April
From “Network Security” to a “Secure Network” with Arista



April
From “Network Security” to a “Secure Network” with Arista




New opportunities and vulnerabilities come with connected technologies. There is a lack of visibility in current security solutions, leaving the organization open to potential attacks. Reactionary bolt-on security measures cannot mitigate continuously evolving cyber threats and instead add operational burdens and cost. To keep their networks safe, organizations need security to permeate everything.
Read more
Undetected Threats: There are many modern threats that blend in with business-justified activities. Many of these threats however go undetected due to the focus on malware in traditional security tools
Narrow Insights: Analysts must piece together a trail of breadcrumbs left by traditional security systems throughout the attack.
Increased Vulnerabilities: The enterprise can become extremely vulnerable to cyberattacks if the enterprise security team cannot see every threat, detect malicious intent, or gather insight to respond.

Read more


Arista Networks has embedded network detection and response security software into its campus switches to provide AI-driven threat protection across the campus network.

“The software-based upgrade will also offer network detection and response (NDR) visibility without deploying additional hardware. Arista's software approach simplifies NDR deployments and effectively turns the entire network into a security sensor”.
- Zeus Kerravala, Founder, ZK Research

Arista NDR has exceeded our expectations and empowered us to secure our connected workplace more effectively and autonomously than ever.






 - Gary Golomb
- Gary Golomb
Candidates must understand the evolving technical characteristics of the threat landscape as well as tools and strategies for defending against and investigating these threats. This post walks you through the PCAP, CTF, discusses the skills evaluated, and explains the theory behind each test. Read the blog


 - Kieran Evans
- Kieran Evans
jjjj
Awake Labs' team of security experts has a unique perspective on how threat actors attempt to access our client’s networks and what they plan to do with them. This post highlights how a threat actor exploited an older Atlassian vulnerability to gain access to an external-facing client's server and run cryptocurrency mining malware.
Read the blog

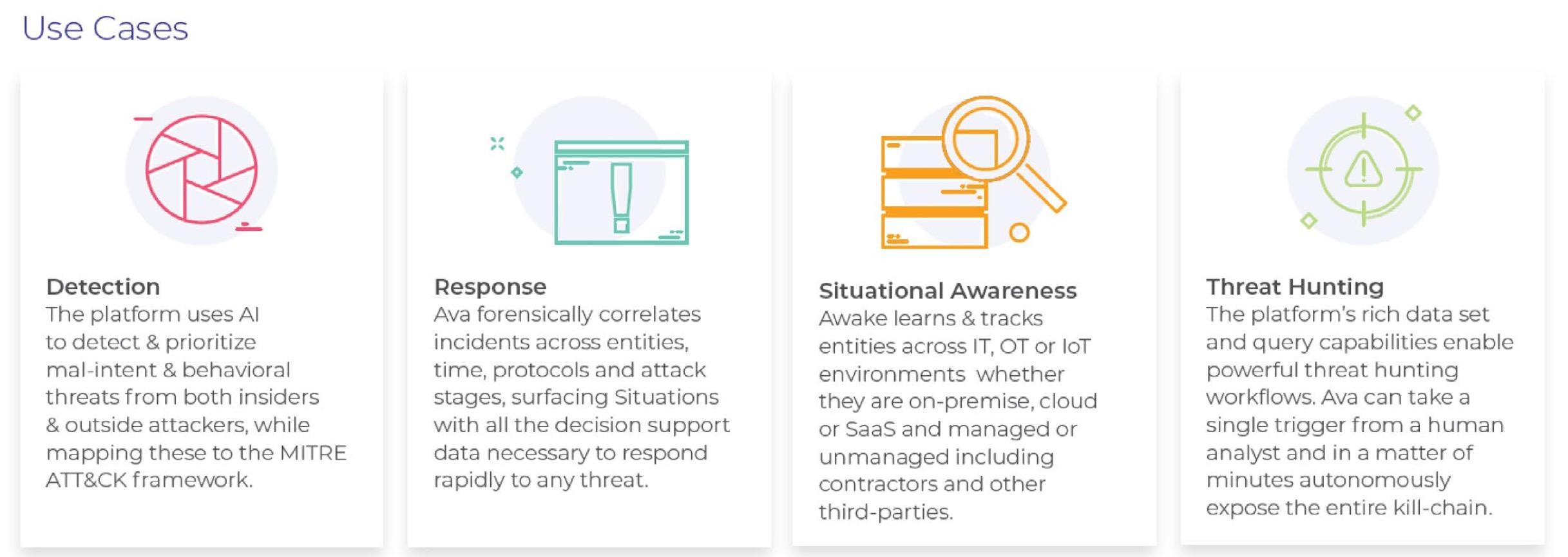


Did you know Arista’s Network Detection and Response (NDR) can protect you from insider threats and ransomware?
Using artificial intelligence, Arista NDR hunts for adversarial behaviors and delivers threat detections with low false positives and negatives while also providing the context necessary for triage, incident response, and remediation.
Come see how we do security at the Arista booth #1443 at RSA 2023!

Register here Join Arista Security Team at RSA Conference 2023 9

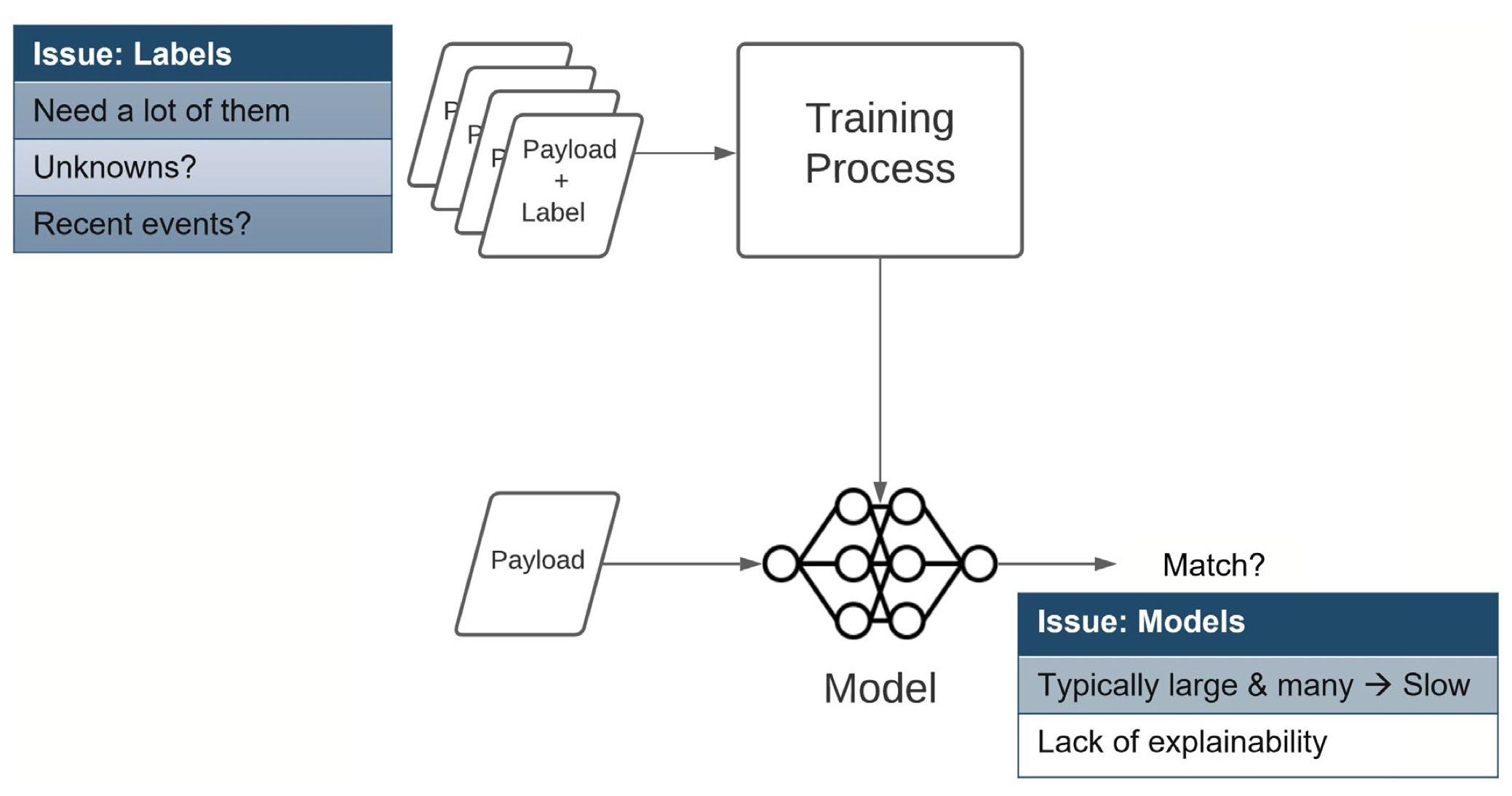

An employee at a large media and entertainment company was caught selling extremely sensitive intellectual property to a third party. This type of activity is especially hard to detect using traditional tools such as threshold-based solutions that look for large or anomalous uploads. In this case, the files were sent infrequently, and when they were sent, the amount of data traversing the network was very small. Read the use case to learn more about it.

Organizations looking to build a robust cybersecurity program need to start at the network layer. Network traffic reveals hidden threats with high fidelity and offers a unique vantage point for threat detection and response.
Arista’s zero trust security portfolio eliminates the need for several network monitoring or security tools by delivering a unified architecture that provides real-time visibility to the threat posture across the network with the ability to take immediate action.

See the power of Arista NDR with a short to-the-point demo.

Schedule a demo

Follow us!



