat Evolution provides comprehensive cyber security solutions for all types of businesses.
Our services are here to help you tackle the ever -growing threat landscape while you focus on growing your business safely and securely.
Our experts are ready to help and support you. Contact us today and secure your business!!

Artists Impression of Escape Room at AICS
If you want to bring Cyber Security alive for your staff who are not involved in information security, then our pop-up “escape room” style training is an engaging and interactive experience.
Cyber Escape Rooms “Knock your Cyber Training out the Park!”
Cyber News Global had the pleasure of catching up with Irene Coyle, Chief Operating Officer OSP Cyber Academy who shared her thoughts on Immersive Training and the OSP Cyber Academy Cyber Escape Rooms.
Knock your Cyber Training out of the PARK.
I believe that to have an effective cyber training programme and not a one-off event), there are a number of things you should be considering when building your programme ...
Typically, information security training happens when an employee joins and they are overloaded with information, and they are only really concerned with where the coffee machine is.
1. Frequency and recency of signals passing from one neuron to the next increase memory
Tell people what you want them to know often! (don’t worry I am not getting too scientific here) Shift the focus from an annual task to an ongoing program, comprising e-learning, team meetings, face to face training and newsletters. The more you provide information, the more chance you will have that the message will land.
2. Emotions strengthen Memory
When we have fun, our brains release dopamine. According to neuroscientist Dr Martha Burns, dopamine has a direct impact on our ability to remember.

The more interested we are in an activity; the more dopamine is released and the better we remember it. She calls dopamine the “Save” button.
3. Memories are stored in multiple parts of the brain Research suggests that memories are stored in many different parts of the brain. Different ways of learning trigger different reactions and different connections between synapses. If we engage all the senses while learning it will create memories in many parts of the brain and will reinforce your learning.

In addition, our brains are programmed to focus on new and unusual ways of learning. Learning that taps into the brain’s natural curiosity will be more successful.
OSP Cyber Academy want your staff to be engaged and motivated and feel minimal stress, Learning comes not from quiet classrooms and directed lectures, but from classrooms with an atmosphere of exuberant discovery” – that’s what we have introduced in our Immersive Training – a pop up escape room style exercise.
Our immersive training is a mental and physical adventure-based game in which players solve a series of puzzles and riddles using clues, hints, and strategy to complete an objective. During our training, users will have fun, cover important topics, and have time to reflect on that learning. The originality of the immersive approach will also support remembering key lessons.
“We come to your office and just need the space of a desk, we set up the exercise all from one suitcase, so you are in a police officers desk area with items on the desk to explore” Solve clues, crack lock codes, decipher information in emails. You need to act as a team to complete the exercise.
We all know from training some people will just sit back and hide and let others do the guesswork – we have designed our training so that everyone has a part to play The message should be for your organisation to build cyber resilience – everyone has a part to play not just your IT team.
The training should form part of an overall information security awareness training, comprising different types of learning including e-learning and regular newsletters.
Studies show that people will retain up to 60% more information when they are having fun and this training is designed to be fun for the learners involved which means it is more effective in increasing cyber security awareness with your staff.
You will also be providing a great team building experience as well as valuable skills that will help to keep company data and personal data safe.
Get in touch with me and we can demo the immersive training over a 10-minute teams call –the advantages of technology.
To hear more about what Irene had to say with Lets Talk Cyber scan the code.




Don’t Duck with your Cybersecurity.
The world’s first zero-touch, non-invasive technology to visualize the threat.


Reduce Mean Time to Resolution with







THE EVOLUTION OF DATA PROTECTION: HOW GDPR IS SHAPING GLOBAL PRIVACY STANDARDS
By Irene Coyle, Chief Operating Officer at OSP Cyber Academy
In the digital age, where personal data is a critical asset, the need for robust data protection measures has never been more pressing. The General Data Protection Regulation (GDPR), introduced in 2018, has set a global benchmark for data privacy. It has transformed not only how organisations manage data but also how individuals view their personal information. But what makes GDPR so impactful, and how is it shaping the global landscape of data privacy?
For Irene Coyle, Chief Operating Officer at OSP Cyber Academy, GDPR represents a paradigm shift in how data is treated.
“GDPR is more than just a regulation,” Irene explains. “It’s a framework that redefines the relationship between individuals and organisations in terms of data. It places the individual at the heart of all data processing activities, ensuring their rights are prioritised.”
This shift from a compliance-driven model to one that emphasises individual rights marks GDPR’s most significant contribution to the privacy landscape.


The regulation has empowered individuals to take control of their data.
“ If it was your data, you would want to have control over how it’s used, how it’s stored, and how it’s shared. GDPR puts that power back into the hands of the individual, ” Irene highlights.
The Global Impact of GDPR
One of the most remarkable aspects of GDPR is its global influence. While it originated in the EU, it has set the standard for data privacy laws worldwide. Irene points out that many countries have followed suit, recognising GDPR as the blueprint for modern data protection.
“Obviously we now have the UK GDPR too but also countries like Brazil, South Korea, and various states in the US are adopting GDPR-like laws because they see the value in creating a unified framework for data protection,” she says.
This influence extends beyond simple adoption; GDPR has prompted a cultural shift towards transparency and accountability in data practices.
“GDPR makes organisations answerable to the people whose data they handle. It ensures that privacy is not just a legal obligation but a fundamental value,” Irene notes.
Why GDPR’s Approach to Consent and Transparency Matters
One of the cornerstones of GDPR is its emphasis on consent and transparency. Before GDPR, consent was often buried in long detailed legalese, making it difficult for individuals to fully understand what they were agreeing to. GDPR changed that.
“GDPR requires clear, informed, and affirmative action consent. It forces organisations to be transparent and to explain their data practices in simple, understandable terms,” Irene explains.
This shift towards transparency has been crucial in building trust.
As Irene highlights,“Transparency isn’t just about compliance—it’s about trust. Companies that are clear about how they use data are more likely to earn the trust of their customers. And in today’s world, trust is a competitive edge.”
Data Governance Under GDPR
The implementation of GDPR has forced organisations to rethink their approach to data governance. No longer is data protection viewed solely as an IT issue; it is now recognised as a business risk.

“Data protection is a business-wide issue that affects every department, from marketing to HR. GDPR makes it clear that this is essential to the integrity and reputation of the organisation,” says Irene.
For Irene, a key component of effective data governance is having a dedicated data protection officer (DPO).
“A DPO plays a crucial role in ensuring that an establishment adheres to GDPR principles. It’s not something that can be tacked onto someone’s existing responsibilities,” she explains. “Without a dedicated DPO, organisations struggle to demonstrate the level of accountability that GDPR demands.”
Irene describes the importance of mapping data flows:
“GDPR forces companies to trace the entire journey of their data—from collection to storage, sharing, and disposal. This mapping process is not only essential for compliance but also for strengthening an organisation’s overall data governance framework.”
GDPR
vs. CCPA: Key Differences
Comparing GDPR with other privacy laws, such as the California Consumer Privacy Act (CCPA), highlights some key differences. While both laws aim to protect personal data, GDPR takes a more comprehensive approach.
“GDPR requires opt-in consent, whereas CCPA allows individuals to opt out of data sales. This is a fundamental difference because opting in ensures that the individual is fully aware and in control of how their data is used,” Irene explains.
Furthermore, GDPR introduces the concept of “privacy by design,” meaning that privacy must be integrated into the development of new products and services from the very beginning. Irene underscores this by saying,

“GDPR doesn’t allow organisations to scramble to comply at the last minute. Privacy must be embedded in the design process from day one. It’s about proactively protecting data, not reacting to issues after the fact.”
Another critical distinction between GDPR and CCPA is GDPR’s extraterritorial scope.
“Even if a company is based outside the EU, if they process the personal data of EU citizens, they must comply with GDPR. This global reach is something that other regulations, like CCPA, don’t have,” Irene notes.
“This extraterritorial reach ensures that organisations worldwide are held to the same high standards of data protection, which is crucial for the digital economy.”
Looking Ahead: The Future of Data Protection
This global reach is something that other regulations, like CCPA, don’t have, Irene notes.
“This extraterritorial reach ensures that organisations worldwide are held to the same high standards of data protection, which is crucial for the digital economy.” she says.
As Irene prepares to attend the GISEC Conference in Dubai, she reflects on the future of data protection and GDPR’s continuing evolution.
“The world is changing rapidly, and data protection must evolve with it. GDPR has set the foundation, but it’s important for organisations to continue to adapt and embrace data protection as a core business value,” she says.
At OSP Cyber Academy, Irene and her team are helping companies navigate the complexities of GDPR compliance and data protection training.
“We’re seeing a real shift in how organisations approach data protection. It’s no longer seen as a regulatory hurdle but as a strategic asset that can enhance brand value and build consumer trust,” Irene adds.
Looking ahead, GDPR is likely to remain the global standard for data protection, influencing not just new regulations but also the way businesses think about data.
“GDPR has set the bar for data privacy, and it’s up to all of us to ensure that we continue to meet and exceed those expectations,” Irene concludes.






The Human Side of Cybersecurity –Ben Owen on OSINT, Digital Footprints
and Global Collaboration
Ben Owen is the co-owner of The OSINT Group, a unique cyber risk mitigation and intelligence collection training company with a global reach. The business specialises in safeguarding digital environments for individuals and organisations, providing expert training in open source intelligence, digital vulnerabilityassessments and strategic security awareness.

Cyber News Global recently caught up with Ben, well known to many for his role on the hit TV show Hunted. Over the past decade, the series has become a fascinating look at how people can be tracked down using both privileged information and open source intelligence, OSINT. Ben has appeared in the UK, US and Australian versions, and has seen first-hand how much valuable information can be found online in minutes.
People have no idea just how much they share every day. Signing up for accounts, leaving reviews, commenting on social media, even logging activity on fitness apps and all of it creates a trail. That data can be used by both the good guys and the bad guys.
One case study from his training sessions illustrates the point.

Within 15 minutes, Ben and his team gathered a wealth of personal information on the Chief Information Officer of a major British energy company who is a professional well versed in cyber security and even advised by the government.
They found personal email addresses, phone numbers, home address, vehicle details, passwords, internal images of their home, and fitness app routes that tracked them to within 20 metres of their front door.
The point, Ben says, is not to scare but to show the reality. We are the good guys, so we lock things down and remove what we can, but imagine the opportunity for hackers. Espionage, blackmail, social engineering – the vulnerabilities are huge.
Why OSINT is Not Just for Techies
A common misconception is that OSINT is purely a technical skill. You do not need to be a coder to be a great online investigator. It is about how you think.
You need to be dynamic, curious, mentally agile. You have to follow threads, backtrack when needed, and most importantly, corroborate what you find. The first piece of information you uncover might look like gold, but it could be misleading. You have to find the gaps.
In a world of user generated content, much of what is online is personal opinion or unverified data. It is not a linear process. You have to be ready to explore, get lost down a rabbit hole, then work your way out again.


Ben has seen regional differences in threats and solutions. But he has also noticed a welcome trend –more collaboration in the OSINT community. One of the best things about this field is that people share. Yes, we run businesses, but there is enough work for everyone. The more collaborative we are, the stronger the whole community becomes.
Some regions stand out for their forward thinking approach, particularly the UAE. They have such a positive mindset. They get it, and they are brilliant to work with.
The Corporate- Personal Security Gap
Most large organisations have strong corporate cyber security. They invest in technology, enforce good password policies, use multi factor authentication and employ skilled teams. But outside the office, it is a different story.The real weakness is when people log off and revert to their personal devices and accounts.
That is where hackers are striking. Look at the major breach at password manager LastPass. This attack started with the developer’s personal laptop, not the corporate network. Hackers take the path of least resistance.
Threats Around the World
With work taking him to over a dozen countries and four continents already this year,
He has also seen a growing appetite for OSINT in regulated industries like finance and government, and in sectors like logistics, green energy and tech start-ups. But the latter often put speed to market above security, which is a risk that can be costly later, particularly in areas like electric vehicles and smart transport.
Why Technology Alone is Not Enough
Too many organisations think that investing in expensive security technology is enough. Tech is only as good as the people interpreting the data. It is not about ripping everything up and starting again. Many of the biggest wins come from awareness and small, strategic changes.
One of the most effective tools his company offers is the Digital Vulnerability Assessment.
One of the most effective tools his company offers is the Digital Vulnerability Assessment. This is a process that identifies what information is publicly available about an organisation and its key people. It is not a technical scan, it is looking at what a hacker could find in minutes and use against you. Every client is shocked by how much is uncovered.
Information might include email addresses, passwords, home images, travel patterns, vehicle details and even favourite pubs. Hackers often have no moral limits, so they may target spouses or children as a route in.
The Rising Threat of Digital Extortion
While ransomware grabs headlines, another threat is growing in the shadows – blackmail and extortion based on stolen personal data. This could involve finding that someone is in a relationship but also active on dating sites, for example. Even if that information is not illegal, it is highly sensitive. In most cases Ben and his team can map almost all of someone’s digital footprint.
Because such incidents often do not involve leaked customer data, companies may not be legally obliged to report them. Many victims simply leave the company quietly. But his team deals with blackmail cases every week, and the numbers will keep rising as breached data becomes more available.
The key is prevention. If you can manage your digital footprint, you can remove many of the opportunities for hackers. That does not need to cost the earth –it just needs awareness, the right







Your Trusted Global Partner in Data Protection & Privacy Compliance
Data protection is no longer just a European issue — it’s a global business imperative. Across the Middle East, organisations are adapting to new data protection laws such as the UAE PDPL, KSA PDPL, and DIFC DP Law 2020. At XpertDPO, we help you navigate these evolving regulations with clarity, confidence, and integrity.
As experienced Data Protection Officers (DPOs) and GDPR specialists, our team brings international expertise and local understanding to ensure your organisation meets compliance requirements — efficiently and ethically.
Our Services

Outsourced and Fractional DPO Services
Gain access to senior data protection expertise without the cost of a full-time hire. We act as your independent DPO, advising on compliance, monitoring obligations, and liaising with regulators across Europe and the Middle East.
Training and Awareness
Build your organisation’s data protection culture through bespoke workshops, leadership briefings, and employee awareness sessions.
Specialist Data Protection Support
Enhance compliance function with expert support in:
- DPIAs – Data Protection Impact Assessments
- DSARs – Data Subject Access Requests
- Regulatory & Audit Response
- Due Diligence for M&A
- GDPR & PDPL Alignment
Industry Expertise
Trusted by clients in finance, healthcare, education, and technology, including organisations managing clinical trials and cross-border data transfers.
Why Organisations Choose XpertDPO
• Global Expertise, Local Insight — Deep understanding of both EU and GCC data protection frameworks.
• Ethical & Transparent — No fear-based selling, just honest, practical advice.
• Pragmatic & Results-Focused — Compliance that supports your business, not hinders it.
• Trusted & Independent — A proven European partner now supporting clients across the Middle East.
Protecting Your Data. Strengthening Your Trust.
At XpertDPO, we combine legal precision with business practicality — helping you manage risk, demonstrate compliance, and earn the trust of your customers and regulators.
We don’t just help you meet regulations — we help you build confidence through compliance. XpertDPO — Ethical. Pragmatic. Trusted.

TRANSFORM YOUR BUSINESS WITH GRC WORKSHOPS


RISK MANAGEMENT APPROACH

ISMS & PIMS, RELEVANT FRAMEWORKS & BEST PRACTICES

SETTING UP GOVERNANCE WITHIN YOUR ORGANISATION

COMPLIANCE EFFORTS













Building Trust, Reducing Risk.

Unlocking value, reducing risk and building resilience across your business. We help organisations like yours navigate today’s complex cyber risk landscape with confidence.
Our services are designed to assess, strengthen, execute and optimise your risk management capabilities so you can focus on what matters most – growing your business securely.
Scan the QR Code to learn more.
