VIDEO SURVEILLANCE
A look into the products, technologies and solutions shaping the market

Sponsored by:

A look into the products, technologies and solutions shaping the market

Sponsored by:

The promise of generative artificial intelligence is convenience for security systems operators, but also next-level performance
By Neil Sutton
Artificial Intelligence (AI) has been one of the dominant driving forces behind technology acceleration in physical security for several years now, as providers highlight advances like more efficient video search tools and expedient data processing on the back end.
A subset of AI, still in its infancy in the security world, is generative AI. One of the major applications of Gen AI is an interface that would allow the user to interact much more easily and naturally with their security technology — in theory eliminating the need to navigate
through clunky menus or spend precious time browsing lengthy reports for specific information.
The promise of Gen AI is a natural language, intuitive interface that delivers exactly what the customer wants almost immediately, and even makes useful suggestions they might not have even considered.
Alert Enterprise, a developer of identity and access management solutions, was early to the market on this.
The company began testing a Gen AI interface for its security systems management tool several years ago in the form of a chatbot pow-

ered by OpenAI’s ChatGPT.
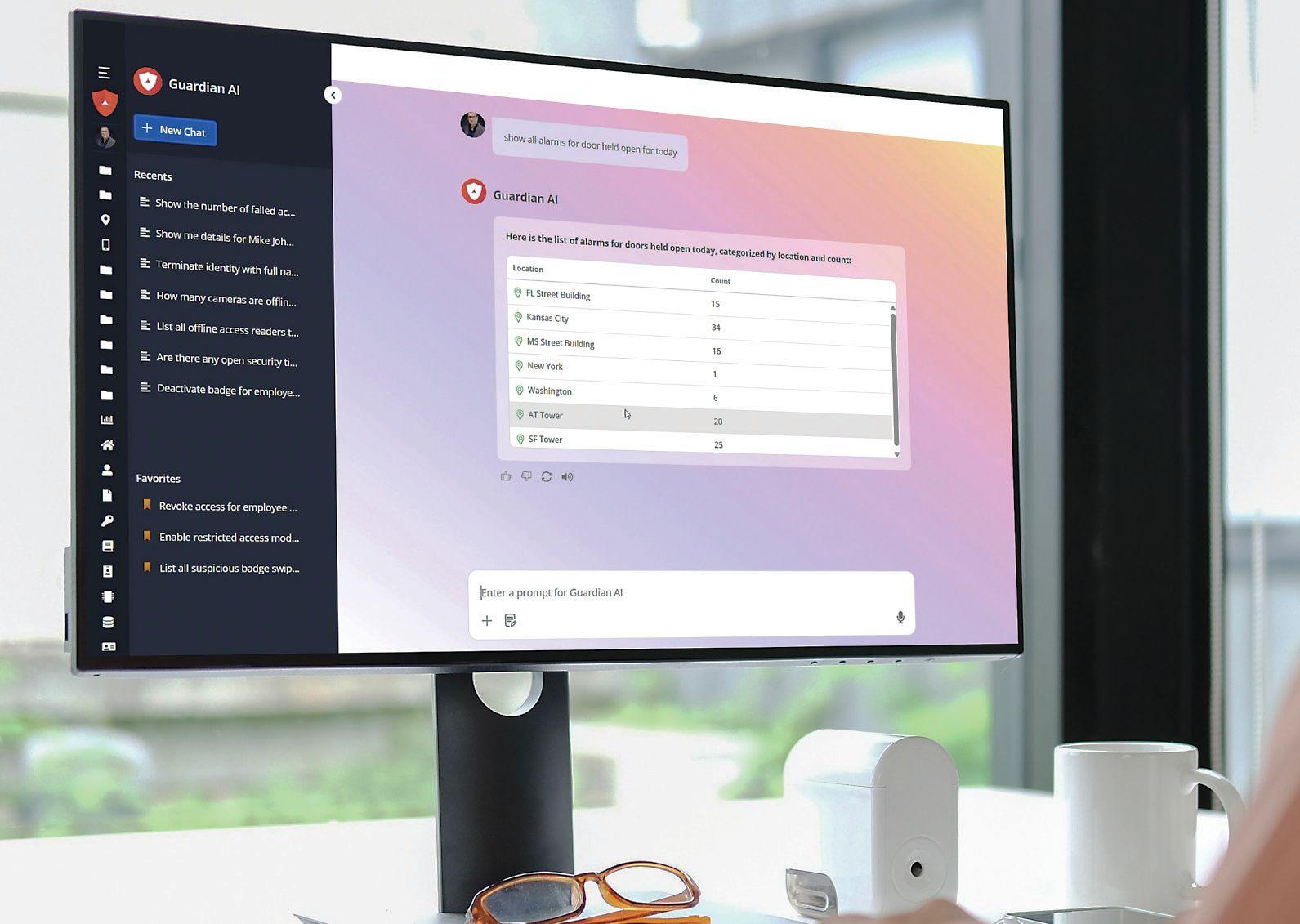
The Guardian AI Chatbot debuted in early 2023 at several security trade shows, including ISC West. The interface promised to “redefine the security operator’s experience, increasing their productivity by over 100 times with instant and actionable insights,” according to a press release issued by the company.
Since then, Alert Enterprise’s Gen AI interfaces have been refined and updated based on the continued evolution of the technology and the large language models (LLMs) that enable natural language chatbot functionality.
Gen AI “provides this amazing experience for rapid response to any question using large language models. They are able to find information for you in a way that is more useful than what we were used to from an internet search,” explains Willem Ryan, senior vicepresident of marketing and communications at Alert Enterprise.
“We applied it specifically to physical security. We used the large language models from OpenAI to create a physical security model that answers specific questions about identity and access for an organization.”
Examples of this include, asking the inter-

face how many employees or visitors are currently in the building, or which doors were held open and when. That data could be accessed previously, but required multiple clicks or menus in order to reach it. “Now you can just type in a question and get that information sent to you right away,” says Ryan.
Generative AI (i.e. the ability to interact with an AI in real time and through natural language) has driven much of the public interest in the technology, and adoption has grown rapidly. Research firm Parks Associates recently released new data indicating that in Q4 2024, 47 per cent of U.S. households with internet access said that they had used a Gen AI tool, up from 40 per cent in Q1 of the same year.
Another Parks Associates study based on data collected from executives at home automation companies indicates the No. 1 use of customer-facing AI is for chatbots that provide technical support.
Jennifer Kent, vice-president, research, Parks Associates says that most companies will rigorously test AI interfaces internally before allowing them to have any direct or primary
contact with customers. “That’s a pretty common story that we’re hearing,” she says. Common uses of AI inside corporations include research, software development, coding and marketing development, adds Kent.
The security industry in particular is using Gen AI to provide natural language descriptions of surveillance video footage, or using it to generate captions — something that both end users and police who must assess the nature of emergencies quickly would find useful.
While interest is high, and companies are rushing to get useful applications of Gen AI into the market, we are still in a “low knowledge, high skepticism moment,” as far as consumers are concerned, notes Kent. “They don’t know exactly what this is and can they trust it?”
Parks data reports that 69 per cent of U.S. internet households said they are concerned about society’s ability to control AI and use it responsibly. They are also concerned about data privacy implications.
In order to build trust with the user, says Kent, any use of Gen AI must serve the customer’s best interests first. “For companies who get it right versus companies who don’t get it right, they’ve got to make the customer feel like
it’s working for them.”
Addressing data integrity concerns and taking next steps
Ryan says Alert Enterprise users have also voiced concerns about how an AI interface might potentially compromise data.
“When we were talking to customers, a couple of things became very clear,” he says. Customers sought assurances that there are guardrails in place to ensure that the AI does not exceed pre-defined operating parameters. In response, Alert Enterprise created a patented process that strips customer identifiers from the LLM, thus keeping sensitive information away from the AI interface.
As Gen AI began to grow in popularity, it also became clear that customers were standardizing on one of several enterprise AI options.
Alert Enterprise used an OpenAI interface
“Gen AI provides this amazing experience for rapid response to any question.”
—Willem Ryan,Alert Enterprise
when it first launched its chatbot two years ago, but has since created options to use LLMs from other major suppliers like IBM and Microsoft. Alert Enterprise also recently announced its Guardian AI Security Agent is natively available on ServiceNow, a cloud-based business automation platform.
The next major step forward for Alert Enterprise is “agentic AI” — a logical extension to the chatbot, Q&A format.
Rather than simply ask the AI a question and receive a response, the AI can be employed to perform certain tasks, such as extend or cancel employee access privileges. “It truly becomes an autonomous agent that gets rid of
some of the repetitive work that humans had to do,” explains Ryan.
As the technology continues to improve and get smarter, Ryan says that more and more customers are coming to the company with a plan on how they want to use it in their own environments. Likewise, Ryan says integrators also want to talk about how they can leverage Gen AI tools to serve their clients and meet their growing needs.
However, he says, some things don’t change: customers still want the ability to audit their software, generate and store reports, and maintain full governance over any AI agents operating on their networks.
According to James Miller, cybersecurity product lead at Bell, the positive applications of generative AI are more immediately obvious for cybersecurity than for physical security.
For example, Gen AI can find malicious code on a network with much greater expediency and accuracy than a human actor operating independently. “I think that physical security has needed to find tangible ways to say how Gen AI is helping as opposed to cybersecurity,” he says. “It’s all speed, really. It’s how fast Gen AI can find a threat.”
Bell recently conducted a study in partnership with Maru Research, collecting survey responses from 600 business leaders and IT/security professionals across Canada. Based on that data, Bell reports that “organizations are embedding generative AI in several core processes, from automating routine tasks to enhancing customer service interactions. IT, finance and security departments are seeing the biggest gains.”
The ability for Gen AI to serve as a helpdesk or troubleshooting function is now an established and proven technology. Miller says a Gen AI interface recently helped him repair an endpoint that was corrupted due to software that wasn’t installed correctly. “The AI got me to the point where it helped me check everything. I think I only had a human for the final few (steps) and I was back up and running.”
However, Miller advises that AI not be the first point of customer contact “where the user could give you critical data. You don’t want AI to collect critical data from a critical server. I would advise, as a cybersecurity professional, to always speak with a person when giving away any information that would help a threat actor get into your network.”
Miller says organizations would benefit from

setting clear policies that govern how AI is used in the workplace. As people become more familiar with using public-facing AI tools in their personal lives, it is imperative that they understand that unsecured chatbots are not appropriate for business use.
He notes that “shadow AI” is similar to the “shadow IT” issue that arose about a decade ago as people began bringing personal technology devices, like tablets and smartphones, into the workplace. Organizations adjusted to this new reality and communicated policies to help maintain data integrity
and keep the business (and their employees) safe.
Bell’s report highlights some of the potential threats and concerns that come with mass adoption of AI in the enterprise, but it is generally positive about its future. For example, almost half of the organizations that participated in the study indicated “we are just at the beginning of AI model progress and much more progress will take place over the next five years… The consensus is clear: generative AI is just getting started and its role in reshaping Canadian industries will continue to expand.”






The security industry is undergoing a pivotal transformation, and at its core stands ECAM—a strategic fusion of ECAMSECURE and Stealth Monitoring under the GardaWorld umbrella. ECAM isn’t just a brand—it’s a force multiplier in live video surveillance, driven by AI, backed by human intelligence, and built on the mission of “Every Camera, Always Monitored.” With a focus on proactive detection, scalable deployment, and high-performance monitoring, ECAM is reshaping how businesses and communities approach protection.
What makes ECAM distinct isn’t just its cutting-edge technology— it’s the seamless integration of advanced AI and real-time human oversight. This hybrid model allows ECAM to recognize, assess, and respond to threats faster and more effectively than traditional systems. While AI handles immediate detection, trained professionals validate and act on incidents, ensuring precision and accountability.
ECAM’s in-house R&D has delivered proprietary tools that improve speed, accuracy, and reliability, setting new standards in the field of intelligent surveillance. Whether it’s securing a remote job site or a bustling urban facility, ECAM tailors each deployment to the specific needs of the environment—delivering custom-fit security with measurable results.
ECAM’s Mobile Surveillance Units (MSUs) represent the future of flexible security coverage. Engineered for mobility, each MSU can be deployed in hours, not days, offering an ideal solution for temporary or high-risk locations. These rugged units come fully equipped with solar power, independent network connectivity, advanced AI-driven cameras, and optional lighting and audio features—making them selfsufficient and always on guard.
MSUs are especially valuable for construction zones, logistics yards, pop-up events, and remote assets. With no reliance on on-site infrastructure or internet access, they extend ECAM’s 24/7 monitoring capabilities to even the most inaccessible locations. Real-time alerts, video capture, and remote speaker systems allow ECAM operators to intervene immediately, often stopping threats before they escalate.
ECAM’s monitoring services are the foundation of its promise to
deliver uninterrupted surveillance. Staffed by seasoned professionals trained in incident verification, law enforcement coordination, and rapid response protocols, ECAM’s monitoring centers ensure no alert goes unanswered.
Operators use advanced software to assess potential threats, distinguish false alarms from genuine risks, and call to dispatch law enforcement with clear, actionable evidence. Remote diagnostics and system health checks allow ECAM teams to proactively maintain devices and troubleshoot issues often before clients are even aware there’s a problem—ensuring optimal uptime and peace of mind.
One of ECAM’s standout innovations is Integra, a proprietary video upscaling solution that enables low-resolution footage to be enhanced in the cloud. This means surveillance data can be transmitted more efficiently while retaining sharpness and detail for AI analysis. The benefits are tangible: up to 40% higher AI accuracy and a 50% boost in identification range, all while minimizing network strain.
Integra allows organizations to cover more ground with less bandwidth, making high-quality monitoring accessible and scalable—without compromising detection capability or image clarity.
The ECAM Promise: Smarter, Safer, Scalable
From mobile units to hybrid solutions, ECAM offers end-to-end security tailored for today’s dynamic environments. Its benefits are clear:
• Proactive protection through AI-human collaboration
• Flexible deployment for single or multi-site operations
• Secure, cloud-based monitoring and video retrieval
• Turnkey solutions with fast ROI and reduced security costs
• Backed by the global reach and experience of GardaWorld
ECAM is more than a security solution—it’s a new approach to safeguarding assets, people, and peace of mind. By blending technology, mobility, and human oversight, ECAM doesn’t just watch—it protects, prevents, and performs.
For companies seeking intelligent, responsive, and adaptable video surveillance, ECAM is the clear choice.

Clean Energy
• Methanol fuel cell and solar powered
• 94% reduction in CO2 vs Diesel Generator
AI-powered Camera Analytics
• Remote monitoring, event based surveillance
Designed to operate in Canadian climate Energy on demand vs. Overproduction
• Lower operating costs and less fuel consumption
Proudly Canadian Made

Highlights of the Wisenet WAVE VMS 6.0 include a redesigned user management interface, enhanced LDAP integration, upgraded calendars, camera linking via hotspot/ teleport, the ability to add temporary users, and cloudbased email. Similar to previous WAVE VMS releases, all features are supported across the mobile, desktop and server versions of the platform using any operating system, as well as WAVE Sync, Hanwha Vision’s cloud-based service. www.hanwhavisionamerica.com
SWEAR
SWEAR announced the release of the enterprise version of its video content authentication tool, SWEAR Security. The tool integrates with video management systems to safeguard video data at the point of capture. SWEAR Security integrates directly with security and video recording platforms, capturing the unique digital layout of each frame, sound byte and pixel in real time. This mapped data is securely stored on a blockchain ledger, creating an unchangeable record. www.swear.com

i-PRO announced a new line of high zoom bullet cameras. Equipped with zoom and IR LED technologies, the new cameras offer precision for long-distance monitoring across various environments. The new lineup includes 10x and 30x zoom options, complemented by long-range (up to 250m) infrared LED capabilities for optimal performance in low-light or nighttime conditions. Available in 2MP, 5MP and 4K resolutions, the range offers 20 new models across the X- and S-series. Four LPRoptimized models are available for capturing plates at high speeds. www.i-pro.com
Opticom announced the release of its new CC04 industrial camera with M12 connection. The new option, CC04-IP3MV-3M12, is now available through Opticom Tech and its distributors. The new camera offers all the features of the CC04 — 3MP resolution, vibration resistance, ONVIF compatibility, IR infrared, IP67 waterproof and dustproof, and more, and the RJ45 connector is still available. This camera is suited for harsh industrial environments that experience vibration, debris and other hazards. www.opticomtech.com


The new First Alert CX4 Camera Series is compatible with both the Resideo ProSeries Security System and Resideo’s First Alert VISTA Hybrid Security System.. The camera series offers three different models: CX4B Bullet Camera for perimeter monitoring, warehouses or retail applications; CX4T Turret Camera for lobbies, stairwells and retail areas; and CX4D Dome Camera for entrances, exits, offices or food service applications. www.resideo.com

Raptor has enhanced its range of SWIR cameras with the launch of the Owl 2560 Vis-SWIR camera. Using a back-illuminated InGaAs sensor (1¼”, 2560 × 2048 pixels with 3.45μm × 3.45μm pixel pitch), the QUAD SXGA camera offers uniform spectral sensitivity from 400-1700nm running at up to 60fps. It interfaces through a single wire CoaXpress interface meaning less connectors for slip-ring / systems integration. The camera is temperature stabilized and is designed to MilSpec standards. www.raptorphotonics.com
AMAG Technology announced Symmetry CompleteView Video Management 7.5. This version introduces new enterprise capabilities including the integration of Iron Yun’s Vaidio AI Video Analytics which provides a comprehensive suite of advanced analytics for people, vehicles, facial recognition and objects, compatible with any camera or video source. This enhanced solution supports both real-time monitoring and forensic investigations. Symmetry CompleteView VMS 7.5 also introduces federation, storage encryption and export encryption. www.amag.com
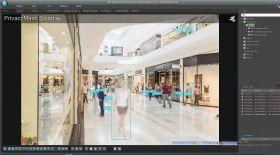
IDIS Smart Privacy Masks are a patented, real-time privacy masking solution that protects individuals’ identities while enabling reliable and responsive real-time video surveillance operations, according to IDIS. Using an in-house developed and trained IDIS Deep Learning Engine, it adjusts mosaic strength to enable video streams to deliver clarity and visibility while protecting privacy. IDIS Smart Privacy Masks combine the advantages of object detection and heatmaps with deep learning and IDIS Solutions Suite VMS processing to increase accuracy. www.idisglobal.com

Ajax Systems
The Ajax IndoorCam is designed for households and small to medium businesses. Operating over Wi-Fi it features a fallback communication channel via the Jeweller radio protocol, built-in AI, and encrypted data transmission. Equipped with a 4 MP camera, HDR, and IR illumination of up to 8 m, the device offers image quality both day and night. The PIR sensor detects movement up to 4 m, while built-in AI recognizes people, pets or vehicles.
ajax.systems

Bosch Building Technologies
The 3100i series of entry-level fixed dome and bullet form factors feature edge-based, application-specific AI, allowing for real-time analysis and immediate response to potential security threats. The range includes the Flexidome micro 3100i, Flexidome 3100i IR, and Dinion 3100i IR cameras in indoor and environmental (outdoor) models from 2 or 5MP, IR, and non-IR models with up to 30 fps and a High Dynamic Range of 120 dB.
www.boschsecurity.com

VIVOTEK launched two 5MP Outdoor Turret Dome AI cameras. Featuring WDR Pro and AI-powered Smart Motion Detection and Smart VCA, the IT9383-HV and IT9383-HVW offer image performance day and night. The cameras also offer built-in IRs and Warm Light (up to 30M), cyber protection via Trend Micro IoT Security, and VIVOTEK’s Deep Search Support. VIVOTEK’s C-series AI camera offers image performance with its advanced Sony sensor featuring STARVIS 2 technology. www.vivotek.com
Rhombus Relay is a new suite of solutions that enable organizations to transform existing camera infrastructure into intelligent, cloudconnected devices. Rhombus Relay establishes a bridge between legacy systems and modern cloud-based physical security. Relay Core N100 is a plug-and-play, on-premise device supporting up to 10 third-party cameras with no added licensing cost for video streaming.

www.rhombus.com
The V300 Ultimate is a rugged cellular-connected security camera that provides on-demand live video streaming for immediate viewing, motion-activated video recording with instant notifications and cloud management and storage all without requiring any wires or Wi-Fi. VOSKER’s remote camera solution can operate in locations without Wi-Fi or electricity, as it only needs a 4G LTE cellular network for connectivity. The combination of the camera and the included solar power bank delivers a minimum of six months of autonomy.

March Networks
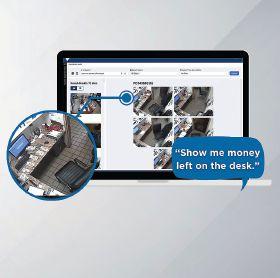
March Networks unveiled new advancements to its AI Smart Search solution. AI Smart Search leverages natural language processing and advanced LLM algorithms to identify specific events, people or objects from thousands of cameras across all locations. Using generative AI, video images are taken at regular intervals and transformed into a searchable database.
www.marchnetworks.com

Genetec
www.vosker.com
Robotic Assistance Devices
RADCam, an AI-powered “Talking Security Camera,” offers all the features of traditional residential security cameras (monitoring, detecting, and recording activity) while adding layers of security and concierge services. With advanced analytics, RADCam captures data through its camera and microphone, allowing the system to analyze and respond to scenarios in near real-time. www.radsecurity.com

Cloudlink 210 is a cloud-managed appliance that supports multiple security workloads, including video management, access control, and intrusion detection. Designed for hybrid applications in Security Center SaaS, Cloudlink 210 serves as a cybersecure bridge between on-premises infrastructure and cloud-based systems. Cloudlink 210 is based on an open architecture, is designed to adapt to the needs of growing organizations and can scale to accommodate additional workloads and devices. A compact edge device, it can be deployed and installed in many types of locations. www.genetec.com