
32 minute read
In Session
from GT Magazine Demo
A court and technology lab collaboration brings a new tool aimed at making the eviction appeals process more accessible.
By Jule Pattison-Gordon / Staff Writer
Advertisement
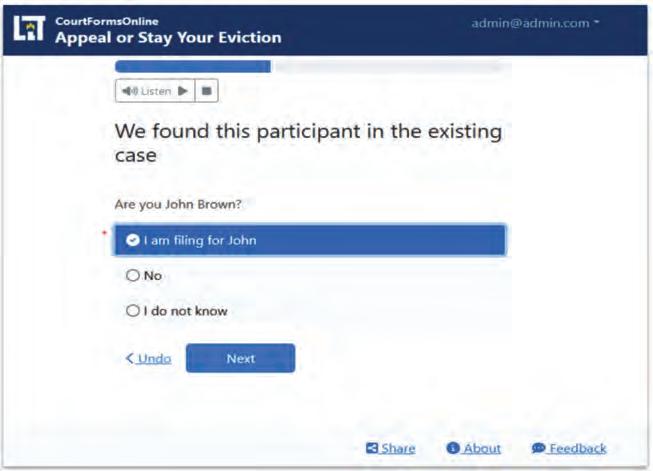
Massachusetts tenants facing eviction orders are often presented with a daunting task when trying to navigate the appeals process, explained Paul Tuttle, assistant clerk at the Massachusetts Appeals Court, speaking during the National Center for State Courts (NCSC) eCourts conference in December.
Pandemic-era court closures only added to the struggle and sent him searching for a fi x. A collaboration with Suff olk University’s Legal Innovation and Technology Lab led to a digital, guided interview tool for defendants who are facing eviction within the next 48 hours. The result, Tuttle said, is a simpler and quicker experience for defendants, and clerks receiving more accurate information.
A Blank Piece of Paper
Ninety percent of defendants in eviction cases represent themselves, Tuttle said, and, pre-pandemic, those whose motions were denied in housing court had to go to Boston to appeal — regardless of where in the state they lived — or fi le online. If they wanted help understanding what kind of information to submit when e-fi ling, defendants had to come to the clerk’s offi ce in Boston. Another challenge? The clinic helping defendants was only open on Wednesdays for two hours.
When defendants came outside the clinic’s hours, clerks “essentially … had to give the litigants a yellow legal pad and tell them that they needed to fi le a motion, and roughly what type of information needs to be in that motion,” Tuttle said. “But really, they were faced with just a blank piece of paper.”
This led to confusion and mistakes. Clerks sometimes received forms with off -topic explanations from defendants confused about what was being asked of them. Fee waiver applications accompanying eviction stay requests might be missing checkmarks or signatures that tenants then had to return to complete.
When the pandemic hit, Tuttle tested a variety of off -the-shelf digital forms in hopes of smoothing the process, before teaming up with the Suff olk lab for a custom off ering.
Their collaboration led to a guided interview tool that helps self-represented litigants go step by step through eviction appeals petitions and several other legal fi lings, with explanations provided. The team continues to iterate on the project, updating features, adding availability in new languages and adding other legal procedures.
A Guided Tool
The tool has been a game-changer for both litigants and clerks, Tuttle said.
Thanks to the guidance the tool gives, clerks receive more relevant
Left to right: Paul Tuttle, Bryce Willey and Quinten Steenhuis speaking at the National Center for State Courts eCourts conference Dec. 5.
JULE PATTISON-GORDON

and complete information from litigants. Plus, clerks receiving paper forms need to type up details by hand, but e-fi lings fl ow more easily into court systems, saving about 20 data entry steps per fi ling.
In turn, the tool spares selfrepresented defendants from having to decipher legal nuances and idiosyncrasies, explained Quinten Steenhuis and Bryce Willey, who are both clinical fellows at Suff olk’s Legal and Innovation Technology Lab. For example, the team also introduced the e-fi ling tool in Illinois, where people fi ling without attorneys must list a specifi c six-digit code that varies by county; the digital tool can fi nd and plug in the code for them.
The tool also gives users rapid access to judicial services. In one instance, a defendant was mid-eviction when she pulled out her smartphone to fi le a motion of appeal. Her approval came in soon after, while the constable was in the middle of removing her property from the premises, Tuttle recalled.
“The eviction started at 9:30 in the morning,” he said. “We got the motion at about 9:45 a.m., and by 10 o’clock there was a judicial order to stop the eviction, so the constable had to move what [furniture] he’d gotten in the truck back into the house and the case was stayed, because there was a problem with how eviction happened in trial court ... there’s just no way she could’ve fi led that motion without the guided interview tool.”
Accessible Design
To make the tool widely useful, the team needed accessibility features. That included designing for those with vision limitations and putting the information in terms accessible to a fourth to sixth grade reading level, Steenhuis said. Features designed to make tools inclusive to people with particular needs also frequently end up benefi ting the majority of users, Willey noted.
Plus, they decided the tool should guide litigants all the way through the process — including having a “one click” process to submit the form to court. Too many off erings fall short by supporting users through one part but then abandoning them to fi gure out the fi nal steps on their own, Steenhuis said.
Given today’s cybersecurity climate, limiting data retention was also important. Willey said they automatically delete data after 30 days if users don’t re-engage with the tool, meaning there’s less information that hackers could potentially steal.
A Software Mindset
A good-enough but available tool is more helpful to tenants than a polished one that releases after they’ve been evicted, speakers said. That meant getting over courts’ usual reluctance to release anything but a highly polished product, Tuttle explained.
Instead, the Suff olk team pushed an iterative approach. They identifi ed what, ideally, they’d like the tool to look like, but decided to release a version of the product once they had something better than the status quo — i.e., better than a PDF or printed form to fi ll out at home, Steenhuis said.
Once that early version was available and helping people, the team could then dig into adding and testing improvements, like user experience tweaks.
Bringing together the judicial and software worlds was important for another reason too: Courts need to stay neutral and avoid giving advice to any party. The collaboration let court representatives stay fi rmly on the side of providing legal expertise, while leaving their tech lab partners to host the software and decide what content to use.
“We can objectively say, ‘What I’m trying to be is helpful,’ which is something that’s a little bit trickier sometimes for the court to do,” Steenhuis said.
The team is two years into the project, and the lab expects to be able to maintain the off ering in part by having students work on it as part of their coursework.
Automating and Accelerating the Constituent Experience
Eliminating manual tasks makes life easier for the public and the government employees who serve them
For far too long, government agencies have implemented community-facing processes that have boiled down to a constituent fi lling out a paper form — and then waiting and wondering. But new process-automation platforms empower governments to overcome paper-driven delays while bringing their constituents clarity and transparency on the status of grant applications and other intricate agency functions.
This brief from the Center for Digital Government explains how process automation platforms can help agency leaders narrow the timelines for complex operations and ease the workload on their hard-pressed staff .
Automation in Action: Transforming a Grant Application
A grant application for COVID-19 local business relief illustrates the potential for an automation platform to make government interactions less cumbersome and more productive.
The problem. A county government had to quickly deliver emergency grants to local businesses that lost income during the pandemic. Paper-based, manual processes dragged out muchneeded fund distributions.
The solution. The county partnered with Laserfi che, a global enterprise software provider, for document management and business process automation to accelerate the grant-approval process and help desperate business owners. Before these changes were made, the grant process took up to three weeks.
“We were able to get the processing time from application to funds distribution down to only three days,” recalled Allison Young, senior director with Laserfi che, in a recent webinar hosted by the software vendor.
How it Worked
In the webinar, Young used her company’s automation platform to demonstrate the steps required to automate and simplify the grant approval process. These steps included creating a form for businesses to enter their location, demographic information and fi nancial impact from the pandemic. Laserfi che helped the agency develop a scoring system based on familiar Microsoft Excel formulas that automatically calculated COVID-related damages. Businesses with the highest scores could then be eligible for the most funding.
Background processes used API calls to an Internal Revenue Service database to validate the company’s existence. A mapping application was used to locate the business address.
“We needed to know what district that business was tied to,” Young explained. This was required to ensure aid was distributed equitably across the county’s districts.
After the applicant entered the necessary data, the automated system sent the application and its score to the people responsible for approvals. They could see all the relevant data and quickly decide the funding total. Checks and balances were built in to give county staff the fi nal say on distributions and to avoid accidental refusals.
Payments by check or bank deposit went out automatically. Finally, all documents created during the process went into a repository that had been indexed to make it searchable.
Because the software and forms are hosted in the cloud, staff can access the system through any web-enabled device. “And we can now run reports and analytics on how long each step in the process took,” Young said. Thus, the automation platform gives leaders insights into making the process even more effi cient in the future.
Agencies have accumulated decades of manual processes that present vast automation opportunities. For instance, when a developer applying for a zoning variance calls an agency to fi nd out the status of her application, she’s taking time away from essential business activities.
Meanwhile, every phone call from a constituent distracts agency staff from whatever they’re working on. Simply creating

process that keeps everyone apprised of an application’s status can save signifi cant time for agency staff and the public.
Almost any department in a public agency, from law enforcement to tax collection, can benefi t from automation. But agency leaders must keep a few points in mind when they’re choosing an automation platform:

Data and analytics are pivotal. Automated, digital processes generate mounds of useful data. With a robust automation platform, agencies can synthesize data from multiple sources and use reporting tools to discover the implications of newly digitized processes.
“We can’t see the full picture all the time,” says Noel Loughrin, strategic solutions manager with Laserfi che. “Our brains just aren’t built to do that type of analysis on the fl y.”
Analytics tools help agency staff visualize the value of automation. “You can track your business processes to gain an understanding on how they’re progressing, fi nd bottlenecks and gain insights on optimizing processes,” Loughrin says.

Human decision-making cannot be automated. While automation can accelerate processes and improve effi ciency, technology is no substitute for human discretion and judgment.
Agency staff must retain the fi nal say in automated processes. A well-designed automation platform takes this into account, creating notifi cations and workfl ows that produce more timely decisions.
“The human element of these processes and applications is still very much built in,” Loughrin says. “The platform just eases the administrative burden of following up and making sure things are done in a timely manner. And communication is seamless.”

Digitizing manual processes is not enough. Rather than starting by finding digital equivalents of analog actions, agencies should thoroughly analyze business processes fi rst. Agencies may need to adjust or re-engineer processes to get the most out of an automation platform and drive genuine productivity improvements.

Best Practices for Success with Process Automation
Successfully implementing a process automation platform has three components:
Personnel. People must be trained to use new software and encouraged to adopt it. This includes leaders, agency staff and public users. “Work with your internal teams to see where they’re struggling,” Loughrin advises. Their struggles will often point to opportunities. Automating processes that eliminate their roadblocks and demonstrating how the new process does so will make it easier to encourage adoption of a new system.
Processes. Agencies must fully understand the steps in the processes they hope to automate, ensuring the automation platform provides data-driven insights and improves visibility and transparency for users. “Once you fi gure out those issues, then you have to prioritize what processes are going to do the most good fi rst,” Loughrin says. Software. Applications must be easy to use, relying on tools like low-code/no-code apps that allow new features to be added quickly and easily with minimal technical acumen. Controls should be built in to discourage cybercrime and protect sensitive data.
Ultimately, the software solution should help agencies break down data silos and act on the automation opportunities that arise. Don’t try to automate everything at once. Instead, use pilot projects to fi gure out what works best for your organization.

Easier Processes for All
Loughrin advises agencies to stay focused on what’s coming next in terms of new capabilities. For instance, robotic process automation bots can detect a water main leak and trigger an alarm that dispatches repair crews to the scene fast enough to limit property damage.
Agencies can also boost self-service options for the public, letting them use government services whenever they choose. “You can make them feel more comfortable with their government because there’s more transparency and communication, and it doesn’t have to happen on government’s time,” Loughrin says. “It can happen on your constituents’ time.”
There’s no need for agency processes to be fraught with delays, confusion and aggravation. A process automation platform can help agencies simplify and accelerate their most elaborate functions, giving time back to their staff and streamlining interactions with the public.
This piece was written and produced by the Center for Digital Government Content Studio, with information and input from Laserfi che.
Produced by: The Center for Digital Government, a division of e.Republic, is a national research and advisory institute on information technology policies and best practices in state and local government. Through its diverse and dynamic programs and services, the Center provides public and private sector leaders with decision support, knowledge and opportunities to help them eff ectively incorporate new technologies in the 21st century. www.centerdigitalgov.com.
Sponsored by:
Laserfi che is the leading SaaS provider of intelligent content management and business process automation. Through powerful workfl ows, easy to use low-code automation tools, document management and analytics, the Laserfi che® platform accelerates how business gets done, enabling leaders to focus on growth across the enterprise. Learn more here.
Read full reports and breaking news about career changes across tech-driven roles in government at govtech.com/people.
Donald Beamer Jr.
Atlanta Appoints Senior Technology Adviser

Atlanta has announced the appointment of Donald Beamer Jr. as the city’s fi rst senior technology adviser to help build on the city’s technology workforce and business ecosystem. In the new role, Beamer will serve as the chief liaison with the technology sector for the mayor and help guide policy development. This is an external role that does not overlap with the CIO’s duties.
Minnesota CIO to Stay for Governor’s Second Term

Minnesota CIO Tarek Tomes — who was fi rst appointed by Gov. Tim Walz — was reappointed to the governor’s cabinet. The announcement came in the immediate aftermath of Walz winning re-election.

Kansas IT Chief Steps Down
DeAngela Burns-Wallace, secretary of administration and chief information technology offi cer for Kansas, left her position Jan. 6. She served in the dual role since 2019, and a statement from the governor’s offi ce indicated that Burns-Wallace would return to teaching in the spring. As of press time, a successor had not been named.
California Names Deputy CIO
Gov. Gavin Newsom in December appointed Jared C. Johnson to the dual role of deputy state CIO and chief deputy director of the California Department of Technology. A 20year veteran of state service, Johnson replaces Russ Nichols, who retired in November.
Jared C. Johnson
Tech Leadership Changes in Cincinnati
Sean Ware was named interim director of Cincinnati Enterprise Technology Solutions upon Tarun Malhotra’s departure from the role in August. Ware has worked for the city’s IT agency since 1995, most recently as manager of enterprise applications.
DeAngela Burns-Wallace Sean Ware




Cybersecurity in the Age of 5G

How will 5G connectivity affect cybersecurity for government agency IT leaders?

Does 5G’s expanded network capacity create a new set of security concerns?
More spectrum means an increase of devices and end-user units, which expands the threat landscape. For example, 5G should eventually support one million Internet of Things (IoT) devices per square kilometer, an order of magnitude more than what’s possible today. Networks are also becoming more important and more integrated into organizations’ operations, so any network disruption can have profound effects.

Is 5G more secure than previous generations of wireless technology?
5G is like a Zero-Trust architecture, in that the network is presumed to be open with no security from overlaid products and processes. All links are assumed to be exposed. To control for that openness, 5G mandates encryption of all inter- and intra-network traffi c and provides for enhanced device and network authentication. There’s a great focus on roaming, which has been a security gap in the 4G LTE environment. For example, fi nal device authentication in 5G is always by the home network, not by the visited network, and 5G uses public/ private key pairs for authentication. 5G has greatly enhanced roaming protection and security compared with previous generations.
Where should agencies focus their attention on addressing cyber risks in the shift to 5G?
The fi rst step is the move toward Zero Trust, assuming no inherited authentications and challenging all transactions. Remember, you’re securing everything: the network as well as, for example, storage and technologies like containerization. Next, adopt an attitude of continuous vigilance, including selfscouting and self-hacking. Engage with security expertise across the ecosystem. But understand that you’re never going to arrive at total security. Something new will come up every day.
Tony Dolezal, public sector 5G and multiaccess edge computing (MEC) specialist with Verizon Business, provides a concise overview of what’s at stake.
Mainstream 5G adoption is still down the road. How long do agencies have before they need to seriously address 5G security?
As a security professional, I advise addressing cybersecurity needs today, regardless of where you are with 5G adoption. Adoption will be a moving target. It’s unlikely we will ever have total 5G. While 4G was designed to replace 3G, 5G is not designed to replace 4G. That’s because 4G LTE is totally appropriate for many applications.
Most communications service providers are moving to a standalone network, which is necessary to enable all the features of 5G, including several of the security features discussed here, in 2023. Full adoption, I would say, is no later than 2024. But there will be early adopters, while some applications, agencies and enterprises will run behind that date.
It’s better to look at it as a process and make sure you’re addressing cybersecurity today in a 4G environment so you won’t be unnecessarily exposed when you move to 5G.
Verizon serves as a trusted partner to the public sector, from rural communities to the largest State and Federal agencies. We enable better government through our best-in-class networks, innovative solutions, exceptional customer experience, and decades of success helping get mission-critical projects done right. For more information, visit
https://www.verizon.com/business/solutions/public-sector/
Closing the MFA Gap to Stop Modern Cyber Threats

Hardware security keys help agencies achieve 100% multifactor authentication coverage and meet cyber insurance requirements.
Cyber threats to state and local agencies have increased signifi cantly in recent years. In 2021 alone, nearly 70% of government organizations experienced at least one cyber attack.1
State and local agencies have always collected high-value data. They now must also contend with a vastly expanded attack surface, thanks to remote and hybrid work and broader digital services. Together, these challenges heighten the need for governments to adopt a more holistic approach to cybersecurity.
One of the best ways agencies can strengthen security is to implement phishing-resistant multifactor authentication (MFA). Insisting on 100% MFA coverage fortifi es long-term security and helps agencies move toward emerging security models like Zero Trust, especially as they embrace distributed work, implement cloud-based collaboration tools and forge partnerships with third-party service providers to accelerate digital transformation.
WHY 100% MFA COVERAGE NOW?
In the current threat environment, relying on usernames and passwords is no longer enough to secure mission-critical systems and applications. Aside from this, several other factors are driving the need for 100% MFA coverage within the public sector.
First, threat actors have grown far more sophisticated. Without 100% MFA coverage, agencies face greater security risks, such as phishing and spear phishing attacks. Indeed, 81% of data breaches are related to stolen credentials such as usernames and passwords, according to the 2022 Verizon Data Breach Investigations Report.² 100% MFA — which typically involves token-based authentication that uses encrypted security keys for identity verifi cation — adds more complexity to shrink this threat vector.
The growing cost of cyber insurance is also a driving factor, says Michael Santini, enterprise account executive for Yubico, a leading provider of hardware-based authentication solutions for the public sector.
“Whether it’s applying for cyber insurance, renewing cyber insurance or getting a better rate on cyber insurance, MFA is now becoming what insurers will use to help you get cheaper cyber insurance,” he says.
The federal government has also become more focused on cybersecurity as an integral part of the country’s national security. The January 2022 Offi ce of Budget and Management memo M-22-09, calling for Zero Trust and phishing-resistant MFA across the federal government, is trickling down to state and local governments and contributing to new discussions about how they approach authentication and identity access management.³
BARRIERS TO 100% MFA
Despite these headwinds, state and local agencies still face challenges in adopting 100% MFA coverage. Many state and local governments rely on legacy forms of MFA such as mobile authenticators, including SMS (text messaging), one-time passwords (OTP) and push notifi cation apps. These forms of MFA are not phishing-resistant and are susceptible to modern cyber attacks such as phishing, account takeovers, SIM swaps and man-in-the-middle attacks.
Mobile authenticators also create gaps in MFA strategy when users can’t, don’t or won’t use mobile-based authentication for MFA. These could include reasons such as union restrictions, users who don’t wish to use personal cell phones for work purposes or users who live in areas with poor cell coverage. In these cases, the typical approach is to fall back on username and password-based authentication, but passwords are easily hacked, and these MFA gaps create opportunities for modern criminals to gain a foothold into the organization.
Cost management and user pushback are two additional barriers. Legacy infrastructure is another issue, according to Santini.
“Organizaitons need to modernize some infrastructure to allow a platform to do MFA,” he says. “So part of the challenge is that you can’t do an MFA that’s not built in because the system is so old.”
IT staffi ng shortages compound these challenges. Even as agencies attempt to modernize their security infrastructure, they may not have enough staffi ng resources to oversee the maintenance process after they adopt an MFA solution.
But even with these barriers, it’s crucial for agencies to advance their MFA strategy and overall cyber maturity. The risk of compromising constituent data and undermining public trust in government systems is too great to do otherwise.
BEST PRACTICES FOR IMPLEMENTING 100% MFA COVERAGE
Plan with the end in mind
Agencies should determine how they want to apply 100% MFA within their organization and work backward from there to implement the best solution that supports their MFA strategy. Agencies should adopt a user-friendly solution to minimize employee pushback. Hardware-based tokens are generally less cumbersome for users than mobile authenticators.
Consider hardware-based MFA
Rather than relying on one-time passcodes sent via text or email, agencies should consider a hardware-based MFA solution. A hardware-based security key is a physical, one-touch authentication device users can place into their computers or tap against their mobile phones to access their organization’s systems and applications.
One of the capabilities that sets hardware-based MFA apart from other solutions is the support it off ers for diff erent authentication methods and the latest protocols. The most eff ective hardware-based MFA solution should be compatible with the leading identity and access management systems, such as Microsoft, Okta, Duo and Ping. It should also address mobile restrictions when employees either don’t want to or can’t use their personal devices, such as in rural areas with poor connectivity.
Collaborate with a strategic technology partner
As agencies rethink their MFA strategy, they should consider working with a technology provider that can guide their implementation.
Agencies should look for a partner with deep expertise in the public sector, but also one that provides comprehensive support and services to complement their technology off erings.
Leverage federal funding
MFA is one part of the State and Local Cyber Security Grant Program,4 which was created by the Infrastructure Investment and Jobs Act (IIJA), passed by Congress in 2021. The federal government is awarding $1 billion in these cyber grants over four years,⁵ creating a prime opportunity for state and local governments to use federal dollars to strengthen their security environment long term. Agencies could use these funds to pay for subscription-based services that accelerate MFA adoption, which would allow them to amortize this cost and convert what traditionally would be a capital-expenditures budget item into an operating expenditure.
CONFRONTING TODAY’S CYBER THREATS WITH 100% MFA
Most data breaches are credential-related, so agencies must have a more formidable plan for strengthening the authentication process and keeping bad actors out of their systems. Advancing their MFA strategy and anchoring it around phishing-resistant MFA and 100% MFA coverage can help agencies enhance their security posture. With this approach, agencies will also be better positioned to prevent account takeovers, phishing attacks and other security threats that disrupt their operations, weaken their cyber resilience and undermine constituents’ confi dence that governments are doing everything within their power to safeguard their data.
This piece was written and produced by the Center for Digital Government Content Studio, with information and input from Yubico.
Endnotes 1. https://www.govtech.com/security/most-governments-were-hacked-in-the-past-yearreports-reveal 2. https://www.verizon.com/business/resources/reports/dbir/ 3. https://www.whitehouse.gov/wp-content/uploads/2022/01/M-22-09.pdf 4. https://www.cisa.gov/cybergrants 5. https://www.cisa.gov/cybergrants#:~:text=Through%20the%20Infrastructure%20
Investment%20and,be%20awarded%20over%20four%20years.
Produced by:
The Center for Digital Government, a division of e.Republic, is a national research and advisory institute on information technology policies and best practices in state and local government. Through its diverse and dynamic programs and services, the Center provides public and private sector leaders with decision support, knowledge and opportunities to help them eff ectively incorporate new technologies in the 21st century. www.centerdigitalgov.com. Sponsored by:
As the inventor of the YubiKey, Yubico makes secure login easy. As a leader in setting global standards for secure access to computers, mobile devices, and more, Yubico is also a creator and core contributor to the FIDO2, WebAuthn, and FIDO Universal 2nd Factor (U2F), and open authentication standards. Yubico is privately held, with a presence around the globe. For more information, please visit www.yubico.com.
96%
Intel has introduced what it says is the fi rst real-time deepfake detector and claims it has a 96 percent accuracy rate. Called FakeCatcher, the product analyzes “blood fl ow” in the pixels to determine whether an image is real or a clever digital reproduction of a person’s likeness. It uses a method called photoplethysmography that measures the amount of light refl ected by blood in living tissue. Signals are collected from 32 locations on a face, then the system maps them as real or fake, returning a result in

milliseconds. SOURCE: VENTUREBEAT
SPACE CASE:
Construction of the world’s largest radio telescope kicked off in Australia in December. The Square Kilometre Array (SKA) Observatory will include 131,072 antennas in Australia’s western region and is projected to map space about 135 times faster than existing telescopes. Another portion of the SKA, built with 197 radio dishes, is already in use at Meerkat National Park in South Africa. The combined array is expected to help study the early universe, dark energy and potentially even extraterrestrial life. Completion is anticipated by 2028.
SOURCE: NEW ATLAS


HOLD STEADY: Robot behaviors just continue to get more human-like. Researchers at the University of Lorraine in France have developed a “Damage Refl ex,” or D-Refl ex, system to help a humanoid robot catch its balance if one of its legs is broken. It’s a neural network based on 882,000 training simulations that taught a TALOS bot to prop itself up on a wall three out of four times it was injured. So far D-Refl ex only works with stationary robots, but researchers eventually want it to work while the robots are in motion and able to grab objects besides walls for support.
SOURCE: ENGADGET
$599
That was the price for a signed copy of Bob Dylan’s latest book The Philosophy of Modern Song when it was released in November. But fans who forked over the money were disappointed to learn that Dylan himself hadn’t signed their books. Instead, he did it with the help of an autopen, a device that isn’t new — the brand Dylan used is at least 60 years old — but which replicates a handwritten signature, saving people like celebrities from spending hours signing their names over and over. Dylan said he used the autopen while experiencing a bout of vertigo and issued a formal apology to fans. Simon & Schuster, the book’s publisher, refunded buyers’ money.
SOURCE: GIZMODO ADBOBESTOCK
Here’s a look at a few recent Questions of the Day from govtech.com. Subscribe to our newsletter to get them daily in your inbox.
Are people still using bad passwords?
Answer: Unfortunately, yes.
ADBOBESTOCK
It seems one of the world’s universal constants is that no matter how adamant the experts are or how many breaches there are, people will still want to use simple, easy passwords. Yes, you will be able to remember “password12345” every time, but so will the cyber criminals.
Cybernews and NordPass both independently released data in November on the world’s most commonly used passwords for 2022. The former got its data from 56 million breached or leaked passwords discovered on darknet and clearnet hacker forums. NordPass’ team scoured the dark web for passwords and came out with 3 terabytes of info to compile its results.
Surprising absolutely no one, “password” and “123456” were in the top five of most commonly used passwords. “Admin,” “guest” and “root” also made it up there. According to Cybernews, 25 percent of all the passwords they looked at were only eight characters long, as compared to the recommended 12 or more; 16 percent were only four characters long.


Can your smartphone detect damage to bridges?
Answer: Yes.
As our infrastructure ages, detecting issues before it comes down on our heads or out from underneath our feet is becoming increasingly important. But the easiest way to do it is with laborintensive and time-consuming manual inspections, for now.
Every day, thousands of people drive over bridges with smartphones in their cars. A team from the Massachusetts Institute of Technology discovered that they can use these smartphones to check the health of the bridges. They do this by analyzing the accelerometer data that all smartphones are constantly collecting. They were able to pick out the bridges’ modal frequencies, which are unique to each bridge.
This is a lot like taking the bridge’s temperature — if there’s any damage, it will show in the modal frequencies, even before it’s visible to the naked eye. The team envisions smartphones in city and commercial vehicles, such as police cars and delivery trucks, being used to collect this data.
Why might someone build a PC in a microwave?
Answer: To save money.
When one man lost his job during the COVID-19 pandemic, he decided to save money by building a PC in his microwave. The Brazilian man’s creation was shared on Twitter by user Jake Lucky (@JakeSucky).
While details are a bit scant on the ground, the whole thing reportedly cost $900. According to Digital Trends, PC Gamer guessed based on looking at the video Lucky shared that the motherboard is most likely an Asus A320M-K. The device is reportedly fully functional, although it probably can’t warm up your leftovers (not because it doesn’t get hot enough, but because there’s no room left inside the microwave).

A Fresh Approach
Now is the time for a new look at cybersecurity in state capitols.
Governors, mayors, county executives and other newly elected or re-elected leaders listen up: It’s time to revisit your cyber policy.
I know, most of you are thinking, “Thanks for the advice, but that won’t be necessary.”
Digging deeper, most politicians and their appointed executives often say something to the eff ect of, “Cybersecurity is already a top concern. We understand that the National Association of State Chief Information Offi cers has made cyber defense the top priority for the past decade-plus, and we’ve seen how ransomware has ravaged the public and private sectors. We’ve been briefed on foreign adversary mischief online, and the cyber attacks just keep coming against our government. But have no fear, we’ve got this. Been there, done that, got the T-shirt.”
But that old mindset will no longer suffi ce.
Why? Because the messages, actions and urgency set from the top of the government impact your organization’s risk profi le, and the due diligence required to ensure critical infrastructure resiliency cannot be left to lower-level appointees.
Also, last year’s cyber program will not be enough to address tomorrow’s cyber challenges. Even if your government has been successful at addressing cyber attacks and ransomware threats so far, our rapidly expanding digital world is bringing new, even greater stakes and greater tests in the future. Sadly, the bad actors are improving as fast or faster than the good guys.
Neglecting cybersecurity can: 1 / Undermine the reputation of both the government and elected offi cials; 2 / Force unacceptable expenditures associated with the cost of cleaning up after security breaches; 3 / Cripple governments’ abilities to respond to a wide variety of homeland security emergency situations or recover from natural or manmade threats; 4 / Disable elected offi cials’ ability to govern.
So what steps can you take?
First, I’ve never seen any public- or private-sector executive leader say, “Cybersecurity is not important or a low priority.” Such statements would harm credibility. Just as in physical health, everyone agrees that good cyber hygiene makes sense and actions like patching servers, solid identity management and having an incident response plan are important.
However, actions often don’t match the words. What is more common is for government organizations to treat cybersecurity as an annual event that comes and goes, or a check-the-box requirement needed for compliance or to address audit fi ndings.
Elected and appointed leaders need to make cybersecurity a true priority and a core part of government culture. Talk about cyber protections often — and walk the talk. Surround yourself with experts who can advise your organization on best practices from similar governments around the country.
Second, many government leaders believe that cybersecurity
is just another subcategory under technology. One reason is that from a governance perspective, the state’s chief information security offi cer generally reports to the CIO, who runs technology. But cybersecurity is a business risk issue that will either strengthen or harm your entire government strategy. Security experts agree that what is needed is a robust system of governance and accountability that starts at the top and is similar to the way that risk is managed in other parts of government. Government leaders have come to expect that dashboards and action plans be put in place to track revenues, spending, project status on key government initiatives and much more — and cybersecurity metrics should be a part of that executive-level dashboard. Third, the NIST Cybersecurity Framew ork is a great place to gain direction and guidance, and it covers how organizations of any size can improve cybersecurity risk management by identifying, protecting, detecting, responding to and recovering from inevitable cyber attacks. But regardless of the framework used, your employees, clients, constituents, partners and others you interact with need to see leadership on cybersecurity from the top. The exciting mandate that comes Daniel J. Lohrmann is an internationally recognized with a new or re-elected administration is the perfect time to realign — or cybersecurity leader, technologist and author. From 2002 to even start over — on cybersecurity. As Theodore Roosevelt once said, “In 2014, Lohrmann led Michigan’s awardwinning technology any moment of decision, the best thing you can do is the right thing, the next and cybersecurity programs, serving as CSO, CTO and CISO. best thing is the wrong thing and the worst thing you can do is nothing.”


