



We have developed quality product and state-of-art service to ensure our customers interest. If you have any suggestions, please feel free to contact us at feedback@dumpscafe.com
If you have any questions about our product, please provide the following items: exam code screenshot of the question login id/email please contact us at and our technical experts will provide support within 24 hours. support@dumpscafe.com



The product of each order has its own encryption code, so you should use it independently. Any unauthorized changes will inflict legal punishment. We reserve the right of final explanation for this statement.

Which PKI enrollment method allows the user to separate authentication and enrollment actions and also provides an option to specify HTTP/TFTP commands to perform file retrieval from the server? url terminal profile selfsigned
Answer: C
Reference:
https://www.cisco.com/c/en/us/support/docs/security-vpn/public-key-infrastructure-pki/211333-IOSPKI-Deployment-Guide-Initial-Design.html
Which deployment model is the most secure when considering risks to cloud adoption?
Public Cloud
Hybrid Cloud
Community Cloud
Private Cloud
Answer: D
Explanation

A private cloud is a cloud deployment model that is dedicated to a single organization and provides exclusive access to its resources and services. A private cloud can be hosted on-premises or off-premises by a third-party provider, but in either case, the organization has full control and visibility over the security, privacy, and compliance of its data and applications. A private cloud can also leverage the security features and best practices of the public cloud service provider, if applicable, while maintaining a higher degree of isolation and customization. A private cloud is the most secure deployment model when considering risks to cloud adoption, as it minimizes the exposure of sensitive data to external threats, reduces the dependency on the security posture of the cloud service provider, and enables the organization to meet its specific security and regulatory requirements123. References: 1: Best Practices to Manage Risks in the Cloud - ISACA 2: Security in the Microsoft Cloud Adoption Framework for Azure 3: Five challenges to cloud adoption and how to overcome them - PwC Middle East
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a recipient address. Which list contains the allowed recipient addresses?
Answer: D
Explanation
The RAT (Recipient Access Table) is the list that contains the allowed recipient addresses on the Cisco ESA. The RAT controls whether the ESA accepts or rejects messages to a recipient address based on the sender group and the mail policy. The RAT can be configured to allow, relay, or reject messages to specific recipients or domains. The RAT can also be used to apply different message filters or content filters to different recipient groups12. References: 1: Implementing and Operating Cisco Security Core Technologies (SCOR) course, Module 2: Network Security, Lesson 3: Deploying Cisco Email Security Appliance, Topic: Configuring Mail Policies2: Cisco Email Security Appliance User Guide, Release 13.5 - Configuring Mail Policies [Cisco Secure Email Gateway] - Cisco.
An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA. Which Cisco ASA command must be used?

flow-export destination inside 1.1.1.1 2055
ip flow monitor input
ip flow-export destination 1.1.1.1 2055 flow exporter
Answer: A
Reference:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/monitor_nsel.html
Which Cisco security solution provides patch management in the cloud?
Cisco Umbrella
Cisco ISE
Cisco CloudLock
Cisco Tetration
Answer: D
Explanation

Cisco Tetration is a Cisco security solution that provides patch management in the cloud. Patch management is the process of identifying, acquiring, installing, and verifying patches for products and systems to correct security and functionality problems in software and firmware1. Cisco Tetration is a cloud-native platform that delivers comprehensive workload protection for multicloud data centers by enabling a zero-trust model using segmentation2. One of the features of Cisco Tetration is software vulnerability detection and patch management, which allows users to identify software vulnerabilities on workloads, prioritize patching based on risk scores, and automate patch deployment using orchestration tools3. Cisco Tetration leverages the National Vulnerability Database (NVD) and Cisco Talos Intelligence Group to provide up-to-date information on software vulnerabilities and their severity levels3. Cisco Tetration also supports patch management for both Windows and Linux operating systems, as well as third-party applications such as Apache, Java, MySQL, and Oracle4. Therefore, the correct answer is D. Cisco Tetration. References: 1: RFC 9232: Network Telemetry Framework - Internet Engineering Task Force 2: Cisco Tetration - Workload Protection - Cisco 3: Cisco Tetration Software Vulnerability Detection and Patch Management - Cisco 4: Cisco Tetration Platform Data Sheet - Cisco
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices The default management port conflicts with other communications on the network and must be changed What must be done to ensure that all devices can communicate together?
Set the sftunnel to go through the Cisco FTD
Change the management port on Cisco FMC so that it pushes the change to all managed Cisco FTD devices
Set the sftunnel port to 8305.
Manually change the management port on Cisco FMC and all managed Cisco FTD devices
Answer: D
The management port on Cisco FMC is used to establish a secure connection with the managed Cisco FTD devices. If the default management port (8305) conflicts with other communications on the network, it must be changed on both the Cisco FMC and the Cisco FTD devices. This cannot be done automatically by the Cisco FMC, as it would lose connectivity with the devices. Therefore, the administrator must manually change the management port on the Cisco FMC and all the managed Cisco FTD devices using the command line interface (CLI). The steps to change the management port are as follows:





Log into the CLI of the Cisco FMC and the Cisco FTD devices using a console connection or SSH.
Enter the configure network {ipv4 | ipv6} manual ip_address netmask data-interfaces command to change the management port on the Cisco FMC. For example, configure network ipv4 manual 10.10.10.10 255.255.255.0 data-interfaces changes the management port to 10.10.10.10/24.
Enter the configure network {ipv4 | ipv6} manual ip_address netmask gateway management-only command to change the management port on the Cisco FTD devices. For example, configure network ipv4 manual 10.10.10.11 255.255.255.0 10.10.10.10 management-only changes the management port to 10.10.10.11/24 and sets the gateway to the Cisco FMC’s management port.
Save the configuration and restart the Cisco FMC and the Cisco FTD devices.
Verify the connectivity between the Cisco FMC and the Cisco FTD devices using the show managers command on the Cisco FTD devices and the show devices command on the Cisco FMC.
References :=




Firepower Management Center Device Configuration Guide, 7.1 - Device Management
Change management port fmc 1600 - Cisco Community

Solved: FMC 2120 FTD Management Only Port - Cisco Community
Change the FMC Access Interface from Management to Data
Question #:7 - (Exam Topic 3)
Which attribute has the ability to change during the RADIUS CoA? NTP
Authorization Accessibility
Membership
Answer: B
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_aaa/configuration/15-sy/sec-usr-aaa-15-sy-book/sec-rad-coa.html
What are two features of NetFlow flow monitoring? (Choose two)
Can track ingress and egress information
Include the flow record and the flow importer
Copies all ingress flow information to an interface
Does not required packet sampling on interfaces
E.
Can be used to track multicast, MPLS, or bridged traffic
Answer: A E
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/netflow/configuration/15-mt/nf-15-mt-book/cfgmpls-netflow.html

An organization received a large amount of SPAM messages over a short time period. In order to take action on the messages, it must be determined how harmful the messages are and this needs to happen dynamically. What must be configured to accomplish this?
Configure the Cisco WSA to modify policies based on the traffic seen
Configure the Cisco ESA to receive real-time updates from Talos
Configure the Cisco WSA to receive real-time updates from Talos
D.
Configure the Cisco ESA to modify policies based on the traffic seen
Answer: D
Explanation
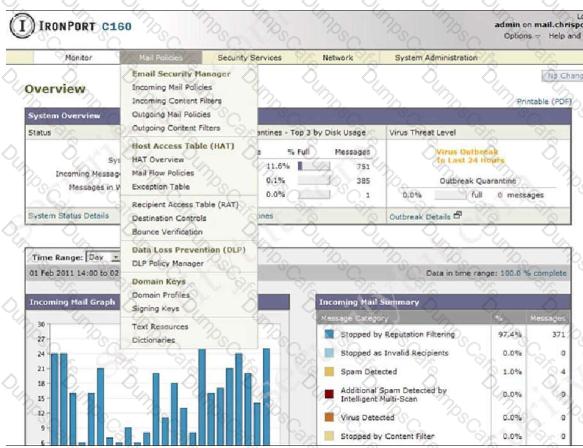
ExplanationExplanationThe Mail Policies menu is where almost all of the controls related to email filtering happens. All the security and content filtering policies are set here, so it’s likely that, as an ESA administrator, the pages on this menu are where you are likely to spend most of your time.

An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the organization to create a policy to control application specific activity. After enabling the AVC engine, what must be done to implement this?

Use security services to configure the traffic monitor, .
Use URL categorization to prevent the application traffic.
Use an access policy group to configure application control settings.
Use web security reporting to validate engine functionality
Answer: C
Explanation
ExplanationExplanationThe Application Visibility and Control (AVC) engine lets you create policies to control application activity on the network without having to fully understand the underlying technology of each application. You can configure application control settings in Access Policy groups. You can block or allow applications individually or according to application type. You can also apply controls to particular application types.
dumpscafe.com was founded in 2007. We provide latest & high quality IT / Business Certification Training Exam Questions, Study Guides, Practice Tests.
We help you pass any IT / Business Certification Exams with 100% Pass Guaranteed or Full Refund. Especially Cisco, CompTIA, Citrix, EMC, HP, Oracle, VMware, Juniper, Check Point, LPI, Nortel, EXIN and so on.
View list of all certification exams: All vendors












We prepare state-of-the art practice tests for certification exams. You can reach us at any of the email addresses listed below.



Sales: sales@dumpscafe.com
Feedback: feedback@dumpscafe.com
Support: support@dumpscafe.com
Any problems about IT certification or our products, You can write us back and we will get back to you within 24 hours.