Chapter 10: Hardware and communication
involve many different people. As data travelling over WANs is likely to travel over many different networks owned by many different people, there is a much higher risk of data being intercepted. This form of threat, known as a man-in-the-middle attack, means that unencrypted data could be stolen or altered. This is why you should be careful about what information you send over the internet and why you should also make sure that you only use sites that encrypt your personal data before sending.
Structures for networked services Two common structures for networks are client–server and peer-to-peer.
Client–server structure
Sa m
pl
e
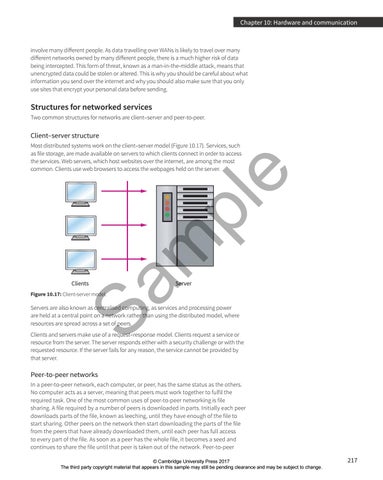
Most distributed systems work on the client–server model (Figure 10.17). Services, such as file storage, are made available on servers to which clients connect in order to access the services. Web servers, which host websites over the internet, are among the most common. Clients use web browsers to access the webpages held on the server.
Clients
Server
Figure 10.17: Client-server model.
Servers are also known as centralised computing, as services and processing power are held at a central point on a network rather than using the distributed model, where resources are spread across a set of peers. Clients and servers make use of a request–response model. Clients request a service or resource from the server. The server responds either with a security challenge or with the requested resource. If the server fails for any reason, the service cannot be provided by that server.
Peer-to-peer networks In a peer-to-peer network, each computer, or peer, has the same status as the others. No computer acts as a server, meaning that peers must work together to fulfil the required task. One of the most common uses of peer-to-peer networking is file sharing. A file required by a number of peers is downloaded in parts. Initially each peer downloads parts of the file, known as leeching, until they have enough of the file to start sharing. Other peers on the network then start downloading the parts of the file from the peers that have already downloaded them, until each peer has full access to every part of the file. As soon as a peer has the whole file, it becomes a seed and continues to share the file until that peer is taken out of the network. Peer-to-peer © Cambridge University Press 2017 The third party copyright material that appears in this sample may still be pending clearance and may be subject to change.
217