Cybersecurity Awareness Month 2024
Background
Cybersecurity Awareness Month highlights the growing importance of cybersecurity in our daily lives and encourages individuals and businesses to take important cybersecurity steps everyday to Secure Our World and stay safe online.
Founded in 2004, Cybersecurity Awareness Month, held each October, is the world’s foremost initiative aimed at promoting cybersecurity awareness and best practices. Cybersecurity Awareness Month is a collaborative effort among businesses, government agencies, colleges and universities, associations, nonprofit organizations, tribal communities, and individuals committed to educating others about online safety.
Every Year Cybersecurity Awareness Month is led by the Cybersecurity and Infrastructure Agency (CISA) and the National Cybersecurity Alliance. For more information about ways to keep you and your family safe online visit https://www.cisa.gov/cybersecurity-awareness-month and https://staysafeonline.org/cybersecurity-awareness-month/.
Introduction to Cybermonth 2024
This year, the theme for Cybersecurity Awareness Month 2024 is “Secure Our World”. Launched in 2023, “Secure Our World” empowers everyone to understand the simple ways to protect yourself, your family and your business from online threats. We’re increasingly connected through digital tools and more of our sensitive information is online. This convenience comes with risks. Each of us has a part to play in keeping ourselves and others safe. It’s easy to do and takes less time than you think.
Key Messages and Facts for 2024
While we’ve witnessed amazing advancements in technology such as AI, the tried-and-true cyber basics still apply and are greatly effective at keeping you safe. This is why we continue to highlight the four simple ways to stay safe online during this year’s Cybersecurity Awareness Month:
• USE STRONG PASSWORDS AND A PASSWORD MANAGER
• TURN ON MULTIFACTOR AUTHENTICATION
• UPDATE YOUR SOFTWARE
• RECOGNIZE AND REPORT PHISHING
Between the strong passwords entered, 6- digit pins texted to our phones, and fingerprints scanned, cybersecurity is a constant part of our everyday lives. When done right, these everyday practices greatly improve our online safety and give us the peace of mind that our data, finances, organizations, and families are protected.
According to the Annual Cybersecurity Attitudes and Behaviors Report 2023, the following statistics were noted:
• Only 38% of people used unique passwords for all their accounts
• Only 36% of people always install software updates when they become available
• Only about a third of respondents began using a password manager after receiving cyber training
• 84% of people who responded considered online safety to be a priority
• Only 79% of respondents were “familiar” with multifactor authentication (MFA) and only 70% of those respondents know how to use MFA
• Only 69% of people express confidence in their ability to identify phishing attempts
o 51% of Americans actively report cybercrimes, particularly instances of phishing.
The Basics of How to Stay Safe Online
1. Use Strong Passwords and a password manager
All passwords should be
• Long: At least 16 characters
• Unique: Never reuse passwords
• Random: Use a random string of mixed-case letters, numbers and symbols, like: Yuc8$RikA34%ZoPPao98t
• Keep your passwords safe by using a password manager!
2. Turn on Multifactor Authentication
Multifactor authentication provides an extra layer of security on your accounts and may include a biometric login or entering a code sent to your phone or email.
3. Update Software
Updating software and devices is the easiest way to stay protected from security threats. Perform updates as soon as they become available or set automatic updates.
4. Recognize and Report Phishing
Keep an eye out for phishing and other scam attempts in your emails, texts, direct messages or phone calls. Always verify the sender before clicking links or downloading attachments. If you spot a scam, report it!
The BioBridge Global 2024 Cybersecurity Campaigns
Week 1: Understanding Cyber Threats and Their Impact
Think before you click
• As more of our daily lives move online, the risks associated with online security increase.
• Cybercriminals base a lot of their attacks on getting people to act impulsively and without thinking, whether this is through a phishing email, a malware attack, or a more sophisticated social engineering assault.
What to do
• When you receive an email that includes a link, or you come across a message on social media or a pop up online, the first thing you should do – as per the campaign – is stop and think.
• If possible, hover your mouse over the link to reveal the true source. Often this will show you that the link is fraudulent, directing you to a malicious website or location. If this isn’t possible, copy the link and paste it into an incognito browser, ensuring it can’t gain access to any of your accounts – though this still poses the risk of installing malware on your device. If you have any suspicions at all, the best course of action is to do nothing. If possible, report the email or link to your IT department.
Week 2: AI and Deepfakes- Novelty Treat or Novelty Threat?
What are deepfakes?
Deepfake is a form of artificial intelligence (AI) that can be used to create convincing hoax images, sounds, and videos.
How To Spot Deepfakes
Deepfakes can be spotted by recognizing unusual activity or unnatural movement, including:
• Unnatural eye movement
o A lack of eye movement is a good sign of deepfakes.
o Replicating natural eye movement is challenging as peoples’ eyes usually follow and react to the person they are speaking with.
• A lack of blinking
o A lack of blinking is also a flaw with deepfaked videos. Replicating the natural, human action of regular blinking is difficult with deepfake technology.
• Unnatural facial expressions and facial morphing
o Deepfake technology involves morphing facial images, with faces simply being stitched from one image over another.
o This typically results in unusual or unnatural facial expressions.
• Unnatural body shape
o If a person’s body does not look to have a natural shape, then it is most likely fake. Deepfake technology largely focuses on faces rather than the entire body, which leads to unnatural body shapes.
• Unnatural hair
o Fake images cannot generate realistic individual characteristics, such as frizzy or messed-up hair.
• Abnormal skin colors
o Deepfakes are unable to replicate the natural colors of images and videos. This leads to them showing abnormal skin colors.
• Awkward head and body positioning
o Deepfake images will often feature inconsistent or awkward-looking head and body positioning.
o Examples of this include jerky movements and distorted images when people move or turn their heads.
• Inconsistent facial positions
o Deepfake images will often feature inconsistent or awkward-looking head and body positioning. Examples of this include jerky movements and distorted images when people move or turn their heads.
• Odd lighting or discoloration
o Similar to the reasons for unnatural skin tones, deepfake images are also prone to discoloration, misplaced shadows, and unusual lighting.
• Bad lip-syncing
o Deepfake videos will likely feature lip-syncing that does not align with the words being spoken by the people in the video.
• Unnatural perspective or movement
o People or animals may move in unnatural ways, or body parts may vanish as they walk into each other or objects.
What is being done To Combat Deepfakes
• Social media rules
o Social media such as Facebook has hired researchers from universities to help it build a deepfake detector, which enforces its ban on deepfakes.
o Twitter has policies in place to prevent fake content and is working to tag deepfake images that are not immediately removed.
o YouTube also vowed to block any deepfake content related to the 2020 U.S. election and census.
• Research lab technologies
o Researchers have been working on data science solutions that detect deepfakes.
o Many of these have quickly become ineffective as the attackers’ technology evolves and creates more convincing results.
• Filtering programs
o Filtering programs are also working to prevent deepfakes. AI firm DeepTrace’s program acts in the same way as an antivirus or spam filter and diverts fake content into a quarantine zone, while Reality Defender, from AI Foundation, aims to tag manipulated content before it can do any damage.
• Corporate best practices
o One of the best ways to prevent deepfakes is for employees to understand the signs of fake images and videos.
o Corporate best practices include advising users on the telltale signs of cyberattacks and fraudulent online activity.
• U.S. legislation
o Laws have already been passed in several U.S. states to criminalize deepfake and prevent the technology’s use around elections or to harm the reputations of individuals.
o A deepfake legislation was also introduced into the National Defense Authorization Act (NDAA) in December 2019.
Week 3: Mobile Device, Travel Security and Remote Workers
Mobile
Cybersecurity Risks
Travelers and their organizations can face additional information security risks while traveling. Mobile devices face many risks, including:
• Phishing attacks: Hackers take advantage of the general assumption that mobile devices are safer than computers.
• Data leakage: Employees may download apps and grant access permissions without understanding what the app will do with their information.
• Malware: This intrusive software can damage a device's internal systems, steal information, and more.
• Risky apps: Apps can be high-risk if they cause a phone to lose data connection, drain the battery, or expose security or privacy.
• Spyware: Spyware attacks can be more difficult to catch on a phone because the small screen makes it hard to monitor multiple programs.
• Network spoofing: Hackers can insert themselves between a user and the internet when using an unsecured or spoofed Wi-Fi connection.
• Unsecured public Wi-Fi: Using unsecured public Wi-Fi can put a user's actions at risk.
• Poor password habits: Using weak passwords can put a user's information at risk.
• Lost or stolen devices: Lost or stolen devices can put a user's information at risk.
• Out of date operating systems: Not installing updates can put a user's device at risk.
To stay safe, travelers can:
• Use a VPN for remote working
• Avoid connecting to unknown Wi-Fi access points and Bluetooth devices
• Use private browsing
• Use Two-factor authentication (2FA): A security feature that reduces the risk of identity theft and hacker attacks
• Antivirus software: Regularly scans and eliminates threats like viruses, malware, spyware, and phishing scams
• Avoid unsecured public Wi-Fi
• Report theft promptly: If your device is stolen, report it promptly so IT administrators can restore it to its default settings
Week 4: Incident Response
What is Incident Response?
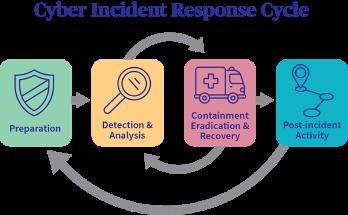
Incident response (IR) is the process for identifying and responding to cyberthreats, security breaches, or cyberattacks. The goal of IR is to restore operations, minimize damage, and learn how to prevent similar breaches in the future.
What are the basic steps for Incident Response
Step 1: Preparation and prevention
• Preparation is key to an effective response. Start by developing a policy for how you will manage your incident response, what actions must be prioritized, and who will lead incident handling.
• Prevention includes a defense in depth model and using safeguards to prevent an incident from occurring
Step 2: Detection and analysis
• Use the security safeguards in place to monitor your network. This way, you can quickly determine if your organization is vulnerable.
• Use analytics to measure the attack surface of your organization and implement continuous monitoring of potential risks
Step 3: Containment, eradication, and recovery
• During this step, the incident response team is focused on mitigating the effects of an incident.
• To understand what systems are affected, look to your security management tools for intelligence and indicators of compromise, then shut down or isolate these devices, address the root cause, and restore systems
Step 4: Post-incident activity
• After any cybersecurity incident, hold a postmortem meeting to discuss what happened and your organization’s response, including what worked, what didn’t, and what can be improved.
• Position it as an open and blameless forum for sharing lessons learned with senior leaders and stakeholders. Invite input and feedback on how the organization can be better prepared if or when another incident occurs.
Step 5: Test your incident response process
• Don’t wait until an incident occurs to test your incident response plan.
• Conduct regular drills and simulation exercises.
• Continue working on your cyber-resilience.