Cyber Security
Investigator and that is why the skills shortage is a real challenge. While technical skills can be taught, Stephen Kho believes that attitude is key. “During the interview, I would ask technical questions, but this is only to allow me to gauge how much technical training I need to give. From an incident response perspective, having ability to think outside the box and analytical abilities are key to enable a Level 1 security analyst to progress to a Level 2 for example, where the security incident related tasks are more challenging. At the security analyst Level 2 level and above, the investigative activities can include digital forensics, network analysis and reverse engineering. Inquisitiveness and having the motivation to learn are vital traits, especially as the attack landscape is constantly evolving and the level of attack sophistication is increasing.” Uncovering cybercrime and expectations from authorities Should a cybercrime be uncovered, Authorities would want to clarify that the data handling & information dissemination steps the client has taken comply with the relevant legal requirements. This includes the policies and procedures that are in place internally. Stephen acknowledges that this encompasses many aspects. “For example, HR policy should set out code of conduct in relation to data handling policy pertaining to privacy and protection of personal and sensitive data. There should also be procedures on data breach notification and the relevant escalation triggers and procedures. This should also include disclosure and confidentiality procedures in the event of a potential cybercrime under investigation, including who is allowed access to the investigation details and progress. These policies would be aligned to the rules and regulations of the relevant jurisdictions that the client operate under. Internally, forensic handlers must understand the regulatory and legal requirements, and these vary across jurisdictions, meaning, how to handle evidence and maintain evidence for admission into the court of law. With HPE
Consulting we share with our clients, in our training sessions, the framework to ensure that adequate policies and procedures are in place to process information and data relating to cybercrime, that comply with the legislations and regulations.”
on the server had
Achieving outcomes from Incident Response
been reported,
The IR platform must have a good reporting and tracking functionality, including workflow and case management functionality. It is important to have a robust reporting tool with time stamped and staged details for events, and acknowledgement of who is looking after which case. This allows members of the team to do immediate investigations, make informed decisions and take appropriate and timely action. Team members who are responsible for responding to incidents need to be familiar with the reporting tool, as well as the policies and procedures on documented standards. This includes the minimum amount of information that needs to be captured to enable handoffs between L1 and L2 security analysts. Or between experienced and newer members of the team. “For example,” Stephen notes, “if a malware on the server had been reported, the reporting tool should highlight if it had been resolved, and if not, what is the resolution stage of the incident, and who is the case owner. It is important for the reporting tool to capture the right information, that is, relevant and timely information. Availability of actionable data is important to enable the team to understand the background of the issue, and the case status. At HPE Consulting we help our clients achieve this by a combination of initial and continuous training and teaching. We share the best practices in terms of opening and closing an incident with an adequate audit trail. We also provide training on frameworks and approaches that allow the clients to standardise the documentation in a consistent manner, in order to allow decisions and actions to be taken. Not only does this reduce the time spent on response, it also addresses the skills shortage challenge, which is one of the key areas we are focusing on in our roadmap.”
the reporting tool
"if a malware
should highlight if it had been resolved, and if not, what is the resolution stage of the incident, and who is the case owner. It is important for the reporting tool to capture the right information"
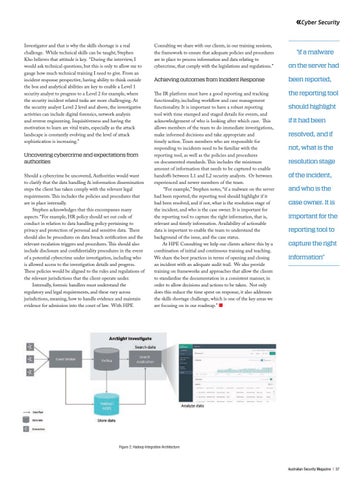
Figure 2: Hadoop Integration Architecture
Australian Security Magazine | 37