ISSN2050-6732(Print)
ISSN2050-6740(Online)
UNDERSTANDINGANDTHREATALIGNMENTWITHINAC-IEDENTERPRISE
IEDCLASSIFICATION–BREAKINGDOWNBOMBATTACKS
AJOURNEYTHROUGHPIECESOFSPICEPIES WHATCOMPONENTSMAKEUPANIED–TECHNICALCOMPONENTCLASSIFICATION “OLD?”C-IEDFORA“NEW?”ALLIEDCONCEPT: THEC-IEDAPPROACHINTHELIGHTOFNATOWARFAREDEVELOPMENTIMPERATIVES
IMPROVINGUNDERWATERCAPABILITIES: THEIMPACTOFARTIFICIALINTELLIGENCEONIEDDETECTIONANDIDENTIFICATION
INFRASTRUCTUREANDCOMMERCIALPROJECTS: EOCLEARANCEANDRISKMANAGEMENT LANDMINEREMOVALINPOST-CONFLICTAZERBAIJAN 2024-2025THREATDYNAMICS: PROLIFERATIONOFONLINEINSTRUCTIONSPOTENTIALLYSUPPORTINGTERRORISTATTACKS
EDITORIALANDTECHNOLOGYPARTNERS
Counter-IEDReport PublishedbyDeltaBusinessMediaLimited 167-169GreatPortlandStreet,5th Floor London,W1W5PF UnitedKingdom
Tel:+44(0)2071932303 info@deltabusinessmedia.com www.counteriedreport.com
ISSN2050-6732(Print) ISSN2050-6740(Online)
Theopinionsandviewsexpressedintheeditorialcontentinthisreportare thoseoftheauthorsaloneanddonotnecessarilyrepresenttheviewsofany organisationwithwhichtheymaybeassociated.Materialinadvertisements andpromotionalfeaturesmaybeconsideredtorepresenttheviewsofthe advertisersandpromoters.Theviewsandopinionsexpressedinthisreport donotnecessarilyexpresstheviewsofthepublisher.Whileeverycarehas beentakeninthepreparationofthereport,thepublisherisnotresponsible forsuchopinionsandviewsorforanyinaccuraciesinthearticles.
©2025.Theentirecontentsofthispublicationareprotectedbycopyright. Fulldetailsareavailablefromthepublisher.Allrightsreserved.Nopartofthis publicationmaybereproduced,storedinaretrievalsystemortransmittedin anyformorbyanymeans,electronic,mechanicalphotocopying,recording orotherwise,withoutthepriorpermissionofthecopyrightowner.
CONTENTS
IFCSMARTRAYVISION
5ICORTECHNOLOGY/MED-ENG
7NATOEODDEMONSTRATIONSANDTRIALS2025
8SAFEPROGROUPINC.
8VIDISCOLTD.
9FOREWORD
ByRobHyde-Bales,ConsultingEditor,Counter-IEDReport
11TELEDYNEICM
16COUNTERINGEXPLOSIVETHREAT&DEMININGCONFERENCE
17UNDERSTANDINGANDTHREATALIGNMENTWITHINAC-IED ENTERPRISE
ByPaulAmoroso,anexplosivehazardsspecialist atAssessedMitigationOptions(AMO)consultancy
25IEDCLASSIFICATION–BREAKINGDOWNBOMBATTACKS
ByPaulAmoroso,anexplosivehazardsspecialist atAssessedMitigationOptions(AMO)consultancy
33AJOURNEYTHROUGHPIECESOFSPICEPIES WHATCOMPONENTSMAKEUPANIED-TECHNICALCOMPONENT CLASSIFICATION
ByPaulAmoroso,anexplosivehazardsspecialist atAssessedMitigationOptions(AMO)consultancy
CONTENTS
41FUTUREFORCESEXHIBITION&FORUM2026
42EOD/ IED&COUNTERMINESYMPOSIUM
43“OLD?”C-IEDFORA“NEW?”ALLIEDCONCEPT:THEC-IED APPROACHINTHELIGHTOFNATOWARFAREDEVELOPMENT IMPERATIVES
ByLieutenantColonelJoseMRufas,ChiefofAttacktheNetworksBranch, C-IEDCentreofExcellence
51IMPROVINGUNDERWATERCAPABILITIES:THEIMPACTOF ARTIFICIALINTELLIGENCEONIEDDETECTIONANDIDENTIFICATION
ByMuratAydoğmuş,LieutenantCommander(OF-3)TUR-N, ElectronicWarfareSpecialist,C-IEDCentreofExcellence
57INFRASTRUCTUREANDCOMMERCIALPROJECTS: EOCLEARANCEANDRISKMANAGEMENT
ByDrRobertKeeley,RKConsulting(EOD)Ltd
72DEFENSE&SECURITYASIA2025
73LANDMINEREMOVALINPOST-CONFLICTAZERBAIJAN
ByWilderAlejandroSánchez,President,SecondFloorStrategies
792024-2025THREATDYNAMICS:PROLIFERATIONOFONLINE INSTRUCTIONSPOTENTIALLYSUPPORTINGTERRORISTATTACKS
ByLieutenantColonelJoseMRufas,ChiefofAttacktheNetworksBranch, C-IEDCentreofExcellence
87MILIPOLPARIS2025
OBCSCANNAMSCLTD
FOREWORD
ByRobHyde-Bales,ConsultingEditor,Counter-IEDReport
Aswecommemoratethe80thAnniversaryofthe endoftheSecondWorldWarinEuropeon8th May 2025,thebloodiestandthelargestwarintheworld’s recenthistory,confictcontinuesinmanyareasofthe world.InEuropewarhasreturnedafterRussia’s invasionofUkraineinFebruary2022.IntheMiddle East,IsraelremainsmiredinGazainitseffortsto defeatHamasafteritsattacksonIsraelinOctober 2023.Mostrecently,tensionshavefaredupagain betweenIndiaandPakistan–twonucleararmed nations–afterthedeathsofIndiantouristsatthe handsofsuspectedPakistanbasedmilitantsinthe disputedterritoryofKashmirinAprilthisyear.
EUROPE
Russia-Ukraineconfict
Oneofthemajorsourcesofconfictintheworldtoday remainsthebitterwarbetweenRussiaandUkraine.The initialconfictwhicherupted11yearsagoinDonbas regionwassparkedbyapoliticalunrestinUkraineand Russia'sannexationofCrimeaduringthepower vacuumintheweeksaftertheEuromaidanRevolution inMarch2014.Afterafull-scaleRussianinvasionin February2022,itremainsoneofthemostcomplexand defningissuesinworldpoliticstoday.Aftermorethan threeyearsofhostilities,Russianowoccupiessome 20%ofUkrainianterritoryincludingCrimea.
Asaresultofheavyfghting30%oftheUkrainian territoryispotentiallycontaminatedwithlandmines, unexplodedordnance(UXO),andimprovised explosivedevices(IEDs).Themostaffectedregions includeKharkiv,Kherson,Donetsk,Luhansk, Zaporizhzhia,andMykolaivregions.NGOslikeHALO Trust,MAG,andFSDareconductingclearance operationsinsaferareas.USA,EU,Japan,Canada, andotherinternationaldonorshaveprovidedfunding, equipment,andtraining;mineriskeducationisbeing rolledoutinschoolsandruralcommunities.Modern technologies,suchasdronesandremote-sensingare beingusedtomapminefeldsalongwithground-based roboticdeminingsystemsandmetaldetectors;AIassistedtoolsareusedtoimprovedetectionspeedand accuracyinclearanceoperations.IntheKurskregion ofRussia,whichbordersUkraine,deminingandUXO disposaloperationsarealsounderwayfollowingheavy fghtingduringUkraine’snine-monthsincursion.
SincethestartofRussia'sfull-scaleinvasionof Ukraine,therehavebeenanumberofhigh-profle assassinationsinRussiausingimprovisedexplosive devices.Thelatestincidentoccurredon25th April,when LieutenantGeneralYaroslavMoskalik,asenior Russianmilitaryoffcer,waskilledinasuburbeastof Moscowwhenanimprovisedexplosivedeviceflled withshrapnelwasconcealedinacarparkednearhis homeanddetonatedashewalkedpast.Thisattackis verysimilartotheonethattookplaceinDecember 2024inwhichLt.Gen.IgorKirillov,whoservedasthe commanderoftheRussianRadiological,Chemical,and BiologicalDefence,waskilledbyanexplosivedevice hiddeninsideanelectricscooter,whichwasleftnextto theentranceofthebuildingwhereLt.Gen.Kirillovlived.
Inanothernotableoperation,abatchofFPV(FirstPersonView)dronegogglessenttoRussianmilitary unitswereriggedwithexplosivesanddeliveredaspart of‘humanitarianaid’.Russianmilitarypersonnelnoticed signsoftamperingwiththepackages,leadingtoafurther inspectionandthediscoveryofconcealedexplosives. Eachdevicecontainedabout10-15gramsofexplosives, enoughtokillorseriouslyinjureaperson.
Severalroundsofindirectpeacetalksinitiatedbythe newlyelectedUSgovernment,sofarhavenot producedanytangibleresultsduetotheirreconcilable positionsofthewarringparties.Atthetimeofwriting, Kyivandwesternleaderscalledfora30-daypausein fghting.On11th May,Moscowproposedtoresume directnegotiationswithKyiv,whichwereinterrupted inApril2022.Itremainstobeseenwhetherthetalks (iftheytakeplace)willbeabletobridgethedifferences betweenthetwosidesandleadtoade-escalationof theconfict.
Ireland
Explosive-ladendroneshaveemergedasasignifcant securityconcerninIreland1,particularlyinthecontextof organisedcrimeandprisonsmuggling.Inthelatest development,Gardaíarecurrentlyinvestigatingwhat appearstobeanattempttodropapipebombfroma droneonahouseinnorthDublin.Thewreckageofthe droneandanintactpipebombwerefoundinthegarden ofahouseinGlentiesPark,Finglas,lateon4th May 2025afteritappearedtohavecrashedatthewrong address.Authoritiesareconcernedthatthegangland feudlinkedtotheincidentwillnowescalatesharply. Thesedevelopmentsrefectabroadertrendwhere criminalorganizationsareleveragingdronetechnology tocarryouttargetedattacksusingexplosives.
MIDDLEEAST
Israel–GazaConfict
IntheMiddleEast,IsraelremainsmiredinGazainits effortstoreleasetheremaininghostagesanddefeat
HamasafteritsattacksonIsraelinOctober2023.There areconfictingreportsofthenumberofhostagesinthe Hamascaptivity.Accordingtothelateststatementof IsraeliPrimeMinisterBenjaminNetanyahutherewas "uncertainty"overtheconditionofthreeofthe24 hostagespreviouslybelievedtobealive2.Amid continuationoftheongoinghostilitiesintheGazaStrip thereisagrowingconcernoverthehumanitarian situationandthepresenceofunexplodedordnance (UXO)whichposesaseriousthreattociviliansand humanitarianaideffortsfollowingintensemilitary operationsandbombardments.Inaddition,Gazalacks suffcientmineclearanceteams,accesstomodern deminingtechnologyandequipment,andtheongoing confictmakesitdiffculttoconductsurveysand explosivesclearanceoperations.
Yemencrisis
SinceIsraellaunchedamilitaryoffensiveagainstHamas intheGazaStripfollowingthePalestinianmilitant group’sdeadlyattackonIsraelon7th October2023,the Iran-backedHouthisinYemenhavesteppeduptheir militaryactions,particularlytargetingshippingintheRed SeaandIsraelimainland.
InanattempttokeepthevitalRedSeatraderoute open,theUnitedStatesandBritainhaverespondedwith airstrikesagainstHouthitargets,whileothercountries independentlypatrolthewatersnearYemen.TheIsraeli militaryhascarriedoutseveralairstrikesagainstHouthi weaponsfacilities, commandandcontrolcentres,and criticalinstallations,includingtheportofHodeidaand Yemen’smainairportinSanaa.On6th May2025,a ceasefreagreementbetweentheUnitedStatesandthe Houthiscameintoeffect,endingtheUSandUK airstrikes.TheHouthisagreedtostoptheirattackson shippingintheRedSea,howevertheystressedthatthe ceasefredoesnotapplytoIsrael“inanyway,shapeor form.”ItremainstobeseenwhethertheUS-Houthi ceasefrewillholdorwhetherIsraelcanforcethe Houthistostoptheirattacksthroughsustainedmilitary anddiplomaticefforts.
1 https://www.irishtimes.com/crime-law/2025/05/07/drone-pipe-bomb-incident-raises-concerns-of-serious-feud-escalation/ 2 https://www.bbc.co.uk/news/articles/c8d1pngdjzmo
Turkey
On1st May2025,theKurdistanWorkers'Party(PKK) declaredaceasefreafter40yearsofconfictwith Turkeythathavekilledtensofthousandsofpeople. ThePKK,whichisdesignatedaterroristgroupbythe UnitedStates,theEuropeanUnionandTurkey,called onAnkaratoreleaseitsleaderAbdullahOcalan,who hasbeenjailedsince1999.On12th May2025,ina historicmove,thePKKannouncedits plantodisbandanddisarm,potentially endingfourdecadesofconfictwith Turkey.Thelastsignifcantattack attributedtothePKKoccurredon23rd October2024,whentheytargetedthe TurkishAerospaceIndustries(TAI) headquartersnearAnkara.Theattack leftfvepeopledeadand22wounded.
Post-AssadSyria
Syriaiscurrentlydividedamong severalarmedgroupsandregional powers.HayatTahriral-Sham(HTS) controlsmuchofthewesternand centralpartsofthecountry,including Damascus,andhasinitiatedeffortsto unifyarmedfactionsunderanational defenceframework.TheSyrian DemocraticForces(SDF),aKurdishledalliance,maintainscontrolover north-easternSyriabuthasfaced pressurefromTurkish-backedSyrian NationalArmy(SNA)forces,leadingto ongoingclashesinareaslikeTalRifaat andManbij.TheIslamicState(ISIS) hasexploitedthepowervacuum carryingoutaround700attacksin 2024.ISIShasalsoattemptedtoincite sectarianviolence,includingplansto targetShiaholysites,whichwere thwartedbyHTSforces.Aseriesof masskillingsandmassacresagainst AlawitesoccurredinSyriafrom
6th to17th March2025,witharesurgenceinearlyApril. Overseveraldaysofthesustainedattacksinthe coastalareaofthecountryinTartus,Latakiaand Hamagovernorates,armedgroupskilledentire families,includingwomenandchildren3.TheUN HighCommissionerforHumanRights(OHCR) spokespersonThameenAl-Kheetansaidtheagency haddocumentedatleast111killings,thoughthetrue
3 https://edition.cnn.com/2025/03/12/middleeast/syria-sectarian-violence-un-ohcr-intl-hnk/index.html Go-Scan C-View
REAL-TIME X-RAY INSPECTION
→ Up and running in less than 90 seconds
→ Lightweight (less than 6.5 kg/14 lbs)
→ Wireless or cable driven
→ High quality imaging
→ Radiation shielding
→ Telescopic arm (up to 65 cm/26 in)
numberisbelievedtobefarhigher.Accordingtoawar monitor,thebloodshedsawmorethan800people killedinclashesbetweenarmedgroupsloyaltoBashar al-AssadandforcesloyaltothenewSyrianregime.
MineclearanceinSyriaremainsacriticaland urgenthumanitarianchallengein2025,asthecountry continuestograpplewiththelegacyofits14-yearcivil war.Internationalorganizations,includingTheHALO TrustandUNMAS,haveintensifedtheireffortsto addressthecontamination.UNMAShassurveyedover 83millionsq.mandremoved1,102explosive ordnanceitemsbetweenAugust2023andJanuary 2025,focusingonhigh-priorityareassuchasRural Damascus,Aleppo,andLatakia.Despitethese efforts,challengespersist,includinglimitedfunding, bureaucraticobstacles,andthevastscaleof contamination.TheSyrianNetworkforHumanRights (SNHR)hasdocumentedatleast3,521civiliandeaths duetolandmineexplosionssince2011.
SOUTHASIA
India–PakistanConfictinKashmir
TheIndia–PakistanconfictinKashmirisoneof thelongest-runningterritorialdisputesinmodern history,rootedinthepartitionofBritishIndiain 1947.Indian-administeredKashmirhasseena decades-longinsurgencywhichhasclaimed thousandsoflives.
InlateApril2025,tensionsbetweenIndiaand Pakistanescalateddramaticallyfollowingamilitant attackinIndian-administeredKashmirthatkilled28 civilians,mostlyHindutourists.Indiaattributedthe attacktoPakistan-basedmilitants,whichPakistan denies,andrespondedwithmissilestrikesagainst militantgroupsitclaimsarebackedbyPakistan.In response,Pakistanfredmultiplemissilesand launchedover50dronestowardsJammuand Kashmir,PunjabandRajasthan.TheUnitedStatesled effortstode-escalatetheconfict,resultinginIndiaand Pakistantoagreetoaceasefre,buttheriskoffurther escalationremainshigh,asthecountrieshave accusedeachotherofviolationsshortlyafterthe agreementcameintoforce.
JaffarExpressattackinPakistan
On11th March2025,theBalochistanLiberationArmy (BLA)attackedtheJaffarExpress,aPakistani passengertraintravelingthroughtheBolanPassin Balochistan,takingaround440passengershostage, includingasignifcantnumberofwomenandchildren. Theattackers,whowerereportedlyintouchwiththeir foreignhandlersinAfghanistanviasatellitephone, detonatedexplosivesintunnelsandonthetrain tracksbeforeopeningfreonthetrain,haltingitina mountainousareadiffcultforauthoritiestoreach.The terroristorganizationhadissueda48-hourultimatumto releasetheBalochpoliticalprisoners,threateningto executethehostages,althoughtheyhadalready releasedsomeofthem.Within30hours,securityforces killedall33militants,includingthesuicidebombers,and rescued354hostages.Theoperationleftatleast64 peopledead,including18soldiersand33attackers,and wounded38.TheBLAclaimedtohavekilled50security personneland214hostages,althoughthosefgures weredisputedbyPakistanioffcials.Thehijackingtook placeagainstthebackdropofalmostdailyIEDandgun attacksonthesecuritypersonnelandciviliansin BalochistanandKhyberPakhtunkhwaprovinces.
AFRICA
Sahel&LakeChadbasin
TheSahelcontinuestobeahotspotforextremist activity,accountingforoverhalfofallmilitantIslamist incidentsonthecontinent.GroupslikeJama’atNusrat al-Islamwal-Muslimin(JNIM)andtheIslamicStatein theGreaterSahara(ISGS)haveintensifedattacks, leadingtonearly11,000fatalitiesin2024alone.Since 2010,over1,600IED-relatedincidentshavebeen recordedacrosstheregion,resultinginatleast6,680 deathsandmorethan9,000injuries.Thesedevices havebeenusedtotargetsecurityforces,UN peacekeepers,andcivilians,particularlyincountries likeMali,BurkinaFaso,andNiger.Theproliferationof IEDshasalsoledtoenvironmentalcontaminationand signifcanteconomiclosses,impedingdevelopment effortsanddisplacingmillions.Inadequateborder controlsandregulatoryframeworksallowforthe
uncheckedmovementofIEDcomponentsandthe establishmentofmanufacturingnetworks.IntheLake Chadbasinwomenplayasignifcantroleintraffcking importantcomponentsandbomb-makingmaterials throughcheckpointsandacrossbordersbecausethey arerarelysubjectedtobodysearches4.TheBoko Haram,typicallyknownforitsconservativeviewson women’ssocialstatus,haspermittedwomengreater mobilitybecausetheyareawarewomenareusually abovesuspicionwithlawenforcementauthorities. WomenoftenconcealIEDcomponentsinvarious ways,suchasstrappingthemtotheirbacksdisguised as‘babies’,hidingtheminfour-litrebottlesor concealingcomponentsunderpillows.Oncepast checkpoints,womeneitherdeliverthecomponents directlytoremoteBokoHaramhideoutsordropthe productsoffatpre-designatedlocations,inthebushor onfarms,creatingadditionalchallengesforlaw enforcementandcounterterrorismeffortsintheregion.
Nigeria
In2024,Nigeriaexperienced197attacksfrom improvedexplosivedevices(IEDs)–anaverageof nearlyoneIEDattackeverytwodays. On8th May,an IEDexplosioninMafaLocalGovernmentAreaof BornoState,leftfvechildreninjured,oneofwhomlost ahand.Theexplosionoccurredwhenthechildren unknowinglytamperedwithanIEDdevice.On28th Aprilatleast26people,includingwomenandchildren, werekilledwhenvehiclesdetonatedbyIEDsplantedin Nigeria’snorth-easternBornoState.Thevictimswere travellinginvehiclesalongtheroadfromRannto GamboruNgala,whereBokoHaramterroristsplanted anumberofexplosivedevices.Inadditiontothe26 fatalities,threepeoplesustainedseriousinjuries.
TheNigerianNationalSecurityAdviser(NSA), MallamNuhuRibadu,hascalledfordevelopmentof effectivemechanisms5 toenhancetheabilitytoprevent andcountertheuseofIEDsbyterroristgroupsinWest Africa.Ribadusaidthatthethreatofterrorismknows
nobounds,addingthatitwasthroughcollaborative effortsbycriticalstakeholdersthattheycould effectivelyconfrontanddefeatthemenace.
On25th MarchCamerooniantroopsstationedin Wulgo,Nigeria,havebeenkilledinthejihadists’attack. AccordingtoAFP,theattackersusedrocket-propelled grenadesand‘armeddrones’toinfictheavycasualties. Theattack,oneoftheregion'sdeadliestincidentsin recentmonths,comesasarmedgroupsinwest Africapivottowardstheuseofcheap,recreational dronesmodifedintoone-way,explosives-ladenattack vehicles.ArmedgroupsinNigeriaandtheSahelhave longuseddronesforsurveillanceandflming propaganda,however,ashiftisunderwayasjihadists andseparatistsoutftthemforattacks.Jihadistgroups inMaliandBurkinaFasohaveclaimedtousedrones equippedtodropgrenadesfromabove,aswellas explosive-laden‘suicidedrones’thatcrashintotargets6
DEMININGEFFORTS
BosniaandHerzegovina
Accordingtotherecentreports,theArmedForcesof BosniaandHerzegovina(BiH)cleared903,326square metersoflandin2024aspartofongoingdemining efforts7.Intotal,over14.7millionsquaremetersofland werereturnedtocivilianuse,contributingtothe developmentandsafetyoflocalcommunities.Despite operationalchallenges,theArmedForcessuccessfully implemented61.28percentofthenationalmine actionplan.Deminingactivitiestookplaceacross18 municipalities,including13intheFederationofBiH and5inRepublikaSrpska.
Vietnam
MarkinganotherstepintheUSandVietnam’s decades-longefforttohealthescarsofwar,anew trainingrangeforexplosiveordnancedisposal(EOD) hasrecentlybeeninauguratedinHanoi’soutlying districtofBaVi.ThefacilitywasfundedbytheOffceof
4 https://enactafrica.org/enact-observer/under-the-radar-women-traffc-ied-parts-to-boko-haram
5 https://nannews.ng/2025/05/06/nsa-seeks-effective-mechanism-to-tackle-ieds-usage-by-terrorists/
6 https://www.msn.com/en-us/news/world/nigeria-sahel-militants-embrace-diy-drone-warfare/ar-AA1BLzq6
7 https://english.news.cn/europe/20250424/e84b9d702e2f414fbd81ec940c36992e/c.html
DefenceCooperation(ODC)undertheUSEmbassyin VietnamanddeliveredtotheVietnamNationalMine ActionCentre(VNMAC),aspartofVietnam’sNational MineActionProgrammeforthe2010–2025period, whichseekstoaddressthedeadlylegacyof unexplodedbombsandminesleftfromthewar.The two-hectarerangebrokegroundinJuly2024, supportedbyagrantofover700,000USDfromtheUS Government8
Cambodia
AccordingtoareportfromtheCambodianMineAction andVictimAssistanceAuthority(CMAA)releasedat theendofApril2025thenumberofpeopleinjuredor killedbylandminesdroppedby26%inthefrstfour monthsofthisyear9.Inanotherpositivedevelopment, on29th ApriltheKohKong’sBotumSakordistrict wasoffciallydeclaredmine-free10,beneftingabout 100,000residents,throughgrantaidfromtheIndian government.LyThuch,frstvicepresidentofthe CambodianMineActionandVictimAssistance Authority,expressedappreciationforIndia’ssupportin helpingthegovernmentaddressthedangersposedby landminesandexplosiveremnantsofwar.However,it wasalsoreportedthatnearlyhalfofallmineaccidents inCambodiaoverthepastdecadehaveoccurred outsideofoffciallyidentifedminefelds-analarming indicatorthatvastareasremainunsurveyed.
INTHISEDITION
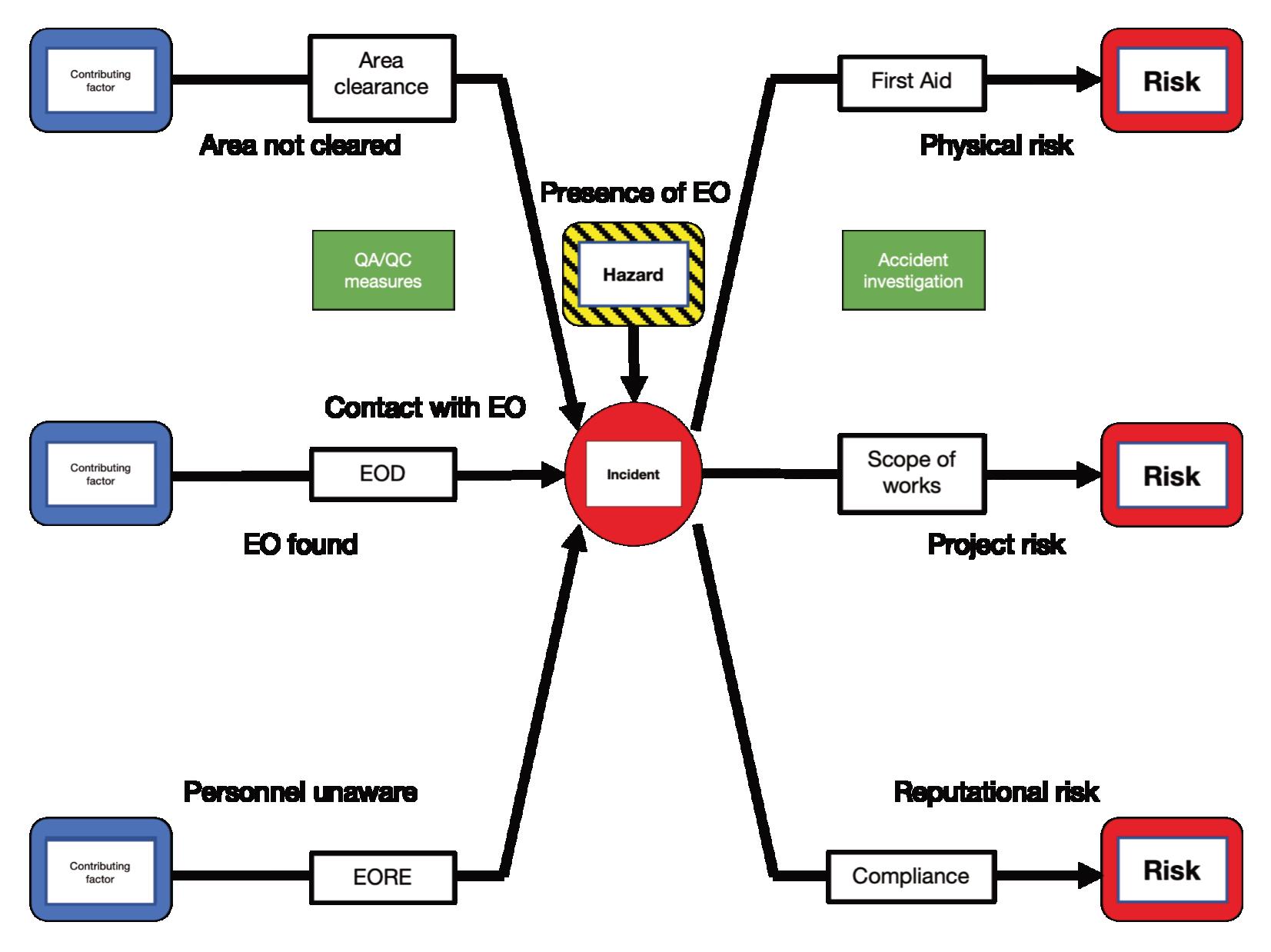
Inhiscomprehensivepaper“Infrastructureand commercialprojects:EOclearanceandrisk management,”DrRobertKeeleyofRKConsulting (EOD)Ltdoutlinesthedifferencesbetween humanitarianandcommercialperspectivesofmine actionandhowtheyinfuencetheattitudetoEO clearanceincommercialprojectsandinfrastructure.He beginsbydescribingtheUNguidingprinciplesof Neutrality,Humanity,Impartiality,andIndependence. Underthe1997APMBCand2008CCMconventions
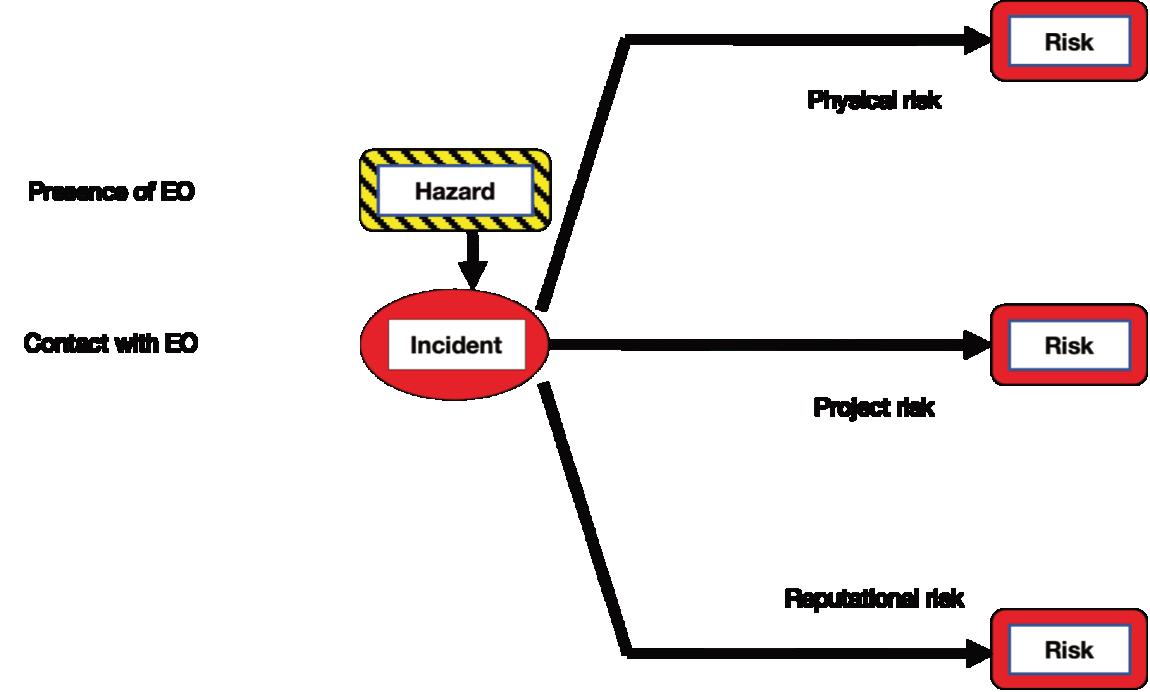
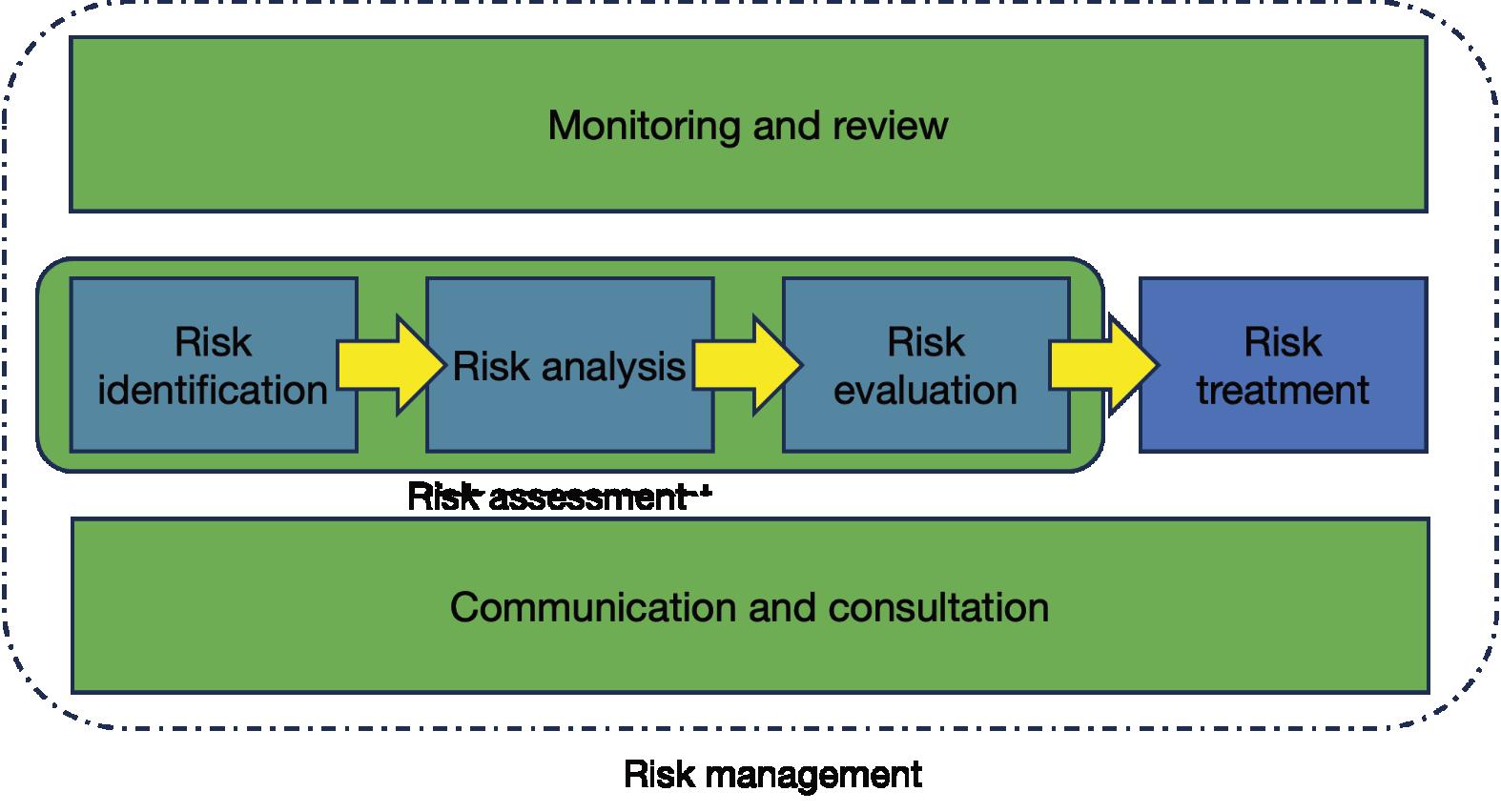
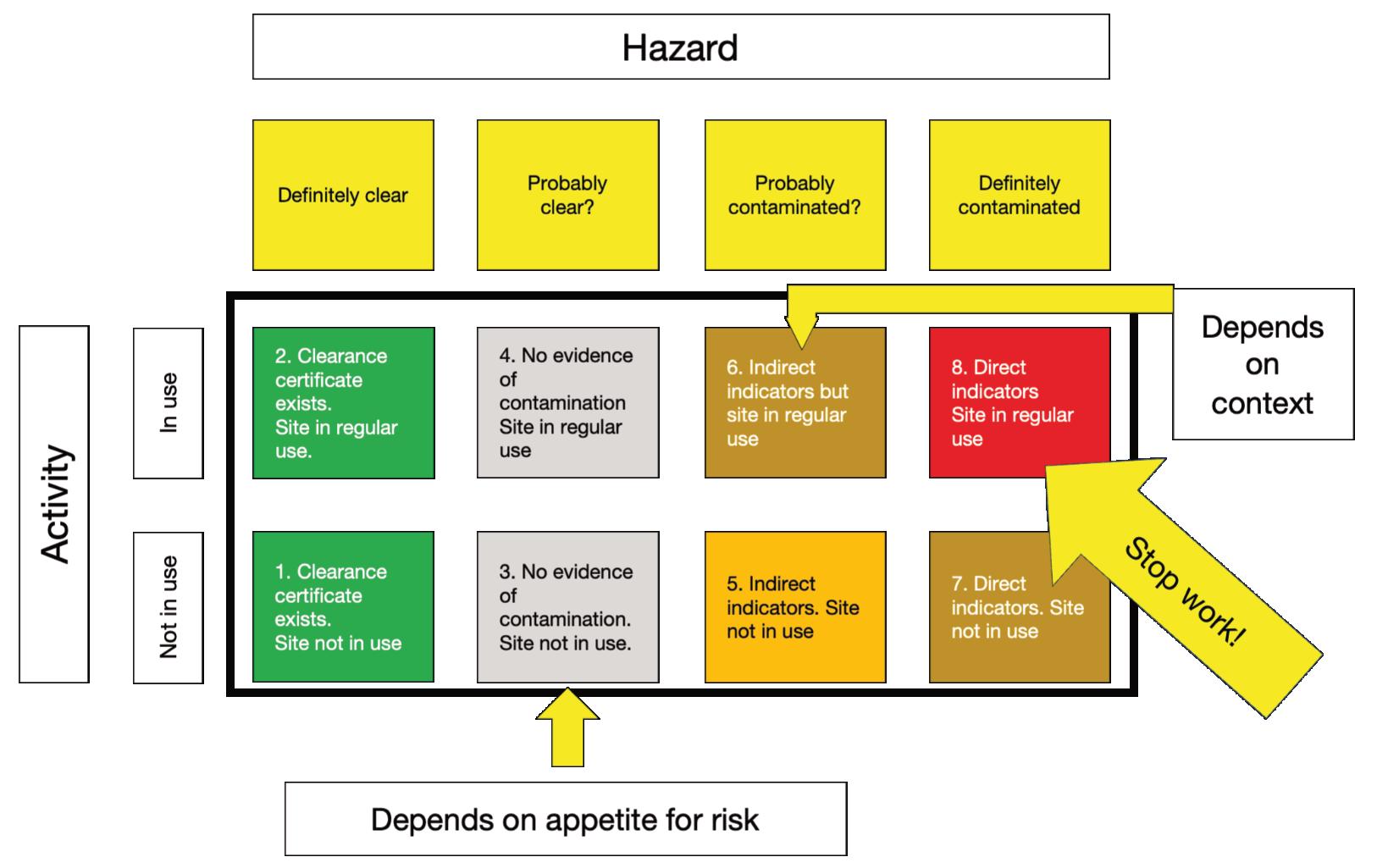
thereisarequirementforhumanitarianmineactionto clearallEOcontaminationwithinaprescribedarea, whereasincommercialprojectstherequirementisto clearEOspecifcallyrelevanttotheprojectinhand.He providesaformaldefnitionofrisk,attitudestoriskand potentialconsequences–physicalrisk,projectriskand reputationalrisk.IncommercialmineactionEO clearanceisseenasanenablertoallowthewidergoals oftheprojecttobeachieved.Hedescribestheoverall riskmanagementprocessandprovidesadetailed tableonrecommendedriskmanagement/treatment approachesfortheclearanceofcommercialproject sites.HeprovidesamostusefulSPRtabletoassistin theidentifcationofanappropriatemineaction intervention–‘S’beingtheSourceofthepotential hazard,‘P’isthePathway-theroutetothepotential hazardand‘R’istheReceptor–forexampleapersonor abuildingbenefttingfromtheclearance.Healso identifespossibleresponsestothehazard.
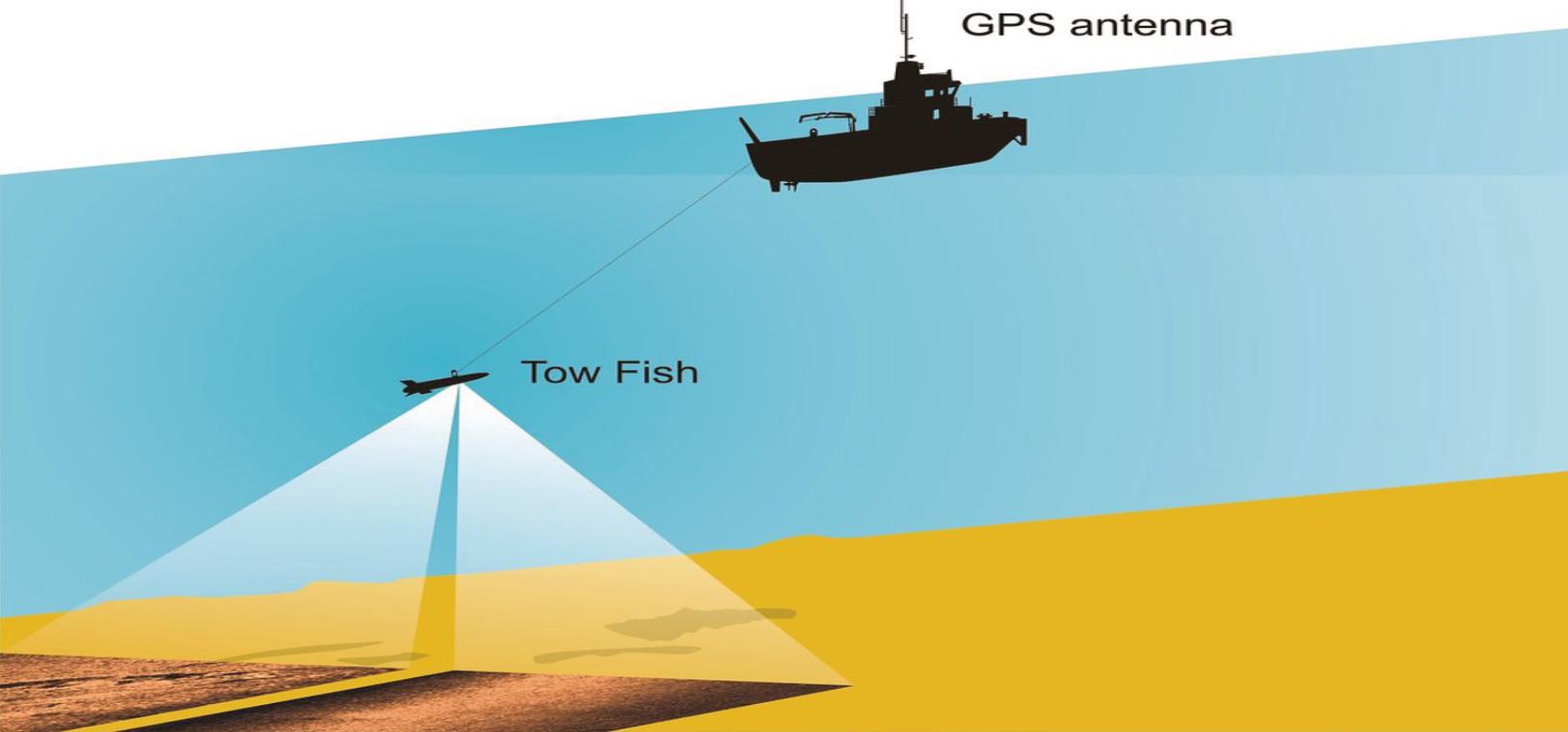
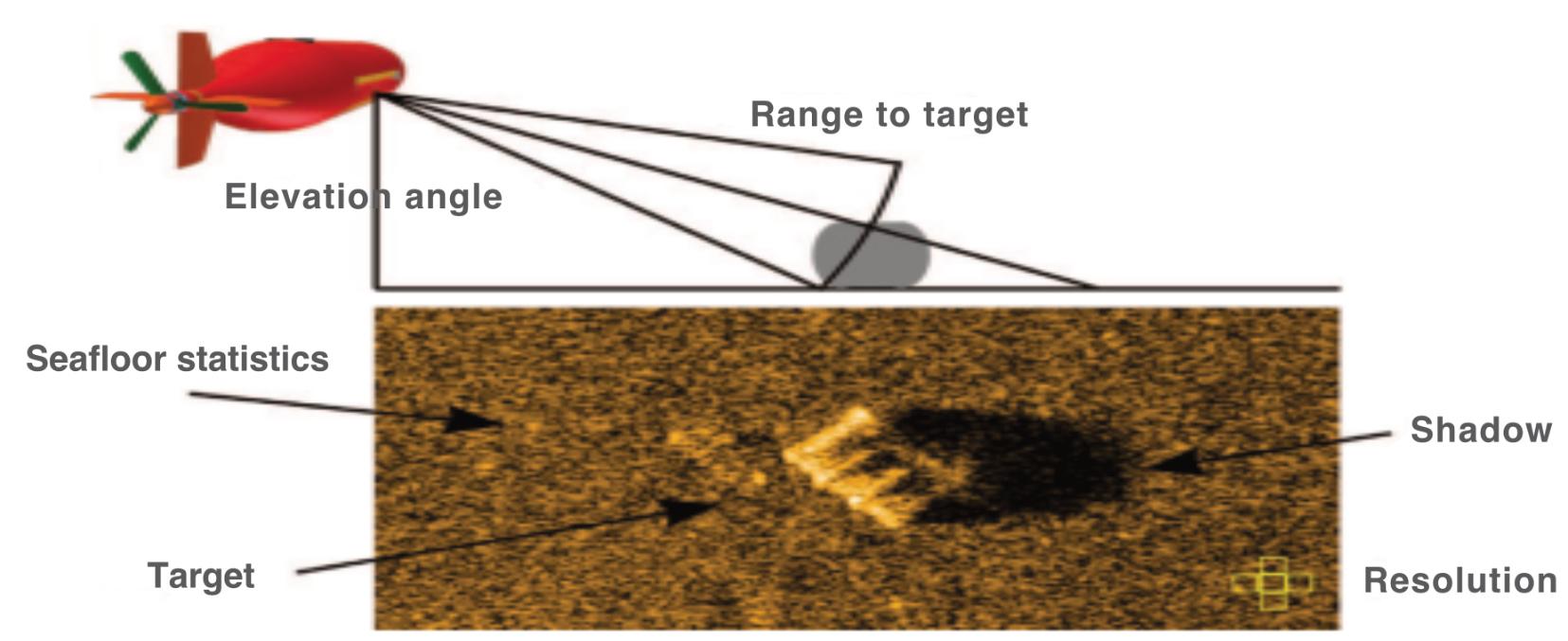
InhistechnicallydetailedarticleLieutenant CommanderMurat Aydogmus oftheTurkishNavyand basedattheNATOC-IEDCentreofExcellence, examinestheimpactofAIonunderwaterdetectionand identifcationofIEDsonorburiedintheseabed.He pointsoutthattheincreasingrelianceonnavaland offshoreassetsfortrade,energyproductionand defencemeansthattheunderwaterthreathasbecome acriticalconcernforglobalsecurity.HedescribeshowAI hasrevolutionisedunderwaterthreatdetection.He outlinestechnicalapproachestothreatdetectionsuch assonarscanning,magneticanomalydetection,diver inspectionandROVs.Hedescribestheoperationsof twosonarsystems,theSideScanSonar(SSS)and SyntheticApertureSonar(SAS).Bothsystemsproduce detailedimageryoftheunderwaterenvironment.The SSSisatowedsystemandemitssoundwaveswhich interactwiththeseafoorandobjectsonitorburiedinit, producinganacousticrefection.TheSASismounted onaUUVandmonitorsandrecordsbackscattered signalsfromtheseabed.Itproducesafnerresolution thantheSSSsystem.Magneticanomalydetectionuses
8 https://vietnamnet.vn/en/vn-us-boost-ties-with-new-uxo-disposal-training-site-launch-2398876.html
9 https://www.khmertimeskh.com/501675501/cmaa-reports-26-drop-in-mine-blast-victims-in-frst-quarter-of-year/
10 https://www.khmertimeskh.com/501674937/botum-sakor-district-in-koh-kong-to-be-declared-mine-free
asensitivemagnetometertodetectdisturbancesin theEarth’smagneticfeld.Forunderwaterdetection purposesitmaybeattachedtoships,UUVsoraircraft. TheintegrationofArtifcialIntelligenceintounderwater detectionsystemsenhancessituationalawareness, effciency,anddecision-makingcapabilities.
InawidelyresearchedarticleLtColJoseMRufasof theNATOC-IEDCentreofExcellencestatesthat despiteintenseeffortsbynationalandinternational authorities,theinternetremainsthemostprolifc sourceoftechnicalknowledgefortheplanningand preparationofterroristattacksduringthiscenturyto date.Itprovidesextensiveonlinedisseminationof manuals,videos,andinstructionsonthemanufactureof HMEandIEDs.Jihadistsandotherterroristsand extremistscansourceawealthofcontentdescribingthe planningofattacks,acquiringprecursorsand components,themanufactureofexplosivesandthe constructionofdevices.ThecurrentconfictinUkraine haswitnessedasignifcantuptickinthistypeofonline informationprovidedbysupportersofbothsidesofthe confict.TodatethisyearthemediaoffcesofDAESH/ ISIShaveportrayedanincreasingnumberof explosivesrelatedthreatsintheirpropagandaposters. Aworryingtrendduring2024and2025hasbeenthe increasingdiversityandlocationsofsourcesinaddition tothetraditionalArabicandEnglishlanguages information.Itisnowpossibletofndinformationin theBrazilian,German,Italian,Russian,Spanish,and Turkishlanguages.Afurtherconcernhasbeenthe reappearanceofhithertodormantsourcesofterrorist informationincluding,interalia,theDAESHrelated “AlSaqriFoundationforMilitaryScience”thatisonce againproducingawealthofterroristrelatedinformation. Itisassessedthattheongoingconfictcampaignin Ukrainewillcontinuetobeavaluablesourceof referenceforIEDmanufactureanddeployment.
InhisinformativearticleWilderAlejandroSanchez,an internationaldefenceandsecurityanalyst,reviewsthe currentstateoflandmineremovalinpost-confict Azerbaijan.TheAzerbaijanigovernmentiscurrently undertakingextensiveclearanceoflandmines,UXOand otherERWresultingfromthe2020and2023conficts betweenArmeniaandAzerbaijaninordertoreturnthe
contaminatedterritoriestocivilianandcommercialuse. ThecontaminationcomprisesbothAPandAV landminesandotherUXOandERW.TheMineAction AgencyoftheRepublicofAzerbaijanistaskedwiththe extensiveclearanceoperationsandhasmadegood progresstodate,butmuchmoreneedstobedone. Civiliansreturningtotheterritoryremaininperiland from2020to31st December2024therewere229 landmineexplosionsinKarabakhresultingin382 victimsand70fatalities.Azerbaijanwillrequire continuinginternationalassistancetodecontaminate Karabakhterritory.TodatetheUS,UK,EU,Canada, Japan,Turkey,UNHCR,UNDPandICRChaveprovided assistanceandGICHDhasprovidedsubstantial technicalassistanceincludingIMSMA.Apositive developmenthasbeentheinvolvementoffemale deminingteamsintheclearanceactivities.The decontaminationoftheKarabakhregionwillremaina long-termproject.■
RobHyde-Balesbiography
DuringhiscareerintheUKRoyal Engineers, RobHyde-Bales was responsibleforlandmineclearance inLibyaand,morelatterly, Afghanistanintherunningofthe frstUnitedNationshumanitarian landmineclearancetraining programme–OperationSalam. TheprogrammetrainedAfghanmalerefugeesin landmineclearancetechniques,andAfghanwomen andchildreninmineawarenessandavoidance training.MorerecentlyhesetuptheCaribbean SearchCentreinKingston,Jamaica.TheCentreis designedtotrainsecurityforcesacrosstheCaribbean inmodernsearchtechniques.Afterretiringfromthe armyhejoinedCranfeldUniversityatShrivenham, nearOxford,andundertookaresearchprojecton behalfoftheUKMinistryofDefencethatexamined waystoimprovethesharingofIEDthreatinformation betweenthemilitaryandcivilianorganisationsin hazardousareas.
The ONLY conference bringing together military, humanitarian groups, and industry leaders to discuss and improve operations in EOD and demining
23 - 24 September, 2025
Copthorne Tara Hotel, London, UK
Advancing EOD and C-IED Capabilities: Cooperation, Innovation, and Capacity Building
“The different perspectives across Military and NGOs were stimulating and good to see new industrial developments”
Senior Researcher, DSTL
Leading speakers from across the EOD and Demining Sector:
Colonel Darren Fisher, Commander, 29 EOD & Search Regiment
Stephen Ingram, Global Technical Advisor HMA, Mine Advisory Group
Brigadier General Jihad Al Bechelany, Director, Lebanese Mine Action Centre (LMAC)
Major Mark Fetters, Counter-Explosive Ordnance, Army Futures Directorate
View the agenda here
Georgina Darlow, Advisor in the Research and Innovation Programme, Geneva International Centre for Humanitarian Demining (GICHD)
UNDERSTANDINGANDTHREATALIGNMENT WITHINAC-IEDENTERPRISE
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy.
INTRODUCTION
InpreviousarticlespublishedinTheCounter-IED Report,theauthorhasadvocatedforawhole-ofsocietyapproach1 tocounteringtheuse orthreatened use ofIEDsthroughanationalCounter-IED (C-IED)enterprise.2 Suchapproachesnecessitatea coordinatedeffortamongstakeholderswithcomplex institutionalstructures,requiringinternalcoherence andcollaborationtoensureeffectiveC-IED strategies.Aclearandsharedunderstandingofthe IEDthreatisessentialtoeffectivelycoordinate C-IEDefforts,3 alignthemwiththespecifcthreat,
andoptimiseresourcesforbothrespondingtoand preventingtheiruse.Tobeeffective,anynational C-IEDenterprisemustfrstfullyunderstandthe problemitaimstocounter.Thisbeginswith recognizingthecurrentIEDthreatandanticipating potentialfuturethreats.Thisunderstandingofthe threatwillguidethestructureandcompositionofa C-IEDenterprise,requiringacarefulandstrategic selectionofstakeholderstoensureitseffectiveness. Itwillalsoinfuencetheenterprise’sstrategicgoal alongwiththeC-IEDeffortsinvestedinandtheir
1Awhole-of-societyapproachtoC-IEDisacomprehensiveapproachtoC-IEDinvolvingabroadarrayofstakeholders contributingtoaC-IEDenterprise.Itcanincludemultipleelementsofstatesecurity,defence,governmentdepartments, ministries,offces,andagenciesalongwithcivilsocietyorganisations,commercialandindustryentitiesaswellas internationalandregionalorganizations.Whole-of-societyC-IEDapproachesoftenhavestakeholderswithcomplex institutionalstructuresandproceduresrequiringinternalcoherence,acooperativeandcollaborativeculturebetween memberstosupporteffectiveC-IEDeffortsthroughasharedunderstandingoftheIEDthreatfaced.Source: Managinga C-IEDEnterprise,TheCounter-IEDReport,Winter2024/25.
2AC-IEDenterprisereferstothecollectiveeffortsaimedatcounteringIEDthreats.Itcaninvolveanythingwhichisintended topredict,discoverordetect,prevent,protectagainst,respondtoorneutralise,recoverfromorexploit,mitigateagainst,or deterIEDattacks.
3C-IEDeffortsmayberesponsive,preventativeorcross-cuttinginnature.Sucheffortsinclude,interalia,legalinstruments, training,mentoring,advice,operationalandtacticalortechnicalassistance,technologyandequipmentprovision,intelligence activities,investigationsandactionsagainstanIEDsystem,interagencyandinternationalcooperation,controlofexplosives andotherIEDcomponentsaswellasanyotherinvestmentmadetorespondtoandultimatelypreventIEDuse.Source: ManagingaC-IEDEnterprise,TheCounter-IEDReport,Winter2024/25.
objectives.Keyentitiescentraltounderstandingina C-IEDenterprisecanincludethenationalleadentity forC-IED,theOffceoftheNationalSecurityAdvisor, andvarioussecurityservices.4 Theimportanceofa designatedleadentity5 haspreviously6 been emphasized.Itisimportanttoremembernoonesize-fts-allandthebestfttoleadanynationalC-IED enterprisewillinvolveconsiderationofthecontext, limitationsimposed,andimportantlythethreat.7 The leadentitymustmonitorandadaptC-IEDeffortsto theevolvingthreatlandscape.
Understandingisacriticalcross-cuttingelement withinanyC-IEDenterpriseandonewhichhastwo aspectstoit.Oneisunderstandingthethreatand secondisunderstandingtheeffectivenessofthe C-IEDeffortsinvestedin.Thisarticlewillexplorethe conceptofunderstandingwithinaC-IEDenterprise andtheimportanceofaligningC-IEDeffortswiththe threat.Wewillbeginbyexaminingthesignifcanceof understandingwithinaC-IEDenterprise,highlighting itscriticalroleintheenterprise'ssuccessandthe potentialrisksthatarisefromitsabsence.Wewill thenexaminetheneedforandabilitytoachieve initialandsustainedunderstandingwithinthe enterprise.TheimportanceofaC-IEDenterprise remainingthreatalignedisshownbyexaminingits importancewhenpersonnelneedtooperateina highthreatIEDenvironment.Theevolutionofthe IEDthreathasanimpactacrossallelementsofthe enterprise,whichwillbeillustratedbyexaminingits importanceregardingIEDcomponentcontroland C-IEDbordercontrols.Thisisthefrstinaseriesof
articlesexamininghowtodevelopandsustain anaccurateIEDthreatpicturetooptimize understandingandensuretheC-IEDeffortsinvested inremaineffectiveasthreatsevolve.
UNDERSTANDINGWITHINAC-IEDENTERPRISE
ApreviousarticleinTheCounterIEDReport statedthat‘beforeyoucounteraproblem,youneed toknowtheproblem.’InthecaseofC-IEDthisrefers tounderstandingtheuseorthreateneduseof IEDs,sothatintimeeffectiveandeffcientC-IED effortsmaybeinvestedinaspartofaC-IED enterprisetoatleastmatchbutideallyovermatchthe IEDthreat.’8
Oneoftheffteenpreviously9 proposedelements toformthebasisforanynationalC-IEDenterprise, wasunderstanding.SecuritycentricC-IED frameworksoftenhaveunderstandingasthe foundationuponwhichthelinesofeffortofattackthe network,defeatthedevice,andtraintheforceare builtupon.10 Assuch,understandingwithinaC-IED enterpriseiscriticaltoeffectivelyrespondingto andultimatelypreventingIEDuse.Itcanbea challengingelementofanenterprisetogetright,as itinvolvesmorethanjusthavinginsightful comprehensionoftheIEDthreat.Italsorequiresa thoroughgraspofallelementsoftheenterpriseto evaluatetheeffectivenessofalleffortsinvestedin andtheoverallimpactoncounteringtheIEDthreat. Infact,“thekeyfundamentalC-IEDenablingaction of‘understanding’boththeproblemandtheC-IED effortsinvestedin,isdeemedessential.’11
4Source: BuildingtheC-IEDEnterprisetoCountertheIEDSystem,TheCounter-IEDReport,Winter2023/24.
5Inapreviousarticleofthispublication,ColonelHRNaiduGade,spokeoftheneedtodesignatewhatiscalledanodal agency,“tocoordinateandtrackprogressacrossalltheagenciesatnational,state,andlocallevelstowardbuildingtheC-IED capabilities.Itshouldfacilitateharnessingtheinnovativepotentialoftheresearchanddevelopmentorganizationstomeeta dynamic,complex,andadaptivethreatandtopromoteaninformedandagileresearchandacquisitionsprocessthatstays aheadofthethreatanddevelopstimelyandeffectiveC-IEDsystemsandsolutions.”Source: India–TheNationalCounterIEDStrategy,TheCounter-IEDReport,Winter2023/2024,byColonelHRNaiduGade(Retd),pp.40.
6 NecessityofaDesignatedLeadEntitywithinNationalC-IEDEnterprises,TheCounter-IEDReport,Spring/Summer2024.
7 NecessityofaDesignatedLeadEntitywithinNationalC-IEDEnterprises,TheCounter-IEDReport,Spring/Summer2024.
8 UnderstandingandMaximisingC-IEDInformationSharing,TheCounter-IEDReport,Autumn2023.
9 BuildingtheC-IEDEnterprisetoCountertheIEDSystem,TheCounter-IEDReport,Winter2023/24.
10Thesethreelinesofeffortarecapturedwithintheffteenelements,outlinedin BuildingtheC-IEDEnterprisetoCounterthe IEDSystem,TheCounter-IEDReport,Winter2023/24.
11 AStrategicPrinciplesApproachtoRegionalC-IEDEnterprises,TheCounterIEDReport,Spring/Summer2023.
‘Thecriticalityofunderstandinginsupportofany coherentC-IEDenterpriseisbothcross-cutting andmulti-dimensional,referringtotheneedto comprehendinteralia:
•WhyandhowIEDsareused;
•Useofappropriateterminology;
•WhatanationalC-IEDenterpriseentails;
•MaintaininganaccurateIEDthreatpicturefor effectiveC-IEDdecisionmaking;
•Roleandimportanceofexploitationinmaintaining anaccurateIEDthreatpicture;
•TimelyinformationsharingbetweenC-IED stakeholders;
•AppropriateclassifcationofC-IEDinformation.’12
Itrequiresbothaninitialassessmentofthethreat andabaselineassessmentofexistingC-IED elementswhichcanthenbeusedtoinformthe designanddevelopmentofaC-IEDenterprise.It subsequentlyrequireson-goingthreatassessment toensuretheC-IEDeffortsinvestedinremainthreat alignedalongwithanembeddedmonitoring, evaluation,andlearning(MEL)13 processtoinform anunderstandingoftheeffectivenessoftheC-IED elementsinvestedin.Assuch,asystemto maximiseinitialandon-goingunderstanding needstobedevelopedthroughinitialbaseline assessments,on-goingthreatassessmentand embeddingaMELprocesswithintheenterprise. Withathoroughunderstandingofthethreataswell asallofitselements,anenterpriseisbestpositioned toremainthreataligned,effective,andeffcient overtime.
EvolutionofThreatandEffectivenessofC-IED EffortsInvestedIn
Anotherarticlediscussingthemanagementofa C-IEDenterprise,outlinestheneedforC-IED activitiestobesynchronizedandunityofefforttobe achievedacrossitsconstituentC-IEDefforts.It stated‘thetemptationtopursueneatandclean synchronisationacrossC-IEDeffortsshouldbe avoided,especiallythatwhichisrigidandinfexible. Thereisoftenaneedtosimultaneouslyinvestin variousC-IEDefforts,eachwithdifferentpriorities. Overtime,theseinitialprioritisationrequirementswill change,necessitatingadaptationandfurther synchronisation.Thus,fexibilityisrequiredastherate atwhichvariousC-IEDeffortsmaturetobeing impactfulcanvary,thethreatcanevolve,andthe widersecurityenvironmentcanchange.’14 This evolutionoftheIEDthreat,variationinthe effectivenessofC-IEDefforts,andchangesinthe broadersecuritylandscapeindicatethatalthoughan accurateunderstandingmaybeachievedduringthe designanddevelopmentofanenterprise,this understandingwillinevitablyneedtoadaptovertime. Therefore,thereisaneedforbothinitialandsustained understandingtosupportaC-IEDenterprise.
TheRiskPosedbyaLackofUnderstanding Employingstrategicprinciplesinsupportofa regionallycoherentC-IEDenterprisehaspreviously beenproposed.15 Severalapproacheswere consideredindevelopingananalysisframeworkto facilitatetheidentifcationofsuchprinciples. Throughtheexaminationandcombinationoffour suchapproaches16 aseven-questionframework17
12 UnderstandingandMaximisingC-IEDInformationSharing, TheCounter-IEDReport,Autumn2023.
13‘MonitoringandevaluationwithinaC-IEDenterpriseinvolvesobservationanddocumentationoftheC-IEDeffortsinvested in,followedbythesubsequentevaluationoftheirimpactontheIEDthreat.Thisprocessofobservationandanalysisis intendedtoidentifylessonsforeachoftheC-IEDeffortsinvestedin.’Source: ManagingaC-IEDEnterprise, TheCounter-IED Report,Winter2024/ 25edition.
14 ManagingaC-IEDEnterprise, TheCounter-IEDReport,Winter2024/ 25edition.
15 AStrategicPrinciplesApproachtoRegionalC-IEDEnterprises, TheCounter-IEDReport,Spring/Summer2023.
16Thesefourapproachesinvolvedidentifyingends,waysandmeans;consideringthesituation,task,execution,authority,and supportdemands;examiningwhat,why,who,where,whenandhow(5W+H)oftheproblem;andagenericsetofseven questionswhichmaybeappliedtoanyplanningscenariowhichisadaptedfromthemilitarysevenquestionestimate.
wasdevelopedtoidentifyoptimalC-IEDstrategic principlesforagivenIEDaffectedstateorregion,18 toachievetherequiredimpactsandoutcomesfrom C-IEDdonorassistance.19 Thisseven-question frameworkcanequallybeappliedasamethodology toestablishwhatC-IEDeffortsneedtobeinvested inbyanationalenterprise.Withtheproblem statementknown,20 thesevenquestionframework21 posesthefollowingquestionsintermsofcountering theuseandthreateneduseofIEDs.
1.Whatend-stateisdesired
2.Whatactionsaretobetaken?
3.Whoaretotaketheactions?
4.Whenaretheactionstobetaken?
5.Wherearetheactionstobetaken?
6.Whatrisksneedtobemanaged?
7.Whatresourcesdotheactionsrequire?
Thequestionof‘whatrisksneedtobemanaged’ hastwoaspectstoit;namely,whatwilloptimizethe likelihoodofsuccessofanationalC-IEDenterprise
andsecondlywhatrisksneedtobemitigatedagainst. Fiverecurrentriskswereidentifedwiththefrst22 beingalackofunderstandingwithintheC-IED enterprise.Assuch,notonlyisunderstanding essentialforaC-IEDenterprisetobeeffective,buta lackofunderstandingalsoposesarisktoitbeing effectiveandultimatelyasuccessbutalsooftenleads toawasteofoftenvaluableresources.
Theriskarisingfromalackofunderstandingcan beminimizedthroughfourkeysteps:conductingan initialthreatassessment,establishingabaseline evaluationofexistingC-IEDefforts,maintaining ongoingthreatassessments,andintegratinga structuredMELprocessintotheC-IEDenterprise. Assuch,understandingwithintheC-IEDenterprise occursattwocriticaljunctures:initiallyandon anongoingbasistosustainanaccurate understanding.WhenthisisdonetheC-IEDefforts investedincanremainthreataligned,andtheir effectivenesscanbemonitoredandadjustedas requiredwhenneeded.
17Theseven-questionframeworkpresentedpreviouslyusessevenquestionstoestablishwhatC-IEDstrategicprinciples bestsuitagivenIEDaffectedregiontoachievetherequiredimpactsandoutcomesfromC-IEDdonorassistance;however, itcanequallybeappliedasmethodologytoestablishwhatC-IEDeffortsneedtobeinvestedinbyanationalC-IED enterprise.
18Suchprinciplescanserveasthefoundationforreasoninganddecision-makingabouthowIEDaffectedstates,their regionalorganisations,andinternationalorganisationsprovidingC-IEDdonorassistancecanrespondstrategicallytothe threatposedbyIEDs.ThedesiredendstateforsuchprinciplesisthattheysupportthedevelopmentofcoherentC-IED enterprisestoatleastmatch,butideallyovermatch,thethreatposedbyIEDs.Source: C-IEDStrategicPrinciplesforEast Africa,TheCounter-IEDReport,Autumn2023.
19C-IEDdonorassistancereferstoC-IEDsupportprovidedonabilateralbasis,onajointinitiativefromtwoormoreStates orbyaninternationalorganisation,e.g.,EU,LeagueofArabStates,ECOWASetcoranalliancee.g.NATO,toanIED affectedstateorregion.Source: IsImplementationofWesternC-IEDEnterprisesSuitableWhenProvidingDonorC-IED Assistance,TheCounter-IEDReport,Spring/Summer2023; C-IEDStrategicPrinciplesforEastAfrica,TheCounter-IED Report,Autumn2023; NecessityofaDesignatedLeadEntitywithinNationalC-IEDEnterprises,TheCounter-IEDReport, Spring/Summer2024.
20Inthedevelopmentoftheseven-questionframeworkthestartingpointwasconsiderationof‘whatisthesituationandhow doesitaffectus?’Thisprovidestheproblemstatementbeingaddressed.Inthiscase,wehavethestartingassumptionthat anIEDthreatexistsinagivenregion,stateorlocalityrequiringanIEDaffectedstateornumberofstatestoengageinaCIEDenterprise.Asthisproblemstatementisknown,nosuchquestionneedstobeincludedintheanalysis.
21ThisframeworkusessevenquestionstoestablishwhatC-IEDstrategicprinciplesbestsuitagivenIEDaffectedregionto achievetherequiredimpactsandoutcomesfromC-IEDdonorassistance.
22Othersincluded,lackofcoherence,coordinationandcooperationoftenleadingtounnecessarycompetitionandwasteof resourcesamongststakeholders;lackofpowerofenforcementtocompelstakeholderstoengageeffectivelyintheC-IED enterprise;andfnally,theriskofsomeC-IEDeffortshavingnegativecounterproductiveeffectswhichoveralldamagethe C-IEDenterprise.
INITIALUNDERSTANDING
DuringthedesignanddevelopmentofaC-IED enterprise,itisnecessarytoundertakeaninitial IEDthreatassessmentaswellasabaseline assessment23 ofthematurityorlackthereof,of existingC-IEDeffortsbeinginvestedin.
InitiallyAssessingtheIEDThreat
Itisessentialtohaveaclearunderstandingofthe IEDthreatwhendesigninganddevelopingaC-IED enterprise,toensurethattheenterpriseisaligned withthespecifcthreatfromthebeginning.The methodologyadoptedoradaptedforthisinitialIED threatassessmentisthefocusofaseriesofarticles throughout2025.
AssessingExistingC-IEDCapabilities
Initial‘understandingisinformedbyabaseline assessment,whichcomparescurrentC-IED capabilitiestothoserequiredtoachievetheplanned C-IEDenterprise.’24 Suchabaselineassessment candetermine‘thematurityorlackthereof,ofthe keyelementswhichcontributetoaC-IED enterprise.’25 Theseven-questionsframeworkcan beadaptedtodeterminethemosteffectiveC-IED effortsfortheenterprisetoinvestin.Theseefforts canthenbeevaluatedagainstcurrenteffortsto identifythenecessarylevelofinvestmenttoachieve thedesiredoutcomes.Thisprocessmayalso highlightnewC-IEDeffortsthatrequireinvestment. Amorecommonapproachtoundertakinga nationalC-IEDbaselineassessmentistousethe UNIDIRC-IEDCMMself-assessmenttool26 or adaptationsofthis.
SUSTAINEDUNDERSTANDING
Oncethefndingsoftheinitialthreatassessmentand baselineassessmentareassimilatedintoaC-IED enterprise,themostappropriateC-IEDeffortscanbe investedinandprioritizedaspartofabroader strategicplan.Onceoperationalized,theC-IED enterpriseneedstobemanagedwiththeobjectives ofremainingthreataligned,effectiveandeffcient, which‘collectivelypresentachallengetotypical linear,rigidmanagementpractices,necessitatingthe needforfexibility.’27 AfexibleC-IEDenterpriseisone thatisagile28 thatcaneffectivelyrespondtoand ultimatelypreventIEDincidents. Oneofthe15 elementsproposedasthebasisforaC-IED enterpriseisadaptingC-IEDefforts.Adaptationofthe enterpriseisnecessaryowingtotheevolutionofthe threatandchangesintheeffectivenessoftheC-IED effortsinvestedin.Tosupportsuchadaptation,there isaneedforinternalmechanismstomonitor,evaluate andfeedbacklessonsidentifedintotheenterprisein relationtoboththeIEDthreatasitevolvesaswellas theeffectivenessoftheC-IEDeffortsinvestedin.
EvaluatingEffectivenessandAdaptation
IntegratingaMonitoring,Evaluation,andLearning (MEL)processwithintheC-IEDenterpriseservesasa tooltoassessandimprovetheeffectivenessofC-IED efforts.Itenablestheidentifcationoflessonsthat guidenecessaryadaptationstoenhanceimpact. Additionally,theMELprocessstrengthensoversightby trackingtheprogressofC-IEDinitiatives,ensuringthey remainalignedwithobjectivesorhighlightingareas requiringadjustment. This,inturn,cancontributetoa moreeffcientC-IEDenterprisebyoptimizingtheuse
23 PhaseswithinaC-IEDEnterprise,TheCounter-IEDReport,Autumn2024.
24 BuildingtheC-IEDEnterprisetoCountertheIEDSystem,TheCounter-IEDReport,Winter2023/24.
25 AConceptualFrameworkforC-IEDEnterpriseDesign,TheCounter-IEDReport,Autumn2024.
26 https://unidir.org/publication/counter-ied-capability-maturity-model-and-self-assessment-tool/
27 ManagingaC-IEDEnterprise,TheCounter-IEDReport,Winter2024/25.
28ThisneedforagileC-IEDresponsesisdiscussedin‘AgileC-IEDEnterprises’,TheCounter-IEDReport,Winter2024/25.
ofinvestedresources. Asmonitoringandevaluationof theeffectivenessofC-IEDeffortscanidentifylessons, informeddecisionsto‘modifyexistingorinvestinnew C-IEDefforts,’29 areempowered. Once‘politicalbacking tomodifytheenterprise’30 issecured,‘aneffcient process,involvingkeystakeholderengagement, resourcemobilization31 andcommunication,isneeded toensuretheresultingconstituentC-IEDeffortswithin theenterpriseremainthreataligned,effectiveand effcient.’32 Assuch,embeddingaMELprocessinto aC-IEDenterpriseisakeytooltoachievingan agileenterprise.
MaintainingAwarenessofEvolvingIEDThreats
WhiletheeffectivenessoftheC-IEDeffortsinvested inwillbedeterminedbyanumberoffactors,33 the IEDthreatwillbetheprimaryone.Parallelto anembeddedlessonslearnedprocess;threat monitoringneedstobeon-goingtodetectchanges inIEDuseandhorizonscan.
‘AnIEDthreatisnormallyanevolvingand dynamicproblem’34 as thethreatbeingconfronted willevolveovertimeintermsofthetechnical complexityandtacticalsophisticationastheIED networkemployingthemwillseektocircumventthe C-IEDeffortsinvestedagainstthem. Forthis reason,itisimportanttoacknowledgeanIED threattypicallyevolvesduetotheaction-reactioncounteractioncyclethatplaysoutbetweenIED threatactorsandthoseengagedinaC-IED
enterprise.Whateverapproachistakenbyanational C-IEDenterprise,thefactthatthethreatwill inevitablyevolveduetotheaction-reactioncounteractioncycle,theC-IEDeffortsinvestedin needtoremainagile.
TherequirementforC-IEDeffortstobeagile, implicitlyrequirestheC-IEDenterprisetomonitor theireffectivenessandevaluatethemtoensurethey remainthreataligned.35 Monitoringandevaluationof theeffectivenessoftheC-IEDeffortsinvestedincan detectIEDthreatevolution;36 however,theprimary meansbywhichIEDthreatevolutioncanbe detectedisbydedicatedeffortstomaintain awarenessoflikelyevolutionintheIEDthreat.This requiresongoingmonitoringoftheIEDthreat, enablingtimelyadjustmentstokeeptheenterprise threatalignedandagile.
Threatmonitoringisintendedtodetectboththreat evolutionaswellashorizonscanforemerging threats.37 TimelyC-IEDintelligenceproductsarethe outputsfromeffectivethreatmonitoring.These C-IEDintelligenceproductsshouldideallyprovide feedback,throughacollaborativeinformation sharingculture,tothestakeholdercommunity involvedtoensuretheeffortsinvestedinandtheir respectiveprioritizationremainthreataligned.
Thisstakeholdercommunitycanthenusethe informationprovidedbysuchintelligenceproducts, toupdateorchangetheIEDthreatpicture,sothatit remainsthreataligned.ByhavingwithinaC-IED
29 ManagingaC-IEDEnterprise,TheCounter-IEDReport,Winter2024/ 25edition.
30 ManagingaC-IEDEnterprise,TheCounter-IEDReport,Winter2024/ 25edition.
31 Resourceinvestmentwillneedtobeconsideredoverthemediumtolongtermasthevariouseffortsinvestedinwillneed tobemaintainedandprobablymodifedastheIEDthreatevolvesandtheC-IEDenterpriseneedstobeadapted,sothatitsstays threatalignedandcontinuestoinvestinthemostappropriatewaysunderthelegalframeworkitisrequiredtooperate.Source: NecessityofaDesignatedLeadEntitywithinNationalC-IEDEnterprises,TheCounter-IEDReport,Spring/Summer2024.
32 ManagingaC-IEDEnterprise,TheCounter-IEDReport,Winter2024/ 25.
33Thesefactorsincluded‘therateatwhichvariousC-IEDeffortsmaturetobeingimpactfulcanvary,thethreatcanevolve,and thewidersecurityenvironmentcanchange.’Source: ManagingaC-IEDEnterprise,TheCounter-IEDReport,Winter2024/25.
34 UnderstandingandMaximisingC-IEDInformationSharing,TheCounter-IEDReport,Autumn2023.
35 AConceptualFrameworkforC-IEDEnterpriseDesign,TheCounter-IEDReport,Autumn2024.
36 AConceptualFrameworkforC-IEDEnterpriseDesign,TheCounter-IEDReport,Autumn2024.
37Source:Regulatingcontrolofthreatexplosiveprecursorchemicalsforuseinimprovisedexplosives,Backgroundpaper, PreparedbyPaulAmorosoandManonBlancafortfortheSmallArmsSurvey,20thJanuary2025.
enterpriseanembeddedMELprocess,aswell asaneffectivethreatmonitoringsystem,informed decisions,effectiveresponses,andultimately preventativemeasures,canbeinvestedinand, whennecessary,adjusted.38
THREATALIGNMENTINHIGHTHREATIED ENVIRONMENTS
TheneedfortimelyandthreatalignedC-IED capabilitiesareessentialwhen‘securityforceand defenceforcepersonnelarerequiredtooperateina highthreatIEDenvironment.’39 Thesepersonnel‘will needtobeprovidedwithsuitablethreatalignedIED awarenessandtrainingwhich maybeconsidered specialisedpreparationandcanincludethe provisionofcertainspecialisedC-IEDequipment. Examplesofthisincludeintermediatesearch capabilitiessuchasroutesearch,theuseof electroniccountermeasures(ECM)equipmentor whatmaybeconsideredlevel1exploitation. TheaimofC-IEDspecialistpreparationisto appropriatelytrainandequipallthoserequiredto undertakekeyactivitieswithinanynationalC-IED enterprise.SuchkeyC-IEDactivitiesinclude,inter alia,informationmanagementandthreatpicture developmentaspartofunderstandingefforts aswellasdefeatthedeviceactivities,and exploitationactivities.’40
THREATALIGNMENTOFIEDCOMPONENT CONTROLANDC-IEDBORDERCONTROLS
TwoofthepreventativeC-IEDelementspreviously outlinedareIEDcomponentcontrolandborder controls.Bothneedtobethreatalignedatalltimes tobeeffectiveandarecloselyrelatedinmanyof theC-IEDeffortstheysupport.IEDcomponent controlinvolvesdevelopingandimplementing
measurestoregulateandcontrolaccesstoIED components.Thesecontrolmeasuresmaytarget explosiveprecursorchemicalsdeemedathreatdue totheirassessedriskofbeingusedinthe manufactureofimprovisedexplosives.Theymay alsobeusedtocontrolaccesstoswitches identifiedascomponentsinIEDs.Anystate securityentitywitharoleinidentifyingsuch chemicalsorcomponents,developingappropriate controlmeasures,theirimplementationand enforcementwillneedtobeinvolvedinthiselement ofanationalenterprise.
Policeorotherlawenforcementagenciesmay haveprimaryresponsibilityforinvestigatingand enforcingsuchcontrolsdomestically.Itmay alsoinvolve,bordermanagementauthorities, particularlythosewithcustomsresponsibilities requiredtomonitorandenforceregulationsrelated totheinternationalmovementofcertaincontrolled IEDcomponentsintoorfromthestate.Wider bordersecurityentitiesmayalsoberequiredtobe onthelookoutforandtrainedtoidentifytheillicit movementofIEDs,componentsthereofaswellas IEDnetworkpersonnel.Theymayalsobetrained andequippedtotakeappropriatesafeactionupon discoveryofanysuspecteditemsorpersonnel.As such,bordercontrolisakeyelementinany nationalC-IEDenterprise.
On-goingmonitoringofthechemicalsand componentsinuseinIEDswillbenecessaryto ensureevolutioninthethreatisdetected. Subsequentappropriateadjustmentintherequired regulationandcontrolmeasureswillneedtobeput inplace.Theseadjustmentswillthenneedtobe communicatedtothosewhoneedtoimplementand enforcethem,whichmayalsoentailtraininginnew proceduresorassociatedequipment.
38Source:Regulatingcontrolofthreatexplosiveprecursorchemicalsforuseinimprovisedexplosives,Backgroundpaper, PreparedbyPaulAmorosoandManonBlancafortfortheSmallArmsSurvey,20thJanuary2025.
39 NestingC-IEDAppropriatelyWithinaState’sNationalSecurityArchitecture,TheCounter-IEDReport,Spring/ Summer2024.
40 NestingC-IEDAppropriatelyWithinaState’sNationalSecurityArchitecture,TheCounter-IEDReport,Spring/ Summer2024.
CONCLUSION
Understandingisavitalcross-cuttingelementof anyC-IEDenterprise,encompassingtwokey aspects:thethreatitselfandtheeffectivenessof theC-IEDeffortsinvestedin.Toachieveeffective understanding,itmustbeinitiallyestablished duringthedesignphasetoguidethedevelopment ofanationalC-IEDenterpriseandsubsequently sustainedovertime.Initialunderstandingrequires aninitialIEDthreatassessmentaswellasa baselineassessmentofexistingC-IEDcapabilities. Sustainedunderstandingrequiresmonitoringthe evolvingIEDthreataswellasassessingthe effectivenessofC-IEDeffortsinvestedin.The importanceofensuringallC-IEDeffortsremain threat-alignedandefficienthasbeenemphasized, withtheirefficiencydependingonmaintainingthis alignment.However,asanIEDsystemevolvesto circumventtheC-IEDeffortsinvestedinagainstit, theIEDthreatisconstantlyevolvingmakingthisa dynamicandchallengingendeavour.Despitethese challenges,theC-IEDenterpriseneedstoadapt, toensure‘firstlyitremainsthreataligned, secondlytheC-IEDeffortsinvestedinare optimisedtosupporttheoverarchingstrategic goaloftheenterpriseandthirdly,toworkefficiently andeffectivelywithintheresourcesprovided totheenterprise.’ 41
Suchadaptationisonlypossiblethroughan embeddedMELprocesstoinformanunderstanding oftheeffectivenessoftheC-IEDeffortsinvestedin. Italsorequireson-goingthreatmonitoringtodetect changesinthethreatandhorizonscanforemerging threats.Theabilitytosystematicallyundertakean initialthreatassessmentandtothreatmonitoron anongoingbasisrequiresthedevelopmentand sustainmentofanIEDthreatpicture.Subsequent articlesoverthecourseof2025willexaminehowto developandsustainanaccurateIEDthreatpicture tooptimizeunderstandingandensuretheC-IED effortsinvestedinremaineffectiveasthreats evolve.■
ABOUTTHEAUTHOR

PaulAmoroso isanexplosive hazardsspecialistandhas extensiveexperienceasanIED ThreatMitigationPolicyAdvisor workinginEastandWestAfrica. HeservedintheIrishArmyasan IEDDisposalandCBRNeoffcer, uptoMNTlevel,andhasextensive tactical,operational,andstrategicexperiencein PeacekeepingOperationsinAfricaandtheMiddle East.Hehasexperienceinthedevelopmentof doctrineandpolicyandwasoneofthekey contributorstotheUnitedNationsImprovised ExplosiveDeviceDisposalStandardsandtheUnited NationsExplosiveOrdnanceDisposalMilitaryUnit Manual.HeworksatpresentintheMENAregionon SALWcontrolaswellasinwiderAfricaadvisingon nationalandregionalC-IEDstrategies.Hehasa MScinExplosiveOrdnanceEngineeringandanMA inStrategicStudies.Herunsaconsultancy, AssessedMitigationOptions(AMO),whichprovides advice,support,andtrainingdeliveryinEOD,C-IED, WAMaswellasPersonalSecurityAwareness Training(PSAT)andHostileEnvironmentAwareness Training(HEAT).Thisarticlerefectshisownviews andnotnecessarilythoseofanyorganisationhehas workedfororwithindevelopingtheseideas. LinkedInprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/
IEDCLASSIFICATION–BREAKINGDOWN BOMBATTACKS
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy.
I NTRODUCTION
Thisisthesecondarticleinaseriesexamininghow todevelopandsustainanaccurateIEDthreatpicture tooptimizeunderstandingandensuretheC-IED effortsinvestedinremaineffectiveasthreatsevolve.
Thefrstarticletitled,‘UnderstandingandThreat AlignmentWithinaC-IEDEnterprise’emphasised understandingasavitalcross-cuttingelementofany C-IEDenterprise,encompassingtwokeyaspects:the threatitselfandtheeffectivenessoftheC-IEDefforts investedin.Therestofthisseriesofarticleswillfocus onunderstandingthethreatofIEDattacks,through anIEDthreatpicture.
Inattemptingtodevelopasystembywhichan accurateIEDpicturecaninitiallybedevelopedand subsequentlysustained,oneapproachcouldbeto workoffadefnitionofanIED.Whileseveral defnitionsofanIEDareinuse,withvaryingdegrees ofaccuracyandoftenscriptedforspecifcaudiences orcontexts,onethatisagoodfttogenerically describethisweaponssystemisgivenby:adevice placedorfabricatedinanimprovisedmanner incorporatingdestructive,lethal,noxious,pyrotechnic orincendiarychemicalsanddesignedtodestroy, incapacitate,harassordistract.Itmayincorporate
militarystoresbutisnormallydevisedfromnonmilitarycomponents.1 However,thereareaspectsof IEDs,andtheirusenotcapturedinthisdefnition,that wouldbeneededtobaseanIEDthreatpicture around.Forexample,IEDspossessthecharacteristic ofbeingclandestinewhichisnotcapturedinthis defnition.Aspreviouslynoted,defnitionsofIEDsare oftentailoredtospecifcaudiencesorcontexts, resultinginmultipledefnitions,withlittlelikelihoodof consensuswithintheinternationalC-IEDcommunity. Thishighlightstheinherentdiffcultyincreatinga methodologytoconstructanIEDthreatpicturebased solelyonadefnition.
AmoresystematicapproachtounderstandIEDuse inagivencontextinvolvesexaminingIEDattacks undertheheadingsoftheirwhat,how,where,when, whoandwhy.Morepreciselyacomprehensive understandingofthefollowingisrequired:
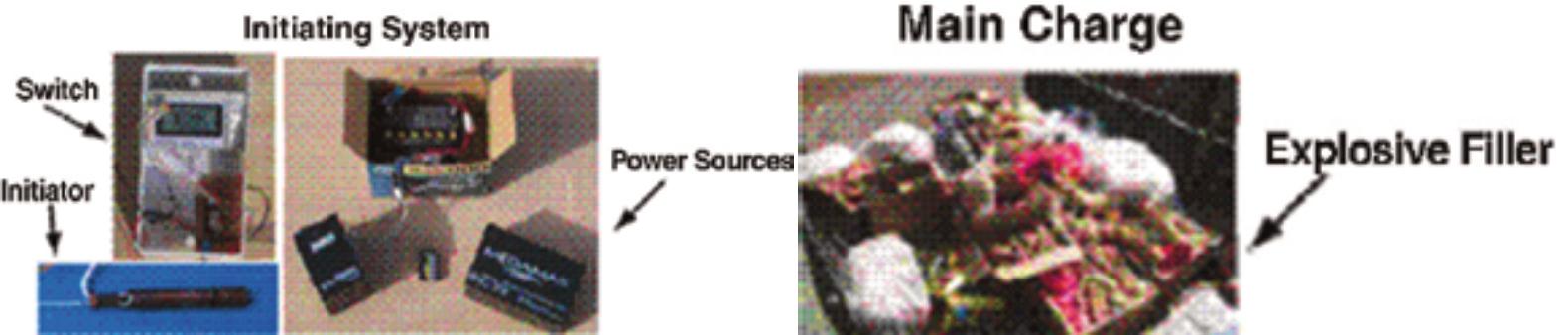
•WhatcomponentsmakeanIED?
•WhereareIEDattackslikelytotakeplace?
•WhenareIEDattackslikelytotakeplace?
•WhoisinvolvedinIEDattacks?
•WhyareIEDsbeingemployed?
•HowareIEDsbeingemployed?
1 UnitedNationsOffceforDisarmamentAffairs(UNODA)InternationalAmmunitionTechnicalGuidelines(IATG)datedApril2011.
Thisunderstandingcanbeconsideredthe5W+H ofIEDs.Thiscomprehensiveanalysishelpstoattain anunderstandingofthethreat,developIEDanalysis tools,andmaintainanaccurateIEDthreatpicture. Suchanapproach,helpsidentifythestrengthsand weaknessesofanIEDsystem,enablingathreatalignedC-IEDenterprisetomakewell-informed decisionsregardinginvestmentsineffective counter-IEDefforts.Severalsubsequentarticlesin TheCounter-IEDReportwillexaminethe5W+Hof IEDsasaprocessincreatingaflexibleyet systematicapproachtodevelopingandmaintaining anIEDthreatpicture.Thisarticle,however,focuses onexaminingsomecommonmethodsusedto classifyIEDs.ItwilloutlinehowIEDsandtheir employmentcanbeanalysedfrommultiple perspectives,eachemphasizingparticularaspects oftheirdesignanduse.Akeymessageisthatwhile eachclassificationmethodhasitsmerits,engaging morethanonemethodofclassificationallowsfora morecomprehensiveunderstandingofthetechnical complexityofIEDsinuse.Wewillbeginby discussingtheimportanceofexploringdifferent methodsforclassifyingIEDs,whichareessentialto developingandmaintaininganaccurateIEDthreat picture.Asupportinginformationmanagement systemwillplayakeyroleinthisprocess,inevitably requiringadatabasetoefficientlyorganizeand managethenecessarydata.
DATABASESINSUPPORTOFANIEDTHREAT PICTURE
AnyIEDthreatpicturewillneedtobebasedupon accurateinformationofsufficientdetailonIEDuse, theIEDsystememployingthemandthecontextof theiruse.Thiswillrequirethecaptureofdatarelated tothesethreeelementsoftheIEDthreatpictureand itssubsequentanalysisaspartofsomeprocessor intelligencecycle.ThiswillultimatelyproduceIED intelligenceproductswhichcanthenbeusedto supporttheunderstandingoftheC-IEDenterprise
sothattheC-IEDeffortsinvestedinremainthreat alignedatalltimes.IntermsofIEDuse,thereisa needtounderstandtheirtechnicalcomplexityand theirtacticalemployment.Thiswillnecessitatethe captureofIEDincidentdataanditsinputintoa database.DatabasesofIEDinformationand intelligencecanbeusedtofindandcompareIED incidents.Overtime,asthedatasetisgrown,this willallowfortrends,patternsandinsightstobe obtained.Itissuchtrends,patternsandinsightsthat areneededtodevelopandsustainanaccurateIED threatpicture.ForanIEDdatabasetobeusefulin informinganIEDthreatpicture,alldataentered needstobestructured,systematicandconsistent. Whileadvancedcomprehensivedatabasescanbe designed,someofthechallengeswhichneedtobe consideredinclude:
•ThevastnumberofIEDsintermsoftheir technicalcomplexityandhowtheycanbeusedin termsoftheirtacticalemploymentisimmense andisachallengetocovereverypossible scenario.
•Theacceptanceofthelikelythreatevolutionover timeowingtoaction-reaction-counteractioncycle betweentheIEDsystemandthoseengagedin theC-IEDenterprise.
•Theneedfornon-specialistsindatabase management,dataentryandIEDstobeableto engagewiththedatabaseinauserfriendlyand intuitivemannerrequiringminimaltrainingto doso.
Itisforthesereasonsthatwhendesigning anIEDdatabasethatasystematicandas comprehensiveaspossible,withoutbeingoverly complex,systemisneeded.ApplyingtheKISS principle2 inIEDdatabasedesignisagood approach.ThisiswheretheuseofIEDclassification systemscanbeusefultoassistwiththischallenging endeavour.
2KeepItSimpleandStructuredaspossible.
IEDCLASSIFICATION–BREAKINGDOWNBOMBATTACKS
IEDCLASSIFICATIONMETHODS
IEDscanbeclassifed3 inmultiplewaystoaccountfor alargenumberofdesignpossibilitiesandtactical employmentmethods.4 Itisunrealisticforevery possibleIEDtobedescribed.However,byapplying theKISSprincipleandutilizinggenericclassifcations withspecifcexamples,itbecomespossibleto systematicallyclassifyIEDsinvariouswaysthatare bothfexibleandpractical.TheIEDthreatpicture developedandsustainedbyaC-IEDenterprisewill ideallyspeaktoitsstakeholderswhichwillinclude specialistsandnon-specialistsatthestrategic, operational,andtechnical / tacticallevels.These variousaudienceswillhavevaryingrequirements whichshouldideallybeaccountedfor.Byconsidering IEDsunderthefollowingfourclassifcations,alarge numberofvariationsisreducedtoamanageable numberofgenericclasseswhichprovides understandingforthevariousstakeholderswithinthe C-IEDenterpriseandtheirdifferentrequirements:
•Methodofactuation
•Tacticalemployment
•Targeteffect
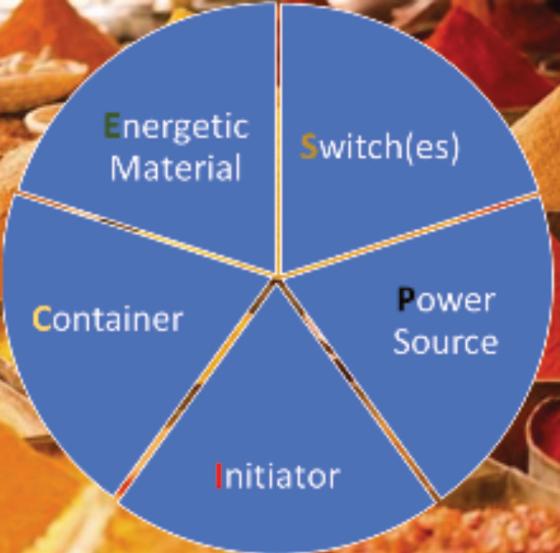
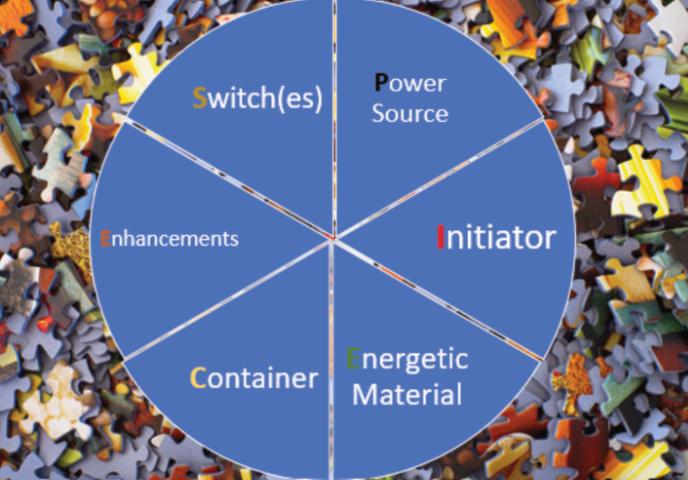
•Technicalcomponents
AnexaminationofthefrstthreemeansofIED classifcationisprovidedbelowwiththefourth,
classifcationbytechnicalcomponents,thesubjectof asubsequentarticleexaminingwhatcomponents makeupanIED.Wewillconcludebyexaminingthe issueofclassifcationcrossover,emphasizingthatthe variousmeansofclassifyingIEDsshouldnotbe viewedasisolatedormutuallyexclusive.Instead,the importanceofadoptingafexibleandcontext-driven approachwhenclassifyingIEDsisadvocated, ensuringthattheclassifcationappliedbesthighlights therelevantcharacteristicswithinagivencontext.
MethodofActuationClassifcation
IEDscanbeclassifedbytheiractuationmethod5 whichreferstohowtheIEDisdesignedtobeinitiated. IEDscanbeclassifedbyoneofthreemethodsof actuation,namely,time,victim-operated,and command.Belowanargumentissetoutthatsuicide IEDsareaspecialcategoryofcommandIEDs; however,insomesystemstheyareconsideredasa fourthmethod.Understandingthemethodof actuationcanprovideinsightintothemost appropriatedefeatthedevicecapabilitiestobe investedin.ThesethreecategoriesofIEDactuation method,arealsothethreecategoriesofIEDswitch, whichcanbeeitherafringorarmingswitches.IED switchesareoneoftheelementscapturedunderthe technicalcomponentsofanIED.
3Theactofarrangingororganizingasetofobjectsintogroupsbasedoncommonattributes,characteristics,qualities,traits, capabilities,orfeatures.
4Adescriptionofhowthedeviceandtargetwerebroughtinproximityofeachother.TheIEDIncidentReportingGuide, 6thEdition.
5ThetermsoperationandactuationaresometimesusedinterchangeablywhenreferringtohowanIEDisinitiated;however, actuationandoperationhavedistinctmeanings,particularlyintechnicalcontexts.Actuationreferstotheprocessofturning on,starting,activating i ortriggering ii anymechanical,electrical,electronicorchemicaldeviceorsystem.Mechanical actuationcaninvolveturningonoroffamotor,openingorclosingavalve,movingaleverorswitch,andinitiatinga mechanicaltimer.Electricalactuationcaninvolveswitchingonoroffanelectricalcircuit,activatingarelayorcontactor, poweringanelectricaldevice,triggeringanelectricalsignaloralarm,andinitiatinganelectricalprocess,suchasaheating element.Electronicactuationcaninvolveactivatingasemiconductordevicesuchasatransistor,poweringonanelectronic circuit,triggeringadigitalsignalorprocess,engaginganelectroniccontrolsystemandstartinganembeddedsystemor microcontroller.Chemicalactuationcaninvolveinitiatingachemicalreaction,startingacatalyticprocess,activatinga chemicalsensorordetectorandtriggeringachemicalreleasemechanism.Actuationfocusesontheinitiationstep.Onthe otherhand,operationreferstotheoverallfunctioningorperformanceofadeviceorsystem.Itencompassestheentire processfromstarttofnish,includingactuation,control,andexecutionoftheintendedtask.Forexample,theoperationofa machineincludesnotonlyturningiton(actuation)butalsoallthestepsinvolvedinitsfunctioninguntilitcompletesitstask.
i.Activationcanimplyturningonasystemorprocess,makingitreadyforoperationandisfrequentlyusedinthecontextof electricalandchemicaldevicesorsystems.
ii.Triggeringisusedtorefertocausinganeventoractiontooccur,oftenusedinelectronicstostartasequenceorresponse.
Time
TimeIEDsarethosewhichfunctionafterapredeterminedperiodoftimehaselapsed.AnIEDfred afterthepassingoftimeallowsattackerstobeata safedistanceatthemomentofinitiation,andtoescape thescenebeforesecurityforcescanrespond.Time IEDsaresuitableforstatictargetssuchasbuildings andinstallationsbutlimitedagainstmovingtargets. AnotherdisadvantageoftimeIEDsisthattheintended victimsmightnotbewithinthedangerareawhenit initiates.However,theystillposeaseriousthreatas tacticscanbeemployedwhich,drawanunwarytarget intoloiteringnearitwheninitiatedortheycanbe employedinindiscriminateattacks,targetinganybody presentatacertainlocationandtime.
VictimOperated
Avictim-operatedIEDisanIEDwithafringswitch thatisactivatedbytheactionsofanunsuspecting individual,relyingonthevictimtocarryoutsomeform ofactionthatwillcauseittofunction.Thismethod offerstheattackerameanstoensurethetargetis closetotheIEDwhenitinitiates.Themainchallenge fortheattackersistofndcircumstancesinwhichonly anintendedtargetwilltriggertheIED,i.e.,an innocentpersonwillnotinadvertentlytriggerit. However,victimoperatedIEDsmaybeemployedin indiscriminateattacks,targetinganybodyatacertain locationandtime.Victim-operatedswitchesmayalso beincorporatedintoIEDsasasecondarymeansof actuationtotargetthosewhoattempttodefeatthe device.
Command
CommandIEDsarethosewhichallowanattacker, oftencalledthetriggermanorbomber,toinitiateitat amomentoftheirchoosingbycompletinganaction thatactuatesthefringswitch.CommandIEDsare especiallysuitedtoattackingmobiletargets.This authorcontendsthat,commandIEDscanbe categorisedunder:
•EmplacedandremotelyinitiatedIEDs
•SuicideIEDs
◦Bomberinitiated
◦Triggermaninitiated
TheauthorseeslogicconsideringsuicideIEDs, whetherinvolvingsuicidebombersorproxybombers, asaformofcommandIED.Thisisbecausetheir initiationisultimatelycontrolledbyadeliberateaction, eitherbythebomberthemselvesorbyatriggerman monitoringandactivatingthedeviceremotely.Inboth cases,adeliberateintendedactionisnecessaryto initiatethedevice.However,deliveryofsuicideIEDs byahumanelementaddsalayerofcomplexitythat distinguishesthemfromothercommandIEDswith theirmeansofemploymentoftenneedingtobe capturedalso.Thishighlightstheissueof classifcationcrossoverwhichisdiscussedlater.
EmplacedandremotelyinitiatedIEDs
Anemplaced6 andremotelyinitiatedcommandIED involvesanattackerselectingtwosuitablelocations: thecontactpointwheretheIEDwillbeemplaced,and thefringpointfromwherethetriggermanwillinitiate thedevice.AnemplacedcommandIEDgivesthe attackerthemeanstoattackaspecifctargetfroma safedistanceatamomentwheninitiationwillhave optimaltargeteffects.Therearemanymethodsto initiateanemplacedcommandIED.Twocommon methodsarebyradiocontrolandbycommandwire. Othermethodsarepossible,forexample,pullinga longstring.Moreobscurecommandfringswitches havebeenusedinvolvingtheuseofvarious technologiesthatallowatriggermantocompletean actionthatcausesafringswitchtofunctionfroma distance.
SuicideIEDs
AsuicideIEDisinitiatedatanattacker’schosen moment,withanindividualcarryingthedevice intentionallykilledeitheraspartoftheattackorto
6AnIEDthatisstaticallyplacedwhereitislikelytobeencounteredbytheintendedtarget. TheIEDIncidentReportingGuide, 6thEdition.
avoidcapture.Bothsuicidebomberandproxy bomber 7 attacksareconsideredsuicideIEDs.The bomberinbothcases,isthepersoninvolvedin transportingordeliveringtheIEDtothepointwhere itisinitiated.SuicideIEDsfallunderthecommand actuationmethodastheirinitiationultimately dependsonadeliberateaction—eitherbythe bomberthemselvesorbyatriggermanremotely controllingthedevice.Thismethodofcommand actuationisoftencloselytiedtoitsdelivery mechanism,whichmayincludeaperson-borne IED(PBIED)orasuicidevehicle-borneIED (SVBIED).Distinguishingbetweensuicideand proxyattacksisfrequentlychallenginguntilafter anattack,leadingtosignificantoverlapinthe defeat-the-devicecapabilitiesdevelopedtocounter suicideIEDs.
BomberInitiatedSuicideIEDs
Suicidebomberattacksinvolveacompliantand cooperativebomberwhoactivelyparticipatesinthe attack.Suicidebombersprovidetheabilityto circumventdefencesbyavoidingthemandguidean IEDtoadesiredcontactpointearningthemthe nicknameof'guidedIEDs.'Unlessneutralisedorthey havelastminutereservationsoncompletingan attack,asuicidebombersisthetriggermaninsuch attacks.Although,proxybomberattacksinvolve someonewhoisnotawillingparticipantintheattack, theymayhavebeenintimidated,threatened,or manipulatedthroughforcedsubstanceconsumption toactivatethedeviceagainstagiventarget.
TriggermanInitiatedSuicideIEDs
Therearevariousreasonsandscenarioswhya remotetriggerisincludedeitherastheprimaryor secondarymeansoffringasuicideIED.Thisallows anattacker,otherthanthebomber,toactasa
triggermanwiththeabilitytoinitiatethedeviceasthe primaryorsecondary(backup)8 meansoffring. Thesescenariosinclude:
•Asuicidebomberisneutralisedpriortohavingthe opportunitytoinitiatethedevice.
•Asuicidebomberbecomesreluctanttocomplete theirattack.
•Aproxybomber,despitebeingthreatened, intimidated,ordruggeddoesnotcarryoutthe directionsgiventothem.
•AproxybomberisunwittinglydeliveringanIEDto atarget.
TacticalEmploymentClassifcation
TacticalemploymentisameansofIEDclassifcation, inwhichIEDsarecategorisedbyhowthedeviceand targetwerebroughtinproximityofeachother.Itoften referstothemethodofdeliveryallowingan understandingofhowanattackwasintendedtobe conducted.TacticalemploymentofIEDsinclude vehicle-borne;animal-borne;person-borne(proxyor suicidebomber);emplaced;standoff;water-borne; air-borne;andpostalIED.Itisnotedthatbothwaterborneandair-bornerefertotheirdomainofuseas muchasanyothercharacteristicandareoften consideredtypesofstandoffIEDs.
StandoffIEDsareaspecialcategoryoftactical employmentofIEDsforseveralreasons.Forthis reason,thiscategoryofIEDswillbeelaboratedon inmoredetail.StandoffIEDsrefertoamethodof IEDemployment,involvinganexplosivedevice launchedorreleasedbyanattackerfromasafe location,whichthentravelstoitspointofcontact. StandoffIEDsenableattackerstoengageatarget withoutrequiringtheirpresenceatthepointof contactatanystageoftheattack.Theyalsoallow forthebypassingofphysicalsecuritymeasures, suchasbarriersthatpreventtheemplacementor
7WhenasuicideIEDisdeliveredbyanindividualwhohasbeencoercedintocarryingouttheattackorisunknowingly transportingthedevicetoitstarget,itisclassifedasinvolvingaproxybomberratherthanasuicidebomber.Thelevelof controlandassuranceofsuccesswithproxybomberscomparedtosuicidebombersislower,asthepersondeliveringthe devicemaynotactasdirected,orifcarryingthedeviceunwittingly,mayactinanunplannedmanner.
8A'chickenswitch'referstotheuseofasecondaryfringswitchbyatriggerman.Thisservesasabackuptoremotelyinitiate asuicideIEDifthebomberhesitates,failstoact,orisneutralized,ensuringthedevicefunctionsasintended.
deliveryofIEDsbyothermeans.StandoffIEDs canbeemployedacrossland,air,andmaritime domains.
StandoffIEDscanbefurtherclassifedasunguided andguided.UnguidedstandoffIEDs,oncelaunched orreleased,havenomeansofsubsequentcontrolby theattacker.Theirtargetingreliesontheirinitial positioning,trajectoryandoftenenvironmentalfactors thatwillinfuencetheirexternalballistics.Unguided standoffIEDsareonlysuitableforattackingstatic targets,requiringtheattackertocarefullyselecttwo locations:itslaunchorreleasepointandthecontact pointwhereitwillinitiate.Theyaretypicallynot suitableforattackingmobiletargets.
Ontheotherhand,guidedstandoffIEDscanbe controlledinsomeaspectafterlaunchorreleaseby anattacker,allowingthemtoadjusttheirtrajectory orplacementtoacontactpoint.Examplesinclude remotecontrolleduncrewedvehiclesintheland domain,aerialplatforms,morecommonlyreferredto asuncrewedaerialsystems(UAS),controlledbyan attackertodeliveranIED,andguidedsurfaceand subsurfacewaterborneIEDs.GuidedstandoffIEDs canbeusedtotargetbothstatictargetsaswellas mobiletargets.Theguidanceandcontrolofsuch standoffIEDscanbelinkedorunlinked.Alinked standoffIEDretainsaphysicallinkbetweenthe attackeratthepointofreleaseandtheIED,9 whileanunlinkedstandoffIEDiscontrolledbya remotemeans,typicallyinvolvingtheuseofsome bandoftheelectromagneticspectrumatcertain frequencies.
Inthelanddomain,standoffIEDscanbedelivered usinguncrewedvehicles.Thesevehiclesaretypically controlledbytheattacker,eitherthroughlinkedor unlinkedsystems,enablingpreciseguidancetothe
desiredcontactpoint.However,casesofunguided uncrewedvehicleswhichwerenotcontrolledinterms oftheirmovementoncereleasedfromtheirlaunch/ releasepointhavebeendocumented.Insuchcases itistypicalforunguidedlandbasedstandoffIEDsto remainlinkedtotheattackertoallowforthemoment ofinitiationtobecontrolled.
Inthemaritimedomain,surfaceandsubsurface standoffIEDscanbeguidedorunguidedonce releasedfromtheirlaunchpoint.Animprovised torpedoisanexampleofasubsurfaceunguided standoffIED.Variousimprovisedsurfacevessels adaptedasIEDsaretypicallycontrolledtoguidethem ontotheirintendedtarget.
Intheairdomain,thereisafargreatervariationof standoffIEDtypes.Intermsofunguidedairstandoff IEDs,theymaybefurtherclassifedasdirector indirect.Improvisedprojectilesfreddirectlyata targetareexamplesofdirectunguidedaerialstandoff IEDs.ExamplesincludetheProvisionalIRA’sMk16 mortar10 aswelltheirProjectedRecoillessImprovised Grenade(PRIG)andtheirImprovisedProjected Grenade(IPG).Improvisedmortarsandrocketsfred withalobbedtrajectoryatatargetareexamplesof indirectunguidedaerialstandoffIEDs.Balloon-borne IEDsareanotherexampleofindirectunguidedaerial standoffwhichuponreleaserelyonwindcurrentsto reachtheirtargets,makingthemunpredictablebut canbeeffectiveincertainscenarios.Theirusehas beendocumentedbeingreleasedinGazatotarget locationsinIsrael.11
GuidedaerialstandoffIEDstypicallyinvolvesome aerialplatform(uncrewedaerialsystem(UAS)12) beingusedtodeliveranIEDtoatarget.UASmaybe usedinavarietyofwaysinstandoffattacksto deliverexplosiveeffectstoatarget.Thesesystems
9ExamplesincludefringcableorfbreopticcableremainingattachedtoanIEDorit’sdeliveryplatformandunwindingasit movesfromthelaunch/releasepointtoitscontactpoint,retainingaphysicalconnectiontotheattackerwhichtheyuseto guidetheIEDtoitstargetandorcontrolitsinitiation.
10ThedesignationofthisprojectedhorizontalshapedchargestandoffIEDismisleading,asitdoesnotalignwiththe characteristicsofamortar,whichisdefnedbyitslobbedtrajectoryfromthelaunchpointtothepointofcontact.
11 https://www.terrorism-info.org.il/app/uploads/2020/01/015_20_E.pdf
12Oftenreferredtocolloquiallybytheterm‘drone’whichhasbecomeawidelyrecognizedandinformaltermincommonuse; however,itisnotaprecisetechnicalterm.Droneisalsooftenusedcolloquiallyinthewaterdomainalso.UASinthiscontext istakentoincludeunmannedaerialvehicles(UAV)andremotelypilotedaircraftsystems(RPAS).
arecontrolledbytheattackeruntilacertainpoint, wheretheyeitherreleasetheirexplosiveordnance ontoatarget,freatatarget,orcrashintoatarget. Theactofreleasingexplosiveordnancebydropping itontoatargetisknownasimprovisedaerial bombing.WhenaUASiscrashedintoitstargetasa one-wayattackitisoftenreferredtoasa‘kamikazedrone,’withitsexplosivepayloadinitiatingupon impact.
TargetEffectClassifcation
IEDscanbeclassifedbytheirintendedprincipal targeteffect.Thisclassifcationprovidesaquick understandingofanattacker’sintendedpurposeofan attackor,alternatively,the‘intended,immediate,or directtacticaleffectofanIED’13 attack.Itcanbe usefulinsendingaquickreportororganisingthe immediateresponsetoanattack.Possibleintended purposesincludeanti-armour;anti-personnel;anti-air; anti-infrastructure;anti-vehicle;anti-maritime;tactics, techniques&procedures(TTP)identifcation;obstacle creation;breaching.
CLASSIFICATIONCROSSOVER–FLEXIBLEAND CONTEXT-DRIVENAPPROACH
WhenclassifyingIEDs,itisessentialtorecognize thatthevariousmeansofclassifcationarenot isolatedormutuallyexclusive.CertainIEDscanfall undermultiplecategories,dependingonthe perspectiveorthelensthroughwhichtheyarebeing examined.Thisoverlaphighlightstheimportanceof avoidingasiloedapproachtoclassifcation.Instead, thechosenclassifcationshouldrefectthe characteristicsmostrelevanttothecontextorthe specifcaspectsthatneedtobeemphasized.Itis alsooftenadvantageoustoconsiderIEDsunder multiplesystemsofclassifcation,especiallywhen addressingmorecomplexdevices.TheseIEDsmay exhibitcharacteristicsthatoverlapacrossdifferent
classifcationsystems,suchastheirmethodof actuation,tacticalemployment,andtargeteffect. ThefactthatsuicideIEDsareoftencloselytiedto theirdeliverymechanism,whichmayincludea person-borneIED(PBIED)orasuicidevehicle-borne IED(SVBIED)isanexampleofthemeritofusing morethanoneclassifcationsystemsforcertain IEDs.ExaminingstandoffIEDsfurtherillustratesthe realityofIEDclassifcationcrossover.Classifcation ofstandoffIEDscanbecomplicatedowingtothe largenumberofswitchtypesthatcanbeusedto launchtheIED,armitandthencauseittoinitiatei.e. thefringswitch.Forexample,commandlaunch, delayarmed,timedaerialburststandoffIEDshave beendocumented.Firingswitchclassifcationcan becomeevenmorechallengingwhenconventional itemsofexplosiveordnanceareemployedand functionintheiroriginaldesignrolee.g.impact initiatedortimedelayafterrelease.Forexample, lightdependantresistorshavebeenemployedto allowforthetimedelaylaunchofunguided conventionalrocketsfromimprovisedlaunch platformswhichfunctionbyactivationoftheir conventionalimpactfuze.AUASemployedstandoff IED,mayhaveatimed(delay)armingswitch activatedafterrelease,withaconventionalfuze functioninguponimpactintoitstarget.Integrationof improvisedfringswitcheswithconventionalitemsof explosiveordnanceisalsoknown.Hybridswitches14 areoftenusedwithaerialstandoffIEDs.For example,secondarytimedswitchescanbe integratedintostandoffIEDstopreventtheircapture andsubsequenttechnicalexploitation.Thiscanbe takenevenfurtherwithsecondaryvictimoperated switchesintegratedtotargetanypersontryingto recovertheIEDandpreventitsexploitation. ClassifyinganIEDasstandoffoffersvaluableinsight intoitstacticalemployment.However,this classifcationcanbefurtherrefnedbyincorporating
13TheIEDIncidentReportingGuide,6thEdition. 14AhybridIEDswitchreferstoanyswitchornumberofswitchesconfguredasacombinationoftimedand/orcommandand/or victimoperatedswitchestoactindependentlyand/ordependentlyoneachother.
detailssuchasthedomainofoperation,launch method,armingmethod,and,whereapplicable,the specifcsofprimaryandsecondary fringswitches. Thisexpandedapproachaddsgreaterdepthand precisiontotheclassifcation.
Byutilizingmorethanonemeansofclassifcation whenexaminingIEDs,analystscanmore comprehensivelycapturethefeaturesofdevices. Detailedunderstandingoftheinterplaybetween deliveryandactuationofanIEDisparticularly valuableinC-IEDefforts,asitempowersinformed decisionmakingforeffectivedefeatthedevice capabilities.Byadoptingafexibleandcontext-driven approach,IEDclassifcationcanremainbothpractical andinsightful.DescribinganIEDthroughmorethan onemethodofclassifcationallowsforamore comprehensiveunderstandingoftheirtechnical complexitywhichisakeypartofanyIEDthreat pictureandinturninformsanunderstandingof thethreat.
CONCLUSION
Aspartofseriesofarticlesexaminingamethodology forthedevelopmentandsustainmentofanIED threatpicture,thisarticlehasoutlinedthreeIED classifcationsystemsinuse.Ithasalsointroduced theneedforacomprehensiveunderstandingofthe 5W+HofIEDstodevelopsuchamethodology. Severalsubsequentarticlesin TheCounter-IED Report willexaminethe5W+HofIEDsasaprocess increatingafexibleyetsystematicapproachto developingandmaintaininganIEDthreatpicture. ThesesixconsiderationsofIEDswillworkfromthe technical(what)tothetactical(how)levelsbefore movingtomoreoperationalaspects(whereand whenandwho)priortoexaminingstrategiclevel considerations(why).Theexaminationofwhat componentsmakeupandIEDislinkedtothesubject ofthisarticle,usingthefourthnamedIED classifcation–technicalcomponents.Thisisthe topicofthenextarticleinthisseriesinthecuriously titleda‘JourneyThroughPIECESofSPICEPIES.’■
ABOUTTHEAUTHOR

PaulAmoroso isanexplosive hazardsspecialistandhas extensiveexperienceasanIED ThreatMitigationPolicyAdvisor workinginEastandWestAfrica. HeservedintheIrishArmyasan IEDDisposalandCBRNeoffcer, uptoMNTlevel,andhasextensive tactical,operational,andstrategicexperiencein PeacekeepingOperationsinAfricaandtheMiddle East.Hehasexperienceinthedevelopmentof doctrineandpolicyandwasoneofthekey contributorstotheUnitedNationsImprovised ExplosiveDeviceDisposalStandardsandtheUnited NationsExplosiveOrdnanceDisposalMilitaryUnit Manual.HeworksatpresentintheMENAregionon SALWcontrolaswellasinwiderAfricaadvisingon nationalandregionalC-IEDstrategies.HehasaMSc inExplosiveOrdnanceEngineeringandanMAin StrategicStudies.Herunsaconsultancy,Assessed MitigationOptions(AMO),whichprovidesadvice, support,andtrainingdeliveryinEOD,C-IED,WAMas wellasPersonalSecurityAwarenessTraining(PSAT) andHostileEnvironmentAwarenessTraining(HEAT). Thisarticlerefectshisownviewsandnotnecessarily thoseofanyorganisationhehasworkedfororwithin developingtheseideas.
LinkedInprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/
AJOURNEYTHROUGHPIECESOFSPICEPIES
WHATCOMPONENTSMAKEUPANIED-TECHNICALCOMPONENT
CLASSIFICATION
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy
INTRODUCTION
Thisisthethirdarticleinaseriesexamininghowto developandsustainanaccurateIEDthreatpictureto optimizeunderstandingandensuretheC-IEDefforts investedinremaineffectiveasthreatsevolve.Thefrst articletitled,‘UnderstandingandThreatAlignment WithinaC-IEDEnterprise’ emphasisedunderstanding asavitalcross-cuttingelementofanyC-IED enterprise,encompassingtwokeyaspects:thethreat itselfandtheeffectivenessoftheC-IEDefforts investedin.Therestofthisseriesofarticleswillfocus onunderstandingthethreatofIEDattacks,throughan IEDthreatpicture.
TosystematicallyunderstandtheuseofIEDsbya specifcnetworkinagivencontext1,itisessentialto analyseIEDattacksusingthefollowingkeyquestions: what,how,where,when,who,andwhy.Moreprecisely acomprehensiveunderstandingofthefollowing isrequired:
•WhatcomponentsmakeupanIED?
•WhereareIEDattackslikelytotakeplace?
•WhenareIEDattackslikelytoplace?
•WhoisinvolvedinIEDattacks?
•WhyareIEDsbeingemployed?
•HowareIEDsbeingemployed?
Thisunderstandingcanbeconsideredthe5W+Hof IEDs.Thiscomprehensiveanalysishelpstoattainan understandingofthethreat,developIEDanalysis tools,andmaintainanaccurateIEDthreatpicture.By doingso,thestrengthsandweaknessesoftheIED networkcanbeidentifed,contributingtoathreat alignedC-IEDenterpriseempoweredtomake informeddecisionsoninvestmentineffectiveC-IED efforts.
AlongwithseveralfuturearticlesinTheCounter-IED Report,thisarticlewillexplorethe5W+HofIEDsasa processtocreateafexibleyetsystematicapproachfor developingandmaintaininganIEDthreatpicture.It examinesoneofthepreviouslymentionedmethods ofIEDclassifcation2 –technicalcomponentsasa meanstoexplorethefrstquestionofthe5W+H,‘what componentsmakeupanIED.’
UnderstandingtheIEDcomponentsinuseisvitalto informingmultipleC-IEDeffortsinvolvedinanyC-IED enterprise.Mostnotably,thiswillinformthemost appropriateIEDdefeatthedevicecapabilitiesthat needtobeinvestedin,developedandsustained.Itwill alsobethemostvitalinformationaroundwhichall effortstocontrolIEDcomponentswillbebased.We
1 ContextintermsofanIEDthreatpicturereferstoboththeIEDsysteminvolvedandthelocalcontext.TheIEDsystemis assessedunderitsintent,capabilitiesandtheopportunitiesithastoemployIEDsagainstdefnedtarget(s).Localcontextis defnedbyageographicarea,thetargetoftheattacksandotherlocalfactors.
2 IEDClassifcation–BreakingDownBombAttacks,TheCounter-IEDReport,Spring/ Summer2025.
willexplorehowthisquestioncanbeaddressedby recognizingthatdifferentlevelsofdetailmaybe appliedwhenansweringit.Aprogressivelydetailed examinationofIEDcomponentswillbestructuredusing threesimplemnemonics,eachprovidingasimple memoryaidtoassistinsystematicproflingofIED components.Eachmnemonicprovidesanincreasingly comprehensiveframeworkforIEDtechnicalcomponent categorisation,thesimplestbeingPIES,followedby SPICE,withPIECESbeingthemostcomprehensive. ThisexaminationinvolvesajourneythroughPIECESof SPICEPIES.Wewillfrstexamineaquestionoften askedbymanywheninitiallybeingbriefedonthethreat posedbyIEDs,‘whatdoesanIEDlooklike?’
WHATCOMPONENTSMAKEUPANIED?
Arecurrentquestionoftenaskedwhenbriefngor deliveringtrainingtothoseinvolvedinvariousC-IED efforts,is‘whatdoIEDslooklike?’Inmanycasesthe audiencearenotC-IEDspecialistsbutfromlaw enforcement,frstresponders,all-armsmilitaryunits, bordersandcustomscontrol,localinternationalNGOs, governmentoffcials,membersofthejudiciaryand evenIEDaffectedcommunities.
Examininghowtoaddressthisquestionwithout creatingfalseawarenessthroughoverlyspecifcor prescriptivedescriptionsisacrucialstartingpoint.The answerprovidedbythisauthortodatehasbeenthat anIEDmostlikelyresemblesitscontainer,3 which,due toitsimprovisednature,cantakeonanalmostlimitless varietyofitems.Thishighlightsthesignifcant challengeinsystematicallyclassifyingthetechnical componentsofIEDs,achallengerootedintheir inherentlyimprovisednature,inthatanIEDcanin theorybeconstructedfromavastarrayofcomponents.
PIES
ThebasiccomponentsneededforanyIEDinvolve someexplosivetrain,aswitchtocauseittofunction andtypicallyapowersource.4
Theexplosivetrainwilltypicallyinvolvebothamain chargeandaninitiator.Thisprovidesthebasis componentsofmostIEDs,totypicallyinclude explosives,aninitiator,oneormoreswitches,anda powersource.Thesefourcomponentscanbe arrangedtomakethemnemonicPIES,referringto Powersource;Initiator;Energeticmaterials;5 and Switches–bothfringandarmingifpresent.
Anonlinegraphic6 outliningthecomponentsofanIED–inthiscasetheterminitiatingsystemisusedtodescribe theswitch,initiatorandpowersource.
3Inmostcases,thecontainerofanIEDcanbeanyitemwithavoidwithinwhichtheothercomponentsaresecretedorheld. AcontainermayalsoacttohavesomeoftheIEDcomponentsattachedtoit.
4TheauthoracknowledgesthatitispossibletohaveanIEDwithoutapowersourceinthetraditionalsensewithsuchIEDs havingbeendocumented;however,theyarerareanddiffculttoemployeffectively,typicallyowingtothesensitivityofthe energeticmaterialinvolved.
5 Theterm"explosives"isoftenusedinthiscontexttoreferspecifcallytothemaincharge.However,inabroadersense,it encompassesallenergeticmaterialsintheIED,apartfromtheinitiator.WithinthePIESframework,the"E"accountsforthese energeticmaterials,whichcanincludehighexplosives,propellants,andpyrotechniccompositions.Consequently,the"E"in allthreemnemonicsreferstoanyenergeticmaterialinvolved.
6ImagesfromExaminingtheRoleofMetadatainTestingIEDdetectionSystem,byPaulJ.FortierandKiranDasariUniversity ofMassachusettsDartmouth,PublishedintheITEAJournal2009:30:421-433

Undereachofthetechnicalheadingsofpower sources,initiators,energeticmaterialandswitches variousfurtherclassifcationispossible,leadingtoa hierarchyoftechnology7 Asabasicexample,the typeoffringswitch,canbefurtherclassifedas command,time,victimoperatedorhybrid.8 This conceptofahierarchyoftechnologycanbeapplied tocategorizingthecomponentsofIEDsby organizingthemintolevelsbasedontheir functionality,complexity,andimportancewithinthe device.Thisapproachhelpsinsystematically analysingandunderstandingtheconstructionof IEDs,providingclaritytotheirdiverseand improvisednature.Asystematicanddetailed classifcationsystemofhowpowersources, initiators,energeticmaterialandswitchescanbe furthercategorised,alongwithextensiveexamples, isprovidedin‘ TheIEDIncidentReportingGuide ,’ 6thEdition,9 andalsoreproducedinAnnexALexiconoftheUNIEDThreatMitigationHandbook, SecondEdition,2024.
SPICE
Whenweconsiderthecomponentsaccountedforunder thePIESheadings,wemayreturntothequestionposed earlier–whatdoesanIEDlooklike?Theanswerto which,isthatittypicallylookslikeitscontainer.So,we mayneedtoaccountforanIED’scontainerwhen consideringitscomponents.Whenwedothis,wecan usethemnemonicSPICE,standingforSwitch(es), Power-source,Initiator,ContainerandEnergeticmaterial.
Fromatechnicalperspective,inadditiontoageneral descriptionofanIED,10 thekeycharacteristicsofa containerthatneedtobecapturedareanyaspects whichcontributetotheIED’sconcealmentorexplosive effects.ConcealmentcharacteristicsofanIEDcontainerreferto‘materialsusedtopreventthediscoveryof anIEDbyvisualinspection.’11 Explosiveeffects characteristicsofacontainerrefertoaspectssuchas:
•Confnementofanexplosivemainchargewhich mayleadtoadefagrationtodetonationeffectand isoftenhowpipebombsfunction.
•Confgurationofthecontainertoproducedirected explosiveeffectswhichareconsideredatypeof enhancementandarecoveredlaterinthisarticle.
7Theterm"hierarchyoftechnology"referstothestructuredarrangementorclassifcationofdifferenttechnologicalsystems, tools,orcomponentsbasedontheircomplexity,functionality,orimportance.Thishierarchyoftenhighlightstherelationship betweenfoundationaltechnologiesthatserveasbuildingblocksandmoreadvancedtechnologiesthatdependonorarebuilt uponthem.
8AhybridIEDswitchreferstoanyswitchornumberofswitchesconfguredasacombinationoftimedand/orcommandand/or victimoperatedswitchestoactindependentlyand/ordependentlyoneachother.
9 https://tripwire.dhs.gov/carousel/ied-reporting-guide-6th-edition ReleasedJanuary2024.
10Forexample,theuseofcertaincontainersinsomeareashasgivenrisetogenericdescriptionsbaseduponthecontainerin usesuchascoffeejarIED.
11TheIEDIncidentReportingGuide,6thEdition.
PIECES
WhiletheSPICEmnemonicaccountsforthemain componentsinanIEDitfailstoaccountforcomponents whichareoftenofgreatestinterest–enhancements.12 Theinclusionofenhancementsleadstothemnemonic PIECES,standingforPower-source;Initiator;Energetic material;Container;Enhancements;andSwitch(es).
ItisacknowledgedthatnotallIEDshave enhancements,withsomeIEDsproducingalltheir explosiveorincendiaryeffectsfromthemaincharge. AnIEDcanbeconsideredenhancedwhenadditional materialisintegratedintothemaincharge,positioned incloseproximitytoit,orwhenthemainchargeis confguredinaspecifcwayrelativetothecontaineror addeditems.EnhancementsareaddedtoanIEDto increasetheirharmfulanddamagingeffects.The followingsixtypesofenhancementsarepossible:
•Blastenhancements
Theblastfromsomecommonexplosivescanbe increasedbymixingcertainmaterialwiththem. CommontermsassociatedwithsuchIEDsare blastbombsandenhancedblastIEDs.
•Fragmentationenhancements
Theeffectsofblastreducequicklywithdistance fromthepointofinitiation,withthecontainerof anIEDoftenproducingnaturalfragmentation whichalongwithothercomponentsarepropelled omnidirectionallyfromthepointofinitiationoften causingmanyoftheinjuriesandincertaincases damage.Forexample,apipebombpropelsoften lethalfragmentationinthesurroundingareadue totheruptureandprojectionofthecontainer material.Theeffectsoffragmentationcanbe increasedbytheadditionofadditionaloften metallicmaterialtoanIED.Thisgivesriseto suchdescriptorsasnailbombs,ballbearingIEDs etc.Suchomnidirectionalfragmentationcharges cancausecasualtiesinalldirections. Alternatively,fragmentationmaybepositionedto channelfragmentsintoanarrowerpath, functioningsimilarlytoalargeshotgun,forming whatisknownasaDirectionalFragmentation Charge(DFC)andsometimesreferredtoas shotgunIEDs.Avariationonthisdesignisto produceacurtainoffragmentationprojected outfromonesideofanIED.SuchIEDsareoften referredtoasclaymoreIEDsorimprovised claymores.AnothervariationontheDFCdesign isaDirectedFragmentationFocussedCharge (DFFC)designedtoprojectfragmentstoapoint ofoptimalconcentrationsomedistancefrom theIED.ThisallowsustoclassifyIED fragmentationenhancementunderfoursub headingsasshownbelow.
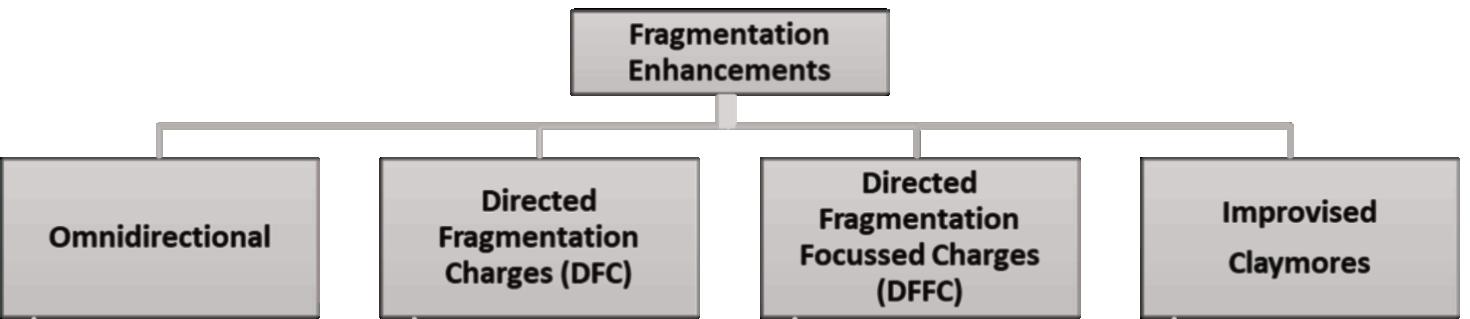
12Anoptional,deliberatelyaddedcomponentorconfgurationoftheIEDasopposedtoasecondaryhazardwhichmodifesthe effectsoftheIED.TheIEDwouldbeeffectiveyetproduceadifferentmeasurableresultifthismaterialorconfgurationwas notpresent.Theeffectcanbeadditionalphysicaldestruction,proliferationofdangeroussubstances(radiation,chemicals, etc.),orotherresultstoenhancetheeffectoftheIED.TheIEDIncidentReportingGuide,6thEdition.
•Directionalexplosiveeffectenhancements
IEDscanbeenhancedforthepurposeof attackingarmouredvehicles,includingblastresistantarmouredvehicles,bytheuseof directionalexplosiveeffect13 enhancements.Such IEDsconcentrateexplosiveforceontoaplate, metaldiskorlinerwhichisprojectedatthetarget. Theycanhavevariousdegreesoftechnical constructionfromlooselyfttedfatplatestowellengineeredcopperconeswithresultingvariations incomplexityofdesign,effectiverange,and penetrativecapability.Therearethreebasictypes ofdirectionalexplosiveeffectenhancements:
DirectionalEffectEnhancements
Plattercharges,EFPandSCareall examplesofdirectionaleffectIEDs. ThetermdirectionaleffectIEDsis onethatreferstoIEDswhichhave eitherdirectionalexplosiveeffects, suchasplattercharges,EFPandSC aswellasthosewithdirected fragmentationeffectssuchasDFC, DFFCandimprovisedclaymores. Thisisanexampleoftheoverlap thatcanoccurwhenclassifying enhancements.Theclassifcation systememployedmaychoose separatecategoriesoffragmentationenhancementsanddirected explosiveeffectsofhavethem combinedunderthebroader directionaleffectcategory.
•Plattercharges;14 •Explosivelyformedpenetrators(EFPs);15 •Shapedcharges(SC).16
Variationincharacteristicsofdirectionalexplosiveeffect enhancements.
13Atermusedtodescribeexplosiveeffectsproducedbytheinitiationofexplosivesinintimatecontactwithalinerwhichis projectedforwardwithvaryingeffectsdependingonmanyfactorsresultingineithershapedchargejets,ExplosivelyFormed Projectiles(EFP)orplattercharges.
14InaplatterchargeIED,theenhancementisaddedintheformofafatmetalplate.WhentheIEDisinitiated,theplateis projectedtowardsthetargetathighvelocity,oftenbreakingintoseverallargefragments.Theplate,orfragments,maybe capableofpenetratinglightarmouratdistanceofafewmetres.
15Alsoreferredtoasexplosivelyformedprojectiles,explosivelyforgedprojectilesandexplosivelyforgedpenetrators.InanEFP IED,theenhancementisaddedintheformofadish,preciselyshapedfromductilemetal.WhentheIEDisinitiated,explosive forcesbendthedishcausingittoinvert.Thisformsasmallermoreaerodynamicallystablecross-sectionalareapenetrator thatisprojectedtowardsthetargetatveryhighvelocity.Dependingontheirdesign,theseprojectilesarecapableof penetratingsubstantialarmouratdistancesevenbeyond10morso.
16Shapedchargesarecommoninconventionalmunitions,oftenreferredtoasHEATwarheads.InashapedchargeIED,the enhancementofteninvolvestheadditionofacoppercone.WhentheIEDisinitiated,ajetofcopperisfredtowardsthetarget atextremelyhighvelocity.Jetscanpenetrateverythickarmour,butonlyiftheIEDisinitiatedincloseproximitytoitstarget.
•Incendiaryenhancements
IEDscanbeenhancedbytheadditionof fammableliquidsforthepurposeofincreasing casualtiesorstartingfresinbuildings. Unconfned,muchoftheeffectoffuel enhancementwillresultinafreballwhichwilllead tothermalinjuriestothosewithinthedangerarea. Wheninitiatedinsideabuildingorinclose proximitytofammablematerial,theeffectsare oftenmuchmoredestructivethantheuseof explosivesalone.Thetermblastincendiaryis sometimesusedtodescribesuchdevices.
•ChemicalBiological&Radiological(CBR) enhancements
IEDscanbemademoreterrifyingbyadding Chemical,Biological,orRadiological(CBR) enhancements.TheexplosiveblastofCBRenhancedIEDs,isdesignedtodispersechemical, biological,orradiologicalsubstancesintothe surroundingarea.Thisresultsincontaminationof theareawithtoxicmaterials,exposingthose presentatthetimeofinitiationaswellas potentiallythoserespondingtosuchanattack. BroadlytherearethreecategoriesofCBR enhancements.Thosewhichareimprovised,
thosewhichinvolvetheuseofcommercialtoxic materials17 andthosewhicharemilitaryor weaponisedagents.
ChemicallyenhancedIEDsmayinvolvetheuseof improvisedchemicals,18 toxicindustrialchemicals 19 ormilitarygradeweaponisedchemicalsalso referredtoaschemicalwarfareagents(CWA).20 For example,anexplosivechargemaybeattachedto cylindersofchlorine,withtheintentthatupon initiation,chlorineisreleasedintotheatmosphere. AttemptstousetheCWAmustardgas(sulphur mustard)21 havebeendocumentedaswellasefforts toemploythenerveagentsarin; 22 however,the developmentofsuchcomplexandrelatively unstableCWAisnoteasilyachieved,typically requiringspecialistequipmentandhigh-level competentchemistsandengineers.Thismakes improvisedCWAproductionlimitedintermsof qualityandquantityandoftenrestrictedtocertain industrialfacilitiesandinsomecasesresearch institutes.
RadiologicallyenhancedIEDsmayinvolvetheuse oftoxicindustrialradiologicalmaterials.23 Theuseof anIEDtoexplosivelydisseminateradiological particlesisoftenreferredtoasa‘dirtybomb’.
17Generictermfortoxicorradioactivesubstancesinsolid,liquid,aerosolized,orgaseousformthatmaybeused,orstoredfor use,forindustrial,commercial,medical,military,ordomesticpurposes.Toxicindustrialmaterialmaybechemical,biological, orradioactiveanddescribedastoxicindustrialchemical,toxicindustrialbiological,ortoxicindustrialradiological.
Source:TheIEDIncidentReportingGuide,6thEdition.
18Thiscategorystandsapartfromtheuseofcommercialtoxicindustrialmaterialsandmilitary-gradeweaponizedCWAsources duetoitsimprovisednatureandrelianceonnon-standardorimprovisedcomponents.Onemayconsidertheseasanalogous toimprovisedexplosivesincomparisontocommercialexplosivesandmilitarygradeexplosives.
19 Achemicaldevelopedormanufacturedforuseinindustrialoperationsorresearchbyindustry,government,oracademia.For example:pesticides,petrochemicals,fertilizers,corrosives,poisons,etc.Thesechemicalsarenotprimarilymanufacturedforthe specifcpurposeofproducinghumancasualtiesorrenderingequipment,facilities,orareasdangerousforhumanuse.Hydrogen cyanide,cyanogenchloride,phosgene,andchloropicrinareindustrialchemicalsthatcanalsobemilitarychemicalagents.
Source:TheIEDIncidentReportingGuide,6thEdition.
20Achemicalsubstancewhichisintendedtokill,seriouslyinjure,orincapacitatemainlythroughitsphysiologicaleffects. Thetermexcludesriotcontrolagentswhenusedforlawenforcementpurposes,herbicides,smoke,andfames.
Source:TheIEDIncidentReportingGuide,6thEdition.
21 https://news.un.org/en/story/2023/06/1137492;and https://ctc.westpoint.edu/islamic-state-chemical-weapons-case-contained-context/
22 https://worldview.stratfor.com/article/sarin-shell-who-might-have-used-it;and https://www.newsweek.com/ieds-secret-sarin-supply-129165
23ToxicIndustrialRadiological(TIR)enhancementreferstoanyradiologicalmaterialmanufactured,used,transported,orstored byindustrial,medical,orcommercialprocesses.Forexample,spentfuelrods,medicalsources,etc.
Source:TheIEDIncidentReportingGuide,6thEdition.
BiologicallyenhancedIEDsmayinvolvetheuseof toxicindustrialbiologicalmaterials24 ormilitarygrade weaponisedbiologicalwarfareagents(BWA).25 The explosivedisseminationofabiologicalagentisunlikely tobeeffectivewiththesamechallengespresentfor BWAproductionasfacedwithCWAproduction. However,thisdoesnotmeananattackerwiththeintent andcapabilitywillnotattempttousebiologically enhancedIEDs.
ThelethalityofadispersedCBRagentinanarea dependsonitsconcentration.However,itsuseoften hasaprofoundpsychologicalimpact–notonlyon thosewithintheimmediateareabutalsoonpeople beyondit,especiallywhennewsoftheattack, particularlyifflmed,spreadswidely.CBR-enhanced IEDsareprimarilydesignedtoterroriseatargetgroup, anditisthisimpactthatmakesthemasignifcantly impactfulcategoryofIEDcomparedtoothers.
TheacronymPIECESframeworkisusefulfor classifyingallthepossibletechnicalcomponentsof IEDs,recognizingthatnotallIEDswillincludeallsix
TheutilityofthePIECESnmemonicframeworkfor IEDcomponentidentifcationisillustratedabove,with thecomponentsshownintransitpriortoassemblyinto anIED.
components.ThemeritsofthePIECESframeworklie initsapplicabilityatboththetechnicallevelandin supportingeffortstocontrolaccesstoIEDcomponents.
CONCLUSION
Aspartofseriesofarticlesexaminingamethodologyfor thedevelopmentandsustainmentofanIEDthreat picture,wehaveexaminedthefrstquestionwithinthe 5W+HofIEDs–whatcomponentsmakeupanIED? Threesimplemnemonictoolsofincreasingdetailhave beenoutlinedthatcanbeusedwhendesigninganIED databasetosystematicallyandconsistentlycapture detailsofIEDcomponentsinuseinastructuredmanner. ItisadvocatedthatthePIECESframeworkisemployed whenproflingIEDcomponents,withthe caveatthat
24Anybiologicalmaterialmanufactured,used,transported,orstoredbyindustrial,medical,orcommercialprocesseswhich couldposeaninfectiousortoxicthreat.Source: IEDIncidentReportingGuide,6thEd,Jan24.
25 AmicroorganismoratoxinA derivedfromitthatcausesdiseaseinpersonnel,plants,oranimalsorcausesthedeteriorationof materiel.
NOTEA:Atoxicsubstanceproducedbyandderivedfromplantsandanimalsorcreatedsynthetically. Source:TheIEDIncident ReportingGuide,6thEdition.
thereisacknowledgmentthatnotallIEDshaveallsix componentspresent.Themeritsoftheuseofthe PIECESframeworkarethatitisnotonlyapplicableat technicallevel,butitcanalsosupportIEDcomponent controlefforts. Astrendsandpatternsofthe componentsinuseandtheirtechnicalconfguration emerges,deviceproflingisempoweredwhich canthen informthetechnicalcomplexityofthethreat.Detailsofthe technicalcomplexityofanIEDthreatisoneofthekey componentsthatwillmakeupanIEDthreatpicture.The nextarticleinthisserieswillexaminethetactical sophisticationofIEDsinusebyexploringthequestion, ‘howareIEDsbeingemployed?’■
ABOUTTHEAUTHOR

PaulAmoroso isanexplosive hazardsspecialistandhas extensiveexperienceasanIED ThreatMitigationPolicyAdvisor workinginEastandWestAfrica.He servedintheIrishArmyasanIED DisposalandCBRNeoffcer,up toMNTlevel,andhasextensive tactical,operational,andstrategicexperiencein PeacekeepingOperationsinAfricaandtheMiddle East.Hehasexperienceinthedevelopmentof doctrineandpolicyandwasoneofthekey contributorstotheUnitedNationsImprovised ExplosiveDeviceDisposalStandardsandtheUnited NationsExplosiveOrdnanceDisposalMilitaryUnit Manual.HeworksatpresentintheMENAregionon SALWcontrolaswellasinwiderAfricaadvisingon nationalandregionalC-IEDstrategies.HehasaMSc inExplosiveOrdnanceEngineeringandanMAin StrategicStudies.Herunsaconsultancy,Assessed MitigationOptions(AMO),whichprovidesadvice, support,andtrainingdeliveryinEOD,C-IED,WAMas wellasPersonalSecurityAwarenessTraining(PSAT) andHostileEnvironmentAwarenessTraining(HEAT). Thisarticlerefectshisownviewsandnotnecessarily thoseofanyorganisationhehasworkedfororwithin developingtheseideas.
LinkedInprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/
CALLFORPAPERS
COUNTER-IEDREPORT
Subscribeat: www.counteriedreport.com/subscribe
Counter-IEDReporteditorialteaminvitesgovernment bodies,armypersonnel,researchers,industryexperts tocontributetheirarticles,casestudies,whitepapers tothereport.
Wearelookingfortheoreticalandpracticebasednonpromotionaleditorialcontributions.*
Autumn2025editiondeadlines: Abstractsubmission:18July2025
Fullarticlesubmissiondeadline:2September2025
Publicationdate:6October2025
Winter2025/26editiondeadlines: Abstractsubmission:3November2025
Fullarticlesubmissiondeadline:5December2025
Publicationdate:27January2026
Spring/Summer2026editiondeadlines: Abstractsubmission:27February2026
Fullarticlesubmissiondeadline:15April2026
Publicationdate:28May2026
Abstractsandarticlesshouldbesubmittedbyemailto: editorial@deltabusinessmedia.com
*Feesapplyforpublicationofarticlessubmittedbycommercialand for-proftorganisations.Allarticlesaresubjecttoeditor’sapproval.
“OLD?”C-IEDFORA“NEW?”ALLIEDCONCEPT: THEC-IEDAPPROACHINTHELIGHTOFNATOWARFARE
ByLieutenantColonelJoseMRufas,ChiefofAttacktheNetworksBranch,C-IEDCentreofExcellence
“Yourealizethatourmistrustofthefuturemakesithardtogiveupthepast.” (ChuckPalahniukinhisbook“Survivor”,frstpublishedin1999)
Ifyou,dearreader,havebeenreading abouttheNorthAtlanticTreatyOrganization (NATO),mostprobablyyouwouldbe familiarwithhearing(andevenharderto effectivelyunderstand…)terminologysuch as“comprehensiveapproach”,“countering improvisedexplosivedevices”,“enhanced forwardpresence”,“integratinggender perspectiveasaforcemultiplier”,“attack thenetworks”,“innovationcontinuum”or “greyzone”..
Solately,undertheumbrellaof “counteringhybridthreats”approachandin thecontextoftheNATO“ Warfghting CapstoneConcept”,theNATO“Warfare DevelopmentAgenda”(WDA)framework emerges…
Figure1:Coverof“NATOWarfghting CapstoneConcept”document,as publishedin2021 (Source–www.act.nato.int)
D'oùvenons-nous? Quesommes-nous? ... 1
DespitethestrongfocusoftheAllianceontheRussian threatattheEasternFront,theNATOStrategicConcept
2022wasstillconsideringterrorismasoneofthemain threatsfortheAlliance.
Figure2:Capturefrom“NATOStrategicConcept”page8,aspublishedin2022 (Source–www.nato.int)
Additionally,thelastAnnualReportfromtheNATO SecretaryGeneral(aspublishedsomedaysbefore thepublicationofthisarticle)ismakingdirect referencenotonlytoterrorismbutalsodirectlyto C-IEDandTechnicalExploitation…
Inotherwords:doyouknowaboutanyterrorist groupwhichhasbeen/isnotemployingorwillingto employimprovisedexplosivedevicesasaweapon ofchoice?
Betweenthelines,wecouldreadandunderstand howtheCounteringImprovisedExplosiveDevices (C-IED)approachcouldpersistasabsolutely necessaryevenwithoutanycasualtyasdirectly causedbythedetonationofanyIEDoverallied troops.Infact,C-IEDisbasedontheintegration, synchronizationandcoordinationofactionsseekingfor anticipationinbeneftofthereductionofcapabilitiesof adversaryhumannetworksintheaimofdenyingthem thepotentialmanufactureanduseofthosedevices.
Figure3:Capturedfrom“NATOSecretaryGeneral2024Report”page15,aspublishedinApril2025 (Source–www.nato.int)
1TakenfromthetitleofPaulGauguin´soiloncanvas“D 'oùvenons-nous? Quesommes-nous? Oùallons-nous? ” (WhereDoWeComeFrom?WhatAreWe?WhereAreWeGoing?)aspaintedin1897.
...Oùallons-nous ? 2
TheNATOWarfghtingCapstoneConceptprovides fvewarfaredevelopmentimperativestofocusand synchronizeeffortstodeveloptheAlliancemilitary instrumentofpower(MIoP).
Figure4:NATOwarfaredevelopmentimperatives (Source–www.nato.int)
Oneofthoseimperatives is “CognitiveSuperiority” (akaCOGSUP),whichis describedasthedegree ofdominancethrough possessingandapplying faster,deeperandbroader understandingandmore effectivedecision-making thanadversaries.
Figure5:NATOdescription ofCognitiveSuperiority (Source–www.nato.int)
2TakenfromthetitleofPaulGauguin´soiloncanvas“D'oùvenons-nous?Quesommes-nous?Oùallons-nous?” (WhereDoWeComeFrom?WhatAreWe?WhereAreWeGoing?)aspaintedin1897.
FromaC-IEDperspective,theblocksderivedfrom theconceptforCognitiveSuperiorityhavealways beenconsideredfromtheAttacktheNetworks approach:
•Awareness(sensing)isessentialfordeep knowledgeaboutthethreat,ourowncapabilities, andtheHumanTerrainthroughanalyzingthe cognitiveenvironment.
•Understanding(sensemaking)posesamustfor HumanNetworkAnalysisandSupportto Targeting/Engagement.
•Advantage(acting)fullyimpliesHumanNetwork EngagementandAssessmentsteps.
Nonetheless,themainproblemsforaneffectiveand anticipatoryapplicationoftheC-IEDapproach(So AttacktheNetworks)remainactiveforachievingthe CognitiveSuperiority.Informationcollectionand intelligenceprocessingcapabilitiesneedtobe reinforced,enhanced,andrefned…which,ingeneral terms,hasneverhappenedevenduringtheAllied involvementinAfghanistan,Iraqandsoon.The emergingthreatscenariosunavoidablyrequirean increaseinintelligencecapabilitiesandanevolutionof theprocessesassociatedwiththoseintelligence capabilities!
Ontheotherhand,thedevelopmentofallied initiativesinthefeldofCognitiveWarfare(COGWAR)is directlyassociatedwithCognitiveSuperiorityimperative. FromanAttacktheNetworkspointofview,thecurrent approachtoCognitiveWarfarehasbeenconsidered insidetheessential-to-successnon-lethalactions.
COGWARintegratescyber,information, psychological,andsocialengineeringcapabilities. Theseactivities,conductedinsynchronizationwith otherinstrumentsofpower(sonotonlytheMilitary InstrumentsofPower(MIoP)),canaffectattitudesand behaviourbyinfuencing,protecting,ordisrupting individualandgroupcognitiontogainadvantageover anadversary.Infact,thereisahugeumbrellaof differentemerginganddisruptivetechnologies(EDTs) whichcouldpotentiallysupportCOGWARdevelopment.
Withregardsto
“LayeredResilience”,soasortof comprehensiveandholisticapproachtocollective defenceresilience,itwouldrefertotheabilityofa singlenationandallalliednationstowithstandand recoverfromabroadspectrumofthreatsand challenges.Accordingly,NATOemphasizesthatthe resilienceofeachmembercountrycontributestothe overallstrengthandpreparednessoftheAlliance,but alsothecommoncohesionandunityofeffortis essentialforthat.
Figure6:VisualizationofNATOcognitivewarfareworkingdefnition. (Source-https://doi.org/10.3389/fdata.2024.1452129)
(Source-www.e-arc.ro)
Althoughalayeredresilienceisnotdirectlyrelatedto agenericC-IEDapproach,itispartiallyapplicablefrom AttacktheNetworksperspectivewhenreferringtoboth:
•Thepreparationoffriendlyhumannetworksagainst thepotentialnegativeeffectsfromadversary actions.
•Theeffectivenessofownactionsdeveloped insupportoftheachievementofpositiveeffectsover friendlyhumannetworksinbeneftofstrengthening owncapabilitiesintheaimofunderminingthe potentialdevelopmentofadversarycapabilities.
Fromthecombinationoftheotherthree imperatives(“InfuenceandPowerProjection”, “Cross-DomainCommand” and “Integrated Multi-DomainDefence”)wearriveattheallied implementationoftheconceptforMulti-Domain Operations.
Multi-DomainOperations(MDO)arecurrently defnedbyNATOas“ theorchestrationofmilitary activities,acrossalldomainsandenvironments, synchronizedwithnonmilitaryactivities,toenable theAlliancetodeliverconvergingeffectsatthe speedofrelevance ”.
Afteraninitialreview,MDOconceptismostlybasedon:
•Militaryandnonmilitaryactivitiessynchronization, whichisanotherwayofconsideringtheessential “Interagency”favorofC-IED/AttacktheNetworks.
•Actionsoveralldomainsandenvironments,which havebeenamustforC-IED/AttacktheNetworks fromitsconceptualcreation.
•Integrationofeffectsatthespeedofrelevance, whichistherootoftheapplicationofC-IED/Attack theNetworksapproachintheaimofachieving effectsoverthecapabilitiesofhumannetworks.
Figure7:Structuredvisualizationofthefactorsinfuencingresilienceinthecontextofallieddefence
Figure8:RussianconceptualmodelofbilateralinteractionsbasedonUSAstrategicMDOaggression (Source-www.vm.ric.mil.ru)
Figure9:JointCommand&ControlevolutioninthesightofAll-DomainOperations (Source-www.secrss.com)
Multi-DomainOperationsisanewNATO concept...Areyoureallysure?
Infact,NATOAlliedCommand Transformation(ACT)hasmerely adoptedconcepts(Multi-Domain ExtendedBattlefeldandMultiDomainOperations)whichwere developedbytheUnitedStatesof America(USA)ArmyandMarines Corpsduringlastdecade (althoughfnallypublishedbythe Army).
Ontheotherhand,Russiahas imitatedtheUSAapproachtoMDO throughtheir“многосферной операции,multi-sphereoperations” concept.
Inparallel,Chinaadoptedthe equivalenttoMDO“全域作战 all-domainoperations”approach.
MDOfnallymovesaroundtwo essentialelements:networkcentricwarfare,anddeepstrike capabilitiesasintegratedatthe fvedomains(air,land,sea,space &cyber).
Iftherebenothingnew,butthatwhichis! 3 Firstly,itlookslikethewholespectrumofNATO WarfareDevelopmentAgenda(WDA)isnottoo revolutionaryin2025.
Figure10:Cross-domainintegrationforMulti-DomainOperations (Source–www.imrmedia.in)
3FromtheSonnet59aswrittenbyWillianShakespeare
Secondly,itlooksliketheAlliance(butmostlyits membernations)couldcurrentlynotbereadyfor effectivelyimplementingMulti-DomainOperations,due toboththeNATOlackofaccuracyindefningthe conceptandthehugeeffortinthedevelopmentof intelligenceandoperationsthatMDOwouldrequire.
Thirdly,itseemsthattheMDOapproachisalready implemented(sofullyapplicabletoC-IED)intothe AttacktheNetworksapproachfromitsverybeginning ofexistencein2008.Alongwiththeevolutionofthe emergingthreatsandthepersistenceofIEDasa futureweaponofchoice,thatmakesC-IEDstillvalid andofcoursenecessary.■
“Extinctionistherule.Survivalistheexception.” (CarlSaganinhisbook“TheVarietiesofScientifc Experience: APersonalViewoftheSearchforGod”,2006)
REFERENCES
•(NATO)2019NATOMilitaryStrategy
•(NATO)2020ConceptforDeterrenceandDefence oftheEuro-AtlanticArea(DDA)
•(NATO)2021NATOWarfghtingCapstone Concept(NWCC)
•(NATO)2022NATOWarfareDevelopmentAgenda (WDA)´
•(NATO)2022NATOStrategicConcept
•(NATO)2024SecretaryGeneral'sAnnualReport
•www.e-arc.ro
•www.irsem.fr
•www.japcc.org
•www.tandfonline.com/journals/ucst20
•www.c2coe.org
•www.act.nato.int
•www.fnabel.org
•R.McDermott,“RussianArmedForcesTestMultiDomainOperations”,JamestownFoundation,9 September2020.
•D.Solen,“ChineseViewsofAll-DomainOperations”, ChinaAerospaceStudiesInstitute,August2020
•www.cssas.unap.ro
•www.secrss.com
•UKMoDJointConceptNote1/20“Multi-Domain Integration”(archived) “OLD?”C-IEDFORA“NEW?”ALLIEDCONCEPT
•Ionita,Craisor “THECONCEPTOFMULTI-DOMAIN OPERATIONSANDITSMULTINATIONALUNDERSTANDING” (STRATEGIESXXI: TheComplexand DynamicNatureoftheSecurityEnvironment,186193)2022
Disclaimer
Thisarticledoesnotrepresenttheopinionofanynational ormultinationalorganisation;itswholecontentshould onlybeconsideredastheopinionoftheauthor.Asall informationhasbeenobtainedfromopensources, potentialmistakescouldhavebeenmadeduringthe researchprocess.Pleasefeelfreetosendyour comments,correctionsandinputstotheauthor;theywill behighlyappreciated.
ABOUTTHEAUTHOR
LieutenantColonelJoseMRufas graduatedfrom theSpanishArmyMilitaryAcademyin1993.Hewas commissionedintotheC-IEDCentreofExcellenceas HeadoftheDefeattheDeviceBranchinAugust2016 andcurrentlyholdsthepostofChiefofAttackthe NetworksBranch.AsaMilitaryEngineerOffcer,his backgroundhasbeenmainlybasedonExplosive OrdnanceDisposalactivitiesintheSpanishArmyand C-IEDstaffissuesatthemultinationalheadquarters.In additiontohisEODOperator/EODOffcereducation, heattendedsomeothermilitarycoursesregarding Parachuting,ArmyStaff,InformationOperations,War CollegeGeneral/JointStaff,MilitarySearch,Technical ExploitationOperations,WeaponsIntelligenceTeam, ExploitationLaboratories,HomemadeExplosivesand otherC-IEDcourses.Hisoperationalassignments includeBosniaandHerzegovina(3),Afghanistan(3), theRepublicofEcuador,IraqandUganda. E-mail:jrufas@ciedcoe.org
IMPROVINGUNDERWATERCAPABILITIES: THEIMPACTOFARTIFICIALINTELLIGENCE ONIEDDETECTIONANDIDENTIFICATION
ByMuratAydoğmuş,LieutenantCommander(OF-3)TUR-N,ElectronicWarfareSpecialist, C-IEDCentreofExcellence
INTRODUCTION
DetectingandidentifyingImprovisedExplosive Devices(IEDs)inunderwaterenvironmentspresents signifcantoperationalchallenges.Unliketraditional explosives,IEDsaredesignedinanimprovisedway andoftenactivatedremotely,whichmakesthema continuousthreatinbothmilitaryandcivilianmaritime contexts.Withtheincreasingimportanceand relianceonnavalandoffshoreinfrastructurefor trade,energyproduction,anddefense,theriskposed bytheunderwaterthreathasbecomeacriticalconcern forglobalsecurity.Morerecentincidents,suchasthe detonationoflimpetminesillustratethesignifcantrisks posedbyexplosivesthatcanbemanufacturedwith relativeeaseandevolveintoasymmetricthreats1
DetectingIEDsandotherpotentiallysuspicious underwaterobjectsrepresentsacriticalcomponentof operations. Thesethreatspresentsignifcantrisksnot onlytonavalandcommercialassetsbutalsotohuman life. Ensuringthesafeidentifcationandhandlingof suchunderwaterhazardsisthereforeofgreat importance.Traditionaldetectionmethods,suchas sonarscanningandmanualdiverinspections,have proventime-consuming,labor-intensive,andrisky, particularlyindeep-seaenvironmentsorareaswith
poorvisibility.Advancementsinartifcialintelligence (AI)haverevolutionizedthefeldofunderwaterthreat detection.ToolsdevelopedwithAIsupporthave improvedtheprecisionandeffectivenessofdetecting underwaterobjects 2 .Deeplearningmodelstrainedon extensivesonarandopticalimagedatasetscanquickly identifypossiblethreats,minimizefalsealarms,and enhanceoverallsituationalawareness.Additionally, AutonomousUnderwaterVehicles(AUVs)equipped withAI-drivennavigationandobjectrecognition capabilitiescanautonomouslypatrolhigh-riskareas, minimizingtheneedforhumandiversandenhancing operationalsafety.Researcheffortsaroundtheworld havefocusedondevelopingAI-supportedsonar processingtoimprovedetectioncapabilitiesin complexmarineenvironments 3
Asunderwaterthreatscontinuetoevolve,the integrationofAIsolutionsremainsanimportantaspect ofmodernnavaldefenseandmaritimesecurity.This articleexaminesthetechnologicaladvancementsinAIaideddetectionandidentifcationofsmallunderwater targetsorthreatswithanemphasisonIEDs, highlightingthebenefts,challenges,andfuture potentialofthesesystems 3
TRADITIONALMETHODS
TodetectandclassifyunderwaterIEDsorpotential suspiciousobjects,therearesometraditional approacheslikeusingsonarscanningandanalysing thescreen,magneticanomalydetection(MAD),diverbasedinspections,andremotelyoperatedvehicles (ROVs).Theprimarytechnologyusedforunderwater detectionissonarsystems.Sonardevicesrelyon soundwavestodetectobjectsorthreatsunderwater becauseelectromagneticwavesareheavilyabsorbed andattenuatedbywater,makingthemineffectivefor communicationordetection.
Sonardeviceshavedifferentmonitoringtechnology accordingtothesystem'sactiveorpassiveoperation mode.Whilepassivesystemsareusedtolistentothe environmentwithoutanyemissions,activesystems sendoutpulsesandreceivetherefections.Inthis article,exampleswillbegivenfromactiveandhighresolutionsonarsystems.Althoughtherearedifferent kindsofsonarsystemsusedforunderwatermonitoring likemulti-beamechosounders,forward-lookingsonar, side-scansonar(SSS),andsyntheticaperturesonar (SAS)systems,theuseofSSSandSASoperationwill bebriefyexplainedinthisarticle.Bothsonar systemsprovidedetailedimagesoftheunderwater environment.
Magneticanomalydetection(MAD),ontheother hand,identifeschangesintheEarth'smagneticfeld causedbymetallicobjects,andthesesystemsare usedtraditionallytodetectanomaliesandpotential underwatertargets 4 .WhileMADisparticularlyuseful fordetectingmetal-basedthreats,itislesseffective whenitcomestonon-metallicIEDs.
SonarSystemOperations:
Theunderwaterenvironmentposesmanychallenges becauseofthecomplexcharacteristicsofwater. Severalsonartechnologiesareusedforseabed scanningandsmallobjectdetection,andthese systemstypicallyoperateathigherfrequencies,which allowsforhigh-resolutionimaging.
Inthetraditionalapproach,detectingsmallobjects reliesheavilyonmanualanalysisofsonarimages,a processthatistime-consumingandhighlydependent
ontheskilloftheoperator.Thisdependencecanlead toinconsistentoutcomesandlimitsscalability, particularlywhenlargeamountsofdataneedtobe processed.Theinherentcomplexityoftheunderwater environmentaddsanadditionallayerofdiffcultyto detectionoperations 5 .Factorssuchasnoise,clutter, andvaryingseabedconditionsmakeitdiffcultfor operatorstoaccuratelyidentifyobjectsmanually.
a.SideScanSonar(SSS):
SSSisanimportanttoolfordetectingunderwater objects,includingIEDsandothersmallobjectsonthe seabed.SSSworksbyemittingconicalorfan-shaped pulsesthataredirecteddownwardtowardtheseabed atawideangle,perpendiculartothesensor'spath throughthewater.Thesensorcanbetowedbehinda surfacevesselorsubmarine,oritcanbemountedon theship'sorunmannedvehicle’shullformore stationaryscanning.
Thesonaremitssoundwaves,whichinteractwith theseafoorandanyobjectsrestingonorburiedwithin it.Thesesoundwavesrefecttothesonarsystem,and theintensityoftheseacousticrefectionsisrecorded. Theresultingdataiscapturedinaseriesofcross-track slices,whichcanthenbeanalyzedtoreveal anomaliesontheseafoor.
Thissonarisusefulfordetectingmetallicobjects likeunderwatermines,IEDs,anddebris,asthese typicallyproducestrongacousticrefections.However, side-scansonarcanalsodetectnon-metallicobjects whentheirshapeanddensityexhibitsignifcant contrastrelativetothesurroundingenvironment.For example,irregularitiescausedbyburiedobjectsor disruptionsintheseafoorstructuremightindicatethe presenceofIEDs,whichareoftenburiedor camoufaged 6 .
b.SyntheticApertureSonar(SAS):
SASisalsoapowerfultoolforobtaininghighresolutionunderwaterimagesandtheycanalsobe usedfordetectingtheobjectslikemines,underwater IEDsorotherpotentialobjects.SAS,whichismounted onaUUV,movesalongatrackandsynthesizesa muchlargervirtualarrayfrommanypings.It
continuouslyrecordsbackscatteredsignalsfromthe seafoorortheobjects.Thesystemcoherently combinestheechoesreceivedatdifferentpositions, effectivelysynthesizingalargeaperture.Muchfner resolutionisobtainedwithSAS 8
RegardingthedetectionofIEDsorsmallburied objectsunderwater;theyoffermoredetailedimageryof theseafoorandlargeareasarescannedeffciently withhigh-resolutionoutputs.
MagneticAnomalyDetection(MAD)Operations: MADsystemsutilizesensitivemagnetometers designedtodetectperturbationsintheEarth's magneticfeldinducedbythepresenceofferrous objects9.Normally,theEarth’smagneticfeldisquite stable,andnaturalunderwatermaterialslikesandor waterdon’taffectitmuch.Butwhenthereisametal object–likeaminecasingorpartsofanIED–itmight createasmall disturbanceinthemagneticfeld.
Figure1:IllustrationofSSSOperation 7
Figure2:IllustrationofSASOperation 8
MADsensorsareusedtodetectthesedisturbances, knownasmagneticanomalies.MADsensorscanbe attachedtoships,underwaterdrones,orevenaircraft fyinglowovershallowwaters.Asthesensormoves,it constantlymeasuresthemagneticfeld.Ifitdetectsan unusualmagneticsignal,itmarksthatlocationasa potentialthreat.ThisisespeciallyusefulwhenIEDsare madewithmetalparts,andMADcanhelpfndthem eveniftheyareburiedundertheseabedornotvisibleon sonarimages.That’soneofthebiggeststrengthsof MAD–itcandetecthiddenobjectsincluttered underwaterenvironments.
However,whileMADisgreatfordetectingwherea metallicobjectmightbe,itdoesn’ttelluswhattheobject is.Arockanchor,anoldpipe,oraminemightall producesimilarmagneticsignals.So,onceMADfnds somethingsuspicious,othertoolslikesonar,cameras, ordiversareusuallyneededtotakeacloserlookand identifytheobject.Thegreatestlimitationsarethatsmall deviceshaveaweakermagneticfootprint,MADonly workseffectivelyatcloserange,andsmallanomalies areonlynoticeablewhenbackgroundmagnetic noiseislow.
AISUPPORTINUNDERWATERMONITORING
Inthetraditionalapproach,operatorsvisuallyinspect thehigh-resolutionsonarimagery,andtheylookfor shapes,shadows,textures,andothercuestoidentify potentialthreatslikeIEDsormines,whichisvery dependentonexperienceandfamiliaritywithunderwater environments.
Inthefeldofunderwatertargetdetectionand identifcation,AIoffersatransformativealternativeto traditionalmethodsbyenablingautomatedprocesses thatreduceorminimizehumanintervention.Unlike traditionalapproaches–whichoftenrelyonmanual analysis,andanoperator-dependentdecision-making–AI-basedsystemsutilizedata-drivenmodelsto autonomouslydetectandidentifyunderwaterobjects. Thisshiftisparticularlysignifcantwhenconsideringthe complexanddynamicnatureoftheunderwater environment,wherefactorssuchaslightabsorption, turbidity,backgroundclutter,andnoisesubstantially hinderimageclarityandobjectvisibility.
TheeffectivenessofAIinsuchscenariosisheavily dependentonthequalityoftheinputdata.Obtaining high-resolution,noise-freeimageryisessentialfor accuratedetectionandreliableidentifcation. However,duetoenvironmentalconstraints,such idealconditionsarenotalwaysachievable. Therefore,duringthealgorithmdevelopmentphase, preprocessingtech-niquessuchasdenoising, contrastenhancement,andsuper-resolutionplaya criticalroleinpreparingthedataforsubsequent analysis.Thesepreprocessingstepsnotonly improvethevisualqualityoftheimagesbutalso enhancetheperformanceofAImodelsbyensuring thatessentialfeaturesarepreservedand emphasized.
Inaddition,thevarietyandrichnessofadatasethave adirectimpactonhowrobustandgeneralizablethe trainedmodelsare.Whenadatasetcoversdiverse objectappearances,angles,environmentalscenarios, andsensortypes,itallowsAIsystemstolearnmore detailedandrepresentativefeatures.Asaresult,this enhancesdetectionperformanceandlowersthe chancesoffalsealarmsormisseddetections.
Inrecentyears,therehasbeenincreasinginterestin utilizingdeeplearningapproaches–likeconvolutional neuralnetworks(CNNs)andtransformer-basedmodels –forautomaticallydetectingandclassifyingobjectsin underwaterenvironments.Thesetechniqueshave demonstratedstrongpotentialinrecognizingpatterns andirregularitiesthatmightbechallengingforhuman observerstodetect.EventhoughIEDsaretypically non-standardinshapeandcompositionsincetheyare constructedusingimprovisedandunpredictable methods,AI-basedapproachescanstillprovide valuableinsights.Whiletheymaynotalwaysdeliver defnitiveidentifcation,theyarehighlyeffectivein faggingpotentialthreatsanddrawingtheoperator’s attentiontoregionsofinterest.
Ultimately,theintegrationofAIintounderwater detectionsystemsenhancessituationalawareness, operationaleffciency,anddecision-making capabilities.Bycombininghigh-qualitydata acquisition,advancedpreprocessingtechniques,and powerfulAIalgorithms,itbecomespossibleto
developrobustsystemscapableofperforminginrealtime,evenunderchallengingconditions.Thisnotonly increasesthesafetyofunderwateroperationsbut alsoreducesthecognitiveloadonhumanoperators, enablingmorefocusedandinformedassessmentsof suspiciousobjects.
Althoughthisarticledoesnotaimtoexplorethe technicalbackgroundindepth,itisimportantto highlightthatsignifcantresearchhasbeendedicatedto theautomaticdetectionofunderwaterobjects.These studiesspanabroadmethodologicalspectrum, encompassingsingle-stagedetectionmodels,twostagedetectionframeworks,andmoresophisticated multi-stagesystems.
Single-stagemethodsintegrateobjectlocalization andclassifcationintoaunifedpipeline,enablingrapid inferenceandmakingthemparticularlyadvantageous forreal-timeapplicationsandresource-constrained, modularsystems.Conversely,two-stageandmultistageapproachesintroduceintermediateprocessing steps–suchasregionproposal,candidatefltering,and refnedclassifcation–that,whilecomputationallymore demanding,oftenyieldhigherdetectionprecisionand robustness,especiallyincomplexorvisuallycluttered underwaterenvironments 10 .
Variousalgorithmshavebeendevelopedwithin eachofthesemethodologicalcategories,andthe researchcommunitycontinuestoexplorenovel techniquesandarchitecturesinpursuitofimproved performance.Theseeffortsrefecttheintrinsic challengesposedbytheunderwaterdomain,where visibilitylimitations,sensornoise,andtheirregular, non-standardizedconstructionofIEDscomplicate reliableidentifcation.Assuch,thereisnosingle superiorapproach;rather,eachmethodofferscontextspecifcadvantages,andtheirrelativeeffectivenessis oftendeterminedbyoperationalconstraintssuchas processingtime,hardwarecapabilities,andmissioncriticalrequirements.
Inthiscontext,theongoingdevelopmentofAI-driven detectionsystemsisofparticularsignifcance.Even whendefnitiveclassifcationofanobjectasanIEDis notimmediatelypossible,theabilitytoautomatically faganomalousorsuspiciousitemscontributes
IMPROVINGUNDERWATERCAPABILITIES
substantiallytoenhancingoperatorsituational awarenessandfacilitatingmorefocusedhuman analysis.Therefore,thequality,speed,andadaptability ofthedetectionalgorithmsplayacrucialroleinthe overalleffcacyofunderwatersurveillanceand securityoperations.
Amongmorerecentapproaches,theintegrationof advancedpayloadsystemsonunmannedunderwater vehicles(UUVs)hassignifcantlyenhancedtarget detectioncapabilities.Theseplatformsare increasinglyequippedwithbothopticalandsonar imagingtechnologies11,enablingthecollectionof comple-mentarydatasets.Byapplyingmulti-modal datafusiontechniques–whereopticalimagery provideshigh-resolutiondetailandsonarimaging offersgreaterpenetrationinturbidorlow-visibility environments,theoverallaccuracyandreliabilityof underwaterdetectionsystemscanbesubstantially improved.
Thissynergisticuseofsensormodalitiesallowsfor amorerobustassessmentofsubmergedobjects, particularlyincomplexanddynamicunderwater conditions.Asaresult,suchtechnological advancementscontributetosaferandmoreeffective operations,whetherinmilitaryreconnaissanceor counter-IEDmissions.
Asanexample,limpetminesusedasunderwater IEDsaretypicallyrudimentaryandconstructedwith readilyavailablematerials,makingthemdiffcultto detectordefendagainst.Theimprovisednatureof thesedevicesmeansthattheymaylackthe sophisticatedtriggeringmechanismsofstandard militarymines,butthisalsomakesithardertotrace andneutralize12.Theseminesmaybemanually placedbydiversordeployedusingUUVs,making theirdetectionandidentifcationachallenge.Theuse ofAI-drivensystemstodetectandidentifysuch underwaterIEDs,includinglimpetmines,byutilizing advancedsonarimagingandopticaltechnologiesisa verygoodapplicationarea.Asitwasstated,when fusedtogether,thesetechniquesoffergreater accuracyindistinguishingbetweenbenignobjects andpotentialthreats,contributingtosaferoperations innavalenvironments.
CONCLUSION
Inrecentyears,therehavebeenmanyresearchtopics concentratedonleveragingAI-supportedsystemsfor underwaterobjectdetection.Theprimarygoalofthese studiesistoimprovesituationalawarenessandensure saferoperationsbyminimizingtheneedforhuman interventioninriskyunderwaterenvironments.The effectivenessoftheseautomateddetectionsystems heavilydependsonthevolumeanddiversityofthe trainingdata,asricherandhigher-qualitydatasetsallow AImodelstoperformmorereliablyacrossdifferent environmentsandobjectvariations.
AlthoughtheimprovisednatureofIEDs–characterizedbytheirunpredictableshapes,materials, anddeploymentmethods–posessignifcantchallenges forreliableidentifcation,theapplicationofAI-supported toolsplaysacriticalroleindrawingattentionto potentialunderwaterthreats.Ultimately,minimizing humanexposurewhilemaximizingdetectionreliability throughautomatedsystemsnotonlyimprovessafetybut alsostrengthenstheoveralleffectivenessofunderwater threatmitigationstrategies.■
REFERENCES
1TheMaritimeExecutive,"Ambrey:TankeratUst-LugaMay HaveBeenHitWithLimpetMines,"TheMaritime Executive,Feb.12,2025.[Online].Available: https://maritimeexecutive.com/article/ambrey-tanker-at-ust-luga-may-havebeen-hit-with-limpet-mines
2M.Kanguya,"SmartOceans:TheRiseofAIinDeep-Sea Exploration,"TheFutureList,Feb.2025.[Online].Available: https://www.thefuturelist.com/smart-oceans-the-rise-of-ai-indeep-sea-exploration/
3M.Aubard,A.Madureira,L.Teixeira,andJ.Pinto, “Sonar-basedDeepLearninginUnderwaterRobotics: Overview,RobustnessandChallenges,”arXivpreprint arXiv:2412.11840,2024.[Online].Available: https://arxiv.org/ abs/2412.11840
4Clem,T.;Allen,G.;Bono,J.;McDonald,R.J.;Overway,D.; Sulzberge,G.;Kumarb,S.;King,D.Magneticsensorsfor buriedminehuntingfromsmallunmannedunderwater vehicles.InProceedingsoftheOceans’04MTS/IEEE Techno-Ocean’04(IEEECat.No.04CH37600),Kobe,Japan, 9–12November2004;Volume2,pp.902–910.
5 F.Zhao,B.Huang,J.Wang,X.Shao,Q.Wu,D.Xi,Y.Liu, Y.Chen,G.Zhang,Z.Ren,J.Chen,andK.Mizuno, "Seafoordebrisdetectionusingunderwaterimagesand deeplearning-drivenimagerestoration:Acasestudyfrom
KohTao,Thailand,"MarinePollutionBulletin,vol.214, 117710,2025.[Online].Available: https://doi.org/10.1016/ j.marpolbul.2025.117710
6NOAAOceanExploration,"ExplorationTools:Side-Scan Sonar,"NOAAOceanExplorer.[Online].Available: https://oceanexplorer.noaa.gov/technology/sonar/sidescan.html [Accessed:Mar.24,2025].
7RobertWilsonMarineTechnologies(RWMT),“Side-Scan Sonar,”RWMTSurveyingTools.[Online].Available: https://www.rwmt.se/surveying-tools/side-scan-sonar [Accessed:Mar.24,2025].
8R.Edgar,“IntroductiontoSyntheticApertureSonar,”inSonar Systems,InTechOpen,2011.[Online].Available: https://cdn.intechopen.com/pdfs/18868/InTechIntroduction_to_synthetic_aperture_sonar.pdf
9CAE,"MagneticAnomalyDetectionExtendedRole (MAD-XR),"CAE,Mar.2023.[Online].Available: https://www.cae.com/media/media-center/documents/ datasheet.MAD-XR.pdf
10SharkYun,"ComputerVision—ObjectDetection,One-Stage vsTwo-Stage,"Medium,Oct.31,2024.[Online].Available: https://sharkyun.medium.com/computer-vision-objectdetection-one-stage-vs-two-stage-b05dbff88195
11Kim,H.-G.;Seo,J.;Kim,S.M.UnderwaterOptical-Sonar ImageFusionSystems.Sensors2022,22,8445. https://doi.org/10.3390/s22218445.
12J.D.Caverley,"FromtheEditors,"NavalWarCollege Review,vol.77,no.3,pp.1–2,Summer/Autumn2024. [Online].Available: https://digital-commons.usnwc.edu/cgi/ viewcontent.cgi?article=1756&context=nwc-review
ABOUTTHEAUTHOR
LieutenantCommanderMurat Aydoğmuş wascommissionedinto theC-IEDCentreofExcellenceasa C2ElectronicWarfareSpecialistin theDefeattheDeviceBranchin August2023.Afterassumingthis position,heorganizedthe6thNATO C-IEDTechnologyWorkshopin Seville,Spain,in2024.Heholdsmaster’sdegreein ElectricalEngineeringandEngineeringAcousticsfrom theNavalPostgraduateSchool.Hisbackgroundis primarilybasedonmaritimeprojectsandresearchand developmentactivitiesinthemaritimedomain.Heis currentlypursuingPhDstudiesinunderwatertarget detectionusingmoderndeep-learningmodels.
Email: maydogmus@ciedcoe.org
INFRASTRUCTUREANDCOMMERCIALPROJECTS: EOCLEARANCEANDRISKMANAGEMENT
ByDrRobertKeeley,RKConsulting(EOD)Ltd
INTRODUCTION
InternationalMineActionStandards(IMAS)have becomethebenchmarkforhumanitarianmine actionsincetheywerefrstintroducednearlya quarterofacenturyago.Yettheydon’tftexactly intocommercialclearancework.
Theaimofthispaperistoexplorethe differencesbetweenhumanitarianand commercialperspectives,howtheybothinfuence attitudestotheclearanceofcommercialprojects andinfrastructure.Thepaperalsomakes recommendationsonbestpracticeforEOrisk managementoninfrastructureandcommercial projects,drawingontherelevantelementsof IMASwherepossible.
THEHUMANITARIANPERSPECTIVE
Itmaybeusefultostartwithadefnitionof‘humanitarian’.For thisitispossibletorefertotwodifferentUnitedNations(UN) GeneralAssemblyresolutions,namely:
•46/182(19Dec1991)
•58/114(5Feb2004)
Thesedescribehumanitarianactionashavingfour principles,whichare:
•Neutrality
•Humanity
•Impartiality
•Independence(added2004)
Theprincipleshavebeendefnedinanelaborationby theUNOffcefortheCoordinationofHumanitarianAffairs (OCHA)1,assetoutin Table1 below.
Humansufferingmustbeaddressedwheneveritisfound.Thepurposeof humanitarianactionistoprotectlifeandhealthandensurerespectforhumanbeings. “whereveritisfound”
Humanitarianactorsmustnottakesidesinhostilitiesorengageincontroversies ofapolitical,racial,religiousorideologicalnature. 3 Impartiality
Neutrality
Humanitarianactionmustbecarriedoutonthebasisofneedalone,giving prioritytothemosturgentcasesofdistressandmakingnodistinctionsonthe basisofnationality,race,gender,religiousbelief,classorpoliticalopinions
“Onthebasisofneed alone” 4 Independence
Humanitarianactionmustbeautonomousfromthepolitical,economic,militaryor otherobjectivesthatanyactorsmayholdwithregardtoareaswhere humanitarianactionisbeingimplemented
Table1.OCHAelaborationonhumanitarianaction.
“Humanitarianactionmust beautonomousfrom… economic…objectives”
1 Source:OCHAonMessage:HumanitarianPrinciples,November2011 https://www.unocha.org/sites/unocha/fles/dms/Documents/v.2.%20website%20overview%20tab%20link%202%20Humanitarian%20Principles.pdf
Whenonealsotakesintoaccountthelanguageof the1997Anti-PersonnelLandmineBanConvention (APMBC),andthe2008ConventiononCluster Munitions(CCM),thereisaclearrequirementtoclear all contamination.Forexample,CCMsaysinArticle4:
“EachStatePartyundertakestoclearand destroy,orensuretheclearanceand destructionof,clustermunitionremnants locatedinclustermunitioncontaminatedareas underitsjurisdictionorcontrol…notlaterthan tenyearsfrom[itsentryintoforce}.
Itisgenerallyacceptedthattheonlylimitationon humanitarianmineactionistheavailabilityoffunding. Muchofthefocusofhumanitarianmineactionhas thereforebeenonfundraising.However,thisimperativeto clearallcontaminationdoesnotapplytocommercial projects,which,bytheirverynature,willonlybeinterested inclearingcontaminationrelevanttotheiractivities.
THECOMMERCIALPERSPECTIVE
Defnitions
Whenexploringthecommercialperspective,itisworth defningnon-proftandfor-proftorganisations.These defnitions,fromtheUnitedStatesChamberof Commerce2,aresetoutin Box1 below.
• Non-proftorganisations. Anon-proft organisation hasalegallyapprovedpurposeorsocialcause beyondproftgeneration.Theorganisation’s incomeisnotdispersedtoanyshareholdersbut insteadisinvestedbackintotheorganisation.
• For-proftorganisations. Afor-proftcompanyis anorganisationthatexiststoearnaproft.These entitiesdonothavelegalobligationsdictating wheretheirproftgoes.Instead,theycandisperse thefundsamongtheownersandemployeesor spendithowevertheychoose.
Box1.Defnitionsofnon-proftandfor-proftorganisations.
Itshouldalsoberememberedthatnon-proftandforproftorganisationsarelikelytohavedifferenttax obligations,dependingon(a)wheretheyare registeredand(b)wheretheyareworking. Therearethreeotherusefulconceptsthatare usefullydefnedhere.Theseare‘infrastructure’3 and theeconomicconceptsof‘publicgood’4 and‘market failure’5.Thesearedefnedin Box2 below.
• Infrastructure. Thebasicsystemsandservices, suchastransportandpowersupplies,thata countryororganisationusesinordertowork effectively.
• Publicgood. Apublicgoodcanbedefnedas a commodity orservicethatisprovidedwithout profttoallmembersofasociety,eitherbythe governmentorbyaprivateindividualor organisation.
• Marketfailure. Asituationinwhichamarketdoes notoperateasitshould,forexamplewherethe supplyofaproductisnotrelatedtothelevelof demandforit.
Box2.Defnitionsofinfrastructure,publicgoodandmarket failure.
Economicperspectiveonmineaction
Takingallofthesedefnitionstogether,humanitarian mineactioncanbedescribedasaformofmarket failure,asitisaproductwheretheintended benefciaryisnotthecustomer.Notleastbecause mostbenefciariescouldnotaffordtomeetthefullcost oftheservices.Commercialmineactionactivities,on theotherhand,haveaconventionalbuyer-seller relationship.Thesetwomodelsarerepresented graphicallyin Figure1 below.Infrastructureprojects maybepublicgoodsasdefnedin Box2 above,but, aswillbediscussedbelow,theyshouldberegardedin thesamelightascommercialprojectsinthatthey requirefocused,project-orientedactionratherthanthe clearanceofallEOcontamination.
2 https://www.uschamber.com/co/start/strategy/nonproft-vs-not-for-proft-vs-for-proft
3 https://dictionary.cambridge.org/dictionary/english/infrastructure#google_vignette
4Source: https://languages.oup.com/google-dictionary-en/
5 https://dictionary.cambridge.org/dictionary/english/market-failure
Figure1.Behaviourofthemarketin(A)commercialor(B)humanitarianmineaction.
Landneededbyhouseholdsfor subsistenceandlivelihoods Directfromprojectfunds,atno chargetobenefciaries
Villageschools,ponds,wells,etc 3 State-owned infrastructure
Publiclyownedinfrastructure (suchasroadnetworks)which havetheirownmaintenance andrefurbishmentbudgets
Privately-ownedlandorfacilities (beyondthosecoveredbySer1) wheretheproftfromoperationis heldbytheowners.
NGOdoestheworkonacost recoverybasis,chargedtothe infrastructureproject,withinoverall prioritysettingprocessandprogram scope
TheNGOwilldotheworkonacost +(perhaps10%)basis.Profts treatedasperlegalrequirementin countryofincorporation.
Therefore,using thesedefnitions,there isnoobjectivereason whycommercialmine clearanceorganisations cannotundertake humanitarianclearance projects,orindeedwhy mineactionNGO shouldnotbidon commercialprojects. Bothtypesof organisationwillhave differentlegalandtax liabilitiesofcourse,but thosearebeyondthe scopeofthispaper. Somethoughtsonhow NGOshouldtreattheir pricingofcommercialor infrastructurebidsare neverthelesssetoutin Table2 below.
CostscalculatedusingtheNGO’s standardbudgetingprocesses
Forlargeprojects(over$100,000),it isrecommendedthatseparate teamsnotfundedbyhumanitarian budgetsshouldbeused.
Largercommercialprojectsmayalso needapprovalbytheNGOboard.
Notes:
1.ThisfgureisfromstandardWorldBankestimatesofthelandneededbyruralhouseholdsinSouth-EastAsia.Thisfguremayvarydependingonthe carryingcapacityoflandinothercountries.However,thisfgureshouldbeusedunlessalternativeplanningdataisavailable.
Table2.NGOclearanceofinfrastructureorprivateland:possiblepricingarrangements
Economicperspectivesonprojectmanagement
Commercialandinfrastructureprojects,whetherthey beprivateorpublicsector,aregovernedtoaverylarge degreebythereturntheywillbringontheirinitial investment.Thisreturnismeasuredbyanumberof economicconceptsincluding:
•Thediscountrate
•Internalrateofreturn(IRR)
•NetPresentValue(NPV)
Briefdefnitions6 ofthesearegivenin Box3 below.
• Discountrate:arateofinterestthatyouuseto calculatethepresentvalueofanamountofmoney thatyoureceiveorpayinthefuture.
• Internalrateofreturn:theaverageamountof moneyearnedeachyearfromaparticular investment,calculatedbycomparinghowmuch moneyitmakeseachyearwiththeoriginalamount invested.
• Netpresentvalue:Thepresentvalueofan investment'sfuturenetcashfow(= difference betweenthemoneycominginandgoingout)after thecostoftheoriginalinvestmenthasbeen subtracted.
Box3.Economictermsusedinprojectmanagement.
Thekeypointsfromthesedefnitionsarethat(a) costspaidforusingtoday’smoneyand(b)today’s moneyisworthlessthantomorrow’smoney. Furthermore,becauseclearanceistypicallya preliminaryactivityitisparticularlyexpensive.A graphicalrepresentation7 ofthedecreasingvalueof moneyovertimeisshownat Figure2
Thus,anydemandbycommercialprojectswill dependontheirexposuretorisk.Thisisdiscussedin moredetailbelow.
Aformaldefnitionofrisk
Peopleoftenusetheterms‘risk’,hazard’and‘threat’ interchangeably.However,riskisamathematical conceptandassuchhasaformaldefnition.IMAS 04.108 givesaversionofthatdefnition,whichittakes fromISOGuide51:1999:
A“combinationoftheprobabilityofoccurrence ofharmandtheseverityofthatharm”.
Expressedformally,thistakesthefollowingform: R=f(ip,os)
Figure2.Anexampleoftheeffectofdiscountingonthefuturevalueofmoney.
6 https://dictionary.cambridge.org/
7 https://www.fnyear.com/On-Investors-and-Discount-Rates_a35557.html
8 https://www.mineactionstandards.org/standards/04-10/
9 https://data.unsaferguard.org/iatg/en/IATG-02.10-Introduction-risk-management-IATG-V.3.pdf
WhereR=risk,ipistheprobability oftheincidenceandOsistheseverity oftheoutcome.Practicallyspeaking, riskcanalsobeconsideredafunction ofhazardplusactivity:itdoesn’t matterhowcontaminatedanareaisif nobodygoesthere(fromarisk perspective).
Thiscanbeusedinsomething calledan‘expectedmonetaryvalue’ (EMV)calculationwhichcanbeused tocomparethecostoftakinga precautionwiththepotentialcostofan outcomeshouldthatprecautionnotbe taken.UseofanEMVcalculationis explainedinmoredetailin InternationalAmmunitionTechnical Guidelines(IATG)02.109 Para15.1.
Attitudestorisk
Riskcalculationshelpdetermine aproject’sexposuretorisk. However,theydonotfully explainpeople’s(orinstitutions’) attitudestorisk.Thesegenerally rangefromrisk-aversetorisk seeker,butonmanyoccasions thecommercialmineaction serviceproviderencounters clientswhoaretolerantof thepotentialriskfromEO contamination. Figure3 sets outagraphicalrepresentationof thespectrumofdifferent attitudestorisk10.
Incidentally,thosefamiliarwith theprovisionofexplosive ordnanceriskeducation(EORE) willrecognisewherethe twocategoriesofrisk-taking behaviour11 (theintentionaland thereckless)ftonthis spectrum.
Itmayseemstrangeto outsidersthatanycommercial projectcouldbetolerantofa riskfromEO.Theprinciples behindprojectfnanceand EMVgosomewaytoexplain that.Mineactionisan expensive,up-frontactivityto manageahazard(EO)that maynotactuallyimpactthe projectandmaynotactuallyevenbepresent. However,thereisanotherdimension,whichisthatEO posesdifferenttypesofrisk,notallofwhichactinthe samedirection.Thisisbestexplainedusingthe‘Bow Tie’riskmanagementtool12,assetoutin Figure4.
Figure4.AssemblingtheEOriskbowtie(1).Identifyingthepotentialconsequences.
alsogivesausefuldefnitionofhazard,whichitalso takesfromISOGuide51:1999: A“potentialsourceofharm”.
Ina‘bowtie’riskdiagrameverythingstartsatthe centrewiththehazardandtheincident.IMAS04.10
Italsodefnesincidentthus: “aneventthatgivesrisetoanaccidentorhas thepotentialtoleadtoanaccident”.
10 https://www.managementyogi.com/2022/04/risk-attitude-and-risk-attitude-spectrum.html 11FirstsetoutinaUNICEFhandbookin2005.
12 https://www.gov.uk/government/news/bowtie-a-visual-tool-to-keep-an-overview-of-risk-management-practices
Figure3.Thespectrumofdifferentattitudestorisk.
Inthiscontext,thehazardisthe(potential)presence ofEOandtheincidentisanincidentarisingfrom contactwiththatEO.Atfrstitisonlynecessarytoset outtheright-handsideofthe‘bowtie’,namelythe consequences.Theleft-handsidecanbecompleted later.Thesecanbeseparatedintothreedifferent potentialconsequences,whicharedefnedbelow:
• Physicalrisk. Death,injuryordamagetoproperty orequipmentarisingfromanEOincident.
• Projectrisk.Delaysoradditionalcostsarising fromanEOincident
• Reputationalrisk.Thedamagetoaprojectora projectimplementer’sreputationamongstrelevant stakeholders,arisingfromanEOincident,with potentialtoaffectfutureengagement(suchasthe allocationoffuturefundingortheawardingof subsequentcontracts).
Whereasbothphysicalandreputationalriskwould tendtomakeaprojectmoreriskaverse,projectrisk (asdefnedhere)hasthepotentialtopullinboth directions.Projectmanagersmustdecideonthe balanceofriskbetweenthecostofpreventativeaction andthepotentialcostofanincidentandforunplanned delays.Thisisexacerbatedbythehighercostof preliminaryactivitiesasdescribedinthediscussions ondiscountingabove.Thepotentialimplicationofthis needtobalancerisksisillustratedinthecasestudy describedin Box4 below.
Aninternationalpharmaceuticalcompanywas consideringundertakinganorganicmedicinalplant agribusinessprojectinacountryinSouth-EastAsia. Theirrepresentativeshadheardaboutthepotential riskofEOcontamination(theplannedprojectsite wasinthegeneralareaoftheformerHoChiMinh Trail)andtheyapproachedacommercialdemining companyforadvice.
Thecommercialdeminingcompanygaveaquote forfullclearanceoftheentiresite.Thequotedcost fortheclearancemeantthattheagribusiness projectwouldnolongerbeproftableandtheproject didnotproceed.
Box4.ArealcasestudyoftheeffectofEOclearancecosts onacommercialproject.
13 https://www.iso.org/standard/65694.html
Theexampleassetoutin Box4 aboveacritical thingaboutclearanceofcommercialprojects(or infrastructure).Unlikehumanitarianprojects–especiallyonesfocussedoncompliancewiththetwo conventions–clearanceperseisnotthefocus;rather, EOclearanceisanenablertoallowthewidergoalsof theprojecttobeachievedinasafeandtimelymanner. ThefocusofEO-relatedactivitiesonthiswiderproject Schwerpunktwillbediscussedinmoredetailinthe sectionon‘scopeofworks’below.
Onefnalpointthatshouldbeintroducedhereisthe questionofliability.Thisisnottheplacetodiscussthe legalaspectsofriskandinanyeventaproject’slegal exposurewillvarydependingontherelevantnational laws.Butingeneral,itisreasonabletosaythatboth physicalriskandreputationalriskwillenterinto considerationsofliability.
Managingrisk
Theperspectiveofthemineactionsectoronthe managementofriskissetoutinIMAS07.14.However, itissuggestedthatthisislargelyseenthroughthe humanitarianlens.
Mineactionpractitionerswillrecognisethatthe commercialdeminingcompanydescribedin Box4 presentedafalsedichotomytotheirpotentialclient. Fullclearancewasnottheonlyoptionavailable.Arisk managementapproachcouldhavebeentaken.Before thisriskmanagementapproachisdiscusseditis necessaryagaintointroducesomedefnitions,drawn fromtheInternationalStandardsOrganisation(ISO)13, asfollows:
• Riskanalysis.Riskanalysisisthe‘systematicuse ofavailableinformationtoidentifyhazardsandto estimatetherisk’.
• Riskassessment. Riskassessmentisthe‘overall processcomprising[riskidentifcation,]arisk analysisandariskevaluation’.Somesources interchange‘analysis’and‘assessment’.
• Riskevaluation.Riskevaluationisthe‘process basedonriskanalysistodeterminewhetherthe tolerablerisk[willbe]achieved’.
• Riskmanagement.Riskmanagementisthe proactivecontrolandevaluationofrisksvia policiesandmanagementdecisions.
Theoverallriskmanagementprocesscanbe representedgraphically,asshowninFigure5below.
Insomecountries,therearealreadyregulations and/orbestpracticeguidesarealreadyinplace.For example,intheUnitedKingdomtherearetwoguides publishedbytheConstructionIndustryResearchand InformationAssociation(CIRIA),namelyCIRIAReport C681andCIRIAReportC785.InGermanythereisthe Constructionguidelinesforexplosiveordnance clearance(BFRKMR)(‘Kampfmittelräumung(BFR KMR)BaufachlicheRichtlinien’intheoriginalGerman). InVietnamthereisaregulationcalledDecreeNo. 18/2019/ND-CP.
Incircumstanceswheretherearenospecifc regulationsorwhereexistingregulationsdonot providesuffcientguidance,thefollowingfour-steprisk managementprocessisproposed:
1.Riskassessment
2.Non-technicalsurvey(NTS)
3.Technicalsurvey(TS)(includingareareduction)
4.Fullclearance
Notethatfullclearanceisonlyrecommendedifall previousstepssuggestitisnecessary.Itis,ineffect, theriskmanagementoptionoflastresort.
Thereisnoneedtodescribesteps2-4 indetail here.Thesearecoveredindetailinthevarious relevantIMASornationaltechnicalstandardor guideline(NTSG).Themainissueistounderstand howaninitialriskassessmentmightworkandhowthe fndingsmighttriggersubsequentmineaction activities.
Riskassessmentpartone:riskidentifcation
Riskidentifcationinthiscontextisasimplecheckto identifyanypotentialhistoricalevidenceofEO contaminationinthecountry(orregionifpossible). Thiscannormallybedoneasadeskstudy.
Riskassessmentparttwo:riskanalysis
Ifthepotentialprojectisinacontaminatedcountryor region,thenextstepintheriskassessmentprocessis todeterminehowcloseitistoanyrecorded contaminatedareasoranypreviouslyclearedareas. Theanalysisprocessshouldtrytoidentifythe presenceofanyindicators(directorindirect)ofthe presenceofEOcontamination.
Figure5.Graphicalrepresentationoftheriskmanagementprocess(ISO13000/2018)
Thepresenceofanyindicatorswillsuggesttheneed forfurtheraction.Thiswouldfollowthesameprinciples as‘landrelease’inhumanitarianmineaction,i.e. proceedingfromanNTSviaareareductionto clearanceofanyremainingcontaminationidentifed withintheprojectarea.However,incommercial projectssomedecisionshavetobetakenaboutthe needtogofurtherdownthispath.Thisis‘risk evaluation’.
Thisriskassessmentprocedurecanbevisualised asaformofaconventional‘riskmatrix’assetoutin Figure6 below.Notethatitincludestheunfortunately rathercommonsituationwhereasiteisalreadyinuse beforetheEOriskassessmentisundertaken.
Thefrstkeypointbroughtoutby Figure6 isthat activityaffectsrisk.Aprojectsitenotinusepresentsa differentcategoryofrisktoonethatisalreadyinuse. Thesecondpointisthatanyprojectfallingintothegrey categorywilldependontheclient’sappetiteforrisk. Likewise,theimplicationsofasitefallingintothebrown
categorywillbeverycontextspecifc.Finally,itis recommendedthatanyprojectthatis‘red’willneed immediateaction,includingstoppingworkuntil contaminationistreated.
Thisriskmatrixhighlightstheimportanceofthe client’sappetiteforrisk.Thisisdiscussedabovebut notsomethingthatisnormallyconsideredin humanitarianmineaction(HMA).InHMAtheevidence ofabsenceasisimpliedinlandreleaseasaformof ‘triage’,i.e.ofbeingsuffcientinitselfasareasonnot toclear.ThismaybepragmaticinHMAwhere,as describedabove,thereisaformof‘marketfailure’(i.e. thebenefciaryoftheclearanceisnotthecustomer (thedonoris))andmayalsobereasonablewherethe landisalreadyinuseforseveralyears.However,as saidbyCarlSagan,“theabsenceofevidenceisnotthe sameasevidenceofabsence”,andinacommercial contexttheabsenceofevidencemaybenecessarybut notsuffcient.Thisleadstotherecommendedbest practiceforEOrisktreatmentassetoutinTable3.
Figure6.AformofEOriskmatrixforcommercialprojects.
1 Clearance certifcateexists. Siteinregular use.
Defnitelyclear
2 Clearance certifcateexists. Siteinregular use.
Documentreviewcandefneaspecifc pieceofgroundas‘defnitelyclear’ when(1)ithasbeenclearedtothe correctstandardbyacompetentand accreditedorganisation,(2)when appropriatequalitymanagement requirementshavebeenmet,and(3) whereanoffcialclearancecertifcate hasbeenissuedbyanappropriate authority.Furthermore,(4)the certifcatemustalsosetouttheexact perimeteroftheareacleared,the searchmethodusedandthedepthto whichasearchhasbeenundertaken.
Noclearance required.Provide EORE.
3 Indirect indicators.Site notinuse.
Probablyclear
4 Noevidenceof contamination. Siteinregular use.
5 Indirectindicators Workforcemay avoidsome areas. Probably contaminated?*
6 Indirectindicators butsiteinregular use.
7 Directindicators. Sitenotinuse. Defnitely contaminated
8 Directindicators. Siteinregular use.
Thismaybelandthatdoesnotmeet theexactstandardsof‘defnitely clear’,butitmayalsobeapieceof landwherethelocalpopulationhas beenusingthelandforseveralyears withoutanyindicationthat contaminationispresent.Another exampleof‘probablyclear’landis landwheresomeclearanceworkhas beendonebutwherethestandards setoutinPoint#1abovecannotbe met.
Moreinformation required:needs NTS.Mayneed EORE/EODlater.
Unlessallfourofthese requirementsaremet, thesitecannotbe regardedas‘defnitely’ clear.
ConsiderprovisionofoncallEODresponse service
ProvideEOREand on-callEOD responseservice.
Notpossibletocall ‘defnitelyclear’. Dependingonappetite forrisk,‘proving’the groundbyuseofanarea reductiontool(e.g.dogs ormachines)maybe acceptable.
Maybepossibleto ‘disregard’clearance basedonappetitefor risk.
Areasidentifedas‘probably contaminated’areareaswherethere areindirectindicatorsoflikely contamination(suchasproximitytoa defensiveposition)orwherelocal behaviouravoidsthelandbecauseof theperceptionofcontamination.
Defnitelycontaminatedareasare areaswherethereare‘direct’ indicatorsofcontamination,suchas visibleEOpresence,recordsoflaying minefeldsorrecordsofEOcasualties. Inordertoproperlydefneanareaas ‘defnitelycontaminated’itisusually necessarytobeabletodefnethe boundaryofthecontamination.
Areareduction/TS recommended.
NTSand/orarea reduction/TS recommended.
Conductclearance inlinewithproject worksplan
Needtounderstand workforcebehaviour
*Thisisverycontext specifc.
Typeofclearancemay varyduetocontext. BattleAreaClearance (BAC)maybesuffcient insomecircumstances.
IMMEDIATE clearancerequired Ceaseworksuntilsite clear.
Table3.Recommendedriskmanagement/treatmentapproachforcommercialprojectsites
Onerelevantconceptinriskmanagementisthat of‘Source-Pathway-Receptor’(SPR)14.Theseare defnedinBox5below.
• Source.Acontaminantorpollutantthatisin,onor underthelandandthathasthepotentialtocause harmorpollution.
• Pathway.Aroutebywhichareceptorisorcould beaffectedbyacontaminant.
• Receptor.Somethingthatcouldbeadversely affectedbyacontaminant,forexampleaperson, controlledwaters,anorganism,anecosystem,or Part2Areceptorssuchasbuildings,cropsor animals.
Box5.Defnitionsofsource,pathwayandreceptorasused inenvironmentalrisk management.
InthecontextofEOcontaminationitistheEO hazardthatisthesourceofrisk.Thepathwayisthe activityconductedonaprojectsite(eitherduring constructionorduringuse)andthereceptoristhe constructionworkforce,theconstructionequipment andthepersonnelwhoaretheend-usersofthe project.Asanexample,asiteinaregionthathasbeen subjectedtoaerialattackhasdifferentsourcesof hazardthanonethatisbeingbuiltinanareathatwas mined,andpathwayswouldbedifferentinanarea wherefoundationsarerequiredtobedug,comparedto anareawherepeoplejustneededtowalk.Thishas implicationsforthescopeofworksofEOrisk treatment,asdiscussedbelow.Similarly,battlearea clearanceusingvisualsurfacesearchmaybe suffcient,dependingoncontext.Amatrixshowinghow theSPRconceptcouldbeusedinaprojectpotentially contaminatedwithEOisincludedat AnnexA
SCOPEOFWORKS
Oneareawhereprojectmanagerscanreducethe costsofclearance(andhencechangethebalanceof projectrisk)istolimit(andclearlydefne)thescopeof
worksforaproject.Thiswillalsohavethebeneftof reducingbothphysicalandreputationalrisksfrom projectpersonnelwanderingoutofaclearedarea andhavinganaccidentinvolvingEOoutsideofthe projectarea.
Thus,projectmanagersshouldprovidemine clearancecontractorswithadetailedlarge-scalemap oftheprojecttasksitewiththeboundariesclearly defned.Itshouldalsoincludethefollowingwhere thesefalloutsidethefnishedboundaryoftheproject site:
•Stores/laydownareas
•Parkingareas
•Temporarysiteoffcespace
•Workroomforheavyplant
•Accessroutes
Also,thoughtneedstobegiventothedepthof clearance.Clearanceagencieshavethreetechniques availabletothem,namely:
•Surface(visual)search
•Shallowinstrumentsearch
•Deepinstrumentsearch
Inshort,thedeeperthesearchthelongerittakes andthemoreitcosts.Searchdepthsforshallow instrumentsearcharenormallysetbythenational mineactionauthority(NMAA);theinternationalnorm assetoutinIMASis(atthetimeofwriting)13cm.Deep instrumentsearchisusuallypossiblewithhandheld equipmentdownto3mbutcanbedeeperifboreholes aredrilled.Itshouldbenotedthatusuallyonlyaircraft bombspenetratethisdeeply:forexample,itisnot unknowntofndalargeaircraftbombatadepthof 20m,thoughthisisadmittedlyrare.Deepsearchis veryslowandexpensiveandshouldbelimitedtoareas wherefoundationsaretobedugandwherethereisa credibleEOthreat.TheSPRprocesssetoutabove helpsdeterminetheappropriateresponsetopotential EOhazards.
Consideragainthestorysetoutin Box4.Ifthe clearanceorganisationhademployedthefour-step
14 https://www.gov.uk/government/publications/land-contamination-risk-management-lcrm/lcrm-stage-1-risk-assessment#uxo
processsetouthere,andencouragedtheclientto providealimitedscopeofworks,arangeofmore positivescenarioscouldhaveunfolded,including:
“We’vedoneanNTSofyoursiteandthereisno evidenceofcontamination.Youcouldconsider thefollowingactionstodealwithresidualrisk…”
“We’velookedatyoursiteandhaveidentifed thatonlyasmallportioniscontaminated.Ifyou canworkwithoutthatareawecanmarkandfence itoffsothatyourprojectstaffdon’twanderintoit.”
“We’velookedatyoursiteandhaveidentifed thatonlyasmallportioniscontaminated.Itwill cost$Xtoclearthatarea”
Quitefrankly,iftheclearanceorganisationhadsaid anyofthesethingsthereisaverygoodchancethat theywouldhavegotthework.Asitwas,theygot
nothing.Thus,aproperriskmanagementapproachis a‘win-win’forboththeclientandtheclearance organisation.
Conversely,worktocleartheoilfeldsinKuwaitin 1991wasanexampleofhowadefnedscopeofworks facilitatedwhatwasotherwiseaverydiffcultproject. Thefrefghtersworkedoutthattheyneededanaccess laneof30metresforeachwellfre,andadefned workingareaaroundeachfre.Clearanceworkwas donemainlytoidentifyclustermunitionstrikesandthe primarysearchtechniquewasasurfacevisualsearch. See Figure7 below.
ThetaskplanningfortheKuwaitemployedthe ‘minimumoperatingstrip’conceptasusedbymilitary airfelddamagerepair.Inotherwords,whatisthe minimumworkneededtobedoneinordertogetthe jobdone?Thus,evenifa30maccesslanepassed throughaclustermunitionstrike,noactionwouldbe takenagainstanyEOoutsideofthe30mboundary.
Figure7.DealingwithoilfresinKuwait,1991.AllaccessandworkingareasweresearchedforEObeforethefrefghters couldgainaccess.
Thisisaprofoundconceptualdifferencetomuchwork undertakeninHMA,whichwilloftentendtofollow linesofcontaminationoncethesehavebeen identifed.
Themanagementofresidualriskisdiscussed below.
Itisnowpossibletocompletetheleft-handsideof theriskmanagementbowtie.Thisisdonebyadding thepotential‘contributingfactors’.Thisisshownin Figure8 below.Threemaincontributingfactorshave beenidentifed.Theseare:
•Theareahasnotbeencleared
•EOhasbeenfoundonthesite
•Personnelareunawareofthehazardand/or unawareofsafebehaviour
Probabilityoftheincidence
Rememberingtheformaldefnitionofriskasafunctionof theprobabilityoftheincidenceandtheseverityofthe outcome,itisnowpossibletoplotvariousmineaction ‘products’asmeansofreducingtheprobabilityofthe incidence.Thesecanthenbebrokendowninturnto either(a)removingthehazardor(b)changingbehaviour. Therearethreemineactionproductsthatare relevantincommercialwork.Theseare:
•Areaclearance
•Explosiveordnancedisposal(EOD)
•Explosiveordnanceriskeducation(EORE)
ThesearealldefnedinIMAS04.10.However,itis worthnotingthatallofthesefocusonreducingthe probabilityoftheincidence.EOREdoesthisby modifyingbehaviour,whilstEODandareaclearance
Figure8.BuildingtheEOriskbowtie.Notetheuseofqualitymanagementmeasuresinthegreenboxes.
addressthepresenceofahazard.Areaclearance doesthisprophylactically(anareacanbesearched evenifdefniteindicatorsarenotpresent)whilstEOD teamsareusuallydeployedonareactivebasis(after thereportofapossibleitemofEO).
Inriskbowties,risktreatmentoptionsaredrawnas boxesonthevariouscausalarrows.Thus,boxesfor thethreemineactionproductshavebeenaddedto Figure8.
Qualitymanagement
Qualitymanagement,consistingofqualityassurance (QA)andqualitycontrol(QC)playanimportantrolein EOrisktreatment,inorderfortheclienttobesurethat therisktreatmentemployedisftforpurpose.Inthe eventofanincident,accidentinvestigationisalso importantasitcanidentifyanyrootcause(suchasan inadequatescopeofworks)orcontributingfactorsand thushelppreventanyfutureincidents.Thesequality managementmeasuresareshowninthegreenboxes in Figure8
Managingtheseverityoftheoutcome
Sofarthispaperhasdiscussedmanagementofthe riskprobability.However,itisalsonecessarytotreat theseverityoftheoutcome.Threeboxeshavebeen addedtotheright-handsideof Figure8
Theseverityoftheoutcomeofphysicalriskcanbe managedtosomeextentbythetimelyavailabilityofan adequatefrstaidcapacityabletodealwithtypicalEO injuries.FirstaidprovisionisdiscussedinIMAS10.40. Thiswillalso,forremotesites,requireacasualty evacuationplantoahospitalcapableoftreatingtypical woundsfromEO.
Likewise,treatmentofprojectriskcanbedone throughtheapplicationofthe‘scopeofwork’principles assetoutabove.Thismaynecessitatearobust accidentinvestigationproceduretoidentifyany systemicissueswiththemineactionactivities undertakenonthesite.
Finally,theseverityofreputationalriskcanbe amelioratedwhenaprojectcanshowthatithas
applied‘allreasonableeffort’(asdiscussedin IMASTechnicalNoteforMineAction(TNMA) 07.11/03).Ifaprojecthasestablishedaclearscope ofworks,andemployedrelevantrisktreatment throughareaclearance,EOD,andEOREtorelevant IMASandnationalstandards,andwhereadequate frstaidcoverisavailable,thenitisheldthat itcanclaimtohavemettheconditionsof‘all reasonableeffort’.
MANAGINGRESIDUALRISK
Thereremainsthequestionofresidualrisk.Thiscan bethoughtofinseveralways.Iftheprimary treatmentofriskisbytheprophylacticremovalof hazard(withinsetboundariestotheappropriate standard)thentheprovisionofEOREandanon-call EODresponsetorecogniseanddealwithitemsthat stillturnupcanbeconsideredasonewayof managingresidualrisk.Especiallyunder circumstanceswheretheinitialriskassessment suggestedthatfullclearancemaynothavebeen necessary(see Figure6).
However,thesecondwaytodealwithresidualrisk isthroughinsurance.Insurancepremiumsare assessedthoughtheinsuranceindustry’sownrisk managementprocesses,butitispossiblethata projectthatcanshowcompliancewiththebest practicesuggestionssetoutheremaybeneftfrom reducedinsurancepremiums.
Thewillingnessofaninsurertocoverriskfora particularprojectwilldependgreatlyona presentationbytheorganisation(ortheirinsurance broker).Thepresentationwillneedtoaddressany questionsontherisksandmitigationmethodsused. AbrokerthatspecialisesinUXOriskcoverage15 reportsthatpotentialinsurerswill“wantbestpractice asabasicrequirement”.Thebrokeralsostated:
“apoorlypresentedriskcanendupbeing punitivelyexpensiveand/orendupwithcover thatisinadequatetoprotectagainstUXOrisks”
15CorrespondencewithJonathanStarkeyofSpecialistRiskGroup,March2025.
AnnexA.UsingtheSPRapproachtoidentifyingappropriatemineactionintervention
ThematrixatTable4usestheSPRapproachtoidentifypotentialreceptorsfordifferentEOhazardsandthe possiblemineactionresponse.
Notethattheenduserisnotalwaysthemostlikelypossiblereceptorbutcannotalwaysberuledout, especiallyinareasoftheprojectsitethatarenotdirectlywalkedonorotherwiseprocessedduringtheproject construction.
Theconductofthevariouspossibleresponsesshouldineachcasebeconductedinaccordancewiththe relevantIMAS/NTSG.
1 Mines
•Walkingtheland
•Handling •Digging
2 Aircraftbombs •Excavation1
3 Guided weapons •Approaching •Disturbing
4 Cluster munitions
5 OtherLSA
•Handling •Digging •Proximity
•Handling •Digging
6 IED4 •Disturbing •Proximity
•Constructionworkers
•Constructionequipment
•Endusers
Mineclearance
•Constructionworkers •Constructionequipment Deepinstrument search2
•Constructionworkers •Constructionequipment EOD
•Constructionworkers
•Constructionequipment •Endusers
•Constructionworkers
•Constructionequipment •Endusers
•Constructionworkers •Constructionequipment
Battlearea clearance(shallow instrument search3)
Battlearea clearance(shallow instrument search3)
Search/IEDD
Includingvictim-operatedIED functioningasimprovisedmines
Potentialhazardfromrecently deployedtime-fuzedweapons. A‘soaktime’maybeappropriate.3
Potentialsensitivefuzing mechanisms
Potentialhazardfromrecently deployedtime-fuzedweapons. A‘soaktime’maybeappropriate.
Landserviceammunitionother thanmines
Potentialhazardfromrecently deployedtime-fuzedweapons. A‘soaktime’maybeappropriate. Notes:
1.Defnedasdigging>30cm
2.Onlyrequiredinareasrequiringexcavationorwherethereisadefniteindicatorofaburiedbomb(e.g.presenceoftailunitor holeofentry)
3.Visualsurfacesearchmaybesuffcientonhardsurfacessuchasconcreteortarmacwherepenetrationisunlikelyorwillbe obviousonvisualinspection.
4.RefersmainlytocommandortimedelayedIED.VictimoperatedIEDdesignedasimprovisedminesshouldbetreatedasper Ser1;projectedIEDasSer5.
Table4.UsingtheSPRapproachtoidentifyingappropriatemineactionintervention
Finally,EOREremainsanappropriatemeanstomanageresidualrisk,asdoesaccesstoanEODresponse. Thepossiblepathwaysincol(c)canbeusedtoinformthecontentsoftheEOREprovided.WhereEOD responseisusedasatreatmentofresidualrisk,itmayalsobeappropriateasaformofqualitymanagement toassesswhytheEOwasnotfoundduringtheinitialrisktreatment.
MostUXOrelatedriskscanbecoveredbyinsurance heldbytheclearanceagencyandtheirclientswillwant toseetherelevantpoliciesaspartoftheirduediligence duringthecontractingprocess.Siteownersandgeneral constructioncompaniescanalsofndinsurancecover forpersonnelandequipment.Ownershipofresidualrisk coverageofUXOfndsorincidentsafterthesitehas beenhandedoverwilldependonlegislationand/or NTSG.Itishardforthecontractortomaintain responsibilityforasiteaftertheclearanceworkhasbeen completed:whoisliableifaworkerleavesthecleared areaorbringsanitemofEOontothesiteoutof curiosity?Thismayperhapsbeincludedintheclearance agency’sinsurance,butitmightbemoreappropriate (andcosteffective)tomitigateonwardliabilitybya comprehensivequalityassuranceandhandover process.Inotherwords,insuchanarrangementthe liabilityoftheclearanceagencyendsatsitehandover. ■
ABOUTTHEAUTHOR
Dr.RobertKeeley isaformerBritish ArmyBombDisposalOffceractive inhumanitarianandcommercial mineactionandexplosiveordnance disposal(EOD)since1991.Hehas workedinnumerouscountriesand forseveralgovernmentsand internationalorganisations.He specializesinprojectdesign,evaluation,andquality assuranceofallaspectsofmineactionandhashelped shapetheemerginghumanitarianimprovisedexplosive device(IED)sector.Dr.Keeleyisamemberofthe InstituteofExplosivesEngineers,aMemberofthe InternationalAssociationofBombTechniciansand Investigators,andisaFellowoftheRoyalGeographical Society. HeholdsaPhDinAppliedEnvironmental Economics;histhesiswason“theEconomicsof LandmineClearance.”
ContactInformation
Dr.RobertKeeley,Director,RKConsulting(EOD)Ltd Ashford,Kent,UnitedKingdom Bobkeeley@rk-consulting.net www.rk-consulting.net
C-IEDCOEAnnualConference2025 9–12June2025,Malaga,Spain https://www.ciedcoe.org/index.php/ events/ciedac 12thAnnualEOD/IED&Countermine Symposium 16–17July2025,NationalHarbor,MD, USA https://countermine.dsigroup.org/ CounteringExplosiveThreatand DeminingConference2025 23–24September2025,London,UK https://www.defenceiq.com/eventscountering-explosives/
NATOEODDemonstrationsand Trials2025 8–9October2025,Bratislava,Slovakia https://eodcoe.events/event-3/
Defense&Security2025 10–13November2025,Bangkok, Thailand https://www.asiandefense.com/ MilipolParis2025 18–21November2025,Paris,France https://www.milipol.com/
FutureForcesExhibition&Forum 2026 21–23October2026,Prague, CzechRepublic https://www.fff.global/
LANDMINEREMOVALINPOST-CONFLICTAZERBAIJAN
ByWilderAlejandroSánchez,President,SecondFloorStrategies
TheAzerbaijanigovernmentiscarryingouta massiveclearingoperationoflandmines, unexplodedordnance(UXO),andexplosiveremnants ofwar(ERW)afterthe2020and2023conficts betweenArmeniaandAzerbaijan.Bakuwantsto decontaminatetheterritoriessotheyareftforcivilian life,however,thisoperationwillbealengthy, expensive,andcomplexprocess.International partnerswillbeofvitalimportanceforBakutoachieve thisobjective.
BACKGROUND
ThankstoitsmilitaryvictoryintheSecondKarabakh War(2020) andaone-daymilitaryoperationon September2023, Azerbaijanrestoreditsterritorial integrityafterthelosestoArmenia intheFirst KarabakhWar(1988-1994).By2023,negotiations resultedintheArmeniangovernmentagreeingtogive uptheYerevan-controlledterritorialentityknown asNagorno-Karabakh 1 ,nowcalledtheKarabakh EconomicRegion.(Duetospaceconsiderations,we willnotdiscussthecomplexhistoricalrelations, tensions,andconfictbetweenthesetwocountries).
Sincetheendofmilitaryoperations,Bakuand Yerevanhaveengagedindiplomaticnegotiationsfora permanentpeaceagreement.Inmid-March 2 ,thetwo
1 https://www.britannica.com/place/Nagorno-Karabakh
governmentsannouncedthatthefnaltextofapeace treatyhadbeenagreedupon.However,thedocument hasyettobesigned.(OlesyaVartanyan ,aconfict analystontheSouthCaucasus,hasdiscussedthe probablereasonswhybothgovernmentshaveyet tosignthedocument).Whilediscussionsand negotiationscontinue,theremovaloflandmines,UXO, andotherERWisapriorityasBakuhaspledgedthat theinternallydisplacedpeopleduetotheKarabakh wars,canreturntoKarabakh.Additionally,forthe regiontothrive,civilianinfrastructuremustbeinplace, likehouses,schools,hospitals,roads,inadditionto agriculturalland.Landmines,UXO,andERWmustbe removedtoachievethisgoal.
TheMineActionReviewestimatesthattheextentof contaminationis“certainlymassive”asthereare decadesworthoftensionsandmilitaryoperations. Contaminationispresent“alongtheapproximately 254km-long,5km-wideformerLineofContact(LoC) betweenArmeniaandAzerbaijan.Thedefensivebelts ofberms,anti-tankditches,andbarbedwirealongthe LoCcontainhugequantitiesofbothAPandAVmines,” accordingtotheReview.However,becauseofthe historyofinter-statetensionsbetweenBakuand Yerevan,“theareasalongtheLoCwereheavilymined overthethreedecadesafter1990byallpartiestothe
2 https://eurasianet.org/a-peace-treaty-is-fnalized-but-azerbaijan-is-accusing-armenia-of-preparing-for-war
confict.Furtherminefeldsandotherexplosive ordnance(EO),includingabandonedexplosive ordnance(AXO),arefoundinareaspreviously occupiedbyArmeniaoutsideNagorno-Karabakh.”In otherwords,thecontaminationoftheterritorygoes backdecades.
TheMineActionAgencyoftheRepublicof Azerbaijan(ANAMA) 3 istheprimeagencytaskedwith thismassiveoperation.Otherentitiesinvolvedinclude theMinistryofDefense,theMinistryofEmergency Situations,theStateBorderService,andlocal companies,liketheAzerbaijanDeminingCompany andAlphaDemining 4 .Overall,2,485operationalstaff areinvolvedintheseoperations,supportedby87 mine-clearingmachinesand182mine-detectiondogs (Croatiahasdonatedeightdogs),anunknownnumber ofmine-detectionrats,accordingtoANAMAasoflate 2024.Troopsarealsoinvolvedintheseoperations, andANAMAhasconductedthree-weekcoursesfor militarypersonnel 5 on“HumanitarianMineClearance”
and“BattlefeldCleaning.”AnInteragencyWorking GroupontheClearanceofMinesandUnexploded Ordnancemeetsthroughouttheyear“toreview operationsandenforcestandards.”
THESITUATION
Decontaminationoperationshavebeenongoingsince theKarabakhregionfullyreturnedtoAzerbaijanicontrol. AccordingtoANAMA,thecontaminationofterritorywith theremnantsofwarreaches“60%offatagricultural land,30%ofgrassyhills,and10%ofmountainous regions.”In2023,MineActionReview 6 estimatedthat 10squarekmsofterritorywerecleared,including3,495 anti-personnelminesdestroyed(basedonANAMA info).Asfor2024,atotalof62,023hectaresofKarabakh territoryweredecontaminated,includingtheremovalof 59,163piecesofunexplodedordnance,4,286antipersonnelmines,and2,372anti-tankmines.According tothemostrecentstatistics,atotalof4,556hectares wereclearedinMarch2025,whichresultedinthe removalof9,755UXO,331antipersonnelmines,and105anti-tank mines.Someofthemines neutralizedincludemodelsPMN-E 7 , PMN-2 8 ,andTM-62 9

Asforrecentoperationsand fndings,inFebruary,anF-1hand grenade 10 waslocatednearwaste binsinGazakhCity,Gazakhdistrict. Improvisedexplosivedevices (IEDs)alsocontaminatethe territory:anIEDwaslocatedin Bulutanvillage,Khojavenddistrict. Theexplosiveconsistedofone PQ-7Lrocket 11,105smallarms
3 https://anama.gov.az/en
4 https://www.alfarazminiranje.hr/?lang=en
5 https://www.azernews.az/nation/238567.html
6 https://www.mineactionreview.org/assets/downloads/Azerbaijan_Clearing_the_Mines_2024.pdf
7 https://metis.fenixinsight.com/munition/mine/pmn-e
8 https://cat-uxo.com/explosive-hazards/landmines/pmn-2-landmine
9 https://cat-uxo.com/explosive-hazards/landmines/tm-62m-landmine
10 https://anama.gov.az/en/news/302
11 https://anama.gov.az/en/news/309
Anti-tankmine (Source:ANAMA)
Asformorerecentincidents, inearlyApril2025,alandmine explodedintheGalaychilar village,Aghdamregion.A civilian“sustainedinjuries 13 to hislegasaresultofanantipersonnelmineexplosion whileenteringanareathat hadnotbeenclearedof landmines.”Specialiststasked withremovingtheexplosives canalsobeinjured:inApril 2025,anANAMAemployee14 “hitananti-personnelmine whileperforminghisduties” inMehdilivillage,Jabrayil region.Hewassuccessfully evacuatedbuthisrightlegwas amputatedfromtheankle.
INTERNATIONALSUPPORT
cartridgesattachedviaadhesivetape,andahand grenadedetonator,whichwouldbetriggered viatripwire.
Theoperationisnotwithoutincidents,andcivilians whoaremovingtotheterritoriesremaininperil; accordingtoANAMA,between2020and31December 2024,therewere229landmineexplosionincidentsin Karabakh,resultingin382victims,including70 fatalities.Thetallyincludesapersonwhosteppedon alandmineinGushchuAyrimvillage,Gazakhdistrict, last14October,2024 12.Theincidentoccurredasthe individual“whilegrazinganimalsinanareathathad notbeenclearedofmines,”whichhighlightstheneed todecontaminateareaswhichwillbeusedbyfarmers andotherfeldworkers.
12 https://anama.gov.az/en/news/283
13 https://anama.gov.az/en/news/314
14 https://anama.gov.az/en/news/313
Azerbaijanwillrequire internationalassistanceto successfullydecontaminate theKarabakhterritories.Currentpartnersincludethe UnitedStates,UnitedKingdom,EuropeanUnion, Canada,Japan,andTurkiye,aswellasinternational agenciesliketheUnitedNationsDevelopment Programme(UNDP),UNICEF,theUnitedNations HighCommissionerforRefugees(UNHCR),the InternationalCommissionoftheRedCross(ICRC). Otheractorsincludeorganizationsthatspecializein thesetypesofoperations,suchasthePiperDemining Company 15 .
ThankstoapartnershipwiththeGeneva InternationalCentreforHumanitarianDemining (GICHD),ANAMA“hasimproveditsoperational effectivenessthroughtheadoptionoftheInformation ManagementSystemforMineAction(IMSMA).”
15 https://dushanbe.mfa.gov.az/ru/news/landmine-contamination-problem-in-azerbaijan
Meanwhile,theMarshallLegacyInstitute16 has contributedmine-detectiondogs(MDDs);aspartofa Spring2024visittoAzerbaijanbyInstitutestaff,the centerexplainedthat“with41MLI-sponsoredMDDs arrivingoverthelastthreeyears,ANAMAutilizesthe Horadizbasetohouse,acclimate,andtraintheirK9 capacity.”SofarthepartnershipbetweenANAMAand theMarshallInstituteisworkingwellbecausethedogs andthehandlersaregettingalong,“itwasrewardingto seetheamazingbondformedbetweentheMDDsand handlers,”theInstituteexplained 17
Toincreaseawarenessandgaininternational support,theAzerbaijaniMinistryofForeignAffairsand ANAMAhaveconductedmeetingswithpartnersand thegeneralpublic.Inrecentmonths,BakuandANAMA havemetwithBritishdiplomatsinBaku18,anda meetingwasheldinWashingtonattheHudson Institute,athinktank,todiscussthisissue.Also,during theCOP29climateconference 19 heldinlate2024in
Baku,ANAMAandUNDPco-organizedaneventtitled “ClearingthePath:AddressingMineThreatsfor ClimateResilienceandSustainableDevelopment” whileaphotojournalexhibitiontitled“SilentEchoes: UntoldStoriesofMineVictims” 20 wasorganizedby Azerbaijan’sembassyinSpain.Azerbaijanalso participatedinthe5thReviewConferenceofthe OttawaConvention 21,heldinSiemReap,Cambodia.
LOOKINGTOTHEFUTURE
Thefutureoftheremovaloflandmines,UXO,and ERWacrossAzerbaijan’sterritorywilldependon variousfactors.First,apermanentpeacetreaty betweenArmeniaandAzerbaijanwouldbeginthe healingprocessandimproverelationsbetweenthe twocountries.Moreover,Yerevancouldprovide informationaboutminezonesdeployedduringthe confict(s).Sharingthisinformationwouldbea signifcantconfdence-buildingmechanismbetween thetwogovernments, anditwouldobviously speeduptheprocess ofdecontaminatingthese areas.
AsforANAMAandother Azerbaijaniagenciesand organizationsinvolvedin thislong-termproject, unsurprisingly,budgetsare afactorthatlimitthespeed oftheprograms.“Since 2020,foreignassistance hasaccountedformerely 6%oftheresources dedicatedtohumanitarian demining,”explainsthe
16 https://www.marshall-legacy.org/
17 https://www.marshall- legacy.org/post/paws-of-progress-mli-donated-mdds-play-a-major-role-in-azerbaijan-s-mineclearance-success
18 https://anama.gov.az/en/news/315
19 https://azerbaijan.un.org/en/283794-undp-and-anama-held-side-event-mine-action-and-environmental-sustainability-within-cop29
20 https://x.com/ANAMA_gov_az/status/1867605039608459587
21 https://www.apminebanconvention.org/en/review-conferences/5revcon
ANAMA’sdeminers (Source:ANAMA)
October-December2024QuarterReportofthe agency.Countriesthathavedonatedfundsinclude SaudiArabia,Italy,andtheUnitedArabEmirates.For 2025,BakuwillincreaseANAMA’sbudgetto approximatelyUSD49.9million 22 (85millionmanats), a1.2%increasecomparedtolastyear.However, morefnancialassistanceisnecessary.
Initsfnal2024QuarterlyUpdate,ANAMAdiscussed severalprojectsthatrequireinternationalfundingand assistance.Theyincludeacquiringminedetection dogs,explosivecontainmentchambers,explosive materialtransportationvehicles,groundpenetrating radars(whichcanbemountedonadroneforfaster mappinganddetectionoperations),anddemarcation
andfencingmarkersand signs.Otherrequirements aredirectedattraining andassistance,like explosiveordnancerisk education,technical surveysandfeasibility studies,andminevictim assistance.
Thereareotherissues tomonitorregardinghow internationalactorscan assistAzerbaijan.For example,backin2024, UNDPandANAMA signedastatementof intent 23 toestablishan internationalcentreof excellenceandtraining formineaction.Ayear later,itisunclearifthe facilitieswillbebuiltbut thiscentrewouldbe helpfulfortrainingoperationsofAzerbaijanitroops andotherspecialists.Similarly,duringthe IntersessionalMeetingoftheAnti-PersonnelMine BanConventionlastJune2024,EdsonAsgaro v 24 , AttachéofthePermanentRepresentativeofthe RepublicofAzerbaijantotheUNOfficeandother InternationalOrganizationsinGenevastated,“we believethattheUnitedNationsanditsspecialized agenciessuchasUNMAScouldalsoplayarolein mobilisinginternationalsupportfordemining operationsinAzerbaijan.”ItisuncleariftheUN MineActionServicewillstartamissionin Azerbaijan,butitwouldbebeneficial.Moreover, MineActionRevie w 25 recommendsthatAzerbaijan
22 https://www.azernews.az/nation/235749.html
23 https://www.undp.org/azerbaijan/press-releases/undp-and-anama-signed-statement-intent-cooperation-establishmentinternational-centre-excellence-and-training-mine-action
24 https://www.apminebanconvention.org/fleadmin/_APMBC-DOCUMENTS/Meetings/2024/IM24-6a-UniversalizationAzerbaijan.pdf
25 https://www.mineactionreview.org/assets/downloads/Azerbaijan_Clearing_the_Mines_2024.pdf
accedestotheAnti-PersonnelMineBanConvention (APMBC) 26,adoptsitsrevisedNationalMineAction Standards(NMAS),andBakushouldalso“fnalise andadoptitsnewmineactionstrategy,refectingthe signifcantincreaseincontaminationnowunder Azerbaijan’scontrol.”
Thereisoneotherrequirementthatisworth noting,andwhichwouldbeneftfrominternational support.ANAMAlabelssupportforfemaledemining teamsasapriority.TheQuarterlyReportexplains that“encouraginggendermainstreaminginmine actionandempoweringwomeninreturn, rehabilitation,reintegrationandreconstruction phases.”Genderdiversityandtheroleofwomenas specialistswhoclearlandminesisatopicthat deservesfurtheracademicresearch.Withouta doubt,womenhavealsosteppedforwardtorisktheir livesforthisnoblecause.Afghanwomen 27,for example,clearedlandminesbefore,sadly,the Talibanreturnedtopower.Womenhavealsostepped forwardandbecomedeminersinZimbabwe,“When theopportunitycame,Iwantedtojoin.Toshowto othermen,women,supportersthatuswomencan alsobedeminers,”saidthedeminerRumbidzai 28 . Since2017,thehumanitarianorganizationMAG (MinesAdvisoryGroup) 29 hasbeenworkingin Zimbabwetomakelandsafeagainforlocal communities – femaledeminersconstitutearound 40%ofthepersonnel.
Ihavenotfoundinformationabouthowmany AzerbaijaniwomenareinvolvedinANAMA’sfeld operations.However,morefemalepersonnelwould helpimprovegenderequality,asthesemissions demonstratethatAzerbaijaniwomenarejustas courageousastheirmalecounterparts.International supportformine-removaloperationswould,thus, haveapositivecollateraleffect,demonstratingthe braveryofAzerbaijaniwomen.
26 https://www.apminebanconvention.org/en/
CONCLUSIONS
IfBakuandYerevancansignapeacetreaty, permanentpeacecouldbewithinreachintheSouth Caucasus.Whilepeaceonpaperisimportant,soare activitiesontheground.ForBaku,decontaminating theKarabakhEconomicRegionisapriority.Thedata releasedbyANAMAandotheragenciesaboutthe landmines,UXO,ERW,andIEDslocatedinthepast coupleofyearsdemonstratethatdecontamination willbealong-termproject.Sofar,internationalactors haveprovidedvitalfnancialassistance,technical assistance,expertise,andequipment–includingthe invaluableminedetectiondogs.However,asthis analysishasdemonstrated,moreassistanceis requiredfortheterritoriestobeftforcivilianlife onceagain. ■
ABOUTTHEAUTHOR
WilderAlejandroSánchez isan analystwhofocusesoninternational defense,security,andgeopolitical issuesacrosstheWestern Hemisphere,CentralAsia,and EasternEurope.HeisthePresident of Second Floor Strategies 30,a consultingfrminWashington,DC. Hewroteananalysison“Proliferation ofMines, ImprevisedExplosiveDevices(IEDs)andUnexploded Ordnance (UXO)inColombia” 31 fortheWinter2020-21 IssueoftheCounter-IEDReport.
27 https://unfoundation.org/blog/post/innovation-in-action-brave-afghan-women-clear-landmines-make-history/
28 https://www.maginternational.org/whats-happening/the-female-lens-zimbabwe-stories/
29 https://www.maginternational.org/
30 https://secondfoor-strategies.com/
31 https://counteriedreport.com/proliferation-of-mines-improvised-explosive-devices-ieds-and-unexploded-ordnance-uxo-in-colombia/
2024-2025THREATDYNAMICS:
ByLieutenantColonelJoseMRufas,ChiefofAttacktheNetworksBranch,C-IEDCentreofExcellence
“Nevertrustamanwhoteachesaboutdeathbutyethadnorealexperienceatallaboutit.” (TobaBetainhisbook“MasterofStupidity”,frstpublishedin2011)
Mostprobablyanyreaderwouldagreethatthe Internethastraditionallybeenthemosteffective
sourceoftechnicalknowledgeonplanningand preparationofterroristattacksduringthe21stCentury.
Figure1:CoversofpublicationsoncounteringonlineterrorismbyEUROPOLInternetReferralUnit
Despiteintensiveeffortsbynationalandmultinational authoritiestocombatthedisseminationofmanuals, videosandinstructionsontheInternetformaking improvisedexplosivedevices(IEDs)andhomemade explosives(HMEs),most(ifnotall)ofthevarious publicationsremainavailableonnumerousInternet sitesassociatedwithhumannetworkslinkedto jihadismorothertypesofviolentextremism(e.g. whitesupremacism,anarchism,eco-terrorism,far-left, separatism…).
Butitisnotonlyradical,terroristand/orcriminal organizationsthatareinvolvedindistributingcontenton theInternetthatdescribes:
•Planninganattack
•Acquiringprecursorsandcomponents
•Manufacturingexplosives,incendiaryand hazardoussubstances
•Constructingdevices… …unfortunately,thecurrentconfictinUkraineis posingoneofthemosteffectivesourcesforterrorist performance,asbasedonboththewidelyshownideas andthedisseminationofonlineinstructions.
Thelawofconservationofterroristpropaganda: onlinecontentcanneitherbebannednor destroyed
Aspreviouslysaid,mostofthedigitalmanualsonIEDs andHMEmanufactureareeasilyaccessiblethrough severalonlineopenaccessrepositories.
Butnotonlyjihadismisstillpotentially contributingtotheuseofhomemadeexplosives andimprovisedexplosivedevices:theimprudent socialmediasupportersofbothRussianand Ukrainiansideshavebeenactivelydistributing videosanddocumentsclearlyshowinghowto manufacturehomemadeexplosivesaswellas howtoconstructandusehundredsofdifferent improvisedexplosivedevicesagainstyour adversaries(orvictims…).Foradditional information,youcouldreadseveralarticles publishedinpreviousissuesofthe‘Counter-IED Report’digitalmagazine...
Outofsightoutofmind…
Thearticle ‘Jihadistthreatdynamicsconcerning Europe:Aretheyposingarealityorjust“Argumentum inTerrorem”?’ (Counter-IEDReport,Winter2024/2025 edition),predictsasignifcantincreaseinbothattacks andfoiledplotsrelatedtojihadisminEuropefrom January2024:nodoubtthenexteditionofEuropol's EuropeanUnionTerrorismSituationandTrends(TESAT)reportwillconfrmthistrend.
Oneofthefrstindicatorsidentifedinthefrst monthsof2024wasasignifcantincreaseinthe numberofexplosive-relatedthreatsonpropaganda postersdistributedbymediaoutletsdirectlyor indirectlylinkedtoDAESH.
Informationisnotknowledge,buteverything counts
Oneofthemostworryingmattersduring2024and 2025hasbeenthediversityandlocationofthe differentsourcesspreadingtechnicalinformation aboutthemanufactureofhomemadeexplosivesand
improvisedexplosivedevices:soalongwiththe traditionalArabicorEnglishlanguage-basedsources, hasbeenidentifedthedistributionofHME/IED instructionsinSpanish,Russian,BrazilianorTurkish languages,butalsoinGerman,French,Italian… during2024-2025.
Itwasquiteremarkabletheactivityofpreviously knownjihadistgroupsdistributingHME/IEDmanuals throughdifferentsocialmediameanssuchas Telegram,RocketChat,Element,Chirpwireoreven SImpleX:forsure,theChechenLAMANHOgrouphas beenoneofthemostactiveduring2024,andtheyare stillactiveduringthefrstmonthsof2025.
Thepotentialriskfromtheinformationasshared byLAMANHOgroupismostlybasedontheirhighly didacticalapproach,dedicationonlytoeffectiveand “battle-proven”explosives,devices,andtacticsplus aselectionofcomponentsandprecursorseasyto acquire,effectivetoemploy,andhardtotrack…
Figure5:Onlinemanuals&videosinBrazilian,Turkish&SpanishlanguagesonHMEmanufactureaspublishedduring2024 (Source–RocketChat/Youtube)
Figure6:EnglishlanguageversionofLAMANHO’scatalogueofHME/IEDmanuals (Source:RocketChat)
Theresurgenceoftheveterans
FromMarch2024onwardsbutmostlyduringthefrst monthsof2025,severalaccountsunderthelabelof DAESH-related“AlSaqriFoundationforMilitary Sciences”havenotonlybeenredistributedbutalso
publishedindifferentmanualsinbothArabicand Englishlanguagesonhomemadeexplosives, improvisedexplosivedevices,chemicalbiological radiological(CBR)agents,explosive-ladendronesand terrorist/insurgenttactics,techniquesandprocedures.
Afteryearsofceasingtoprovidetechnicaland tacticalsupporttoterrorismandinsurgency,the infamousAlSaqrimediaoffcehasonceagaintaken theleadonjihadistsocialmedia.
AlongwiththeDAESH-relatedinitiatives,AlQaeda followershavealsopublishedonlinematerialsinthe formofvideosanddocumentsrecoveringtechnical informationthatwasincludedinoldissuesof AlQaedaintheArabianPeninsula(AQAP)AlMalahem (ElectronicArmy)mediaoffce(e.g.INSPIREand WOLVESOFMANHATTANdigitalmagazines).
Additionally,thejihadist“digitallibrary”wasalso reinforcedwiththeredistributionofhundredsofold
publicationsonhomemadeexplosives,improvised explosivedevices,sabotage,guerrillas,improvised frearms,assassinationtechniques,poisons…from editorsbasedinUnitedStatesofAmerica,possiblythe PaladinPress.
Prospective
Whileitremainstobeseenwhetherthetrendof growingonlinedistributionofHME/IEDtutorials andvideoswillcontinueinthefuture,jihadist effortstodisseminatethistechnicalandtactical informationhavebeenhaltedduringRamadan2025: weshallsee!
Figure7:AlSaqriHME&CBRrelatedmanualsasdistributed/redistributedduring2025 (Source:RocketChat/Matrix)
Figure8:ReferencestoIED/HMEmanualsasreleasedbyalternatejihadistsourcesduring2024&2025 (Source:X/RocketChat)
Figure9:Referencestoarsonandincendiarydevicesbyjihadistpropagandaduring2024&2025 (Source:RocketChat/X)
AfterthehighimpactoftherecentOlympicGames andtheIsraeliattacksonPalestineandLebanon,it maybediffcultforjihadismtoregaintherhythmof disseminatingonlineinstructionsformaking improvisedexplosivedevicesandhomemade explosives.
Nonetheless,andintheshortterm,theUkrainian confictisforsuregoingtokeepalivethereferences (andideas)toIEDmanufactureanduse.■
“Whenworkingwithexplosives,I'vefound thatattitudeiseverything.”
(AlanBradleyinhisbook“IAmHalf-SickofShadows”,frstpublishedin2011)
REFERENCES
•‘JihadistthreatdynamicsconcerningEurope:Are theyposingarealityorjust“Argumentumin Terrorem”?’(Counter-IEDReport,Winter2024/25 edition)
•X(formerTwitter)
•Telegram
•RocketChat
•Element
•Chirpwire
•SimpleX
Disclaimer
Thisarticledoesnotrepresenttheopinionofanynational ormultinationalorganisation;itswholecontentshould onlybeconsideredastheopinionoftheauthor.Asall informationhasbeenobtainedfromopensources, potentialmistakescouldhavebeenmadeduringthe researchprocess.Pleasefeelfreetosendyour comments,correctionsandinputstotheauthor;theywill behighlyappreciated.
ABOUTTHEAUTHOR
LieutenantColonelJoseMRufas graduatedfromthe SpanishArmyMilitaryAcademyin1993.Hewas commissionedintotheC-IEDCentreofExcellenceas HeadoftheDefeattheDeviceBranchinAugust2016 andcurrentlyholdsthepostofChiefofAttackthe NetworksBranch.AsaMilitaryEngineerOffcer,his backgroundhasbeenmainlybasedonExplosive OrdnanceDisposalactivitiesintheSpanishArmyand C-IEDstaffissuesatthemultinationalheadquarters.In additiontohisEODOperator/EODOffcereducation, heattendedsomeothermilitarycoursesregarding Parachuting,ArmyStaff,InformationOperations,War CollegeGeneral/JointStaff,MilitarySearch,Technical ExploitationOperations,WeaponsIntelligenceTeam, ExploitationLaboratories,HomemadeExplosivesand otherC-IEDcourses.Hisoperationalassignments includeBosniaandHerzegovina(3),Afghanistan(3), theRepublicofEcuador,IraqandUganda.
E-mail:jrufas@ciedcoe.org
Counter-IEDReporteditorialteaminvitesgovernmentbodies,armypersonnel,researchers, industryexpertstocontributetheirarticles,casestudies,whitepaperstothereport.
Wearelookingforboththeoreticalandpracticebasednon-promotionaleditorialcontributions. Onlyoriginal,sofarnotpublishedarticlesareaccepted.
Allenquiriesandarticlesshouldbesubmittedbyemailto: editorial@deltabusinessmedia.com
Formoreinformationpleasevisit: www.counteriedreport.com/editorial
UniquecontentIGlobalreachIInprintandonline
Keepup-to-datewiththelatestC-IED,EODandCBRNenewsanddevelopments. Subscribeat www.counteriedreport.com/subscribe
Oneoperatingplatform
Doublethecapability
CR+DRcombinedsystems enableyourteamtorespond quickly,withanoptimised solution, for Counter-EOandCBRNE missions