ISSN2050-6732(Print)
ISSN2050-6740(Online)


DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL: ASTUDYINTOTHECOGNITIVEPROCESSESUSEDBYPRACTITIONERS ISIMPLEMENTATIONOFWESTERNC-IEDENTERPRISESSUITABLE WHENPROVIDINGDONORC-IEDASSISTANCE?
ASTRATEGICPRINCIPLESAPPROACHTOREGIONALC-IEDENTERPRISES DEVELOPMENTFROMIMPROVISEDHOMEMADETOMASSMARKET CONSUMERELECTRONICSCOMPONENTSINIEDs
AIRBORNEMAGNETICS-AVIABLETOOLFORDETECTIONANDQUALITYCONTROL NEXT-GENERATIONDEMININGWITHAIANDDRONES




UNATTENDEDPACKAGES–THESECURITYOFFICER’SDILEMMA PIRSENSORSINIEDs USINGCONSTANTPOTENTIALGENERATORS
INDIA–THEIEDCHALLENGES
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
Counter-IEDReport Spring/Summer2023

REPORTCONTRIBUTORS MEDIAPARTNERS



Theopinionsandviewsexpressedintheeditorialcontentinthisreportare thoseoftheauthorsaloneanddonotnecessarilyrepresenttheviewsofany organisationwithwhichtheymaybeassociated.Materialinadvertisements andpromotionalfeaturesmaybeconsideredtorepresenttheviewsofthe advertisersandpromoters.Theviewsandopinionsexpressedinthisreport donotnecessarilyexpresstheviewsofthepublisher.Whileeverycarehas beentakeninthepreparationofthereport,thepublisherisnotresponsible forsuchopinionsandviewsorforanyinaccuraciesinthearticles.















©2023.Theentirecontentsofthispublicationareprotectedbycopyright. Fulldetailsareavailablefromthepublisher.Allrightsreserved.Nopartofthis publicationmaybereproduced,storedinaretrievalsystemortransmittedin anyformorbyanymeans,electronic,mechanicalphotocopying,recording orotherwise,withoutthepriorpermissionofthecopyrightowner.


3 counteriedreport.com
Counter-IEDReport PublishedbyDeltaBusinessMediaLimited 3rdfoor,207RegentStreet London,W1B3HH UnitedKingdom Tel:+44(0)2071932303
www.counteriedreport.com
info@deltabusinessmedia.com
ISSN2050-6732(Print) ISSN2050-6740(Online)
CONTENTS
CONTENTS
IFCNATOEODDEMONSTRATIONSANDTRIALS2023
5ICORTECHNOLOGY
7GARRETTMETALDETECTORS
8SAFEPROGROUPINC.
83DX-RAYLTD
9FOREWORD
ByRobHyde-Bales,ConsultingEditor,Counter-IEDReport
11TELEDYNEICM
13DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL:
ASTUDYINTOTHECOGNITIVEPROCESSESUSEDBYPRACTITIONERS
ByEdwinA.Bundy,Ph.D.inF.S.,Ph.D.inEd,CIPBI ProgramManager(GS-15),EOD/EXOSubgroup, IrregularWarfareTechnicalSupportDirectorate
23ISIMPLEMENTATIONOFWESTERNC-IEDENTERPRISESSUITABLE WHENPROVIDINGDONORC-IEDASSISTANCE?
ByPaulAmoroso,anexplosivehazardsspecialist
atAssessedMitigationOptions(AMO)consultancy
30DEFENSE&SECURITY2023
31ASTRATEGICPRINCIPLESAPPROACHTOREGIONALC-IEDENTERPRISES
ByPaulAmoroso,anexplosivehazardsspecialist
atAssessedMitigationOptions(AMO)consultancy
4 COUNTER-IEDREPORT,Spring/Summer2023
SMART, STRONG, AFFORDABLE OUR LATEST CUTTING-EDGE ROBOT!
ADVANCE CAPABILITIES INCLUDE:
• Crystal-clear image transmission through IP Mesh COFDM radios
• Convenient pre-set positions for easy operation
• Real-time 3D Avatar positioning for enhance accuracy
• Integrated LIDAR and precise crosshairs targeting
• User-friendly touchscreen CCU interface for intuitive control
• Fine-tuned controls for maximum precision
• Choice of control style: gamepad or joystick
DISCOVER THE FUTURE OF ROBOTICS WITH OUR MOST ADVANCED CALIBER® YET !



CHECK OUT OTHER
CONTINUING THE LEGACY OF SAFETY AND RELIABILITY !
With new management and ownership, Proparms Limited has refreshed its product line with innovative equipment. Maintaining its position as the primary supplier of waterjet distrupters and de-armers globally for over 45 years, Proparms is serving EOD/IED operators in over 80 countries.
Experience the unmatched safety & reliability, ease of use, and swift deployment capability to render safe threats of any size.
CALIBER® MK4 MINI-CALIBER® MK3 CALIBER® CALIBER® T5
CALIBER® ROBOTS
Tel:+1.450.658.5207 | info@proparms.com | proparms.com Tel:+1.450.658.5207 | info@proparms.com | proparms.com
CONTENTS
38DEVELOPMENTFROMIMPROVISEDHOMEMADETOMASSMARKET
CONSUMERELECTRONICSCOMPONENTSINIEDs
BySerkanKoc,Major(OF-3)TUR-A,ElectronicWarfareSpecialist,NATOC-IEDCoE
47 AIRBORNEMAGNETICS-AVIABLETOOLFORDETECTIONANDQUALITYCONTROL
ByDipl.-Ing.WolfgangSuß,ManagingDirector,SENSYS
54NEXT-GENERATIONDEMININGWITHAIANDDRONES
ADVANCEDSOFTWAREALGORITHMSPOWERNEXT-GENSOLUTIONS
FORAUTOMATINGTHREATDETECTIONANDIDENTIFICATION BySafeProAI(aSafeProGroupInc.Company)
58EDEX2023
59UNATTENDEDPACKAGES–THESECURITYOFFICER’SDILEMMA
ByVincentDeery,CEO,3DX-RayLtd
62IDEF2023
63PIRSENSORSINIEDs USINGCONSTANTPOTENTIALGENERATORS
ByTeledyneICM
68INDIA–THEIEDCHALLENGES
ByColonelHRNaiduGade–IndianArmyVeteran
76“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
ByLieutenantColonelJoseMRufas,ChiefofAttacktheNetworksBranch, C-IEDCentreofExcellence
IBCMILIPOLPARIS2023
OBCSCANNAMSC
6 COUNTER-IEDREPORT,Spring/Summer2023
CONTENTS
Optimum Detection
Your quest is our mission Advance technology
and highly versatile
Garrett’s AML (All Metals Locator) detector is trusted in many countries for mines, UXO, and IED searches. Low metal content targets to large metallic items are detected in ALL soils and shallow water with full detection capability.

Uncover the Unseen™






Next-GenDemining, EOD/UXO,Ballistics ServingtheneedsofGovernment, MilitaryandHumanitarianCustomers forOveraDecade PROTECTINGTHOSEWHOPROTECTUSALL AMORPHOUS SILICON PORTABLE X-RAY SYSTEM For more infomation call +44 (0) 1509 817400 or visit www.3dx-ray.com Fully integrated amorphous silicon system c/w 150kV generator High penetration with sub-millimetre resolution Powerful image enhancement and analysis tools (ISC)
FOREWORD
Theearlypartofthisyearhasbeendominatedby thecontinuingarmedconfictinUkrainewhich startedin2014andledtothefull-scaleRussian invasioninFebruary2022.
Aswithmostarmedconficts,thewarinUkraineis leavingbehindanever-growinglegacyofunexploded landmines,operationallyfunctionalImprovised ExplosiveDevices(IEDs)andotherExplosive RemnantsofWar(ERW).Anestimated174,000 squarekilometresofUkrainianterritoryarecontaminatedbylandmines–bothanti-tankandantipersonnel1 –thelatterincontraventionoftheOttawa Treaty1997banningtheuseofanti-personnelmines. ThecontaminatedareaislargerthanEngland, NorthernIrelandandWalescombinedandrepresents amassiveclearancetaskasandwhentheoperational environmentpermitssuchclearance.
Accordingtoajointassessmentreleasedon23 March2023bytheGovernmentofUkraine,theWorld BankGroup,theEuropeanCommission,andtheUnited Nations,Ukraineneeds$37.4billiontocarryout humanitariandeminingofitslands.Thissumincludes morethan$397millionneededjustfortheyear2023.2
Intermsofglobaldeminingeffortstherearesome positivenews.AccordingtoareportbytheCambodian MineActionandVictimAssistanceAuthority(CMAA), thefrstfourmonthsofthisyearsawa65percent decreaseinnumberofvictimscomparedtothesame periodlastyear.3
InYemen,thefragiletrucebetweenwarringparties bringssomepositivedevelopmentsandhopeforthe countryaftermorethaneightyearsofwar.Yemen alongsideIraq,Afghanistan,Cambodia,Bosnia& HerzegovinaandCroatia,tonameafew,isoneofthe mostLandmineandExplosiveOrdnance(EO) contaminatedcountries,makingmanyresidential neighbourhoodsuninhabitableanddangerous.
InAfghanistan,heavyERWlandcontamination spanningfordecadesbacktotheSovietinvasion posesadditionalchallengestothefarmersandrural communitiesdevastatedbyfoodshortagesand insecurity.AccordingtotheUnitedNationsOffcefor theCoordinationofHumanitarianAffairs(OCHA)some $18.3millionisneededyearlyforsurvey,explosive ordnancedisposal,andlandmine/ERWclearance inAfghanistan.4
1 https://www.hrw.org/news/2023/01/31/ukraine-banned-landmines-harm-civilians
2 https://documents1.worldbank.org/curated/en/099184503212328877/pdf/P1801740d1177f03c0ab180057556615497.pdf
3 https://phnompenhpost.com/national/cmaa-mine-victims-down-65-cent
4 https://twitter.com/OCHAAfg/status/1630094885112934407
FOREWORD
9 counteriedreport.com
ByRobHyde-Bales,ConsultingEditor,Counter-IEDReport
Theviolencecausedbyimprovisedexplosive devices(IEDs)continuesaroundtheworld.Oneofthe deadliestattacksthisyeartookplaceon30January 2023whenasuicidebomberdetonatedhisvest atthePeshawarPoliceLinesmosqueinPakistan, asnumerousworshippers,includingmanylocal policemen,wereprayinginside.Atleast100people werekilledintheblastand225wereinjured.
Theuseofcarbombingsasapreferredmethod ofattacktargetinggovernmentoffcials,securityforces, lawenforcementoffcersandjournalistsisnotedin Somalia,Kenya,Nigeria,Niger,Cameroon,Burkina Faso,Mali,Iraq,Syria,India,Pakistan,Afghanistan, Cyprus,Myanmar,RussiaandRussian-occupied territoriesofUkraine.
Inamostthought-provokingarticle, Dr.EdwinA. Bundy,a SeniorProgramManagerfortheU.S. DepartmentofDefenseattheIrregularWarfare TechnicalSupportDirectorate(IWTSD), discusses decision-makingandproblem-solvinginbombdisposal anddescribesarecentstudyundertakenintothe cognitiveprocessesusedbybombdisposal practitioners.Inearly2022datawascollectedfrom currentandformerEODpractitionersin17countriesin ordertoinvestigatecognitiveapproachesusedin problem-solvinganddecision-making.Thestudyused IEDsasthecatalysttostimulatecognitiveprocessesin studyparticipants.Theparticipantshadbetween1and 35yearsofexperienceandwidelydifferingeducation levels.Forthestudy,participantshadaccesstoan onlinesitecomprising18scenarios,eachconsistingof twoorthreeimagesofapotentialIEDcircuit,checklists oflabelstoidentifycomponentsofthecircuit,potential hazardstheyconsideredassociatedwiththecircuit,and thecircuit’stype-by-function.Thescenariosrangedfrom veryeasytoverydiffcult.Participantswerealsoasked toidentifyfactorsorfeaturesregardingthecircuitsthat drovetheirdecisionmakingandfnallytoratetheir confdencelevelsineachscenariointermsofcircuit components,potentialhazards,andtype-by-function. Datafromthestudyparticipantssuggestthattheyused pattern-matchingorheuristicstoreach90%oftheir decisions.Incontrast,thestudyfoundthatlessthan 6%ofdecision-makingistheresultofamore
deliberateandanalyticalprocess.Theauthoropines thattheresultsofthisstudyhavesomeveryserious implications,nottheleastofwhichisforhowbomb techniciansaretrained.Whilemostdecisionsmade duringanaverageday,inanyoccupationoractivity, arebasedonlearned,repetitivebehaviours,or whatcognitivescientistscallheuristics,innewor criticalsituations,relyingonheuristicscanfail catastrophically.Thecommunityowesittobomb technicianstoprovidebettertoolsandtrainingin thecognitivedomain.Notonlywillthisimprove survivability,butitwillallowourpractitionersto keeppacewithadversaries,whoaremorelikelythan ever,tousenot-yet-seencomponentsandcircuitsin theirdevices.
Inhisinformativearticleonthetransitionfromhomemadetomassproduced,commercialoff-the-shelf (COTS)electroniccomponentsintheproductionof IEDs,MajorSerkanKoç oftheTurkishArmyand currentlyservingastheEWSpecialistat theNATOCounter-IEDCentreofExcellenceexamines theimpactofthistransitionbothontheproducersof IEDsandIEDDspecialists.Hepointsoutthatthemass productionofthesecomponentshasresultedintheir ever-increasingavailabilitytogetherwithfallingprices. Inparticular,theproliferationofRadioControlledIEDs (RCIEDs)haspresentedalowcost,highlyfexibleand unpredictablethreattotheC-IEDworld.Accordingto INTERPOL,internationalorganisedcrimeisamajor componentinthehighlylucrativetradeincounterfeit goods–includingcounterfeitelectroniccomponents, manyofwhicharecomponentsofRCIEDs,toinclude transformers,relays,timers,fusesandwiring accessories.Therearestronglinksbetweenthistrade andillegalnarcotics,moneylaunderingandgeneral systemicglobalcorruption.IntheCounter-IED campaignboththeAttacktheNetworksandDefeatthe Devicepillarsofthecampaignareusedextensivelyto combattheubiquitousthreatofRCIEDs.COTS electronicdevicesenablegreateruseofthecontested electromagneticenvironment–ofparticularuseinthe RCIEDfeld.Theyalsomakeitmorediffculttoidentify theelectronicsignatureofanIEDmanufacturer.There isnodoubtthattheomnipresentRCIEDstogetherwith
FOREWORD 10 COUNTER-IEDREPORT,Spring/Summer2023
thevictimoperatedpressureplatesub-surfaceIEDs continuetocreatemajorchallengestoboththegeneral publicandtheCounter-IEDoperativesinbothcurrent andformerwarzonesandotherhostileenvironments.

Inhisthought-provokingarticleonthesuitabilityand effectivenessofWesternCounter-IEDenterprises whenprovidingdonorC-IEDassistance,PaulAmoroso ofAssessedMitigationOptionsexaminesthe challengesandpotentialpitfallsinherentinsuch assistance.Heusestheterm “Counter-IEDenterprise”asa collectivetermtodescribeallaspects ofC-IEDactivitiesdesignedand intendedtomatchandideally overmatchtheuseorthreateneduse ofIEDs.Heopinesthat,giventhe transnationalnatureoftheIEDthreat today,regionallycoherentC-IED responsesarerequired,basedon strategicapproaches.Heexamines theneedforregionalC-IED enterprisesastodate,insomecases theeffortsofWesternC-IEDdonor enterpriseshavebeendisjointed, lackingincoordination,and cooperationandoftenresultingin duplicationofeffort.Aspartofhis research,heidentifedC-IED strategicprinciplesforEastAfrica.He examinesregionalandglobalC-IED effortsincludingthoseoftheUNand AfricanUnion.Hefurtherhighlights responsesfromtheUS,NATO,the UKandAfghanistan.TheC-IED experienceoftheUKwashoned duringtheso-called“Troubles”in NorthernIrelandfrom1969onwards, whenthesecurityforcesinboth NorthernIrelandandmainlandUK facedthemostskilfulbombmakersin theworldatthattime.Hehighlights Afghanistanasonenationbeyond WesternC-IEDeffortsthathasa nationalC-IEDstrategy,dueinlarge
measuretothepresenceofNATOforcesfghtingthe Taliban2004-2014.Heconcludesthattodevelopan effectiveC-IEDstrategy,strategicprinciplesare requiredtoachieverequisiteimpactsandoutcomes whenprovidingC-IEDdonorassistance.
Dipl.-Ing.WolfgangSüß,istheManagingDirectorof SENSYS,aGermancompanybasedeastofBerlin, whichmanufacturesmagnetometersandtimedomain electromagnetics.Inhisinformativearticlehe

→ Up and running in less than 90 seconds

→ Lightweight (less than 6.5 kg/14 lbs)
→ Wireless or cable driven
→ High quality imaging
→ Radiation shielding


→ Telescopic arm (up to 65 cm/26 in) www.teledyneicm.com

FOREWORD 11 counteriedreport.com REAL-TIME X-RAY INSPECTION GO-SCAN
C-VIEW
THE PARTNER TO YOUR SECURITY INSPECTION
describeshowCOTSdronescombinedwithadditional computingpowerandmagnetometersarebeingused inthefeldforUXOdetection,areaobservationand qualitycontrol.SENSYSfocusonFluxgate Magnetometers–passivesensorsthatmeasurethe Earth’smagneticfeld.Ferrousobjectssuchas landminesdistorttheEarth’smagneticfuxlinesand thisisdetectedbythemagnetometersasanomaliesin theEarth’smagneticfeld.Thedetectionsystem describedinthearticlecomprisestheSENSYS MagDroneR4Datalogger,fveSENSYSFluxgate sensors,combinedwiththeLatvianproduced SkyHubTrueTerrainFollowingsystemallmountedon aCOTSDJIM300commercialdrone.This enablesthe droneinanautonomousterrainfollowingmode,ideally ataheightbetween0.5and1meteronapreprogrammedfightpatterntocoverupto30hectaresin asingleday.Hedescribestwoprojectsusingthis system.Thefrstisonafringrangeordnanceimpact areawhichwasusedfrstbytheSovietarmedforcesin theerstwhileDDR,andsubsequentlybytheGerman Bundeswehr.Theotherprojectisthesurveyofaformer GermanWorldWarTwoairfeldconstructedbyforced labourtowardstheendofthewar.Inbothoperationsthe SENSYSdronemountedsurveillancesystemhas provedtobehighlyeffective.Ithasalsobeenused elsewhereinGermanyandinUkraine.SENSYSisnow turningitsattentiontothechallengeoflocatingnonferrousERW.
InhishighlytopicalarticleVincentDeery,CEOof 3DX-RayLtdexaminesthesecurityissuesassociated withunattendedpackages.Hebeginswithanoverview oftheglobalsecuritysituationtodayandnotesthat therewasawelcomereductioninbothdeathsand incidentsresultingfromterroristattacksfrom2021to 2022.However,ofthetoptenmostlethalattacks,six involvedIEDstodevastatingeffect,illustratingthat explosivesremainafavouredmethodofattackby terrorists.InEuropefor2021,themajorityofreported terroristattackswereclassifedasjihadistterrorism withacontinuingintenttousebothIEDsandIIDsas weaponsofattack.Hethendescribestheproblemof anorganisation’ssecurityoffcerwhenconfrontedby anunattendedpackage.Iftheoriginofthepackage
cannotbeidentifed,thenthesecurityoffcerneedsto identifythecontentsofthepackage.Ifthiscannotbe donevisually,thedilemmaisthenwhethertoescalate toafull-scalebombthreatincidentnecessitatingthe evacuationofanareaortakereasonablestepsto identifythecontentsofthepackage.Thesurest methodofsuchidentifcationisbymeansofaportable x-rayscanner.SuchascannerallowstheEOD operatortoexaminethecontentsofthepackage withouttouchingordisturbingit.3DX-Rayoffersa comprehensiverangeofportablescanningsystems. Themostsignifcanttechnicaldevelopmentinx-ray scanningsystemshasbeentheintroductionofcolour differentiatedscanswhichenabletheoperatorto accuratelyidentifythecontentsofthepackage.The 3DX-Raysuiteofscannersutilisesthreecolourscan systems,whereasmostotherscannersusejusttwo, thusreducingtheaccuracyofpackagecontents identifcation.Astheauthorpointsout,allsecurity offcersshouldconsidertheacquisitionofaportable x-rayscanner,butseeingcontentsinjustblackand whiteisnolongergoodenough. ■
RobHyde-Balesbiography
DuringhiscareerintheUKRoyal Engineers, RobHyde-Bales was responsibleforlandmineclearancein Libyaand,morelatterly,Afghanistan intherunningofthefrstUnited Nationshumanitarianlandmine clearancetrainingprogramme–OperationSalam.TheprogrammetrainedAfghanmale refugeesinlandmineclearancetechniques,andAfghan womenandchildreninmineawarenessandavoidance training.MorerecentlyhesetuptheCaribbeanSearch CentreinKingston,Jamaica.TheCentreisdesignedto trainsecurityforcesacrosstheCaribbeaninmodern searchtechniques.Afterretiringfromthearmyhejoined CranfeldUniversityatShrivenham,nearOxford,and undertookaresearchprojectonbehalfoftheUK MinistryofDefencethatexaminedwaystoimprovethe sharingofIEDthreatinformationbetweenthemilitary andcivilianorganisationsinhazardousareas.

FOREWORD 12 COUNTER-IEDREPORT,Spring/Summer2023
DECISION-MAKINGANDPROBLEM-SOLVING INBOMBDISPOSAL:

ASTUDYINTOTHECOGNITIVEPROCESSESUSEDBYPRACTITIONERS
ByEdwinA.Bundy,Ph.D.inF.S.,Ph.D.inEd,CIPBI ProgramManager(GS-15),EOD/EXOSubgroup,IrregularWarfareTechnicalSupportDirectorate
INTRODUCTIONTOTHESTUDY
Inearly2022,datawascollectedfromcurrentand formermilitaryandpublicsafetybombtechniciansfrom 17countries,toinvestigatecognitiveapproachesused inthiscommunityforproblem-solvinganddecision making.Thestudyusedimprovisedexplosivedevices (IEDs)asthecatalysttostimulatecognitiveprocesses instudyparticipantsrelatedtodecision-makingand problem-solving,andvariousdemographicfactors wereexaminedtodetermineifvariablescouldbe identifedthatmadesomebombtechniciansbetterat performingthesecognitivefunctionsthanothers. Studyparticipantshadfrom1to35yearsof experience,andeducationlevelsrangedfromthe equivalentofahigh-schooleducation,toseveral participantswithaPh.D.Additionally,information relatedtofactorslikelengthofinitialbombdisposal training,andanyspecializedIEDelectronicstraining, wascaptured,aswellasformalelectronicstraining (i.e.,atechnicaloracademicdegreeinelectronics), andwhetherornotastudyparticipantwasanIED electronicstrainerforotherbombtechnicians.
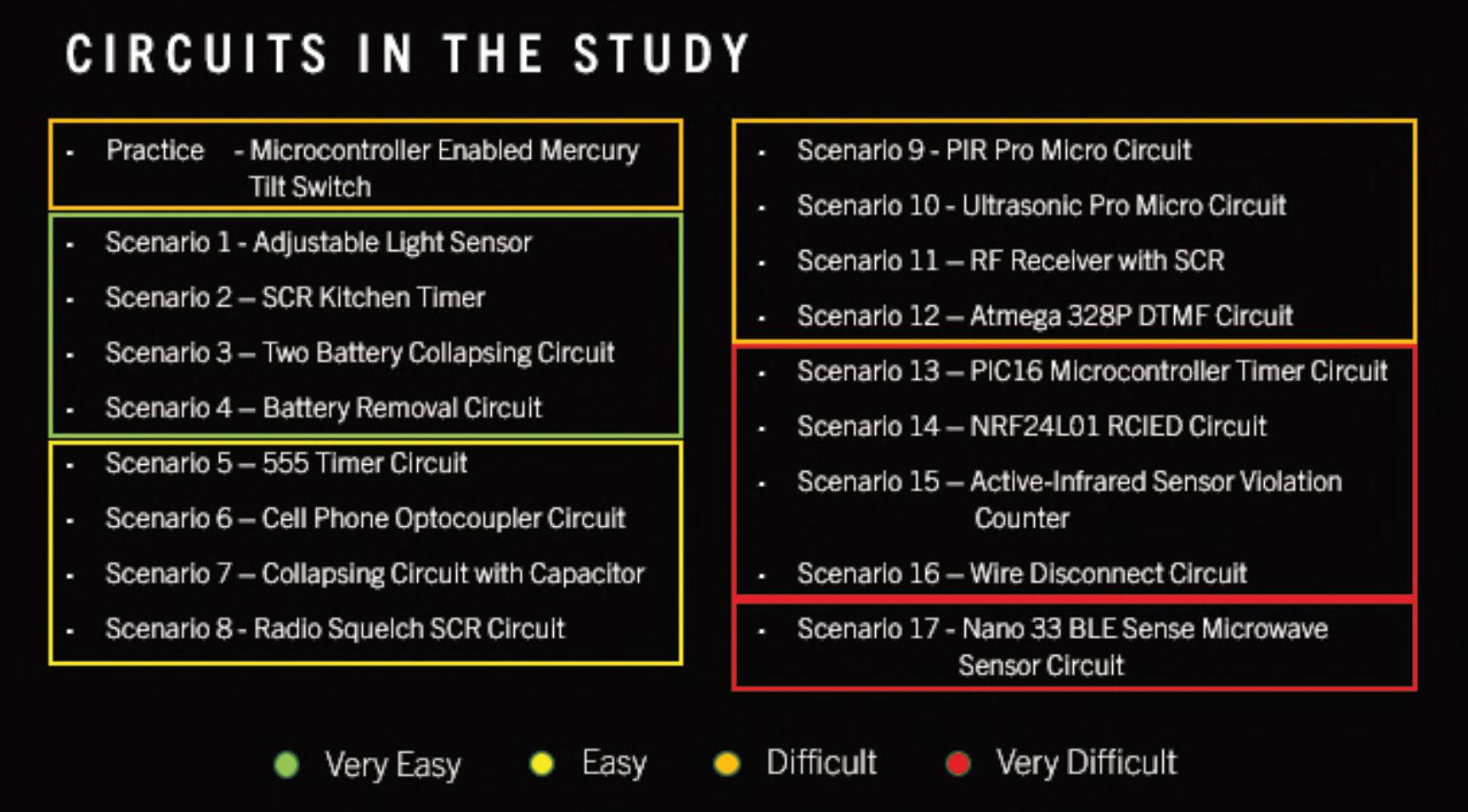
Afterapplyingtobeconsideredforthestudy,a processthatwasusedtoverifythatapplicantswerein factcurrentorformerbombtechnicians,participants weregivenaccesstoanonlinesiteconsistingof18 scenarios(seeFigure1),witheachscenarioconsisting oftwotothreeimagesofapotentialIEDcircuit,and
checklistsoflabelstoidentifycomponentsinthecircuit; anyhazardstheyfeltwereassociatedwiththecircuit; andthecircuit’stype-by-function.Allcomponentsforthe circuitwerevisible(i.e.,nohiddencomponents),andifa nomenclaturewasstampedinto,orsilkscreenedontoa component,atleastoneoftheimagesincludedensured thatthesemarkingswereclearlyvisible.
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL
13 counteriedreport.com
Forhazardsandcircuittype-by-function,participants werealsoaskedtofllinafree-textfeldidentifyingthe factorsorfeaturesregardingthecircuitthatdrovetheir decision-making.Participantscouldalsosuggest additionalcomponents,hazards,andcircuittypes-byfunctioniftheyfeltanywereinadvertentlyleftoutofthe relevantchecklists.Finally,studyparticipantswere alsoaskedtoratetheirownconfdencelevels regardingdecisionsmadeforeachcategory(i.e., components,associatedhazards,andcircuittype-byfunction).Qualitatively,thishelpedinunderstandingif thosewithmoretrainingorexperienceweremore confdentintheirdecision-makingcapabilitiesthan thosewithlesstrainingandexperience,andthe degreetowhichthatwaswarranted.
Inadditiontotheprincipalinvestigatorbeingan experiencedresearcherandaformerU.S.Army ExplosiveOrdnanceDisposal(EOD)technician, standardchecksandbalanceswereusedforthisstudy. Aswithallhumansubjectsresearch,approvalwas soughtandgrantedbyanInstitutionalReviewBoard, andoversightwasconductedbyanacademicreview committeeconsistingofDr.JohnFrucci,aformerbomb
squadcommanderandExecutiveDirectoroftheSchool ofForensicSciencesatOklahomaStateUniversity;Dr. KirkYeager,ChiefExplosivesScientistfortheU.S. FederalBureauofInvestigations;Dr.CJCowlin,a formerU.S.NavyEODtechnicianandcurrentDirectorat LargeforBombTechsWithoutBorders;andDr.Jason Beaman,ChairofPsychiatryandBehavioralSciencesat OklahomaStateUniversityCenterforHealthSciences.
Thecontentforthisstudywasvettedthroughuseof anexpertpanel.Thispanelconsistedofsubjectmatter experts(SMEs)inthefeldsofbombdisposalandIED electronics,andselectedbasedondepthandbreadth ofknowledgeandexperience.Thepanelconsistedof ChiefSuperintendent(Ret)MichaelCardash,Israel NationalPoliceBombDisposalDivision;Lt.Col,Adam Modd,NewZealandSpecialAirService;SpecialAgent BombTechnician(Ret)RobertvonLoewenfeldt,South CarolinaLawEnforcementDivision;SergeantRobert Epps,BombSquadCommander,RiversideCounty CaliforniaSheriffDepartment;Mr.JaredFrench,aU.S. DoDTacticalBombTechnician;andMr.RickHayworth, aForensicExaminerandTechnicalLeadforthe TechnicalExploitationUnitattheFBI’sTerrorist
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL 14 COUNTER-IEDREPORT,Spring/Summer2023
Figure1:StudycircuitsanddegreeofdiffcultyasratedbytheExpertPanel.
ExplosiveDeviceAnalyticalCenter(TEDAC).
Mr.Hayworthwastheonlynon-bombtechnicianin thegroup,butisaninternationallyrecognizedIED electronicsexpert,andholdsanadvanceddegreein ElectronicsEngineering.
Becausethestudywasconductedusingawebbasedplatform,thestudywasnaturallylimitedto participantswhohadaccesstotheinternet,and becausethedatacollectioninstrumentwaswrittenin English,itwasalsoassumedthatparticipantshada technicalunderstandingoftheEnglishlanguage.One ofthefnalassumptionswasthatbecausethiswasa voluntarystudy,andparticipantswereself-selected, thattheywerelikelytohaveaninterestinIED electronics,andthereforetheresultsofthisstudy couldpotentiallybeskewedinthedirectionofhigher successratesforcomponentidentifcation,hazard assessment,andcircuittypes-by-functiondetermination.
FINDINGS
Itshouldbenotedbythereader,thatthesefndings shouldnotbeinterpretedeitherdirectlyorindirectly,as thisauthor,theacademicreviewcommittee,ortheexpert panel,suggestingthatbombtechniciansarenothighly capable,orprofcientatthejobstheyaretrainedtodo. Thisstudysimplyfocusesonwhattypesofcognitive reasoningapproachesbombtechniciansuseindecision making,andlooksathoweffectivetheseapproachesare usedforproblemsolvingbybombtechniciansintheIED electronicsdomain.Furtherresearchneedstobe conductedtoseeifsimilarapproachesareusedby bombtechniciansinotherdomains,suchasx-ray interpretation,andifsimilarcorrelationsexist.
Thatsaid,theresultsofthestudywererathereyeopening.Datagatheredfromstudyparticipantssuggests thatoverall,bombtechniciansusepattern-matchingfor over90%oftheirdecision-making,ratherthanusinga truehypothetico-deductivereasoningprocess.Cognitive psychologistsclassifythisasSystem1thinking,whichis anintuitivemodeofthinking,soisconductedalmost effortlessly.Thissystemisresponsibleforspontaneous orimmediatereactionstostimuli,andisoftendrivenby pre-existingbiasesoranemotionalresponse.System1 thinkingreliesalmostexclusivelyonheuristics,ormental
shortcuts,andallowsdecisionmakingtooccurwithvery littleconsciouseffortorrefection.
Conversely,System2thinkingwasusedbystudy participantslessthan6%ofthetimewhileconducting theiranalyses.System2thinkingisamoredeliberate andanalyticalprocessthatrequiresgreaterlevelsof attentionandcognitiveeffort.Thissystemisinvolvedin complexproblem-solvingtasks,andischaracterizedby deliberate,effortfulcognitiveprocessing,andcan overrideautomaticresponsesgeneratedbySystem1 thinking,whichallowstheusertoconsideralternative pathsoroptionswhileinuse.
Together,System1andSystem2thinkingarereferred toasDual-Processtheory,anditiswidelybelievedthat thesetwosystemsoperateinparallel,interactingwith eachother,butsometimescompetingforcontrolover thoughtprocesses.Inthisstudyhowever,System1 thinkingwasclearlydominant,andsuggeststhatrather thanparticipantsconductingwhatmightbethoughtofas atrueanalysisofthecircuit,theykeyedinoncertain components,presumablythosetheyhadbeentaught duringtraining,orhadencounteredatsomeotherpoint intheircareer.Theythenbasedtheremainderoftheir decisionsonlyonthepresenceofthoseveryspecifc components,andregardlessofwhatothercomponents mighthavebeenpresent,someunquestionablymore dangeroustothebombtechnicianthantheones recognized,theseunrecognizedcomponentswerenot factoredintofurtherdecisionmaking.
Anexampleisprobablywarrantedhere.Acomponentcommonlyusedinbombdisposaltraining, whetherduringinitialorsustainmenttraining,isthe555 integratedcircuit(IC).Thiscircuitiseasilyrecognized bymostbomb technicians,and iscommonlyreferredtoasa

15 counteriedreport.com
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL
“555-timer.”Ithas aratherdistinct appearance,in thatitissmall, black,andhas8 pins/legs(see Image1).
Image1:555IC.
Thisbecomesproblematicwhenbombtechnicians starttothinkthatanysmall,black,8-pinICisa555timer,andthereforebyextension,carriesthesame

associatedhazards,andalwayscreatesaspecifc circuittype-by-function.Assuggestedbydata collectedduringthestudy,ifacomponentwithsimilar physicalcharacteristicsisusedinacircuit,even thoughavisiblenomenclatureispresent,clearly indicatingotherwise(seeImage2),manystudy participantsdefaultedtoselectingthe555IC,and indicatedthatthecircuitwasforuseasa“Time”typeby-function,aswellascarryingatimehazard.Thisis problematic,notonlybecause555ICsarecapableof beingusedforfunctionsotherthantiming,butthere arenumerousothercomponentswithsimilarphysical characteristicsthatpresentmanyothertypesof potentialhazards.
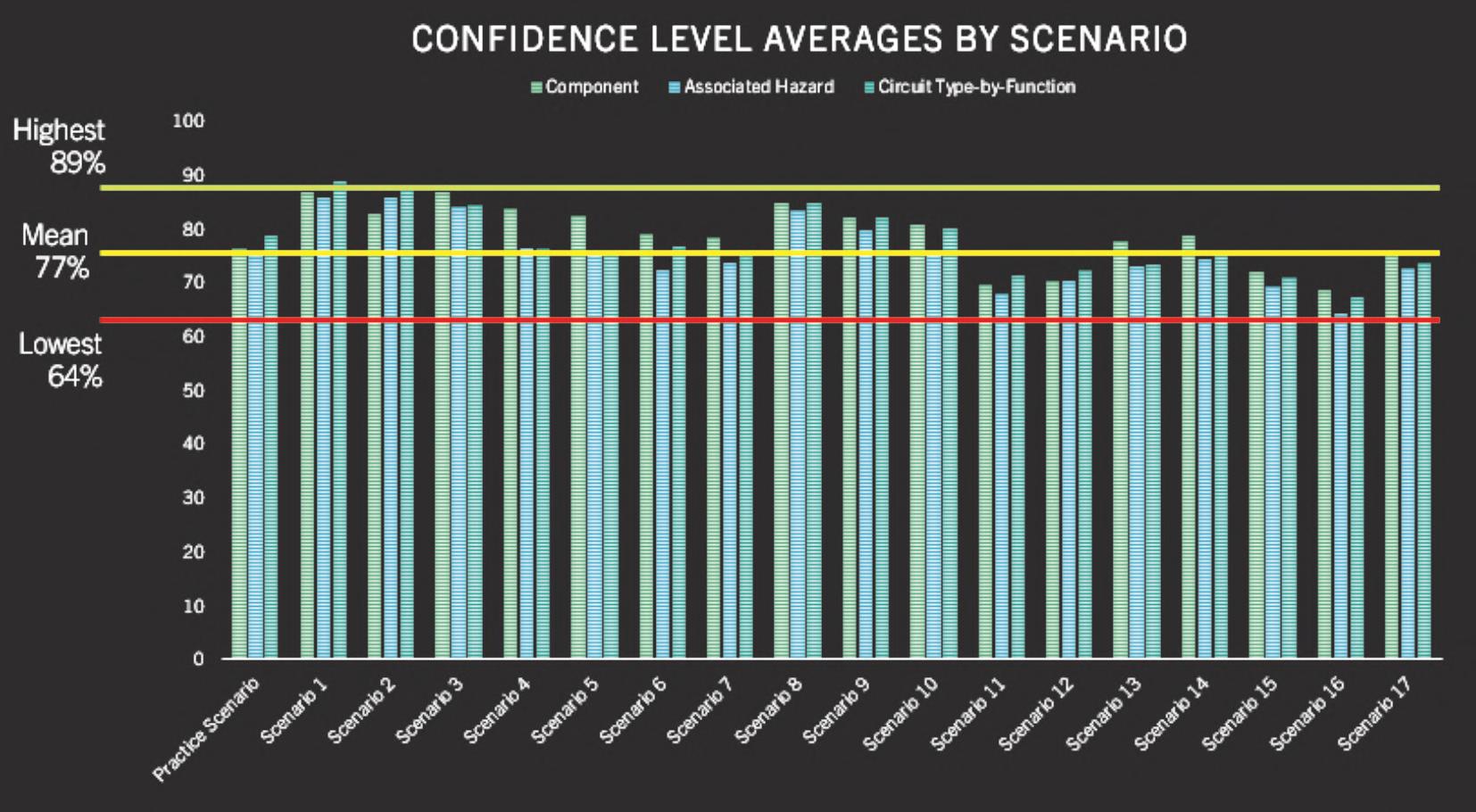
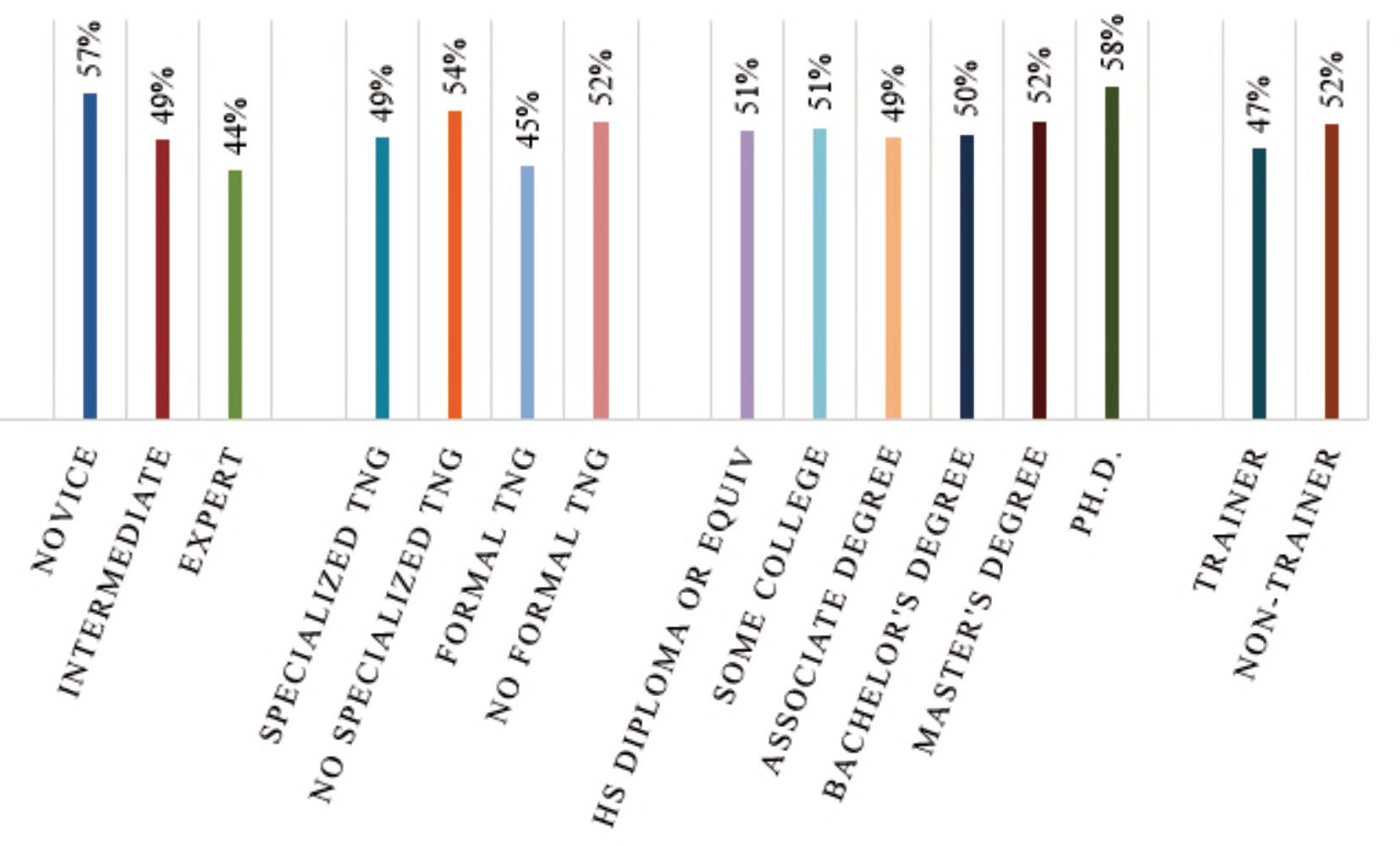
Quantitatively,thestudyfoundthataverage successratesforstudyparticipantswereonly20%for componentidentifcation,16%forassociatedhazards, and51%forcircuittype-by-function.However,study participantsratedtheirconfdenceinmakingthese decisionsratherhigh(seeFigure2).Thiswould suggestthatbombtechniciansingeneral,signifcantly overratetheaccuracyoftheirowndecisions.
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL 16 COUNTER-IEDREPORT,Spring/Summer2023
Image2:PIC12microcontroller.
Figure2.Averageself-assessedconfdencelevels.
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL
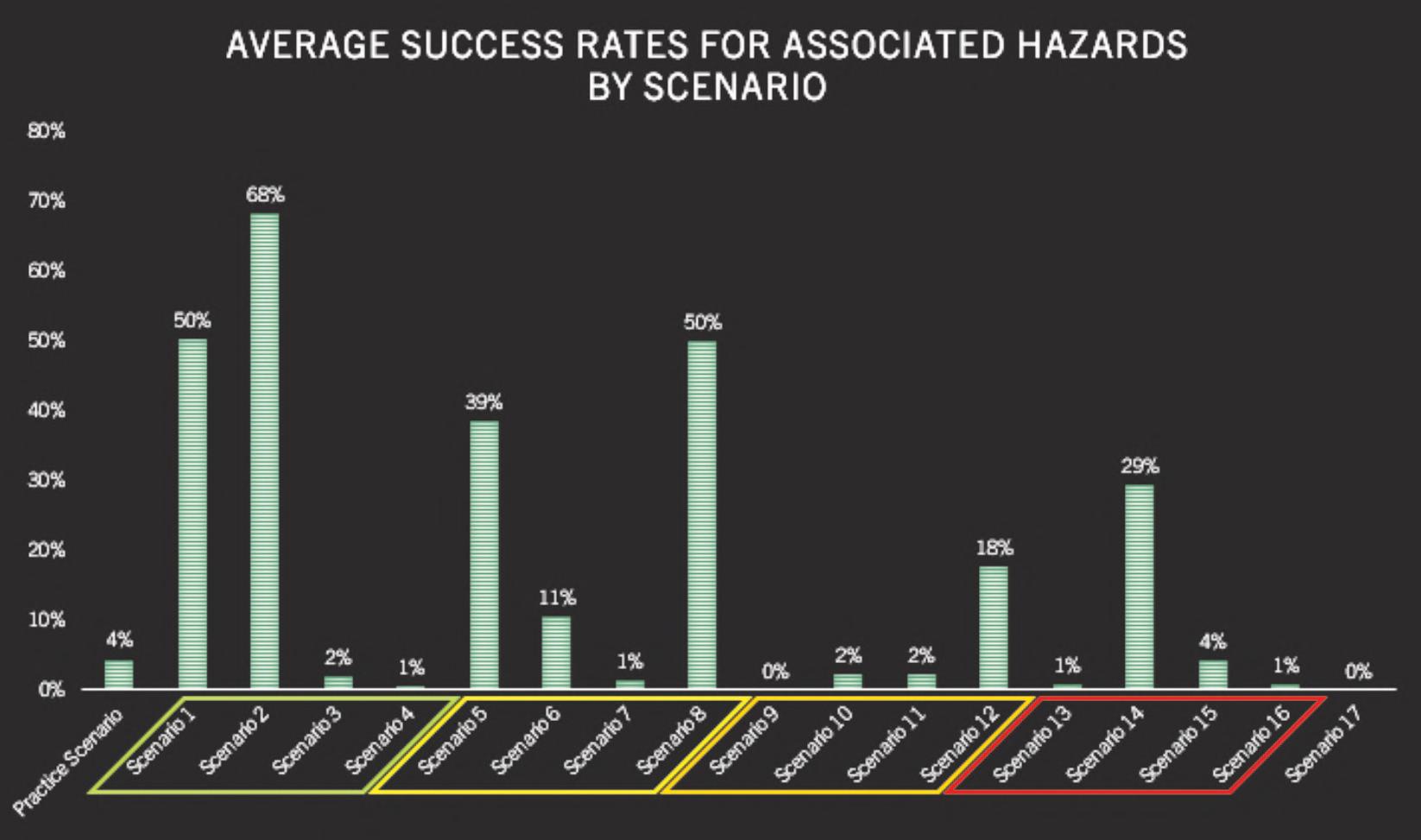
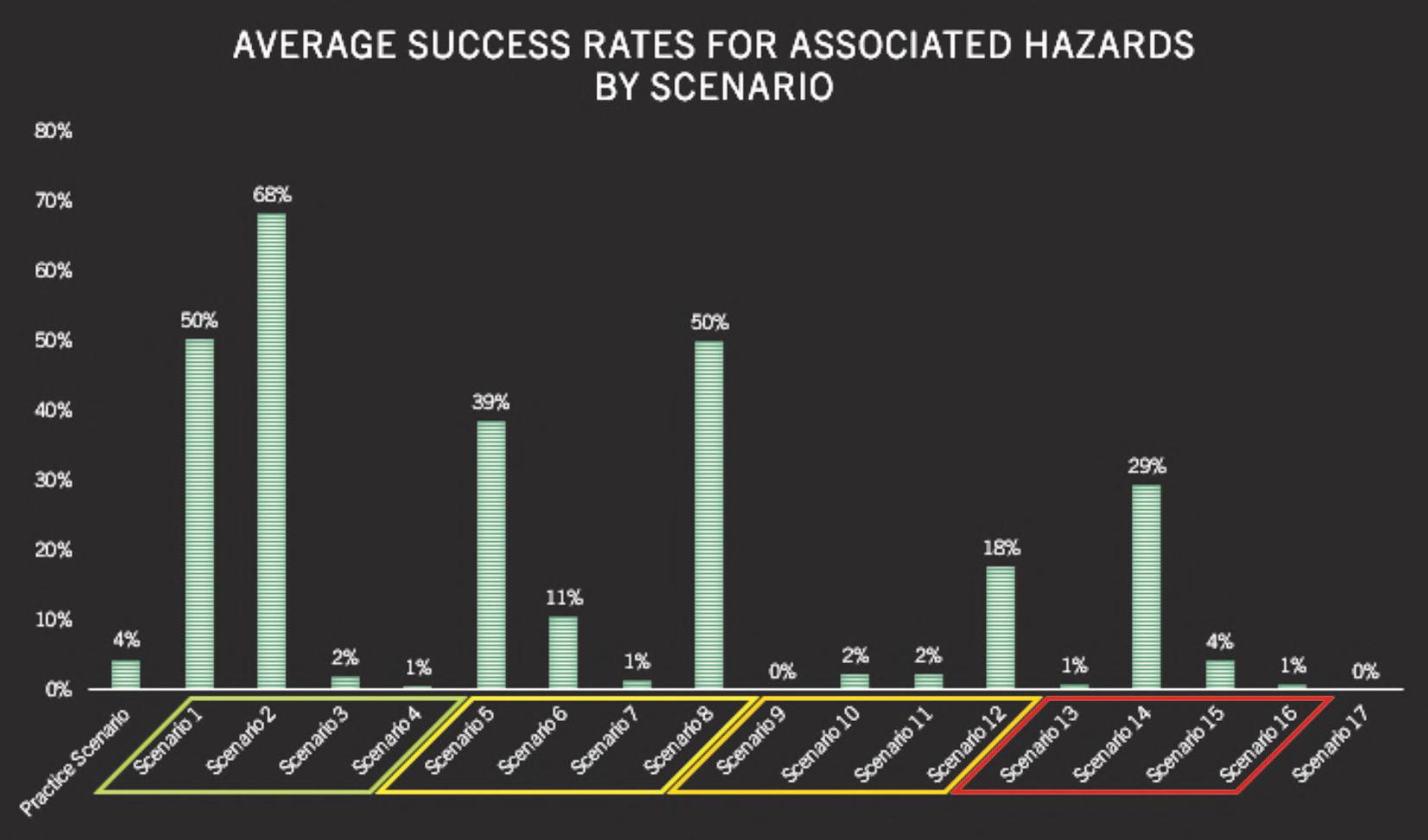
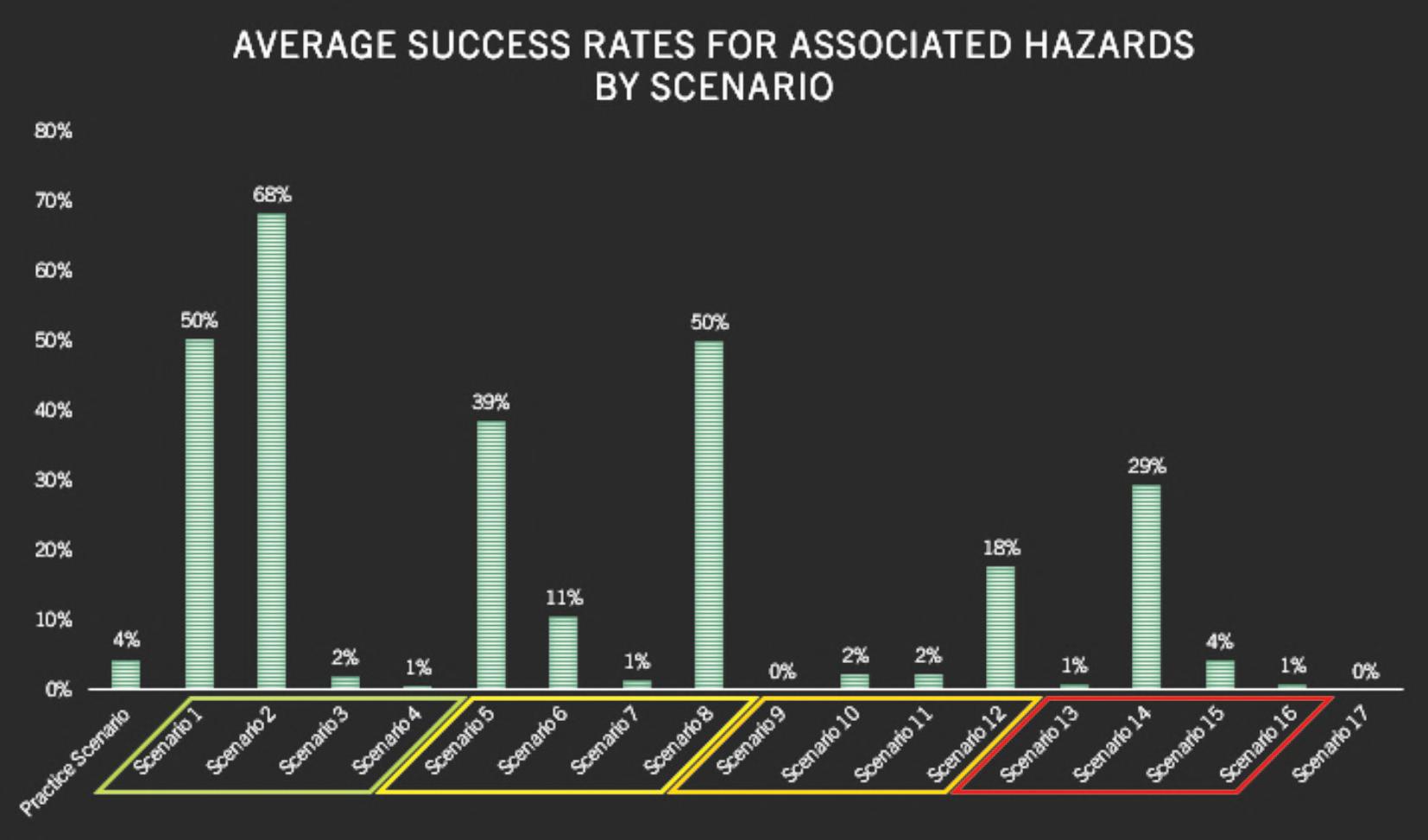
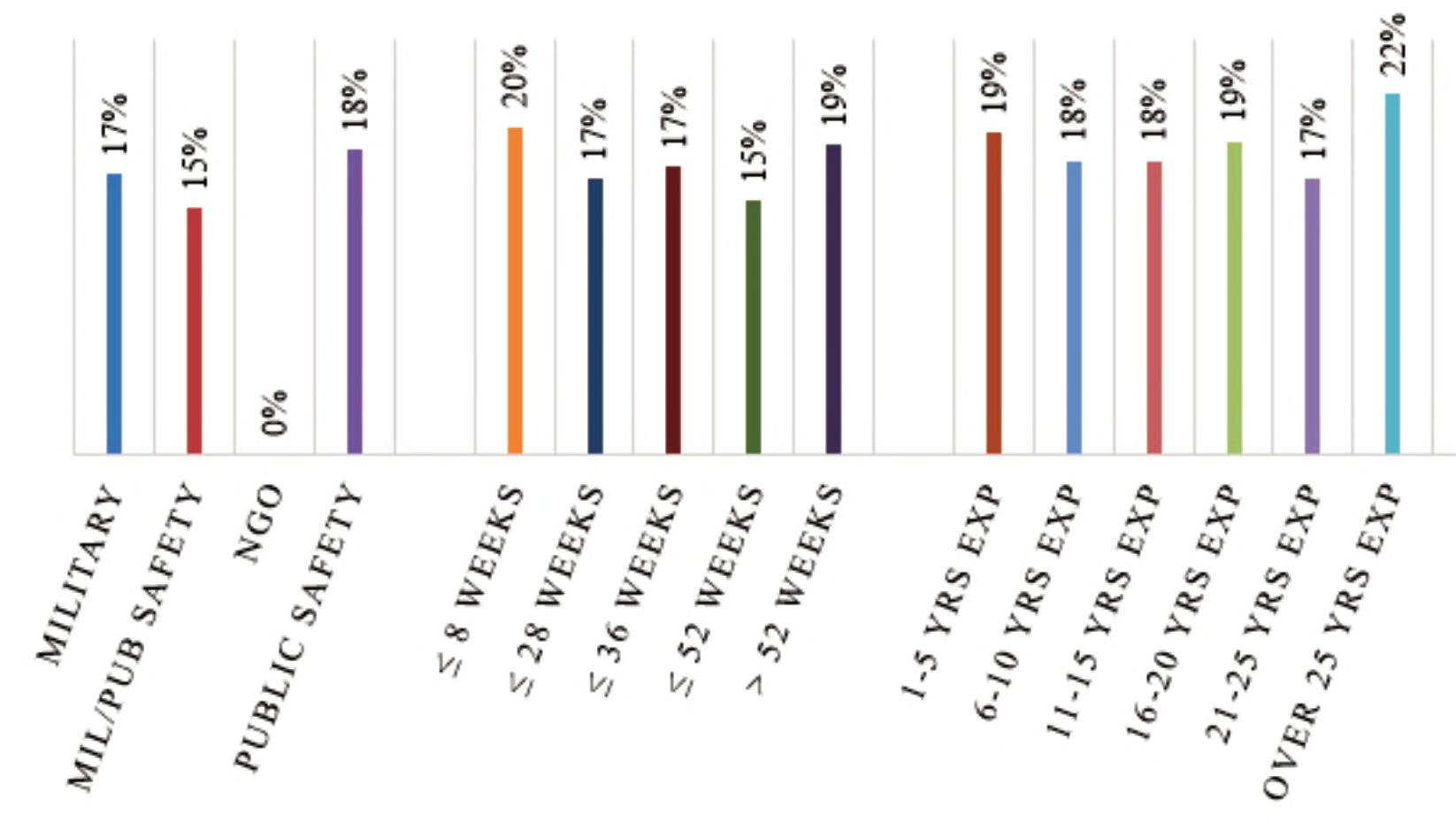
Figures3–5providestudyresultsbydependent variables.Thereaderwilllikelynotethataverage successratesarehigherforcircuitsthatarecommonly taughtduringbombdisposaltraining.Thisisinline withthequalitativefndingssuggestingthatbomb techniciansperformtheircircuitanalysesusing pattern-matchingratherthandeductivereasoning,as theyarelikelytohaveseenthecomponentsusedin thesecircuits,taughtthehazards,andthenexplained thecircuittype-by-function.Whilesomeofthecircuits receivinghighersuccessratesmaynotbetaught duringinitialbombdisposaltraining,areviewofthe curriculafrom“advanced”coursessuggestthatthey aretaughtthere.
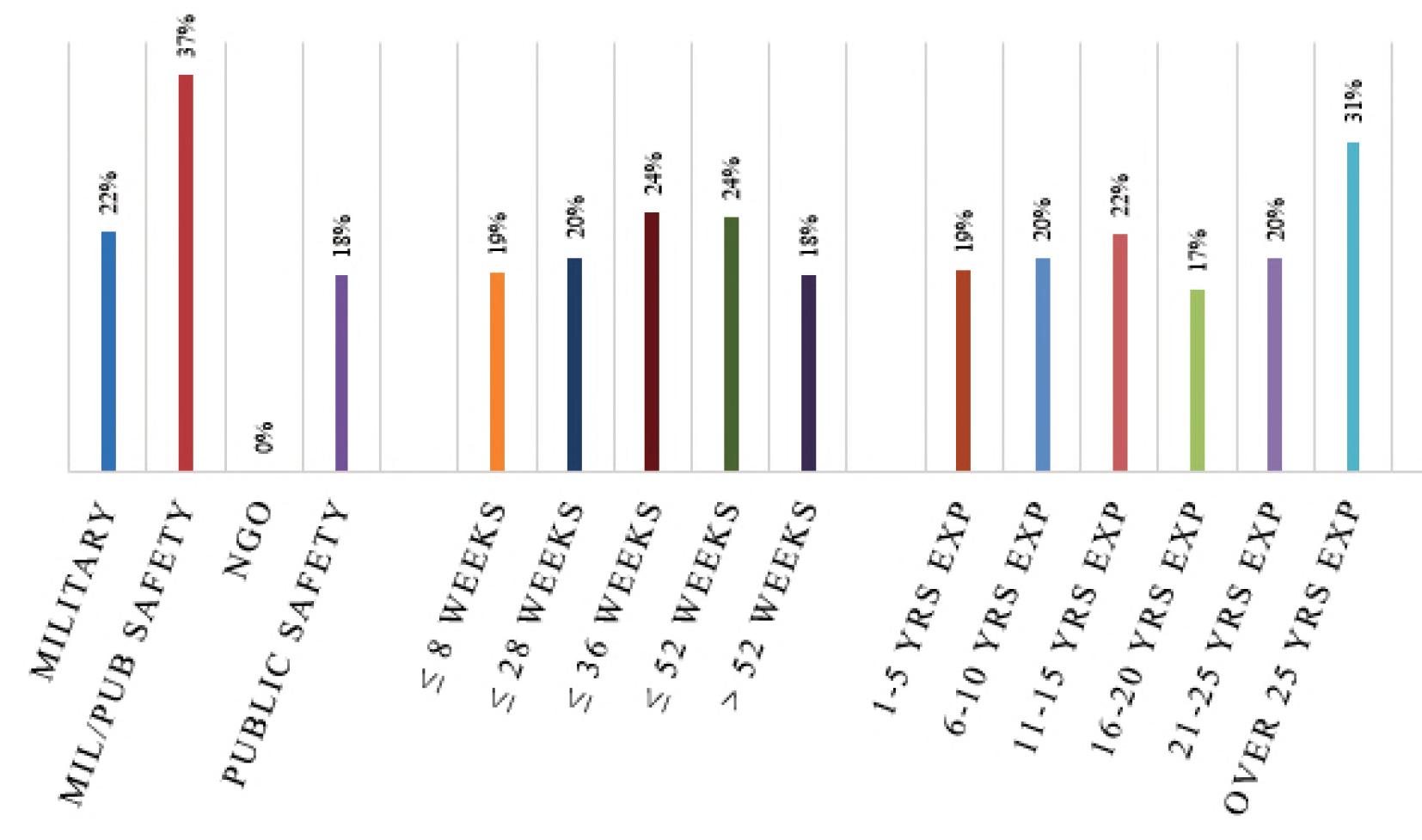
Datafromthestudyalsosuggeststhatindependent variableslikeyearsofexperience,specializedtraining, orevenlengthofinitialtraining,hadnoeffectona bombtechnicianbeingabletosuccessfullyidentify thecomponentsinacircuit,knowwhathazardsthat circuitpresents,orinmakingadeterminationasto circuittype-by-function.Figures6-11identifyaverage successratesbyindependentvariables.

IMPLICATIONS
Theresultsofthisstudyhavesomeveryserious implications,nottheleastofwhichisforhowbomb techniciansaretrained.Whilemostdecisionsmade duringanaverageday,inanyoccupationor activity,arebasedonlearned,repetitivebehaviors,or whatcognitivescientistscallheuristics,innewor criticalsituations,relyingonheuristicscanfail catastrophically.Andeventhoughitisprobablynot lostonanyoneinbombdisposal,thattousepattern matchingtotrainanewbombtechnicianeffectivelyto quicklyandaccuratelyidentifyalloftheelectronic componentsorcircuitstheymightencounterduring theircareer,theywouldhavetobeshownliterally thousandsofdifferentcomponents.Thefactremains however,thatmostbombtechniciansaretrainedto relyalmostexclusivelyonheuristics,evenafteronly beingshownwhatamountstoahand-fullof componentsduringinitialtraining,ratherthanbeing taughttousedeductivereasoningfortheirprincipal decision-makingstrategy.Therearemanyreasonsfor thisofcourse,suchaslimitedresourcesandtraining
17 counteriedreport.com
Figure3.Averagesuccessratesforcomponentidentifcation.
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL
18 COUNTER-IEDREPORT,Spring/Summer2023
Figure4.Averagesuccessratesforhazardanalysis.
Figure5.Averagesuccessratesforcircuittype-by-functiondetermination.
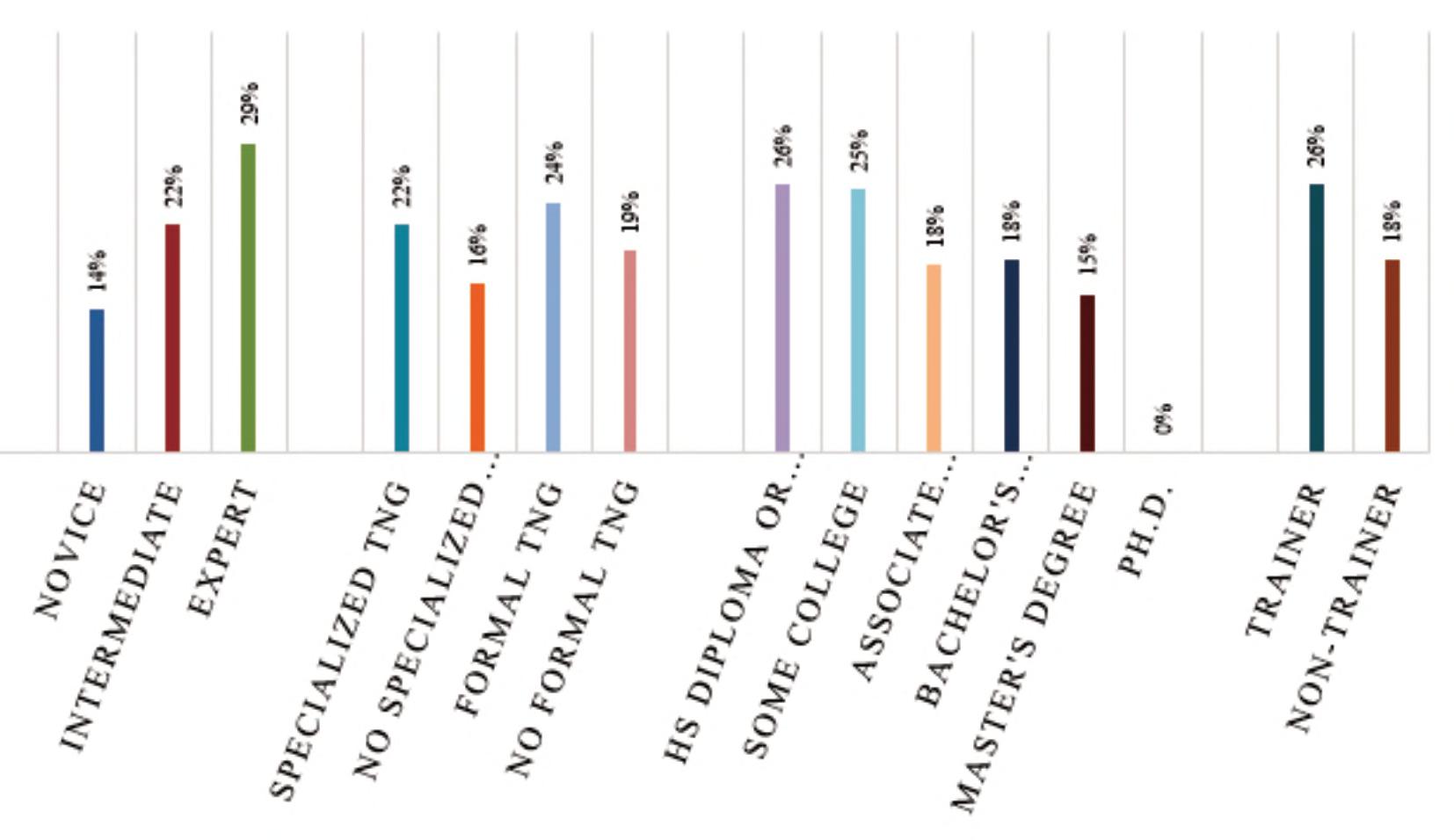
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL 19 counteriedreport.com
Figure6.Componentidentifcationsuccessratesbyaffliation,lengthofinitialtraining,andyearsofexperience.
Figure7.Componentidentifcationsuccessratesbyself-assessedknowledgelevel,specializedandformaltraining, highesteducationlevel,andtrainerexperience.
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL
Figure9.Hazardassessmentsuccessratesbyself-assessedknowledgelevel,specializedandformaltraining,highest educationlevel,andtrainerexperience.
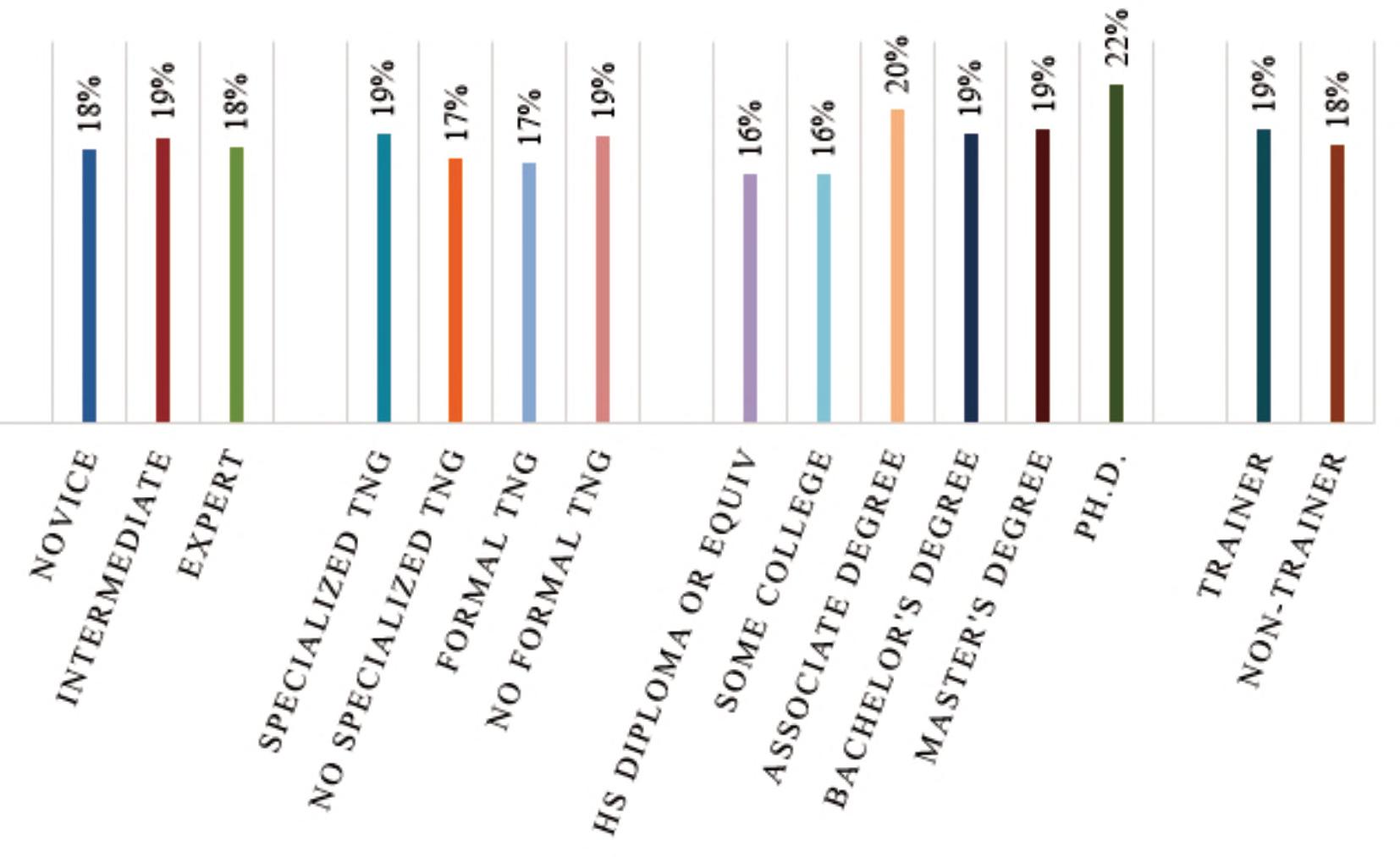
20 COUNTER-IEDREPORT,Spring/Summer2023
Figure8.Hazardassessmentsuccessratesbyaffliation,lengthofinitialtraining,andyearsofexperience.

DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL 21 counteriedreport.com
Figure10.Circuittype-by-Functiondeterminationsuccessratesbyaffliation,lengthofinitialtraining,andyearsof experience.
Figure11.Circuittype-by-Functiondeterminationsuccessratesbyself-assessedknowledgelevel,specializedandformal training,highesteducationlevel,andtrainerexperience.
time,aswellastryingtoinstillintraineesthe perceivedneedtoresolveanincidentandreturna scenetonormalcyasquicklyaspossible.Becauseof this,initialtraininggenerallyfocusesontool-use, ratherthancriticalthinkingandproblem-solving, whicharearguablysomeofthemostvaluable skillsabombtechnicianneedswhenfacedwith,and havingtomakedecisionsregardinganytypeof hazardousdevice.
Thisdataalsohasimplicationsforwhatwebelieve tobethetypesandvarietiesofIEDsusedglobally.If wefunctionundertheworkingpremisethatstatistics regardingdeviceuseisgatheredthroughbombdata centers,andbombdatacenterscollecttheirdatafrom reporting,whichisusuallydonebybombtechnicians, andbombtechniciansareonlyrecognizingthe componentsusedincircuits16%ofthetimeon average,orcircuittype-by-function51%ofthetime, howaccuratecoulddevicereportingpossiblybe?And byextension,howaccuratecouldinformation regardingdeviceconstructionpossiblybe,unlessit hasbeenanalyzedatanexploitationlabbyproperly trainedandqualifedforensicscientistsorexaminers?
Finally,theresultsofthisstudyhaveimplications fortheuseofbombtechniciansasexpertwitnesses. IntheU.S.,itisnotuncommonforbombtechnicians, particularlyattheStateandLocallevel,tobecalled onbyprosecutingattorneystoactasexpert witnessesregardingtheconstructionandfunctioning ofadevice,oreventhepotentialforpiecesandparts foundataresidencetobeusedtoconstructadevice. Again,thisbecomesproblematicwhenthetestimony callsforanythingbeyondrecognitionofthingsother thansimplecircuitsorcomponents.Ofcourse,thisis nottosuggestthatsomebombtechniciansarenot suffcientlyqualifedtoprovideexperttestimonyon deviceconstructionorfunctioning,butitwould behooveprosecutorstoensuretheirbombtechnician expertwitnessesdonotstraytoofarbeyondthe basicgeneralizedfunctioningofadevice,unlessof course,whattheyaretestifyingtohasbeenpeer reviewed,andconfrmedthroughvalidscientifc testing.ItisjustfartooeasyinthisageoffastfactcheckingandAIcapabilitieslikeChatGPT,toaccess
whatusedtobeconsideredarcaneknowledge,like thatofbombdisposal.
CONCLUSION
Bombtechniciansdoaseriesofnon-routinetasksthat requirementalandphysicaldexterity,complexcritical thinkingskills,andcreativeproblem-solving…and that’stheeasypartofthejob.Whilethesebravemen andwomenareexpertsintheuseoftoolstodefeat IEDs,thereseemstobealackoftrainingonthe generalcognitivereasoningskillsnecessaryto enhanceabombtechnician'sabilitytoconductactual problem-solving,whichinturncreatesdown-stream issueswithdecision-making.AsnotedbyLouis Pasteur,“Chancefavorsonlythepreparedmind,”so thecommunityowesittoourbombtechniciansto providebettertoolsandtraininginthecognitive domain.Notonlywillthisimprovesurvivability,butit willallowourpractitionerstokeeppacewith adversaries,whoaremorelikelythanever,tousenotyet-seencomponentsandcircuitsintheirdevices.■
ABOUTTHEAUTHOR
Dr.EdwinA.Bundy isaSenior ProgramManagerfortheU.S. DepartmentofDefenseatthe IrregularWarfareTechnicalSupport Directorate(IWTSD).Heoversees advancedtechnologydevelopment effortsrelatedtoExplosive OrdnanceDisposalandExplosives Operations(EOD/EXO)andprovidestechnologybasedsolutionsforcombatingterroristandcriminal useofexplosivestooperationalpersonnelworldwide.
Dr.BundyservesasafederalliaisontotheNational BombSquadCommandersAdvisoryBoard(NBSCAB) intheU.S.,andisanadvisorforboththeInternational AssociationofBombTechniciansandInvestigators (IABTI)andU.S.BombTechnicianAssociation(USBTA).
Dr.BundyisalsoaformerU.S.ArmyExplosive OrdnanceDisposal(EOD)Technician,andCertifed InternationalPost-BlastInvestigator(CIPBI).Dr.Bundy holdsPh.Ds.inbothForensicScienceandEducation.

22 COUNTER-IEDREPORT,Spring/Summer2023
DECISION-MAKINGANDPROBLEM-SOLVINGINBOMBDISPOSAL
ISIMPLEMENTATIONOFWESTERNC-IEDENTERPRISES SUITABLEWHENPROVIDINGDONORC-IEDASSISTANCE?
INTRODUCTION
Owingtothetransnationalnatureofthenetworks whichfacilitateIEDuse,regionallycoherentC-IED responsesaredeemednecessary.Strategic approachestosuchregionalC-IEDeffortsarerequired forthemtobeeffective.TheresultingC-IEDenterprise developedandimplementedoftenrequiresC-IED donorassistance1 totheIEDaffectedstateorregion. Intheabsenceofsuchstrategiccoherententerprises, theresultingassistancecanoftenbedisjointedand lessthanoptimal.AttimesC-IEDefforts2 havebeen oversimplistic,promotingsilverbulletsolutionswhich areoftentechnologyandequipmentintensive.At othertimesproposedapproachescanbe overambitious,involvingthereinventionofthewheel andlackingtheresourcestomaketheinitiativesa reality.Inmanycases,C-IEDeffortshaveinvolved attemptstoshoehornelementsofpreviouslyused Westerntemplatesintoactionwithinaspecifc operationalenvironment.Thisarticlewillexamine aspectsofWesternC-IEDenterprisesillustratingtheir complexitiesandhowtheirrealisationismore challengingtoachievethanmightotherwisebe considered.Forthepurposeofthisandseveralrelated articles,C-IEDenterpriseisthecollectivetermto describeallinitiatives,activities,assistance, capabilitiesandcapacitiesthatcontributetotheC-IED effortsintendedtoatleastmatchbutideally
overmatch3 thethreatposedbytheuseorthreatened useofIEDsandcaninvolveanythingwhichisintended topredict,discover/detect,prevent,protectagainst, respondto/neutralise,recover/exploit,mitigate against,ordeterIEDattacks.Thearticlewillillustrate howattemptstoreplicateorimplementWesternC-IED enterpriseswhenprovidingC-IEDdonorassistanceis notthebestapproach.Wewillfrstexaminetheneed forregionallycoherentC-IEDenterprisesastodate, sucheffortshaveoftenbeendisjointed,lackingin coordination,andinsomecasescooperation.The contentofthisarticleisinformedfromresearch conductedbytheauthoraspartofaMAinstrategic studieswhichexaminedandidentifedC-IEDstrategic principlesforEastAfrica.
RegionalandGlobalC-IEDEfforts-UNandthe AfricanUnion(AU)C-IEDResponses
TheUNhasacknowledgedtheenduringandpervasive threatposedbyIEDsincontestedandfragilesecurity environments.Theyhavestatedthatsince2014,a steadyincreaseinthenumberandcomplexityof explosiveordnancethreatshasbeenrecordedagainst UNpersonnel,nationaldefenceandsecurityforces, civilianpopulations,andotheractorswithinUNmission areas.On24May2021,theUnitedNationsSecurity Councilrequestedanindependentreviewtoaddress
C-IEDDONORASSISTANCE–DEVELOPINGEFFECTIVEC-IEDSTRATEGY
23 counteriedreport.com
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy
thenatureofthisincreasingthreatandsuggestactions thattheUNSecurityCouncil,secretariat,missions, andtroop/police-contributingcountries,amongst others,cantaketoreduceandmitigatethethreat. On23November2021,thereportwasdeliveredwith recommendationswhichemphasizethatresponses neededtobeintegrated,coherentandproactive,as wellasresponsive.
LiketheUN'sfndings,theAUC-IEDstrategystated thatitisnecessarytoconfrontthischallengeinaunited effortthroughtheAfricanUnionCommission, Regional EconomicCommunities/RegionalMechanisms, Member Statesandpeacesupportoperations.Thus,awholeof continentperspectiveisneededtodevelopregionally specifcthreat-alignedapproachestoconfrontthis transnationalthreat.Suchregionalapproaches, coordinatedandsupportedbytheAfricanUnion Commission,needtoinvolveasuiteofcomplementary enablerswhichseektoprevent,counter,andrespond totheuseofIEDs.Suchregionalstrategiesmust complementwidermemberstatenationalsecurity strategiesaswellastheirnationalsecurity architecturesandstateinterests.Whileregional approachesarerequiredforeffectiveC-IED enterprisesowingtothetransnationalnatureofthe networkswhoemploythem,therearepotentiallyother beneftstoregionallycoherentC-IEDenterprises.
C-IEDstrategiesmaybeaneffectivemeanstoachieve morewithlessresources.Onacostbeneftanalysis basisthedevelopmentofregionalC-IEDstrategies canbeworthwhileendeavoursiftheyprovidetheway toachieveagreaterimpact(closertothedesiredends) fromlessmeans(resourcesneeded).
TheUSResponsetoIEDUse
AccordingtothelatestUSArmyC-IEDstrategy (February2022),aftertheIEDrosetoprominence duringtheconfictsofAfghanistanandIraqtheUSand alliedmilitariescommencedthedevelopmentofC-IED efforts.However,beforethisresponsetoIEDusein IraqandAfghanistan,otherIEDaffectedstateshad undertakeninitiativesandcollectiveeffortstocounter theirusebutdidnotusethetermC-IED.Examples includetheUK,Turkey,SriLankaandColombia.
ThesecollectivepracticesreferredtoasC-IED continuetoevolve.
Atanationallevel,theUSestablishedtheJoint ImprovisedExplosivesDeviceDefeatOrganisation (JIEDDO).Originallycreatedin2006todeviseand feldnewtechnologiestohelpidentifyroadsidebombs andotherimprovisedexplosivesthatwerequickly becomingtheweaponofchoiceofinsurgentsagainst UStroops,by2008ithadabudgetofUS$4billionper annum.NATO,theEuropeanDefenceAgencyand manyofthenationsoperatinginboththeatres,along withthosefacingIEDattacksdomestically,also contributedtothedevelopmentofC-IED;however, JIEDDOwithitsimmensebudgetalongwiththeUS’s commandingroleinboththeatresandwithinNATO wasakeyinfuencerinhowC-IEDdeveloped.By2012 withtheon-goingeffectivenessofIEDsagainstUSand coalitionforcesinAfghanistan,JIEDDOwasatthe heightofitspowerwithintheUSmilitaryestablishment. RefectingthegrowinginfuenceofJIEDDOwithinthe USmilitaryandtheglobalincreaseinIEDuse(with IEDattacksexceeding4,000in2011),on26February 2013,theWhiteHousereleasedapolicystatementon counteringIEDs.ThisPresidentialPolicyDirectiveis referredtoasPPD17.Thesubsequentproliferationof IEDuseinPakistan,acrosstheMiddleEast,North, EastandWestAfrica,tonamebutafew,aswellas sensationalistattacksintheWest,e.g.,UK,US, France,Belgium,andSpain,sawmultiplenational, regionalandinternationalC-IEDefforts.
TheUSwhichhasoneofthemostmatureand developeddefenceandsecurityarchitectureshave strategiesdedicatedtoseveralnationalsecurityand defenceissues.However,ithasnodedicatednational C-IEDstrategybuthashadseveralsupporting documentsthatseektocoordinatenationalC-IED efforts.TheUSmilitaryhaveproducedseveralC-IED strategiessuchastheUSArmyC-IEDstrategy.Two otherinfuentialUSC-IEDdocumentswerePPD17 andtheJIEDDOC-IEDStrategicPlanfor2012–2016. WhilePPD17isnotanationalC-IEDstrategy,itdoes providethreepolicyobjectivesalongwitheightactions intendedtoguideUSsecurityanddefencepolicy makers.Italsoprovidesfveexamplesofsuccessfor
24 COUNTER-IEDREPORT,Spring/Summer2023
C-IEDDONORASSISTANCE–DEVELOPINGEFFECTIVEC-IEDSTRATEGY
theseactions.PPD17conceptualisesaC-IEDcycle4 thatinvolvesthestepsofdiscover–prevent–protect against–respondto–recoverfrom–mitigateagainst IEDattacks.ThissixcomponentC-IEDcyclecanbe adaptedintoaneight-componentcycleasshowninthe fgurebelow,5 providingagoodframeworkto appreciatepotentialpointswithinanIEDattackcycle thatC-IEDeffortsmaybefocussedontoachieve desirableeffectstoprevent,counterorrespondtoIED attacksorthreatsthereof.
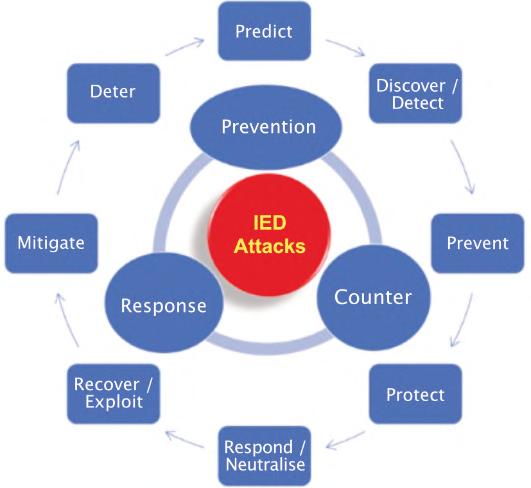
PPD17offersatoolforthosewithintheUSengaged intheC-IEDenterprise,toensuretheirC-IEDefforts remainstrategicallyalignedtotheirgovernment’s C-IEDpolicy.Itsconcludingsentenceisinsightfulin termsofwhatanationalstrategyshouldendeavourto achieve.Ittalksofawholeofgovernmentapproach integratingnational,sub-national,privatesectorand globalparticipationinC-IEDactivitiestobestposition theUStodiscoverplotstouseIEDsdomesticallyor againstitscitizensabroad,beforethosethreats becomeimminent.
TheJIEDDOC-IEDstrategicplanwasatoolto providestrategicdirectiontotheUSmilitary establishment’seffortstocounterthethreatposedby IEDs.Itwasintendedtoprovideaunifedandcoherent approachtoeffortsbytheUSdefenceestablishmentto countertheuseofIEDsagainstUSforcesbothwhenon expeditionandwhennecessary,domesticallyinsupport ofUSfederalagencies.Itsoverallgoalwastomitigate theeffectsofIEDsonthecommander’sfreedomof manoeuvreandtosetthepathfortheC-IEDeffortsin collaborationwithpartnernations,interagency,and intergovernmentalorganisationstoenablethedefeatof theIEDasaweaponofstrategicinfuence.The documentheavilyinfuencedUSmilitaryC-IEDduring thedecadeofthe2010sand,bydefault,subsequently infuencedNATOC-IED,thatofUSalliesandelements oftheUSmilitary-industrialcomplex.Whileeffortsto developnationalandregionalC-IEDstrategies,can harnesscertainelementsofthisJIEDDOstrategicplan, itfallsshortofwhatIEDaffectedstatesandregions requireforseveralreasons,whichincludeinteralia:
1.DomesticC-IEDissecondary toexpeditionaryC-IED;
2.Afghanistanwasthefocus;
3.Inconsistencyinwhat counteringIEDsmeans;6
4.Explanationofattackthe networkistoonarrowand belowparforastrategic document;
5.PrimaryresponsetoIEDsis heavilytechnologyand equipmentfocussedwiththe secondarytargetaudience beingelementsoftheUS militaryindustrialcomplex.
Forthesereasons,the JIEDDOstrategicplanfailsasa guidetoC-IEDdevelopment, investmentandimplementation.
25 counteriedreport.com
C-IEDDONORASSISTANCE–DEVELOPINGEFFECTIVEC-IEDSTRATEGY
Figure1.C-IEDcycle.
NATO
Mostnotably,NATOhasitsAlliedJointDoctrinefor CounteringIEDs,AJP-3.15.7 Manywesternmilitaries eitheradoptoradaptAJP-3.15asC-IEDdoctrinefor usebytheirarmedforces.Forexample,withintheIrish DefenceForcesfromcirca2007,theOrdnanceSchool ledmanyeffortstodevelopC-IEDbothatthetactical developmentlevel,throughtooperationalcapabilities andinformingstrategicperspectiveswhichincluded effortstoadaptNATOAJP-3.15C-IEDforIrish DefenceForces’use.8 Overall,theNATOAJP-3.15 publicationcouldnotbeuseddirectlybyanIED affectedstateindevelopinganationalC-IEDstrategy. Instead,itwasdesignedasmilitarydoctrineand intendedforusewithinthewiderNATOecosystemfor militariesthatareNATOconfguredandresourced accordingly.Itwasintendedformilitarystrategyand operationsratherthannationalstrategy.Thatsaid, thereismuchcontentwithintheNATOAJP-3.15 publicationthatcouldbeharnessedtoinformanIED affectedstateonwhattheymayconsiderfortheir militariesiftheirmilitaryaretobeacomponentoftheir nationalC-IEDstrategy.
WesternC-IEDApproaches
NowesternnationalC-IEDstrategieshavebeen identifedanditisnoteworthythattheUSistheonly stateidentifedashavingindependentlydevelopeda C-IEDstrategicplanandaPPDonC-IED.However, severalwesternstateshavevariousC-IEDpolicies, initiatives,strategicplans,anddoctrineswhichthey employ.IntermsofdomesticC-IED,therearevarious approachestakenbywesternstatestocounterthe threat.Inmostcases,westernnations'C-IEDis primarilyconductedundertheumbrellaofcounterterrorism(CT)oracriminaljusticeapproachandhence itisadomesticlawenforcementissue.Thisinturn meansthattypically,domesticC-IEDcomesunder nationalsecurityorcriminaljusticeorpotentiallya hybridofboth,andpredominantlyhasnomilitary involvement.Forexample,theUSJIEDDOstrategic planfortheUSmilitarywasprimarilyexpeditionary focussedand,onlyintendedtosupportUSfederal agencieswhohaveprimacydomestically.However,in
somecaseswesternmilitariescanhaveamore substantiveroleindomesticC-IED,mostnotablyinthe provisionofExplosiveOrdnanceDisposal(EOD).For example,theBelgianmilitaryprovideallnationalEOD capabilitiesasdotheDutchmilitarywithinThe NetherlandsandthesameforMalta.Thisissimilarto theprovisionofallEODcapabilitiesbytheIrish DefenceForceswithintheRepublicofIrelandtothe nationalpoliceforce,AnGardaSíochána,inanaidto thecivilpowerrole.
TheUKC-IEDEnterprise
ToexploretheprovisionofC-IEDdonorassistance,it isinformativetoexaminetheUKC-IEDenterpriseand howtheseevolvedtobeconsideredbymanyasthe leadC-IEDnationasitwasbeingdevelopedinthefrst decadeofthe2000s.Examininghowthistranspired, canassistunderstandingwhysofewWesternnations havestandaloneformalC-IEDstrategies.Thereare twoprimaryreasonswhytheUKwasconsideredthe leadingnationinthisarea.Firstly,theBritishretreat fromempiresawthemengagedinseveralsignifcant counterinsurgenciesthatexposedthemtoasymmetric threats,includingclandestineattackmethodsinthe formofboobytrapsandIEDs.UKarmedforcesand theirlocalconstabularyforceswereexposedtosuch threatsinHongKong,Aden,andCyprus.Other nations,postWWII,wereexposedtoIEDsasthey retreatedfromempire,mostnotablytheFrenchfor exampleinAlgeria.However,itistheauthor’s contentionthatitistheBritishretreatfromempireand theirexposuretoasymmetricattacksfrom‘Irish terrorism,’whichincludedIEDs,goingasfarbackas theFeniansandtheIrishRepublicanBrotherhood ‘dynamitewars’whichmarkedouttheBritish experienceasdifferent.TheLondonMetropolitan PolicealongwithotherelementsoftheUKsecurity serviceshadtocounteraclandestineorganisation undertakingterrorismusingmethodswhichincluded IEDattacks.WithinIrelandtheBritishmilitaryandother securityforceshadtocontendwithIEDattacksduring theIrishWarofIndependenceandsubsequently intermittentlyinNorthernIreland,especiallyalongthe borderupto1969,suchastheIRAbordercampaignof
26 COUNTER-IEDREPORT,Spring/Summer2023
C-IEDDONORASSISTANCE–DEVELOPINGEFFECTIVEC-IEDSTRATEGY
C-IEDDONORASSISTANCE–DEVELOPINGEFFECTIVEC-IEDSTRATEGY
1956–1962.From1969,Britishsecurityforcesfaced whatbecamethemostsophisticatedandpossiblythe mosteffectiveuseofIEDsuptothattime.‘The Troubles’sawtheUKmilitarydeployedtoNorthern Irelandinanaidtothecivilpowerroleinsupportof NorthernIrelandsecurityforces,inwhatcouldbe consideredanexpeditionaryoverseasdeploymentfor manyoftheBritishmilitarywhodeployed.Thename giventotheBritishArmedForces’operationsduring ‘TheTroubles’from1969to20079 wasOperation Bannerandwasconsideredaninternalsecurity operation.CoupledwiththeoperationsinNorthern Ireland,wastherelativelysteadyrateofIEDattackson theUKmainland.ThisresultedintheUKpoliceand securityservicesdirectinvolvementinC-IEDefforts. Itwastheseexperiencesduring‘TheTroubles’that exposedthemtosophisticatedIEDusethat signifcantlyinfuencedthedevelopmentoftheirC-IED enterprisewhichevolvedandsubsequentlysetthem apartfromotherIEDaffectedstates.Allthemilitary, policeandsecurityserviceexperiencesinC-IED,both domesticallyandinaquasi-overseasrole,resultedin theUKbecomingthemostreputable,experiencedand expertnationatC-IEDbytheturnofthetwentieth century.Thisleftthemastheleadnationwhenthe needforC-IEDaroseinIraqandAfghanistan; however,itisessentialtounderstandthecomplexities ofthisBritishC-IEDenterprise.
Bycirca2005,theBritishC-IEDenterprisehad developedfrom‘TheTroubles’andalsoinresponseto anemergingJihadithreat,requiringahybridapproach involvingamixtureofcounter-insurgency(COIN) practices,counter-terrorism(CT)andcriminaljustice approaches.TheUKhasnosingleC-IEDleadagency. Instead,ithasattimesinvolvedtheBritishmilitary, localpoliceforces,locallyraisedinfantryregiments, securityservices,domestic,foreignanddefence intelligence,stateandlocalforensiccapabilities, militaryandLondonmetropolitanEODandsearch teams,andCTpoliceunits.TheirEODcapabilities residewiththemilitary,exceptfortheGreater MetropolitanLondonareawheretheUKMetSO15 EODhasresponsibility.Thevariouselementsofthe Britishdefence,securityandjusticeapparatus
employedduringtheTroublesfrom1969to1991, whentheColdWarwason-going,facednomajor fundingorresourcingrestrictions.TheirC-IED intelligencecapabilitiesinvolvedpoliceforcesrelating tocriminaluseofIEDs,withUKSecurityServices (MI5)involvedwithnationalsecurityIEDissuesand theSecretIntelligenceService(MI6)potentially involvedifthereisaninternational,foreignstateor foreignnon-stateactorelementtoit.Thereisa potentialfortheinvolvementofmultiplesecurity agenciesinvolvingcivilian,policeandmilitary intelligenceelements.Foroffensiveattackthenetwork activities,theUKmilitary,canexecuteoverseas actionswithavarietyofUKpoliceandsecurityservice elementsinvolvedinthesamedomestically.Such attackthenetworkoperationscanincluderaids, interdictionsandarrests,beingexecutedundera criminaljusticeapproachoraCTframework.When doneunderaCTapproachtoC-IEDitbecomeseven morecomplexastheUKmilitaryactinsupportof policeelementsaswasthecaseforexamplewhen specialforcesoperativeswereembeddedwithLondon MetropolitanPoliceduringtheperiodofJune2017in relationtoterroristattacksinLondon.Thesame complexarrayofactorscanbeseenwithintheUK defence,securityandpolicesectorswhenitcomesto IEDexploitationwithforensicpersonnelandvarious laboratoriesofvaryingexpertiseandcapability involved.WhenprovidingC-IEDdonorassistancean appreciationoftheUKnationalC-IEDenterprise illustratesitsinterconnectedmulti-agencyandfexible approach.Itisequallyimportanttoappreciatethetime scaleandresourceinvestmentrequiredtodevelop suchdecentralisedcapabilitieswithinmatureandwellestablisheddefence,securityandjusticestructures.
Afghanistan’sNationalC-IEDStrategy
ExpandingthefocusbeyondwesternC-IEDefforts, onenationstandsoutforitsnationalC-IEDstrategy, Afghanistan.10,11 In2016,theIslamicRepublicof Afghanistan’soffceofnationalsecuritycouncil, internalaffairsdirectorateproducedthenation’s secondnationalC-IEDstrategy,withthefrstsuch nationalC-IEDstrategyproducedin2012.TheAfghan
27 counteriedreport.com
C-IEDDONORASSISTANCE–DEVELOPINGEFFECTIVEC-IEDSTRATEGY
InternalAffairsDirectorateweresignifcantlyassisted, supportedandadvisedbyISAFindevelopingand implementingthesestrategies.Thepartneringand outreachchiefduringthedraftingofthefrstAfghan nationalC-IEDstrategystatedthattheoutreachand partneringcelloftheISAFHQ(4Star)C-IEDbranch wasdeeplyinvolvedinthedevelopmentoftheC-IED StrategywithitsAfghangovernmentpartners; however,itwasalwaysathemeofthestrategythatit wouldbeAfghanled.Asecondkeypointisthatthese strategiesweredevelopedwithinafragilestate, counteringaviolentanddestabilisinginsurgency. Manyoftheministriesandsecurityforceswere embryonicandunderdeveloped,astheycountered IEDs.Thebackgroundtothedevelopmentofthe AfghannationalC-IEDstrategiesisanimportant considerationwhenattemptingtouseitasamodelto provideC-IEDassistance.Overall,thequestionmay beposed,whetherthewesterndominatedISAF alliance,resourcedandforcedthedevelopmentand implementationoftheirparadigmofanationalC-IED strategyforAfghanistan?
CONCLUSION
WhileregionalinitiativestocoordinateC-IEDcanbe slowpacedincomparisontonationaleffortswhichare typicallyfasterpacedtheneedforregionalapproaches tocounteringIEDuseispromotedduetothe transnationalnatureofthethreat.Thisisamonumental challengeandonethatwillbegenerationalinlength, butitcanbedoneiftheappropriateinternationally coordinatedapproachistaken,providedthereis internationalcooperationandappropriateresources allocated.Itisunrealistictothinksuchagrandstrategic endeavourwillhave193UNmemberstates’ consensus;however,evenwithmajoritybuyinfrom keyUNP5,G7andG20nations,overtheperiodofa decademassiveprogresscouldbemade.Inanysuch grandstrategicendeavour,itisnecessarytoseethat individualdevelopingnationswillnotbeabletodothis alonebutwillneedactivesupportfromacooperative internationalsecurityecosystem.Suchsupportmay involveregionalandinternationalorganisationssuch as,theUN,AU,NATO,EU,ECOWAS,INTERPOL,
WCO.Itisproposedthatowingtothematurityof Westernlawenforcement,securityanddefence architecturesandthegreaterresourcesavailableto them,coupledwiththeoften-evolutionarynatureof theirdevelopment,attemptstoreplicateorimplement suchC-IEDenterprisesintheprovisionofC-IEDdonor assistanceisnotconsideredtobebestpractice.So, howcananIEDaffectedregionanditssupporting donorsbestgoaboutdevelopingeffectiveC-IED strategy?ItisproposedthatC-IEDstrategicprinciples areneededtoachievetherequiredimpactsand outcomeswhenprovidingC-IEDdonorassistance, whichwillbethesubjectofasubsequentarticleinthe Counter-IEDReport. ■
NOTES
1.C-IEDdonorassistancereferstoC-IEDsupport providedonabilateralbasis,onajointinitiative fromtwoormoreStatesorbyaninternational organisation,e.g.,EU,LeagueofArabStates, ECOWASetcoranalliancee.g.NATO,toanIED affectedstateorregion.
2.C-IEDeffortsrefertoallinitiativesandactivities undertakenbyaState,organisationorentitytoat leastmatchbutideallyovermatchthethreatposed bytheuseorthreateneduseofIEDsandcan involveanythingwhichisintendedtopredict, discover/detect,prevent,protectagainst,respond to/neutralise,recover/exploit,mitigateagainst,or deterIEDattacks.C-IEDeffortscanincludeinter alia,training,mentoring,advising,accompanying, assisting,technologyandequipmentprovisionand intelligencesupport.
3.TheUSArmyC-IEDstrategy2022,states “developingcapabilitiestomaintainovermatchisa criticalenabler,”whenassessingIEDsasamultidomainthreatintothefuture.
4.TheC-IEDcyclepresentedhaseightsteps involvingpredict,discover/detect,prevent,protect, respond/neutralise,recover/exploit,mitigateand deter.Thesestepsintendtocollectivelyachieve thedesirableeffectsofpreventing,counteringor respondingtoIEDattacksorthethreatthereof.
28 COUNTER-IEDREPORT,Spring/Summer2023
Theeightstepsprovidedinthiscyclemaynot necessarilyalwaysbepresentinanygiven C-IEDeffort.
5.Theeightnamedstepsareasynthesisofvarious C-IEDcyclesreviewedaspartofthisresearch.In thedefningofC-IEDeffortswithinthisresearcha seventhandeighthstepofdeterrenceandpredict wereincludedtothoseintheUSArmyC-IEDcycle. InadditionthreeUSArmyC-IEDcyclestepswere expandedwithdiscovertoexplicitlyincludedetect, respondtoincludeneutralise(whenpossible)and recovertoincludeexploitsolessonscanbe learnedtofeedallotherpartsoftheC-IEDcycle.
6.Itsstrategicvisionspeaksofreducingthe effectivenessandlethalityofIEDswhichisrealistic andachievable;however,itsmissionstatement, referstodefeating"theIEDasaweaponsystem ofstrategicinfuence.”(p.1)ThedefeatofIEDs isnotarealisticendstatewiththestrategy acknowledgingtheIED“willremainanenduring globalthreatduetotheaccessibilityofmaterials andthepotentialstrategicimpactresultingfrom theiruse.”(p.3)Assuchtheacknowledgementin theforewordthat“wearenevergoingtostopall IEDs”(p.iii)shouldhavebeenfollowedthroughout, withathreatmitigationapproachtocountertheir useadoptedthroughoutthedocument.
7.AsofApril2022thisNATOCounter-IEDdoctrineis underreview.
8.Asof2015,aworkingdraftofthisadaptedC-IED doctrinewasdevelopedandbeingusedto informIrishDefenceForceC-IEDthinkingand approaches.
9.BritishArmy deploymentinNIwasunderthe militarynameOperationBannerwhichformally endedon01Aug2007;however,alatent,virulent butlowcapabilityIEDthreathaspersistedfrom dissidentrepublicangroupssincethe1998Good Friday Agreement.

10.Theauthorhasbeenmadeawareofthepotential existenceofaPakistaninationalC-IEDstrategy; however,despiteextensiveeffortstheexistence ofsuchastrategycouldnotbeconfrmedor denied.PotentialC-IEDsecuritysensitivitywithin
Pakistanmaycontributetochallengesin answeringthisquestion.
11.Theauthorisalsoawarethatfrom2018,the conceptofaC-IEDstrategyforKenyawas mooted.Asofmid-2022itwasrecordedthat Kenyawasintheprocessofdevelopinganational strategyinC-IED.
ABOUTTHEAUTHOR
PaulAmoroso isanexplosive hazardsspecialistandhas extensiveexperienceasanIED ThreatMitigationPolicyAdvisor workinginEastandWestAfrica.He servedintheIrishArmyasanIED DisposalandCBRNeoffcer,upto MNTlevel,andhasextensive tactical,operational,andstrategicexperiencein PeacekeepingOperationsinAfricaandtheMiddle East.Hehasexperienceinthedevelopmentof doctrineandpolicyandwasoneofthekeycontributors totheUnitedNationsImprovisedExplosiveDevice DisposalStandardsandtheUnitedNationsExplosive OrdnanceDisposalMilitaryUnitManual.Heworksat presentintheMENAregiononSALWcontrolaswell asinwiderAfricaadvisingonnationalandregional C-IEDstrategies.HehasaMScinExplosive OrdnanceEngineeringandanMAinStrategicStudies. Herunsaconsultancy,AssessedMitigationOptions (AMO),whichprovidesadviceandsupportinrelation toconventionalandimprovisedweaponsand explosivehazardriskmitigation.Thisarticlerefectshis ownviewsandnotnecessarilythoseofany organisationhehasworkedfororwithindeveloping theseideas.
Linkedinprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/
29 counteriedreport.com
C-IEDDONORASSISTANCE–DEVELOPINGEFFECTIVEC-IEDSTRATEGY

ASTRATEGICPRINCIPLESAPPROACH TOREGIONALC-IEDENTERPRISES
INTRODUCTION
InapreviousCounter-IEDReportarticleitwas outlinedhowowingtothetransnationalnatureofthe networksthatfacilitateIEDuse,thatstrategic approachescoupledwithregionalcoherenceare requiredtoachieveappropriateandeffectiveimpactin C-IEDdonorassistance1 providedtoIEDaffected states.Itwasalsoarguedthatowingtothematurityof Westernlawenforcement,securityanddefence architecturesandthegreaterresourcesavailableto themcoupledwiththeoften-evolutionarynatureoftheir development,attemptstoreplicateorimplementsuch C-IEDenterprisesintheprovisionofC-IEDdonor assistancearenotconsideredtobebestpractice. PursuitoftheperceivedgoldstandardofWestern C-IEDenterprisescreatesanunachievableendstate foranIEDaffectedstaterequiringC-IEDdonor assistance.Thisissuecanbeaddressedbyhaving C-IEDstrategicguidancewritteninclear,concise, accuratelanguagewhichcanbeemployedbyIED affectedstatesanddonorstoserveasabridgeto barriersaswellasdifferencesinexpectations.Asetof C-IEDstrategicprinciplescanservetoinformsuch C-IEDstrategicguidance.Thisarticlewilloutlinehow C-IEDstrategicprinciplesareneededtoachievethe requiredimpactsandoutcomeswhenprovidingC-IED donorassistance.Thecontentofthisarticleisinformed fromresearchconductedbytheauthoraspartofaMA
instrategicstudieswhichexaminedandidentifed C-IEDstrategicprinciplesforEastAfrica.
ASTRATEGICAPPROACH
AccordingtoColinS.Gray,strategymaybe consideredastheusemadeofforceandthethreatof forcefortheendsofpolicy.Itisthebridgethat connectspolicywithmilitarypower.Forourneeds,the conceptofstrategyexceedswhatmaybeconsidered classicalmilitarystrategy.ItrefectswhattheAfrican Union(AU)statesastheneedtocomplementwider securitystrategiesaswellastheirnationalsecurity architectureandstateinterests.Acomprehensive nationalstrategyinvolvesmoreelementsthanmilitary powertoeffectivelysupportC-IEDefforts.TheUS DODdefnitionofnationalsecuritystrategybetterfts ourneeds.Itexplainsthatitspurposeisfordeveloping, applying,andcoordinatingtheinstrumentsofnational powertoachieveobjectivesthatcontributetonational security.Securityinthiscontextcanbeconsideredas aconditionthatresultsfromtheestablishmentand maintenanceofprotectivemeasuresthatensurea stateofinviolabilityfromhostileactsorinfuences.In thiscaseitissecurityfromactualorthreatenedIED attacks.Thestrengthofthisdefnitionliesinabroad approachencompassingtheinstrumentsofnational power.Itisnotsimplyfocusedonthemilitaryand
C-IEDDONORASSISTANCE – C-IEDSTRATEGICPRINCIPLES
31 counteriedreport.com
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy
C-IEDDONORASSISTANCE – C-IEDSTRATEGICPRINCIPLES
refectstheneedforastrategicwholeofgovernment approachtoC-IED.Itisproposedthatanoptimally effectivestrategicapproachtoC-IEDrequiresall elementsofstatecraft.2 Awholeofgovernment approachtoC-IEDneedstoencompassthe instrumentsofnationalpowerinvolvingmilitary; information;diplomacy;fnance;intelligence; economics;legal;developmentalongwithlaw enforcement,regulatoryinstrumentsandcivilsociety organisations.
Lykke’sends-ways-meansstrategymodel3 provides anincompleteapproachtostrategicC-IED,asitfailsto comprehendallthenecessarydimensionsofC-IED.4 Insteaditisproposedthatstrategycanbeanyhigherlevelcoordinatingmechanismthatseeksapositionof advantageandarticulateshowthismaybeachievedby recognisingstrengthsandweaknessesinagiven operationalenvironment.Multiplenationaldocuments suchaspolicydocuments,doctrines,policystatements andactionplanscaninformnationalapproaches toC-IED.Whatgoodstrategylookslikecanbe challengingtodefne;however,thosestrategic documentsthathaveproventobeeffectivetypically communicatesuccinctlyitswhy(whatisintendedtobe done)andwhomustdowhatandbywhen.Justas goodstrategydoesnotneedtofttheLykkemodel,any publicationordocumentthatarticulatesorservesto coordinateC-IEDcanqualifyasanelementofstrategy.
AccordingtoUSPresidentialPolicyDirective17, issuedin2013undertheObamaAdministration,the greatestresponsibilityoftheStateistoprovideforthe safetyandsecurityofitscitizenswhileprovidingan economicenvironmentthatpromotesopportunityand prosperity.IftheuseorthreateneduseofIEDs underminesorimpedesthenationalinterestsofsafety, securityandprosperity,thenIEDsmaybeconsidered atactical5 issuewithstrategicimpacts.6 Forexample, IEDscandisrupteconomiclifeandfragmentcohesion withinthecommunitiesinwhichtheyareemployed. Thiswillundermineeconomicdevelopmentalongwith governancetothedetrimentofnormallyfunctioning society.Nationalsecurity,safetyandprosperityare strategicissues,whichIEDuseundermines,meaning thatC-IEDenterprisesneedtobestrategic.Itis
proposedthateffortstodatetocounterIEDusehave notbeenadequate.Thishasbeenacknowledged withintheUSArmyC-IED2022strategywhichstates, thecurrentiterationexpandstheaperturetomorefully provideacohesiveandholisticapproachtothis evolvingchallengeandmakesignifcantchangestothe linesofeffort7 traditionallyassociatedwithC-IED.This USArmyC-IEDstrategyclaimsthatsuchalineofeffort frameworkalignswithestablishedstrategicguidance whileallowingfortheadaptabilitythatC-IEDdemands.
C-IEDASSISTANCEDONOR-RECIPIENT DYNAMICS
AnEastAfricanIntergovernmentalAuthorityon Development(IGAD8)meetinginFebruary2022on regionalC-IED,notedtherehadbeensomesuccesses againstIEDuseintheregion.AccordingtotheIGAD securitysectorprogramdirector,ColMuleneh,despite thechallengesinaccuratelyestimatingthenumberof IEDevents,itappearsthatthetotalnumberrecorded in2019marksforthefrsttimeaslightdiminutionin comparisontothegradualincreasesincethe beginningoftheiruseinSomalia.Onepotentialreason forthisassessedC-IEDsuccesswithintheEast AfricanregionmaybeduetoC-IEDdonorassistance toIGADstates.ThistypicallyinvolvesanIEDaffected statereceivingdonorsupport,forexampleintheform ofassistancerelatedtointeralia,training,mentoring, advising,accompanying,assisting,technologyand equipmentprovisionandintelligencesupport.This establishesarecipient-donorrelationshipbetweenthe IEDaffectedstateandthedonorprovidingC-IED assistance.ArecipientstateneedssuchC-IED assistanceastheyhaveadefciencyintheirC-IED capabilitiesorthescaleoftheIEDthreatfacedis beyondtheircapacity9 toatleastmatchbutideallyover matchthethreat.Themotivationsofadonortoprovide C-IEDassistancecanvarybutwilltypicallybe capturedundersomeaspectoftheirforeignpolicy objectivesandbealignedtotheirnationalinterests. Regardlessofthelevelofaltruismespousedbya donor,therewillinevitablybevestedinterestswhich mayormaynotbealignedtothenationalinterestsof therecipientstate.
32 COUNTER-IEDREPORT,Spring/Summer2023
Thedefcienciesinatleastsomeelement(s)of C-IEDofanIEDaffectedstateandtheprovisionof C-IEDassistancefromadonorcanleadtoapower imbalanceintheresultingrelationship.Achallenge oftenfacedbyanIEDaffectedstatereceiving assistanceisthefactthatdonorsmaydrivethe decisionmakingintermsofwhatC-IEDcapabilitiesare investedinandwhattheirprioritiesare.Thereisa requirementfortheestablishmentoftheappropriate relationshipbetweendonorsandrecipientIEDaffected states,sothemosteffectiveC-IEDassistanceis provided,insupportofthenationalsecurityand developmentobjectivesoftheaffectedstate.Itiskey thatabalanceisstruckbetweentheexpectationsof thedonor(s)supportingC-IEDdevelopmentandthe stakeholderswithinanIEDaffectedstate.Thiswill oftenrequireinitialnegotiationsbetweenthedonorand thestakeholderswithintheIEDaffectedstatewhom theysupport.Therecipientstatepotentiallyendsupin asubmissivepositionrelativetothedonorunlessthe necessarychecksandbalancesareimplementedto ensuretherecipientnationremainsinlegitimate controloftheirownsecurity,safetyandstability.Atthe veryleastadonorwillwantaccountabilityand oversightofwhereandhowitsmoneyisbeing expended.Forvariousreasonsadonormaystipulate caveatsandrestrictionsontheC-IEDassistanceitwill provide.Inextremis,thedonormayrestrictwhatC-IED assistancetheyarewillingtoprovidetosuchanextent thattherecipientnationhasnosayintheassistanceit receives,howitisimplementedandevenwhocontrols itsdeployment.SuchextremisdonorcontrolsoverCIEDassistancemayevengoasfarasunderminingthe independenceandsovereigntyoftherecipientstate. Thisextremepowerimbalanceisdetrimentalto developingindigenouscapabilitiesoftherecipient nation.Suchextremepowerimbalancesarenot consideredcommonbutrepresentaworst-case scenarioinC-IEDassistanceprovision.
STRATEGICPRINCIPLES
InmanycaseswhenadonoroffersC-IEDassistance toanIEDaffectedstatetheywilleitherhavetheirown matureC-IEDexpertiseoralternativelytheywill
engageanimplementingpartnere.g.private contractor,todeliverthenecessaryC-IEDassistance. Ineithercase,thepersonneldeliveringtheassistance willcomewiththeirownparadigmofwhattheC-IED assistancetobedeliveredwillinvolve.Thefactthata recipientstatehasaC-IEDdefciency,meansthatthey maybeunawareofwhatsupporttheyrequire.This presentsthepossibilityofthosedeliveringC-IED assistancetodelivertheirparadigmofrequirements withoutconsideringtheneedsoftherecipientstate. Theserecipientneedscanincludeinteralia,wider nationalinterests,longtermneeds,indigenous capability10 development,sustainablecapacity development,culturalnuances,environmentalfactors andtheatrespecifcrealities.Inthemostextreme casestheassistancemaynotbethreataligned. Withoutsuchcontextspecifcconsiderationstherecan beamisalignmentbetweentheC-IEDassistance deliveredandthewiderneedsoftheIEDaffected state.Suchundesirablerecipientanddonordynamics involvingpowerimbalancesandmisalignment betweentheassistanceprovidedandthelongerterm needsoftheIEDaffectedstatecanbemitigated againstifrecipientnationshaveC-IEDstrategic principlestoreferto.
C-IEDstrategicprinciplesrefertofundamentalrules andguidelinesthatserveasafoundationforreasoning anddecisionmakingaboutthelonger-termdirectionin aC-IEDenterprise.Theycanhelpstatesandregional organisationsindevelopingandsustaininganeffective C-IEDenterprisewithinagivenregion.Aneffective C-IEDstrategicprincipleneedstobeaclear,concise, memorableandactionablephrasethatrepresentsa planforhowtoeffectivelyallocateresourcesto contributetoatleastmatchingbutideallyover matchingthethreatposedbyIEDs.Theyshould provideadirectivebroadenoughtopromote enterprisingbehaviour,butspecifcenoughtoalignthe C-IEDeffortsdecidedupontocomplementwider nationalsecurityordevelopmentobjectives.Arecipient stateofC-IEDassistancecanreferencesuch principleswhenconsideringhowtoengageinaC-IED enterprise,whatassistancetobeagreedtoandhowit maybemanaged.SuchempowermentofIED
33 counteriedreport.com
C-IEDDONORASSISTANCE – C-IEDSTRATEGICPRINCIPLES
C-IEDDONORASSISTANCE – C-IEDSTRATEGICPRINCIPLES
affected statescanallowforoptimalindigenous capabilityinvestmentandintimecapacity developmenttoatleastmatchbutideallyovermatch theIEDthreatfaced.
IDENTIFYINGSTRATEGICPRINCIPLES
Toidentifystrategicprinciplesinsupportofa regionallycoherentC-IEDenterpriseweneedto assesswhichC-IEDeffortsshouldbepromotedand thosewhichshouldbeavoidedorminimized.Several approacheswereconsideredindevelopingan analysisframeworktofacilitatetheidentifcationof commonthemesforagivenIEDthreatunder examination.Theseincluded:
•Identifyingends,waysandmeans;
•Consideringthesituation,task,execution, authority,andsupportdemands;
•Thesevenplanningquestions;11
•Why,what,who,where,whenandhowofthe problem(5W+H).
Considerationoftheoverlapbetweeneachofthese approachesallowedforthemappingofrelationships betweenthemascapturedin Table1.
Thefrstofthesevenquestions,‘whatisthesituation andhowdoesitaffectus?’effectivelyprovidesthe problemstatementthatweareattemptingtoaddress. Inthiscase,wehavethestartingassumptionthatan IEDthreatexistsinagivenregion,stateorlocality requiringtheIEDaffectedstateornumberofstatesto engageinaC-IEDenterprise.Asthisproblem statementisknown,nosuchquestionneedstobe includedinanyanalysistoidentifyC-IEDstrategic principles.
ReferringtoTable1,weseethatweareleftwith sevenquestionsinadditiontotheproblemstatement question.Thesequestionsare:
•Whatend-stateisdesired?
•Whatactionsaretobetaken?
•Whoaretotaketheactions?
•Whereareactionstobetaken?
•Whenareactionstobetaken?
•Whatrisksneedtobemanaged?
•Whatresourcesdotheactionsrequire?
ApplyingthesesevenquestionstoagivenIED threat,allowscommonthemestoemergeintermsof whatmaybemostandleastimpactfulinsupportofa regionallycoherentC-IEDenterprise.Inconsidering thequestion‘whatendstateisdesired’thereisa requirementtoidentifydetailedrealitiesofthedesired endstateofaregionallycoherentC-IEDenterprise. Thequestionof‘whatactionsneedtobetaken’can bechallengingwhendevelopingC-IEDstrategic principles.ForagivenIEDthreat,asignifcant numberofspecifcC-IEDactionscaninvariablybe listed;however,thesewillbecontextspecifc.The temptationtolistactionsneededaspartofaC-IED strategyshouldberesisted.Instead,generic guidanceonthemostappropriateactionstobe takenisrequired.However,thekeyfundamental C-IEDenablingactionof‘understanding’boththe problemandtheC-IEDeffortsinvestedin,isdeemed essential.
Thequestionof‘whoaretotakeactions’isan examinationofwhothestakeholdersareintheC-IED enterprise.Thisstakeholderanalysishastwoelements toit,namely,whoaretherequiredmembersofthe C-IEDenterpriseandsecondlywhoistoleadthis communityofstakeholders.Whenconsidering‘where areactionstobetaken’fromastrategicratherthanan operationalortacticalperspective,thisquestion considerswherewithinastateoritsinstitutions,C-IED effortsshouldreside.Likethequestion‘whatactions aretobetaken,’thequestion‘whenactionsaretobe taken’canbechallengingtoanswerfromastrategic perspective.Thisquestionaddressesthechallengesin identifyingappropriatemanagementstructuresand practicesacrossanyC-IEDenterprise,whichcanbe multistakeholder,complex,dynamicandeven competitive.Suchstructuresandpracticesgobeyond timingandsynchronizationtowidercrosscutting considerationsacrossallaspectsofmanaginga C-IEDenterprise.
Thequestionof‘whatrisksneedtobemanaged’has twoaspectstoitnamelywhatwilloptimizethe likelihoodofsuccessofanationalC-IEDenterprise andsecondlywhatthreatsneedtobemitigated against.Somerecurrentriskstypicallyarisesuchas
34 COUNTER-IEDREPORT,Spring/Summer2023
interalia;lackofunderstanding;lackofcoherence, coordinationandcooperationoftenleadingto unnecessarycompetitionandwasteofresources amongststakeholders;lackofpowerofenforcementto compelstakeholderstoengageeffectivelyintheC-IED enterprise;andfnally,theriskofsomeC-IEDefforts havingnegativecounterproductiveeffectswhich overalldamagetheC-IEDenterprise.
Thefnalquestionof‘whatresourcesdowerequire’ examineshowemploymentoftechnologyand equipmentcansupportanationalC-IEDenterprise mosteffectively.Havingundertakenthisanalysisto identifywhatisconsideredasmostandleastimpactful insupportofaregionallycoherentC-IEDenterprise, distillingthesefndingsinto‘whatgoodenoughmaylook like’intermsofstrategicC-IEDprinciplesispossible.
C-IEDDONORASSISTANCE – C-IEDSTRATEGICPRINCIPLES 35 counteriedreport.com
EndsWaysMeans → Demands → 7Questions → 5W+H → QuestiontoPose → Situation → Whatisthesituationand howdoesitaffectus? → Whyarewetaking action? → ProblemStatement–AnswerKnown Ends → Mission → Whathavewebeentoldto doandwhy? → Whatistobeachieved? → Whatend-stateis desired? Ways → Execution+ Command/ Authority → Whateffectsdoweneedto achieve? → Howarewetoachieve whatistobedone? → Whatactionsareto betaken? → Wherecanwebest accomplisheacheffect? → Whoaretotakethe actions? → Whoaretotakethe actions? → Whenandwheredothe actionstakeplacein relationtoeachother? → Whenareactionstobe taken? → Whenareactionsto betaken? Whereareactionstobe taken? → Whereareactionsto betaken? → Whatcontrolmeasuresdo weneedtoimpose? Additionalto5W+H → Whatrisksneedtobe managed?
Whatwilloptimizethe likelihoodofsuccess?
Means → Support → Whatresourcesdowe needtoaccomplisheach effect? → Whatresourcesdothe actionsrequire? → Whatresourcesdo theactionsrequire?
Table1.ProcessInDevelopmentoftheSevenQuestionFrameworkforC-IEDStrategicPrinciple.
→
Whatthreatsneedtobe mitigatedagainst?
CONCLUSION
WhenprovidingC-IEDdonorassistance,the importanceofastrategicapproachhasbeenoutlined.
C-IEDassistancedonor-recipientdynamicscanbe challengingformultiplereasons.C-IEDstrategic principlescaninformC-IEDstrategicguidancethatcan inturnbeusedtooptimizesuchdynamics.
HowregionallycoherentC-IEDenterprisesare establishedisuniqueandcontextspecifc.Theydonot needtohaveaspecifcstandaloneC-IEDstrategy.In general,withtheUnitedStatesanexception,most WesternnationsdonothavededicatedC-IED strategies.Instead,theirstrategicapproachto addressingtheuseofIEDsisembeddedwithinother nationalsecuritystrategiesordealtwithasalaw enforcementissueandforthisreasonthereisnoneed tohaveastandalonenationalC-IEDstrategy.Infact anyinstrument,publicationordocumentthat articulatesorservestocoordinatenationalC-IEDcan qualifyasanelementofsuchstrategy.However,the meritofastandaloneC-IEDstrategicdocumentshould notbedismissed.InthecaseofsomeIEDaffected statesorregionsrequiringC-IEDdonorassistance,the impactofIEDusecanbesogreatandowingtoalack ofsuitablesecurityforcecapabilitiesandcapacities, thatastandalonenationalC-IEDstrategymaybe necessary.
Oneperspectiveisthatpolicydocuments,doctrines, policystatementsandactionplanswhicharticulateCIEDstrategy,shouldprimarilybefocusedtoinform donorswheretheinvestmentoftheirmoneyisbest servedtocountertheiruse.Insomecases,C-IED strategymaybedevelopedtoappeasedonorswho seekreassurancethatthemoneytheyareprovidingis beingdoneunderastrategicapproach.Such strategiesmaybe‘papertigers’andnothave foundationinwhatisneededorachievableinsupport ofreducingIEDuse.However,byapplyingC-IED strategicprinciples,theriskofsuchanoutcomecanbe minimized.
Finally,wehaveprovidedaframeworkofseven questionstobeusedwhentryingtoestablishwhat C-IEDstrategicprinciplesbestsuitagivenIED affectedregiontoachievetherequiredimpactsand
outcomesfromC-IEDdonorassistance.Toemploythis frameworkinidentifyingoptimalC-IEDstrategic principles,itisnecessarytohaveappropriatekey stakeholderengagementandotherbaseline assessmentscompletedtoinformtheunderstandingof theIEDthreatbeingcountered.Theapplicationofthis methodologywillbethesubjectofasubsequentarticle intheCounter-IEDReportbasedonresearch conductedinEastAfrica.■
NOTES
1.VariousformsofC-IEDsupportthatanIED affectedstatecanreceivefromadonorwhich canincludeinteralia,training,mentoring, advising,accompanying,assisting,technology andequipmentprovisionandintelligencesupport.
2.Statecraftmaybeconsideredas“theskillof governingacountry”(CambridgeDictionary Online)“theartofconductingstateaffairs” (MerriamWebsterDictionary)or“theskilful managementofstatesmanship”(Oxford LanguagesLanguage.oup.com).
3.AccordingtoHarryYargerinhisarticleinTowarda TheoryofStrategyin GuidetoNationalSecurity PolicyandStrategypublishedin2006,ArtLykke gavecoherentformtoatheoryofstrategywithhis articulationofthethree-leggedstoolmodelof strategywhichillustratedstrategy=ends+ways+ means,andifthesewerenotinbalance,the assumptionofgreaterrisk.IntheLykkemodel,the endsare“objectives,”thewaysarethe“concepts” foraccomplishingtheobjectives,andthemeansare the“resources”forsupportingtheconcepts.
4.TherearemanywhoderidetheLykkemodelfor strategy,forexample,JeffreyW.Meisierauthored anarticleinParametersintheWinter2016-2017 editionentitled“AreOurStrategicModelsFlawed? Ends+Ways+Means=(Bad)Strategy.”
5.Tacticalisusedhereinitsmilitarycontext,referring tocarefullyconsideredactionsintendedtoachieve aspecifcaim.
6.Strategicinthiscontextisconsideredtheeffects IEDusehasattheatre,nationalorinternational levels.
36 COUNTER-IEDREPORT,Spring/Summer2023
C-IEDDONORASSISTANCE – C-IEDSTRATEGICPRINCIPLES
7.Linesofeffortinthecontextofplanning,usethe purpose(causeandeffect)tofocuseffortstoward establishingoperationalandstrategicconditionsby linkingmultipletasksandmissions.
8.TheIntergovernmentalAuthorityonDevelopment (IGAD)inEastAfricawascreatedin1996to supersedetheIntergovernmentalAuthorityon DroughtandDevelopment(IGADD)whichwas foundedin1986tomitigatetheeffectsofthe recurringseveredroughtsandothernatural disastersthatresultedinwidespreadfamine, ecologicaldegradationandeconomichardshipin theregion.Djibouti,Ethiopia,Kenya,Somalia, SudanandUganda–actedthroughtheUnited Nationstoestablishtheintergovernmentalbodyfor developmentanddroughtcontrolintheirregion.
Eritreabecametheseventhmemberafterattaining independencein1993.Withthenewemerging politicalandsocio-economicchallenges,the assemblyofHeadsofStateandGovernment, meetinginAddisAbabainApril1995,resolvedto revitalizeIGADDandexpandareasofcooperation amongMemberStates.Thenewandrevitalized IGADwaslaunchedduringthe5thSummitofIGAD AssemblyofHeadsofStateandGovernmentheld on25-26November1996inDjibouti.TheSummit endorsedthedecisiontoenhanceregional cooperationinthreepriorityareasoffoodsecurity andenvironmentalprotection,economic cooperation,regionalintegrationandsocial developmentpeaceandsecurity.In2011South SudanjoinedIGADastheeighthmemberstate.
9.Capacityreferstothemeansofanindividual/ organizationtoperformassigneddutieseffectively. Thisincludeshumancapacity(individualand collectivecompetenciesandexperience),physical capacity(appropriateassets)andinstitutional capacity(systems,structuresandorganisational cultureinplace).
10.Capabilityreferstothemeansofanorganizationor entitytobeprofcientinastatedactivityfromthe collectivecontributionofassetsandcompetencyof individualsandgroupstoundertakeitsafely, effectivelyandeffciently.
11.Thisreferstoagenericsetofsevenquestions whichmaybeappliedtoanyplanningscenario whichisadaptedfromthemilitarysevenquestion estimate.
ABOUTTHEAUTHOR
PaulAmoroso isanexplosive hazardsspecialistandhas extensiveexperienceasanIED ThreatMitigationPolicyAdvisor workinginEastandWestAfrica.He servedintheIrishArmyasanIED DisposalandCBRNeoffcer,upto MNTlevel,andhasextensive tactical,operational,andstrategicexperiencein PeacekeepingOperationsinAfricaandtheMiddle East.Hehasexperienceinthedevelopmentof doctrineandpolicyandwasoneofthekeycontributors totheUnitedNationsImprovisedExplosiveDevice DisposalStandardsandtheUnitedNationsExplosive OrdnanceDisposalMilitaryUnitManual.Heworksat presentintheMENAregiononSALWcontrolaswell asinwiderAfricaadvisingonnationalandregional C-IEDstrategies.HehasaMScinExplosiveOrdnance EngineeringandanMAinStrategicStudies.Herunsa consultancy,AssessedMitigationOptions(AMO), whichprovidesadviceandsupportinrelationto conventionalandimprovisedweaponsandexplosive hazardriskmitigation.Thisarticlerefectshisown viewsandnotnecessarilythoseofanyorganisationhe hasworkedfororwithindevelopingtheseideas.
Linkedinprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/

37 counteriedreport.com
C-IEDDONORASSISTANCE – C-IEDSTRATEGICPRINCIPLES
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
DEVELOPMENTFROMIMPROVISEDHOMEMADE TOMASSMARKETCONSUMERELECTRONICS COMPONENTSINIEDs
INTRODUCTION
Theelectronicsindustryemergedinthe20thcentury, andsinceitsintroductionintothelivesofordinary peopleasconsumerelectronics,ithasgrownand becomeatrillion-dollarbusiness.Thepredominant characteristicoftheconsumerelectronicsmarketisthe ever-increasingavailabilityofelectronicsproducts. AccordingtoMoore’sLaw,semiconductorcomponents gaindoubleperformanceeverytwoyears.Thistrend allowedanothertendency,thatoffallingpricesinthe consumerelectronicsmarket.Generally,ithas accountedforgainsinmanufacturingeffciencyand automation,aswellasfallinglaborcostsandoverall designimprovements.
Theconsumerelectronicsindustryisvaluedatmore than$1.3trilliontodayandisexpectedtoincreaseits marketvalueinthefollowingyears.Secondly,the globalconsumerelectronicsrepairandmaintenance marketcontinuestogrow,withanestimatedincreaseto $16.52billionin2020.
TheproliferationoftheRadioControlledImprovised ExplosiveDevice(RCIED)haspresentedalowcost, highlyfexible,andunpredictablethreattoC-IED operators.Highavailabilityofconsumerelectronicsand readilyavailableelectroniccomponentsareusedby threatnetworksintheconstructionofIEDs.
OftenthecomponentsusedinIEDsareeasily obtainablecommercialgoodssuchasfertilizer,bleach (peroxide),nailpolishremover,brakefuid,herbicides, disinfectants,andcleaningsolvents.Thetrade, transportationandstorageoftheseproductsistypically subjecttoalesserdegreeofscrutinyandregulation thanthetransportationandstorageofconventional munitions.ResearchonIEDshasnotrevealeddirect transportationofcommercialgoodsfromlegal manufacturerstoarmedgroups.Rather,smalllocal tradeentities,havingobtaineddualusegoodsfrom regionaldistributioncompanies,appeartobethe weakestlinkinthechainofcustody.1
Oneofthemostimportantelectroniccomponents usedinRCIEDsisthesemiconductor.Thecentral drivingforcebehindtheconsumerelectronicsindustry isthesemiconductorindustrysector,whichbyitselfhas annualsalesnearing$500billion.
AccordingtoINTERPOL,asaglobal,multibilliondollarcrime,organizedcriminalgroupshavenot hesitatedtocashinonthetradeincounterfeitgoods.In manypartsoftheworld,international,regional,and nationallawenforcementauthoritieshaveuncovered intricatelinksbetweenthiscrimeandotherserious offencesincludingillicitdrugs,moneylaundering,and corruption.Someestimatesputthecounterfeit business
38 COUNTER-IEDREPORT,Spring/Summer2023
1Counteringthethreatposedbyimprovisedexplosivedevices,UNGeneralAssemblyReport,25July2016.
BySerkanKoc,Major(OF-3)TUR-A,ElectronicWarfareSpecialist,NATOC-IEDCoE
atwellinexcessof$250billionayear,andsomeportion ofthesecounterfeitgoodscanbeusedascomponents forRCIEDs.Amongthesecounterfeitgoods,thereare manyeasy-to-usecomponentssuchaspower distributioncomponents,transformers,switchgears, relays,contacts,timers,circuitbreakers,fuses, distributionboards,wiringaccessoriesandbatteries.2
BoththeAttacktheNetworksandDefeattheDevice pillarsofcounteringIEDsareusedinordertofghtthis evolvingthreat.Severalelectroniccounter-measures willbeusedinordertodetect,prevent,orneutralizethe RCIEDinanoperationalenvironment.However,these technologiesaresupportedwiththepropermeansof attackingthreatnetworksinordertoachievealongtermsolution.

RCIEDTHREAT
RCIEDsarethemostcommonIEDinitiationsystemin theworld.Thetriggermaninitiatesthedevice,sending anelectromagneticimpulsetoinitiatethefringchainor
toarmthemainswitch.Anyelectronicdeviceableto sendandreceiveasignalthroughelectromagnetic radiationcanbeusedasanIED(RCIED)trigger switch.Accordingtotheirtypesandqualifcations, theseswitcheshaveindividualadvantagesand limitations.Forexample,accordingtolatestreports3; inBahrain,RCIEDelectronickitsandvictim-operated PassiveInfra-Red(PIR)triggercomponentswereused together.Inthisscenario,theradio-controlledunits receivethearmingsignalfortheIED,whichfunctions onlywhenthePIRsensoristriggeredbythetarget.As seeninvariousIEDevents,constructionofanRCIED varies,basedontheintendedtargetandthefriendly forcecounter-measuresandTTPs.
AccordingtolatesttrendsintheuseofIEDs,terrorist organizationschoosedevicedesignprinciples accordingtotheintendedtargetandavailable materials.Whenthetargetisimportantandmustbe attackedespeciallyinconvoy,IEDsarearmedby mobileradiosbyusingapassiveinfraredsensor.For
2FocusonTheIllicitTraffckingofCounterfeitGoodsandTransnationalOrganizedCrime,UNOffceonDrugsandCrime FocusSheet.
3TheIEDThreatinBahrain,AcomparativeanalysisofcomponentsdocumentedintheGulfregion,ConfictArmament Research,2019. 4ibid.,p.38.
39 counteriedreport.com
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
APIRtriggerrecoveredfromBahrainiHezbollahmilitantcellsin2017-20184
thesecurityofthedeviceandfortheprotectionofthe triggerman,asecondary,andtertiarymeansof initiationareincorporated.Regardingtherender-safe procedures,thiscomplexdesignseriouslycomplicates themitigationtaskofEODoperator.Accordingto reports,approximately36percentofallEODoperator deathsinthepasttwodecadeshaveoccurredduring clearanceofcommand-initiateddevices.
RCIEDsuseawidevarietyofcommercialand homemadetransceiverandreceiversetstosendthe wirelessinitiationsignalfromvariabledistances.There areseveraltypesofelectronicdevicesabletotransmit indifferentfrequencieswithvariedpower.Forthelast twodecadesseveralRCIEDswitchvariationssuchas; DualToneMultiFrequency(DTMF),LongRange CordlessTelephones(LRCTs),PersonalMobileRadios (PMRs),CarAlarms,RCControllersfortoys,telemetry devices,severalwirelesscommunicationdevicesand cellphoneswereusedbyterroristorganizations.The workingfrequenciesofconsumerelectronics(CE)can
varygreatlyfromregiontoregionduetodifferentlegal requirements.Thefrequencyrangesof,forexample, RCtoyswiththesameexternalconstructioninAsia differconsiderablyfromAfrica,EuropeorAmerica. SinceitcannotnecessarilybeassumedthatCEare onlypurchasedintheoperationalarea(theInternet makesitpossiblewithoutrestrictions),thetechnical exploitationandtheevaluationreportresultingfromit areofessentialimportanceforasuccessfuldefense againstthethreat.
Historically,itemsusedforanIEDbyoneterrorist organizationarealsousedbyotherterrorist organizations.Forexample,RCIEDcomponents capturedfrommilitantsinBahrainandHouthirebelsor AQAPmilitantsinYemenhaveverycommonelectronic componentswhichcanbeorderedinmassamounts. Asimplerelay,usedtoswitchonandoff,andtocontrol ahigh-powerelectronicdevice,canbeobtainedin massamountsandisusedinmosttypesofRCIEDs. Thistrendisalsoobservedinmicrocontrollers.
5ibid.,p.50.
40 COUNTER-IEDREPORT,Spring/Summer2023
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
Components RCIEDkits andPIR sensorsin Bahrain HouthiRCIED kitsandPIR sensorsin Yemen HouthiUAVs inYemen IslamicState inYemen/ AQAP RCIEDs IslamicState ofIraq RCIEDs HKESignalRelay X X X X X MicrochipMicrocontrollers X X MicrochipAtmel Microcontrollers X X MicrosemiMT8770DEDTMF Receiver X X NaisAGN2004HPowerDelay X X OmronGS6K-2-HPCBPower Relay X X X PanasonicSignalRelay X PrincetonTechnologyCorp PT2262RemoteControlEncoder X STMicroelectronicsVoltage Regulators X X X X X WoeHeat-ShrinkWrap X X X GreyCable X X X ElectronicComponentsinIEDsinArabianPeninsulaandIraq2016-2018 5
CountryName
DesignPrinciples ofTerrorist Organizationsin LatestIEDs
TypesofIEDs usedbyTerrorist Organizations UsedMaterial
NotesonindividualTerrorist Organization
Democratic Republicof theCongo
Simpledesign withmilitaryor dual-use commercial components
CommandWire
Recovered Militaryand/or Commercial Explosivesand Detonators
Nigeria
Simpledesign withmilitaryor dual-use commercial components
VictimOperated Person-Borne
Anincreaseinthetechnical capacityofarmedgroupsto diversify,designanddeploy increasinglysophisticateddevices hasbeenobserved
Somalia
Dual-use componentsand chemicals
Vehicle-Borne
Military explosives harvestedfrom explosive remnantsofwar
Al-Shabaabusinghome-made explosivesdemonstratesthat deviceconstructionmethodshave diversifed
Colombia
Complexdesign toselecttarget
Commandinitiate dimprovised explosivedevices
Diversifcationcouldindicatean increaseintechnicalcapacity amongarmedgroups
Yemen
Anti-personnel minesofan improvisednature
Improvised PressurePlates
Massproduction ofIED components
Newtacticsinthedesignand deploymentofvictim-operated devices,includingdisguising devicesasrockstohindertheir identifcationbyclearanceexperts
TheinformationtableisdevelopedbasedontheCounteringthethreatposedbyimprovisedexplosivedevices, UNGeneralAssemblyReport,17July2020.
AccordingtolatestreportsfromUN,thetechnical capacityofarmedgroupstodiversify,design,and deployincreasinglysophisticateddeviceshas improved.TheinformationonrecenttypesofIEDs, designprinciples,andmaterialsusedindifferent regionsisseeninthetableabove.
Inrecentyears,severalbrandedelectronic components–includingmicrocontrollers,power relays,andvoltageregulators–areconsistentacross RCIEDsrecoveredinBahrainandRCIEDsandUA (UnmannedAircraft)recoveredfromtheHouthisin Yemen.6

41 counteriedreport.com
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
6AGuidetoIllicitIranianWeaponTransfers,TheBahrainFile,AtlanticCouncil,TimMichetti,December2020.
PIC16F628AMicrocontrollers.
TRENDSINCONSUMERELECTRONICSMARKET
Beforeanalysingtheeffectsoftrendsinconsumer electronicsmarketonIEDs,itisbenefcialtomakea cleardefnitionofwhatconsumerelectronicsinclude.

Intermsofdifferentapproaches,consumerelectronics areclassifedinfourdifferentways:
Inaccordancewith“ImprovisedExplosiveDevice IEDTechnicalExploitationLexicon5thEdition(2017)”:
•“ConsumerElectronics”conceptislimitedto:
◦RadioControlledToy
◦ApplianceController
◦GarageDoorOpener
◦DoorBell
•Butthisconceptwouldnotinclude:
◦Hand-HeldRadio
•PersonalMobileRadio(PMR)
•RadioTransceiver
◦Non-Hand-HeldRadio
•TaxiRadio
•TrunkMountRadio
◦CordlessPhone
•LongRangeCordlessTelephone(LRCT)
•HighPowerCordlessPhone(HPCP)
◦MobilePhone
•GlobalSystemforMobileCommunications (GSM)
•CodeDivisionMultipleAccess(CDMA) phone

◦CustomRadioControl
•WirelessCustomReceiver(WICR)
•DualtoneMultiFrequency(DTMF)MOD1-5
•Multi-hopWirelessSensorNetworksusing RadioFrequency(Multi-hopRF)
•FireworksController
◦Telemetry
•Linx(DigitalEnhancedCordlessTelecommunicationsDECT)
•Maxstream(Radiomodems)
•Others.
42 COUNTER-IEDREPORT,Spring/Summer2023
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
Omron,NAISandHKEBrandedPowerRelays.
STMBrandedVoltageRegulators.
DTMFReceiverBoards.
Ifconsumerelectronicsareconsideredfromapoint ofviewofthewidestpublicapproach,accordingto latestestimatestoday,theconsumerelectronics industryisvaluedatmorethan$1.3trillion,andis expectedtogrowsteadilyinthefollowingyears. Emerginganddisruptivetechnologiesandinnovations willcontinuetodrivethemarket.Inaddition, capabilitiesofnewproductsfostercustomer expectations,andconsequentlytheappetitefor spendingonnewtechnologycontinuestogrow.
Threatnetworkscontinuetousecommercialoff-theshelf(COTS)componentsinthemassproductionof IEDs.Especiallytheeasyaccessibilityofcommercial radiocontrolledtransmittersandreceiverkitsfacilitates deviceproductionofadependableandsafeIED.The programmabilityofmicrocontrollersandtheavailability ofawiderangeoffrequenciesavailabletooperate makestheRCIEDaneffectivetoolagainstfriendly forces.Withtheexpanseofthecommunication electronicsmarketandeasyavailability,RCIEDs requirelittleornomodifcation.MobileradiosorRF transmittermodulesaremorecapablethanever,are
easilyusedasthefringswitchwithinaRCIED.In general,consumerelectronicsdevicesavailableinthe marketareofhighquality,reliable,andofcheapcost duetomassproduction.Theyarealsosoftware adaptableanddesignedtooperateinacongested electromagneticenvironment.
InthepastThreatNetworkswereselectingamong specifcfrequencieswhichareavailablefortheRF deviceortransmittermoduleinthemarket.
Thehighavailabilityofthesedeviceshasstemmed fromtheoveralltrendintheconsumerelectronics market.Themiddle-classpopulationisincreasing worldwide,inthepastfewyears.Moreover,urban consumershavebeenindicatingashiftinlifestyle. Soaringinternetpenetrationandincreasingincomeare allowingconsumerstousemultipleelectronicdevices. Thiswillcontinuetofuelthemarketgrowthoverthe nextfewyears.7
Traditionallyoneofthemostimportantdesign principlesforanyterrorististooperatetheRFdevice effectivelywhiletriggeringtheIEDfromasafe distance.Becauseofthislimitation,terroriststendto

USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs 43 counteriedreport.com
ConsumerElectronicsRevenues(USD,millions).
7ConsumerElectronicsMarketRevenuestoRakeinataCAGRof15.4%,SmartphonestoContinueDominanceover 2016-2020,PersistentMarketResearch,23December2016.
selectcommunicationchannelsthatareclearand effcientenoughtosendthesignaltothereceiver.For counter-measuredevelopment,engineersandIED expertshavefocusedmainlyonoperatingrange.The constrictionofhealthycommunicationchannelsofthe RFdevicesavailableinthepasthasledtorelatively

narrowfrequencybandsinjammers.Consideringthe abundanceofdifferentelectroniccomponentsinthe markettoday,terroristnetworkshaveawiderangeof availablefrequenciestooperateinordertotrigger theRCIED.

Counter-measuresagainstRCIEDswerefocusing onnarrowfrequenciesinthepast,buttoday’s consumerelectronicsmarketpresentsthemost effcient,effectivedevicesforverycheapprices.With commerciallyavailableRFdevicesrangingfromafew MHztomanyGHz,therangeofpossiblethreatsspans nearlytheentireRFspectrum.Thesedevicesare

44 COUNTER-IEDREPORT,Spring/Summer2023
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
SimplePMRsinthepast446Mhz.
ReadyWirelessRCSwitches(25Euros).
PassiveInfra-RedSensors(0.44Euros).
Today’sChineseBaofeng(20Euros)136-174,144-148,400-480,430-450Mhz.
obtainedinlargequantities.Asaresultoftheextentof potentialRCIEDoperatingfrequencies,CounterRCIEDdesignersshouldtakeintoaccountallofthe availablefrequenciesinRFdevices.Ontheother hand,anintelligentRFprofessionalcanmake modifcationstoanykindofRFdevicetoadaptit againstfriendlyforces’electroniccounter-measures.
Newtechnologieshaveenabledthreatnetworksto producetheirowndesignsinaneasierway.With additivemanufacturingor3Dprinting,threedimensionalproductscanbecreated(suchasnew designsforIEDcontainersetc.)bylayeringmaterial usingacomputerizedprocess.Reducedprocess time,costreduction,andbetterqualityand improvementsinthedesignofthefnalproductare beneftsobtainedfromthisemergingtechnology.With theadventof5G,InternetofThings(IoT),anothernew technologywillbeavailableforthreatnetworksand canbestartedtobeemployedinthenearfuture.In thiswayanecosystemofelectronicdevicesis connectedtothesamenetwork(inhere5G),andcan beaccessedremotelyandIEDattacksareexecuted fromadistancewiththeuseofsensortechnologies andconnecteddevices.
Additionally,the5Gtechnology,withitsdisruptive nature,seemstoaffectnotonlytheadversarieswho areaimingtousethistechnologyformoreeffective IEDattacks,butalsofriendlyforceswhoaretryingto developcounter-measuresagainstthistechnology.
Fromthepointofviewoffriendlyforces,the5G technologywillleadtotheemergenceofnew equipmentwithnewcapabilitiesintherealmof intelligence,surveillance,andreconnaissance(ISR) systems,command-and-controlapplications,manned andautonomousvehicles,anddrones.Inthisway5G willincreasethesituationalawarenessoftheIED operator.Especially,abetteruseofremoteand autonomousvehicleswithanumberofsensors connectedthroughtheInternetofThingswillincrease thestand-offdistancesoftheIEDoperatorinthe approachtotheexplosivethreat.Ontheotherhand,
theabilityforinterconnectionofdifferentequipment andsensorsenablesadversariestoplanmore complexTTPsintheoperationalarea.
However,5Gtechnologycomeswithsome restrictions,suchastherangeof5Gconnectivityis limitedbecausefrequencywavescanonlytravela shortdistance.Inordertodeliver5G,newantennas mustbeinstalled.Thisisataskwhichisboth expensiveandtime-consuming.Additionally,thereare limitationsforthreatnetworksforruralaccessto thetechnology.
ThenextthreatinNATOcountriesandAfricanareas ofoperations/crisis,isexpectedtocomefromCOTS UA(UnmannedAircraft)whicharecarryingIEDs. Advancedmanufacturingallowstheproductionoftens ofthousandsofsmall,smart,andinexpensivedrones. Itcombinesadditivemanufacturing(a.k.a3Dprinting), robots,andartifcialintelligencetomassivelyincrease thespeedandqualityofmanufacturing.Ofparticular importanceinsmalldroneproductionistherapid printingofcompositematerial.Todayacommercial3D printeris100timesfasterthanpreviousprinters.In additiontospeed,thecontinuingmassiveinvestment in3Dprintinghasimprovedbothqualityand complexityofmanufacturedproductswhilereducing prices.Priceshavedroppedtopointwhereweekend hobbyistsareprintingtheirowndrones.8
FromaC-IEDpointofview,anyplatformand technologythatcancarryexplosivestothetarget,or thatcanenablebetterTTPsforthreatnetworks,should beregardedasanareatoconsiderwhiledeveloping effectivecounter-measures.Withtheadventof emerginganddisruptivetechnologiessuchasArtifcial Intelligence,InternetofThingsandAutonomy,both friendlyforcesandthreatnetworkswillhavenewtools intheirtoolbox.
CONCLUSIONS
IntermsofDefeatingtheDevice,readilyavailable consumerelectroniccomponentsarebeingusedby threatnetworksintheconstructionofIEDs.According
45 counteriedreport.com
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
8T.X.Hammes,TechnologyConverges;Non-StateActorsBeneft, https://www.hoover.org/research/technology-convergesnon-state-actors-beneft
tolatesttrendsintheuseofIEDs,terrorist organizationsarechoosingtheirdesignprinciples accordingtotheirtargetsandavailablematerials. Consumerelectronicsdevicesavailableinthemarket areofhighqualityandcheapduetomassproduction. Inaddition,theyaredesignedtooperateinacontested electromagneticenvironment.Non-LinearJunction DetectionandHigh-PowerElectromagneticscanbe theareastofocusoninthefuture.
IntermsoftheAttackingtheNetworkspointofview, thetrendstoahigheruseofmassmarketconsumer electronicswithoutmodifcationasRadioControlled IEDswitchesbyThreatNetworksarewidelyevidenced inAfrica,whichseemsnottobethetypicalcaseinthe restoftheworld.Itseemslikethepotentialuseofmass marketconsumerelectronicsbyThreatNetworksis mainlyaffectedby:
Leveloffnancing
Higherbudgetsseemtoberelatedtolessuseof consumerelectronics,somostlyfocusingon homemade/semi-industrialRCdevicesand/or modifedelectronicdevices.
Availabilityofexperiencedinstructors(internalor externaltothegroup)
Therelativelackofspecialistsinelectronicsand/or thelackofexperiencedIEDinstructorspositively infuencesthepredominanceofconsumerelectronics over homemade/ modifed electronicdevices.
Levelofexternalsupport
Greaterexternalsupportisrelatedtolessuseof consumerelectronics,somostlyfocusingon homemade/semi-industrialRCdevicesand/or modifedelectronicdevices.
Availabilityofimportedgoods
Alowervarietyormorediffcultaccesstoimported goodscouldleadtotheuseofavailableconsumer electronics.
Adecreaseduseofhomemade/ modifed electronicdeviceswouldreduceopportunitiesfor theidentifcationofspecifcbombmakers
signaturesrelatedtodifferentincidents.Usingmass consumerproductswouldmakeithardertoidentify specifccommonsignaturesfromelectronicexperts andmaketrackingofcomponentsmorediffcult regardingdifferentincidentsfromareasof operations. ■
Disclaimer
Thisarticledoesnotrepresenttheopinionofany nationalormultinationalorganisation;itswholecontent shouldonlybeconsideredastheopinionoftheauthor. Asalltheinformationhasbeenobtainedfromopen sources,potentialmistakescouldhavebeenmade duringtheresearchprocess.Pleasefeelfreetosend yourcomments,correctionsandinputstotheauthor, theywillbehighlyappreciated.
ABOUTTHEAUTHOR
MajorSerkanKoç wascommissionedintotheC-IEDCentreof ExcellenceasanElectronicWarfare SpecialistintheDefeattheDevice BranchinAugust2020,and organized5thNATOC-IED TechnologyWorkshopinSegovia/ Spainin2022.AsanElectronics EngineerOffcer,hisbackgroundhasbeenmainly basedonIEDcounter-measureactivitiesandproject management(R&Dandprocurement)asElectronic WarfareOffcerintheTurkishArmyHeadquarters.In additiontohiselectronicsengineeringeducation,he hasanM.A.degreeinTechnologyManagementfrom TurkishMinistryofDefence,DefenceScienceInstitute andSystemsEngineeringprogramdegreefromU.S. NavalPostgraduateSchool.Hecurrentlycontinueshis PhD.Program.
Email: skoc@ciedcoe.org

46 COUNTER-IEDREPORT,Spring/Summer2023
USEOFMASSMARKETCONSUMERELECTRONICSCOMPONENTSINIEDs
AIRBORNEMAGNETICS-AVIABLETOOLFOR DETECTIONANDQUALITYCONTROL
ByDipl.-Ing.WolfgangSüß,ManagingDirector,SENSYS
Thescopeofthisarticleistoillustratethecurrent stateofairbornemagneticsasacommercial andviablesolutionalreadyinuseworldwidefor commercial,defense,buthumanitarianapplications. Thelastdecadeoftechnologyevolutionbroughta massiveinnovationintheareaofremotelyoperated platformsonland,waterandintheair.Self-established vehicleswithopen-sourcesoftwarewerereplacedby commercialofftheshelfsolutionsintegratingavast
numberofsensorsforoperation,navigatingand obstacleavoidanceinthefeld.
Unmannedaerialvehicles(UAVs),Unmannedground vehicles(UGVs)andUnmannedsurfacevehicles (USVs)arealreadyindailyoperationformanifoldtasks likesurveillanceofproperties,industrialinspectionand monitoringofmachineriesorindustrialchimneys, agriculturalsupport,parcelservices,orthophotography and3Dmodellingofminingareasorbuildingyards.

AIRBORNEMAGNETICS
47 counteriedreport.com
SENSYSMagDroneR4operatedwithaDJIM300overamilitarycontaminatedarea.
Sensitivefeldslikethesearchforanddetectionof bombs,ammunition,minesandIEDsarestill underdevelopedoratleastthecommercialsolutions areunderrated.Anumberofgrantsandscientifc studiesalreadyledtoverydifferentsolutionsusing largedronestocarryground-baseddesigned equipmenttoshowcaseanewapproachtothe hazardousgroundworkofpeoplewithinminefelds. Attheend,thechallengesoffnancingatruly technology-drivensolution,turninglaborcostsand competenciesupsidedownaswellashavingdifferent technicalsolutionsforsingleusecases,made remoteoperatedsensorplatformslessattractive. Nevertheless,themarketoffersafewtechnology packagescombiningacommercialdronewith additionalcomputingpowerandmagnetometersfor simple,butprofessionaluseinthefeldofUXO detection,areaobservationandprojectqualitycontrol.
SENSYSisamanufacturerofmagnetometerand TimeDomainElectromagnetics(TDEM)solutionsfor monitoring,detectionandanalysisofareasand objects.Thecompanywasfoundedin1990andis basedinGermany,EastofthecapitalBerlin.Since then,thecompanygrewto50employees developing,producingandservicingsingleFluxgate Magnetometers,hand-helddevices,multi-sensor systemstobeoperatedbyman,carorremote platformsonland,underwaterorintheair. Commercialcompanies,thedefenseindustry,military andNGOsareusingtheequipmentinmorethan90 countriesworldwide.SENSYSproductsaredesigned forsimpleoperationinharshfeldconditions, providingexcellentdata.
ClientslikeAIRBUS,Rheinmetall,SafeLaneGlobal andmanyothersrelyonSENSYSsolutionswithin theirprojects.
ThecompanyfocusonFluxgateMagnetometers allowsSENSYStooptimizethesensortechnology andenablecustomizationfordifferentapplications. Magnetometersarepassivesensorsthatarerecording magneticintensity.Comparabletotheprincipleofa temperaturesensor,Fluxgatesmeasureatthepointof thesensoritself(notatanydistance,norhavinga certainangleofoperation).ThatwayaFluxgatesensor
isalwaysmeasuringtheEarth’sMagneticfeld.Ferrous objectsaredistortingtheEarthmagneticfuxlinesin theirproximity.Thus,whenasensorcomesclosetoa buriedobject,itdetectstheanomalyintheEarth’s magneticfeld.AssuminganambientEarth’smagnetic feldofaround60,000nT,thesensornoiseofSENSYS producedFluxgateMagnetometersisaslowas 0,006nT;therefore,SENSYSsensorscandetect changesinthemagneticfuxaslowasthe10millionth partoftheEarth’smagneticfeld.
Theillustrationoppositeshowshowfasta magneticfeldofanobject(physicallydescribedvia itsmagneticmomentinAm2)decreasesover distance.Thatmeans,thatthebestchancefor detectingofburiedobjects,isalwaysbygettingas closeaspossibletoorevenintotheground(e.g. borehole/drillingsurveys).
Thejourneytowardsairbornesolutionsstartedin 2015,whenSENSYSinvestigatedintodrone-based Magnetometersurveys.Usingaself-assembled octocopterwithanopen-sourcecontrolsoftware,frst fightswerebumpyandtobesafewemaintaineda distancetogroundofseveralmeters.Theapproachof hangingtheverysensitiveFluxgateMagnetometers awayfromthedronewasgood,butnotpracticalatall asthatresultedinunstablefightcontrolsofthedrone. Thesensorswereswingingheavilyduringfight,so thataprecisepositioningofthesensordataonthe colorcodemagneticmapwasimpossible.Also,at thistime,standardizedinterfacestothedrone(GPS, control,power)werenotavailable,sothatthedrone integrationwasahassle.
Withtwoyearsofresearch,trialsandprototyping, SENSYSfocusedonacompact2-sensorsolutionwith itsownbattery,GPSanddatastorage,calledMagDrone R3.Withonly800gweightandnoeffortstointegrateand fythedeviceitrapidlymadeitswayintoGeophysics, MiningandExploration.Everybodywhohadtooperate aCessna,twopilotsandheavyequipmentonboard couldnowcoverthesamework(andproducebetter data)withabackpackloadedwithasmallcommercial droneandtheSENSYSMagDroneR3surveykit.
Withagrowingmarketaskingformoreeffcient solutions,SENSYSreleasedthe5-sensorMagDrone
48 COUNTER-IEDREPORT,Spring/Summer2023
AIRBORNEMAGNETICS
R4in2020offeringa2.5mspan/swathtobemounted onmostcommercialUAVswith2kgpayload.The systemhas5sensors,separated50cmfromeachother. TheinstalledFluxgatesaretriaxialMagnetometers, whereasallaxes(x,yandz)fromeachsensorare recordedseparately200timespersecond,generating 18,000measurementvaluesperminute.The200Hz samplingratesallowforfastfightswithoutlosingdata density.Atthesametime,thelowweightofthe MagDroneR4supportstheuseofsmalldronesand stablefightconditions.

Atthesametime,DJIreleaseditsfagshipmodel M300andtheLatviancompanySPHEngineering reachedapointinproductstabilitywiththeirUgCS SkyhubTTF(trueterrainfollowing).UsingtheM300as themainplatformandaddingtheSkyHubfor overrulingDJI’sfightcontrol,enablesustoconduct
closegroundfightswithterrainfollowingmode. Furthermore,theSkyHubcontrollercanexportthe DJIGPSinformationandforwardtotheSENSYS MagDroneR4foradirectRTKGPSbased georeferencingofallmeasurementdata.With controllableinterferencesofmountingtheMagDrone R4directlyintothelandinggear,thesetupoftheUAV magnetometersurveysystemisascompactas possible,aswellasitensuresanexcellent maneuverabilityoftheUAV.ApowerfulMagDrone DataToolcanprocessandflterthedatatocancel detectedrotornoiseoffthesurveydata,concentrating onburiedstructuresandobjectsintheground.
TheuseoftheMagDroneindozensofcustomer projectsshowsthatthisproductiswaybeyondbeing developed,ithaslongbecomeanex-stockoff-theshelfsolutionforourmarkets.
AIRBORNEMAGNETICS 49 counteriedreport.com
Illustrationofrapiddecreaseofmeasurementvalue(innT)overdistance(inm).
AIRBORNEMAGNETICS
TofurtherapprovethecombinationofDJIM300, SkyHubcontrollerandMagDroneR4magnetometerkit forthedetectionofferromagneticmines,theCroatian MineActionCentre–CentreforTesting,Development andTraining(HCR-CTRO)conductedafeldsurveyon theirBenkovactestsite,whichhas90ferromagnetic minesburiedatdifferentdepthsupto25cm 1 .The resultswerepresentedatthe19thInternational Symposium–MineAction2023,inVodice,Croatiaon May4thtoprovideawarenessofthecapabilitiesof suchadetectionsystem.
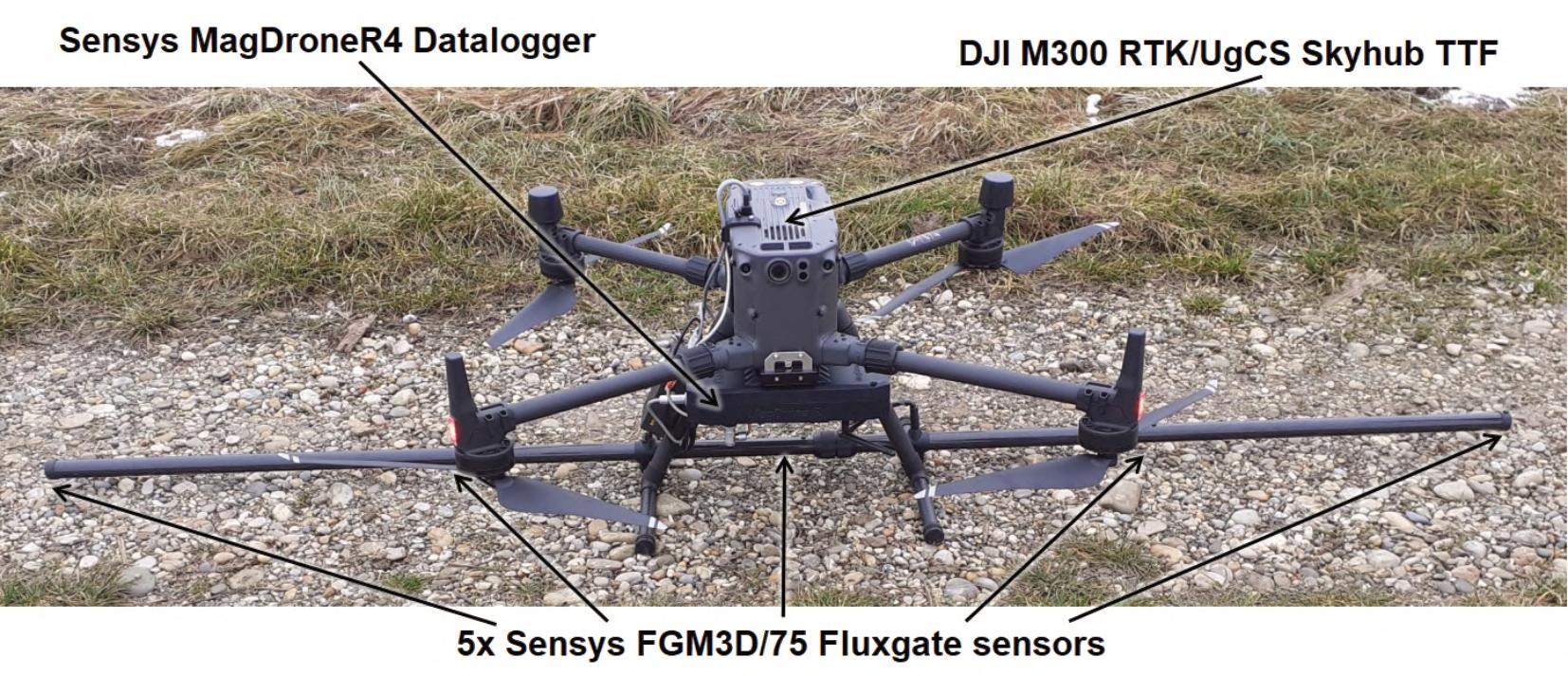
AnothercampaignwasexecutedbytheHeinz SielmannFoundationandtheGermanInstitutefor FederalRealEstate(BImA)onthegroundofthe foreignmilitarytrainingrangeKyritz-RuppinerHeide withtheso-calledBombodromascentraldropzone, NorthofBerlin.SincetheKyritz-RuppinerHeidehas beenintensivelyusedformilitarypurposesbythe Sovietarmedforcessince1950andlaterbythe GermanFederalArmedForces,upto1.5milliontons ofexplosiveordnancearesuspectedaroundthe formerBombodrom.
Nowadays,theHeinzSielmannFoundationis responsibleforthemaintenanceoftheheath,itis importanttodefnecontaminatedareasandtomakeit easiertoplanboththeriskandtheuseoftechnology onthesecontaminatedareas.
Arangeofdifferentammunitionwassurveyedto formulizethecapabilitiesandlimitsoftheairborne surveysystem,whichwillhelptobetterplanpre-scansof areasforriskmitigationaswellastheimplementationof qualitycontrolchecksbeforeandafterfeldwork.The resultsarepromisingaslongasthefeldconditions allowedforshallowfightintherangeof0.5to1mabove theground.Sincealotofammunitionisoflessferrous material,themagneticsignatureoftheseUXOitemsis weak.Forexample,somesmallcasesof20mm,23mm and30mmdiameterwerehardtodetect,whereasallthe grenadesof57mmdiameter,TM62tankmines,piecesof mortarshellsandsteelwireswereclearlydetected. Hence,thesurveysystemneedstooperateclosetoand bestableabovethegroundatconstantconditions(also withinthedrone)tobeabletodistinguishmagnetic noisefromUAVmovements,electronicsandrotors.
50 COUNTER-IEDREPORT,Spring/Summer2023
UAVdetectionsystemconsistingofDJIM300,SkyHubcontrollerandMagDroneR4.

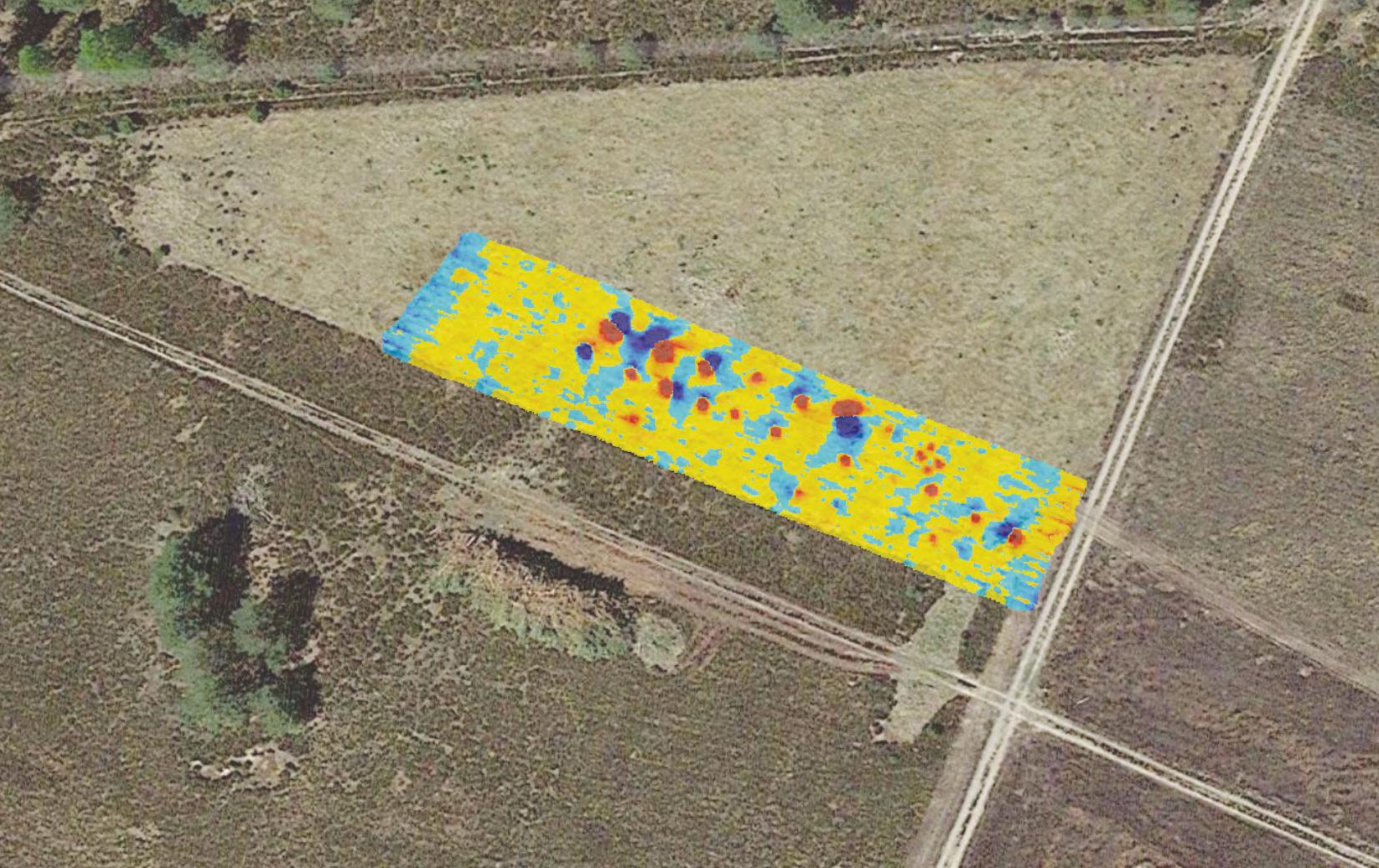
AIRBORNEMAGNETICS 51 counteriedreport.com
MunitiondetectioncapabilitytestatKyritz-RuppinerHeideusingairbornemagnetics.
Resultsofairbornemagneticssurveyat1meteraltitudeabovegroundlevelatKyritz-RuppinerHeide.
Asexplainedinitially,Magnetometersdonothavean openingangle,butoperateatthepointoftheirsensor head.Becauseofthat,ascanoftheentireareais required.Theusualdistancebetweentwosensor tracksis25or50cm.AstheMagDroneR4hasa sensorframewithsensorsat50cmspacingeach,the UAVdetectionsystemneedstofyalineevery2.5m.
With30-40minutesfighttimewithhot-swappable batteriesthedailycoveragecanbeupto30 hectares.Such,thatwasdoneduringahistorical studybytheBavarianStateDepartmentof MonumentsandSitesatGanacker,Bavaria 2 .This siteisaformer“Luftwaffe”operationalairfeld.Since February1945andunderinhumaneconditions, forcedlaborerswereusedtobuildarunwayforthe MesserschmittMe-262jet-poweredfghteraircraft. Towardstheendofthewar,theairfeldwasattacked severaltimesbyAlliedairforces(low-levelattacks
andbombardments).Within4days120haofdata weregenerated,fying8hourseachday.Thetracks wereupto700meterslong,wheretheDJIM300was fyingwith5meterpersecondat1meterabove groundlevel.Downtimestochangebatterieswere around30secondseach.
Especiallyforhistoricalandinfrastructuralsurveys, thedensecoverageofanentireareaallowstoreveal thebiggerpictureofactivities,buriedinfrastructure andlinkbetweensingleanomaliesintheground.
Thebeneftsofusingaerialapproachesare obvious.Withnocontacttotheground,thesafetyof involvedoperatorsandEODtechniciansisincreased asnobodyneedstoentertheareaofinterest.Radio connectionbetweenUAVandoperator’scontrolleris severalkilometers,whichallowstoalsosurveylarge areasfromoutside.Anotheradvantageistheprecise GPSandaclick-and-tickpre-fightplanningofthe
52 COUNTER-IEDREPORT,Spring/Summer2023
AIRBORNEMAGNETICS
120haofseamlessdata,generatedwith4daysofaerialmagneticssurveyatGanackersite.
surveyareaandfightlinesofthedrone.The operatorisnotsteeringtheUAVanymore,butonly actingasasupervisorandbackupincaseoffailure. Duringnormaloperation,theUAVcanfyvery straightandprecisetracks,havinganonboard obstacledetectionand(preferably)thetrueterrain followingmodecontributingtoincreaseeffciencyof datagenerationandfeldcoverage.Last,butnot leastistheadvantageofredundancy.Ononeside, thefailureofasinglesensorinamultisensor’s systemsismuchbetterdetectedandcompensated bytheothersensors.Withpre-plannedautomated fightsanddatacollection,asurveycanberepeated anytime.Thatallowsacomparisonbeforeandafter, whichopensthedoorformoreeffcientqualitycontrol mechanismswithinsensitiveprojectssuchasUXO andmine-clearance.
Insummary,theindustryreachedapointin technologyweretheuseofUAVswithinsensitive projectsonhazardousareasisviableintermsof achievementscomparedtothemoneytoinvest,as allusedproductsarecommerciallyavailable.The presentedairbornemagnetometersystemusing theDJIM300,theSkyHubcontrollerandthe MagDroneR4isalreadyinuseonanumberof formermilitarysitessuchasinGermanyorthe Ukraine.Withapre-planningofthesurveyarea,the UAVwillworkitswayautonomouslythroughthefeld atminimumheightsof0.5to1meter,5meterper secondfightspeed,entirelycoveringupto30 hectareswithinasingleday.InthecontextofEOD, suchasystemisdetectingshallowsmallferrous itemsuptodeeplyburiedlargebombs.Thisprovides agreatchancetointegrateaUAVbased magnetometersystemintolargeareainvestigations orfollowonqualitycontrols
Achallengesurelyremainswithnon-ferrous objects,suchasminesorIEDsaswellassurveying onhighlymineralizedsoils.Thisisduetothe natureofmagnetics.AtSENSYS,thischallengeis underinvestigationoptingforelectromagnetic sensorstobeintegratedorevencombinedwiththe Fluxgatesensorstomaximizethedetection capabilities. ■
REFERENCES
1 MilanBajić,MarkusSchikorra“Detectionofferromagnetic landmineswithaUAV-basedmagnetometer,demonstration, andverifcation”,MineActionSymposium2023
2AndreasStele1,RolandLinck,MarkusSchikorra“LargescaleUAVmagnetometryonaformerWorldWarIIairfeld atGanacker(LowerBavaria,Germany)”,DGG2022
ABOUTTHEAUTHOR
Since2016, WolfgangSuess is oneoftheManagingDirectorsat SENSYSandresponsibleforSales, MarketingandStrategicGrowth. Before,heworkedforglobal companieslikeAIRBUSIndustries andBOMBARIDERTransportation inseveralrolesinEngineering, ProductDesignandInnovation,afterhefnishedhis studyofInformationTechnologiesin2004.

AIRBORNEMAGNETICS 53 counteriedreport.com
NEXT-GENERATIONDEMININGWITHAIANDDRONES
NEXT-GENERATIONDEMININGWITHAIANDDRONES
ADVANCEDSOFTWAREALGORITHMSPOWERNEXT-GENSOLUTIONS
FORAUTOMATINGTHREATDETECTIONANDIDENTIFICATION
BySafeProAI(aSafeProGroupInc.Company)

AccordingtoLandmineandClusterMunition Monitor1, a signifcantportionoftheglobeiscontaminated bylandmines,asthisinfographicdemonstrates.The explosiveremainsofwarandlandminesbothpresent asignifcantandongoingthreattocivilians.These
weaponscanbefoundonroads,footpaths,farms, forests,deserts,borders,inandaroundhomesand schools,andotherplaceswherepeoplegoabouttheir dailylives.Theydenyaccesstofoodandwaterand hinderthedeliveryofhumanitarianaid.
1 http://www.the-monitor.org/en-gb/reports/2022/landmine-monitor-2022.aspx
Landminecontamination map2022.
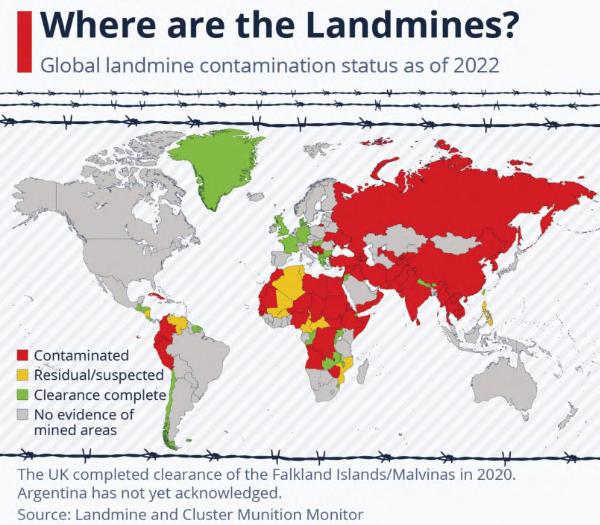
54 COUNTER-IEDREPORT,Spring/Summer2023
NEXT-GENERATIONDEMININGWITHAIANDDRONES
THENEEDFORNEXT-GENMINEDETECTION
Artifcialintelligenceanddronescanbeusefultoolsin thede-miningprocessinbothactiveconficts zonessuchasUkraineorinpost-combatareassuch asAfghanistan,Kuwait,orBosnia&Herzegovina. AccordingtorecentdatafromStatistaandthe InternationalCampaigntoBanLandmines–Cluster MunitionCoalition,thethreatofanti-personnel landmines andunexplodedordnanceispresent inover60countriesacrossAfrica,theMiddleEast, SouthAmerica,SoutheastAsia,andthroughout mainlandChinaandRussia.Theseexplosivedevices exposemillionsofcivilianstolife-threatening injuriesanddeathonadailybasis(7,000+casualties peryear).

Theglobalscopeandscaleoftheissueconfrmsthe inadequacyoftoday’smanualdeminingprocessas beingslow,labor-intensive,anddangerous.Thatis whySafeProAIbelievesthereisaclearneed forinnovativeandpracticalwaystoincreasethe effciencyandsafetyofdeminingutilizingdronesand AI/machinelearningtechnology.
SafeProAI’saward-winningartifcialintelligence (AI),machinelearning(ML)andcomputervision capabilitiesenablethe rapid,automatedprocessing ofaerialandground-based imagerymakingitan idealsolutionforanumber ofapplicationsincluding deminingandinlaw enforcementandsecurity. Thetechnologycurrentlyis beingappliedtothe identifcation,classifcation, andclearanceoflandmines. Builtwithanextensive proprietarylandmineand unexplodedordnance(UXO) dataset,SafeProAIcan rapidlydetectthreatsfrom aerialimagery,relaying preciseGPSlocationand actionablereportinginfor-
mationtodecisionmakersandgroundpersonnel,greatly increasingthescaleandeffcacyofremediationefforts. ThroughthecombinationofAI,ML,anddrone technologies,SafePro’snewdeminingsolutionsdirectly addressthelimitationsofcurrentmine/UXOclearance methodologieswhichcanbeslow,expensive,and dangerous.
SAFEPROAIDISRUPTIVEMODERNIZEDMINE DETECTION
Step1:
HighAltitudelargeareasurveywithpowerfulAI& MLfromhighresolutionaerialimageryto autonomouslylocate,label,andGPStag.
Step2:
LowaltitudedronesarmedwithGPSdatahunt minesdownandgatherhighresolution3Dlidar imagery,preciselocationtag.
Step3:
Generateanalyticalreportsfordecisionmakersto analysesafeanddangerzonesandprioritizemissions, resourcesandEODteams.
55 counteriedreport.com
SafePro’s3StepDisruptiveAIApproach. Source:SafeProAI
NEXT-GENERATIONDEMININGWITHAIANDDRONES
APPLICATIONS
Next-genminedetection
SafeProAI’ssoftwarebringsartifcialintelligence, machinelearningandcomputervisioncapabilities thatenabletherapid,automatedprocessingofaerial andground-basedimageryinreal-timetodetect landminesandunexplodedordnance.
Infrastructureinspection
Providingdetailedvisualanalysisoffacilities,power andtelecommunicationsinfrastructureandequipment throughAIandmachinelearning-enhancedvideo processing.
Securityandincidentresponse
AI-basedprocessingofaerialimageryofcanrapidly detect,locateandidentifyobjectsofintereston
thegroundincludingweapons,contraband,or improvisedexplosivedevices(IEDs).
INITIALAPPLICATION: NEXT-GENMINEDETECTION
Utilizingavarietyofoff-the-shelfconsumerand commercialdronesequippedwithanarrayofsensors includingoptical/thermalinfrared/multispectral,ourAI modelsoftwarecannowdetect50+typesofminesand UXOwithover80%accuracyincludinggrenades, projectiles,andanti-personnelmines.
SafeProAIhasdevelopedanAI-assisteddrone surveymethodthatquicklyandeasilyprovidesfeld operatorswithmapsandlocationsof80-90%ofthe presentsurface-lainlandminesandUXO,enabling themtoplansaferandmoreeffcientclearance operations.
Source:SafeProAI
56 COUNTER-IEDREPORT,Spring/Summer2023
Capabilitiesthatenabletherapid,automatedprocessingofaerialandground-basedimageryinreal-timethreatdetection.
ABOUTSAFEPROAI
SafeProAI (aSafeProGroupInc.company)was foundedin2020followingyearsofresearchintothe utilizationofdronesandAI(artifcialintelligence)to automatethedetectionoflandmines,unexploded ordnance(UXO)orimprovisedexplosivedevices (IEDs)andotherexplosivethreats.


SafeProAI’smachinelearningandvision-based processingcapabilitiesarebeingleveragedwithSafe ProGroup’sdroneoperationalexpertisetodelivera powerful‘Next-Gen’approachtosituationalawareness.
ARTIFICALINTELLIGENCE& MACHINELEARNINGTECHNOLOGY
SafeProAI’ssoftwarebringsartifcial intelligence,machinelearningand computervisioncapabilitiesthatenable therapid,automatedprocessingofaerial andground-basedimageryinreal-timeto detectthreatsincluding:
•Landmines,unexplodedordnance, improvisedexplosive devices(IEDs)
•Abilitytodetectitemsofinterest includingcontrabandorweapons
ExpandedAImodelcapabilitiesto detect50+typesofminesandUXOwith over80%accuracy:
•Anti-personnelandanti-tankmines
•Projectiles
•Clustermunitions
•Grenades
ExtensiveProprietaryLandmine& UXODataset:
•Compilingtheworld’slargestaerial imagerydatabaseofminesandUXO todetectanytypeofmunition
•EnablingAItodetectminesinvisual, thermal,andmultispectralimagery
Watchhowdronesandmachine learninghelptodetectlandmines: https://youtu.be/VBnNqBzUHdQ ■
ThisnewcapabilityisalsosynergisticwithotherSafe ProGroupportfoliosolutions,forexample,more effectivelyguidingandaidinggroundpersonnel equippedwithourstate-of-the-artballisticprotection productsincompletingtheirlife-savingsecurity missionsorinacceleratingthedrone-basedanalysisof criticalinfrastructure.Formoreinformation,pleasevisit: www.SafeProGroup.com and www.SafeProAi.com
Contact: info@safeprogroup.com
NEXT-GENERATIONDEMININGWITHAIANDDRONES 57 counteriedreport.com
Drone-BasedAISolutionforthreatdetection.
Source:SafeProAI
ThermalProcessing. Source:SafeProAI



















































































































HELD UNDER THE PATRONAGE OF HIS EXCELLENCY, PRESIDENT ABDEL FATTAH EL-SISI THE PRESIDENT OF THE ARAB REPUBLIC OF EGYPT, THE SUPREME COMMANDER OF THE EGYPTIAN ARMED FORCES 4-7 DECEMBER 2023 EGYPT INTERNATIONAL EXHIBITION CENTRE EGYPT INTERNATIONAL EXHIBITION CENTRE 4-7 DECEMBER 2023 EGYPT’S LEADING TRI-SERVICE DEFENCE EXHIBITION @visitedex /egyptdefenceexpo @egyptdefenceexpo www.egyptdefenceexpo.com Media Partner Gold Sponsor Silver Sponsor Platinum Sponsor Platinum Sponsor Platinum Sponsor Headline Sponsor O cial Carrier Organised by WORLD EVENTS Supported by Ministry of Defence Egyptian Armed Forces Ministry of Military Production National Service Projects Organisation
UNATTENDEDPACKAGES–THESECURITYOFFICER’s DILEMMA
AccordingtotheInstituteforEconomicsand Peace,GlobalTerrorismIndex2023‘Deathsfrom terrorismfellto6,701in2022,representinganineper centdecreasefromtheprioryear.Thefallindeaths wasmirroredbyareductioninthenumberofincidents, withattacksdecliningbyalmost28percentfrom 5,463in2021to3,955in2022.’
Thedownwardtrendisgoodnews.Butterrorismis andremainsascourgeandahugechallengeforlaw enforcementandsecurityprofessionalseverywhere.
Ofthetoptenmostlethalattacks,sixemployed improvisedexplosivedevices(IEDs)usedto devastatingeffect.Refectingthatexplosivesremain aprimaryweaponintheterrorist’sarsenal.
InEurope,weonlyhave EUTerrorismSituationand TrendReport(TE-SAT)1 fguresfor2021,but‘France experiencedthehighestnumberofattacks(5), followedbyGermany(3)andSweden(2).Austria, Denmark,Hungary,Belgium,andSpainreportedone attackeach.Oftheffteenattacks,fourwere completed.Mostreportedterroristattackswere categorisedasjihadistterrorism(11),ofwhichthree werecompletedattacksconductedinFrance,Spain, andGermany,andeightwerefoiledrespectivelyin France(4),Sweden(1),Hungary(1),Denmark(1)and Germany(1).Thetwofatalitiesrecordedin2021were theresultofthejihadistattacksconductedinSpain andFrance.’
‘WeaponsusedinattacksintheEUin2021included bladedweapons,vehicles(inrammingattacks)and improvisedincendiarydevices(IIDs).Disruptedplots showedtheintentandeffortstoproduceimprovised explosivedevices(IEDs).’
Thesefguresshowthatdespitethehighnumbersof successfuldisruptionsofattacksinEurope,the intentiontouseIEDsandIIDsinattackscontinuesto beaprofoundlyseriousthreat.
ItistruethatthelikelihoodofarealIEDorIIDattack remainsextremelylow,buttheveryexistenceofthe threat,nomatterhowsmall,createsotherproblems, thatofthereceiptofsuspiciouspackages,hoax bombthreatsandunattendedpackages.
Figuresforhoaxcallsandsuspiciouspackages worldwideareimpossibletofnd,sowewillhaveto relyonthe 2021UnitedStatesBombDataCenter, ExplosivesIncidentReport 2.Accordingtotheirreport therewere4,935suspicious/unattendedpackages reportedintheUSin2021and1,876reportedbomb threatincidentsinthesameyear.
Unfortunately,thereportdoesnotbreakdownwhich oftheseweresuspiciouspackagesreceivedandwhich unattendedpackages,butitissafetoassumethat mostareinthelattercategory.
Everycountrywillhaveitsownclearlydefned protocolsandproceduresformanagingabomb threatorthereceiptofsuspiciouspackages,and
UNATTENDEDPACKAGES
59 counteriedreport.com
ByVincentDeery,CEO,3DX-RayLtd
wecanprobablysumthemupinonesentence, ‘evacuatetheimmediateareaandcallthe emergencyservices.’
Butwhattodoaboutunattendedpackages?
Weallknowthatbyfarthevastmajorityof unattendedpackageswillbelittleJonnie’s/Jennie’s sweatysportskit,theverylatestinmen’sfacialcare productsorevenafullsuitofarmour(truestory).
Buteverysecurityoffcerineveryoffcebuilding, bank,shoppingcentre,concerthall,hospitalortheme parkwillatsometimeoranotherbefacedwiththe samedilemma.Dotheyescalatethediscoveryofan unattendedpackageintofullblownbombthreat incident,ordotheytakereasonablestepstoascertain whetheritreallyisathreatornot?
Thedisruptionandcostcausedbyabuilding evacuationisdiffculttoquantifybecausefguresare hardtocomebyandeverybuildinguseisdifferent.The costofevacuatingashoppingcentreforacoupleof hourscouldrunintothousands,butthecostof evacuatingacommercialbankinthecitycouldruninto tensofmillionsinlosttransactions.Thecostof evacuatingahospitalcouldinsteadbemeasuredin humansuffering!
Thatiswhythesedecisionsaresoimportant!
Thisiswherethepropertrainingandequippingof securitystaffiskey.
So,howshouldaprofessionallytrainedand equippedsecurityoffcerhandleanunattended packageorbag?
Firstly,theywillattempttogetavisualinspectionof theinsidethebagorpackagetocheckifthereare wires,circuitboards,batteries,tape,liquids,orputtylikesubstances.Arethereunusualodourssuchas accelerants,anythingthatwouldindicateadevice?
Butasmanytimesasnot,itwillsimplynotbe possibletosafelyseeinsidethebag.
Next,theywillcheckintheimmediateareaforthe owner.TheniftheareaiscoveredbyCCTVcallinto thecontrolroomandgetthemtocheckiftheowner canbeidentifedthatway.
Butallthatdone,andtheownernotfound,security staffcannotknowforsurewhetherthepackageorbag issafeunlesstheygetagoodlookinside.
Andtherereallyisonlyonewaytodothat.Andthat iswithaportablex-rayscanner.
Portablex-rayscannershavenowbeenaroundfor agoodmanyyears.
Generally,theyconsistofanx-raygenerator,afat detectorpanelandalaptop,andareinoperationwith militaryandlawenforcementEODteamsworldwide. Theyallowtheoperatortheopportunitytoseeinside thepackageorbagwithouttouchingordisturbingit.
Theyareprobablyoneofthemostaffordableand versatilepiecesofequipmentavailabletosecurity professionalsandshouldbeinthetoolkitofany securityteamresponsibleforanybuildingorfacilityof anysize.
Andaswithallgoodtechnology,thesesystemsare beingcontinuallydevelopedandthemostsignifcant developmentofrecentyearsistheintroductionof colourdifferentiatedscans,whichhavemadeitpossible todeterminethenatureofthematerialsbeingscanned. Thisisareallyimportantdevelopmentbecauseit meansthatinsteadofrelyingonshapetodeterminethe identityofanobject,thesesystemsarenowableto accuratelyidentifymaterialsbycolour.So,orange showsorganics,suchassomeexplosives,chemicals, anddrugs,aswellasmoreinnocentitemssuchas foodstuffs.Blueisformetals,suchasmanyguns, knives,handgrenades,metalpipebombsaswellas IEDcomponentssuchasthepowersources,switches, circuitcomponentsandmetallicfragmentation.Greenis forinorganicmaterialslikeblackpowdersand aluminumizedhomemadeexplosives.Greyscaleis usedforrecognitionofshapesandtheformofobjects.
Itisimportanttonotethatmostportablex-ray systemsonthemarketonlyusetwocolourscansand leaveoutthecolourblue,thisisbecauseofalackof understandingabouthowmaterialsimagingworks, whichcouldputoperatorsatasevereandpotentially dangerousdisadvantage.Accuratethreecolour differentiationisessential.Accuracynotonlyrelatesto thecorrectcolourisationofthespecifcobjectbutalso totheconsistentcolourisationacrosstheentire scannedarea.
60 COUNTER-IEDREPORT,Spring/Summer2023
UNATTENDEDPACKAGES
3DX-Rayofferacompleterangeofportablex-ray systems.
ThreatScan®-AS1(ISC)isarobustamorphous siliconportablex-rayinspectionsystem.Itcomprises, asstandard,adetectorpanelwithanimagingareaof 430mmx347mm,anewhighpenetration150kV generator,andalaptopalongwithbatteries,chargers, theuser-friendlyThreatSpectsoftware,wireless communication,andtransportcase.
Thesystemisfullyintegrated,withaprimarydisplay, computer,communications,andpowersupplies consolidatedintoasingle,waterproofruggedcase. Asecondarydisplaytabletoffershighfexibilityin deploymenttomeetthewidevarietyofuser applicationsandthreatscenarios.


Thecombinationoftechnologiesusedin ThreatScan®-AS1(ISC)offersexceptionalX-ray imagingperformance,3DX-Ray’srenownedadvanced materialsdiscrimination,andsophisticatedimage processingsoftware.

ThreatScan®-LS1sharesthesamehighquality,high penetrationimagecharacteristicsbutwithalarger 600mmx460mmimagingarea.ThreatScan®-LS1 enablestypicalbagsandpackagestobescannedin onescan.
ThreatScan®-LS3isacompactyetpowerfulx-ray scanningsystemthatcanpenetratesteelupto40mm at120kVandupto60mmat150kV.The305mmx 256mmimagingareaenablestypicalbagsand packagestobescannedinonescan.Thecomplete systemftssecurelyintoabackpack.
3DX-RayrecentlysoldsixteenunitsofThreatScan®LS3toanundisclosedsouthernEuropeansecurity agency.
So,ifyouareresponsibleforthesecurityofyour organisation,youshouldseriouslyconsidermakinga portablex-raysystempartofyourteam’sequipment toolbox.Butremember,seeingthingsinblackand whiteisnolongergoodenough! ■
REFERENCES
1 https://www.europol.europa.eu/publication-events/mainreports/european-union-terrorism-situation-and-trendreport-2022-te-sat
2 https://www.atf.gov/fle/166841/download
UNATTENDEDPACKAGES 61 counteriedreport.com
ThreatScan®-AS1(ISC)
ThreatScan®-LS1
ThreatScan®-LS3














PIRSENSORSINIEDs USINGCONSTANT POTENTIALGENERATORS
ByTeledyneICM
INTRODUCTION
ForEODteams,theuseofPIR(PassiveInfrared) sensorsinexplosivedevicescanbeamajorconcern astheyaresensitivetoX-Ray,andthencantriggera devicewhileperformingtheinspection.
TheclassicX-Raymethoduseddoesnotallowto managekVthenitbecomesverydiffculttobe undetectedbyPIR.Withthetechnologyevolving, ConstantPotentialX-Raygeneratorshaveappeared andallowtoadjustkVandmAwhilebeingabletoset thedurationofashot.Whenhavingtheparametersof
thegeneratorsettolowkVandmA,wecanremain undetectedbyPIRsensors.
Toprovethistheory,wehaveconductedastudyto determinetheoperabilityofCP(ConstantPotential) Batteryoperatedgeneratorsbelowthesensor sensitivitywhilekeepingasuffcientimagequality.
SAMPLEOFPIRSENSORS
Forthisstudy,anon-exhaustivesampleselectionof PIRsensorshasbeenused:

PASSIVEINFRAREDSENSORSINEXPLOSIVEDEVICES
63 counteriedreport.com
The4PIRsensorsappearedtohaveverysimilarresultssowewillfocusontheChacontodemonstratethefndings.
PASSIVEINFRAREDSENSORSINEXPLOSIVEDEVICES
TYPEOFGENERATORUSEDFORTHESTUDY
Features
TeledyneICMLITEX
Generatortype ConstantPotential
Beam Directional
Powersupply DewaltBattery
Outputvoltagerange 40to120kV
Tubecurrentrange 0,05to0,25mA
Tubecurrentatfulloutput 0,25mA
Weight 2,5kg/5,51lbs
Focalspot(EN12543) 0,8x0,5mm
Beamangle 50x50°
IPLevel IP54

Operatingtemperature -25to+50°C/-13to+122°F
Connections Bluetooth/Wired
MAINCHARACTERISTICS
•AdjustablekV,mAandexposuretime
•CompatibilitywithX-RayScannersandAmorphousSilicondigitaldetectors

64 COUNTER-IEDREPORT,Spring/Summer2023
TYPEOFDETECTORUSEDFORTHESTUDY
(optional)

PASSIVEINFRAREDSENSORSINEXPLOSIVEDEVICES 65 counteriedreport.com Features Unit TeledyneICM TACTX Sensortype - aSi Resolution lp/mm 4.16 Pixelsize µ/m 120 Dynamicrange(Greylevels) bits 16 Activearea mm/ indiag. 246x307/ 10x12 Maximumpenetration mm/ inofsteel 35/ 1.3 (withCP120B) mm/ inofsteel 45/ 1.7 (withCP160B) Numberofcoveredsides – 3(left,bottom,right) Deadzone mm/ in 4.6/ 0.15 (frombottom) 15/ 0.59 (fromside) Externaldimensions mm/ in 327.3x285.6x18.65/ 12.87x15.15x0.7 Weight Kg/ lbs ~2.9 / 6.39 Operatingtemperature °C/ °F -20to+50/ -4to+122 Storagetemperature °C/ °F -20to+65/ -4to+149 Communicationprotocols –Bluetooth/Wiforcabledriven
Workwith –
ImagingStation –Notebook,toughbook, Tablet,toughpad
CP120B/CP160B/LiteX X-raygenerators
SENSITIVITYTESTS
Target:identifyingtriggeringlimitversusoperatingconditionsbasedonkVandmA,distanceandduration.
a.Effectonduration
Testconditions:
•PIRSensor:Chacon
•120kV,0.25mA(Fullpower)
Conclusion:
WhileshootingatfullpoweroftheLiteXgenerator,thePIRsensortriggersimmediatelywhenx-rayed,theduration hasnoeffectevenat1second.
b.EffectofkV–mAadjustment
Conclusion:
ThekVandmAadjustmentcapabilitiesoftheLiteXCPgeneratormakeitpossibletoreducethedistance.
Testconditions: •PIRSensor:Chacon kV mA Triggeringlimitbetween…cm and…cm 120 0.1 110 120 120 0.2 220 240 100 0.1 100 110 100 0.2 180 200 80 0.1 70 80 80 0.2 140 160 Duration(s) Triggeringlimitbetween…cm/in and…cm/in 1 220/86,6” 240/94,5” 2 220/86,6” 240/94,5” 10 220/86,6” 240/94,5” 60 220/86,6” 240/94,5” PASSIVEINFRAREDSENSORSINEXPLOSIVEDEVICES 66 COUNTER-IEDREPORT,Spring/Summer2023
IMAGEQUALITY
Nowthequestionis,canwegetagoodqualityimagewhilenottriggeringthePIRsensor?



a.ImagequalityusingTactX withLiteX
b.Correctedimagequality usingTactXwithLiteX
c.Correctedimagequalityusing TactXwithLiteX–SNRValue
Parameters:
kV 80kV mA 0.1mA Distance 80cm Time 60”
d.Processedimagequalityusing TactXwithLiteX
Parameters: kV 80kV mA 0.1mA Distance 80cm Time 60”
CONCLUSION
Parameters: kV 80kV mA 0.1mA Distance 80cm Time 60”
SNRValue: 190
ConstantpotentialgeneratorscanoperatebelowPIR triggeringlimitwhilehavingagoodaveragefuxandan excellentimagequalitybecause:
•Signaliscontinuous
•Focalspotissmaller
•kVandmAareadjustable
•Timeisadjustable
So,whenPIRsystemsareused,thebestwaytonot triggerthemistodecreasekVandmAbutincrease exposuretime.Thiswillofferagreatimagequalitywhile remainingundetectable. ■
ABOUTTELEDYNEICM
Parameters: kV 80kV mA 0.1mA Distance 80cm Time 60”
TeledyneICM hasover25yearsofexpertiseindeveloping innovativeportableradiographysolutions.Itsportable generatorshaveexcellenttechnicalcapabilitiesandwhen coupledwithhigh-resolutiondetectors,providehighly accurateradiographs.Contact: icm.sales@teledyne.com
PASSIVEINFRAREDSENSORSINEXPLOSIVEDEVICES 67 counteriedreport.com
INDIA – THEIEDCHALLENGES
INTRODUCTION
AccordingtotheIndianNationalBombDataCentre, duringtheYear2021,therewerearound132reported ImprovisedExplosiveDevices(IED)blastsinIndia killing/severelyinjuring323people.Itisgenerally estimatedthatonanaverageforeveryreportedIED attempttherewereabouteightunreportedattempts, successfullyfoiledbythesecurityforcesbasedon timelyactionableintelligence.IEDshavebeenthe weaponofchoiceforinsurgents,terroristsandmilitant groupsoperatingacrossIndia’sverybroadlandscape. EventhoughtheinternalsecuritysituationinIndiahas vastlyimprovedoverthelasttwodecades,the appearanceofnewmilitantandterroristgroupsinthe arena,theinnovativetechnologiesadoptedbythese groupsinbuildingavarietyofIEDsanduseofnew mediaincludingdronesfordeliveryoftheseIEDs,pose newandvariedchallengestothesecurityforces.Is Indiafullypreparedtomeetthesechallengestokeep itspeopleandinfrastructuresecureinordertodrive development?
THREATANALYSIS
TheIEDthreatstoIndiaemanatefromtheongoing insurgencies,separatistandterroristactivitiesover somepartsofthecountry.TheUnionTerritoryof JammuandKashmir(UTJ&K)wasontheboiloverthe lastthreedecadesduetohostileactivitiesof separatists,terroristsandmilitantsinfltratingfrom
acrosstheborder.ThesituationinUTJ&Khasnow beencontrolledthroughwell-coordinatedand persistentoperationsbythesecurityforces.Theleftwingextremists’(LWE/Maoists)insurgencywhich initiallyaffected160districtsinCentralIndia–popularlyknownasthe‘RedCorridor’hasnowbeen containedandislimitedtojustabout50districts.The decadesoldseparatistinsurgenciesinNorth-East India,especiallyinthestatesofAssam,Nagaland, MizoramandManipur,havebeeneffectivelycontained throughmassivesocio–economicdevelopment, improvedroad,railandairconnectivitytotheseremote areasandstrengtheningofdemocraticinstitutions throughfairandfreeelections.Also,anumberof religiousradicalisedextremistandfundamentalist organisationshaveresortedtoterrorthroughtheuse ofIEDsinurbanandsemi-urbanareaspropounding theirmisplacedcauses.RapidlydevelopingIndiafaces bigthreatstoitsinternalsecurityfromallthese elementsthatuseIEDsasaprimarymeansof terrorisingpeople,causingdestructiontopublic propertiesanddisruptingdevelopmentalactivities. Thesehostileelementsapplygreatingenuityand intelligence,andleveragetechnologiestodesigna varietyofsophisticatedIEDsandtheirdelivery mechanisms.TheyfrequentlyadoptnewTactics TechniquesandProcedures(TTPs)thereby unbalancingthesecurityforces,andextensivelyuse
INDIA–THEIEDCHALLENGES
68 COUNTER-IEDREPORT,Spring/Summer2023
ByColonelHRNaiduGade–IndianArmyVeteran
realtimehumanintelligenceinordertothwartand frustrateanyCounter-IEDoperationsundertakenby thesecurityforces.

ThecomplexityoftheIEDSystemsisincreased sincemobilesmartphones,internetandsocialmedia
providealow-costandeasilyaccessiblemediumfor informationsharingandtheswiftadoptionofTactics, TechniquesandProcedures(TTPs),thereby facilitatingtheeffcientoperationofthesediverse systems.Suchsystemscanbeextremelyresilient,
INDIA–THEIEDCHALLENGES 69 counteriedreport.com
IEDIncidents2021India. Source:BombShell,NSG,India
INDIA–THEIEDCHALLENGES

invariablyhardtotargetandare,therefore,survivable. BecausetheIEDthreatisconstantlychanging,the Counter-IEDfghtisdynamic,andmaintaining effectivenessremainsanenduringrequirementfor operationsdevelopment.TocounterthesefastchangingTTPsbyhostileelements,thesecurityforces havealsotoinnovatethroughadoptionofnew technologiesincludingArtifcialIntelligence.
NATIONALCOUNTER-IEDSTRATEGY
Presently,Indiadoesnothaveanycomprehensive NationalCounterIEDStrategyencompassingthefour pillarsofCounter-IEDoperationsi.e.,Attackthe Networks,PreparetheForce,DefeattheDeviceand ExploittheIncidence.Thestrategyshouldhaveapan governmentapproach,beacoordinatedeffortofall applicableagenciesofnationalpower,havecommon understandingofthestrategicenvironmentwith respecttoIEDchallenges,andbuildenduring capabilities.DespiteenhancedIEDsthreatslooming
large,IndiahasnotyetevolvedCounter-IEDstrategy atanylevelofsecurityestablishmentsandgovernance. TheIndianArmyenunciatedbroadstandard proceduresandprocessestoCounter-IEDthreats mostlyrelatedtoCounterInsurgencyOperations (COIN).TheCentralPoliceForceshaveoverthe decadeevolvedstandardoperatingprocedures(SOPs) forCounter-IEDoperationsapplicabletovarious terrainstheypresentlyoperatein.However,thepolice forcesofmostofthestateshaveyettoevolveany standardCounter-IEDproceduresandstilloperatein anadhocway.EvenifacomprehensiveCounter-IED strategyisfnallyenunciatedbythecentral government,theimplementationoftheabove strategiesandproceduresbecomesverydiffcultina federalstructureofgovernanceasinIndia,which requirescoordinationandsynergybetweenmultiple agenciesatvariouslevels.Nevertheless,Indiahas madegoodprogressinthisregardoverthelast twodecades.
70 COUNTER-IEDREPORT,Spring/Summer2023
IEDs-AGlobalProblem. Source:AOAV,UK
TheIEDChallenges. Source:InertProductsLLC
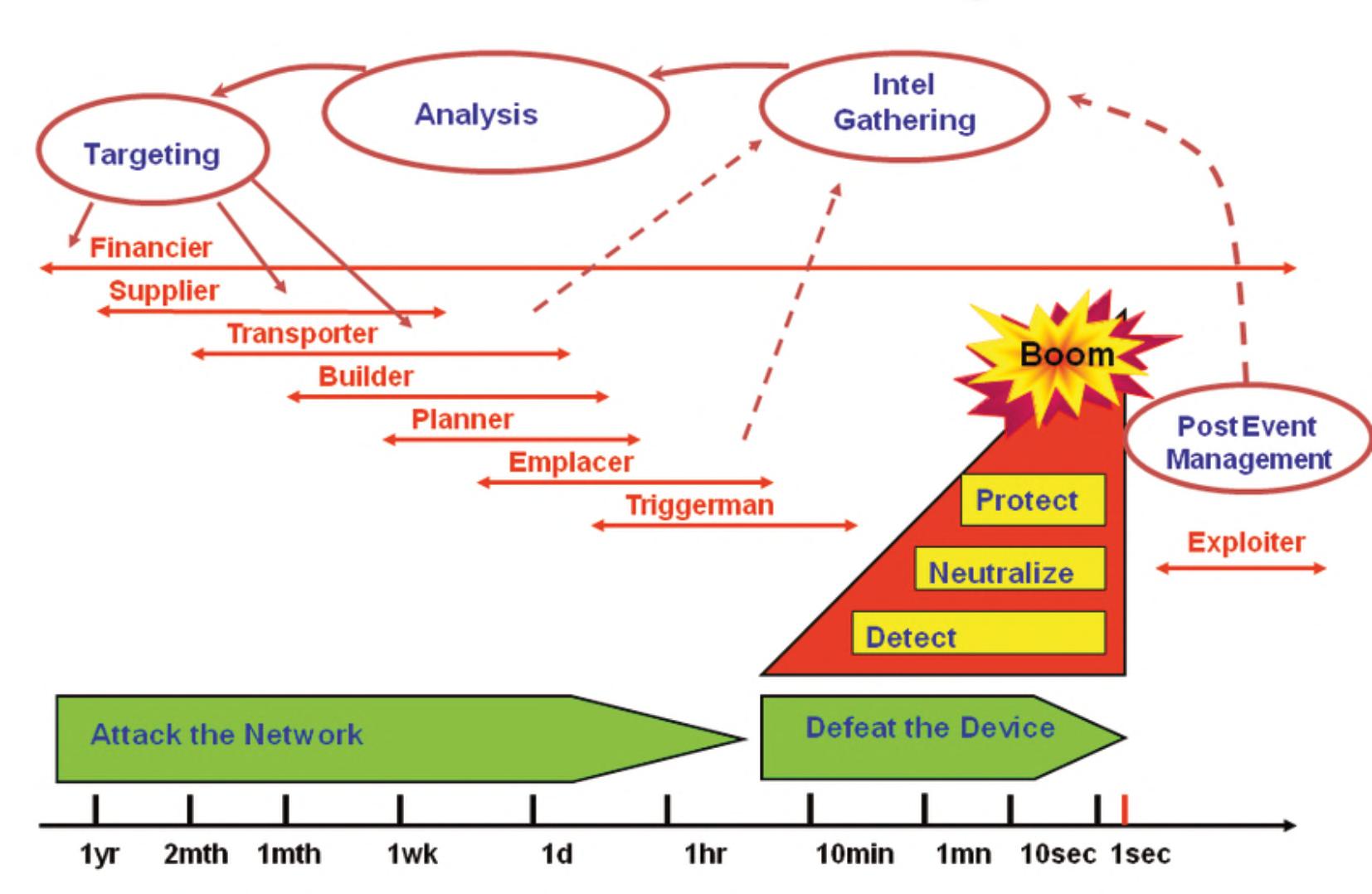
ThreatsLoomingLarge. Source:www.zeenews.india.com

INDIA–THEIEDCHALLENGES 71 counteriedreport.com
COUNTER-IEDCAPACITYBUILDING
TheCounter-IEDcapacitybuildinginvolves-creating suitableorganisations;developingrequisitetraining andtraininginfrastructure;adoptinginnovativeTTPs basedonthreats;providingorganisationswithsuitable equipmentthroughleveragingoftechnology; establishingeffcientandeffectiveintelligence apparatusandbuildingaseamlessandwidenetwork forintelligencegatheringandtimelydissemination; regulatingandmonitoringsupplyofmaterialsrequired fordesigningandbuildingtheIEDs;identifyingand eliminationofsourcesofterrorfnance;creatingan adequatefrstrespondermechanism;settingup multiagencycoordinationcentresatalllevelswith effcientcommunicationnetworkslinkingthese centres;andundertakinglargescalepublicoutreach programmestoeducatethegeneralpopulationonthe Do’sandDon’tsaimedtominimisecasualtieson occurrenceofanIEDevent.Thecapacitybuildingwill havetobebasedontherealisticthreatanalysis.
INDIA’SCOUNTER-IEDCAPACITY
Organisations–TheIndianArmyhas specialcounterinsurgencyunits operatingintheUTJ&Kandthe North-East.Theseunitshave inherentCounter-IEDresourcesand capabilities.Additionally,special CounterExplosiveDevicesUnits (CEDU)arefunctionalwitheachofthe OperationalCommands.These CEDUshavebeenrestructuredand equippedforgreaterfexibilityintheir deploymentintosmallerteams.All armyfeldformationshaveintegral combatengineerunitstrainedand equippedforCounter-IEDsupport.The NationalSecurityGuard(NSG),a highlyspecialisedcontingencyforce primarilyconsistingofarmyunits–is deployedatvariousgeographicalhubs torespondtocounter-terrorand counter-hijackingthreats.TheBorder GuardingForcesallalongthe15060 kmsofinternationallandbordersfoil anycross-borderattemptsbymilitantsandterrorists. TheyhaveCounter-IEDteamslocatedattheBorder Outposts(BOPs)inthethreatenedsectorstotakecare ofanypossibleIEDincidents.TheCentralReserve PoliceForcecarryingouttheCOINoperationsinthe ‘Redcorridor’,UTJ&KandtheNorth-Easthaswell trainedsub-unitstohandleIEDs.TheCentralIndustrial SecurityForce(CISF)isdeployedalloverIndiato protectnationalstrategicassetsandcritical infrastructurefromhostileelements.TheRailway ProtectionForce(RPF)isdeployedtoprotectthe world’sthirdlargestrailwaynetworkof67,000kmsand associatedinfrastructure.AllthestatesinIndiahave dedicatedbombsquads/teamsaspartofthecrime investigationdepartmentsoftheirpoliceforces.These bombsquadsaretrainedbytheIndianArmy/NSG/ CRPFandarereasonablywellequippedforcarryingout Counter-IEDoperations.However,theseresourcesare limitedandcannotbedeployedinatimelymannerall overaparticularstate.Theirreachislimitedmostlyto
INDIA–THEIEDCHALLENGES 72 COUNTER-IEDREPORT,Spring/Summer2023
PillarsofCounter-IEDStrategy. Source:JIEDDO,USA
DronewithExplosivePayload. Source:MHA,India


urbanareas.TheCivilDefenceandHomeGuardunits ineachofthestatespossessbasicawarenessofIEDs andsupplementtheeffortsofthesecurityforceswhere required.
Training-isacontinuousprocessforhoningand updatingCounter-IEDskills.Manydecadesago,the
Indianarmyestablisheda centreofexcellence–the EDDSchoolaspartof theCollegeofMilitary Engineering.TheEDD Schooltrainshundredsof personnelbelongingto theIndianandforeign armedforcesandthe centralandstatepolice forces.TheIndianarmy’s feldformationsrunbattle schoolsatthefeld formationlevelstotrain andupdatepersonnelin Counter-IEDskillsand tasks.TheCRPFestablishedanInstituteforIED managementtotrainpersonnelfromthecentralpolice forcesandstatepolice.Likewise,theBorderForcerun similarinstitutestotrainitspersonnelonCounter-IED tasks.Inaddition,mostsecurityforcessubscribeto varioustrainingcoursesabroadforselectedpersonnel
INDIA–THEIEDCHALLENGES 73 counteriedreport.com
ConfdenceBuildingTraining. Source:InertProductsLLC


INDIA–THEIEDCHALLENGES 74 COUNTER-IEDREPORT,Spring/Summer2023
EDDSchool-CollegeofMilitaryEngineering. Source:IndianArmy
MultiagencyCoordinationCentre. Source:MHA,India
inCounter-IEDtasks,proceduresandgivethem exposuretothelatesttechnologiesandprocedures availablearoundtheglobe.Eachofthesecurityforces havetheirowncaninetrainingestablishmentsforthe trainingofnewandrefresherfortheexistingcanines.
Equipment&Technology-TheIndiansecurityforces andotherspecialistCounter-IEDunitsareadoptingthe latesttechnologiesavailableglobally,whichnotonlyact asforcemultipliers,butalsoreducetherisktomanual operatorscounteringexplosivedevices.Thephilosophy andprocessof‘defeatingthedevice’hasundergonea radicalchange.High-techequipmentliketheunmanned aerialvehicles,unmannedgroundvehicles,remotely operatedvehicles,disrupters,robots,non-destructive evaluationequipment,controlleddetonationchambers/ vehicles,RCIEDjammers,GPRs,anddetectionand neutralisingequipmentarebeingdeployedonalarger scalebythesecurityforces.Requisitefundsare earmarkedtoprocurethesetechnologiesand equipmentfrombothindigenousandforeign sources.TheDefenceResearchandDevelopment Organisations(DRDO)havebeenworkingonalarge numberofprojectstodeveloptechnologiesforaerial surveillance,reconnaissance,andsafeandeffcient handlingofexplosivedevices.Theprivateindustryis beingactivelyinvolvedandpartneredtodevelopthese technologiesforthesecurityforces.Asubstantial quantityofhigh-techCounter-IEDequipmenthasbeen inductedinrecenttimesintothesecurityforces.

CONCLUSION
Asevidentfromtheabove,Indiaisslowlybutsteadily buildingcapacitiesintermsoforganisations,training, equipment,technologiesandintelligencegatheringto undertakealargenumberofCounter-IEDoperations simultaneouslyovervaryingterrainsandenvironments. However,therearestillcertaingreyareastobe addressedonapriority.Theserelatetotheaspectsof evolvingacommonnationalstrategy,closerattention totheissueof‘attackingthenetworks’,and coordinationamongstthenumeroussecurityforces. TheIndiansecurityforcesarefullygeareduptotakeup anychallengestoitsinternalsecurityarisingfromthe useofexplosives. ■
ABOUTTHEAUTHOR
ColonelHRNaiduGade -IndianArmyVeteran [BE(Civil),MSc(DefenceStudies),MBA(HR)]
CommissionedintotheCorpsofCombatEngineers. ACivilEngineer,andSecurityProfessional,with47 yearsofrichexperienceinthefeldofCombat Engineering,Chemical,Biological,Radiological, NuclearandExplosives(CBRNe)Defence,Security& DisasterManagementandCounter-IEDOperations.Is aqualifedCBRNandCounter-IEDProfessional.
IsaformerMemberoftheInternationalCivilService whileworkingasChiefCWInspector1997-2004with the‘OrganisationforProhibitionofChemicalWeapons (OPCW)’,TheNetherlands,winneroftheNobelPeace Prize2013.Ledteamsofinternationalprofessionalson manyverifcationmissionstovariousmember countries,toverifytheinventoryofChemicalWeapons andmonitortheirdestruction.
Presently,ChiefConsultantwith‘CBRNeSecure India’a‘forumandaknowledgecentre’forbringing awarenessinthegeneralpublic,governmentand securityentitiesonthethreatsarisingfromtheuseof CBRNematerialandtheirdisastrousconsequences. Aprolifcwriterandspeaker,participatedinvarious internationalanddomesticconferencesonCBRN Security,DisasterManagementandCounterExplosive Issuesandwritesarticlesforprofessionaljournals worldwideonthesesubjects.
INDIA–THEIEDCHALLENGES 75 counteriedreport.com
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISM INUKRAINIANLANDS
Afterthepro-RussianprotestsinDonetskand
LuhanskoblastsinMarch2014,armed separatistsdeclaredboththeDonetskandLuhansk People’sRepublics(DPRandLPR)asindependent statesfromUkraine.
FromJune2014,andinparallelwithsomeYouTube and www.mojevideo.sk publishers,acurrentlybanned channel(www.vk.com/isodal)inRussianVKontakte socialmediastartedreleasingvideosmixingproRussianseparatistforcesincombatalongwithDaesh combatantsinSyriaandNorthCaucasianfghtersin theRussianFederation.Allthosevideoshave soundtracksbasedonIslamicNasheedandTakbirs.
Almostsimultaneously,anotherVKontakteaccount (www.vk.com/isdl_jihad)createdimaginaryfags combiningthosefromDonetskandLuhanskwith jihadistsymbolism.

Atafrstglance,itlookslikethepersonsbehind thatgraphicdarkhumorinitiativearepro-separatist supporters,whoarealsocollectingmoneyfrom donationstosupporttheindependenceofDonbass:it isalldesignedindirectimitationofDaeshinfuence activitiesthroughtheworldwideweb…
From2022,theRussiangovernmenthasbeen promotinganinfuencecampaigntomitigatethe tensionsbetweenChristianandMuslimsoldiersin Russianforces,allindirectbeneftofattractingMuslim Russianstorecruitment.
Inparallel,andfromMay2022,theconfictinthe disputedDonbass(thehistoricalareawhichis currentlyunderstoodasmainlycomprisingDonetsk andLuhansk)haswitnessedsomesortoffreak propagandaandmotivationcampaignunderthe genericnameof “ImaratDonbass”
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
76 COUNTER-IEDREPORT,Spring/Summer2023
“Imaginethere'snocountries.Itisn'thardtodoNothingtokillordiefor.Andnoreligiontoo...” (JohnLennoninhissong"Imagine"frstrecordedandreleasedin1971)
Figure1:Imagesandcapturesfromvideosfrom“IslamicStateofDonbassandLugant”. (Sources–VKontakte&Youtube).
ByLieutenantColonelJoseMRufas,ChiefofAttacktheNetworksBranch, C-IEDCentreofExcellence
Theirfrstvideowasentitledas “Returnofthe RussianCaliphate” andstatingthat“alllandsbelongto Allah”,amongothermessagestryingtoshowthat RussiaisanallyofIslam.
Thevideosandmerchandisingfrom “Imarat Donbass” werewidelypromotedbytheassassinated RussianbloggerMaximFomin(AKAVladlenTatarsky), whowasevenfeaturinginsomeoftheproducedvideos.
Oneofthemainvectorsfordiffusionof “Imarat Donbass” productshasbeentheTelegramchannel “TVJIHAD” (www.t.me/tvjihad),whichposesan inconsistentcombinationofsarcasticproductions,proRussianpropaganda,andsomepiecesofrealistic jihadistcontentfromNorthCaucasussources.

ThepresenceofMuslimcombatantsfghtingforboth theRussianorUkrainianforceswascausingahuge debateabouthowtheMuslimcommunityshould considerthem.AdamShakhidov,oneadvisertothe ChechenpresidentKadyrov,statedthatthoseMuslims takingpartintheRussian“SpecialOperationin Ukraine”areMujahideenservinginthewayofAllah, andthosekilledonthispathbecomemartyrs (Shaheeds).
ButthefactthatMuslimfghtersarecontributingto bothsidesoftheconfict,thedebatecontinueswhen consideringwhoarereallyfollowingthepathofAllah, andwhoaremeredisbelievers:
•AbuHamza,AmiroftheMujahideen-Muhajirsofthe WilayatNokhchichoyofImaratKavkaz(Caucasus Emirate),commentedthatthepro-Russianfghters fromtheChechenRepublicarefghtingforVladimir PutinandnotinthepathofAllah.
•DaysaftertheRussianinvasionofUkraine,the
CrimeanTatarfghterIsaAkayev(commanderof thevolunteerbattalion“Crimea”)appealedtothe RussianMuslimsand“fellowbelievers”whoare fghtinginUkraineto“throwdowntheirweaponsor jointheUkrainianArmedForcesinthefghtagainst Russia”.
•SimilarmessageswerespreadbytheChechen volunteerfghtinggroupsontheUkrainianside (e.g.DzhokharDudayevBattalionandShaykh MansurBattalion).
•Inanswertothat,leadersofMuslimRussian religiousorganizationsappealedfortheirsupport oftheleadershipofRussia,justconsideringthe RussianspecialoperationinUkrainetoseekfor peaceasaforceddefensiveandpreventive measuretoprotectRussiaandallitscitizensfrom therealthreatofnuclearandbiologicalweapons byNATOandEurope.
“#NafrforUkraine”:Muslimreactionstothe Russo-Ukrainianconfictin2014
Thehashtag “#NafrforUkraine” wasoftenusedinTwitter inMarch2014:theoriginalmeaningof “nafr” (نفير) wasthe "calltowar",soitshouldbeunderstoodasthe calltojihadielementsforactiontotraveltothereferred countryandtakepartintheholywarinthenameof Allah:itwaspreviouslymadewithSyriaandEgypt.
InadditiontothepastextraditionfromCrimeato CentralAsiaandtheprosecutionofTatarsbyRussia, thereferendumforannexationofCrimeatothe RussianFederationin2014madeseveralregional andinternationalSalaf-jihadistorganizations(e.g. AlQaeda)totakeuptheTatarcause.
77 counteriedreport.com
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
Figure2:Capturesfromthevideo“ReturnoftheRussianCaliphate”under“ImaratDonbass”brand. (Source–Twitter)
OneofthemostpopularTatarorganizationsis Hizb-ut-Tahrir,whichadvocatesaglobalIslamic Caliphate,andithasbeenconsideredbytheRussian Federationasaterroristorganization.
WithregardtoTatarunitsfghtingontheUkrainian sidebeforetheRussianinvasion,wecouldfnd:
•TheNomanÇelebicihanTaburuBattalion,created byLenurIslamov(ex-DeputyPrimeMinisterof Crimea)in2016andcomposedofTurkic/Crimeans alongwithotherMuslimvolunteers.
•TheDevletGirayYedekTaqimigroup,as composedofTatarsandUzbeks.
•SomeotherTatargroupsarealsosaidtobepartof the“RightSector”units.
InthecaseofChechenunits:
•ChechenRepublic’sPresidentKadyrovis supportingRussiawithpartofhisarmedforces.
•TheDeath(Смерть)battalionisfghtingalongwith DonetskPeople´sRepublic(DPR)separatists.
•TheDzhokharDudayevBattalion,ascomposed ofChechens,Azerbaijanis,Georgiansand Ingushetia’smembers.
•TheSheikhMansurbattalion,whichseemstobe morereligiouslymotivatedandradicalized.
OntheUkrainianside,manyChechenfghterswere youngfundamentalistscomingfromthe“Caucasus Emirate”,whosefghterswerecombatinginSyriaand IraqalongwithDaeshcombatants.Infact,mostofthe formermembersoftheCaucasusEmiratewerefurther
embracingtheWilayahal-Qawqaz,sotheDaesh brandinNorthCaucasus(theyissuedacallfor potentialmilitantsinRussiaandCaucasianrepublics tojointhegroupandfghtagainstRussianforces ratherthanjoiningDaeshinSyria.).

“Obportumvenies” 1,Jihadismandthe2022
RussianaggressionagainstUkraine
Foryears,Ukrainehasbeenatransitpointontheway toandfromSyria.Infact,theSecurityServiceof Ukraine(SBU)hasdisruptedseveralofthose operations.InJuly2020,itwasjudgedanAzerbaijani networkwastransportingDaeshmilitantsfromthe NorthandSouthCaucasusandCentralAsian countriesviaUkrainetoTurkey,andfromtheretoSyria andIraq.AstheintensifcationofjihadistsinSyriawas confuentwiththewarinDonbas,soUkrainepaidlittle attentiontothemilitantswhowerepassingthrough itsterritory.
Althoughmostoftheroutesforforeignfghtersgoing toSyriawereblocked,Ukraineremainsmoreorless opentothemtoday(e.g.legallyorusingfake passportsthroughanairplaneorillegallybyferry throughtheBlackSea).Ifamilitantisnotincludedin theInterpoldatabase,hecaneasilyenterUkraine inprinciple.
Themostcommonapproachfromradicaljihadism supporterstotheconfictbetweenUkrainian government,Ukrainianseparatists,andRussiawasto celebrateawarinwhichtwocrusadercountrieswere killingeachother.
78 COUNTER-IEDREPORT,Spring/Summer2023
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
Figure3:Picturesofmembersof“CaucasusEmirate”&“QawqazWilayah”. (Source–www.longwarjournal.org&Twitter)
1(FromLatinlanguage)Literallymeaning"comingtowardaport",itrefersto“opportunity”.
Justbasedonreligiousjustifcations,clericsin UkraineandChechnyaencouragedMuslimsto participateinthemilitarycampaignonbehalfof UkraineandRussia:
•InChechnya,themuftiSalakhMezhievasked MuslimfghterstotakepartintheRussianspecial operationinUkraineanddeclareditasa“jihad.”
•InUkraine,themuftiSaidIsmagilov(highest Muslimreligiousauthorityinthecountry)stated thatMuslimswilldefendUkrainewithmorethan justprayers,andthenissuedafatwaurging MuslimstodefendUkraine.
•AyderRustemov,themuftioftheBlackSea peninsulaofCrimea,urgedUkrainianMuslimsto
defendthehomeland,andurgedRussianMuslims nottocontributetotheRussianaggression.
•AbuHamza,Amirofthe“Mujahideen-Muhajirsof theWilayatNokhchichoyofImaratKavkaz”(so CaucasusEmirate)hasstatedthattheChechen troopsofKadyrovcannotbeconsidered“real Chechens”duetotheirsupporttoRussia.
•TheCrimeanTatarfghterIsaAkayevappealedto theRussianMuslimswhoarefghtinginUkraineto throwdowntheirweaponsorjointheUkrainian ArmedForcesinthefghtagainstRussia.
AlthoughAlQaedawasnotmakingoffcial statements,severalsourcesofpropaganda(e.g.


79 counteriedreport.com
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
Figure4:RadicaljihadistpropagandareferredtoRusso-Ukrainianconfict. (Source–Twitter,AnNaba,WolvesofManhattan)
Figure5:InformationrecommendingDaeshfollowerstouseexplosive-ladendronesforJihad. (Source–www.archive.org)
“WolvesofManhattan” magazine)sawtheUkrainian confictasanopportunityfortheirfghterstoexploitthe Ukrainianwar,theopenborders,thepotentialtraining andcreationofcells,andtheaccesstoweapons…all ofitindirectbenefttoextendtheglobaljihadover Europeanterritory.
Ontheotherhand,Daeshcondemnedthe participationofChechenfghtersinsupporttoRussia andurgedMuslimstostayawayfromthiskindofwar madeby“crusaders”and“infdels”.
Infact,theUkrainianconfictiscallingtheattention ofDaeshfollowers,asitisevidencedbythecontinuous referencestohowthecurrentevolutionofimprovised explosivedevices’tactics,techniques,andprocedures inUkrainecouldsupporttheirobjectives.
NotonlyspecifcJihadistpropaganda,butseveral otherwebsitessuchas “Kavkazcenter” and “Checheninfo” havebeenindirectlysupportingtheideaoftheJihad againstRussiaandtherelevanceoftheUkrainianconfict initsdevelopment.
TheUkrainianconfictisstillcallingtheattentionto minoritiesandMuslimcommunitiesintheex-Soviet republicstocombatRussia:asanexample,wecould takealookatthefoundationoftheTurkicbattalion
“Turan”inUkraineinlate2022,whichcurrently comprisesAzerbaijani,Kazakh,Kyrgyz,Buryat, Dagestani,Uzbek,andAltaifghters.
LastFebruary,aCaucasianMuslimvolunteer combatunitformedin2022,MuslimCorps“Caucasus” (MKKavkaz),releasedthevideo “Musul’manskij korpus“Kavkaz”zashhishhaetUkrainuUAotorkov
rashistovvBahmute…!” (MuslimCorpsCaucasus defendsUkrainefromtheracistforcesinBakhmut) showingitsmilitantsfghtinginBakhmut,Ukraine. Russiansourcesindicatethegrouptobecomposedof Azerbaijani,Dagestani,Chechen,andTurkishfghters.
Firstindicatorsonradicalizationorjust unmaskedrealobjectives…
Duringlastmonths,theChechenShaikhMansur battalion(currentlyfghtingontheUkrainianside)has beenshowingaslightlydifferentapproachto improvisedexplosivedevices’tactics,techniquesand proceduresthroughsocialmedia,asfollows:
•PreparationanduseofvehicleborneIEDs
•UseofpersonborneIEDsasindividualtactical equipment
Thatspecifcuseofsuicidetacticsisbasedona coupleofexplosive-ladenmagazineholsters connectedtotheplatecarrier:thosedevicesare composedofTrinitrotoluene(TNT)blocks,detonating cord,andaUZGRMfuzeforahandgrenadewhichhas beenmostprobablymanipulatedthroughremovingits timedelaycomponenttoallowinstantdetonation.
Thatinitiativecouldmovetosomepotential consequences:
•Increaseinideologicalradicalizationbythe componentsofthereferredunit.
•BadimageforUkrainianforces,whichcouldbe exploitedbyRussiaasUkraineconnectionto terrorism…

80 COUNTER-IEDREPORT,Spring/Summer2023
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
Figure6:PersonborneIEDsusedbyShaikhMansurbattalionmembersinUkraine. (Source–Twitter&SkyNews)
SinceOctober2022,militantsfromAjnadal-Kavkaz (أجنادالقوقاز,“SoldiersoftheCaucasus”)arefghting inUkraine.ItisaChechen-ledJihadistIslamic fundamentalistrebelgroupwhichhasbeenfghtingin northernSyria.Theyareactingincoordinationwith ShaikhMansurbattalion,andtheleaderofAjnadalKavkaz(RustamAzhiev,“AbdulHakimal-Shishani”)was appointedbytheleaderoftheChechenRepublicof Ichkeria'sgovernment-in-exile,AkhmedZakayev,as deputycommanderoftheChechenforcesoperating alongsidetheArmedForcesofUkraine.
TheconfuenceofthedecisionbytheUkrainian governmentaboutfacilitatingtheintegrationof ChechenfghtersfromChechnyaandSyriawiththe changeoffocusbyseveralChechengroupsregarding UkraineasabetterwayoffghtingRussiathaninSyria couldinciteotherJihadistgroupstoarriveinUkraine.
2023transnationalvisionfromDaeshinKhurasan Wilayat
FromJanuary2022,DaeshinKhurasanWilayat(ISKP)propagandameanshavebeenevolvingfrom publicationsandmaterialsintheoriginalPashto language(alsoDariandArabicones),intotheuseof Englishintheaimofaworldwideaudience.During 2022,theapproachhasmovedtotranslationsinto Urdu(PakistanandsomezonesofIndia),Uzbek (UzbekistanandminoritiesinAfghanistan,China,and otherformerSovietrepublics),Tajik(Tajikistan, Afghanistan),Hindi(India,Nepal…),Malayalam (KeralaregioninIndia),andeveninUyghur.
OnFebruary4th,2023,the21stissueoftheEnglish languageversionof“VOICEOFKHURASAN”was showingchangesindesign,makingthemagazine morevisualandmodernized.Additionally,itincluded implicitdirectionandguidanceonattacksinrevenge for2023Quranburningsaswellasexplicitreferences topastattacksinWesternterritories.
OnFebruary19th,2023,waspublishedthe22nd issueof“VOICEOFKHURASAN”,whichisbreaking theusualmonthlyreleaseofthemagazineand publishingiteachffteendaysforfrsttime.The evolutionofthepotentialthreattoEuropeandNorth Americainsidethepublicationismainlybasedonthe inclusionofrecommendationsfortargets,tactics, techniquesandproceduresregardingtheconductof attacksinWesterncountries,alongwithmore aggressiveimagespromotingarmedactions.
Inadditiontothat,Al-AzaimFoundationcontinues publishing(andredistributing)aparallelmagazine intheArabiclanguage(صوتخراسان,“Voiceof Khurasan”),whichincludesdifferentarticlesand targetsdifferentaudiences.
Ontheotherhand,theidentifeddynamics regardingpropagandabyDaeshinKhurasanare takingplaceinparallelwithahighincreasein messagesrecommendingviolentattacksagainst Europebyothermediaagenciesandforumsrelatedto Daesh,alongwiththeproductionofnewvideos, redistributionofoldones(translatedandsubtitledinto English,Spanish,French…)dealingwithterrorist actionsinEuropeandNorthAmericainthepast,and

81 counteriedreport.com
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS
Figure7:PagesfromVOICEOFKHURASAN#21and#22. (Source:www.archive.org)
callingforreactionsagainsttheQuranburningsand otherestimatedaggressionsbyChristiancountries toIslam.
WhataboutUkraineasapotentialgatefor terrorisminEuropeanterritory?
DaeshinKhurasanWilayatiscurrentlystrengthening linksandinfuencewithothergroupsandaudiencesin theCaucasus,alongwithtakingsomesortofmore globalrolethroughincludingwiderpropagandatarget audiences,launchinginfuencemessagestothe wholeworldwidecommunity,andprovidingdirect guidanceonplanningandconductingattacksinside Europeanterritory.
Duetoforeignfghters’presenceinmilitary operationsontheUkrainiansoil,jihadistpropaganda andterroristgroupsmightexploittheUkraineconfictto conveytheirmessageandreachabroaderaudience.
Duetoitsstrategiclocation,Ukrainemightbecome a“bridge”betweenEuropeandAsia,particularlythe MiddleEast,forjihadistandterroristgroups.The vacuumofpowerregisteredonUkrainiansoildueto theconfictandKyiv’sstrategytouseforeignfghters againsttheRussiansmightpushterroristcombatants tojointheso-called“internationallegion”toacquire Westerntrainingandweapons,andmaybeusingthem againstEuropeinviolentattacks.
Consideringthatin2021theUkrainianPresident signedadecreegrantingcitizenshiptoforeigners fghtingagainstRussia,ifUkrainewouldbecomea memberoftheEuropeanUnion,theseforeignfghters couldquicklymoveonEuropeansoilandcarryout targetedattacks.
ThepresenceofAjnadal-Kavkazmilitantsraisesthe regionalgeopoliticalrisk.Itconfrmsthefearsthatthe Ukrainianterritorycouldbecomeanattractiveplacefor jihadistfghters.■
REFERENCES
•C-IEDCoE “ThreatNetworks´TacticsTechniques &ProceduresUpdateDecember2022”
•C-IEDCoE “ThreatNetworks´TacticsTechniques &ProceduresUpdateJanuary2023”
•C-IEDCoE “PropagandaonUkrainianExplosiveladenDronesinDaeshChannels”,20FEB2023
•C-IEDCoE “DaeshinKhurasan:transnational visions&threats”,24FEB2023
• www.zaborona.com
• www.ips.ac.rs
• www.nationalinterest.org
Disclaimer
Thisarticledoesnotrepresenttheopinionofany nationalormultinationalorganisation;itswholecontent shouldonlybeconsideredastheopinionoftheauthor. Asalltheinformationhasbeenobtainedfromopen sources,potentialmistakescouldhavebeenmade duringtheresearchprocess.Pleasefeelfreetosend yourcomments,correctionsandinputstotheauthor; theywillbehighlyappreciated.
ABOUTTHEAUTHOR
LieutenantColonelJoseMRufas graduatedfrom theSpanishArmyMilitaryAcademyin1993.Hewas commissionedintotheC-IEDCentreofExcellenceas HeadoftheDefeattheDeviceBranchinAugust2016, andcurrentlyholdingapostofChiefofAttackthe NetworksBranch.AsaMilitaryEngineerOffcer,his backgroundhasbeenmainlybasedonExplosive OrdnanceDisposalactivitiesintheSpanishArmyand C-IEDstaffissuesatthemultinationalheadquarters.In additiontohisEODOperator/EODOffcereducation, heattendedsomeothermilitarycoursesregarding Parachuting,ArmyStaff,InformationOperations,War CollegeGeneral/JointStaff,MilitarySearch,Technical ExploitationOperations,WeaponsIntelligenceTeam, ExploitationLaboratories,HomemadeExplosivesand otherC-IEDcourses.Hisoperationalassignments includeBosniaandHerzegovina(3),Afghanistan(3), RepublicofEcuador,IraqandUganda.
E-mail: jrufas@ciedcoe.org
(أيها الناس خلقناكم من ذكر وأنثى وجعلناكم في عشائر وقبائل قد تتعرفون على بعضها البعض)” (TheHolyQuran,Surahal-Hujurat,Ch.49:V.14)
“Omankind,Wehavecreatedyoufromamaleanda female;andWehavemadeyouintoclansandtribesthat youmayrecogniseoneanother
82 COUNTER-IEDREPORT,Spring/Summer2023
“DONBASSWILAYAT”ORHOWTOPLAYWITHJIHADISMINUKRAINIANLANDS



X-raysystemsdesigned andbuilt forBombTechs
DualDRandCRX-rayImagersinOneX-raysystem
- Extendingyourx-raycapabilityacrossmultiplemissions.
SCANSILC-LightweightRuggedisedDRX-rayDetectors
•Remotecontrolof yourx-raysourcewithoutreapproachusinganysizedScansilcDRx-raypanel.
•Scansilcreducestimeontarget-Minimalcomponentsandsetup-getthejobdonequicklyande ciently.
•Reliablewhenitcounts-Rugged,Resilient,Dust,DirtandWaterResistantinallconditions.

SCANXSCOUT-CRX-rayImagePlates




•Flexibleplates–Truegroundlevelimaging.Slideplatesintotightareas andwraparoundobjects.

•Fastgrabandgo-nocablesorwi-fitoconnect-sonodropouts.

•Combinemultipleplatesingrid formattox-raylargetargets.

SCANSILC 1824 SCANSILC 3643 SCANSILC 8686 SCANSILC 2430
SCANX SCOUT Onecontrollerrunsboth CRandDRplates
www.scanna-msc.com info@scanna-msc.comm






















































































































































































































































