ISSN2050-6732(Print)
ISSN2050-6740(Online)
EXPLORINGIEDEMPLOYMENT–UNDERSTANDINGTHE‘HOW’OFIEDATTACKS
INSIGHTSINTOIEDEMPLOYMENT IEDTACTICALDESIGNPROFILESANDSIGNATURES
IEDINCIDENTPROFILES
ANALYZINGEMERGINGWEAPONEFFECTSONEXPOSEDINFRASTRUCTURES
ACCELERATINGTHREATDETECTIONWITHREAL-TIMEVIDEOX-RAYIMAGING
AUNAV.CBRSVEHICLESAMPLECOLLECTIONKIT–ENHANCINGSAFEAND EFFICIENT SAMPLECOLLECTIONINHAZARDOUSCBRNENVIRONMENTS
TRACKING3D-PRINTING: APPLICATIONOFTECHNICALEXPLOITATIONOVERADDITIVEMANUFACTURING
MEASURINGTHEEFFICACYOFEORE:ODDSRATIOS, ANDANEVIDENCE-BASEDSOLUTION
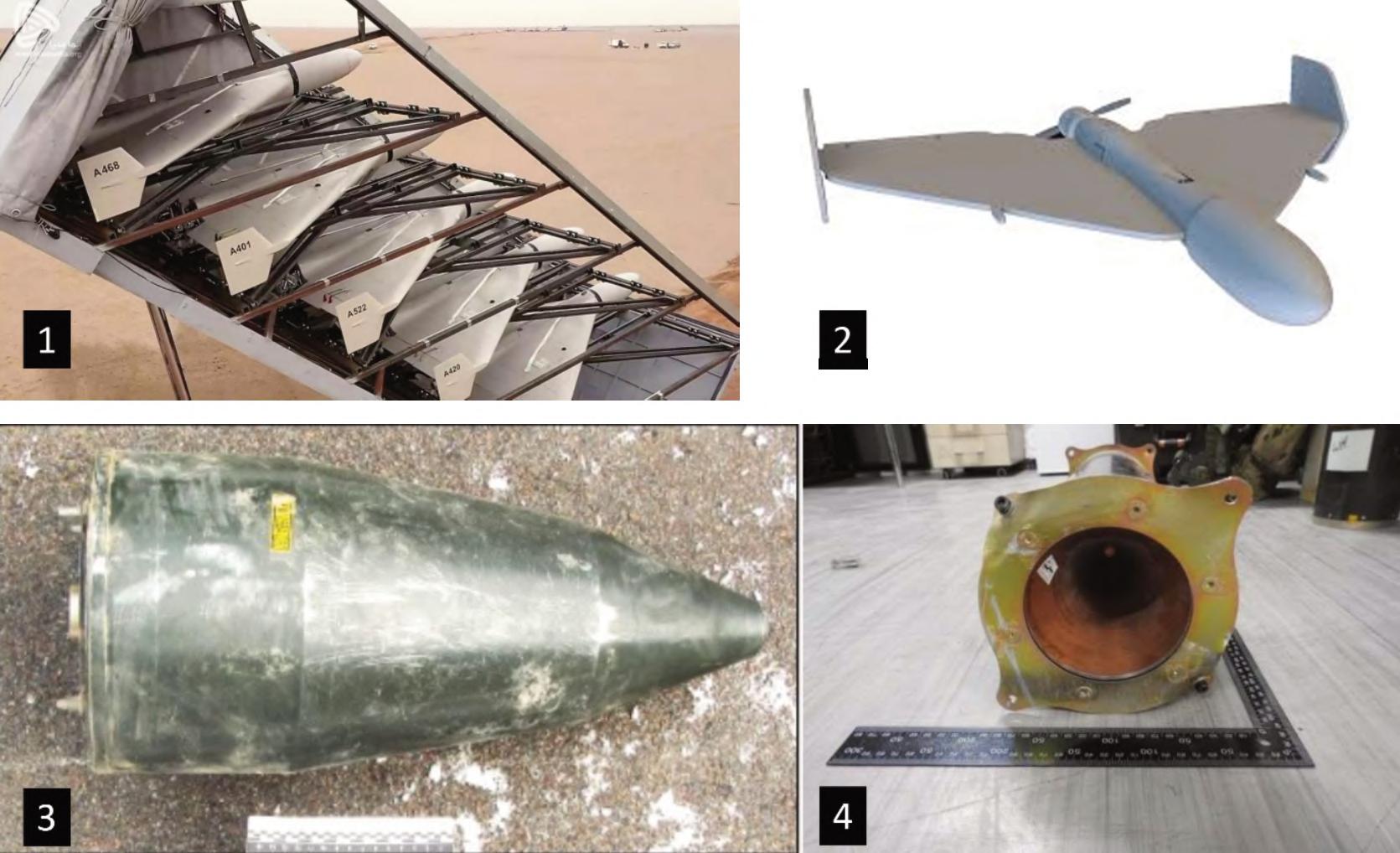
“BIRDSDETONATINGOVERALKEBULAN”:THEGROWINGUSEOFEXPLOSIVE-LADEN DRONESBYNON-STATEACTORSINTHEAFRICANCONTINENT
EDITORIALANDTECHNOLOGYPARTNERS MEDIAPARTNERS
Counter-IEDReport PublishedbyDeltaBusinessMediaLimited 167-169GreatPortlandStreet,5th Floor London,W1W5PF UnitedKingdom
Tel:+44(0)2036271985 info@deltabusinessmedia.com www.counteriedreport.com
ISSN2050-6732(Print) ISSN2050-6740(Online)
Theopinionsandviewsexpressedintheeditorialcontentinthisreportare thoseoftheauthorsaloneanddonotnecessarilyrepresenttheviewsofany organisationwithwhichtheymaybeassociated.Materialinadvertisements andpromotionalfeaturesmaybeconsideredtorepresenttheviewsofthe advertisersandpromoters.Theviewsandopinionsexpressedinthisreport donotnecessarilyexpresstheviewsofthepublisher.Whileeverycarehas beentakeninthepreparationofthereport,thepublisherisnotresponsible forsuchopinionsandviewsorforanyinaccuraciesinthearticles.
©2025.Theentirecontentsofthispublicationareprotectedbycopyright. Fulldetailsareavailablefromthepublisher.Allrightsreserved.Nopartofthis publicationmaybereproduced,storedinaretrievalsystemortransmittedin anyformorbyanymeans,electronic,mechanicalphotocopying,recording orotherwise,withoutthepriorpermissionofthecopyrightowner.
ByPaulAmoroso,anexplosivehazardsspecialist
ByPaulAmoroso,anexplosivehazardsspecialist
ByPaulAmoroso,anexplosivehazardsspecialist atAssessedMitigationOptions(AMO)consultancy
ByMarcMenne,UniversityoftheBundeswehrMunich, InstituteforStructuralEngineering,Germany
ByMarcJansen,HeadofSales&MarketingatTeledyneICM
ThisisanotherexampleofEM&EGroup'scommitmentto protectingtheoperatorandofferingthelatesttechnologyinthe roboticfeld.
65 TRACKING3D-PRINTING:APPLICATIONOFTECHNICAL EXPLOITATIONOVERADDITIVEMANUFACTURING
ByJoseMRufas&DavidHerraiz,SubjectMatterExperts inC-IEDandTechnicalExploitation
70DEFENSE&SECURITYASIA2025
71 MEASURINGTHEEFFICACYOFEORE: ODDSRATIOS,ANDANEVIDENCE-BASEDSOLUTION
ByDrRobertKeeley,RKConsulting(EOD)Ltd
77 “BIRDSDETONATINGOVERALKEBULAN”: THEGROWINGUSEOFEXPLOSIVE-LADENDRONES BYNON-STATEACTORSINTHEAFRICANCONTINENT
ByJoseMRufas,SubjectMatterExpertinC-IEDandTechnical Exploitation
FOREWORD
ByRobHyde-Bales,ConsultingEditor,Counter-IEDReport
2025witnessedtwosignifcantSecondWorld Waranniversaries–frstly8May2025which commemoratedthe80thanniversaryoftheendofthe warinEurope,andthen15August2025which commemoratedthe80thanniversaryoftheendofthe waragainstJapanandthustheendoftheSecond WorldWar.Itisthereforebothpoignantandtragicthat 80yearslater,andafterallthesacrifcesandhuman costsofthatwar,themostsavagewarsincethe SecondWorldWarhasnowragedinUkrainefor elevenyears.
In2025,60millionpeopleinsome70countriesare affectedbylandminesandimprovisedexplosive devices(IEDs).Amongthecountriesmostseriously affectedareAfghanistan,Angola,Cambodia,Iraq, Libya,SyriaandUkraine.TheuseofIEDsincreases annuallybecausetheseweaponsareinexpensiveand easytoproduce,andhavesignifcantpropaganda valueforterrorists,insurgents,andcriminals.Porous bordersinregionswithactiveterrorgroups,suchas BokoHaraminNigeria,al-ShabaabinSomalia,and ISISinSyria,facilitatetheinternationalsmugglingand transferofarmsandexplosives.Theconvergenceof criminalandterroristorganisationsfurtherexacerbates thisissue,asthesegroupscollaboratetoachieve mutualinterestsandgainaccesstoweaponryand explosives.Thefnancialcapacityofterroristgroups, oftensustainedthroughextortion,illicitdrugstraffcking andsmugglingactivities,enablesthemtoprocurethe necessaryresourcestomanufactureanddeployIEDs. Statesponsorshipofterrorism,aswellasproxywars,
inwhichnon-stateactorsreceiveweaponsand fnancialsupportfromvariousstates,remaina signifcantfactor.
TheuseofIEDsisprojectedtocontinuerisingin 2025andbeyonddrivenbyasymmetricwarfareand geopoliticaltensions.Thefactisthatafteraconfict andthegunsstopfring,itisthenthatlandmineand IEDclearancemustbegininearnest–fundingwilling.
REGIONALSECURITYDYNAMICS
Israel–Hamasconfict
Aftertwoyearsofdevastatingconfictthatreshapedthe MiddleEast,IsraelandHamasagreedinearlyOctober 2025tothefrstphaseofaU.S.-brokeredpeaceplan. AnnouncedbyU.S.PresidentDonaldTrump,the agreementmarkedthemostsignifcantdiplomatic breakthroughsincethewarbegan.Theceasefredeal promisedanimmediatehalttofghting,thereleaseof allremainingIsraelihostagesheldinGaza,thefreeing ofnearly2,000Palestinianprisoners,anda desperatelyneededsurgeofhumanitarianaidintoa territoryravagedbyfamine.OnOctober13,2025,as partofthedeal,Hamasreleasedall20livinghostages heldinGazawhoarrivedbackinIsrael,wheretheywill reunitewiththeirfamiliesandundergomedicalchecks. Thebodiesoftheremaining28deadhostagesarealso expectedtobehandedoveraspartofthedeal, althoughtheexacttimingremainedunclear.TheIsraeli cabinetratifedthedealonOctober10,2025.It representedapivotalmoment,bornfromimmense internationalpressure,regionalmediation,anda
fundamentalshiftinthestrategiccalculationsof both IsraelandHamas.However,italsoleftthemost intractableissues–thedisarmamentofHamasandthe futuregovernanceofGaza–foralater,moreuncertain phase.1 Inadditiontotheheavydeathtoll,theconfict leavesbehindalegacyofdestructionandExplosive OrdnancecontaminationoftheGazaStripwhichwill requiresignifcanteffortandinvestmenttoclearthe landofvarioustypesofammunitionandexplosives, andrestorationofhousing,medicalfacilitiesandother criticalservicesandinfrastructure.
EUROPE
Russia-Ukraineconfict
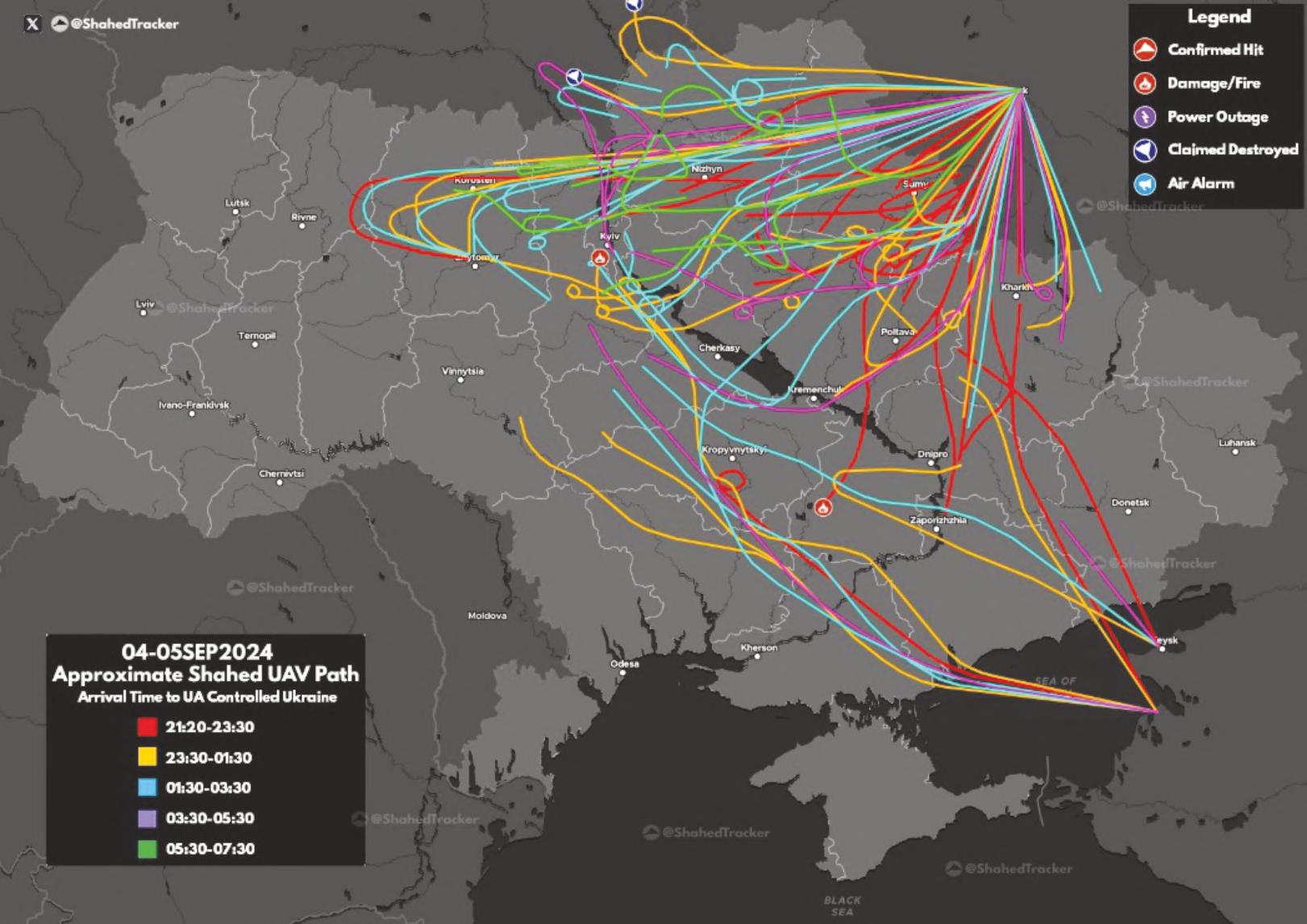
Despiteongoinginternationalpeaceeffortsandhighleveltalks,thefull-scalemilitaryoperationscontinue, includingmutualdroneandmissilestrikesdeepinside UkrainianandRussianterritory.Bothsidesuse landmines,IEDs,andconventionalexplosive weapons,includingclustermunitionswhich exacerbatelandmine/ERWcontaminationinthe EasternUkraineandbeyond.SinceFebruary2022, morethan12,300civilianswerekilled,includingover 650children,andinjuredmorethan27,800.Over sevenhundredmedicalfacilitiesand1,500schools andcollegeshavealsobeendamagedordestroyed.2
AnumberofIEDattackshavebeenreportedin UkraineandRussia,aswellassuccessfullaw enforcementoperationsagainstattemptsto manufactureanduseImprovisedIncendiaryDevices (IIDs)andIEDs.UkraineandRussiablameeach other’s‘specialservices’forrecruitingwould-be attackersviasocialmediaplatforms,promising monetaryrewardsorusingmanipulation/social engineeringtotargetvulnerableindividuals.InMay
2025,severalexplosionstargetedRussianrailway infrastructure,notablyresultinginthecollapseoftwo bridgesinBryanskandKurskregions,causingmultiple casualtiesandinjuries.InSeptember2025,inOryol regionexplosivedeviceswerefoundonrailwaytracks, resultinginthedeathsofthreeRussianNationalGuard offcersandinjuriestoanother.3,4,5
On1stJune2025acovertdroneattackconducted byUkrainetargetedfveRussianmilitaryairbases deepinsideRussianterritory.Theoperationinvolved 117explosives-ladendroneswhichwereallegedly smuggledintoRussiaandlaunchedfromaclose proximitytothemilitaryairfeldsusinginnocuously lookingcivilianvehicles.Theattackreportedly destroyedordamaged10to20warplanes.6,7 The attackbearsaclosesimilaritytotheIsraelicrippling attackonIran'sairdefencesitesanddefenceindustry assetswhereone-wayattack(OWA)droneswere assembledanddeployedfromwithinIranianterritory, andwhichwasthepartoftheSuppressionofEnemy AirDefences(SEAD)campaignpriortotheIsraeli aerialstrikesonIran'sleadership,militaryinstallations andcriticalinfrastructureinJune2025.8
ASIA
Cambodia–Thailandconfict
Landmineexplosionshavebeenasignifcantissuein theongoingconfictbetweenCambodiaandThailand, andoneofthefactorswhichledtoaseriesofviolent borderclashesinJuly2025.Bothcountrieshave accusedeachotherofplantinglandmines,leadingto injuriesamongsoldiers.Thaiauthoritiesallegedthatthe explosionswerecausedbynewlylaidRussian-made PMN-2anti-personnellandmines,blamingCambodia fortheseriesofincidents.Cambodiarejected
1 https://govfacts.org/explainer/israel-hamas-ceasefre-deal-october-2025-agreement-explained/
2 https://www.ohchr.org/en/statements-and-speeches/2025/01/ukraine-deputy-high-commissioner-decries-dangerous-escalation-and
3 https://www.rferl.org/a/russia-train-bryansk-klimov-derailment/33430473.html
4 https://www.themoscowtimes.com/2025/06/05/explosion-partially-halts-railway-traffc-in-voronezh-region-a89350
5 https://novayagazeta.eu/articles/2025/09/14/ukrainian-intelligence-claims-responsibility-for-railway-explosion-that-killed-3-inrussias-oryol-region-en-news
6 https://european-security.com/operation-spider-web/
7 https://news.harvard.edu/gazette/story/2025/06/why-u-s-should-be-worried-about-ukrainian-attack-on-russian-warplanes/
8 https://www.twz.com/air/israel-hid-drones-missiles-around-iran-to-target-nuclear-facilities-and-more-report
Thailand’saccountas‘baselessaccusations’,pointing outthatmanyunexplodedminesandotherordnance arealegacyof20thcenturywarsandunrest.9,10
Pakistan
AccordingtotheCenterforResearch andSecurityStudies(CRSS),Pakistan witnessedanover46%surgeinoverall violenceinitssecuritylandscapefor thethirdquarterof2025,withatleast 901fatalitiesand599injuries–among civilians,securitypersonnel,and outlaws–resultingfrom329incidents ofviolence,includingterrorattacksand counter-terroroperations.Injustthree quarters,2025hasprovennearlyas deadlyasallof2024,with2414 fatalitiesrecordedcomparedtothe entiretallyof2024(2546),which,with anentirequarterremaining,indicates that:a)2025isoncoursetosurpass lastyear’stoll;andb)intensifcationof militantviolenceandtheexpanded scaleofcounter-terrorismoperations. Ifthecurrenttrendcontinues,2025 couldmarkoneofthedeadliestyears inadecade.11
India
InOctober2025,adetailedanalysisby theNationalSecurityGuard(NSG)has revealedasignifcantshiftinthetactics usedbyextremistgroupsacrossIndia, withasharpincreaseintheuseof victim-operatedIEDsduring2024.The fndings,partoftheNSG’sannual comprehensivereportonblasts andexplosivemechanisms,highlight changingattackpatternsthatpresent growingoperationalchallengesfor
securityforces.AccordingtotheNSGreport,47per centofallIEDincidentsin2024(49outof104) involvedunknownmechanisms,while41percent(43 outof104)werevictimoperated.Only11percentwere command-operated,andonepercentinvolveddelay mechanisms.TheNSGnotedthatthisrefectsamarked
Up and running in less than 90 seconds
Lightweight (less than 6.5 kg/14 lbs) → Wireless or cable driven → High quality imaging → Radiation shielding → Telescopic arm (up to 65 cm/26 in)
9 https://www.nationthailand.com/news/asean/40053474
10 https://www.nationthailand.com/news/general/40052828
11 https://crss.pk/three-quarters-of-2025-nearly-as-violent-as-entire-2024/
tacticalshiftbyadversariestowarddevicestriggeredby victimsthemselves,allowingattackerstoremaindistant fromthesceneandreducingtheriskofexposure.12
Afghanistan
TheTaliban,whichisdefactoauthorityinAfghanistan continuedtomaintainapermissiveenvironmentfora rangeofterroristgroups,includingAl-Qaidaandits affliates,posingaseriousthreattothesecurityof CentralAsianandothercountries.ISIL-Kcontinuedto representthemostseriousthreat,bothregionallyand internationally.Withabout2,000fghters,ISIL-K continuedtorecruitbothinsideandoutside Afghanistan,includingamongCentralAsianStatesand theRussianNorthCaucasus,aswellasdisaffected fghtersfromothergroups.InNorthAfghanistanand areasclosetothePakistaniborders,ISIL-K indoctrinatedchildreninmadrassas,establishinga suicidetrainingcourseforminorsagedapproximately 14yearsold.ISIL-Kcontinuedtoprioritizeattackson Shiacommunities,theTalibanandforeigners.The groupistryingtoestablishoperationsinthecountries neighbouringAfghanistanandglobally.13
MIDDLEEAST
Post-AssadSyria
SincefalloftheAl-AssadregimeinSyriain December2024,over10,000peoplehavebeenkilled ofwhichmorethan3,000peopleextrajudicially executed.14 TheissueofSyria’sdiversepopulationhas becomeincreasinglyimportantfollowingasurgein sectarianclashesinrecentmonthsthatlefthundreds ofciviliansfromSyria’sAlawiteandDruzecommunities dead,manyreportedlyatthehandsoffghtersaligned withpro-governmentforces.15 InMarch,morethan
1,400AlawiteslosttheirlivesontheSyriancoast,and inJulythemassacresresultedinover1,600deaths, including20membersofthemedicalstaffatthe Al-SuwaydaaNationalHospitalamongmorethan700 residentsinSweidaprovince,accordingtotheSyrian ObservatoryforHumanRights 16
AFRICA
Theextremistgroupsandaffliatescontinuetoposea seriousthreatacrosstheAfricancontinentinconfict zones,neighbouringcountriesandfartherafeld. AccordingtoarecentUNreportissuedinJuly2025, thethreatfromIslamicStateandal-Qaidaextremists andtheiraffliatesismostintenseinpartsofAfrica,and risksaregrowinginSyria,whichbothgroupsviewasa ‘astrategicbaseforexternaloperations.’WestAfrica’s al-Qaida-linkedJama’atNasral-Islamwal-Muslimin group,knownasJNIM,andEastAfrica’sal-Qaidalinkedal-Shabaabhavecontinuedtoincreasethe territoryundertheircontrol.Thetwogroups‘pivot towardspartsofAfricacontinued’partlybecauseof IslamicStatelossesintheMiddleEastduetocounterterrorismpressures.17 TheDa’eshaffliateintheSahel region‘isbecomingincreasinglyautonomous’and steppingupattacksinMali,BurkinaFasoandNiger.18 TheUNGeneralAssemblyhasurgedMemberStates topreventterroristsfromacquiringweaponsand expressedconcernovertheincreasinguseofIEDsin terroristactivities.TheUNOffceofCounter-Terrorism (UNOCT)reporteda12%annualincreaseinIEDuse bynon-stateactorsinAfricafrom2020to2024.To counterthis,UNOCTlaunchedthe"Supporting EasternAfricaincounteringterroristuseofimprovised explosivedevices"project,aimingtoenhancesecurity inKenya,Somalia,andUganda.19
12 https://www.news18.com/amp/india/victim-operated-ieds-on-the-rise-nsg-warns-of-shift-in-terror-tactics-exclusive-9636582.html
13 https://documents.un.org/doc/undoc/gen/n25/176/00/pdf/n2517600.pdf
14 https://www.syriahr.com/en/369487/
15 https://www.reuters.com/world/how-reuters-counted-dead-march-killings-syrian-alawites-2025-06-30/
16 https://www.syriahr.com/en/367596/
17 https://documents.un.org/doc/undoc/gen/n25/176/00/pdf/n2517600.pdf
18 https://news.un.org/en/story/2023/08/1140077
19 https://www.un.org/counterterrorism/events/project-launch-supporting-eastern-africa-countering-terrorist-use-improvisedexplosive-devices
Nigeria
AccordingtoUNODC,in2024,Nigeriaexperienced 197attacksfromIEDs–anaverageofnearlyoneIED attackeverytwodays,withterroristgroups increasinglyrelyingonthemasaweaponofchoice. Alarmingly,theIEDs’useisincreasinginWestAfrica becausetheirmanufacturerequiresminimalresources andrelativelybasictechnicalknowledge.20 Inanotable development,BokoHaramfactionsareincreasingly usinganimalmanuretodisguiseIEDs,inparticular landmines,andboosttheirignition.Theselandmines aresimilartoconventionalanti-personnelminesin termsoftheirtacticaluseandactivationmode. Nigerianarmyseniorstafftoldresearchersfromthe InstituteforSecurityStudies(ISS)thatanimal excrementhadbeenusedtopreventthedetectionof IEDsinseveralpartsofnortheastNigeria,including Borno,AdamawaandYobestates.Compressed manurewasalsousedinsomeIEDsacrossthethree states.Thefreeandabundantavailabilityofit,together withitslackofcontrolandtraceability,makesita preferredIEDcomponentcomparedtomorecontrolled industrialchemicals.21
LATINAMERICA
TheillicitdrugtradeinLatinAmericaandthe Caribbean,primarilyinvolvingcocaineandcannabis,is fuelledbypoliticalinstabilityandcorruption.Drug cartelsareincreasinglyusingadvancedtechnologies likedronesforsurveillance,smuggling,andarmed attacks,refectingashifttowardsmilitarisedtactics.
Colombia
InJuly2025,Colombianauthoritiesseizedaremotecontrolled,unmannednarco-submarine,designedfor autonomousoperationsandequippedwithaStarlink antenna.Accordingtoareport,thevesselbelongsto
localGulfClan(ClandelGolfo)drugcartelandwas capableoftransporting1.5tonsofcocaine.The submarinewasfoundnearSantaMarta,onthe CaribbeanCoast,andcontainednodrugs.The ColombianNavybelievestraffckerswereconducting testsbeforeusingitforsmugglingoperations.22
Venezuela
InSeptember2025,theUSadministrationhas declaredaformal‘armedconfict’againstVenezuelan drugcartels,claimingtheyare‘unlawfularmed combatants.’SincethestartofSeptember,theUS militaryhaskilled27peopleonatleastfvevessels whichwereallegedlycarryingnarcotics.Themove marksadeparturefromtraditionallawenforcement methodsandcouldblurthelinesbetweenlaw enforcement,interdiction,andwar,raisinglegaland diplomaticquestions.23 Venezuela'sPresidentNicolás Madurohasdeniedallegationsofdrugtraffckingand accusedtheU.S.ofattemptingacoup,urgingfor peaceandcautionagainstfurtherescalation.24
Mexico
Theuseofdronesbycriminalgroupsisrapidly increasingandposesagrowingthreattoUSnational security.Mexicancartelsalreadyusedronesdailyto smuggledrugsandothercontrabandintotheUnited States.Oneofthegroups,theJaliscoNewGeneration Cartel(CJNG),evencreatedadedicateddroneunitwith thelapelinsignia"OperadoresDroneros."Footagehas beenpostedonsocialmediaclaimingtoshowMexican gangsfyingdronesandusingthemtolaunchexplosives.
InJuly2025,Mexicanintelligenceoffcialstippedoff theirUkrainiancounterpartsthatsomecarteloperatives fromMexicoandColombiaarenowinfltrating Ukraine'sforeignfghtergroupstostrengthentheir dronewarfarecapabilities.TheywarnedKyivthatcartel
20 https://www.unodc.org/conig/en/stories/global-counterterrorism-forum-west-africa-capacity-building-working-group-and-unodchold-regional-meeting-to-prevent-and-counter-the-use-of-ieds-by-terrorist-groups.html
21 https://issafrica.org/iss-today/nigeria-must-prevent-dung-being-used-for-ied-terror-attacks
22 https://colombiaone.com/2025/07/03/colombia-narco-submarine-remote-controlled-starlink-antenna
23 https://www.cfr.org/expert-brief/armed-confict-trumps-venezuela-boat-strikes-test-us-law
24 https://press.un.org/en/2025/sc16190.doc.htm
memberswereinfltratingUkraine’sforeignfghterunits tolearnhowtofyfrst-personview(FPV)kamikaze drones.FPVshavealreadyprovedtobeagamechangerintheRussia-Ukraineconfict.Mexico’s warringdrugcartels,whoareengagedintheirown dronearmsrace,nowappeartobeadoptingthe technology.Whileit'sdiffculttodeterminehowmany cartelmemberstravelledtoUkrainefordrone‘training’, theinvestigationidentifedatleastthreeformer membersofthedisbandedColombianguerrilla movement,theRevolutionaryArmedForcesof Colombia(FARC),involvedincocainetraffcking.25
LANDMINES
InJune2025Ukraineannounceditswithdrawalfrom theAnti-PersonnelMineBanConvention.26 Themove wasmadeinresponsetotheongoingconfictwith Russia,whichisnotapartytothetreaty.Thedecision followstheexamplesofFinland,Poland,Estonia,Latvia andLithuania,whohaveannouncedearlierthatthey aretooptoutoftheOttawa1997Treaty,andnowhave planstocreatea2,000-milestretchofminedareasas partofadefensiveeffortagainstanypossibleattack fromRussia.27
InJune2025itwasreportedthatRussianforces operatingneartheborderwithUkrainehave encountered3D-printedanti-personnelminesdeployed byUkrainiantroopsinRussia’sKurskregion.28 These improvisedmines,describedassmall,lightweight,and disguisedtoblendintotheirsurroundings,marka signifcantevolutioninlow-cost,high-impactweaponry. The3D-printedminesrepresentaleapinthe democratisationofweaponsproductionwhichis discussedindepthinthiseditionbySubjectMatter ExpertsJoseMRufasandDavidHerraizintheirarticle titled ‘Tracking3D-printing:Applicationoftechnical exploitationoveradditivemanufacturing‘. Unlike
traditionalanti-personnelmines,whichoftenrelyon metalcomponentsandstandardizeddesigns,these devicesleverageadditivemanufacturingtocreate plasticcasingsthatreducedetectabilitybyconventional metaldetectors.Thetechnologyallowsforrapid, decentralizedproductionofexplosivedeviceswith minimalrelianceontraditionalmaterials,components, andsupplychains.Itremainstobeseenhowlongthe devicescouldremainoperational‘inthewild’and whetherthetechnologywillbewidelyadoptedbythe warringparties.
Whilelandminesmayseemlikeacost-effectiveway todeterorslowdownanoffensive,theconsequences oftheirlong-termusecanbedevastatingintermsof injuriesandfatalities,aswellastakinglargeareasof landoutofcommercialuseforthedecadesafterthe war.AccordingtoLandmineMonitor2024,overthepast 25years,landminesandexplosiveremnantsofwar (ERW)havekilledmorethan110,000people,withmore than5,700killedlastyearalone.Eightoutoftenof thosekilledwerecivilians,manyofwhomwerechildren. ThecostofmineclearanceandERWremovalin UkrainealoneisestimatedatUS$36billion.Thiscomes atthetimeofasharpincreaseinERWcontaminated landduetotheongoingarmedconfictsaroundthe worldanduncertaintywithuninterruptedfundingfor mine/ERWclearanceoperations.
Iraq
Iraq'shistoryofconficts – theIran-IraqWar (1980-1988),theGulfWar(1990-1991),the2003 invasion,andthewaragainstISIS – hasleftthecountry heavilycontaminatedwithexplosiveremnantsofwar. Accordingtothereports,anestimated2,100km2 ofland arestillcontaminatedwithclusterbombs,landmines, improvisedexplosivedevices,andtoxicremnantsof war.ThesheersizeofthethreattoIraqiciviliansis
25 https://www.telegraph.co.uk/world-news/2025/10/14/drug-cartels-learn-modern-warfare-ukrainian-front-lines/
26 https://www.apminebanconvention.org/en/news/article/treaty-president-on-the-statement-by-ukraine-to-suspend-operation-ofthe-convention
27 https://theconversation.com/european-countries-are-now-turning-to-landmines-to-create-new-deadly-defensive-barriers-fromrussia-266181
28 https://bulgarianmilitary.com/2025/06/13/russia-ukraine-uses-homemade-3d-printed-anti-personnel-mines/
refectedinthefnancialcontributionsfromthe internationalcommunity.Between2019and2023, countriesspentacombined$453.4milliononmine actioninIraq,thesecondhighestamountofanycountry afterUkraine.Itisestimatedthatannualcontributions declinedfromafve-yearpeakof$104.5millionin2020 to$68.1millionin202329 andtherecentUSAidcuts, oneofthemajordonorstothedeminingeffortsaround theworld,areputtingthefutureofIraq’sdemining effortsatrisk.30
Croatia
Againstthebackdropofreportsofdecliningfundingand increaseoflandmine/ERWcontaminatedlandin variouspartsoftheworld,thereisgoodnewscoming fromCroatia.Afteranearly30-year-longbattleagainst landmines,andoffciallydeclaringtheSplit-Dalmatia Countymine-freeinAprilthisyear,thecountryison tracktodeclareitselfmine-freeby2026.Croatiabegan clearing1,174squarekilometresoflandin1996,and since1998hasdoneoutstandingworkwiththesupport ofseveraldonors,includingtheEuropeanUnion.Since 1998,€1.107billionhasbeenspentonmineclearance operations,ofwhichapproximately60%wascovered bystatefundsandapproximately26%(€286,441,128) byEuropeanfunds,includingloansfromtheWorld Bankandotherlocalandforeigndonors.31
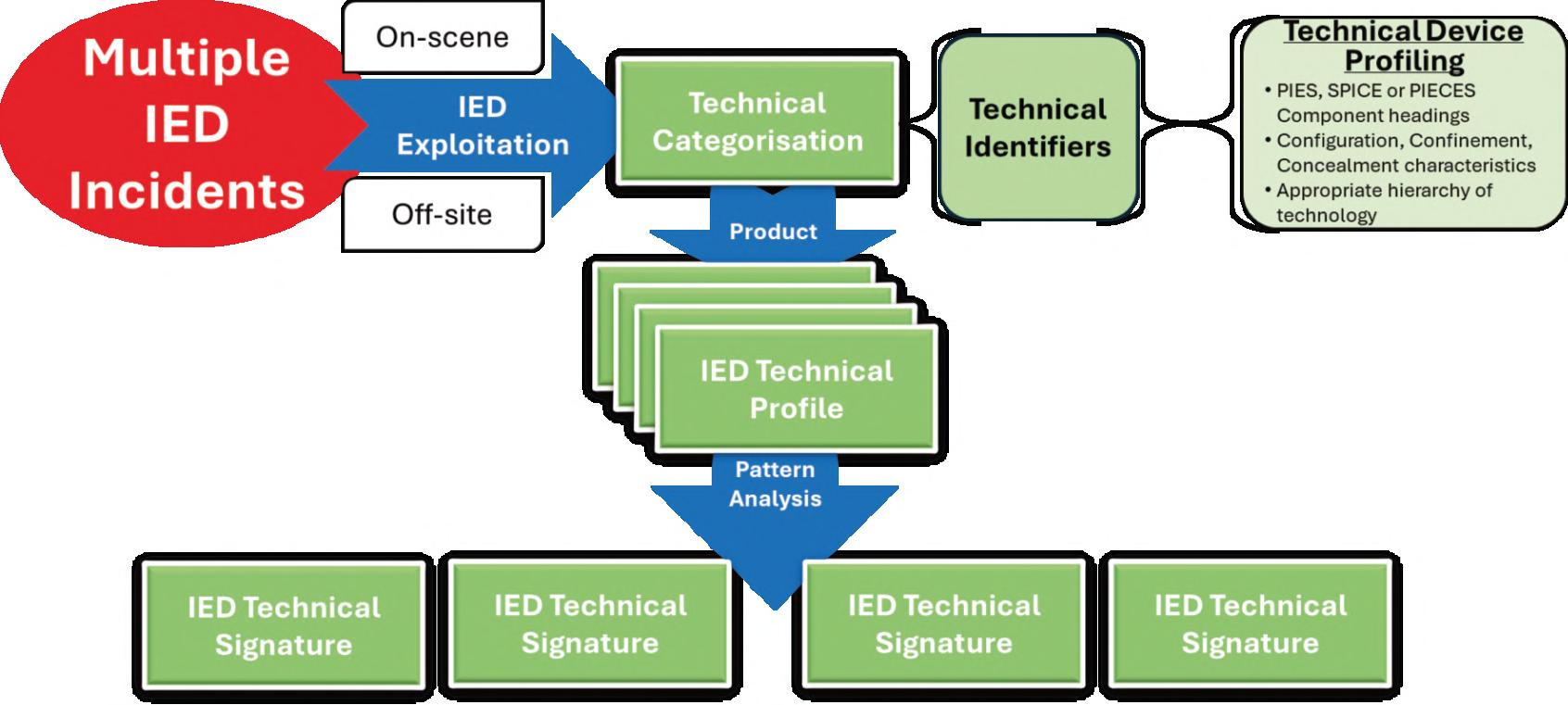
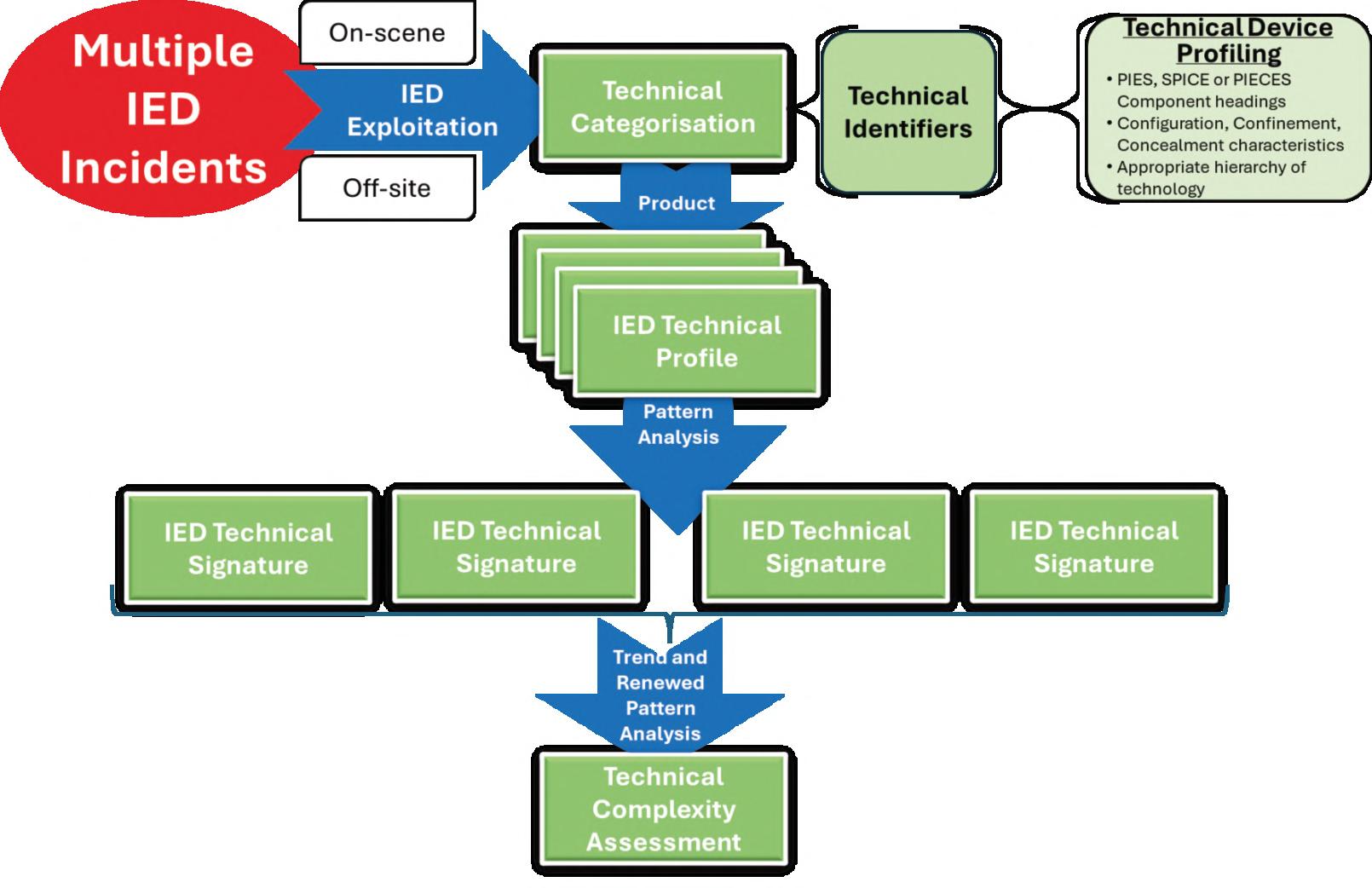
INTHISEDITION
Inaninsightfulandwide-rangingseriesofthreearticles forthiseditionofCounter-IEDReport,PaulAmorosoof AssessedMitigationOptionsConsultancy,analyses IEDincidentsusingthe5W+Hmethod,whichenhances situationalawarenessandidentifesstrengthsand weaknessesinanIEDsystem.Hedifferentiates betweenIEDuseandIEDemployment,focusingon activitiesandbehavioursassociatedwithIEDattack cycles.IEDemploymentreferstothedeploymentof IEDswithinspecifcincidents,emphasizingtactical intentanddesign.The5W+Hanalysisprovidesa
comprehensiveunderstandingofthethreat,enabling thedevelopmentoftoolsforaccurateIEDthreat analysis.Inhissecondarticle,‘InsightsintoIED Employment’,theauthordiscussesthedevelopmentof tacticaldesignproflesandIEDtacticalsignatures, whichprovideastructuredapproachtounderstanding theplanningandexecutionofIEDattacks.Heoutlines threeprimaryanalysismethods:3Ysand2Outcomes, IDREADAnalysis,andTRACE-AS-ADDED Framework.IEDtacticalsignaturesassessthethreat's sophisticationandcanbeadaptedtospecifc operationalcontexts.TheauthordescribesvariousIED attacks,includingareadenial,commandambushes, reoccupation,hoaxincidents,spoofng,TrojanHorses, anddroneuse.InhisfnalarticleinthisEdition,‘IED IncidentProfles’,theauthorexploreshowtactical designproflescanbeintegratedwithother C-IEDanalysistoproduceIEDincidentprofles.He describeshowtechnicalidentifers,IEDcomponents andcharacteristics,areusedtoproducetechnical deviceproflesandhowpatternanalysissupports thedevelopmentofIEDtechnicalsignatures. HedetailsvariouscharacteristicsofanIED–confguration,confnementandconcealment. Componentfunctionality,complexityandimplementation all contributetotechnicaldeviceproflingwiththeend resultbeinganIEDincidentprofle.
Inathought-provokingandhighlytopicalarticle, CaptainMarcMennediscussestheglobal transformationaleffectsofdronetechnologyandthe needforstructuralcountermeasures.Dronesarenow presentincommercialairspace,evolvingfrom reconnaissanceanddeliveryplatformstostrategic weaponssystems.TheBASISProjectaimsto integratestructuralprotectionmeasuresintoa multidimensionalcounter-droneprotectionconcept, focusingonthedevelopment,testing,andevaluation ofamodularsteel-sandwichconstruction(SSC) designedtowithstandexceptionaleffectslike fragmentationandexplosiveinducedblastwaves.The
29 https://inkstickmedia.com/us-aid-cuts-put-the-future-of-iraqs-demining-efforts-at-risk/
30 https://inkstickmedia.com/us-aid-cuts-put-the-future-of-iraqs-demining-efforts-at-risk/
31 https://www.balcanicaucaso.org/eng/Media/Galleries/Mines-in-Croatia-the-fnal-step
SSCisparticularlyvaluableforcriticallyimportantroad bridgesonNATOsupplylinesinmainlandEuropeand anIsraelihospital.Theauthorhighlightsthe importanceofSSCprotectioninprotectingvulnerable roadbridgesandaddressingattacksbyunmanned aerialsystemsagainstSaudiArabianoilproduction facilitiesin2019.Theattacksresultedinfnancial losses,globaloilshortfalls,andpriceincreases.The authorconcludesthatitistimetoprovidestructural protectiontocriticallyimportantinfrastructuresystems andgiveittheweightitdeservesinplanning, procurement,anddelivery.
Inhisarticle ‘AcceleratingThreatDetectionwithRealTimeVideoX-RayImaging’,MarcJansen,Headof SalesandMarketingatTeledyneICM,outlineshow advancementsindigitalradiographyhaveintroduced real-timevideoacquisitioncapabilities,transformingthe tacticalutilityofX-raysystemstodeliveractionable clarityinreal-time.Incontemporarythreatenvironments timeisoftheessence.Asanexampleofthiscapability, hedescribestheTeledyneICMC-ViewX-raysystem thathasbeenengineeredforrapiddeploymentandfeld resilience.Heoutlinesascenariofollowingacredible threattoamajormetropolitantransporthub.This resultsinthenecessitytoevacuatethestationandthe subsequentneedtocheckmanyunattendedpersonal belongingssuchasuitcasesandotherhandbaggage. ThischeckingisundertakenusingalivevideoX-ray systemthatenablestheprocesstobecompletedmuch morerapidlythanifusingconventionalX-raysystems. HedescribeshowtheTeledyneICMC-Viewsystem’s compactarchitectureandrapiddeploymentcapability makesitsuitableforawiderangeofoperational environmentstoincludepublictransporthubs,event security,bordercontrolandcustoms,military operations,CriticalInfrastructureprotection,law enforcementandmailandparcelsecurity.C-Viewis designedforthedeliveryofactionableclarityinrealtime,tacticalagilityandhandhelduseinruggedand austereenvironments–asignifcantshiftinthreat detectiontoday.
IntheirarticletheSpanishEM&EGroupdescribe theaunav.CBRSVehicleSampleCollectionKit.This vehicleisdesignedtoautomatethehithertohazardous
processofCBRNsamplecollectionafterthereleaseof CBRNmaterial.Thefrstresponsestepissample collectionwhichcurrentlyforcespersonneltowear heavycumbersomeprotectionsuits,movingslowly andatgreatrisk.Theaunav.CBRSVehicleSample CollectionKitdramaticallyaltersthedynamicofsuch operationsbyshiftingthisdangerousmissionfrom humanhandstoaroboticarmoperatedsafelyfrom insidethevehicle,thusautomatingbothsample collectionandstorage.Thevehiclecomprisesthree maincomponents–aRoboticArm,aSample ContainerandSamplingTools.Thefveautomated stepsintheprocessaredescribedindetail.The aunav.systemdeliversfvekeyoperationaladvantages –EnhancedSafety,Versatility,Integrity,Effciencyand Compactness.Insummary,theaunav.CBRSVehicle SampleCollectionKittransformswhatwasoncea high-riskmanualtaskintoacontrolled,repeatableand secureprocess.Thisrepresentsatransformational changeinCBRNsamplecollection. ■
RobHyde-Balesbiography
DuringhiscareerintheUKRoyal Engineers, RobHyde-Bales was responsibleforlandmineclearance inLibyaand,morelatterly, Afghanistanintherunningofthe frstUnitedNationshumanitarian landmineclearancetraining programme–OperationSalam. TheprogrammetrainedAfghanmalerefugeesin landmineclearancetechniques,andAfghanwomen andchildreninmineawarenessandavoidance training.MorerecentlyhesetuptheCaribbean SearchCentreinKingston,Jamaica.TheCentreis designedtotrainsecurityforcesacrosstheCaribbean inmodernsearchtechniques.Afterretiringfromthe armyhejoinedCranfeldUniversityatShrivenham, nearOxford,andundertookaresearchprojecton behalfoftheUKMinistryofDefencethatexamined waystoimprovethesharingofIEDthreatinformation betweenthemilitaryandcivilianorganisationsin hazardousareas.
EXPLORINGIEDEMPLOYMENT–UNDERSTANDING THE‘HOW’OFIEDATTACKS
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy
INTRODUCTION
Aspartofanongoingseriesexaminingthe5W+Hof IEDattacks,thisarticlefocusesonthetactical employment,1,2 or‘how’ofIEDattacks.Thisseriesis intendedtosupportthedesign,development,and sustainmentofanaccurateIEDthreatpicture,3 ensuringthatC-IEDefforts4 remaineffectiveandthreataligned.ByanalysingIEDincidentsthroughthelenses ofwhat,how,where,when,who,andwhy,the5W+H approachoffersasystematicmethodforunderstanding IEDthreats.Thisstructuredanalysisenhances situationalawarenessandenablestheidentifcationof IEDsystemstrengthsandvulnerabilities,ultimately guidingmoreeffectiveinvestmentinC-IEDefforts.
Thisarticlebeginsbyclarifyingthedistinction betweenthetermsIEDuseandIEDemploymentas theyapplyinthiscontext.Thisintroducesthekeytactical datapointsknownastacticalidentifersofIEDattacks.It
thenpresentsasimpleclassifcationsystembasedon tacticalemploymentbeforeadvancingtoamoredetailed tacticalcharacterisationofIEDattacks,whichinvolves analysisoftheirtacticalintentandtacticaldesign. Tacticalcharacterisationisbasedontacticalidentifers. Tosupportthis,threeanalyticalapproacheswillbe introduced,eachofferingalternativemethodsfor identifyingtacticalidentifersinanIEDattack:3Ysand2 Outcomes;IDREADanalysis;TRACE-AS-ADDED framework.Thenextarticleinthisserieswilloutlinethe useoftacticalidentifersindevelopingtacticaldesign proflesandtacticalsignatures.
IEDUSEVERSUSIEDEMPLOYMENT
Theterms IEDuse and IEDemployment areoften usedinterchangeably;however,theydifferinanalytical scopeandprecision.Understandingthisdistinctionis
1Adescriptionofhowthedeviceandtargetwerebroughtinproximityofeachother.Source: TheIEDIncidentReportingGuide, 6thEdition
2ThetermtacticaldeploymentofIEDsisoftenusedsynonymouslywiththetacticalemploymentofIEDs.
3AnIEDthreatpictureisanassessmentoftheuseorthreateneduseofIEDsintermsofthetechnicalcomplexity,tactical sophistication,theIEDsystememployingthemandlocalcontext.TheIEDsystemisassessedunderitsintent,capabilities andtheopportunitiesithastoemployIEDsagainstdefnedtarget(s).Localcontextisdefnedbyageographicarea,thetarget oftheattacksandotherlocalfactors.
4C-IEDeffortsmayberesponsive,preventativeorcrosscuttinginnature.Sucheffortsinclude,interalia,legalinstruments, training,mentoring,advice,operationalandtacticalortechnicalassistance,technologyandequipmentprovision,intelligence activities,investigationsandactionsagainstanIEDsystem,interagencyandinternationalcooperation,controlof explosivesandotherIEDcomponentsaswellasanyotherinvestmentmadetorespondtoandultimatelypreventIEDuse.
Source: ManagingaC-IEDEnterprise,TheCounter-IEDReport,Winter2024/25
essentialforaccuratereporting,threatanalysis,C-IED planningandoptimiseddecisionmaking.Analysisof IEDuseprovidesoperationalandstrategiclevel understandingofanIEDthreat,whileanalysisofIED employmentprovidestacticallevelunderstandingof IEDattacks.
IEDUse
IEDuse referstothefullspectrumofactivitiesand behavioursassociatedwithIEDattackcycles,5 whether actualorthreatened,acrossmultipleincidents.Itisa broadanalyticaltermappliedinstrategicand operationalassessmentstocharacterisetheactivities ofanIEDsystemovertime.IEDusecanincludethe activities:
•Facilitation6 -establishingtheenablingenvironment forIEDattacks,whichcanincludefnancing, recruitment,logistics,andcommunicationnetworks beingsetupinparallelwithotheractivitiesinan attackcycle.Facilitationhelpsensureallother activitiesarepossibleandsustained
•Targetselection -choosingalocation,person,or assetthatalignswiththeattacker'sobjectives coupledwiththespecifcdetailsonhowacertain IEDwillbeusedagainsttheselectedtarget.Itcan includerouteanalysiswhentargetingamobile target.Targetsareevaluatedbasedonsymbolic
value,vulnerability,potentialcasualties,andmedia impact.
•Pre-Attacksurveillance -observingpotential targetstogatherintelligence,tohelpattackers understandroutines,securitymeasures,and identifyweakpointssothatopportunitiestoattack canbeidentifed.Thisphasecanlastdaysto months.Pre-attacksurveillancemayoccurbefore orinparallelwithacquisition,transport, manufactureandassemblyactivities.
•Rehearsal -dryrunsorroutetestingtoassess attacksiteandvantagepointswithintervisibility intoit,alongwithapproachestoandescaperoutes fromit.Thesearenecessarytoensurethepathto thetargetisaccessibleandpredictable; chokepoints,surveillancecameras,orcheckpoints areidentifed,andtimingsofactivitiescanbe understoodsuchastimingtraffclightsor observingpatrolpatterns
•Materialacquisition -procuringPIECES componentsorprecursorschemicalsneededto buildthedevice,whichmayinvolvetheft,black marketpurchases,acquisitionthroughsanctioned orgrey-marketchannelseachofwhichmaybe local,externalorviasmugglingroutes.
•Transport -movementofcomponents,network personnel,andpropagandamaterial.Itincludes
5Attackcyclereferstotherepeatableseriesofactivities,actionsordecisionsthatIEDnetworkstypicallyfollowbefore,during, andafteranattack.Thesestepsformarecognisableoperationalrhythm,oftenrefectingstandardoperatingproceduresor learnedbehaviourswithinthreatnetworks.Atypicalcyclemayincludefacilitation → targetselection → pre-attacksurveillance → rehearsals → materialacquisition → transport → manufacture → deviceassembly → emplacement → remoteobservation → initiation → post-attackactivities.Whileeachattackmayvary,understandingcommonactivitieshelpsidentifyexploitable vulnerabilitiesandinformswhereC-IEDcountermeasuresshouldbefocused.Theterm‘attackcycle’canbemisleading,as itimpliesastrictlylinearprocess.Inreality,manyactivitiesoccurconcurrentlyorinfexiblesequences.However,timingand synchronisation,especiallyinthefnalstages,areoftencriticaltomaximisingoperationalimpact.
6FacilitationreferstotherangeofenablingactionsorsupportmechanismsthathelpIEDnetworksplan,coordinate,and executetheiractivities,evenifthefacilitatorsthemselvesarenotdirectlyinvolvedinattacks.Facilitationcaninclude: •ProvidingsafehousesorstoragelocationsforIEDcomponents,manufacturingparaphernalia,personnel,orpropaganda material.
•Supplyingintelligenceorsurveillancesupport,suchasobservingmovementpatternsorhabitsoratargetoridentifying vulnerableroutes.
•Offeringtransportation,whetherformaterialsornetworkpersonnel.
•Managingcommunicationsandlogisticstoensuretimelyandsecurecoordinationbetweennodes,cells,or actors.
•Recruitingindividualswithtechnical,operational,orlocalknowledge.
•Creatingfalsedocumentationorexploitinglegalloopholestoevadedetection. Facilitationisoftenconductedbyperipheralactors,suchassympathisers,coercedindividuals,orcriminalpartners,who enhanceanIEDsystem’scapabilitieswithoutbeingtheactualbomb-makersorattackers.
assembledIEDsfrommanufacturingorassembly locationstothetargetlocation,whichmayinvolve concealmenteffortswithrouteschosentoavoid detectionandminimiseriskofpremature detonation.Itmayinvolve,useofcouriers, modifedvehicles,orsafe-housenetworks.
•Manufacture –mayinvolvefabricatingspecifc componentsbyrepurposingcommercialitems, suchasswitches.Itcanalsoincludethe manufactureofcomponentslikeimprovised explosivesordirectionaleffectcontainers.
•DeviceAssembly –involvesconstructingsubassemblies,suchasfringcircuitsorexplosive trains,orassemblingacompleteIEDusingall requiredcomponentsalignedwiththeintended targeteffectandattackplan.Componentsmaybe manufacturedacrossdistributedlocationsand laterbroughttogetherforfnalassemblyatasingle site.Thisprocesstypicallyoccursinpermissiveor semi-permissiveenvironmentsfortheIED network,suchasasafehouse,garage, clandestineworkshop,remotelocation,orany areathatallowsfreedomofoperation.
•Emplacement –referstothephysicalplacement oftheIEDattheattacksiteormovingitinclose proximitytotheintendedtarget.Thisaction typicallyrequirescoordinationwiththeexecution timelineandmaybeadjustedtorespondto changingconditions.Emplacementiscarriedout covertlytoavoiddetectionandofteninvolves disguisingthedeviceordeployingitduringperiods oflowpublicpresence.However,insomecases, dependingontheattacker’sobjective, emplacementmayoccurduringperiodsofhigh publicactivitytoreducethelikelihoodofdetection bysecurityforces.
•RemoteObservation -monitoringthetargetarea afteremplacementpossiblyinvolvingtheuseof cameras,spotters,orevendronestoconfrm targetpresenceorcrowddensityandcounterany actionsbysecurityforcesorotherstorevealits presenceorrenderitsafe.
•Initiation –actiontocausethedevicetofunction againstthetargettoachievetheintendedeffects
requiringcoordinationandsynchronisationacross allattackcycleactivities.Dependingonthefring switchandtheattacker'sintentandescapeplan, canbemanual,remote,timed,orvictimoperated.
•Post-attackactivities -follow-upactionsfor strategicoroperationaleffect:
◦Escapeandevasion
◦Publicisingtheattackforpropagandaand messaging
◦LessonslearnedofIEDtargetseffectsand tacticalsuccessesandfailings
Whiletheordersetoutoftheseactivitiesrefects howIEDattacksoftenunfoldinpractice,thissequence isnotrigidwithmanyactivitiesoverlappingand occurringsimultaneouslyorinparallel.Havingsucha frameworkofIEDattackactivitiessupportsanalysisfor identifyingvulnerabilitiesorinterventionpointsateach phase. IEDuse helpscharacterisethefulloperational capacityandsustainedactivityofanIEDsystemwithin aconfictorregion.
IEDEmployment
IEDemployment,bycontrast,referstothedeployment ofIEDswithinspecifcincidents.Itemphasisesboth thetacticalintentandthetacticaldesignofanattack, whichreferstohowadeviceisbroughtintoproximity withitsintendedtarget.Tacticalintentandtactical designprovideinsightsintotheplanningchoices, tacticalreasoning,andexecutionbehindanindividual attack.Thistermisespeciallyvaluedinintelligence andC-IEDapplications,asitenablestheidentifcation oftacticalidentiferswithinanIEDincident.These identifersprovidethecriticaldatarequiredto understandthetacticsinvolvedinIEDincidents.We willnowexaminetacticalidentifers,thekeydata neededtounderstandIEDemployment.
TACTICALIDENTIFIERS
Tacticalidentifersrefertotheobservableandinferable tacticalfeaturesofhowanIEDattackisplannedand executed.Theydescribehowanattackeremployed,or intendedtoemploy,adeviceinrelationtothetarget, withinthecontextoftheoperationalenvironmentand
localfactors,toachievetheintendedtargeteffect.These identifersarederivedfromanalysingtacticalfactors suchasdeliverymechanism,placement,useofterrain, initiationmethod,coordinationofattackcycleelements, andtheconcealmentemployed. Tacticalidentiferscan beoutlinedundervariousheadings,suchasthe3Ys+2 Outcomes,IDREAD7 headingsandtheTRACE-ASADDED8 frameworkallofwhichareoutlinedlaterinthis article.Tacticalidentifersprovidethedatawhichare usedtodevelopIEDtacticalproflesandtactical signatureswhicharecoveredinthenextarticleinthis series.BothIEDtacticalproflesandtacticalsignatures arecriticaltoinforminganunderstandingoftheIED tacticalsophisticationofanIEDthreat.
IEDCLASSIFICATIONBYTACTICAL EMPLOYMENT
‘TacticalemploymentisameansofIEDclassifcation,in whichIEDsarecategorisedbyhowthedeviceandtarget werebroughtinproximityofeachother.Itoftenrefersto themethodofdeliveryallowinganunderstandingofhow anattackwasintendedtobeconducted.Tactical employmentofIEDsincludesvehicle-borne;animalborne;person-borne(proxyorsuicidebomber); emplaced;standoff;9 water-borne;air-borne;10 and
postalIED.’ 11 WhileIEDclassifcationbytactical employmentisanimportantandinsightfulmeansto classifyIEDattacks,therearebroaderconsiderationsin termsofhowIEDsareemplacedandemployedthatare capturedundertheirtacticalcharacterisation.
TACTICALCHARACTERISATION
AnalysinghowIEDsareemployedinattacksdirectly supportsthetacticalcharacterisationofanIEDthreat withinagivencontext.Thischaracterisationexamines boththe:
•Tacticalintent -intendedfunctionofthedevice12 i.e.theintendedimmediate,ordirecttacticaleffect ofanIED.13
•Tacticaldesign -planningandexecutionofIED attacks.
ByprovidinginsightintohowIEDsareusedor intendedtobeused,tacticalcharacterisationhelps assessthelevelofsophisticationbehindtheseattacks, whichisanessentialcomponentinanaccurateIED threatpicture.
TacticalIntentofIEDAttacks14
WithinC-IEDanalysis,intentwithinanIEDsystemcan beassessedattactical,operational,andstrategic
7IDREADisanacronymforsixtacticalidentifersofanIEDattackwhichcoversIntent;Deliverymethod;Role;Emplacement location;Attachmentmethod;Deviceorientation.
8Acronymfor,Tacticalintent;Role;Attackgeography;Conditionwhenfound;Environmentalconditions;Atmospherics;Sensor defeat;Attachmentmethod;Delivery;Domain;Employmentmethod;andDiscoverymethod.
9StandoffIEDsrefertoamethodofIEDemploymentinwhichanexplosivedeviceislaunchedorreleasedbyanattackerfrom asafelocationandtravelstoitspointofcontact.Thisapproachallowsattackerstoengageatargetwithoutbeingpresentat thepointofcontactatanystageoftheattack.StandoffIEDsalsoenablethebypassingofphysicalsecuritymeasures,such asbarriersthatwouldotherwisepreventemplacementordeliverybyconventionalmeans.Theycanbeemployedacross land,air,andmaritimedomains.ClassifyinganIEDasstandoffprovidesvaluableinsightintoitstacticalemployment.This classifcationcanbefurtherrefnedbyincorporatingdetailssuchasthedomainofoperation,launchmethod,armingmethod, and,whereapplicable,thespecifcsofprimaryandsecondaryfringswitches.Thisexpandedapproachaddsgreaterdepth andprecisiontotheclassifcation.
10Bothwaterandair-bornerefertotheirdomainofuseasmuchasanyothercharacteristicandareoftenconsideredtypesof standoffIEDs.
11Source: IEDClassifcation–BreakingDownBombAttacks,TheCounter-IEDReport,Spring/Summer2025.
12Source: TheIEDIncidentReportingGuide,6thEdition.p.3
13Source: TheIEDIncidentReportingGuide,6thEdition.p.3
14 TheIEDIncidentReportingGuide,6thEdition,defnestacticalcharacterisationbystatingthattheintentofadeviceisitspurpose. Itfurtherspecifesthatthepurposeofadeviceis“theintendedimmediate,ordirecttacticaleffectofanIED”(p.15).Thiscircular useof intent and purpose suggeststhetermsareinterchangeablewithintheguide.However,forthepurposeofthisarticleseries, intentisusedtodescribethespecifcobjectivebehindanindividualactofviolence,suchasanIEDincident.Thisreferstothe tacticalaim,ortheimmediateresulttheattackerseekstoachieve.Incontrast,purposerepresentsthestrategicorideological rationalebehindtheuseofIEDsbyathreatactor.Itrelatestotheattacker’sbroadermotivations,suchasadvancingacauseor infuencingthetrajectoryofaconfict.
levels.InthecontextofIEDemployment,thefocusis ontacticalintent,theimmediateobjectiveofaspecifc actofviolence,suchasimmobilisingaconvoyor targetingagovernmentoffcetounderminelocal authority.Whiletacticalintentisincident-specifc,itcan beaggregatedacrossmultipleeventstoreveal patternsofbehaviourthatpointtoanoperational-level intent.Forexample,repeateduseoftime-delayed IEDsagainstinfrastructuremaysuggestadeliberate efforttodisruptgovernancewhileavoidingdirect confrontation.Overtime,thissustainedattackpattern canrevealastrategicpurpose,suchasweakening statestructuresorshapingconfictdynamicstoserve ideologicalgoals.Distinguishingbetweenoperational intentandstrategicpurposeiscriticaltodesigning, developing,andmaintaininganaccurateIEDthreat picture.Withinsuchathreatpicture,theIEDsystemis assessedthroughitsintent,capabilities,and opportunitiestoemployIEDsagainstdefnedtargets. Inthiscontext,intentextendsbeyondthetacticallevel tooperationalandstrategiclevels.
Toavoidconfusionorcontradictionsinterminology, itisessentialtoclearlydelineatethescopeofintent beingreferredto.Thisrequiresdistinguishingbetween singulartacticalactions,macro-leveltacticalusage derivedfromclustersofincidents,andtheoverarching strategiccampaignrationale.Tacticalintentrefersto theobjectiveofanindividualIEDincident.When multipletacticalintentsareobservedacrossevents andformadiscerniblepattern,thisreveals consolidatedoperational-levelbehaviourbytheIED system—bestdescribedasitsoperationalintent.In contrast,thebroaderstrategicideologicalrationalethat guidesorjustifesthewidespreaduseofIEDsismost accuratelycharacterisedastheIEDsystem’sstrategic purpose.
Tacticalintent,specifcally,referstotheimmediateor directtacticaleffect15 ofanIEDattack.Assessing tacticalintentinvolvesidentifyingthetargetofthe deviceandthespecifcobjectivesdrivingits
15 TheIEDIncidentReportingGuide,6thEdition
emplacement.Apreviousarticle16 onIEDclassifcation introducedtargeteffectsasamethodforcategorising attacks,basedontheirintendedprimaryimpact. Tacticalintentmayincludeanti-armour;anti-personnel; anti-air;anti-infrastructure;anti-vehicle;anti-maritime; tactics,techniquesandprocedures(TTP)identifcation; obstaclecreation;andbreaching.Thesecategoriescan befurtherspecifed.Forinstance,ananti-personnel IEDmaybemorepreciselyclassifedasanti-EODor anti-frstresponder,dependingonitsintendedtarget. Additionally,descriptorssuchassuspiciouspackages, unattendedpackages,orbombthreatsareoftenused tocharacteriseIEDswithinthecontextofTTP identifcation.
TacticalDesignofIEDAttacks
ThetacticaldesignofanIEDattackoutlinesthe varioustechniquesandactivitiesinvolvedinits planningandexecution.Itfocusesondevice placementandthemethodsusedtobringthetarget anddeviceinproximityandachievethetacticalintent oftheattack.Tacticaldesignshouldasaminimum addressthequestionsof‘whyhere,whynow,andwhy inthisway’17 aswellasassessingtheoutcomeofan attack.Thiscaninvolveapplyingthe3Ys+2outcomes tool.Morecomprehensiveanalysisofthetactical designofIEDattacksarepossibleinvolvingmultiple tacticalidentiferssomeofwhicharecomplementary andoverlapping.Termsusedtodescribeaspecifc typeofdeviceorcomponentofadevice,suchasa SVBIED,areoftenusedtodescribeallorpartofthe tacticaldesign.18
3Ysand2Outcomes
Asaminimum,thesceneexploitationofanIEDincident shouldanswerthequestions “whyhere?”, “whynow?”, and “whyinthisway?”,whilealsodetermining “what wastheactualoutcome?” andassessing “whatwasthe intendedoutcome?”.Thisisreferredtoasthe3Ysand 2outcomesofanIEDincident.
16Source: IEDClassifcation–BreakingDownBombAttacks,Counter-IEDReport,Spring/Summer2025.
17Source: Understanding&MaximizingC-IEDInformationSharing,TheCounter-IEDReport,Autumn2023
18Source: TheIEDIncidentReportingGuide,6thEdition.p.8
Whyhere? Thisquestioninformsourunderstandingof thewhereofanIEDattackandtheexposureofthetarget toattack.Ittypicallyfocusesontheattackgeography alongwithconsiderationofthetargetoftheattack.
Whynow? Thisquestioninformsourunderstanding ofthewhenofanattackandtheexposureofthetarget toattackwhichmayincludepotentialpatternsettingby thetarget.
Whyinthisway? Thisquestioninformsour understandingoftheattackers’tacticalintentandaim, alongwiththeircapabilitiesintermsofthecompetency toplan,emplaceandexecutetheattack.Itcanalso provideinsightsintothevariousactivitiesinvolvedina givenattackcycle.
Whatwastheintendedoutcome? Thismayalso beconsideredtheplannedimmediate,ordirecttactical effectofanIEDattack.Itinformsourunderstandingof whoorwhattheintendedtargetwasandtheattackers tacticalintent.
Whatwastheactualoutcome?
Thereareseveralconsiderationstoaddresswhen answeringthisquestion:
•Isthereadifferencebetweentheintendedand actualoutcome?Ifso,why?
•Doesthisdifferencerefecttheattacker’slackof competenceorprofessionalcapability?Ifso,what didtheyfailtodothatpreventedthemfrom achievingtheirintendedoutcome?
•Isthereagapbetweentheattacker’sintentand capability?
•ArecurrentC-IEDeffortseffectiveinpreventingthe attackerfromachievingtheirobjective?Ifso,what specifcactionsdidthetargettaketodisruptor countertheattacker’sintent?
•Whoweretheactualcasualties?Isthereadifference betweentheintendedtargetandthecasualties?If so,why?Wasthisduetoindiscriminatetargeting, poorattackexecution,C-IEDmeasuresinplace,or acombinationofthesefactors?
•Howdothecasualtiesbreakdownbetweeninjured andkilled?Whatwerethemechanismsofinjury? Whydidsomecasualtiesdiewhileothers survived?
•Whatassetsandinfrastructureweredamaged, and whatwasthelevelofdamage?Whatcapability waslostduetotheattack?
IDREADAnalysis
AstraightforwardmethodforundertakingIED tacticalcharacterisationistousetheIDREAD headings,whichcategoriseIEDattacksaccordingto thetacticalidentifersofIntent,Deliverymethod,Role, Emplacementlocation,Attachmentmethod,and DeviceOrientation.19 Eachofthesetacticalidentifers isalsoincludedwithinthemorecomprehensive TRACE-AS-ADDEDframework.However,inthis framework,emplacementlocationanddevice orientationfromtheIDREADheadingsare encompassedwithinattackgeographyinthe TRACE-AS-ADDEDheadings.
TRACE-AS-ADDED20 Framework
TheacronymTRACE-AS-ADDEDoffersastructured frameworkforassessingthetacticalcharacterisationof IEDattacks.Itpresentsasetoftacticalidentifersthat canbeadaptedtomeetspecifcanalysisneeds, whetherduringon-sceneexploitationoroff-site evaluation.Whilecomprehensive,theframeworkis fexible,andnotallidentiferswillnecessarilybe documentedineverycase.Thetacticalidentifers includedintheTRACE-AS-ADDEDframeworkare Tacticalintent;Role;Attackgeography; 21 Condition whenfound;Environmentalconditions;Atmospherics; Sensordefeat;Attachmentmethod;Delivery;Domain; Employmentmethod;andDiscoverymethod. Beyond itsanalyticalrole,thistoolalsoholdsoperationalvalue, supportingtrendandpatternanalysistodeepen insightsintothetacticalsophisticationbehindIED
19DeviceorientationisatacticaldescriptionofwhereanIEDispositionedandlocatedinitsemplacementrelativetothe intendedtargetwhichmaybemobileorstaticattheintendedmomentofinitiation.Itisequivalenttoangleofattack.
20ThelistedIEDtacticalidentifersalongwiththedefnitionsprovidedarebaseduponandadaptedfromthoseprovidedin TheIEDIncidentReportingGuide,6thEdition
21AttackgeographyofanIEDattackcanbebrokendownunderthesubheadingsofDeviceplacementcharacteristics; Contactpointcharacteristics;CommandIEDSpecifcconsiderations;andPostblastdata.
attacks.Belowisabreakdownofeachofthetactical identifersthatmakeuptheTRACE-AS-ADDED framework.
TacticalIntent
Possibilitiesincludethefollowingdescriptorsaloneor incombination:anti-armour;anti-personnel(anti-EOD oranti-frstresponder);anti-air;anti-infrastructure;antivehicle;anti-maritime;TTPidentifcation(suspicious packages,unattendedpackages,orbombthreats); obstaclecreation;andbreaching.
Role
Whatwastheroleofthedeviceinanattackifmore thanonewasusedorpresent?Wasthedevicepart ofamorecomplexevent?e.g. “immobilizethelead convoyvehicleinthemiddleofthekillzoneofan ambush.” TheroleofanIEDshouldbecharacterised asprimary,secondary,orsubsequentformofattack ifmorethanoneIEDwasutilisedorintendedtobe utilisedinasequentialmanner.Primaryisused foranIEDassessedasthemosttactically signifcantIEDwithinanincidentwhileasecondary IEDreferstoanyadditionalIED(s)usedtoattack individualsorvehiclesafteraninitialevent.22 Such IEDsshouldbeindependentofeachotherin termsofbeingunlinkedintheirexplosivetrainand fringcircuits.
AttackGeography
AdescriptionofthelocationofanIEDattackproviding insightsintohowtheterrainwasemployedtobringthe deviceandtargetintoproximity,optimisethemoment ofinitiation,sloworcanalisetargetmovement,channel tacticalresponsestotheattack,orhinderthepursuitof theattacker.23 Attackgeographycanbebrokendown undertheheadingsof:
DevicePlacementCharacteristics
◦Deviceplacement–canincludesubsurface,24 surface,25 elevated26 andembedded27
◦Devicedistancetotargetatinitiation
◦Concealmentatcontactpoint
◦Angleofattack28 –considerinwhichdirection wasthedevicepointed/orientatedandwhy.This describesthepartofatargetthatanIEDis designedtoattack.Itcanincludeunderbelly,29 topattack,orside-attack.
ContactPointCharacteristics
◦Contactpointdescription–keyfeaturesand notableaspectsofthesurroundings
◦Routesinlocality–importantinassessingthe ingressandegressoftheattackerfordevice emplacement
◦Obstaclesinlocality–importantinassessingthe abilitytopursueanattackerandtheirlevelof groundappreciationinplanninganattack
22Source:Adaptedfrom, TheIEDIncidentReportingGuide,6thEdition
23Source:Adaptedfrom, TheIEDIncidentReportingGuide,6thEdition
24AlsoreferredtoasburiedIEDs,referringtoIEDsemplacedbelowthesurfaceatanemplacementlocation.BuriedIEDsare usuallyemplacedsubsurfacealongroutesagainstamovingtarget.
25SurfaceIEDsareemplacedontopofthesurfaceatanemplacementlocation.SurfacelaidIEDsmaybepositionedalongthe sidesofroutesofmovementandconcealedusingvegetation,rubbish,oranymaterialavailablewithinthevicinity.Insome cases,surfacelaidIEDsarehousedwithinspeciallyfabricatedoradaptedcontainersdesignedtomimicthenaturalor man-madefeaturesoftheirsurroundings – suchas“rockbombs”observedinSouthLebanonandYemen – pioviding enhancedcamoufageagainstdetection.ThecolloquialtermroadsideIEDsisoftenusedtodescribethistypeof emplacement.Broadly,surfacelaidIEDscanbeeitheromnidirectionalordirectional-effectIEDs.
26IEDsemplacedinaraisedpositionrelativetheintendedtargetandcaninvolvetrees,rooftops,bridgesoroverpasses. ElevatedIEDsareemplacedafterobservingtheroutineofthetarget.Theymaybepositionedonrooftopsofplaces frequentedbytargetgroups,suchasteashopsorcafésorothermeetinglocations.Additionally,theyareoftenplacedatop treeswheresecurityforcespauseduringtraveloruseasshadenearcheckpoints.Overpassesalongroutestravelledbythe targetarealsocommonplacementlocations.
27EmbeddedIEDsmaybehiddeninanyspacethatcontainsavoidorprovidesconcealmentfromview – suchasinsidewalls, streetfurniture,orlightposts.Theycanbeencounteredinbothurbanandruralenvironments.Theymaybedeployedagainst movingtargetsorplacedinlocationslikelytobeoccupiedbyatarget,suchasrestlocations,checkpoints,orbuildings.
28Alsoreferredtoasdeviceorientation.
29IEDemplacementintendedtotargettheundersideofavehicle.Source: TheIEDIncidentReportingGuide,6thEdition
CommandIEDSpecifcConsiderations
◦Firingpoint–distancetocontactpoint,lineof sighttocontactpoint,visibilityofapproachesto contactpoint,egressandingressrelativeto contactpointandescaperoute
◦Aimingmarker(s)–typeandlocation
◦Antennaorientationandlocation-importantfor anyRCIED
PostBlastData
◦Blastdimensionsintermsofcraterdiameterand depthalongwithdebrisfeldradius
◦Estimatednetexplosiveweightofcharge initiated
◦Blastcratermateriale.g.soil,sand,concreteetc
ConditionWhenFound
InsituationswhereanIEDisdiscoveredpriorto initiation,capturingitsreadinesstoinitiateisimportant inprovidinginsightintowhyasuccessfulattackwas notachieved.OptionstodescribethestatusofanIED whenfoundinclude,armed,unarmed,dormant, poised,non-functionalandmalfunction.
EnvironmentalConditions
Referstovariablessuchasweatherand oceanographicconditions,alongwiththosepresentin theelectromagneticandterrestrialenvironment.30 TheseconditionsmayimpacttheperformanceofIEDs, theeffectivenessofdetectionsensors,andthe successofcountermeasures.
Atmospherics
Adescriptionoftheenvironmentalmoodofanarea, includinghowitappears,sounds,feels,andsmells, comparedtoanestablishedbaselineforwhatis considered'normal.'Shiftsintheatmospherewithina communityorinindividualbehaviourmaysignal impendinghostileaction,suchasanIEDattack.
Indicatorsofsuchathreatcanincludenoticeable changesinanindividual’sbehaviour,changeinusual routines,patterns,andattitudesamongthelocal population,ortheemergenceofabnormalactivities. Whenconsideringatmospherics,itisinsightfulto consideriftherewasabsenceofthenormaland presenceoftheabnormalandifsowhy.31
SensorDefeat
Referstotechnologiesincorporatedintoadevice constructionaswellasmethodsusedtodefeattheir detection,identifcation,andC-IEDTTPs.32 Such technologiesmayrelatetothecomponentsusedand assuchthismaybecapturedunderthetechnical complexityofanIED.
AttachmentMethod
DescriptionofhowanIEDisplacedincontactwitha targetoritslocationofemplacement.Optionsinclude, magnetic,tied,mechanicalandadhesive.
Delivery
Wasthedevicestatic,mobileorlaunched/releasedin acontrolledoruncontrolledmannertowardsits intendedtarget?Optionsincludeemplaced,vehicleborne;animal-borne;person-borne(proxyor suicidebomber);standoff(ground-based/terrestrial, waterborne,andairborne);andpostalIED.
Domain
Characterisationofthephysicalenvironmentinwhich theIEDisemployedandcoversair,land,maritime surfaceandmaritimesubsurface.
EmploymentMethod
Akeydescriptorcontributingtotheoveralltactical characterisationofanIED,providingadescriptionof howadeviceandtargetwerebroughtinproximityof eachother.
30Examplesofterrestrialenvironmentdescriptorsincludeurban,rural,periurban,woodland,forest,jungle,desert,tundra, mountainous.Itcanalsodescribeterraincompositioninthelocalitysuchasthenatureofthesoil,sand,gravel,stoneorother groundmaterial.
31Source:Adaptedfrom, TheIEDIncidentReportingGuide,6thEdition
32Source:Adaptedfrom, TheIEDIncidentReportingGuide,6thEdition
DiscoveryMethod
Itisimportanttorecord,inasmuchdetailaspossible, informationrelatedtohowanIEDwasdiscovered,as thiscansignifcantlyassistininformingdefeat-the-device efforts,includinginvestmentinsearchanddetection capabilitiesandIEDDrender-safeprocedures.The methodofdiscoveryservesasatacticaldescriptorofan IEDincidentandcanincludevisualobservation,working animal(e.g.,dogs),searchanddetectsensors,and humantip.
CONCLUSION
A5W+HanalysisofIEDattacksenablesa comprehensiveunderstandingofthethreat.This analyticalapproachinformsthedevelopmentoftools usedtodesign,developandmaintainanaccurateIED threatpicture.UnderstandinghowIEDattacksoccur requiresclassifcationbasedoneitherorbothoftheir tacticalemploymentandtacticalcharacterisation. Tacticalcharacterisationinvolvesexaminingthe tacticalintentandtacticaldesignofattacks.Toensure consistentandsystematicdatacapture,standardised reportingformatsmustbeimplementedatthelowest tacticallevel.Thisreportingshouldincludevarious tacticalidentifersdocumentedforeachIEDincident. Threeanalyticalmethodscansupportthetactical characterisationofIEDattacks:
•3Ysand2Outcomesmodel
•IDREADanalysis
•TRACE-AS-ADDEDframework
Thesemethodscanbeusedindividuallyorin combination.However,relyingsolelyononeanalytical methodisdiscouraged,‘certainIEDscanfallunder multiplecategories,dependingontheperspectiveor thelensthroughwhichtheyarebeingexamined.’ 33,34
Thenextarticleinthisserieswillexploretheconcept ofIEDtacticalprofleandtacticalsignaturestosupport ourunderstandingofthetacticalsophisticationofan IEDthreat.■
ABOUTTHEAUTHOR

PaulAmoroso isanexplosive hazardsspecialistandhasextensive experienceasanIEDThreat MitigationPolicyAdvisorworkingin EastandWestAfrica.Heservedin theIrishArmyasanIEDDisposal andCBRNeoffcer,uptoMNT level,andhasextensivetactical, operational,andstrategicexperienceinPeacekeeping OperationsinAfricaandtheMiddleEast.Hehas experienceinthedevelopmentofdoctrineandpolicy andwasoneofthekeycontributorstotheUnited NationsImprovisedExplosiveDeviceDisposal StandardsandtheUnitedNationsExplosiveOrdnance DisposalMilitaryUnitManual.Heworksatpresentin theMENAregiononSALWcontrolaswellasinwider AfricaadvisingonnationalandregionalC-IED strategies.HehasaMScinExplosiveOrdnance EngineeringandanMAinStrategicStudies.Herunsa consultancy,AssessedMitigationOptions(AMO),which providesadvice,support,andtrainingdeliveryinEOD, C-IED,WAMaswellasPersonalSecurityAwareness Training(PSAT)andHostileEnvironmentAwareness Training(HEAT).Thisarticlerefectshisownviewsand notnecessarilythoseofanyorganisationhehasworked fororwithindevelopingtheseideas.
LinkedInprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/
33Source: IEDClassifcation–BreakingDownBombAttacks,TheCounter-IEDReport,Spring/Summer2025. 34MoreinformationonclassifcationmethodsandconsiderationofIEDsundermultiplesystems,especiallywhenaddressing complexdevicesispresentedin IEDClassifcation–BreakingDownBombAttacks,Counter-IEDReport,Spring/Summer2025.
INSIGHTSINTOIEDEMPLOYMENT
IEDTACTICALDESIGNPROFILESANDSIGNATURES
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy
INTRODUCTION
Continuingour5W+HseriesonIEDattacks, intendedtoprovideacomprehensiveunderstandingof theuseandthreateneduseofIEDs,havingpreviously exploredtheirtechnicalaspects,1 thisarticlecontinues ourexaminationofhowthesedevicesareemployed. Thepreviousarticleinthisseries,examinedhowIEDs areemployedthroughtheuseoftacticalidentifers allowingclassifcationbytacticalemploymentandby tacticalcharacterisation.Tacticalcharacterisationof IEDattacksinvolvesassessingtheirtacticalintentand tacticaldesignforwhichthreemeansofanalysiswere presented:3Ysand2Outcomes,IDREADanalysis
andtheTRACE-AS-ADDED2 framework.Buildingon thefoundationlaidin ExploringIEDEmployment–Understandingthe‘How’ofIEDAttacks,3 thisarticle examineshowtacticaldesignproflesandIEDtactical signaturescanbedeveloped.
Thenextarticleinthisserieswillexplorehowtactical designproflescanbeintegratedwithotherC-IED analysisproductstoproduceIEDincidentprofles. Overtime,whentheseproflesaresubjectedtopattern andtrendanalysis,theycanbeusedtoassessthe tacticalsophisticationoftheIEDthreat.Ultimately, evaluatingthetacticalsophisticationoftheIEDthreat
1 AJourneyThroughPIECESofSPICEPIES,TheCounter-IEDReport,Spring-Summer2025. 2Acronymfor,Tacticalintent;Role;Attackgeography;Conditionswhenfound;Environmentalconditions;Atmospherics;Sensordefeat;Attachment method;Delivery;Domain;Employmentmethod;andDiscoverymethod.
3 ExploringIEDemployment–understandingthe‘how’ofIEDattacks,TheCounter-IEDReport,Spring/Summer2025.
informsthedesign,development,andcontinuous refnementofanaccuratethreatpicture.4 Webeginby examiningtheneedtostrikeabalancebetween recognisingthetacticaluniquenessofindividualIED incidents,identifyingevolvingcommonalitiesthrough patternrecognition,anddetectinginevitablechanges inIEDtacticalemploymentovertime.
FINDINGTHERIGHTBALANCE-TACTICAL DESIGNPROFILES,SIGNATURES,ANDTHE EVOLVINGIEDTHREAT
Effectivelyassessingandcommunicatingthetactical sophisticationofanIEDthreatinvolvesusingtactical designproflesforindividualincidentsandtactical signaturesforclustersofincidentsthatshare commonalitiesintactics5 employed.Thisprocess requiresanunderstandingoftheimprovisedand adaptablenatureoftheseattacks.IEDattacksdonot followfxedtemplates.Instead,theyrefectcontextspecifcnuancesshapedbythetypeofIEDbeing employed,thetacticalintentbehinditsuse,andthe environmentalfactorspresentattheattacklocation. Attemptstoimposerigidtemplateswhenanalysing IEDtacticalemploymentriskoverlookingkey variationsandtheinherentnuancesofhowIEDsare usedinindividualattacks.Eachincidentisuniqueand context-specifc,sotheheadingswithinatactical designproflemayvarytorefectthespecifcdatathat needtobecaptured.Despitetheseinevitablenuances, recurringpatternsinIEDemploymentoftenemerge overtime,revealingcommonalitiesacrossincidents withinagiventhreatenvironment.Similartactical patternstendtoarisewhenIEDattackerspursuethe sameobjectiveswithincomparableenvironments. Thesesharedconditionsconstrainavailableoptions andpromotetheuseofprovenmethods,resultingin recurringtacticsacrossincidents.Tacticalsignatures areusedtocaptureandcommunicatetheseshared commonalitiesinIEDtacticalemploymentacross multipleattacks.
OncesuchcommonalitiesinIEDemploymentare identifed,effortscanbeinvestedtocounterthetactics identifed. This,inturn, typicallyforces theIEDsystem tochangethe technicalcomplexityoftheirdevicesand thetacticalsophisticationoftheirattacks. Thisdynamic playsoutasa“catandmouse”interaction,more formallydescribedasanaction–reaction–counteraction cycle,betweenIEDattackersandtheC-IED community.
Thisinevitableevolutioninthethreatrequiresthat changesbedetectedandtacticalsophistication assessmentsupdatedthroughamendedtactical signatures.Tacticalsignaturesmustthereforebe updatedregularly,tailoredtotheoperatingcontext,and supportedbyreal-worldexampleswhenpossible.They shouldalsobemanagedunderappropriateinformation securityprotocolsanddisseminatedinatimely, targetedmannertothosewhoneedthemmost.Striking therightbalance,betweenrecognisingtheuniqueness ofindividualincidents,trackingevolvingtactical commonalitiesacrosscertainincidents,andmonitoring trendsovertimetodetectchanges,isessentialto understandinganIEDthreat’stacticalsophistication.
TACTICALDESIGNPROFILES
Tacticalidentifersrefertotheobservableandinferable tacticalfeaturesofhowanIEDattackisplannedand executed.Theydescribehowanattackeremployed,or intendedtoemploy,adeviceinrelationtothetarget, withinthecontextoftheoperationalenvironmentand localfactors,toachievetheintendedtargeteffect. Theseidentifersarederivedfromanalysingtactical factorssuchasdeliverymechanism,placement,useof terrain,initiationmethod,coordinationofattackcycle elements,andtheconcealmentemployed. Tactical designproflescanbedevelopedusingoneormoreof thethreeprimarymethodsfortacticalcharacterisation: the3Ysand2Outcomesapproach,IDREADanalysis, andtheTRACE-AS-ADDEDframework.Theymaybe appliedindividually,incombination,orselectively.
4AnIEDthreatpictureisanassessmentoftheuseorthreateneduseofIEDsintermsofthetechnicalcomplexity,tacticalsophistication,theIEDsystem employingthemandlocalcontext.TheIEDsystemisassessedunderitsintent,capabilitiesandtheopportunitiesithastoemployIEDsagainstdefned target(s).Localcontextisdefnedbyageographicarea,thetargetoftheattacksandotherlocalfactors.
5Carefullyconsideredactionsintendedtoachieveaspecifcaim.
Comparisonofthethreemethodsthatcanbeadopted,adaptedorcombinedtoconstructtacticaldesignprofles.
Aprocessbywhichtacticaldesignproflescanbedeveloped.
IEDTACTICALSIGNATURES
Whentacticalidentifersareconsistentlygatheredon sceneandanalysedoffsite,andtheresultingdatais systematicallycompiledunderstandardisedheadings withintacticaldesignproflesandenteredintoan appropriateInformationandKnowledgeManagement (IKM)system,effectivepatternandtrendanalysis becomespossible.Overtime,structuredanalysisofIED tacticalidentiferdataacrossmultipletacticaldesign proflesenablestheidentifcationofrecurring characteristicsinIEDdeployment.These characteristics
revealhowIEDsareplanned,delivered/emplacedand executedinrelationtovaryingoperationalcontexts.The recurringtacticalcharacteristicsidentifedthroughthis processinformthedevelopmentofinformal,yetoften insightful,descriptiveIEDtacticalsignatures.IEDtactical signaturesarenarrativetoolsthatprovideinsightsinto specifcobjectives,modusoperandi6 andothertactical behavioursofnetworkswithinagivencontext.In contrasttothemoresystematicandformulaictactical designproflesusedforindividualIEDattacks,tactical
6Methodofoperation;styleofhandlingthings.Source:St.Andrew’sUniversity,Certifcate/AdvancedCertifcateinTerrorismStudies,TerrorismGlossary.
signaturesofferafexibleandintuitivemeansof expressingattackerintentandtacticalbehaviouracross multipleincidents.Byhighlightingkeytactical characteristicsobservedacrossincidents,tactical signaturespresentacontextualoverviewoftactical designstailoredtospecifcobjectives.When systematicallydevelopedandsupportedbypractical examples,theyserveaspowerfulcommunicationtools withintheCIEDcommunity.
Thesesignaturesprovideameansofassessingthe tacticalsophisticationoftheIEDthreat.Onceestablished, monitoringIEDtacticalsignaturescollectivelyovertime throughtrendanalysishelpsrevealshiftsinthethreat, includingescalationinviolenceandadaptationsin responsetocountermeasures.Subsequentpattern analysisallowstacticalsophisticationassessmentstobe updatedaccordingly.This,inturn,supportstimely amendmentstotheIEDthreatpicture,ensuringit remainsaccurateandinformative.
Together,patternandtrendanalysisoftactical designproflesofferinsightsintoattackerintent,
capabilityandtacticalsophistication,directly contributingtoC-IEDunderstandinganddecision making.Theseanalyticalapproachessupport proactivethreatmitigationandpreventative operations.Theexamplesprovidedbelowillustrate howIEDtacticalsignaturescanbedevelopedtorefect specifcoperationalcontextsandthreatenvironments. ThesesignaturesaimtoconveyhowIEDsmaybe employedtactically;however,itisemphasisedthatfor agiventhreatenvironment,specifcIEDtactical signaturesneedtobedevelopedandupdatedover time.ItshouldbenotedthatsomecommonlycitedIED tactics,suchassecondaryIEDs,suicideIEDsand proxyIEDs,arenotincludedinthisselection.In particular,secondaryIEDsareconsideredmore refectiveoftheIEDrole7 withinanattack,whichhas alreadybeenaddressedasatacticalidentifer.8 Inthe caseofsuicideIEDs9 theyarenotoutlinedhereasa standalonetacticbutarecoveredwithintheIED tacticalsignaturesofSVBIEDattacksonconvoysas wellasbreachingusingPBIEDorSVBIED.Finally,
ProcessbywhichIEDtacticalsignaturescanbedevelopedovertime.
7DesignatinganemplacedIEDasaprimary,secondary,orsubsequentformofattack.PrimaryisusedforanIEDassessedasthemosttactically signifcantIEDwithinanincidentwhileasecondaryIEDreferstoanyadditionalIED(s)usedtoattackindividualsorvehiclesafteraninitialevent.Source: Adaptedfrom, TheIEDIncidentReportingGuide,6thEdition
8See ExploringIEDEmployment–Understandingthe‘how’ofIEDattacks,TheCounter-IEDReportAutumn2025.
9Inapreviousarticle,theauthorsetouttheargumentthatsuicideIEDsareaspecialcategoryofcommandIEDs;however,acknowledgedthatinsome systemstheyareconsideredaseparatemethodofIEDactuation. IEDClassifcation–BreakingDownBombAttacks,TheCounter-IEDReport,Spring/ Summer2025.
proxyIEDs10 havepreviously11 beenconsideredasa subsetofsuicideIEDs,whicharethemselvesclassifed asaspecialtypeofcommandIED.However,thisdoes notprecludethedevelopmentofIEDtacticalsignatures forsecondary,suicideandproxytacticswhensuch employmentiscommoninagiventhreatenvironment.
AreaDenialIEDs
ThisinvolvestheuseofIEDsinasimilarmannertothe employmentoflandminesandconventionalboobytraps. SuchIEDtacticshavebeenseeninIraqandSyriaaswell asinSomalia.Typically,themainchargeisburiedclose toavictim-operatedswitchandleftunattended.Area denialIEDsmaybedesignedforuseagainstpersonnelor vehiclesandmaybeplacedsinglyalongacanalised routeorinmultiples.Theymayalsobeemplacedinurban spaces,routesandapproachestoknownareasatarget islikelytouseandcanoftenbeindiscriminateintheir targeting.Multipledevicesmaybelaidtoincreasethe probabilityofastrike,ortheymaybesitedassecondary IEDstoattackpersonnelrespondingtoaninitialstrike.
CommandIEDAmbushes/ComplexAttackson MobileTargetsPossiblyUsingSpotters
CommandIEDscaninitiateanambushorbedeployed afteranambush hasbeentriggered byothermeans,such assmallarmsorlightweapons(SALW)fre.Theseare oftenreferredtoascomplexattacks.Typically,aburiedor concealedsurfacelaidIEDisplaced12 alongaknown routeoftravelofavehicleconvoy,patrol,oratarget movingonfoot.Suchattacksmayincorporatetheuseof spotters,dependingonthelineofsightfromthefring
pointtothetarget’sapproachroutetothecontactpoint. Spottersareoftenpositionedatelevatedorconcealed vantagepointswithinthesurroundingarea,taskedwith observingpotentialavenuesofapproach.13 Dependingon thetypeofIEDbeingused,thespotterprovidesasignal tothetriggermantopreparetoinitiatetheIEDorremotely armaVOIED.Whenthetargetreachesthecontactpoint, theambushisinitiated.Thegoalistokillorinjurethe target,damagevehicles,orrenderthemimmobilewithin theambush'skillzone.Moreadvancedtacticsmayaimto blockthetarget'sextractionorwithdrawalrouteby targetingtheleadand/orrearvehicle.Oncetrappedinthe killzone,thetargetmaybefurtherimmobilisedby secondaryanti-vehicleoranti-personnelIEDsplacedin thesurroundingarea.SALWarethenoftenusedtoattack thefxedtargetwithinthekillzone.
Come-on/LureIEDs
Anattackermaydrawatargetintocloseproximityofthe lethalradiusofanIEDbyattractingtheirattentionor arousingtheircuriositybyplacingavaluable,attractive, familiarortacticallyimportantobjectneartheIED. Trophiessuchasfags,andotheritemsofinteresttothe intendedvictimarelefttobeseenandpickedupbutare boobytrappedwithavictimoperated fringswitch. Familiaritemsofequipmentsuchasrifemagazines, radiobatteries,torchesandwaterbottlesoftendonot arousesuspicionbecausetheylookasthoughthey weredropped,anditisnaturaltorecoverthem.Inmore sophisticatedcome-onIEDattacks,aconspicuousIED, weaponsystem,orcorpseisdeliberatelyleftinplain sighttoluresecurityforcesintoaspecifcareafor
10WhenasuicideIEDisdeliveredbyanindividualwhohasbeencoercedintocarryingouttheattackorisunknowinglytransportingthedevicetoitstarget, itisclassifedasinvolvingaproxybomberratherthanasuicidebomber.Thelevelofcontrolandassuranceofsuccesswithproxybomberscompared tosuicidebombersislower,asthepersondeliveringthedevicemaynotactasdirected,orifcarryingthedeviceunwittingly,mayactinanunplanned manner. IEDClassifcation–BreakingDownBombAttacks,TheCounter-IEDReport,Spring/Summer2025.
11Inthepreviousarticle IEDClassifcation–BreakingDownBombAttacks,TheCounter-IEDReport,Spring/Summer2025,theauthorconsidered consideringsuicideIEDsinvolvingeithersuicidebombersorproxybombers,asaformofcommandIED;however,somesystemsconsidersuicideIEDs asaseparatemethodofIEDactuation.
12CommandIEDambushesareoftenreferredtoascomplexattacksastheyinvolvecoordinateduseofmultipletactics,suchascombiningsmallarms, IEDs,vehicleattacks,andsuicideoperations,oftentargetingbothpeopleandinfrastructure.Theyrequirehigherlevelsofplanning,synchronisation,and resources.However,thistermisalsousedandconnectedtomaraudingterroristattacks.MoreinformationonthisisprovidedintheIEDtacticalsignature ‘BreachingUsingPerson-BorneandSuicideVehicle-BorneIEDs’belowinthisarticle.
13Spottersmayalsobeemployedovertimetomonitorthebehaviourofsecurityforces,withtheintentofexploitingobservedpatternsaspartofTTP (tactics,techniques,andprocedures)identifcation.Theirrolecanincludegatheringintelligencetoinformattackplanning,understandingsecurityforce tactics,anddirectlyassistingintheexecutionofIEDattacks.Additionally,spottersmayrecordattacksformessagingpurposesorusethefootagefor trainingandtheongoingrefnementoftacticsthroughalessons-learnedprocess.
recovery.In suchcases anunseenIEDisemplacedto targetthesecurityforces.Suchcome-onincidentsmay involveinformationbeingprovidedtothesecurityforces aboutthelocationoftheseitemsorplacingthemina locationwheretheyareintendedtobediscovered. Finally,emplacingaVOIEDorcommandIEDatthe fringpointofanattackorthelaunchpointofastandoff IEDisanotherexampleofacome-onIEDattack.Inthis case,theattackerknowssecurityforcestypicallymove tosearchandexploitsuchlocations.Come-onIEDscan harassandsignifcantlydegradeconfdencebyinstilling fearinsecurityforcemembersleadingtohesitationin actionresultinginadecreaseinthetempoandprogress ofoperationalactivitiesasoperatinginsuchthreat environmentsneedstobedonewithextremecaution.
ReoccupationIEDs/Boobytrapping
VOIEDsmaybepositionedatknownsecurityforce locationstoexploitthelikelihoodthatthesepositions willbereoccupiedinthenearfuture.Thistactic typicallyoccursintwoways:
•Predictableoccupationpatterns–Securityforce locations,suchasobservationposts,checkpoints, orstand-topositions,mayonlybemannedduring specifc,oftenpredictabletimesandleft unattendedatothers.
•Post-overrunreoccupation–Asecurityforceposition maybeoverrun,withtheexpectationthat reinforcementswillcounterattackandreoccupythesite.
Inbothscenarios,concealedIEDsareemplacedto killorinjuresecurityforcesenteringthearea.This tacticiscomparabletoboobytrappingfghtingpositions inconventionalwarfare – designedtoinfictcasualties onattackerswhensuchpositionsareabandonedor captured.TheuseofreoccupationIEDscan signifcantlyunderminetheconfdenceofsecurity forcesmovingtooccupytheselocations.
CoordinatedIEDAttacks-MultipleIEDAttacksat aGivenTimeandArea
AttackerscanorchestratemultipleIEDincidentsat differentlocationssimultaneously,exploitingthelimited resourcesofsecurityforces.Whilesecurityforces mightmanagetorespondtoseveralincidentsinquick succession,handlingmultipleincidentsatthesame timeposesasignifcantchallenge.CoordinatedIED attacksarehighlydisruptive,instillingfearamongthe localpopulationandphysicallyandpsychologically strainingtherespondingsecurityforces.Theseattacks oftencombinerealIEDswithhoaxdevices,whichare easiertoprepareandfurthercomplicatethesecurity forces'responseefforts.
HoaxIncidents14
Hoaxincidentsinvolveincompletedevicesormaterials designedtoresembleanIED.Theirpurposeisto provokeasecurityforceresponseorinstilfearina targetgroup,therebydeterringbothsecurityforcesand thetargetgroupwhilegraduallyunderminingmorale. Theseincidentsmayalsodisruptdailyactivitiesinthe targetlocationandchallengethelegitimacyof governingauthorities.Hoaxincidentscanfunctionas partofbroadercoordinatedIEDattacksorconstituteall theincidentsinacoordinatedseriesofdisruptive events.Additionally,attackersmayusehoaxesto monitortheactionsofrespondingsecurityforcesas partofTTPidentifcation.Hoaxesenableattackersto achieveobjectiveswithminimaleffortcomparedto constructingandemplacingrealIEDs.
Spoofng15
Avariationofthehoaxtactic,spoofngisdesignedto triggerafalsepositiveindicationofanIEDbythe searchproceduresorequipmentbeingused.Itmay involveexploitingvisualsearches,workinganimals,or search-and-detectionsensors,byfalselyprovidingan
14HoaxIEDincidentsaredifferentfromfalseIEDincidents,whichrefertoanincidentincorrectlyidentifed,thoughreportedingoodfaith,asanIED,which issubsequentlycategorisedasafalsealarmafterpositiveEODaction.FalseIEDincidentsaresometimesreferredtoasfalsealarms.
15Spoofng,whenusedasanIEDtactic,differsfromitsapplicationinelectronicwarfare,wheredeceptivesignalsaretransmittedtomisleadormanipulate targetedsystems.Forinstance,fakesignalsmaymimiclegitimateones,trickingthetargetedreceiverintoacceptingandactinguponfalsedata.For example,GPSspoofng,aspecifcformofelectronicwarfare,involvessendingcounterfeitGPSsignalstomisleadnavigationsystems.Additionally, spoofnginelectronicwarfarecanbeemployedtoanalysetheresponseofthetargetedsystem,similartoTTPidentifcation.Thesetacticsareextensively usedindroneandcounter-dronewarfareandareincreasinglyobservedintheIEDdronenexus.
indicationofthepresenceofanIEDcomponent.It typicallyinvolvescontaminatingalocationwithitemsor materialsthatgenerateafalsepositiveresponsefrom thesearchprocedureorequipmentinuse.Thegoalis toprovokearesponsefromsecurityforceswhena falsepositiveisdetected.Thisdelaysthesearch process,disruptsoperationaltempo,andgradually erodesconfdenceinproceduresandequipment. Moreover,spoofngoftenleadssecurityforcesto repeatedlydeploycountermeasuresandequipment, whichwhencombinedwithspotters,cansupportTTP identifcation.
TrojanHorseIEDs
TrojanhorseIEDsinvolveanIEDdelivered surreptitiouslybysomeoneunwittinglytoatarget.They areoftenhiddenwithinitemsexpectedtobebroughtto thetargetlocationbyauthorisedindividuals.Theseitems mightholdforensicorintelligencevalueorbeconsidered amementoortrophy.AparcelIEDsentbymailorcourier deliveryserviceisavariationofatrojanhorseIEDtactic.
SuicideVehicle-BorneIED(SVBIED)Attackson Convoys
SVBIEDsareusedtostrikeconvoys,patrols,orhighvaluetargetsintransit.Theirmobilityallowsattackers todeliverlargechargeswithprecisionbyclosing distancetothetarget,oftenbypassingfxeddefences. Thistacticmergesmanoeuvrabilitywithlethality, enablingtheattackertoguidethedevicedirectlytoits objectivewhilecarryingapayloadfargreaterthanthat ofmoststaticIEDsorPerson-BorneIEDs(PBIEDs). Duetothecomplexityinvolvedinplanning,resourcing, andexecutingsuchattacks,SVBIEDsaretypically
consideredhigh-valueassetsandareemployed sparinglybywell-organisednetworks.
Breaching16 UsingPerson-BorneandSuicide Vehicle-BorneIEDs
PBIEDandSVBIEDcanbeemployedtobreachthe defencesofsecurelocations.Thisisoftentheinitial actionthatenablesotherattackerstoenterthesecure locationaspartofacomplexattackormarauding terroristattack.17 Follow-upattackersexploitingthe breachmayincludeadditionalSVBIEDs,person-borne suicidebombers,orassaultinfantryequippedwith SALWsystemssuchasvehicle-mountedheavy machineguns,rifes,handgrenades,orself-propelled grenades.
Messaging/PropagandaandInfuencing
KeyobjectivesofIEDattacksoftenincludeinstilling fearinatargetedgroup,underminingrulingauthorities, and/orgainingthesupportofasegmentofthelocal populacethroughademonstrationofpower.Allof theseobjectivestypicallyinvolveelementsof propagandatoconveytheintendedmessage.Some IEDattacksmaybesymbolic,designedtosenda messagetospecifcgroupsandinfuencetheir perceptionsoractions.Suchmessagingcaninvolve issuingstatementsafteranIEDattack,sometimes accompaniedbyfootageshowingthepreparationand executionphases.Incertaincases,thismaterialis highlyprofessionalanddistributedthroughvarious channels.Theadventofsocialmediahasdramatically amplifedthereachandspeedofsuchpropaganda. Footagemayincludeimagerycapturedbyspotters, drones,orbody-worncameras.
16BreachingisanexampleofaclassofIEDattackbasedontargeteffect.See IEDClassifcation–BreakingDownBombAttacks,TheCounter-IED Report,Spring/Summer2025.
17 Complexattacksandmaraudingterroristattacks(MTA)sharemanyoverlappingfeatures,buttheyarenotalwayssynonymousbutexistonaspectrumof coordinatedviolenttactics.MTAtypicallyrefersto“fast-moving,violentincidentswhereassailantsmovethroughalocationaimingtofndandkillorinjure asmanypeopleaspossible.” A MTAcaninvolveloneattackersorcoordinatedgroups,andmayincludetheuseoffrearms,bladedweapons,explosives, oracombinationofthese.The2008Mumbaiattacksand2015Parisattacksareoftencitedasexemplars.Complexattacks,ontheotherhand,involve coordinateduseofmultipletactics,suchascombiningsmallarms,IEDs,vehicleattacks,andsuicideoperations,oftentargetingbothpeopleand infrastructure.Theyrequirehigherlevelsofplanning,synchronisation,andresources.AMTAcanbeacomponentofacomplexattack.Forexample,a complexattackmightbeginwithanIEDdetonationtocauseconfusionorgainentrytoatarget,followedbymaraudinggunmentargetingfeeingcivilians orfrstresponders.Inthatsense,MTAsareoftennestedwithincomplexattacks,orviceversa,dependingonhowanattackisdesigned.NOTE:Complex attackisalsousedattimestodescribecommandIEDambushes.
Source:A.UKNationalProtectiveSecurityAuthority, https://www.npsa.gov.uk/emergency-incident-management/marauding-terrorist-attacks
UseofDronesinIEDAttacks
UncrewedAerialSystems(UAS)18 areaversatiletoolin supportofIEDattacks.Theycanservemultipleroles, includingintelligence,surveillance,reconnaissance, andtargetacquisition(ISTAR);functioningasplatforms fordeliveringexplosiveordnance;andenablingpostattackanalysisformessagingorfacilitatelessons learned.Theiraccessibilityandadaptabilityhavemade themafavouredassetnotonlyamongstateactors butalsonon-statearmedgroupsandcriminal organisations.Asaresult,theaerialdomainhas becomemoreaccessibleandactive,signifcantly reshapingIEDthreatenvironments.
AerialdronesmaysupportIEDattacksasan unarmedorarmedenabler.Forexample,aerialdrones maybeusedtosurveilorreconnoitreastaticlocation beingtargetedallowingintelligencetobegathered whichcaninformanattackplan.Duringanattack,aerial dronescanmonitorthetargetandassistinattack coordination.Forexample,aUAScanbeusedasan aerialobservationplatformforacoordinatorin communicationwithaSVBIEDorperson-bornesuicide bomber,toguidethemtowardbreachpointsorto opportunistictargetsastheyemergee.g.peoplefeeing anattackorsecurityforcesrespondingtoanattack.The sameaerialdronefootagecansubsequentlybeused formessagingandlessonslearnedpurposespost attack.Atthesametime,armedaerialdrones,todeliver itemsofexplosiveordnancetoatargethave transformedthethreatfromatwo-dimensionaltoa three-dimensionalchallenge.Traditionallayered defencesagainstIEDsnowneedtoaccountforvertical
threats,requiringprotectionnotonlyaroundatargetbut alsoaboveandoverit.Forexample,aerialdronescan nowbedeployedasobservationplatformsusingfrstpersonview(FPV)capabilitiesandequippedwith variousexplosiveordnancepayloads.Thesepayloads maybereleasedinfight,functioningasimprovised aerialbombs,orlaunchedfromthedroneitself. Alternatively,thedronemaybedirectedtocrashintoa target,atacticcommonlyreferredtoasakamikazeor one-wayattackdrone.Thiscombinationofobservation followedbytargetacquisitionandattackisakinto improvisedloiteringmunitions.Whatwasoncethe preserveofstateandmilitaryactorshasnowdevolved tothetacticalbattlefeldandaccessibletonon-state actorsandevencriminalgroupsoperatingincontested spaces.Assuchonemightspeakofarevolutionin militaryaffairs19 –butthistimeitisanimprovised revolution.20 Owingtothenexusbetweenthedualuse natureofmanyoftheUASusedandthereadily availableknow-howontheinternet,pandora’sboxis nowopenandcannotbeclosedtotheuseofaerial dronestosupportIEDattacks.
CONCLUSION
IEDtacticalproflesandsignaturesofferapowerful meanstosupportanunderstandingofthetactical sophisticationofanIEDthreat,providedtheyarecontextspecifc,updatedregularlytostaythreat-aligned,and illustratedwithreal-worldexampleswhenfeasible.Tobe effective,theyalsoneedtobehandledwithappropriate informationsecurityprotocolsanddisseminatedina timelyandtargetedmannertothosewhoneedthem
18Oftenreferredtocolloquiallybytheterm‘drone’whichhasbecomeawidelyrecognisedandinformaltermincommonuse;however,itisnotaprecise technicalterm.Droneisalsooftenusedcolloquiallyinthewaterdomain.UASinthiscontextistakentoincludeunmannedaerialvehicles(UAV)and remotelypilotedaircraftsystems(RPAS).
19Theinteractionbetweensystemsthatcollect,process,fuseandcommunicateinformationandthosethatapplymilitaryforcethathasenabledtheWest touseprecisionviolenceagainstitsfoesisknownastherevolutioninmilitaryaffairs.Source:Thelimitstorevolutionsinmilitaryaffairs:Mauriceof Nassau,thebattleofNieuwpoort(1600),andthelegacy”,byGeoffreyParker,Journalofmilitaryhistory71:2,2007,331-372.
20Throughouthistory,eacherahastendedtoviewinnovationsinwarfareasaformof‘revolution,’whetherduetoincreaseddestructivepowerora perceivedaffronttotraditionalmoralandculturalvalues.Warfarehasgraduallybecomemore‘total,’drivenbyforcessuchasstatecentralisation, expandedresourcemobilisation,technologicaladvancement,theapplicationofscientifcandrationalmethods,A enhancedmilitarydiscipline,andthe institutionalizationofmilitaryeducation.WhatsetstheriseoftheUAS–IEDnexusapartisitsdetachmentfromconventionalstatecontrol.Unlikeprevious militaryrevolutionsthatwereprimarilyshapedbystateactorsandformalmilitaries,thisshiftisincreasinglydrivenbynon-stateactorsandevencriminal networks.Despitethisdecentralization,itsimpactonthecharacterandconductofconfictisnolesssignifcant.
NOTE:A.Referenceto‘rationalmethods’highlightshowpreviouserasofwarfarewereshapedbyinstitutionallogicandstate-sponsoredinnovation, whereastoday'sshiftsaremorechaoticandgrassroots,yetstillhighlyimpactful.
AssessmentprocessofthetacticalsophisticationofanIEDthreat.
most.IEDincidentreporting,whichsupportstactical deviceprofleandtacticalsignaturedevelopment,allows foranassessmentofthetacticalsophisticationof anIEDthreat.
This,inturn,directlysupportsthedesign,development, andmaintenanceofanaccurateIEDthreatpicture, enablingtheC-IEDenterprisetobetterrespond,counter andideallypreventexistingandemergingIEDthreats.
ABOUTTHEAUTHOR
PaulAmoroso isanexplosive hazardsspecialistandhas extensiveexperienceasanIED ThreatMitigationPolicyAdvisor workinginEastandWestAfrica. HeservedintheIrishArmyasan IEDDisposalandCBRNeoffcer, uptoMNTlevel,andhasextensive tactical,operational,andstrategicexperiencein PeacekeepingOperationsinAfricaandtheMiddle East.Hehasexperienceinthedevelopmentof doctrineandpolicyandwasoneofthekey contributorstotheUnitedNationsImprovised ExplosiveDeviceDisposalStandardsandtheUnited NationsExplosiveOrdnanceDisposalMilitaryUnit
Aswecontinuethisseriesonthedesign,development andsustainmentofanIEDthreatpicture,thenextarticle willfocusonIEDtechnicalidentifersasthekeydataupon whichIEDtechnicalproflesandsubsequentIED technicalsignaturescanbedeveloped.TheuseofIED technicalsignaturestoassessIEDtechnicalcomplexity willalsobesetout.AmethodologybywhichIEDincident proflescanbedevelopedwillalsobeprovided. ■
Manual.HeworksatpresentintheMENAregionon SALWcontrolaswellasinwiderAfricaadvisingon nationalandregionalC-IEDstrategies.Hehasa MScinExplosiveOrdnanceEngineeringandanMA inStrategicStudies.Herunsaconsultancy, AssessedMitigationOptions(AMO),whichprovides advice,support,andtrainingdeliveryinEOD,C-IED, WAMaswellasPersonalSecurityAwareness Training(PSAT)andHostileEnvironmentAwareness Training(HEAT).Thisarticlerefectshisownviews andnotnecessarilythoseofanyorganisationhehas workedfororwithindevelopingtheseideas.
LinkedInprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/
IEDINCIDENTPROFILES
ByPaulAmoroso,anexplosivehazardsspecialistatAssessedMitigationOptions(AMO)consultancy
INTRODUCTION
Inthisongoingseriesexploringthedesign, development,andsustainmentofanaccurateIED threatpicture1 througha5W+Hanalyticalframework, wehavethusfarexaminedthe‘what’and‘how’ofIED attacks.Thisarticleconsolidatesinformationonthe ‘what,’referringtothetechnicalcomplexity2 oftheIEDs usedinanattack,andthe‘how,’referringtothetactical sophistication3 oftheIEDattackitself.Previous analysisofthe‘how’outlinedthedevelopmentof tacticaldesignprofles,basedonthetactical characterisationofIEDattacks.4 Thisprocessinvolved
identifyingtacticalidentifers5 toinforman understandingoftacticalintentandtacticaldesign, fromwhichtacticaldesignprofles6 canbedeveloped. Methodologiessuchasthe3Ys+2outcomes,IDREAD analysis,andtheTRACE-AS-ADDEDframeworkcan beemployedtosupportthisanalysis.Inthepreceding article,theuseofpatternanalysistorevealtactical commonalitiesacrossmultipleincidentswithinagiven threatenvironmentwasintroducedtosupportthe developmentofIEDtacticalsignatures.7 Tactical proflesandsignaturesofferapowerfulmeansof
1AnIEDthreatpictureisanassessmentoftheuseorthreateneduseofIEDsintermsofthetechnicalcomplexity,tacticalsophistication,theIEDsystem employingthemandlocalcontext.TheIEDsystemisassessedunderitsintent,capabilities,andtheopportunitiesithastoemployIEDsagainstdefned target(s).Localcontextisdefnedbyageographicarea,thetargetoftheattacksandotherlocalfactors.
2TechnicalcomplexityreferstothedetailedcompositionandarrangementofanIED’scomponents–Powersource,Initiator,Energeticmaterial, Container,Enhancements(ifpresent),andSwitches(PIECES)–aswellastheirconfguration,confnement,andconcealmentcharacteristicstoachieve adesiredtargeteffect.
3TacticalsophisticationreferstoanassessmentoftheabilityofanIEDattackertosuccessfullyemployIEDsinsupportoftheirintendedoutcome.
4TacticalcharacterisationofanIEDincidentexaminesboththe:
-Tacticalintent-intendedfunctionofthedevicei.e.theintendedimmediate,ordirecttacticaleffectofanIED.
-Tacticaldesign-planningandexecutionofIEDattacks.
ByprovidinginsightintohowIEDsareusedorintendedtobeused,tacticalcharacterisationhelpsassessthelevelofsophisticationbehindtheseattacks, whichisanessentialcomponentinanaccurateIEDthreatpicture.Source: ExploringIEDEmployment–Understandingthe‘How’ofIEDAttacks,The Counter-IEDReport,Autumn2025.
5TacticalidentifersrefertotheobservableandinferabletacticalfeaturesofhowanIEDattackisplannedandexecuted.Theydescribehowanattacker employed,orintendedtoemploy,adeviceinrelationtothetarget,withinthecontextoftheoperationalenvironmentandlocalfactors,toachievethe intendedtargeteffect.Theseidentifersarederivedfromanalysingtacticalfactorssuchasdeliverymechanism,placement,useofterrain,initiation method,coordinationofattackcycleelements,andtheconcealmentemployed.Source: ExploringIEDEmployment–Understandingthe‘How’ofIED Attacks,TheCounter-IEDReport,Autumn2025.
6TacticaldesignproflesofferastructuredandsystematicmethodofsummarisingthekeytacticalidentifersofanIEDattack.Tacticaldesignproflescan bedevelopedusingoneormoreofthethreeprimarymethodsfortacticalcharacterisation:the3Ys+2Outcomesapproach,IDREADanalysis,andthe TRACE-AS-ADDEDframework.Theymaybeappliedindividually,incombination,orselectively.Source: InsightsintoIEDEmployment-IEDTactical DesignProflesandSignatures,TheCounter-IEDReport,Autumn2025;
7IEDtacticalsignaturesarenarrativetoolsthatprovideinsightsintospecifcobjectives,modusoperandi,andothertacticalbehaviourswithinagiven context.Source: ExploringIEDEmployment–Understandingthe‘How’ofIEDAttacks,TheCounter-IEDReport,Autumn2025.
AssessmentprocessofthetacticalsophisticationofanIEDthreat.
understandingthetacticalsophisticationofanIED threat,providedtheyarecontext-specifc,regularly updatedtoremainthreat-aligned,andillustratedwith real-worldexampleswhenfeasible.Overall,IED incidentreportingthatsupportstacticaldeviceprofle andtacticalsignaturedevelopmentthroughthe systematiccaptureoftacticalidentifersenablesan assessmentofthetacticalsophisticationofanIED threat.Thisarticlewillexplorehowtacticaldesign proflescanbeintegratedwithotherC-IEDanalysis productstoproduceIEDincidentprofles.
Inapreviousarticle, AJourneyThroughPIECESof SPICEPIES, 8 aprogressivelydetailedexaminationof IEDcomponentswaspresentedusingPIES,SPICE, andPIECES.9 Eachservesasamemoryaidto supportsystematicproflingofIEDcomponents.
Thesemnemonicsrepresentincreasingly comprehensiveframeworksforIEDtechnical componentcategorisation,withPIESbeingthe simplest,followedbySPICE,andPIECESasthemost detailed.Thisarticlewilloutlinehowtechnical identiferscanbeusedtodeveloptechnicaldevice profles.Itwillthenexplainhowpatternanalysisof theseproflessupportsthedevelopmentofIED technicalsignatures.Overtime,whensubjectto structuredtrendandpatternanalysis,these signaturescanempowertechnicalcomplexity assessmentofanIEDthreat,akeycomponentofthe overallIEDthreatpicture.Intheconcludingsection,a methodologywillbepresentedfordetailedproflingof individualincidents.ThiswillinvolvedevelopingIED incidentproflesbyintegratingtechnicaldevice
8 AJourneyThroughPIECESofSPICEPIES,WhatComponentsMakeupanIED–TechnicalComponentClassifcation,TheCounter-IEDReport,Spring/ Summer2025.
9PIECESisanacronymforPowersources,Initiators,Energeticmaterials,Containers,EnhancementsandSwitchescomponentusedinIEDs.
proflesandtacticaldesignprofleswithtarget-specifc detailsoflocation,timing,andidentity.Webeginby examiningtheconceptoftechnicalidentifersaswe continueexploringhowtodesign,develop,and sustainanaccurateIEDthreatpicture.
TECHNICALIDENTIFIERS
TechnicalidentifersrefertoIEDcomponentsandtheir characteristicsi.e.confguration,confnementand concealment,thedetailofeachbasedonahierarchical construction.ThePIES,SPICE,andPIECES frameworksprovidesuitablemeanstodetailthe componentsinanIED.Theonechosendependson thetechnicalcomplexityoftheIEDsandthelevelof detaildesired.
ConfgurationcharacteristicsofanIEDreferto:
•Containerconfgurationtoproducedirected explosiveeffects10 whichareconsideredatypeof enhancement.11
•Thearrangementandinterconnectionofthe componentsandsubassembliessuchasthe explosivetrain12 andfringcircuit13 withinit,which canrevealcommonalitiesinthemethodsof assemblyemployedintheirconstructionbycertain bomb-makers,cellsornetworks.
Confnement,inthecontextofIEDs,referstothe explosiveeffect’scharacteristicsresultingfromthe physicalcontainmentofthemainexplosivechargeby theIED’scontainertodirectoramplifyitseffect.This restrictionsignifcantlyinfuencesthebehaviourofthe energeticmaterialuponinitiationandplaysacritical roleintheprogressionofthereaction – potentially enablingadefagration-to-detonationtransition(DDT),14
whichisacommonmechanismindevicessuch aspipebombs.
Concealmentcharacteristicsrefertotheuseof materials,objects,orenvironmentalfeaturesintended ‘topreventthediscoveryofanIEDbyvisual inspection.’15 Thesecharacteristicscanbecategorised intotwomaintypes:
•ConcealmentprovidedbytheIEDcontainer –TheIEDcontainermaybeinherentlydesignedor specifcallyselectedtodisguisethepresenceof thedevice.Insuchcases,thecontainerfunctions bothasastructuralhousingandasaconcealment mechanism.Examplesinclude:
◦ VBIED –hiddenwithinacar,truck,or motorcycle.Thevehiclemayappearabandoned, parkednormally,orloadedwitheverydayitems toavoidsuspicion.
◦ Electronicdevices -laptops,mobilephones,or cassetteplayersmodifedtohouseexplosive components.
◦ Packages –parcelswrappedfordeliveryor postedasmailmaycontainanIED,relyingon theappearanceofnormalpostalpackaginge.g. letter,parcelandpostalIEDs.
◦ Luggage –suitcases,backpacks,duffelbags, orrucksacksmaybedeliberatelyplacedatthe attacklocation.Theirfamiliarappearanceand integrationintotheenvironmentoftenrender theminconspicuous,minimisingsuspicionand reducingthelikelihoodofdetection.
◦ HouseholdItems –concealedinsideobjects chosenfortheirinnocuousappearancelike vacuumfasks,palmoilcontainers,radios,or toys.
10Atermusedtodescribeexplosiveeffectsproducedbytheinitiationofexplosivesinintimatecontactwithalinerwhichisprojectedforwardwithvarying effectsdependingonmanyfactorsresultingineithershapedchargejets,ExplosivelyFormedProjectiles(EFP)orplattercharges.
11 AJourneyThroughPIECESofSPICEPIES,WhatComponentsMakeupanIED–TechnicalComponentClassifcation,TheCounter-IEDReport,Spring/ Summer2025.
12Asuccessionofinitiatingandignitingelementsarrangedtocauseachargetofunction.Source:UNIEDThreatMitigationHandbook,SecondEdition 2024,AnnexA.IEDLexicon,A.6,Glossary(p.136)
13InthecontextofanIED,afringcircuitreferstoanimprovisedelectricalorpyrotechnicconfgurationdesignedtocausetheinitiatortofunction.Itmay includefringandarmingswitches,powersources,sensorsandassociatedwiring,confguredtoactivatethedevicebasedontheattacker’schosen method,suchascommand,time-delay,victimoperationorahybridcombinationofthese.Advancedconfgurationsmayincludeanti-handlingfeatures orfailsafetriggers.
14Transitiontodetonationfromaninitialburningreaction.
15Source: TheIEDIncidentReportingGuide,6thEdition
•Concealmentusingexternalmaterialfromthe emplacementlocation -materialsoritemsnot partoftheIEDitselfmaybedeliberatelyplaced around,over,ornearthedevicetoobscureitfrom vieworblenditintotheenvironment.Examples include:
◦ DebrisorRubbish –pilesofrubbish,discarded clothing,ordeadanimalsplacedoverroadside IEDs.
◦ Naturalcover –rocks,soil,vegetation,orsand usedtoburyorcamoufagethedevice.
◦ Infrastructureelements –guardrails,signposts, orstreetfurnituretohouseorhideanIED.
◦ Buildingfeatures –deviceshiddenbehindwall panels,underfoorboards,orinsideventilation ducts.
IEDTECHNICALPROFILES
IEDtechnicalidentifersformthebasisfortechnical categorisation.Technicalcategorisationreferstothe descriptionofanIEDusingahierarchicalconstructto identifyitskeycomponents.Thecomponentsidentifed inthiscategorisationaretheelementsfromwhich technicalandforensicinformationisrecoveredand exploited.16 ThePIES,SPICEandPIECESframeworks providebasicheadingsaroundwhichtechnical categorisationcanbeconstructed.Whichever frameworkandassociatedheadingsareused,“further classifcationispossible,leadingtoahierarchyof technology.”17 TheUNIEDThreatMitigation Handbook,SecondEdition2024,AnnexF,Glossary andIEDIncidentReportingGuide,6thEdition,January 2024,bothprovideexcellenthierarchicalconstructsfor whichIEDtechnicalcategorisationcanbeadoptedor adaptedtoagivenIEDthreatenvironment.This conceptofahierarchyoftechnologycanbeappliedto categorisingthecomponentsofIEDsbyorganising
themintolevelsbasedontheirfunctionality, complexity,andimportancewithinthedevice.18 This approachhelpsinsystematicallyanalysingand understandingIEDconstruction,providingastructured approachandclaritytotheirdiverseandimprovised natureofIEDcomponents.
ComponentFunctionality
ThisreferstotheroleacomponenthasinanIED enablingthedevicetooperateasintended.The PIECESframeworkheadingscanbeusedtolist componentfunctionality.Somecomponentsmayhave morethanonefunction.Forexample,acontainermay alsofunctiontoconfnethemainchargeintendedto causeadefagrationtodetonation(DDT)event,while containersmayalsofunctiontocreatecertain explosiveeffectssuchasdirectionalexplosiveeffects.
ComponentComplexity
IEDcomponentcomplexityreferstothetechnical sophistication,composition,andconfgurationof individualcomponentsorsubassemblieswithinan IED.ItincludesthePIECEScomponentsalongwith theirconfguration,confnement,concealment,and integrationwiththeothercomponenttoachievea desiredtargeteffect.Variousscalesofcomplexitycan bedefnedwiththemetricsusedneedingtobe interpretedwithintheoperationalcontexti.e.whatis complexinoneregionorthreatgroupmaybestandard inanother.Componentcomplexity,metricsmay includedesignfeatureconsiderationssuchas:
•Useofadvancedtechnologiese.g.microcontrollers,encryptedcomms
•DeviationfromknownIEDdesignssuchasnovel confgurationsorconcealment
•Levelofprecisionorcontrole.g.burningfuse comparedtoaprogrammabledelay.
16Source: TheIEDIncidentReportingGuide,6thEdition
17Theterm"hierarchyoftechnology"referstothestructuredarrangementorclassifcationofdifferenttechnologicalsystems,tools,orcomponentsbased ontheircomplexity,functionality,orimportance.Thishierarchyoftenhighlightstherelationshipbetweenfoundationaltechnologiesthatserveasbuilding blocksandmoreadvancedtechnologiesthatdependonorarebuiltuponthem.Source: AJourneyThroughPIECESofSPICEPIES,WhatComponents MakeupanIED–TechnicalComponentClassifcation,TheCounter-IEDReport,Spring/Summer2025.
18 AJourneyThroughPIECESofSPICEPIES,WhatComponentsMakeupanIED–TechnicalComponentClassifcation,TheCounter-IEDReport, Spring/Summer2025.
PIECESComponent LowComplexity HighComplexity
PowerSource
Initiator
EnergeticMaterial
Container
Enhancements
Switch
AAbatterypoweringasimplecircuit
Electricmatchorfusewire
Commercialpyrotechniccomposition
PVCpipeorplasticbottle
Nailsorballbearings
Pressureplateortoggleswitch
Examplesoflow-andhigh-levelcomponentcomplexity.
Complexitycanalsoapplytosubassembliesand theirdesignfeatureswithinanIED.Theindividual confguration,componentsandthenumberofsuch subassembliescanincreasethecomplexityofanIED.
Someconsiderationinclude:
•Firingcircuits-basicrelaycomparedtologiccontrolledmulti-pathcircuit
•Armingmechanisms-manualtoggleversus sensor-triggeredarmingwithdelay
Confgurationexamples
Rechargeablelithium-ionbatteries
Microcontroller-basedinitiatorwithmultistagearminglogic19
Highspecifcationmilitarygradehigh explosivee.g.RDXorHMX
Custom-milledshapedchargewith fragmentationsleeve
ThermobaricadditivesorCBRpayloads
Remote-controlledencryptedRFswitchwith anti-tamperlogic
•Explosivetrains-directinitiationincomparisonto stageddetonationwithboosters
•Numberofintegratedsubsystems,forexamplea remotelyarmedintegratedtimedelayfringsensor.
Complexityassessmentscanalsobeappliedto thethreecharacteristicsofIEDcomponentsof confguration,confnementandconcealment.These characteristicsinfuenceadevice’slethality,detectability anddefeatthedevicerendersafeoptions.
Simple Basicseriescircuit:battery→switch→initiator→explosive
Intermediate Parallelcircuitswithmultipleswitchesortimers
Complex Microcontrollermanagingmultipleinputsbeforefringe.g.GPS,RF,andtimer Confnementexamples
Simple Loosepowderinaplasticcontainer
Intermediate Pipebombwithendcapsandmoderateconfnement
Complex Shapedchargewithprecision-milledliner Concealmentexamples
Simple IEDplacedinabackpackorroadsidedebris
Intermediate Componentssecretedinvehiclevoidsordisguisedasinnocuousitems
Complex IEDintegratedintoconsumerelectronicitemse.g.laptopIED.
Examplesofincreasingcomplexityintheconfguration,confnementandconcealmentcharacteristicsofanIED
19Amicrocontroller-basedinitiatorisanelectronictriggeringsystemthatusesaprogrammablemicrocontrollertocausetheinitiatortofunction,allowing precisecontrol,sequencing,andconditionallogicbeforeinitiation.Onlyaftersetconditionsaremetdoesitactivatetheinitiator.
Aprocessbywhichtechnicaldesignproflescanbedeveloped.
ComponentImportance
Componentimportancereferstohowcriticala componentistoanIED’soverallfunctionoreffectiveness i.e.itsroleinenablingthedevicetoachieveitsintended outcome.Theexplosivechargeistypicallythemost importantcomponentintermsoflethality,butawellconcealedswitchmightbevitalforsuccessful employmente.g.ahiddenVOswitch.Alternatively,when thetacticalintentisanti-armour,apreciselyfabricated shapedchargeconemaybethemostimportant componentalongwithahigh-grademainchargewitha highvelocityofdetonation.Inthecaseofhoaxdevice someelementofthecontainerorsimplythepresenceof someelectroniccomponentsmaybemoreimportantso thatitcanbefoundtoelicitasecurityresponse.
TechnicalDeviceProfling
Technicaldeviceprofling20 referstothesystematic categorisationofIEDcomponents,21 alongwiththeir confguration,confnementandconcealmentcharacteristics.Itreferstotheprocessbywhichtechnical categorisationisundertaken,toproduceIEDtechnical profles.Assuch,atechnicaldeviceprofleforanIED incidentrepresentstheproductoftechnicalcategorisation.
TechnicalComplexityAssessments
Thepreviousarticleinthisseriesprovideda methodologyforthedevelopmentofIEDtactical signaturesthroughthepatternanalysisofmultipleIED tacticaldesignproflesovertime.Itoutlinedhow patternandtrendanalysisoftacticaldesignprofles offerameansofassessingthetacticalsophisticationof theIEDthreat.Asimilarmethodologycanbeapplied forthedevelopmentofIEDtechnicalsignaturesfrom whichovertimeIEDtechnicalcomplexityassessments arepossible.IEDtechnicalsignaturesrefertoclusters ofcommonalitiesintheIEDcomponentsandtheir characteristicsofconfguration,confnementand concealmentfoundinIEDsinuse.LikeIEDtactical designsignatures,whensystematicallydevelopedand supportedbypracticalexamples,IEDtechnical signaturesserveaspowerfulcommunicationtools withintheC-IEDcommunity.
Onceestablished,monitoringIEDtechnical signaturescollectivelyovertimethroughtrendanalysis helpsrevealshiftsinthethreat.Inparticulartrend analysisofIEDtechnicalsignaturescanrevealthreat escalationsthatcanmanifestthemselvesaslethality escalations22 orcomplexityescalations.23 Forexample,
20Theauthoracknowledgesthatsomereferences A usethetermsdeviceproflingandeventsignature(development)interchangeably.Theauthormakes adistinctionbetweentheseterms.Technicaldeviceproflingisusedinsteadofdeviceproflingtoreferonlytotheprocessbywhichtechnical categorisationisundertaken,toproduceIEDtechnicalprofles.While,eventsignaturedevelopment,referstoanalysingthetechnicalandtactical identifersofanIEDincidentsupportC-IEDunderstandingtointurninformC-IEDdecisionmaking.NoteA: TheIEDIncidentReportingGuide,6thEdition, andUNIEDthreatmitigationhandbook,2ndEdition.
21ThePIECESheadingscanbeadoptedoradaptedundertheappropriatehierarchyconstructoftechnicaldetailneeded.
22AnincreaseinthedestructivepowerorcasualtyratefromIEDattacks.
23AsystematicincreaseinthethreatposedbyIEDs,refectedinchangesincomponents,confguration,concealment,orconfnementcharacteristics.
ProcessbywhichIEDtechnicalsignaturescanbedevelopedovertime.
achangefromusingsmallnetexplosivecontent(NEC) devicestoIEDswithsignifcantlyhigherNEC,resulting inmorefatalitiesorsevereinjuriesperincident,isan indicatoroflethalityescalation.Complexityescalations typicallyrefectabroaderenhancementinthe adversary’soperationalcapability.Forexample, transitioningfromsimplevictim-operatedpressure platestomulti-triggereddevicesthatcombineradiocontrolledarming,low-metalcontentcomponents,and anti-handlingswitches.Suchcomplexityescalation demonstrateshowIEDnetworksevolvetheirsystemsto circumventdefeatthedeviceefforts.Trendanalysisof IEDthreatsignaturescanalsorevealthreat adaptations.24 Forexample,inasituationwherehighmetal-content,victim-operatedpressureplateshave bothresultedinunintendedvictimsaswellasbeing vulnerabletodiscoverybymetaldetectorsand subsequentlyrenderedsafe,atechnicaladaptation25
mightincludechangingtolow-metal-contentvariants armedwithradiocontrolandfttedwithanti-handling switches.AsC-IEDmeasuresadvance,IEDdesigns oftenevolvethroughmultiplestagesinacontinuous cycleofadaptation.Eachshiftrefectsanattemptto circumventthelatestcountermeasure.Forexample, victim-operateddevices,oncecommon,cangivewayto radio-controlledtriggerswhenattackersseekgreater standoffcapability.Subsequentlyasjammingdisrupts thesesystems,command-linkedconfgurationssuchas commandwirescanemergetoensurereliableinitiation. Insomecases,hybridconfgurations–suchas radio-armedvictim-operateddevices–canappearto combineremotearmingwithimprovedtargetselection. Thisprogressionisnotstrictlylinear,andearlier methodscanre-emergewhenconditionsfavourtheir use,underscoringthepersistent,adaptivenatureofthe threat.Together, patternandtrendanalysisofIED
24ThreatadaptationsinvolvereactivetechnicalortacticalmodifcationsmadeineffortstocircumventC-IEDcountermeasures.
25InC-IEDanalysis,asubtlebutimportantdistinctionexistsbetweencomplexityescalationandtechnicaladaptation.Complexityescalationreferstoa systematicincreaseinthethreatposedbyIEDs,drivenbychangesincomponents,confguration,concealment,orconfnementcharacteristics.These changestypicallyrefectabroaderenhancementintheadversary’soperationalcapability.Incontrast,technicaladaptationinvolvestargeted modifcationsmadeinresponsetospecifccountermeasures.Theseadaptationsmayalsoaffectcomponents,confguration,concealment,or confnement,butaregenerallymorelimitedinscopeandaredesignedtocircumventparticularC-IEDresponsesratherthanelevatetheoverallthreat level.WhilecomplexityescalationmaysignalastrategicevolutioninIEDdesign,technicaladaptationismoretacticalandreactiveinnature.
AssessmentprocessofthetechnicalcomplexityofanIEDthreat.
MethodologyforthedevelopmentofIEDincidentproflesfromtechnicalandtacticalidentifersalongwithtargetlocation, time,andtargetidentitydetails.
technicalsignaturesofferinsightsintothetechnical complexityofanIEDthreatwhichdirectlycontributes toC-IEDunderstandinganddecision-making. Technicalcomplexityassessmentsdirectlysupportthe design,refnement,andadaptationoftheIEDthreat picture,thusenhancingclarityaroundthespecifcIED threatbeingcounteredingivencontexts.
INCIDENTPROFILES
Byintegratingestablishedmethodsforcategorising IEDcomponentsandcharacterisingtacticalbehaviour, incidentproflesofferastandardisedapproachtothreat profling.Anincidentproflecanbeconstructedby combining:
•Technicalidentifers
•Tacticalidentifers
•Incidentlocation(wheretheincidentoccurred)
•Timing(whentheincidenttookplace)
•Targetinformation(whothetargetwas)
Technicalidentifersareobtainedfromthetechnical deviceprofle,whilethetacticalidentifersareobtained fromthetacticaldesignprofleofanincident.Further discussiononthewho,whereandwhenofIEDattacks willbeprovidedinsubsequentarticlesinTheCounterIEDReport.Thiscompositeprofleprovidesastructured waytorepresentandcompareIEDincidentsacross contexts.Itsupportsanalyticalconsistency,threat classifcation,consistentcommunicationofthreatsacross theC-IEDenterpriseaswellas,C-IEDplanningand response.
CONCLUSION
Withinthisarticle,theuseoftechnicalidentifers, specifcallyintermsofcomponentsandthe characteristicsofconfguration,confnement,and concealment,hasbeenshowntoprovidethe foundationaldatauponwhichIEDtechnicalproflescan beconstructed.IEDtechnicalproflescanvaryindetail andstructuredependingonthedataavailableandlevel ofinsightbeingsought.Theyaretypicallybasedaround thecomponentsinuseandtheirfunctionality. Componentimportancecanalsoberefectedwithina profle,withcomponentcomplexityoftenprovidingthe
mostinsightfuldata.Throughpatternanalysisof multipleIEDtechnicalproflesovertime,IEDtechnical signaturescanbedeveloped.Thesesignatures,when subjecttotrendandfurtherpatternanalysis,supportthe assessmentoftechnicalcomplexityoftheIEDthreat.
Thefusionoftechnicalcategorisationandtactical characterisationofanIEDincident,whencombined withtarget-specifcdetailssuchaslocation,timing,and identity,enablesthedevelopmentofincidentprofles. Theseproflesofferastructuredmeanstorepresent andcompareIEDincidentsacrossoperational contexts.Thenextarticleinthisserieswillexplorehow analysisofIEDincidentproflescansupportatechnical/ tacticallevelunderstandingoftheIEDthreat.■
ABOUTTHEAUTHOR

PaulAmoroso isanexplosive hazardsspecialistandhas extensiveexperienceasanIED ThreatMitigationPolicyAdvisor workinginEastandWestAfrica.He servedintheIrishArmyasanIED DisposalandCBRNeoffcer,up toMNTlevel,andhasextensive tactical,operational,andstrategicexperiencein PeacekeepingOperationsinAfricaandtheMiddleEast. Hehasexperienceinthedevelopmentofdoctrineand policyandwasoneofthekeycontributorstotheUnited NationsImprovisedExplosiveDeviceDisposal StandardsandtheUnitedNationsExplosiveOrdnance DisposalMilitaryUnitManual.Heworksatpresentin theMENAregiononSALWcontrolaswellasinwider AfricaadvisingonnationalandregionalC-IED strategies.HehasaMScinExplosiveOrdnance EngineeringandanMAinStrategicStudies.Herunsa consultancy,AssessedMitigationOptions(AMO),which providesadvice,support,andtrainingdeliveryinEOD, C-IED,WAMaswellasPersonalSecurityAwareness Training(PSAT)andHostileEnvironmentAwareness Training(HEAT).Thisarticlerefectshisownviewsand notnecessarilythoseofanyorganisationhehasworked fororwithindevelopingtheseideas.
LinkedInprofle: https://www.linkedin.com/in/paulamoroso-msc-ma-miexpe-60a63a42/
ANALYZINGEMERGINGWEAPONEFFECTS ONEXPOSEDINFRASTRUCTURES
ByMarcMenne,UniversityoftheBundeswehrMunich,InstituteforStructuralEngineering,Germany, marc.menne@unibw.de
Nothingillustratesacapabilitygapmoreclearlythaninstitutionalpowerlessness.
INTRODUCTION
Unmannedsystems(UxS) i arenolongerconfnedto warzonesbutareincreasinglypresentinthecivilian airspaceoverEurope.Germanyisnoexception. AccordingtotheBDLIexpertopinion1 onthecurrent stateofdronedetectionanddefenseinGermany (September2024),morethanoneinfourGerman companieshasalreadyreporteddrone-related incidents.Themostcommonlycitedrisksinclude illegaloverfightsofcriticalinfrastructure(87%)and espionageorinformationtheft(73%).
Assessmentsbysecurityauthoritiesandjournalistic investigationsii in2025paintaconsistentpicture.The numberofsuspiciousdronesightingsinGermany, particularlynearmilitaryinstallationsandsecurityrelevantsites,hasincreasedsharplysincethe beginningoftheRussianwarofaggressionagainst Ukraine.Whilesuchincidentswererelativelyrare before2022,severalhundredcasesiii were documented2 inthefollowingyears,withgrowing frequencyovershorttimeframesandinstrategically
sensitivelocations.Thispointstosystematic reconnaissanceactivitiesthatcannolongerbe attributedtocoincidenceorisolatedincidents.Inthe contextofthemilitarykillchain,comprisingFind,Fix, Track,Target,Engage,Assess3,suchdevelopments canbeinterpretedasanadvancedstageoftarget acquisition.Thetargetingphase,inwhichspecifc targetsareselected,appearstohavebeenreached,if notalreadycompleted.Thisrendersthetransitionto theengagephase,meaninganactualphysicalattack, nolongeranabstractriskbutarealpossibility.
Thatunmannedsystemsareindeedusedforthe physicaldestructionofinfrastructureisclearlydemonstratedbythewarinUkraine.Since2022,various typesofinfrastructurehavebeenrepeatedlyand deliberatelyattackedusingdronesorexplosivedevices4. Inadditiontotacticaltargetssuchasbridges5 ordepots, increasinglyoperationalnetworknodeshavecomeunder attack,assetswhosefailurecantriggerfar-reaching cascadingeffectsinbothcivilandmilitarysystems.
iInthisarticle,theterm"unmannedsystem"(UxS)isusedsynonymouslywithUnmannedAerialVehicles(UAV),unlessotherwisespecifed. iiReferringtoGermany.
iiiTheinformationisconsistentwithdatafromtheJointIntelligenceCenter
EvenwithinEurope,infrastructureattacksareno longeradistantthreat.Between2022and2025,more than50targetedsabotageactsagainstEuropean facilitiesweredocumented,accordingtoareportby theCSIS6.Theseincludedtransportationcorridors, governmentbuildings,andindustrialsites.Themajority oftheseattackswerecarriedoutusingexplosiveor incendiarydevices,oftenbelowthethresholdofstate attributionorformalresponse.
Thesedevelopmentsshowthatinfrastructuretoday isunderanovelandincreasinglyacutethreat.This articleaimstocontributetoabetterunderstandingand structuredassessmentofthesethreats,particularly withregardtoemergingweaponeffectsdeliveredby unmannedsystems.Thecentralquestioniswhat challengesthiscreatesforprotectionandwhatrole structuralprotectionshouldplayinthefuture.
EMERGINGTHREATS
Inrecentyears,unmannedsystemshaveevolvedfrom supplementaryreconnaissancetoolsanddelivery platformsintofully-fedgedweaponsystems,so signifcantlythatsomearmedforceshavealready begunestablishingentirelynewoperationalbranches.
InNATOdoctrine,UnmannedAircraftSystemsare categorizedintothreeclasses:ClassIincludesmicro, mini,andsmalldrones;ClassIIreferstomedium-sized tacticalsystems;andClassIIIcoverslargerplatforms intheMALEorHALErange(MediumorHigh-Altitude LongEndurance).WithinClassI,theterm"Small UAVs"hasbecomeestablishedforsystemswitha maximumtotalweightof25kilograms7.Ingeneral, UASarelift-generatingsystems,eitheraerodynamicor aerostatic,withonboardpropulsionbutnoonboard pilot.Theydonotfollowatraditionalballistictrajectory andarethereforefundamentallydistinctfromcruise missiles3
Fromtheperspectiveofstructuralprotection,the platformitselfisnotthefocus.Whatmattersisits abilitytodeliverapayload.Assuch,thefollowing classifcationdoesnotfollowtechnicalspecifcations butinsteadrefectsoperationalpatternsthathave beenobservedonbothsidesoftheconfictin Ukraine:
•First-Person-Viewdronesforprecisionstrikesat closerange,increasinglycontrolledviatethered connectionssuchasfberopticstobypass electroniccountermeasures
•Vertical-liftsystemswithmultirotorconfgurations, manyoriginallydevelopedforagriculturaluse
•LoiteringmunitionswithgrowinguseofAI-based imagerecognitionfortargetidentifcationand waypointnavigation
•Long-RangeOne-WayAttackDronessuchasthe Shahed-136/Geran-2
•ISR/Strikesystemsthatintegratereconnaissance andstrikecapabilitiesintoasinglemilitaryplatform
Twocharacteristicsmakeunmannedsystems particularlynotable,totheextentthattheyare classifedintheBASISresearchprojectasan emergingweaponeffect.
First,theirmanoeuvrabilityallowsthemtooperate independentlyofterrainortrajectoryrestrictions.This makesthemanomnidirectionalthreatthatchallenges conventionalprotectionconcepts.
Second,theyarehighlyeffcientintheireffect.Low technicalbarriers,minimalproductioncosts,and limitedentryrequirementsmakethemhighlyattractive toawiderangeofactors8.Comparedtoothermodern weaponsystems,thetechnologicalgapbetween militaryandcivilianusehasnarrowedsignifcantly,an unparalleledtrendwithprofoundimplicationsforthe protectionofbothmilitaryandcivilianinfrastructure.
Accordingtotheauthor,globalproliferationisnot merelyinevitable9 butalreadycomplete.UASarenow usedinalmosteveryconfict,bybothstateandnon-state actors.Forexample,theso-calledIslamicStatealready possessedsystemswithmulti-kilogrampayloadsas earlyas201510.Similarly,organizedcriminalgroups, suchasdrugcartelsinLatinAmerica,haveadopted unmannedsystemsfortransportandattackpurposes11
Accesstothesetechnologiesisfurtherfacilitatedby open-sourcemanuals12,retroftkits,and3D-printed components11.Publiclyavailableinstructionsalso enabletheconversionofconventionalmunitionsinto UAV-compatiblepayloads.Atthesametime,military effortstodecentralizesupplychainstoimprove
Figure1:Topleft[1]:Long-RangeOne-WayAttackDronesstoredinamobilelaunchtruck15 ; Topright[2]:DisplayofaShahed136/Geran-2airframe14; Bottomleft[3]:FragmentationWarheadofaShahed136/Geran-2withmetalcasing16 ; Bottomright[4]:Shapedchargewarhead17.
resilienceagainstdisruptionareacceleratingthe spreadofthesesystems.Asaresult,dual-use componentsandCommercialOff-The-Shelfproducts havebecomeincreasinglydiffculttomonitor,raising theriskofmisuse.
Inthecontextofinfrastructureprotection,onesystem standsoutinparticular:theShahed-136(Russian designation:Geran-2;seeFigure1,topright)13.This long-rangeone-wayattackdronehasbecomeamassproducible,modularplatformadaptabletoavarietyof payloads.Documentedwarheadsincludefragmentation, shaped-charge,andthermobaricvariants,aswellas confgurationsthatdeploysubmunitionsbeforeimpact (seeFigure1bottomleftandright).Combinedwarhead
designshavealsobeenobserved14.Transportvia conventionaltrucksmakesthesesystemsdiffcultto identifyasmilitarytargetsandcomplicatespreventive countermeasures(seeFigure1,topleft).Atthesame time,thedestructivepayloadscontinuetoincrease, substantiallyexpandingthepotentialdamageperstrike.
Attacksoftenbeginwithcoordinatedsaturationof localairdefenses,launchedsimultaneouslyfroma limitednumberoforiginpoints(seeFigure2).Sincethe beginningofthewar,thenumberofdeployedShahed droneshasrisensteadily.Evendirectstrikeson productionfacilitieshavefailedtohaltthistrend.Since thefallof2024,asharpescalation17 hasbeenobserved, withseveralhundred iv systemslauncheddaily.
ivThefguresarebasedonvariousreportsbytheCenterforStrategicandInternationalStudies(CSIS)andwerekindlyprovidedasrawdata.However, themostaccessibleandup-to-daterepresentationcanbefoundintheformofaninteractivechartatthefollowinglink: https://www.csis.org/programs/ futures-lab/projects/russian-frepower-strike-tracker-analyzing-missile-attacks-ukraine
Theconsequencesforcriticalinfrastructureare severe.Evenwithan80%interceptionrate v,the remaining20%caninfictsubstantialdamage,especially whencombinedwithotherweapontypes.InOctober 2022,forinstance,approximatelyone-thirdofUkraine’s powergridwasdisabledwithinjustafewdays18
Thesedevelopmentsmakeitabundantlyclearthat UAShaveevolvedfromtacticalsupportassetsinto strategicallyeffectiveattackplatforms.Theyare fexibleinapplication,cost-effcientinproduction,and diffculttoreliablycounter.Forprotectionstrategies, especiallythoserelyingonstructuralsolutions,this createsnewandurgentrequirements,whichwillbe examinedingreaterdetailinthefollowingsections.
COUNTERMEASURES:WHATISMISSING?
Thedefenseagainstunmannedsystemstoday generallyfollowsawell-establishedresponsechain: Detect,Track,Identify,Decide,Counter,Assess vi.Its structuralsimilaritytothemilitarykillchainFind,Fix, Track,Target,Engage,Assessisevident.Inboth cases,theaimistomaketimelydecisionsunder pressure,detecthostileactionsearly,disruptthe adversary’schainofeffects,andenforceone’sown.
Theacademicandprofessionalliteratureprovides numerousandwell-documentedapproachesto counterUAVthreats19.Thesemeasuresaretypically dividedintotwocategories20:soft-killtechniques,such asgeofencing,jamming,spoofng,orhacking,and
vAccordingtorepeatedstatementsbytheUkrainianmilitary,theinterceptionrateofincomingdronesisestimatedatapproximately80percent.Itis importanttonotethatnocleardistinctionismadebetweendroneswithactualpayloadsanddecoysordummysystemsinthesefgures. viResponsechainslikethisarepresentedinvariousforms,oftentailoredtospecifccompanies.Theversionshownhererepresentsonlyonepossible example.
Figure2:ApproximatefightpathsofShaheddroneslaunchedbyRussianforcestowardUkraineon5September2024. Source:Xchannel@ShahedTracker.
hard-killmethods,includingtheuseofprojectiles,laser weapons,microwavesystems,electromagneticpulses (EMP),orphysicalinterceptionmechanismslikenets. Bothcategoriestargetthedroneplatformitselfandrely ondisrupting,misleading,ordestroyingitasearlyas possible.However,thepayloadremainsunaffected unlessitisdetachedordestroyedintheprocess.In scenariosinvolvinglargenumbersofdrones,highspeedapproaches,orhardenednavigationsystems, thesecountermeasuresincreasinglyreachtheir operationallimits.
Whatisoftenmissinginsuchlists3 isstructural protection.Itisrarelymentionedinstandardoverviews ofmodernUAVdefense,yetitisessentialfora comprehensiveapproach.Structuralprotectiondoes notaddresstheplatform,itaddressestheeffectit delivers.Itdoesnotprotectthesystembutthetarget. Itcomesintoplaypreciselywhenothersystemsareno longereffectiveorhavealreadybeenbypassed.Abrief refectionmaybewarranted:consideringtheongoing efforttoestablishabalancebetweenprotectionand offensivecapability,onemustaskwhichofthetwo components,payload,ordeliverysystem,iscurrently undergoingmorerapidtechnologicaldevelopment. Thisdistinctioniscrucialfordeterminingwhere protectionstrategiesshouldbefocusedandwithin whattimeframe.
Comparedtoactive,technology-dependent countermeasures,structuralprotectionoffersawide rangeofstrategicadvantages21.Itisnotsubjecttolegal restrictions,asitdoesnotrequireairspaceclearance orinterferewithoperationalsystems,anditreliably preventscollateraldamage.Itoperateswithoutpower supply,dedicatedpersonnel,orongoingmaintenance. Itsprotectivefunctionremainsintactevenintheevent ofpoweroutages,systemfailures,ortacticalsurprise.
Structuralprotectionisnotboundtoindividual scenarios.Dependingonitsconfguration,itcan provideprotectionnotonlyagainstphysicaleffectsbut alsoagainstsurveillanceandreconnaissance.This includesstructuralcamoufage,signaturereduction,
andshieldingagainstoptical,thermal,or electromagneticsensors.Inaddition,itcanbe integratedearlyintoplanningprocesses.Inlinewitha security-by-design22 approach,itcanbestructurally, architecturally,andfunctionallytailoredtothespecifc application,whetherfornewconstructionorthe retrofttingofexistinginfrastructure.Itssymbolic functionshouldalsonotbeunderestimated:visible structuralprotectioncandeterattackers,raisethe perceivedcostofanattack,anddemonstrate preparednessinthesenseofvisibleforceprotection.
Structuralprotectionalsoofferscleareconomic advantages.Ittypicallyincurslowlifecyclecosts, requiresminimalmaintenance,andcanbeplanned reliablyoverextendedtimeframes.Itsinvestmentcostis predictable,whileitsvalueinacrisiscanbeexistential.
Structuralprotectionisnopanacea.Butitisa resilient,autonomous,andenduringcomponentofa necessarilymultidimensionalprotectionconcept.Ina securityenvironmentshapedbyasymmetricthreats, unmannedsystems,andrapidtechnologicaladvances, itwouldbenegligenttoforgothislastlineofdefense.
Howsuchprotectioncanbeconcretelydesigned, tested,andevaluatedisdemonstratedbytheBASIS researchproject,whichisintroducedinthefollowing section.
THERESEARCHPROJECTBASIS
TheBASISresearchproject(Building Adaptive Shielding forExposed I nfrastructures vii using Steel-SandwichConstructions)addressesthequestionofhowstructural protectionmeasurescanbeintegratedasrobust, autonomous,andscalablecomponentsintoa multidimensionalprotectionconcept.Atitscore,the projectfocusesonthedevelopment,testing,and evaluationofamodularsteel-sandwichconstruction (SSC)specifcallydesignedtowithstandexceptional effectssuchasfragmentationandexplosion-induced blastwaves.Theprojectcombinessecurity-strategic analysiswithengineeringimplementationandis structuredintofourcloselyinterconnectedworkpackages.
viiIntheBASISresearchproject,thetermexposedinfrastructuresisintroducedasanumbrellacategoryencompassingallcritical,defense-relevant,and defense-essentialinfrastructures.
Thestartingpointisascenario-basedthreatanalysis, ensuringthatthetechnicaldesignisconsistently alignedwithrealisticthreatprofles.Themethodological approachcombinesqualitativeandquantitative assessmentlogic.Beginningwithabroadall-hazardsoriented23 threatspectrum,plausibleandsecurityrelevantscenariosarederivedusinginfuencefactor andconsistencyanalysis24.Inafrstanalyticallayer,the affectedinfrastructuresystemisexaminedqualitatively toidentifyvulnerabilities,interdependencies,andcritical functionalnodes.Methodologically,thisissupportedby interdependencyanalyses25,system-theoreticalstability models26,andastructuralvulnerability27 framework.
Thesecondanalyticallayerfocusesonthestructural protectionsystemitself.Resilienceisassessed accordingtothedimensionsofrobustness, redundancy,resourcefulness,andrapidity 28.Theaimis tominimizetheresiliencelossfollowingashockevent
andtodevelopastructurallyandeconomicallyviable protectionsolution.Thisiscomplementedbyan economicdamageassessment 29 thatincludesnotonly repaircostsbutalsoindirect(opportunity)lossesand systemiccascadingeffects.
Fromtheseanalyses,fvekeydesignrequirements arederived:variability,interchangeability,scalability, adaptability,andcost-effciency.Theseareimplementedintheformofamultilayersteel-sandwich constructioncomposedofahardupperfacesheet,an energy-absorbingcore,andaductilelowerfacesheet. Figure3showsanexemplaryconfguration.Initial ballistictestsusing20-millimeterFragmentSimulating Projectiles30 serveasanindicatorforproofofconcept. Thesewillbefollowedbyincreasinglycomplexblast testsdesignedtoinvestigatethestructure’senergy absorptionbehaviourandfailuremodesunderrealistic loadingconditions.
Figure3: Left: Aschematicviewofthesteel-sandwichconstruction(SSC).Thesurfaceproflingisoptional,anditseffect iscurrentlyunderinvestigation; Right: Initialimpressionsfromtheballistictestseriesusing20mmFSP.Projectilevelocitiesrangefrom approximately660m/sto1300m/s.Thesteelplatehasathicknessof22mminthecentralarea.
Thefndingsfromtheexperimentalcampaignsfeed intoanumericalengineeringmodeldevelopedusing theIMPETUSAfeasoftware.Thismodelwillbe capableofsimulatinghighlydynamicloads,material failure,andscalingeffects,andwillbevalidated againstthephysicaltestdata.Thegoalistomake designandassessmentprocessesmoreeffcientwhile providingareliablefoundationforthetargeted applicationofstructuralprotectionmeasures.
BASISbridgesthegapbetweenthreat-based securityanalysisandtechnicalprotectiondevelopment.Ittranslatesoperationalscenariosintospecifc designrequirements,validatesstructuralsolutions underreal-worldconditions,andabstractstheresults intoavalidatedengineeringmodel,contributingto theresilienceofexposedinfrastructuresunder increasinglycomplexthreatenvironments.
APPLICATIONSOFSTRUCTURALPROTECTION MEASURES
Example1:BridgeUseCase
Thechallengesofprotectingexposedinfrastructures canbeillustratedusingtheexampleofbridges.Inthe transportsector,bridgesareparticularlyvulnerable
duetotheirsystemicimportance,limitedredundancy, andexposedlocation.Theirstrategicrelevanceis refected,amongotherthings,inGermany’spotential roleasatransitcountrywithintheframeworkofNATO collectivedefense.IntheeventofanArticle5scenario, theabilitytodeploytroopsandmaterielwoulddepend directlyontheavailabilityoffunctionalcrossingpoints. Withinthestructureitself,resilienceisunevenly distributed.Whiledamagetotheroadwayorindividual bridgespanscanoftenbetemporarilyrepairedwith relativelymodesteffort,piersandabutmentsrepresent structuralweakpoints.Thesecomponentsareoften diffculttoaccess,designedforlongservicelife,and canonlybereplacedwithconsiderableeffortandtime. Thefailureofsuchelementscanresultinthecomplete andprolongedlossofbridgefunctionality.Thisis preciselywheretheBASISproject'sprotectionconcept comesintoplay.Thedevelopedsteel-sandwich constructionscouldofferamodularandadaptable protectionoptionforespeciallyvulnerableelements suchaspiersorbearingzones.Theycouldbe retrofttedinatargetedmanner,tailoredtodifferent threatlevels,andintegratedintoexistingstructures. Figure4(leftside)providesanimpressionofthis conceptunderrealisticconditions.

Figure4: Left: AI-generatedimageillustratingapossibleapplicationofthestructuralprotectionsolutiondevelopedin theBASISresearchproject,shownatabridgepier; Right: Real-worldexampleofanadaptivestructuralprotectionsystem(BPCbyMiframSecurity)installedonan Israelihospital(graypanelsonthewingstructures).
Example2:HospitalProtection
Practicalapplicationsofstructuralprotectionsystems forexistinginfrastructurealreadyexist.Aspecifc exampleisprovidedbytheIsraelicompanyMifram Security,whichhasdevelopedanexternalcladding systemmadeofsteelplates.Accordingtothe manufacturer,thesystemisdesignedtoabsorb theeffectsofsteep-trajectoryweapons,ballistic projectiles,andblastwaves.Theprotectivecladdingis partiallymounteddirectlyonload-bearingstructural elementsandcanthusbeinstalledatparticularly vulnerablesectionsofexistingbuildings.Figure4(right side)showsanapplicationofthissolutiononahighly vulnerablefacility:ahospital.Suchinstitutionsarenot onlycriticalfromamedicalandhumanitarian perspectivebutalsoplayacentralroleinmaintaining treatmentandsupplycapacitiesincivil-militarycrisis scenarios.Thisexampledemonstratesthatstructural protectioncanbeimplementedevenunderchallenging conditionswithoutimpairingthebuilding’sfunctionality ordailyoperations.
Example3:Cost-BeneftConsideration
Aparticularlystrikingexampleofthevulnerabilityof exposedinfrastructureisthecoordinatedattackonoil facilitiesoperatedbytheSaudicompanyAramcoin September2019.Accordingtovarioussources31, betweentenandtwenty-fve32 unmannedsystemsand cruisemissileswereusedtostrikethefacilitiesin AbqaiqandKhurais,bothofwhicharecentraltoglobal oilproductionandprocessing.Theincident demonstratednotonlytheeffectivenessofrelatively simpleandpreciseweaponsystemsagainsthighvaluetargets,butalsothestrategicleveragesuch attackscancreate.Atthetimeoftheattack,globaloil demandwasaround100.8millionbarrelsperday,and thepriceofBrentcrudestoodatapproximately53US dollarsperbarrel33.Theimmediateaftermathsaw noticeablemarketreactions,deliveryshortfalls,and politicalstabilizationmeasures.
Thefollowingassessmentdoesnotconstitutea comprehensivecasestudybutisintendedsolelyto illustratethepotentialconsequencesofphysical attacksonexposedinfrastructuresbasedonpublicly
availabledata.Itisbasedonsimplifedassumptions.A fullquantifcationofdamagesisnotpossibledueto limiteddataavailability.Inparticular,noreliablefgures areavailableregardingrepaircostsorsystemic cascadingeffectssuchasadelayedIPO,therelease ofstrategicoilreserves,orresiliencemeasurestaken inresponsetotheincident.Theopportunitycosts presentedintheexamplearebasedonarough modellingofproductionlossusinganidealized resiliencecurve.Thiswasdevelopedinreferenceto Bruneau’s 28 modelandcalculatedusingtheaverage priceofBrentcrudeatthetimeoftheattackin September2019.Theresultinglossamountsto approximately1.987billionUSdollars.Additionally, theeconomiceffectofthesubsequentincreaseinoil prices,basedonglobalconsumptionvolumes,is estimatedataround6.775billionUSdollars.Both valuesservesolelytoillustratepossibleordersof magnitudeandarenotintendedasadetailed economicevaluation.Nonetheless,theyunderscore thescaleatwhichstructuralvulnerabilitycanmanifest, andtheeconomicrationalebehindinvestinginthe protectionofexposedinfrastructure.
CONCLUSION
Theexamples,threatanalyses,andtechnicalinsights presentedinthisarticleconveyaclearmessage: exposedinfrastructuresareincreasinglybecomingthe focusofdeliberateattacks,whetherinconventional warfare,hybridconficts,orasymmetricoperations. Unmannedsystems,inparticular,haveaddedanew dimensiontothethreatlandscape,onethatchallenges conventionalprotectionstrategiesthroughsheer quantity,precision,andunpredictability.
Inthiscontext,structuralprotectionmustnolonger betreatedasasecondaryconsideration.Asthefnal lineofdefense,itoffersaresilient,autonomous,and scalablecomponentthatcomplementsactiveand organizationalcountermeasures.Itprotectsnotonly againstphysicaldestructionbutalsohelpsmaintain systemfunctionality,operationalcontinuity,and publicconfdence.Itscontributionextendsbeyond technicalresilience,itstrengthenssocietaland strategicstability.
Itistimetogivestructuralprotectionthestrategic weightitdeservesinplanning,inprocurement,andin doctrine.Becauseultimately,structuralprotectionis theBASISofanyrobustandfuture-readyinfrastructure securityconcept.■
Disclaimer
Thisarticledoesnotrepresenttheopinionofany nationalormultinationalorganisation,itswholecontent shouldonlybeconsideredastheopinionoftheauthor. Asalltheinformationhasbeenobtainedfromopen sources,potentialmistakescouldhavebeenmade duringtheresearchprocess.Pleasefeelfreetosend yourcomments,corrections,andinputstotheauthor; theywillbehighlyappreciated.
REFERENCES
1. Förster,Nils.“PlädoyerzurEntwicklungeinereffektiven Drohnenabwehr“.ConferenceContribution.Unbemannte SystemeX-SessionB2,Bonn,25.March2025.
2.NDR,FlorianFlade,WDR,ManuelBewarder,WDR/ NDR,BenediktStrunz.“Ballungvonneuen DrohnensichtungenimNorden“.tagesschau.de. Downloadedon3.August2025. https:// www.tagesschau.de/investigativ/ndr-wdr/drohnenueberfuege-102.html
3.Haider,André,MartinHellmann,AndreasSchmidt,u.a. AComprehensiveApproachtoCounteringUnmanned AircraftSystems.2021.
4.tagesschau.de.“ExplosionlegtZugverkehrinrussischer RegionSamaralahm“.4.March2024. https:// www.tagesschau.de/ausland/europa/russlandeisenbahnbruecke-detonation-100.html
5.tagesschau.de.“ZweiBrückeninRusslandeingestürztVorwurfderSabotage“.1.June2025. https:// www.tagesschau.de/ausland/europa/russlandbrueckeneinsturz-zug-102.html
6.Jones,SethG.Russia’sShadowWarAgainsttheWest. CSISBRIEFS.CenterforStrategicandInternational Studies,2025.
7.NATOStandartizationOffce.UnmannedAircraft SystemsAirworthinessRequirements(Usar).Allied EngineeringPublicationAEP-4671.VersionEditionB, Version1.April2019.
8.Swed,Ori,undKerryChavez.“Theproliferationof dronestoviolentnonstateactors“.DefenceStudies, Online-Vorab-Publikation, 24.November2020. https://doi.org/10.1080/14702436.2020.1848426
9.PublicationsOffceoftheEuropeanUnion.European UnionTerrorismSituationandTrendReport2024. Europol,2024.
10.Rassler,Don,MuhammadAl-Ubaydi,undVera Mironova.“TheIslamicState’sDroneDocuments: Management,Acquisitions,andDIYTradecraft“. CombatingTerrorismCenteratWestPoint,31,2017.
11.PublicationsOffceoftheEuropeanUnion.European UnionTerrorismSituationandTrendReport2024. Europol,2024.
12.R.,Jorge.“Theuseofrockets,grenades,and engineeringmunitionsaswarheadsforvarioustypesof UAVs“.Post.LinkedIn,February2025.
13.KommandoHeerLandIntelligenceCentre.“OWAUAV/ LoiteringMunitionGeran-2/Shahed-136“.28.August 2024.
14.KommandoHeerLandIntelligenceCentre.“OWAUAV/ LoiteringMunitionGeran-1/Shahed-131“.28.August 2024.
15.stern.de.“Shahed136:WarumdieseDrohnendazu gemachtsind,zuscheitern“.22.April2024. https://www.stern.de/digital/technik/shahed-136--warum-diese-drohnen-zum-scheitern-verurteiltsind-34629148.html
16.R.,Jorge.“CombatpartsofShahed136/Geran-2type UAV“.Beitrag/Post.LinkedIn,Mai2025.
17.Jensen,Benjamin,undYasirAtalan.“DroneSaturation: Russia’sShahedCampaign“.CenterforStrategicand InternationalStudies,13.Mai2025.
18. Kunertova,Dominika.“TheWarinUkraineShowsthe Game-ChangingEffectofDronesDependsonthe Game“.BulletinoftheAtomicScientists79,Nr.2(2023): 95–102. https://doi.org/10.1080/00963402.2023.2178180
19. Dharmendra,Chauhan,HarshilKagathara,HirenMewada, SagarkumarB.Patel,SagarKavaiya,undGordanaBarb. “Nation’sDefense:AComprehensiveReviewofAnti-Drone SystemsandStrategies“.IEEE,12.March2025. https://doi.org/10.1109/ACCESS.2025.3550338
20.Chiper,Florin-Lucian,AlexandruMartian,Calin Vladeanu,IonMarghescu,RazvanCraciunescu,und
OctavianFratu.“DroneDetectionandDefenseSystems: SurveyandaSoftware-DefnedRadio-BasedSolution“. Sensors22,Nr.4(2022):1453. https://doi.org/10.3390/ s22041453
21.Karlos,V.,undM.Larcher.Protectionagainst UnmannedAircraftSystems.JRCtechnicalreport. EuropeanCommission-JointResearchCenter,2023.
22.Larcher,Martin,V.Karlos,RalfSchumacher,D. Strezova,undA.Caverzan.SecuritybyDesign:Schutz desöffentlichenRaumsvorterroristischenAnschlägen. JRCtechnicalreport.EuropeanCommission-Joint ResearchCenter,2024.
23.EntwurfeinesGesetzeszurUmsetzungderRichtlinie (EU)2022/2557undzurStärkungderResilienz kritischerAnlagen,DachgesetzzurStärkungder physischenResilienzkritischerAnlagen(2024).
24.Kosow,Hannah,RobertGaßner,LorenzErdmann,und Beathe-JosephineLuber.MethodenderZukunftsundSzenarioanalyseÜberblick,Bewertungund Auswahlkriterien.WerkstattBerichtNo.103.Institutfür ZukunftsstudienundTechnologiebewertung,2008.
25.Schmitt,HannahChristine.“SystemischesKaskadenpotenzialvonKRITIS-Teilsektoren“.IzR-Informationen zurRaumentwicklung,No.4(2019):50–61.
26.Vester,Frederic.DieKunstvernetztzudenken:Ideen undWerkzeugefüreinenneuenUmgangmit Komplexität.Pantheon,2019.
27. Kröger,Wolfgang,undEnricoZio.VulnerableSystems. Springer,2011. https://doi.org/10.1007/978-0-85729-655-9
28.Bruneau,Michel,StephanieChang,RonaldEguchi,u.a. “AFrameworktoQuantitativelyAssessandEnhancethe SeismicResilienceofCommunities“.Earthquake Spectra-EARTHQSPECTRA19(November2003). https://doi.org/10.1193/1.1623497
29. Pant,Raghav,KashBarker,undChristopherW.Zobel. “StaticandDynamicMetricsofEconomicResiliencefor InterdependentInfrastructureandIndustrySectors“. ReliabilityEngineering&SystemSafety125(Mai2014): 92–102. https://doi.org/10.1016/j.ress.2013.09.007
30. NATOStandardizationOffce.ProceduresforEvaluating theProtectionLevelofArmouredVehicles–Kinetic EnergyandArtilleryThreat.AlliedEngineering PublicationAEP-55,Volume1.VersionEditionD Version1.February2022.
31.dw.com.“ReaktionennachAngriffenaufRaffnerien“.15. September2019. https://www.dw.com/de/reaktionennach-angriffen-auf-raffnerien/a-50436080
32.ZEIT,DIE.“Saudi-Arabien:Drohnenangrifftrifft Ölraffnerie“.DieZeit(Hamburg),15.September2019. https://www.zeit.de/politik/ausland/2019-09/saudiarabien-drohnenangriff-oelanlagen-huthi-rebellen
33.boerse.de.“HistorieBrentRohölpreisEUR|Brent RohölhistorischEuro“.Accessed1.September2025. https://www.boerse.de/historische-kurse/BrentRohoelpreis/XC0009677409
ABOUTTHEAUTHOR
CaptainMarcMenne(M.Sc.) isa ResearchAssociateattheInstitute ofStructuralEngineeringatthe UniversityoftheBundeswehr Munich.Hisresearchfocusesonthe resilienceofexposedinfrastructure againstmodernweaponeffects.He leadstheresearchprojectBASIS, whichinvestigatesbuilding-adaptiveprotectionusing steel-sandwichconstructions.HisPhDprojectinvolves theexperimentalandnumericalanalysisofsteelunder emergingthreats.Previously,heservedasanoffcerin theGermanArmy’sEngineerCorpsandworked attheFederalOffceofBundeswehrInfrastructure, EnvironmentalProtectionandServices(BAIUDBw), wherehewasresponsibleforplanningandleadership tasks.Hismilitarybackgroundandscientifcexpertise inprotectiontechnologiesandsimulationscombine operationalinsightwithtechnicalresearch.Heisa juniorspeakerattheRISKResearchCenterand activelyinvolvedintheBMFTR-fundedgraduate network“CivilSecurity”.
E-Mail: marc.menne@unibw.de
LinkedIn: www.linkedin.com/in/marc-menne-167b7430a
ACCELERATINGTHREATDETECTION WITHREAL-TIMEVIDEOX-RAYIMAGING
ByMarcJansen,HeadofSales&MarketingatTeledyneICM
Incontemporarythreatenvironments,timeisnota luxurybutacriticalvariable.ForExplosiveOrdnance Disposal(EOD)teams,operatinginhigh-riskzones, theabilitytorapidlyassessandneutralizepotential threatsisessentialtomissionsuccessandpublic safety.ConventionalX-raysystems,whilereliablein producinghigh-resolutionstaticimages,areinherently limitedbytheiroperationalworkfow.Considering setup,distancingprotocols,andimageacquisition, thesestepscanbetimeconsumingwhichreduces responsivenessinfeldconditions.
OPERATIONALEVOLUTION:FROMSTATIC IMAGINGTOLIVEX-RAYACQUISITION
Advancementsindigitalradiographyhaveintroduced real-timevideoacquisitioncapabilities,transforming thetacticalutilityofX-raysystems.Liveimaging enablesoperatorstovisualizetheinternalstructureof suspiciousobjectssuchaspackages,backpacks, vehicles,withoutthedelaysassociatedwithtraditional systems.High-speeddigitaldetectorsnowachieve frameratesof30fpsorhigher,deliveringactionable clarityinreal-time.
TeledyneICM’sC-Viewhasbeenengineeredforrapid deploymentandfeldresilience,itintegratesahighresolutionCMOSdetector(99µmat30fps)witha70kV
Go-ScanC-View–standalonereal-timedigitalradiography systemforsecurityapplications.
X-raysource.While70kVmayappearmodestcompared tohigher-energysystems,theC-View’simagingfdelity isoptimizedtorevealstructuralanomaliesand suspiciouscontourswithprecision.Crucially,areasthat resistpenetration,manifestingasopaquezones, indicatehigh-densitymaterials.Ifspotted,immediate precautionarymeasuresmustbetaken.
SCENARIOAPPLICATION:RAPIDRESPONSEIN ATRANSITSECURITYINCIDENT
Considerasituationinwhichauthoritiesreceivea crediblethreatalertatamajormetropolitantransit station.Aspartoftheemergencyprotocol,thestation isevacuated,resultinginalargevolumeofunattended personalbelongings,bags,backpacks,andparcels. Eachitemmustbeindividuallyassessedtoensurethe areaissafeforre-entryandoperationscanresume.
UsingconventionalX-raysystems,thisprocess wouldrequireextensivesetup,repositioning,and sequentialstaticimaging,potentiallyconsuming severalhoursorevendaysdependingonthevolume ofitemsandcomplexityof theenvironment.Such delaysnotonlyprolong publicdisruptionbutalso increaseoperationalriskfor securitypersonnel.
UsingalivevideoX-ray systemlikeTeledyneICM’s C-Viewenablesrapid,onthe-spotinspection.Itsrealtimeimagingcapability allowsEODteamstoscan andevaluateeachitem immediately,identifying suspiciousshapesorhighdensitymaterialswithout repositioningorwaitingfor imageprocessing.This dramaticallyaccelerates threatassessment,reduces exposuretime,and facilitatesfasterclearance ofthesite.
VERSATILEAPPLICATIONSACROSS SECURITYDOMAINS
TheC-Viewsystem’scompactarchitecture andrapiddeploymentcapabilitymakeit suitableforawiderangeofoperational environments:
•PublicTransportationHubs: Airports, trainstations,andbusterminalswhere unattendedbaggagemustbequickly assessed.
•EventSecurity: Stadiums,concert venues,andpoliticalgatherings requiringrapidscreeningofsuspicious items.
•BorderControlandCustoms: Inspectionofluggage,parcels,and vehiclesatcheckpointswithminimal disruptiontofow.
•MilitaryandTacticalOperations: Fieldusebyarmedforcesforroute clearance,compoundentry,andIED detection.
•CriticalInfrastructureProtection: Powerplants,governmentbuildings, anddatacenterswheresecurity breachesmustbeswiftlyinvestigated.
•LawEnforcementandSWAT: Tacticalteamsconductingraidsor respondingtobombthreatsinurban environments.
•MailandParcelScreening: Rapid inspectionofsuspiciouspackagesin postalfacilitiesorcorporatemailrooms.
C-Viewisdesignedfortacticalagility. Fullybattery-poweredandwirelessly connected,thesystemachieves operationalreadinesswithin60to90 seconds.Itsruggedizedformfactor supportshandhelduseinaustere environments.
TheintegrationoflivevideoX-ray imagingintofeldoperationsrepresentsa shiftinthreatdetection. ■
Go-ScanC-View.
ABOUTTHEAUTHOR
MarcJansen istheHeadofSales& MarketingatTeledyneICM,basedin Andrimont,Liège.Havingspentmostofhis careerintheX-rayindustry,morespecifcally inSecurityandNon-DestructiveTesting markets,Marcbringsextensiveknowledge andhands-onexpertisetohisleadershiprole. HeplaysakeypartinguidingTeledyneICM’s salesandmarketingstrategies,ensuringstrongalignmentacross globalmarkets.
AUNAV.CBRSVEHICLESAMPLECOLLECTIONKIT–
ENHANCINGSAFEANDEFFICIENTSAMPLE COLLECTIONINHAZARDOUSCBRNENVIRONMENTS
ThisisanotherexampleofEM&EGroup'scommitmenttoprotectingtheoperatorandofferingthe latesttechnologyintheroboticfeld.
CBRN(Chemical,Biological,Radiological,and Nuclear)threatsarerapidlyevolvinginboth sophisticationandaccessibilitydrivenbyscientifc advances,developmentsintechnologyandacomplex globalsecuritylandscape.Whetherresultingfroma deliberateattack,anunintendedreleaseoranatural disasterthesethreatsposesevereriskstopublic health,theenvironment,andnationalsecurity.
Insuchscenarios,thespeed,safety,andaccuracy oftheresponseoftendeterminethedifference betweencontainmentandescalation.Yettheveryfrst stepintheresponsechain,samplecollection,still forcespersonnelintocontaminatedzones,constrained byheavyprotectivesuits,movingslowlyandatgreat risk.DespiteprogressinCBRNdetectionandanalysis, samplingremainsoneoftheleastmodernisedtasks.
EM&EGroup,inclosecollaborationwiththe SpanishArmy,setouttobreakthispattern.Theresult istheaunav.CBRSVehicleSampleCollectionKit–a systemthatshiftsthisdangerousmissionfromhuman handstoaroboticarmoperatedsafelyfrominsidethe vehicle,automatingbothcollectionandstorage.It enablesthecollectionofuptoeightsolids,powders, liquids,andwatersamplesinasealedand refrigeratedcontainer,reducingoperatorexposure andprovidingaccesstoenvironmentsthatwould otherwisebetoodangerousforhumanoperators.
Toachievethis,thesystembringstogetherthree primarycomponents,eachdesignedtocomplementthe othersindeliveringsafeandeffcientfeldsampling:
•RoboticArm–Aprecise7°DoFelectricalarm capableofbothautomatedandmanualmovements, includinggripperandturret-basedcontrol.It integratesanEO/IRdual-bandfltercameraanda distancesensor.
•SampleContainer–Airtightandrefrigeratedfrom 4to8°C,capableofstoringuptoeightsamples whilepreventingcross-contamination.
•SamplingTools–Fourdifferentsamplingtools designedforsolids,liquids,powders,andwater.
1.DEPLOYTHEROBOTICARM:
Thesystem’scompactdesignallowsfullintegration attherearofaCBRNvehiclewithoutcompromising mobilityorperformance,makingitsuitableforboth urbanandoff-roadoperations.Inaddition,thesystem iscertifedaccordingtoIP66standardsandwithstands dust,high-pressurewater,andharshoperational conditions.
Onceinthefeld,thekitstandardizesthesample collectionprocedureintofveautomatedsteps, reducingoperatorworkload,minimizingrisksand acceleratingexecution:
Pressingtheunfoldbottomextendstheroboticarmautomatically.
2.SELECTASAMPLINGTOOL:
Theoperatorselectsatoolviatheinterfaceandthearmautomaticallyretrievesitfromitsslot.
3.COLLECTTHESAMPLE:
Thearmpositionsthetoolnearthetargetusingpre-setpositionstominimizecollisionrisks.Theoperatorthen byusingthegripperandturret-basedmovementcancontroltheend-effectororturretmovementbasedonthe relativepositionofthegripperorturretinits3axesofreferenceandtherestofthearmadjustsitslinks simultaneouslytoperformthemovementforthecollectionofthesample.
4.STORETHETOOL:
Aftercollection,thearmreturnsthetooltoitsdesignatedslotusingpre-setmovements.Theoperatorthen manuallyinsertsthetoolandsecuresit.Thesystemincludesanadjustablelockingmechanism,ensuringtools aresecuredandalignedcorrectly.
5.FOLDTHEROBOTICARM:
Pressingthefoldbuttonretractsthearmautomaticallyintoasafeposition.
Asaresultofthecombinedtechnology,the aunav.CBRSVehicleSamplingKitdeliversasetof operationaladvantagesthatdirectlyaddressthe challengesofCBRNsamplecollection:
•EnhancedSafety:Remoteoperationeliminates directexposuretohazardousenvironments.
•Versatility:Fourinterchangeabletoolsadaptto diversematerialstates.
•Integrity:Temperature-controlled,airtight containerspreservesamplesforlaboratory analysis.
•Effciency:Automatedpresetsaccelerate deploymentandreduceoperatorworkload.
•Compactness:Fullintegrationwithout compromisingvehicleperformance.
Ultimately,theaunav.CBRSVehicleSamplingKit transformswhatwasonceahigh-riskmanualtaskinto acontrolled,repeatable,andsecureprocessproviding feldteamswiththetoolstheyneedtooperatesafely, effciently,andeffectively,regardlessofthe operationalenvironment.■
ABOUTEM&EGROUP
EM&EGroup isaleadingSpanishgroupinthe engineeringandmanufacturingofcomplexDefense andSecuritysystems,distinguishedbyitshigh investmentininnovation,itscommitmenttojob creation,andthedevelopmentofdualtechnologies, withaspecialinterestinincorporatingAIintoits solutions.Thegroup'ssystemsincluderemoteland andnavalstations,ammunitionguidancesystems, electro-opticalsurveillancesensors,androbotic systems,amongothers.Inaddition,thegrouphasa subsidiary,EM&EElectronics,focusedondeveloping electronicsandphotonics.Withsolutionsinmore than25countries,EM&EGrouppostedaturnoverof over€355millionin2024andcurrentlyemploysover 1,700people.
Findoutmoreat: https://eme-es.com/
COUNTER-IEDREPORT- CALLFORPAPERS
Counter-IEDReporteditorialteaminvitesgovernmentbodies,armypersonnel,researchers, industryexpertstocontributetheirarticles,casestudies,whitepaperstothereport.* Abstractsandarticlesshouldbesubmittedbyemailto: editorial@deltabusinessmedia.com Formoreinformation,pleasevisit: https://counteriedreport.com/editorial/ *Feesapplyforpublicationofarticlessubmittedbycommercialandfor-proftorganisations. Allarticlesaresubjecttoeditor’sapproval.
TRACKING3D-PRINTING:APPLICATIONOFTECHNICAL EXPLOITATIONOVERADDITIVEMANUFACTURING
ByJoseMRufas&DavidHerraiz,SubjectMatterExpertsinC-IEDandTechnicalExploitation
“Ifthereseemnoanswersthencreateandapplythem.” (StevenRedheadinhisbook“LifeIsSimplyAGame”,frstpublishedin2016)
Aknifeisnotbadbyitsnature,butitcouldbeused toinjureorkilloneorseveralpeopleinthewrong handsandwiththewrongintentions…Thatis eventuallyhappeningwiththeadditivemanufacturing (commonlyknownas“3D-printing”)capabilities,which areallowingpeopletodesignand/orcreatehomemade partsforfrearmsorimprovisedexplosivedevices.
Thosereferencedtechniquesofprintingpiecesof artworkwithornamentalorpracticalaimsthrough usingdifferentspecifcprintersandmaterialsarenot onlyusefulforindustrial,didacticalorentertainment purposes,butalsoabletoprovidecriminals,fghters andterroristswithuncontrolledandeasy-to-produce componentsformanufacturingweapons.
Figure1:STL-formatpreviewforthe“URUTAU”modelfora9x19mmbullpupweapon. (Source–www.gnet-research.org)
Inprinciple,andalmostwithoutanypotentialalertor trackingbyinvestigators,anyonecouldhavea computer,acquirea3D-printer,fndafree(orpaid) designofchoiceintheinternet,buytherespective flaments(withdifferentpercentagesofplastics,resins, metals,composites,wood,ceramic…),followthe assessmentbyotherusersthroughtheweb,and,after severaltests,fnallymanufactureahazardousdevice abletoshootordetonatewiththeadditionof commercial(alsoimprovised)munitionsoranysortof incendiaryexplosivemixture…
“Untrackedweaponsfordummies”orhoweasy tofndinstructionsfor3D-printedhazards Asoftoday,youwouldnotneedtoseektheDarknet tofndbothblueprintsandinstructionstohaveaccess toyourown3D-printedweapons:notonlyspecifcally dedicatedwebsitesfor3D-printedfrearmsandtheir partsarewidelyavailable(e.g.DEFCAD, 3Dgunbuilder,ctrlpew,printyour2a,3dprintedgungear,
topboyghostguns,hammy3dprints…)butalsomultiple siteswhichdealwithanykindof3D-printingdesigns, includingcomponentsforfrearmsorsometimes almostcompleteweaponsasdisguisedbetweenlegal 3Dreplicas(e.g.cults3d,printables,stlfnder,yeggi, free3d,thinginverse…).
Alongwiththat,andunderconfusinglabelssuch asFOSSCAD(FreeOpen-SourceSoftwareand ComputerAidedDesign)orotherones,someonline communitiesaresharingdesignsfor3D-printedguns orevenselling3D-printedweaponsortheirparts almostwithoutanybanning(e.g.reddit,telegram, facebook…).
Ontheotherhand,bothsidesoftheUkrainian confictarewidelyandopenlysharingterabytesofdata regardingthebattle-provenemploymentofadditive manufacturingindirectsupportofthefabricationand useofimprovisedexplosivedevices.
InMyanmar,severalmilitiasfghtingagainstthe governingMilitaryJuntaareextensivelyusingnot
only3D-printedimprovisedmunitionsforunmanned aircraftsystems(UAS)butalsofullyequippingunits withtheFGC-93D-printed9mmParabellumfrearm.
Inparallel,thereligiouslymotivatedviolentextremist organizations(e.g.DAESH)areshowingagrowing interestinmanufacturing3D-printedweaponsand devices,whileonlinesharingflesandinstructions.
Whatcouldforensicsdowith3D-printing?
Technicalexploitation(alsoconsideredas“forensics”, “criminalistics”or“scientifcpolice”fromaninteragency pointofview)couldsupporttheforensicattributionin therespectivefeldofadditivemanufacturing.
Inprinciple,anycollectableelementasconnected tobiometriccharacteristics(e.g.latentfngerprints, bodyfuidssusceptibletoprovideDNA-related information…)couldbetransferredfrompeopletoany sortofprintedmaterial,printingdevicesandsoonall aroundthe“crime”scene.Alongwiththat,tracesfrom othermaterialsleftbythepotentialsuspectscouldalso remainthere.
FromtheperspectiveofChemicalExploitation,it lookslikelogicalTechnicalExploitationtechniques wouldsupportinthe identifcationofthedifferent chemicalsascomprisingthe flamentswhichareusedfor 3D-printingItiseven possibletoidentifysome specifcchemicaladditivesor markersinsidetheflament’s compositionalongwith identifyingthecleaning substances,lubricants, adhesives,andsoonwhich couldhavebeenusedforthe maintenanceandfunctioning ofthe3D-printersand associatedmaterials.
Severaltechniquescan identifythechemical compositionofthe collectablesamples,as follows:FTIR(Fourier
TransformInfraredSpectroscopy),SEM-EDS (ScanningElectronMicroscopycoupledwithEnergy DispersiveSpectroscopy),RamanSpectroscopy, thermalanalysis,…
Inasimilarmanner,adetailedanalysis(microscopic viewofsurface,marksandlayers,cross-section,as wellasmeasurementsoflayer,wallandinfll…)ofthe printedobjectscanprovideinformationaboutthelayer heights,theprintingspeed,theinfllpattern,theshell thickness,material’sretraction…Allofthatwould supportthepotentialattributionofaprinterwithits printedobjects.Additionally,thepotentialfracturesin layersandfbers,theinternalexpansionofprinted objectsduetotemperature,theprintingpatterns,the printerconfrontationwithexpendableparts…couldbe usefulforpotentialattribution.
Thehardware(theprinterandassociated components)willleavesomesortof“fngerprint”,so toolmarksexaminationcouldbeappliedinthe aimofdiscoveringphysicalimperfectionssuchas misalignmentswiththebedoftheprinter,nozzlewear, printer’saxisbacklash,irregularitiesintheextruder, printsupportmarks…
Figure3:Comparisonof3Dprinters’cross-sectionednozzlewear. (Source–Fabbaloo)
Withregardstotheapplicationofdigitalmedia exploitation(MEDEX):
•Theanalysisofthecomputerswouldprovide essentialdatawithintelligence-valueas downloadinghistory,websiteaccess,socialmedia accounts…aswellascertainIPaddresses.
•TheRAM(Random-accessmemory)isalways storingdataflesasconnectedwiththesoftware installationand3Dprintingprocesses(e.g.log fles,MRU/mostrecentlyusedfles,andother fletypesindicating3Dprintingevidence).The presenceofcertain(DLLs)dynamiclinkedlibraries insideRAMwouldevidence3Dprintingprocesses.
•Theconfgurationdataareshowingallthechanges madetothehardwareandsoftwareofthesystem alongwiththeconnectionsasmadetotheprinter: asanexample,theoperatingsystem’sregistry databasecontainsrelevantdataregardinguser profles,connecteddevices,applications,and computerconfgurations.
•The3DCAD(Computer-AidedDesign)modeling fle(e.g.STLformat)containsgeometricdata, manufacturingspecifcations,andotherproduct
informationaboutthemodeldesignofanobject: but3Dprintersoperatewithinstructionsencoded ingeometric(g-code)flesfleformat,whichare text-basedflesinstructingthe3Dprinteronthe numberoflayersinthemodel,wheretoplaceeach layerintheprocess,materialtype,nozzlesize, timestamps,maximumprintingarea,andwhat temperatures(dependableontheusedmaterial) thatboththeprinter’sextruderandbedmust reach.Thereverseengineeringoftheg-codelogic couldalsoprovidevaluabledata.
•Thegeneratedflesandresidualdataremainon thesystem,indicating3Dslicingoccurredafter recoveringandanalyzingg-codefles,whichalso containmetadata.Inasimilarway,eachCAD softwarecanalsoembedmetadataintothefles.
Additionally,ascomputersand3Dprintersare usuallyconnectedthroughWi-Fibetweenthemand alsotothecloud,thecollectednetworkdataprovide bothplaintextandencryptedfles:thentheycouldgive informationabouttemperaturesofuse,thehost username,uniformresourceidentifer(URI),cookies…
Technicalexploitationisnotinthepoleposition regardingadditivemanufacturing WiththestrongimpulseasgivenbytheUkrainian confictandthehardtotrackinformationand components,theeasypublicaccessto3Dprinting capabilitiesforbothfrearmsandimprovisedexplosive devicesarenotannouncingaquietnearfuturefor counterterroristandcriminalactivities.
Nonetheless,theintenseresearchonthe applicationofforensicsinbeneftofthepotential attributionof3Dprintedweaponsinthelightofthe supportofartifcialintelligenceisallowingsomehope: wewillsee!■
“Everythingiscomplicatedifnooneexplainsittoyou.”
(FredrikBackmaninhisbook“MyGrandmotherAskedMeto TellYouShe'sSorry”,frstpublishedin2013)
REFERENCES
•X(formerTWITTER)
•TELEGRAM
• www.grainger.illinois.edu/news/stories/75700
• www.doi.org/10.3390/electronics13142864
• www.techxplore.com/news/2025-05-3d-printershidden-fngerprints-reveal.html
ABOUTTHEAUTHORS
LieutenantColonelJoseMRufas graduatedfrom theSpanishArmyMilitaryAcademyin1993.Hewas commissionedintotheC-IEDCentreofExcellenceas HeadoftheDefeattheDeviceBranchinAugust2016 andcurrentlyholdsthepostofChiefofAttackthe NetworksBranch.AsaMilitaryEngineerOffcer,his backgroundhasbeenmainlybasedonExplosive OrdnanceDisposalactivitiesintheSpanishArmyand C-IEDstaffissuesatthemultinationalheadquarters.In additiontohisEODOperator/EODOffcereducation, heattendedsomeothermilitarycoursesincluding Parachuting,ArmyStaff,InformationOperations,War CollegeGeneral/JointStaff,MilitarySearch,Technical ExploitationOperations,WeaponsIntelligenceTeam, ExploitationLaboratories,HomemadeExplosivesand otherC-IEDcourses.Hisoperationalassignments includeBosniaandHerzegovina(3),Afghanistan(3), theRepublicofEcuador,IraqandUganda.
Disclaimer
Thisarticledoesnotrepresenttheopinionofanynational ormultinationalorganisation;itswholecontentshould onlybeconsideredastheopinionoftheauthors.Asall informationhasbeenobtainedfromopensources, potentialmistakescouldhavebeenmadeduringthe researchprocess.Pleasefeelfreetosendyour comments,correctionsandinputstotheauthors;theywill behighlyappreciated.
MasterSargeantDavidHerráiz isworksasanIED AnalystintheDefeattheDeviceBranchoftheC-IED CentreofExcellence.Hismilitaryeducationincludes ExplosiveOrdnanceDisposalCourse,Technological RiskSpecialistCourseandC-IEDLevel1Technical ExploitationCourse.HisESPArmedForceseducation hasalsobeencomplementedbyinternational specializedtraininginTechnicalExploitation,healso countsonahugeexperienceinmultinational deployments.
MEASURINGTHEEFFICACYOFEORE: ODDSRATIOS,ANDANEVIDENCE-BASEDSOLUTION
ByDrRobertKeeley,RKConsulting(EOD)Ltd
InarecentpublicationbytheGenevaInternational CentreforHumanitarianDemining(GICHD),itwas notedthatthereisstillaneedtodevelopevidencebasedmethodstoassesstheeffectivenessof explosiveordnanceriskeducation(EORE).1
Theaimofthispaperistosetoutonesuchmethod, drawnfromthedisciplineofepidemiology,thathas beenappliedintwodifferentmineactionprograms. Thismethodiscalleda case-controlstudy,andthis paperwilldemonstratehowthisobjective,quantitative, andestablishedepidemiologicaltoolcanbeutilizedin EORE,especiallyaspartofaknowledge,attitude,and practice(KAP)study.
BACKGROUND:FOCUSGROUPDISCUSSIONS ANDTHE"STATEDPREFERENCEPROBLEM”
Currently,itseemsthatmostEOREprojectsdo attempttoassesstheeffcacyoftheirwork,butdoso inaqualitativemanner,oftenviafocusgroup discussions(FGD).FGDareaqualitativetechnique andassuchprovidecontextandassistresearchers
withunderstandingthenatureoftheissuetheyare studying.However,theproblemwithFGDandother such face-to-faceinterviews isthatthereisasignifcant riskoftherespondentprovidingwhattheythinkisthe rightanswer.Thisisknowntoeconomistsasastated preference problem.SeeFigure1.2
Revealedpreferencessurveys(RP)areabout choicesthatindividualshaveactuallymade.The strongpointofthistypeofsurveyisthatit providesuswiththerealchoicesmadebyusers inadeterminedcontextofconstraints...
Ontheotherhand,statedpreferencessurveys (SP)collectrepliestohypotheticalsituations presentedtousers...ThemaindrawbacktoSP isthattheyarebasedonthehypothesisthatthe userisgoingtomakethesamechoiceinthe scenariospresentedtothemastheywoulddoin reality,whichisnotalwaysthecase.
Figure1.Defnitionsofrevealedandstatedpreferences.3
1ExplosiveOrdnanceRiskEducation(EORE):Sectormappingandneedsanalysis,GenevaInternationalCentrefor HumanitarianDemining,14October2024, https://bit.ly/40riLSS.
2Wolffram,Elsner,TorstenHeinrich,andHenningSchwardt.2015.“CritiquesofNeoclassical“PerfectMarket”Economyand AlternativePriceTheories.”InTheMicroeconomicsofComplexEconomies.UniversityofBremen. https://bit.ly/4fU0kez. 3Ibid.
BACKGROUND:EPIDEMIOLOGY
Thescienceofepidemiologydatestothe1854London choleraepidemicandtheworkofJohnSnow4 to identifythesourceoftheoutbreak.TheWorldHealth Organization(WHO)defnitionofepidemiologyisset outinFigure2.5
Epidemiologyisthestudyofthedistributionand determinantsofhealth-relatedstatesorevents (includingdisease),andtheapplicationofthis studytothecontrolofdiseasesandotherhealth problems.
Figure2.TheWorldHealthOrganizationdefnitionof epidemiology.
Usingthisdefnitionandrecognizinganinjuryfrom minesandotherexplosiveordnance(EO)asa healthrelatedevent, itisappropriatetoapplyrelevant epidemiologicaltoolstointerpretingEOcasualtydata.
CASE-CONTROLSTUDIES
Whiletheprinciplesbehindcase-controlstudieswere beingdiscussedinthenineteenthcentury,thefrst moderncase-controlstudywasJanetLane-Claypon’s studyofbreastcancerin1926.Thenextmajorusewas in1950,whenfourpublishedcase-controlstudies linkedsmokingandlungcancer.6 Case-controlstudies havesincebecomeanestablishedstudydesignin epidemiologyandthesocialsciences.
Acase-controlstudyisatypeofobservationalstudy commonlyusedtolookatfactorsassociatedwith diseasesoroutcomes.7 Thecase-controlstudystarts withagroupofcases,whicharetheindividualswho havetheoutcomeofinterest.Theresearcherthentries toconstructasecondgroupofindividualscalledthe controls,whoaresimilartothecaseindividualsbut donothavetheoutcomeofinterest.Theresearcher
thenlooksathistoricalfactorstoidentifyifsome exposure(s)is/arefoundmore(orless)commonlyin thecasesthanthecontrols.
Oddsratiosandprotectiveeffect. Thekeymeans toanalyzeresultsincase-controlstudiesistheoddsratio (OR).TheORistheoddsofhavingadisease(or outcome)withtheexposureversustheoddsofhaving thediseasewithouttheexposure.
TheORtellsushowstronglytheexposureisrelated tothediseasestate.AnORofgreaterthanone impliesthediseaseismorelikelywithexposure.An ORoflessthanoneimpliesthediseaseislesslikely withexposureandthustheexposuremaybe protective.
Thispaperwillnowdemonstrate,usinghypothetical data,howacasecontrolstudycanbeusedtoassess theprotectiveeffectofEORE.
BUILDINGACASE-CONTROLSTUDYFOR EXPLOSIVEORDNANCERISKEDUCATION
Case-controlstudiesareretrospective:theresearcher worksbackwardintime,usingexistingdatasetsfor casualties.Thebestwayofunderstandinghowoneis builtisbyfollowingthestepsoutlinedinFigure3.
Step1.Identifythetargetpopulation
Thetargetpopulationcanbetheentirepopulationofa country,orperhapsjustoneprovince,orindeedany othersubgroup.Ifthecase-controlstudyisonly conductedinoneprovince,itmaybediffculttodraw conclusionsaboutotherprovinces,butofcoursethe biggerthestudy,themoreresourcesarerequired.
Step2.Identifycases
Thisiseasierincountrieswithexistingvictim informationsystems(VIS)butbewareiftheVIShas notbeenroutinelyupdated.Extratimemightbe
4Begun,Fahema.Mappingdisease:JohnSnowandCholera.9December2016.RoyalCollegeofSurgeonsofEngland. https://bit.ly/3ZzmpJJ
5TheGlobalHealthObservatory. https://bit.ly/3OVT8Tr.
6Paneth,Nigel&Susser,Ezra&Susser,Mervyn.(2004).Originsandearlydevelopmentofthecase-controlstudy. 10.1007/978-3-0348-7603-2_16.
7Steven,Tenny,ConnorC.Kerndt,MaryR.Hoffman.“CaseControlStudies.”NationalLibraryofMedicine. https://www.ncbi.nlm.nih.gov/books/NBK448143/
neededtoworkwithcommunityleaderstofnd additionalcasesifthoseintheVIShavesincediedor movedoutofthecommunity.
Itisrecommendedthatastudyselectscasesbyage andgenderinthesameratioastheyappearinthe overallVIS.Forexample,if70percentofthecasualties inthetargetcountryareadultmales,ensurethat70 percentofthecasesselectedareadultmales.See Figure4.
Step3.Identifycontrols
Controls–peoplewhoarenotEO casualties–shouldbeselectedas randomlyaspossiblebuttheoverall controlgroupmustrefectthesame demographicmakeupasthecases.It’s importanttoensurethatthecontrolsare asidenticalaspossibletothecasesin termsofage,gender,andlocation.This willhelpremoveanypotential confoundingvariables.
Step4.Interviewcasesandcontrols
Oncethecasesandcontrolshavebeen identifed,theycanbeinterviewed.For thepurposesofthecase-controlstudy, thereisonlyonequestiontoask:“Didyou receiveEOREtraining(beforeyour accident)?”Ofcourse,otherquestions relatingtoawiderKAPstudycanbe askedatthesametime.
Thereareanumberofsurveyethicsquestions whichmustalsobeaddressedatthistime.Firstly,the intervieweesmustgive informedconsent.Many academicinstitutionsrequireasigneddeclarationto thisextentwhichcanbeproblematicinplaceswithlow literacyrates.Insuchcircumstancesitcanbepossible toseekoralpermissionwithacommunityleader signingtowitnessthatconsentwasgiven.
Figure4.Identifyingcontrols.Thecontrolgroup(right)mustrefectthedemographicsofthecases(left)andshouldalso refecttheoveralldemographicsofcasualtiesinthecountry.
Figure3.Thestructureofacase-controlstudy.
Secondly,thereisariskofdisturbingacasualtywho issufferingfrompost-traumaticstressdisorder (PTSD).Data-gatherersmustbetrainedonhowto conducttheinterviewsinacomfortablelocation,andto recognizeandreacttosymptomsofPTSD.
Finally,thereisthequestionofinterviewingchildren. Itisunlikelythatagroupofdatagatherersconducting theinterviewswillbetrainedindealingwithchild casualties,andunderthesecircumstancesitwillbe bettertofndadultsurvivorswhowerechildrenatthe timeoftheiraccident.
CALCULATINGTHEODDSRATIO
Theinterviewswillidentifyfourgroupsofpeople:cases whoreceivedEORE(beforetheiraccident);caseswho didnotreceiveEORE(beforetheiraccident);controls whoreceivedEORE;andcontrolswhodidnotreceive EORE.It’scommontosetoutthesedatainan exposurematrix,andheretheyarerepresentedbythe lettersa,b,c,anddasshowninTable1.
Figure6.Calculatingtheoddsratio.
Itisalsopossibletouseanonlineoddsratio calculator8 todothiscalculation.Seetheexamplein Figure7.Thiscanhelppreventerrors,butitisalso usefulforassessingthestatisticalsignifcanceof results.Anexplanationofthestatisticaltests automaticallydonebythecalculatorcanbefound onlineastheyaretoolongtoexplainhere.9
Table1.Exposurematrixexample
Thetablehasbeenpopulatedwithsome hypotheticalresults.TheORisthencalculatedby usingthefollowingequation: (a x d) (b x c)
Figure5.OREquation.
Substitutingthehypotheticalresultssetoutin Table1,thisgivesaresultfortheORas0.32asshown inFigure6.
Figure7.Usinganonlineoddsratiocalculator.
8MedCalcSoftwareLtd.Oddsratiocalculator. https://www.medcalc.org/calc/odds_ratio.php (Version23.0.5;accessed October17,2024)
9Frost,Jim.“OddsRatio:Formula,Calculating&Interpreting.StatisticsbyJim. https://bit.ly/3Zw2OtN
Whatifthereisaproblemwithstatistical signifcance? Themostlikelyreasonforanissue maybeasituationwherethesamplesizewastoo smalltobeconfdentinaverysmallprotectiveeffect. It’spossibletohavecase-controlstudieswithvery smallsamples,butwhereverresourcesallow,the largerthesamplethebetter.
Category Description
REAL-WORLDRESULTS
Thismethodhasbeentriedtwicebytheauthor:the frstinCambodiain2020andthesecondinLaos10 in 2023.TheresultsaresetoutinTable2. Theoddsratiocalculationsforbothstudiesareset outinFigure8.
(b) (c)
Category‘a’ NoofcasespreviouslyexposedtoEORE 12 24
Category‘b’ NoofcontrolsexposedtoEORE 19 45
Category‘c’ NoofcasesnotexposedtoEORE 13 47
Category‘d’ NoofcontrolsnotexposedtoEORE 17 19
Total 61 135 Samplesize
Table2.Real-worldresults.
Figure8.OddsratiocalculationsforCambodia(left)andLaos(right).
10Knowledge,Attitudes,andPracticesStudy.”15October2024.UNDP,LaoPDR. https://bit.ly/3OyCEjI
Whilstbothdemonstrateda protectiveeffect (i.e., wheretheOR<1),thecalculatorshowsthattheresults forCambodiawerenotstatisticallysignifcant.Thiscan beattributedtotherelativelysmallsamplesize.The lessonlearnedfromthisisthatforEORE,asuitable minimum samplesizewouldbearound120intotal.
ADVANTAGESANDDISADVANTAGESOFCASECONTROLSTUDIES
Case-controlstudieshaveseveraladvantagesand disadvantages.
Advantagesofcase-controlstudies. Firstly, case-controlstudiesarelesssusceptibletothe stated preferencesystem commonlyfoundwithinthemine actionsector.
Secondly,case-controlstudiescanbeconductedin situationsofrareevents,i.e.,withrelativelysmall samplesizes comparedtootherquantitativemethods Disadvantagesofcase-controlstudies. The maindisadvantagewithcase-controlstudiesinthe contextofEOREisthattheyarearetrospectivestudy. Assuchitishardtousetheminverynewconfict settings.Similarly,it’sharder(butnotimpossible)to conductacase-controlstudyincircumstanceswhere thereisnofunctioningVIS.Undersuchcircumstances it’snecessarytoallowmoretimetoseekoutcasesby makinginquiriesamongstlocaloffcials.
Anotherdisadvantage–thoughmoreofalimitation –isthattheresultsareaggregated.Thestudymight revealthatEOREinaparticularprovinceiseffective, butonitsownitwon’trevealwhichvectorforEORE hasbeenthemost(orleast)effective.Thisiswhyit’s usefultoembedacase-controlstudywithinaKAPso thatotherresearchmethodscanbeusedtoprovide otherinsights.
CONCLUSIONS
Case-controlstudieshavebeenusedfornearlya centurytoexaminethequantitativerelationship betweenexposuretoaparticularvariableandamedical outcome.Assuch,theyareastandardepidemiological tool,arenotparticularlycomplicated,andcaneasilybe incorporatedintoaKAP.Furthermore,theyproduce objective,quantitativeresults,unlikeFGD.
However,basedontheexamplessetoutinthis paper,case-controlstudiesrequireaminimumsample size(atleast120,dividedequallybetweencasesand controls).Also,inregionswherethereismorethanone meanstodeliverEORE,acase-controlstudycannot byitselfinformontherelativeeffcacyofthosedifferent EOREmeans.Usingthecase-controlstudyaspartof awiderKAPcanresolvethis.
Anyonewishingtoknowmoreabouthowto conductacase-controlstudyiswelcometocontact theauthor. ■
ABOUTTHEAUTHOR
Dr.RobertKeeley isaformerBritish ArmyBombDisposalOffceractive inhumanitarianandcommercial mineactionandexplosiveordnance disposal(EOD)since1991.Hehas workedinnumerouscountriesand forseveralgovernmentsand internationalorganisations.He specializesinprojectdesign,evaluation,andquality assuranceofallaspectsofmineactionandhashelped shapetheemerginghumanitarianimprovised explosivedevice(IED)sector.Dr.Keeleyisamember oftheInstituteofExplosivesEngineers,aMemberof theInternationalAssociationofBombTechniciansand Investigators,andisaFellowoftheRoyal GeographicalSociety.HeholdsaPhDinApplied EnvironmentalEconomics;histhesiswason“the EconomicsofLandmineClearance.”
ContactInformation
Dr.RobertKeeley,Director,RKConsulting(EOD)Ltd Ashford,Kent,UnitedKingdom Bobkeeley@rk-consulting.net www.rk-consulting.net
“BIRDSDETONATINGOVERALKEBULAN”: THEGROWINGUSEOFEXPLOSIVE-LADENDRONES BYNON-STATEACTORSINTHEAFRICANCONTINENT
ByJoseMRufas,SubjectMatterExpertinC-IEDandTechnicalExploitation
“Themostdangerousbirdisafghterpilot.”
(TamerlanKuzgovinduringhisconference
”,2004)
On30January2024,theUnitedNationsInstitute forDisarmamentResearch(UNIDIR)publisheda report(TheuseofuncrewedaerialsystemsbynonStatearmedgroups:ExploringtrendsinAfrica)in whichtheauthorshowednootherreferencestothe potentialuseofexplosive-ladendronesbynon-state actorsinAfricathanseveralinitialtrialsbyJama’a Nusratul-Islamwaal-Muslimin(JNIM)inMali,Daesh inWestAfricaWilayat(ISWAP)inNigeriaandAlShabaabinSomalia,alongwithsomemanualsonthe matterasseizedfromthosegroupsby lawenforcement.
Nonetheless,somepreviouscasesin relationtotacticalemploymentandseized materialsasconnectedwithexplosiveladensmall,unmannedaircraftsystems (s-UAS),werereportedbylocal authoritiesinAfrica,asfollows:
•In2018,aquadcopterfttedwith improvisedmunitionsandusedbythe Libyaninsurgencywasdowned(most probablyitwaspreviouslytakenby themfrommilitarydepotsafterthefall oftheregime).
•InOctober2021,militaryforcesinthe CentralAfricanRepublicreported
seizingaDJIMAVICfttedwithaChineseType 82-2handgrenadewithitspintetheredtothe dronebyastring.
•InMarch2022,as-UASwithexplosivepayload wasallegedlyreportedasdownedbyLaw EnforcementinCaboDelgado,Mozambique.
•Since2024,commercialdroneshavealsobeen usedtosmuggleweaponsandexplosivesin supportofPalestinianmilitiasacrosstheEgyptian border.
Figure1:Pictureofanexplosive-ladendroneasreportedinCentralAfrican RepublicCAR. (Source–CARArmedForces)
“AlQaeda´sAfricanAirForce”ortheuseof explosive-ladendronesbyJNIMgroup
ThefrsttacticaluseofJNIMdronesdroppingacouple ofimprovisedmunitionsagainstpositionsheldbythe Dogonself-defencemilitiaDanNaAmbassagou,in Bandiagara(MoptiregionofMali)wasreportedin September2023.
Fromthenonwards,JNIMattackswithexplosiveladendroneshavebeenevidencednotonlyinMali,but alsoinsideothercountriesinwhichthegroupis conductingactions,suchas:
•4April2024:JNIMusedaUASvehicleborneIED (VBIED)againstDozomilitiamembersinMopti regionofMali.
•March2025:frstcasesofJNIMusingexplosiveladendronesinsideBurkina-Faso.
•9April2025:aUASVBIEDwasusedagainsta policepostinSavanesregionofTogo.
•3May2025:simultaneousattackswithtwo explosive-ladenfrst-personview(FPV)dronesin Kabankoura,Segouregion,Mali.
JNIMismostlyusingChinesecommercialoffthe shelf(COTS)DJImodelsfortheirattacks(dropping munitionsorasaUASVBIED)fromtheairagainst localarmedforces,locallawenforcementmeans, infrastructure,opposingmilitias,andRussianprivate militarycompanies.
Figure2:JNIMCOTSdronefttedwithYugoslavianM-5760mmmortargrenadeinBurkina-Faso. (Source–X)
(Source– ChirpWire)
RegardingthetypesofIEDsusedbyJNIMfor theattackswithexplosive-ladendrones,wecould evidencetheuseof:
•Conventionalmunitions(e.g.mortargrenades, handgrenades,rocketpropelledgrenades…) withmanipulatedfuzes(theyareconsideredas IEDduetothemanipulationfromtheoriginal fuze).
•Droppableimprovisedexplosivedevices(IEDs) initiatedbymilitaryfuzesorimprovisedones.
•IEDswhichtransformthedroneintoaUAS VBIED.
Migrationoftactics,techniquesandprocedures fromUkraine:theTouaregcase
Inasimilarmanner,thetacticaluseofCOTSChinese VTOL(VerticalTake-OffandLanding)andFPV explosive-ladendroneshavebeendocumentedby theFrontfortheLiberationofAzawad(FLA)from February2025onwards.
Morerecently,socialmediahaveshownFPVdrones fttedwithimprovisedmunitionsandwire-guidedby fbreopticinthehandsofFLAfghters.Itisalsoa designandTTPwhicharecurrentlyemployedinthe Ukrainianconfict.
Figure3:AzZallaqapostershowingJNIMoperations28May-25June2025,including3attackswithdrones.
ThemaindifferencebetweentheFLAandJNIMin thetacticaluseofexplosive-ladendronesisthatthe FLAhascloselyfollowedboththetacticalutilization andthetechnicaldesignthatUkrainianforcesare usingthousandsofkilometersawayfromtheSahel.
Itimpliesthatthetechnologiesasusedbythe Touaregseparatistsaremoredevelopedandadvanced thanthoseimplementedbyJNIM…andevenmuch morecapableandeffective.Infact,theFLA
spokesperson(followingtheJuly2024jointFLA–JNIM attackonMalianArmedForcesandWagnerpositions inTinzaouaten)declaredthatthegrouphadacquired itsowndronesandtrainedadedicatedteamovera ten-monthperiod.
AlthoughFLAdeniedreceivingdronesdirectlyfrom Ukraine,somereportingsuggestsUkrainianmilitary intelligencemayhavecontributedtoshapingFLA’s tacticalmodelinadvanceoftheattack…
Figure4:ScreenshotfromFLAvideoofanattackonaMalian/RussianconvoyinJune2025. (Source–X)
Figure5:FLAcombatantswithawire-guidedFPVexplosive-ladendrone/VTOLUASFDG410asusedbyFLA. (Source–FLA)
DAESHisalsoplayingwithdronesflledwith“gifts”
Thefrstevidenceduseofexplosive-ladendronesby DaeshinWestAfricaWilayat(ISWAP)wasconducted throughtwoattacksagainstmilitarybasesinBorno state,Nigeriaon24December2024:itwasfollowedby otherattacksagainstmilitarybasesinthesameBorno state(WajikoroandWulgo)on24March2025.
Ontheotherhand,DaeshinSahel(IS-Sahel) launchedanattackwithaFPVUASVBIEDinTillaberi, NigerinMay2025.
ButitisDaeshSomalia,thegroup´sfranchisewhich hasbeenusingmanyexplosive-ladendrones(inthe formofFPVUASVBIED)inPuntland,Somalia.
Withregardtothekindofs-UASasusedbyeach regionalDaeshfranchise,DaeshSomalialooksasthe moreadvancedoneduetotheiruseofexplosive-laden FPVUASVBIED,whileISWAPandIS-Sahelare mostlybasedonCOTSDJImodels.
Thetacticaluseofexplosive-ladenCOTSDJI modelswasalsoreportedinChad.
InNigeria,notonlyDaeshbutotherdifferentgroups aremanufacturingdronesfortheirfurtheruseas
explosive-ladenones:e.g.theEasternSecurity Network(ESN),armedwingoftheIndigenousPeople ofBiafra(IPOB)builtadronefactoryatOnichaUlona inDeltaState,whichwasdismantledbylocal authoritieslate2023.
OtherpotentialorevidencedusesofexplosiveladendronesinAfrica
TherearereportsindicatingthatAl-Shabaabdrones wereinterceptedbeforeimpactinGalgaduud,Somalia inFebruary2025.
FromMay2025onwards,theRapidSupportForces (RSF)conductedseveralattackswithimprovised munitionsasdroppedbydronesaswellasattackswith FPVUASVBIEDagainstinfrastructureandmilitary convoysinSudan.Thematerials(FPVs-UAS)and someoftheattacksaresimilartothoseconductedby Ukrainianforces…
Theuseofawire-commandfbreopticexplosiveladendronebyM23(Mouvementdu23-Mars)fghters inSouthKivu,DemocraticRepublicofCongohas beenreported.
Figure6:FPVexplosive-ladendronefromDaeshSomaliafghters. (Source–X)
Figure7:Wire-commandFPVdroneseizedfromM23group inDRCinSeptember2025. (Source–www.military.africa)
Whenyour(southern)neighbor'shouseison fre,carrywatertoyourown…
TheinfuenceoftheUkrainianconfictisunfortunately resultinginfromthehugepossibilitiesthattheAfrican instabilityproduces,asisevidencedregardingthe migrationofinformation,tactics,techniquesand proceduresintheuseofexplosive-ladendrones.
Apotentialcombinationof“very-hard-to-counter” FPVs-UASVBIEDwiththeiravailabilityinthehandsof membersofreligiouslymotivatedviolentextremist groups(ascapableofenteringEuropeanUnion withoutanyalarmtoberaised)wouldcertainlyposea highriskforhomelandsecurity.■
“Youwannafy,yougottogiveuptheshitthat weighsyoudown.”
(ToniMorrisoninherbook“SongofSolomon”,frstpublishedin1977)
REFERENCES
•BárbaraMoraisFigueiredo,“Theuseofuncrewed aerialsystemsbynon-Statearmedgroups: ExploringtrendsinAfrica”.Geneva:UNIDIR,2024. https://doi.org/10.37559/CAAP/24/PACAV/01
• www.policycenter.ma
•ChirpWire
•RocketChat
•X(formerTWITTER)
•TELEGRAM
Disclaimer
Thisarticledoesnotrepresenttheopinionofany nationalormultinationalorganisation;itswholecontent shouldonlybeconsideredastheopinionoftheauthor. Asallinformationhasbeenobtainedfromopen sources,potentialmistakescouldhavebeenmade duringtheresearchprocess.Pleasefeelfreetosend yourcomments,correctionsandinputstotheauthor; theywillbehighlyappreciated.
ABOUTTHEAUTHOR
LieutenantColonelJoseMRufas graduatedfromthe SpanishArmyMilitaryAcademyin1993.Hewas commissionedintotheC-IEDCentreofExcellenceas HeadoftheDefeattheDeviceBranchinAugust2016 andcurrentlyholdsthepostofChiefofAttackthe NetworksBranch.AsaMilitaryEngineerOffcer,his backgroundhasbeenmainlybasedonExplosive OrdnanceDisposalactivitiesintheSpanishArmyand C-IEDstaffissuesatthemultinationalheadquarters.In additiontohisEODOperator/EODOffcereducation, heattendedsomeothermilitarycoursesincluding Parachuting,ArmyStaff,InformationOperations,War CollegeGeneral/JointStaff,MilitarySearch,Technical ExploitationOperations,WeaponsIntelligenceTeam, ExploitationLaboratories,HomemadeExplosivesand otherC-IEDcourses.Hisoperationalassignments includeBosniaandHerzegovina(3),Afghanistan(3), theRepublicofEcuador,IraqandUganda.
Counter-IEDReporteditorialteaminvitesgovernmentbodies,armypersonnel,researchers, industryexpertstocontributetheirarticles,casestudies,whitepaperstothereport.
Wearelookingforboththeoreticalandpracticebasednon-promotionaleditorialcontributions. Onlyoriginal,sofarnotpublishedarticlesareaccepted.
Allenquiriesandarticlesshouldbesubmittedbyemailto: editorial@deltabusinessmedia.com
Formoreinformationpleasevisit: www.counteriedreport.com/editorial
UniquecontentIGlobalreachIInprintandonline
Keepup-to-datewiththelatestC-IED,EODandCBRNenewsanddevelopments. Subscribeat www.counteriedreport.com/subscribe
X-raySystemsDesigned andBuilt forBombTechs
DualDRandCRX-rayImagersinOneX-raysystem Extendyourx-raycapability.Domore.Seemore.Safely.
SCANSILC-LightweightRuggedisedDRX-rayDetectors
• Collectdetailedx-rayimages inonoro inemodesusinganysized ScansilcDRx-raypanel.
• Scansilcreduces timeontarget-Minimalcomponentsandsetup-getthe jobdonequicklyande ciently.
• Reliablewhenitcounts-Rugged,Resilient,Dust,Dirtand WaterResistantinallenvironments.
SCANSILCINTELLIGENT HARDENEDX-RAYIMAGEPLATES
• 86x86cm
• 43x57cm
• 36x43cm
• 24x30cm
• 18x24cm
SCANXSCOUT-CRX-rayImagePlates
•Flexibleplates–Truegroundlevelimaging.Slideplatesintotight areasandwraparoundobjects.
•Fastgrabandgo-nocablesorwi-fitoconnect-sonodropouts.
•Combinemultipleplatesingrid formattox-raylargetargets/vehicles.
OnecontrollerandUK designed,licence free ScanViewso warerunsboth CRandDRplates.
DOMOREWITHSCANX SCOUTFLEXIBLE PLATES