




Ukraine’s Ajax Systems ready for Canada
The security systems maker is expanding into North American markets p. 6
Making the most of visitor management
How automation can reduce human error and provide an extra margin of safety p. 22
Specialized applications for video analytics











By Kai Moncino


armed with equal parts physical and networking knowledge may be a rare breed today, but training and college courses could help to fill that gap
By Madalene Arias



• Ukraine’s Ajax Systems expands into Canada and the U.S.
• March Networks exploring building automation focus
• Wesco-Anixter ramps up locking solutions business in Canada
• CANASA kicks off Security Canada 2022 in Quebec
• Ron Jagmohan receives Honorary Member Award from CANASA
does your video live?




ABy Neil Sutton
well-rounded workforce is one that supports groups of all ages with the understanding that some will naturally retire and new folks will take their place as part of a continuum of steady employment.
Of course, it’s rarely that simple and many industries are facing the well-documented challenges of an aging population, skills shortages and in some cases difficulty attracting new, young talent.
Our cover story (see p.16) takes a closer look at some of these phenomena in the security industry, including the provision of college-based education to address skills training.
Aside from the persistent issue of bringing new people into the profession as the older generations plan their exit, the skills required to do the job have changed. Convergence has brought more and more networking-based infrastructure into what was once simply known as physical security (a description that may be losing its currency).
The hot new term in security used to be IP-based technology, and while it still may be hot, it would be charitable at this point to call it new. Increasingly, my discussions with manufacturers, distributors and installers inevitably circle back to the roles of cloud, building automation and data management.
So… what we need is someone (which is to say, many people) who understands and is comfortable with security hardware, the network that gives it life, and the software that supplies crucial functionality. We also need
someone who is well versed in cybersecurity. That’s a tall order, so it’s no wonder that the security industry may struggle in the short term. In a recent SP&T News reader poll, 62.5 per cent of respondents identified recruitment and retention as one of the biggest issues we are currently facing.
As the wise Stu Armour, operations manager at Affordable Security Systems, explains in the article, “Within the next 10 years, if you have any type of technical skills, you’re going to be worth your weight in gold.”
Initiatives to encourage more people to join the security industry, such as those championed by CANASA, are going to be very important in terms of its long-term health. But while there are definitely challenges ahead, there is a silver lining.
Security is moving forward, and quickly. This is an industry overflowing with good ideas and innovation. The issue before us is certainly one of finding skilled individuals, but it’s also one of communicating the industry’s vitality.
The more people who know about the opportunities available, the more likely we are to draw eager new recruits. A skills shortage isn’t only about the provision of up-to-date training and education, it’s also about articulating the value of an industry.

@SecurityEd
READER SERVICE
Print and digital subscription inquires or changes, please contact Barb Adelt, Audience Development Manager Tel: (416) 510-5184 Fax: (416) 510-6875
Email: badelt@annexbusinessmedia.com
Mail: 111 Gordon Baker Rd., Suite 400, Toronto, ON M2H 3R1
Your Partner in Securing Canada Security Products & Technology News is published 6 times in 2022 by Annex Business Media. Its primary purpose is to serve as an information resource to installers, resellers and integrators working within the security and/or related industries. Editorial information is reported in a concise, accurate and unbiased manner on security products, systems and services, as well as on product areas related to the security industry.
Editor, Neil Sutton 416-510-6788 nsutton@annexbusinessmedia.com
Associate Editor, Madalene Arias 416-510-5228 marias@annexbusinessmedia.com
Group Publisher, Paul Grossinger 416-510-5240 pgrossinger@annexbusinessmedia.com
Associate Publisher, Jason Hill 416-510-5117 jhill@annexbusinessmedia.com
Media Designer, Graham Jeffrey gjeffrey@annexbusinessmedia.com
Account Coordinator, Kim Rossiter 416-510-6794 krossiter@annexbusinessmedia.com
COO, Scott Jamieson sjamieson@annexbusinessmedia.com
EDITORIAL ADVISORY BOARD Victor Harding, Harding Security Services Carl Jorgensen, Titan Products Group Antoinette Modica, Met-Scan Canada Anna De Jager, TAG Dispatch Roger Miller, Northeastern
F:
PUBLICATION MAIL AGREEMENT #40065710 Printed in Canada ISSN 1482-3217



department in any of the four ways listed above.
No part of the editorial content of this publication may be reprinted without the publisher’s written permission. ©2022 Annex Publishing & Printing Inc. All rights reserved.
Annex Publishing & Printing Inc. disclaims any warranty as to the accuracy, completeness or currency of the contents of this publication and disclaims all liability in respect of the results of any action taken or not taken in reliance upon information in this publication.






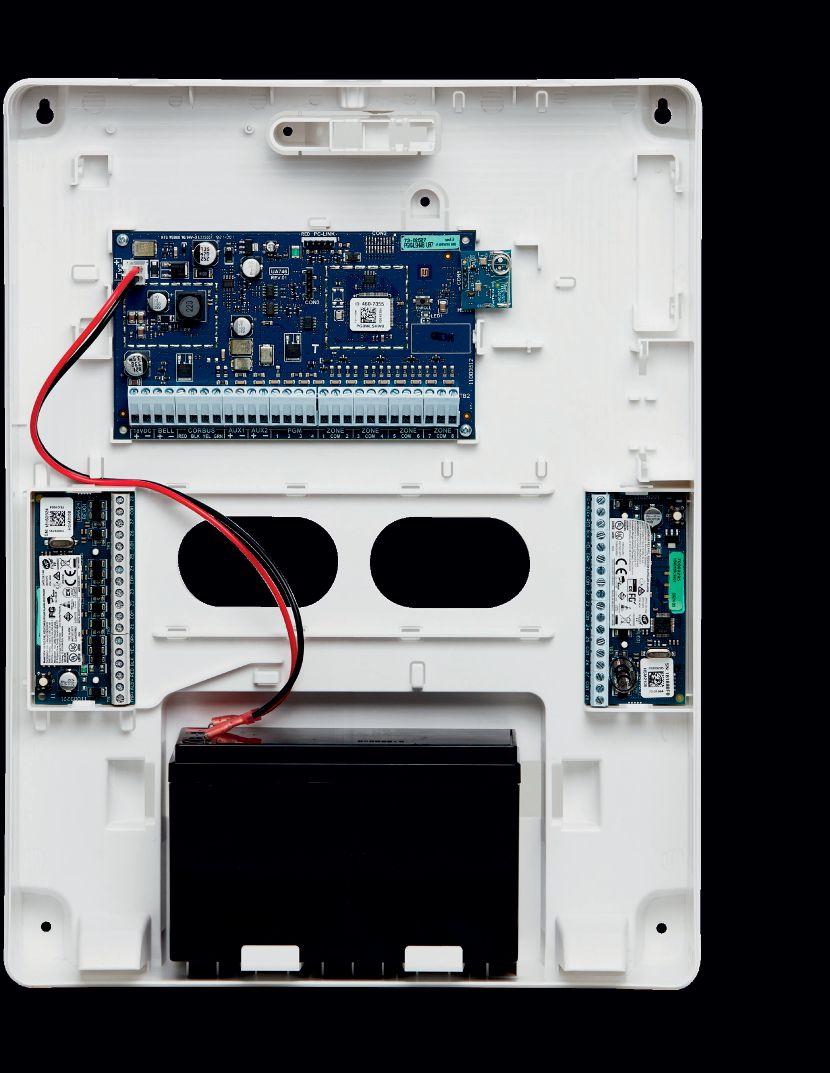
• Use IQ Panel 4 as a Hybrid panel for new installs or easy takeovers
• PGM outputs, up to 80 hardwired security zones, life safety devices & external sirens
• Choose from large or small cabinet
• PowerG wireless for ultra long range, industry best encryption & portfolio
Get the best of both worlds with wireless PowerG and hardwired options. Pairing the IQ Panel and the Wired to Wireless module gives you the strength of using hardwired zones, programmable outputs and keypads with the flexibility of PowerG wireless.
Ajax Systems, a Ukrainian maker of security systems, is now marketing and selling its products in North America.
Established in 2011, Ajax products are available in more than 130 countries and the company says its global user base is in excess of one million customers.
So why North America now? According to Ajax, it has received certificates from both the Federal Communications Commission and Industry Canada, allowing it to expand into markets where the 915 MHz frequency band is used. The U.S. and Canada are new target markets for Ajax, as are Australia and Southeast Asia.
“In order to maintain the quality of the Ajax user experience in the new markets, we’ve done a tremendous amount of work — adapted the hardware, reinvented the radio technology, expanded the software capabilities at all levels, tested, certified, prepared the supply chain and production,” said Ajax in a statement provided to SP&T News
Leading the North American expansion for Ajax is Canadian Rob Harman, a veteran with almost two decades of security industry experience.
Harman, the company’s director of sales for

America, joined Ajax in January 2022. Ajax has had a booth presence at major industry shows this year, including ISC West, held in Las Vegas in March and Security Canada East in April in Quebec. The company will also exhibit at the upcoming ESX conference in Texas, as well as the remaining 2022 Security Canada shows.
“We’re looking to disrupt the market and make a big impact,” said Harman, adding that he has had several discussions with security distributors and monitoring companies on both sides of the border.
In April, Ajax announced a partnership with Lanvac Surveillance, which offers wholesale monitoring capabilities across Canada. Lanvac was the first wholesale firm in North America to provide dealers with Ajax functionality.
Ajax’s expansion comes at an especially challenging time for its home country. But, against the backdrop of the Russian invasion of Ukraine, the company says that it remains resilient and is doing everything it can “to ensure that our own and partners’ businesses work as usual.”
Ajax’s server infrastructure is dispersed across Europe, ensuring continuity of service for customers, says the company. Ajax also recently opened a new production facility in Turkey, with expectations that it will produce at least 150,000 devices a month.
Ajax is hiring approximately 400 people to staff that facility and is also expanding its R&D team, both in Ukraine and in Poland. More than 600 Ukrainian Ajax employees and their families have already been relocated for their safety, according to the company.
Earlier this year, Ajax launched an Air Alert app for iOS and Android in cooperation with developer stfalcon and the Ministry of Digital Transformation of Ukraine. Ajax says the app informs users about the beginning and end of civil defence alerts and has been installed more than five million times.
In terms of post-acquisition synergy, it’s early days for March Networks and its new parent company Delta, but Dan Cremins is keen to explore the opportunities ahead.
Cremins, a product leader for the majority of his 12-year career with March Networks, was recently appointed senior director of business integration and optimization. In this new role, he is liaising not only with Delta, but with the other companies in Delta’s building automation division.
In a deal valued at US$114 million, Delta acquired March Networks last December. When the deal was announced, Delta touted Ottawa-based March’s strength in the video surveillance market, as well as its potential to help grow Delta’s smart buildings business. Delta’s building automation portfolio includes surveillance provider Vivotek; Amerlux, a lighting solutions company; Loytec, a building control solutions firm; and Delta Controls, a B.C.-based company which also makes a wide variety of building control systems.

With March Networks now part of that Delta group, Cremins says he has spent some time meeting with those other companies to figure out how they can best complement each other.
— Neil Sutton
On the surface, it might seem that March and Vivotek have the most in common as established players in the surveillance market. And while integration between their products will definitely be fine-tuned, says Cremins, there is also a bigger picture to consider, particularly since building automation systems provide such a rich vein of information.
Two of the largest vertical markets March serves are retail and banking. As such, the company has expertise in tying transactional data from retail POS (point-of-sale) and ATM bank terminals to video. “If we can tie in the data from building automation the same way we do a transaction in Searchlight [March’s data analytics platform], that could give us a real advantage,” explains Cremins.
“From a product direction, our strategy is not changing,” adds Cremins, reaffirming March’s commitment to its existing customer base, “but now we have this other area we can start investigating.”
Moreover, he says, customers like banks and retailers may benefit from a smart building approach to technology implementation, even at the local branch level.
— Neil Sutton
Wesco-Anixter is in the process of significantly ramping up its locking and door hardware solutions across Canada to complement its existing security business.
Gary Mistak, the distributor’s vice-president and general manager, security and communications solutions, said the renewed focus on hardware will help to round out the company’s offering and meet the needs of more of its customers. “We were missing locking solutions and it’s a critical add to our portfolio,” he said.
Wesco-Anixter is taking a two-pronged approach to increasing its hardware presence in Canada, said Mistak, bulking up inventory from popular lock and hardware makers and also hiring more in-house expertise.
Larry Malo, director of business development, Locking Solutions Canada, joined Wesco-Anixter last year, bringing with him decades of experience in the hardware market.
The distributor isn’t starting from scratch in the market but is moving into a much more

The Canadian Security Association (CANASA) hosted its Security Canada East trade show and exhibition on April 20 in Laval, Que.
The event drew more than 700 attendees and 69 exhibiting companies. According to CANASA, exhibit space was sold out and event attendance rebounded to almost pre-pandemic levels.
CANASA’s two remaining 2022 Security Canada events will be held in Richmond, B.C., on June 22 and in Toronto on Oct. 19-20. For additional event details, visit www.securitycanada.com.
active focus on this aspect of the security business, said Malo, adding that he is assembling a team within the division and building up a presence across Canada.
“It’s a critical add to our portfolio.”
— Gary Mistak,Wesco-Anixter
“Right now, it’s all about training, getting our teams up to speed,” said Malo. “If the customer has an inquiry for a mechanical product, then they have a resource to lean on for information.”
Mistak said that Wesco-Anixter is also taking a global approach to this, with plans to increase its hardware business across multiple territories.
Until recently, the U.S. was the only major market where Anixter had a robust portfolio of locking solutions through its Clark brand. The company acquired Clark Security Products, a California-based distributor of
security and locksmith supplies, in 2010.
The company’s Clark heritage is definitely a benefit and will give Canadian operations a head start and game plan to refer to, said Mistak.
Aside from adding some new products to its arsenal, the locking division also helps Wesco-Anixter deliver on its solutions focus, added Mistak. Locks, doors and access control have become increasingly intertwined and integrated in recent years. “More and more, you’re seeing technologies meld. You’re seeing locks becoming IP-enabled,” he said.
“Access control does not work without a latching device,” added Malo. “You need a lock, you need an exit device, you need a door closer. Those are natural things that go handin-hand with our business.”
Likewise, more locksmiths are embracing the electronic side of the business and Mistak believes Wesco-Anixter can be a partner they can look to for support. “It’s about relevance to the market you’re trying to address,” he said.
— Neil Sutton
Ron Jagmohan, a long-standing member and contributor to the Canadian Security Association (CANASA), was recently recognized for his years of service with the organization’s Honorary Member Award.
Jagmohan joined CANASA more than 20 years ago. In that time, he has participated as an instructor for CANASA’s Alarm Technician Course and was also one of the architects of a recent course redesign as education committee chair.
Jagmohan is a security industry veteran with a resume that includes companies like Resideo, Honeywell and Ademco. In addition to his distinguished history with CANASA, Jagmohan has also volunteered with ULC, serving on multiple standards committees. In 2020, Jagmohan was inducted into the SP&T News Hall of Fame.

The Honorary Member Award was pre-
sented to Jagmohan by CANASA executive director Patrick Straw at the Central Ontario Regional Council Breakfast Meeting, held May 12. The meeting was the first Ontario Council event to be held in person since March 2020.




Power for 12 & 24VDC controllers, devices, and peripherals

Tango power supply/chargers provide faster, safer deployments, eliminating high-voltage by utilizing 802.3bt PoE.
• Converts PoE to 12VDC and 24VDC simultaneously
• Power your access system from a single cable, reducing costs and increasing profits
• Built-in LiFePO4 battery charger

Salata Salad Kitchen, a built-to-order salad kitchen has chosen an advanced video analytics solution to gain critical operational insights.
The organization will leverage an analytics solution from Interface Systems, as well as an upgraded security system installed by Interface.
The analytics technology provides real-time insights on customer movement within the restaurants, customer wait times, restaurant layout bottlenecks, employee staffing gaps, compliance issues, and more. Cameras are integrated with Salata’s point-ofsale solution.
Salata has also implemented Interface’s “Restaurant-Technology-ina-Box” to upgrade their network and voice connectivity. “We chose to work with Interface to help us unlock the insights needed to grow our business,” said Pete Kaufmann, senior director of IT, Salata, in a statement.

One hundred thermal cameras will be deployed across Kenya to help end illegal poaching in wildlife parks.
The FLIR Scion OTM Thermal Monocular cameras are being donated to the World Wildlife Fund (WWF) by Teledyne FLIR.
Thermal vision has a number of applications for the Kenya Wildlife Service. FLIR began donating equipment to support this effort six years ago, including fixed-mount security cameras, vehicle-mounted thermal cameras, as well as handheld thermal cameras.
According to FLIR, the Scion OTM devices offer greater clarity and durability than previous models, and also provide a geo-tagging feature. “As they’re looking through the viewfinder, the rangers can get a bearing of their location,” said WWF lead conservation engineer Eric Becker, in a statement.
Once training on the device is completed, the cameras will be distributed across Kenya.



• Allied Universal recently announced the appointment of Darren Pedersen as president, Allied Universal Canada. The company also appointed Dan Marston as regional VP, Technology Services Canada.
Modern and classic combined at Queen’s U. facility

A major hub for campus life, Mitchell Hall at Queen’s University in Kingston, Ont., went through an $85-million restoration in 2018.
New door hardware and fixtures were incorporated into the historic structure, providing modern amenities while still maintaining the building’s architectural legacy.
Allegion, a long-standing Queen’s University supplier, played an integral role in Mitchell Hall’s modernization. Various materials were used for entry points, including Western Red Cedar for a series of unique doors.
A central doorway at the Union Street entrance was outfitted with interior hardware, concealed electric latch retraction vertical cables, and a concealed auto-door operator.
During the pandemic, Queen’s made the newly renovated Mitchell Hall available as a vaccination clinic.

• ACRE founder and CEO Joseph Grillo recently announced his retirement. Don Joos joins the ACRE executive team as the company’s new CEO.
• Detrick Ellis has been named
June 14-17, 2022
ESX
Fort Worth, Tex. www.esxweb.com
June 22, 2022
Security Canada West Richmond, B.C. www.securitycanada.com
June 23, 2022
Smart Buildings: Now & Tomorrow Online
canadianconsultingengineer.com
September 12-14, 2022
GSX Atlanta, Ga. www.gsx.org
September 20, 2022
ADI Expo Vancouver New Westminster, B.C. www.adiglobaldistribution.ca
October 6, 2022
ADI Expo Ottawa Ottawa, Ont. www.adiglobaldistribution.ca
October 18, 2022
Monitoring Station Symposium Toronto, Ont. www.canasa.org
October 18-19, 2022
Securing New Ground New York, N.Y. sng.securityindustry.org
October 19-20, 2022
Security Canada Central Toronto, Ont. www.securitycanada.com



Zenitel’s Northwestern U.S. regional sales leader in its Americas Onshore Business Unit. Ellis will also oversee sales activities for Western Canada.
• Qognify announced the appointment of Brian Laurienzo as its director of transportation, Americas.
• Lumeo, a designer of computer vision solutions, welcomed George Joseph as vicepresident of engineering.







TBy Victor Harding
There’s a basic vocabulary every buyer and seller in an alarm deal should be familiar with
here are several terms that sellers and buyers of businesses should know. Here are some of the most important ones.
EBITDA: Earnings Before Interest, Taxes, Depreciation and Amortization is the key variable that most M&A professionals use to value a company. Essentially, EBITDA takes annual earnings of a company and adjusts for non-cash items like depreciation and amortization and financing issues giving rise to interest. Despite many finance purists warning us that EBITDA is a dangerous variable to use to assess a company, it is still very much used. Anytime you use the multiple of earnings method to value a business the odds are that you will be using EBITDA as a key metric.
“Adjusted” EBITDA: To get at the proper EBITDA number to value a business, EBITDA often has to be “adjusted” for any non-recurring revenue expense items and for non-business expenses put through the company’s income statement. An example of these adjustments might be a one-time large legal bill for a once in a lifetime lawsuit. The other common adjustment to EBITDA is for the owner’s salary, depending on how it compares to what a buyer would have to pay a new manager to do what the owner has been doing. Some owners over-pay themselves while others under-pay, taking money out of the company through dividends.
Seller’s Discretionary Earnings (SDE): This term is sometimes used to value very small companies and differs from EBITDA because the owner’s salary and expenses are added back into earnings with no deduction for what the owner’s replacement might cost. SDE generally produces a higher earnings number but a lower multiple used to value the company.
Expression of Interest (EOI) and Letter of Intent (LOI): Normally an EOI is given by a seller to express their interest in buying a company but the offer will not go into much detail. EOIs normally come earlier in the sales process – say, within the first month— with LOIs coming later on, in the second month.
I would never recommend a seller “go to bat” with a buyer based simply on an EOI. They
“Most buyers will want to see the trailing 12 months of financials before arriving at an offer.”
don’t contain enough important information about the offer.
Asset Purchase Agreement (APA) and Share Purchase Agreement (SPA): An Asset Purchase Agreement is the final, binding document used to close a deal where just the assets are being sold. Today, many alarm account deals are done using an APA. A Share Purchase Agreement is used when the shares of the company are being sold. SPAs are usually considerably longer and more complex than APAs.
Trailing Twelve Months (TTM): You see this term used in regards to the financial statements shown to buyers in a deal. Most buyers will want to see the trailing 12 months of financials before arriving at an offer.
Running an Auction: When selling a business, most M&A types will effectively run an auction amongst the various buyers to try to maximize the price and terms for their client. Running an auction means just what it says — putting the selling package out to several if not many potential buyers and soliciting bids back in from as many as possible. It is critical here that the buyers know that an auction is being held and that they will be bidding against several others.
Non-compete versus a Non-solicit: M&A deals will normally have one or the other of these two clauses in them and sometimes both.
In simple terms, a non-compete is the more all-encompassing clause which a seller should be careful with unless they are truly about to retire for good. A non-compete generally prevents the seller from operating at all in the industry that their business is in for a certain geographical area and for a period of anywhere from two to five years.
For those not ready to retire, they should try to restrict the non-compete in regards to what they can’t do, where and for how long. I always suggest sellers be careful when they sign
a non-compete because they may change their minds. The courts have stepped in the case of some non-competes where the buyer tries to restrict an owner or employee from working after a sale in the only industry that they are trained in.
A non-solicit is usually narrower in scope and directed at preventing the seller from approaching the customers or employees he is currently selling for a period of two to five years. As a broker, I fully support most non-solicits as it seems only fair that a seller cannot go back to customers they have just sold.
Non-circumvention period or a “Broker’s Tail”: Most brokers or M&A professionals will insert a non-circumvention clause into their brokerage agreements with their clients, preventing the client from cancelling the agreement, then selling the company to a buyer that the broker found without paying the broker.
Typically non-circumvention periods are set at two years. This means that the broker will still get paid if a business is sold to someone that the broker negotiated with while the agreement was active and within two years of the brokerage agreement being terminated. I personally set my “tail” at 12 to 18 months in most of my agreements.
Vendor Take Back (VTB): A VTB is a finance term describing the fact that a seller has been willing to forgo getting paid all of the purchase price up front and will take a “note” for part of the purchase price. VTBs generally range in size from 15 to 30 per cent of the total purchase price and often attract some interest and are paid out over two to four years. VTBs are used by the seller to help close the gap between what a buyer and seller think the company is worth or to help close a deal where the seller knows the buyer cannot come up with 100 per cent of the purchase price and the buyer’s bank will not cover all the difference. Agreeing to a VTB usually indicates the seller has confidence in and trusts the buyer.
It helps to know these standard M&A terms if you are a seller. These are just some. More to come!
Victor Harding is the principal of Harding Security Services (victor@hardingsecurity.ca).
By Patrick Straw
After a successful Quebec show, we’re heading to Richmond, B.C., for Security Canada West
This year the Canadian Security Association is ramping up to include all of our pre-COVID activities across Canada.
Keep an eye on www.canasa.org for updates on our bulletin board.
A huge thank-you to our colleagues in Quebec after the very successful completion of Security Canada East in Laval in April.

Steve Basnett, director of shows and events, working with Danielle Paquin, director of all things Quebec, put on an outstanding trade show followed by a soldout dinner and gala in the evening. We were pleased to be able to honour many companies from the Quebec Region who have been great members and contributors for decades.
Our next Security Canada Conference and Exposition is in Richmond, B.C., on June 22, followed by a joint golf event on June 23 with our friends at the ASIS B.C. Chapter. Registration for both is available now, so please make sure to check them out on our website and we hope to see you there. If you have any questions, please reach out to me at pstraw@canasa.org.
We are excited to be able to put on a full slate of golf tournaments this year, working with our Regional Councils. Details for all of these events are as follows:
• Golf British Columbia – June 23, Mayfair Lakes Golf and Country Club, Richmond, B.C.
• Golf Central Ontario – July 12, Station Creek Golf Club, Stouffville, Ont.
• Golf Alberta – July 19, Alberta Springs Golf Resort, Red Deer, Alta.
• Golf Southwestern Ontario – July 28, Pine Knot Golf Club, Dorchester, Ont.

• Golf Prairie Region – Aug. 2, Glendale Golf and Country Club, Winnipeg, Man.
• Golf Eastern Ontario – Aug. 11, Pineview Municipal Golf Club, Ottawa, Ont.
• Golf Golden Horseshoe Region – Sept. 15, Willow Valley Golf Course, Hamilton, Ont.
• Golf Quebec – Golf and Bike Event, Sept. 21, Parcours du Cerf, Longueuil, Que.
We are hoping to see as many of our members as possible at these events. Details and registration links are easy to find on our website.
Thank you to all of the incredible volunteers from across Canada who work with our staff to make these events a success. Stay tuned as we are planning several social activities across the country and we will be posting these soon. Have a safe and prosperous summer and hopefully everyone will have a chance to relax after a stressful couple of years.
Patrick Straw is the executive director of CANASA (www.canasa.org).
Experience industry-leading trade shows with cutting-edge technology, unparalleled education and the most powerful networking opportunities you’ll get all year.


West Richmond, British Columbia June 22, 2022
Toronto, Ontario
October 19 – 20,

By Colin Bodbyl

WCollection and storage of potentially personal data is governed by some strict rules you should understand
ith the increasing popularity of software as a service (SaaS) in video surveillance, one often overlooked question users should be asking themselves is where that data is being stored.
Despite the name, even cloud services have physical servers storing user data somewhere in the world. The physical or geographical location where that data is stored is called data residency.
“Video surveillance companies need to understand the impact of data residency.”
If you are part of a company that is developing its own software and running it on a cloud service like Microsoft Azure or Amazon Web Services, you likely know which data centre is storing your information and where it is located. On the other hand, if you are part of a company that is using a SaaS or hosted solutions where you pay to use a web-based software or portal, it is usually less clear where your data resides.
This might sound concerning, but Canada has in place the Personal Information Protection and Electronic Documents Act (PIPEDA) to govern how commercial businesses collect, use and disclose personal information. PIPEDA does not restrict the transfer of personal data outside the country, but it does allow the government to hold organizations accountable for the protection of personal information, including when transferred to foreign businesses.
The question then becomes, is video surveillance footage protected under the laws of data residency in Canada? The answer is yes. Video surveillance footage that captures any information about an identifiable individual is subject to privacy laws in Canada. This is not restricted to recorded video and includes live streaming to remote locations.
While a lot of surveillance cameras capture data that would not be considered personal, the improvements in resolution along with new uses of surveillance cameras has complicated the matter. Today, a high-resolution camera could easily capture an identifiable image of an individual from hundreds of feet away. In addi-
tion, surveillance cameras are now being used to capture the behaviour of individuals, like where they walk, or what products they buy.
The most invasive and personal of all surveillance products is facial recognition. In the past, this technology required a camera to be positioned at close range in front of a user’s face, but today even discreet cameras can be used for facial recognition.
Video surveillance companies need to be careful to follow data residency laws, and particularly careful when transferring that video out of the country. Fortunately, there are a few things companies can do to limit their risk and better protect client data.
Signage is a simple and effective way to make the public aware that they are being monitored by a surveillance system. Respect the privacy of those individuals and provide them with answers, including access to footage where they were captured on camera.
access
video and educate those who have access on privacy laws. In addition, formal policies should be in place for those who do have access, and they should be educated on the importance of protecting individuals’ privacy.
Data residency is a complicated and often times confusing topic. The complexity only increases when using cloud or SaaS products where the location of that data is sometimes unclear.
Fortunately, there are some simple steps businesses can take to minimize their risk. As more software moves offsite and into the cloud, video surveillance companies need to understand the impact of data residency, and their responsibility in protecting the privacy of not only their customers, but the people captured on those systems.
Colin Bodbyl is the chief technology officer of Stealth Monitoring
(www.stealthmonitoring.com).

You acquired a security company or expanded into the alarm industry
Your business is a growing concern and you need cash flow to fund your growth
You need support when loading and servicing alarm customers
You need access to quality security products, reliable suppliers and dealer pricing
Your current dealer program is limiting your growth
You need stable and predictable funding
You need to invest in inventory, staff and marketing
You want access to new lines of business
You’ve built a successful business and now it’s time to reap the benefits of your hard work
You need to turn equity into cash for life’s special moments
You need to remove administrative headaches (billing, collections)
You need stable and predictable cash flow but retain ownership of your business
You’re ready to live your dreams
You need to maximize your payout
You have a time-line and you need an experienced buyer who will navigate a smooth transition to the finish line
Your customers need world class monitoring with continuing service and support






Technicians armed with equal parts physical and networking knowledge may be a rare breed today, but training and college courses could help to fill that gap
By Madalene Arias

The demand for skilled technicians in the world of alarm services remains high, and so too does the difficulty in finding the right people with the right skillsets to replenish this side of the industry.
Professional recruiters like Stanley Owah of Classic Fire + Life Safety say that taking the time to engage with schools and educate students on the career possibilities of a particular field or trade can prove useful to attracting new talent to an industry.
In April, the company, which operates offices in Ontario and Manitoba, announced the successful recruitment of 60 new candidates.
Owah explained that even in an “in-demand” industry, recruitment still presents some challenges.
“When it comes to the job market nowadays, it’s a little bit tight. It’s uncertain. A lot of people are looking for job security,” says Owah. “We don’t know what the future brings.”
However, the company offers good employee benefits, and Owah says this fact alone has been instrumental in attracting new candidates.
Additionally, Classic Fire + Life Safety invests time in educating students, or workers with some experience, on how they can pursue a career in a particular trade as a way of simplifying this process for them.
Owah says that the company maintains this level of engagement with potential candidates even if it is not looking to fill new positions.
“I think a lot of candidates actually appreciate that, especially the skilled applicants.”
The value of engagement with students and graduates is not lost on the security industry.
The Canadian Security Association (CANASA) has partnered with educational institutions in Ontario like Centennial and Conestoga colleges to provide a bridge between the needs of the security industry and new technicians as they move into the field of alarms or add alarm installation to their repertoire.
Leaders in this sector who have seen changes in the industry over decades applaud CANASA’s initiatives with post-secondary institutions.
At the same time, these veterans have not shied away from identifying potential reasons for the talent shortage, including advances in technology, the cost of doing business, changing attitudes towards work, and the way security

careers are perceived generally by society.
Before diving into these factors, it is important to define the ideal applicant for a security/alarm technician who meets the needs of today’s clientele.
modern alarm technician
A suitable candidate for this role possesses a strong IT background and enough comfort with a toolbox for the physical installation of an alarm system. This means they can run wires, drill holes, and leave the client with a fully operating
system in minimal time, according to Stuart Armour, sales operations manager at Affordable Security Systems, based in Burnaby, B.C.
The ideal technician would also demonstrate the same level of ef ficiency behind a computer screen to program surveillance cameras, which is what present-day installa tion entails according to Don Con nor, regional manager at Vipond Systems Group in Toronto.
The industry wants someone who is “IT savvy with a little bit of ‘I don’t mind getting dirty,’” in Connor’s words.
“We’re looking for a high level of IT competence,” he adds. “We’re looking for people that have a good understanding of IP systems.”
Armour says there is a rift be tween the skillsets required for this kind of work. There are people em ployed in the security sector who are comfortable with the physical aspect of installations but may lack the technical requirements of the role such as networking.
“It’s really hard to find some one who is well-rounded,” says Armour, “You almost end up with two teams because it’s really hard to find a technician who is really good with both.”
Over the years, security technology has switched over to IP-based sys tems, which introduced an overlap of services from the telecommuni cations and IT sectors with those offered by the alarm and security industries.
Large telecommunications companies can afford to bundle their services to offset the cost of installations, making it difficult for smaller and medium-sized alarm companies to charge reasonably for this service, claims Armour.
“If you’re installing this stuff for free, it’s really hard to attract a technician at a good rate of pay be cause you’re not making any mon ey on the work,” he says.
Armour also says this shift to digital is partly to blame for the talent gap among alarm systems technicians. As networking became integral to most alarm installa tions, it was not necessarily incor porated into the knowledge base of technicians entering the field.

You asked us for a new mortise strike that combines the high quality of European brands with a new level of flexibility performance and value. We answered with our new 1500 Series dual monitor and low profile strikes!

Back to school
Jo Booth, senior manager at Centennial College’s Centre for Part-time and Online Learning in Toronto, says the college has built a relationship with CANASA spanning at least 10 years.
“The relationship began when CANASA was looking to transition their old, pretty basic courses into an online modality,” Booth explains.
Currently, Centennial College offers an Alarm Technician course through online, distance learning in both English and French.
The program allows learners eight weeks to complete the course material according to their own preferred schedule as many of them typically work 10- to 12-hour days.
The course covers a range of topics including basic networking, system design, field wiring, power and grounding, wireless, safety, metering and false alarm management.
“In the last 18 months, we’ve updated the course and combined things to make it more friendly for the learner and make it more of an active experience,” says Booth.
Centennial’s course is not for absolute beginners. The college recommends this course for technicians who have previously installed at least three intrusion alarm systems. They must also
possess a basic understanding of electronics and mathematics to qualify.
Booth says that their program enrollments currently average 15 to 20 students for every eight-week period.
“We’re looking for people that have a good understanding of IP systems.”
— Don Connor,Vipond Systems Group
For the very first time, Conestoga College, in Kitchener, Ont., is offering an entry-level Alarm Systems certificate program, also affiliated with CANASA.
Although the college hoped to launch the program in the spring of 2022, there was not enough enrollment to move ahead with the courses for the semester.
“I think a part of it is the timing. Not as many people are looking to take courses in the spring and summer,” says Brea Medeiros, man-
ager of continuing education at Conestoga College. “But naturally, a lot of students are looking to come in the fall.”
Conestoga’s program is designed to prepare students for careers in surveillance and investigations, alarm product and distribution sales or as representatives for manufacturers.
The college allows students a maximum of three years to complete all course material which includes systems integration, intrusion alarms and surveillance cameras and basic installation techniques.
Medeiros says the college has worked to market this program to high school students. She anticipates enrolment will increase once more people begin to understand the demand for alarm technicians as well as the different career routes that exist within this field.
“I think it’s a great opportunity for students, especially when we see the connection to the career field through CANASA’s support,” she said. “It’s almost like a little bit of a best kept secret right now.”
A shift in perception
Connor also believes that people outside of the industry may not have a very good grasp of how much career diversity exists within the





security sector.
Much of the general public’s understanding of security work is restricted to guard ser-
vices as they have the most public facing roles. Furthermore, unflattering pop culture depictions of security guards and unrealistic por-
trayals of security systems in film and TV have not helped the industry’s image.
“I always like the one where the guy comes in with the spray kit and sprays over the security cameras so they can’t see,” says Connor.
Connor says he thinks the public doesn’t understand the complexity of the security industry nor the challenges and the interest it can generate.
He specifically notes changes in the area of CCTV within the last decade. According to a report from Market Research Future, the industry is projected to be worth more than $46.52 billion by 2030.
According to Armour, who also sits on CANASA’s National Board of Directors and National Executive Committee, the association provides at least one scholarship to each of the three or four colleges in each province that offer an education for the security industry.
He says that CANASA’s involvement with Ontario colleges like Conestoga and Centennial is a step in the right direction, and he anticipates the collaboration will prove fruitful given the province’s population.
“Within the next 10 years, if you have any type of technical skills, you’re going to be worth your weight in gold,” says Armour.


Why ICT’s unified platform means you no longer need a separate system to control door interlocking.
by Pat Alvaro

Historically, sites have required additional systems to enable door interlocking, which weren’t easily integrated with the on-premises access control. But with this feature built into ICT’s Protege platform, it’s easy to use door interlocking as part of a unified access control and building automation solution.
These days interlocks are used across many industries including pharmaceutical clean rooms, correctional facilities, wildlife enclosures, and data centers. While interlocks at a zoo are designed to keep animals inside their enclosures, other environments use them to keep people or objects outside, such as restricting access to authorized users in areas at a data center, or as a safe, intermediary space to make sure weapons and other contraband stay out of prisons.
Door interlocking really comes into its own when it’s part of an integrated platform. And unlike other manufacturers, ICT’s door interlocking solution means no additional software is required, and can be configured in just a few short steps.
It’s simple to combine the interlocks with two-factor authentication if increased security is required. You can incorporate building automation so that HVAC or lighting functions are triggered when an interlock is opened.
Pharmaceuticals and cannabis are two growth industries in North America worth highlighting for their unique security and environmental control requirements – both of which can benefit from an integrated door interlocking solution.
Since it’s legalization in 2018, most people would be aware of the staggering growth of the cannabis industry. Canadian figures are expected to grow from $5.5B this year to $8.8B in 2027. Clean rooms are also a booming industry, with the North American pharmaceutical clean room market expected to grow by 7.2% annually for the next 6 years, according to The Insight Partners.
Pharmaceutical clean rooms (or other locations such as research facilities and laboratories) often require environmentally controlled rooms to prevent contamination and ensure the integrity of any work being carried out. A small corridor and two airtight doors separate the room from other areas. Sensors check that pressure

or temperature levels are correct before allowing the door to unlock, while door interlocks prevent both doors from being unlocked simultaneously.
While commercial cannabis operations also maintain controlled environments for optimal growth, they are also subject to very specific security and reporting requirements. Door interlocking denies access until the interlocked door is sealed, but the integrated technology can also help provide an additional level of support with compliance types.
Not only can you control access based on access levels, but you can also use compliance types to ensure the person trying to enter a restricted area has the appropriate current training and certification. As well as restricting access to those that are certified you also gain an extra layer of reporting to show that the cleanroom was always in compliance.

ICT’s unified access control, intruder detection, and building automation solutions mean that door interlocking has moved from simple containment to part of a multi-functional system that is increasingly safe, automated, and accountable.
To find out more about door interlocking as part of an ICT solution, visit info.ict.co/spt-interlocking
Pat Alvaro is Country Manager, Canada at ICT (www.ict.co)

Secure hazards such as grow rooms or pharmaceutical cleanrooms with ease. ICT’s unified solution means you no longer need a separate system to control door interlocking. As a built-in feature in the Protege platform, door interlocking can be setup in just a few simple steps. Combine interlocks with two-factor authentication for increased security, or incorporate building automation to include HVAC or lighting functionality.

By Ian Holmes
How can organizations create safe working environments that people actually want to visit?
For many, visitor management systems are the answer. Visitor management systems are becoming ever more commonplace as part of facility management strategies for government buildings, workplaces, schools and medical facilities. When combined with self-service technology, these systems become an important first step in a visitor’s journey, offering a pleasant and frictionless experience for customers, contractors and employees.
Yesterday’s reception areas ran entirely on human power. A visitor would enter the building and head to security or a welcome desk, where they told the attendant or receptionist the purpose of their visit while providing identification. That attendant would then verify the visitor with the building occupant and type the visitor’s information into the system to create a visitor pass.
Unfortunately, humans are prone to error. Information can be keyed incorrectly, the building employee could be hard to find, and the visit may be unexpected. With the possibility of dozens of visitors arriving at once, each needing access to different areas to connect with different people, a receptionist or security attendant could become overwhelmed.
In addition, they’re not only expected to be on top of the visitor schedules, but also be able to spot fraudulent IDs from different states, provinces and countries. It’s easy to see how an individual could be granted access to the wrong area or allowed to enter somewhere that should be restricted to vetted employees and contractors.
Automating for a warm (and secure) welcome
On the other hand, an automated visitor system virtually eliminates user error, establishing a more secure building for visitors and staff alike. Sophisticated self-service systems allow visitors to register themselves at multiple kiosks rather than waiting for a security attendant. Modern
self-service kiosks often feature a document reader that simply scans a credential verifying their visit and, depending on the level of security needed, scans their identification. Removing the task of manually entering information into a security system speeds up the registration process while leaving reception and security staff free to better cater to the needs of visitors and staff alike.
credentials
What we refer to as “credentials” are typically either a document, card or data token issued to an individual by a third party that grants them access to the premises while on site. These credentials can include a visitor badge, printed or digital QR code (2D barcode), a radio frequen-
cy identification card or government-issued IDs such as passports or driving licences. Following a visitor’s registration, either online or at the point of entry, one or more of these credentials or tokens can be used by an individual while navigating the building. This includes a final check-out before leaving the site — a crucial last step for fire safety and contact tracing purposes. For more secure applications in data centres, schools or government buildings, government-issued IDs can also be used to enroll a visitor before providing them with access to secure areas on-premises.
Let’s take a closer look at the common types of credentials that a visitor management system can process (see chart above).






Once a visitor has registered and has been issued a credential, that data token or ID document needs to be read by a device at a point of entry. These readers are usually positioned on a reception desk or fitted to an unattended self-service kiosk alongside other peripherals for printing badges or issuing access cards.
Readers are often connected via USB to a host PC with the visitor management or access control software running locally.
Embedded computing and Internet of Things (IoT) technology allow highly capable devices to communicate directly with a server or cloud service via a local area network for easy deployment and integration. IoT-ready devices are widely used today in airports and on public transport networks to improve passenger flow and experience.
The best visitor management systems are capable of accepting whichever credential an organization is currently using. For example, a building with multiple tenants may have multiple security systems.
In one company, the internal person attaches a QR code to the meeting invite; when the visitor arrives, they’ll scan that code at the kiosk. Meanwhile, another may simply request a visitor arrive, register on the enrolment kiosk and scan their driver’s licence or national ID card.
Security requirements can also be dependent on the type of visitor. After all, a person attending an interview poses a much lower threat to an organization than a contractor, so the credentials they are required to provide at entry should reflect this.
In this case, an organization may wish to issue the prospective employee a temporary barcode to be read from their phone or a printout
“The systems used to manage the multitude of individuals attending a site need to be as flexible and dynamic as the organizations deploying them.”
when they arrive on site. However, as the contractor will have access to secure areas, it would be prudent to enroll them using their government-issued ID. Ideally, both the temporary barcode and government ID can be read and verified on the same device.
Organizations can use multi-modal devices to read identity documents and automatically capture personal data, barcodes and high-resolution images of the presented ID.
An example is the HID ATOM ADR300 multi-illumination electronic machine-readable travel document reader. It employs optical character recognition technology to automatically read personal data such as the holder’s name, document number and address from the ID and output it to the visitor management system. This data can then be used to enroll a new visitor or cross-check against a list of pre-registered visitors or employees.
Images of an ID captured using multiple wavelengths of light (white, infrared and ultraviolet) to expose the printed visible and invisible security features can be used to complete automatic authentication.
A wide range of authentication techniques is used to determine whether the document is genuine or not, including the detection of optically variable inks, UV pattern matching, and cross-checking of personal data in the ma-
chine-readable zone, visual inspection zone and biometric chip.
For further assurance in self-service or partially attended applications, a facial image extracted from the document data page or biometric chip can be used to complete a 1-to-1 face match with a live image of the document holder to ensure the visitor is who they report to be.
This ability to read different national IDs, barcodes, RFID cards and even EU Digital COVID Certificates on a single device allows a visitor management system to accommodate a much wider range of visitors.
The future of visitor management starts now
The world is becoming ever more connected due to global trade and cultural exchange. As a result, organizations and workplaces are transforming from national to international entities at an unprecedented rate.
The systems used to manage the multitude of individuals attending a site need to be as flexible and dynamic as the organizations deploying them. The use of multi-modal devices provides a simple, single touchpoint for all types of visitors across an entire global organization for a safer — and simpler — world.
Ian Holmes is a business development manager for identity and security at Access IS, an HID Global company (www.hidglobal.com).


The tools have evolved to provide more reliable protection for critical infrastructure
By Kai Moncino
Video analytics are an essential tool for perimeter security operations.
Motion-based as well as artificial intelligence (AI) and machine learning-enabled intrusion detection technologies have seen widespread adoption across airports, oil and gas facilities and other critical infrastructure locations throughout Canada. Today, new improvements are enhancing the classification accuracy of video analytics, enabling faster threat recognition and earlier intervention for crime deterrence.
For the first few decades of its implementation, analogue video cameras were the primary technology used to surveil facilities. These devices gave security personnel the ability to monitor an area to serve as an additional tool to on-site security guards.
In the early 2000s, the introduction of video analytics created a paradigm shift in the secu-
rity industry. This technology used pixel-motion-based detection that triggered alarms based on a percentage of pixels that changed on a screen within defined borders; this enabled personnel to run motion detection algorithms using onboard hardware to expand the functionality of analogue video cameras.
No longer did an enterprise need to rely on the eyes of a security guard to catch suspicious activity — perimeter systems outfitted with video analytics could still deliver automated, instantaneous detection alerts. This ultimately increased the efficiency of monitoring and video operations, but common sources of motion such as wind-blown foliage and small animals oftentimes overwhelmed security operators with more false alarms than they could handle.
Today, security directors require more from their perimeter intrusion detection systems (PIDS). As threats to critical infrastructure have evolved, it is no longer enough to detect movement at the perimeter. Security managers require analytics that reliably detect and classify an intruder, determine its location, and eliminate most false positives. Convolutional neural networks (CNN)-based analytics is an emerging technology that directly addresses this need. Built to replicate neurobiological systems to
detect and classify objects in an image, convolutional systems rely on object classification to detect, classify and track a potential threat, improving video analytics precision, classification accuracy, geolocation of targets and resilience against false alarms.
To accomplish this, development engineers manually analyze thousands of images to determine the location and classification of interesting objects and train the CNN model on what is noteworthy and what should be ignored. While some CNN-based systems use public datasets to develop its classification capabilities, industry-leading CNN-based video analytics systems use datasets that are curated for specific security applications to reduce false alarms and maximize detection rate.
Alarm
One of the most valuable advantages of CNN-based video analytics is their ability to reduce false alarms. Because CNN analytics do not use motion for input, they are less prone to sources of noise such as swaying foliage, camera shake and animals moving across the frame. By the numbers, CNNbased analytics have been shown to reduce false alarms by as much as 60 per cent, in a sample of 100 unique scenarios.
Robust Classification: Beyond false alarm reduction, CNN-based video analytics draw from libraries of thousands of images to deliver intelligent and informed intrusion detection alerts. Not only have these systems been tested to detect 15 per cent more threats than motion-based analytics in a sample of 100 unique scenarios, but they also improve on motion-based systems by classifying threats that may be slightly obscured or challenging to identify. Because CNN-based video analytics do require more pixels on target than motion-based analytics, they are limited to approximately 20 per cent shorter classification ranges compared to motion-based analytics. This must be accounted for when designing the perimeter security solution and can be compensated for by selecting narrower lenses than with the equivalent motion-based analytic camera.
For any of Canada’s critical infrastructure — whether an airport, an oil refinery, a data centre, or a power plant — CNN-based video analytics offer several benefits for perimeter protection and operational efficiency. To help understand the applications CNN-based video analytics would perform well in, explore the following use case examples:
Airports: For airports whose tarmacs are high-traffic areas, such as the Toronto Pearson International Airport, which served a total of 50,499,431 passengers in 2019, intruder classification and false alarm reduction along the perimeter is indispensable. CNN-based video analytics represent a turnkey solution for large airports, where reducing surveillance video noise can allow security personnel to focus energy and resources on priority alerts.
Oil & gas refinery: With the third-largest oil reserves in the world, Canada’s oil and gas facilities house assets vital to producing energy. From the oil well to the refinery, CNN-based video analytics empower securi-
ty personnel to provide greater detection and classification accuracy in every environment, accurate target tracking, and expanded situational awareness.
Substations: As reported by CIGRE, 88 per cent of substations experience at least one break-in every year. For electrical utilities whose rural substations may have no full-time security staff on-site, accurate classification can be the difference between a preventable perimeter intrusion and a prevented one. CNN-based video analytics enable security personnel, on- or off-site, to alert first responders and inform the best possible response.
Data centres: In 2021, the global cloud data centre traffic grew to 20.6 zettabytes (ZB), according to Cisco. That same year, Cisco expected to witness the number of hyperscale data centres grow from 228 in 2016 to 628. As more industries migrate their highly sensitive data to data centres, data centre perimeter security has become more important than ever. CNN-based video analytics allow data centre security personnel to expand their situational awareness, and in turn, sharpen perimeter security responsiveness.
Regardless of the perimeter, fewer false alarms, greater detection and classification accuracy, expanded situational awareness and novel abilities to track and respond to intruders in real time delivers security personnel an invaluable tool. Designed for continuous evolution, CNNbased analytics are built to keep pace with future technological developments and ever-evolving threats, establishing them as a solution that is truly future-proofed.
Kai Moncino is the director of global business development, security at Teledyne FLIR (www.flir.ca)



The BEST Precision Visual Indicator 2110 is a code compliant safe egress with visual and directional indicators for security lockdown. This panic device incorporates the ANSI “10” function, also referred to as the “Intruder Function,” with new lock/unlock status. A directional indicator is integrated into the housing and contains reflective materials that may be seen in low light conditions. It also features an embossed directional indicator that offers quarter-turn (90°) activation to enable faster lock down.

The SN Series integrated wired locks from ASSA ABLOY brands Corbin Russwin and SARGENT offer a choice of Wiegand communication protocol or Open Supervised Device Protocol that allows for secure channel, serial communication between the reader and Physical Access Control System. Featuring Signo reader technology from HID Global, the SN Series is suited for mixed credential environments and enables migration to higher security credentials and mobile access. www.assaabloy.com
Alarm.com has released three new readers for smarter access control, featuring support for encrypted credentials, as well as mobile access credentials. With the new readers, Alarm.com for Business customers can now use their smartphones to unlock doors instead of using a separate badge or key fob. Readers are available in mullion, single gang and keypad form factors. www.alarm.com



Alvarado’s SU5000 Swinging Barrier Optical Turnstile features bi-directional motorized access control in conjunction with a facility’s access control system. To enter, users present a valid credential which opens the turnstile’s motorized barriers away from the user. If a user attempts to tailgate on a valid entry or attempts to enter without authorization, the integrated sensors recognize the illegal passage attempt and sound an alarm. www.alvaradomfg.com

































































































































































































Additions to GARDiS v2.3 integrated Access Management software solution include: universal decode/auto detect, support for RS485 readers, generation of FILO (First In Last Out) reports, an extended door lockdown feature, a data Fusion and Exporter function, support for Access Control Units (ACU) inconsistency, automated emailing of reports, and bespoke badge design and printing.
www.tdsi.co.uk

IDEMIA
With MorphoWave, users wave their hands in an easy gesture to have their four fingerprints 3D-scanned and verified in less than one second. MorphoWave XP X-tended Performance provides a 20% increase in performance compared with the previous generation. It accommodates demanding deployments with up to 60 users per minute and up to 100,000 user records. MorphoWave SP Simplified Profile accommodates smaller installations with less demanding requirements with up to 40 users per minute and up to 10,000 user records. Both versions leverage the plug & play features of Compact, including software integrations with leading access control platforms.
www.idemia.com
Suprema launched four models of X-Station 2, a next-generation “versatile intelligent terminal” that supports a variety of authentication methods from mobile access cards to RFID cards, QR codes and barcodes. The newest X-Station 2 model comes equipped with a fingerprint recognition module. Features of X-Station 2 include: fraud prevention via authentication photos using a built-in camera; a four-inch touch screen; up to 500,000 users can be stored and processed.

www.supremainc.com

The Nice Soon Pro is a commercial door operator engineered to provide professional installers with an all-in-one control unit solution that contains features that optimize customer door operation, like LED lighting and optional battery backup. The Nice Soon Pro CDO is designed for sectional doors up to 16 feet high with lighter duty cycles (up to 25 cycles per day) and measures 4.5 inches wide. www.nortekcontrol.com

The HES KS210 wired swing-handle server cabinet lock integrates with existing electronic access control systems to protect critical assets against intrusion and costly downtime. Standard features include RS-485 OSDP communication and an integrated HID mobile access enabled multiCLASS SE RFID card reader with Bluetooth option.
www.assaabloyesh.com

The Schlage Encode Plus Smart WiFi Deadbolt is among the first to support Apple’s latest enhancement to the HomeKit experience. With home keys in Apple Wallet, consumers can tap to unlock the Schlage Encode Plus deadbolt using their iPhone and Apple Watch for access to their home. With a Schlage Home Key in Apple Wallet, homeowners don’t even need to unlock their iPhone or Apple Watch to open their lock, and with Power Reserve (supported on iPhone XS or later and Apple Watch Series 4 running watchOS 8 or later), even if the iPhone needs to be charged, they may still be able to tap to unlock for up to five hours after their iPhone battery runs out. Additionally, the lock is also fully supported by the Schlage Home app. The Schlage Encode Plus Smart WiFi Deadbolt will be available for purchase in the Canadian market this summer and will retail for approximately $379. www.schlage.ca
Matrix COSEC ATOM RD100K features a minimalist installation process and integrates with the existing system. With its third-party integration via Wiegand interface, it can be used to expand and update the existing infrastructure. With its multi-credential and multi-interface, Matrix COSEC ATOM RD100K optimizes security in the workspace, according to the company. Key features include: multi-credential support (RFID Card & Mobile authentication); multiple interfaces (Wiegand, RS232, Exit Switch Interface, Door Lock Relay); certified protection against ingress and vandalism; and third-party integration. www.matrixcomsec.com

Abloy Oy
ABLOY CUMULUS is a platform for keyless access, combining hardware products with secure access and management applica tions. CUMULUS provides secure access in commercial real estate, public spaces, housing and other sites. It of fers interfaces for third-party applications and software development. The CUMULUS range of keyless, online access solutions — from mobile keys and padlocks to upcoming electric locks and controllers — can be administered with any software tool that suits the customers’ needs. By selecting ABLOY OS INCEDO, the organization can also manage other ABLOY solutions with the same tool, such as electromechanical PROTEC2 CLIQ and mechanical keys. www.abloy.com


i-PRO
i-PRO Americas announced the launch of its new 4K Panoramic Front Camera for police vehicles, the WV-VCF41P. A component of i-PRO’s ICV4000 in-car video (ICV) system, the new camera is suited for law enforcement agencies seeking wide-angle coverage and high-resolution capture of video evidence from the vehi-
A comprehensive, integration-friendly solution for mass communication, AtlasIED’s IPX Family integrates with all VoIP systems as an SIP device, enhancing a facility’s existing communications platform with the addition of IP-enabled speakers and visual displays. Using a facility’s existing IT infrastructure, IPX offers a way to quickly and reliably dispatch audible and visual emergency notifications and provide routine communications and paging, even in noisy environments. www.atlasied.com

Designed to protect smoke detectors against vandalism and accidental damage, the STI Steel Web


Cobalt Robotics announced enterprise mobile video chat. Now enterprises can connect staff and visitors with a live employee from their organization or security team first with backup from Cobalt’s Command Center, through real-time video on the robot wherever the robot is patrolling. Enterprise mobile video chat en-


TandemVu PTZ Cameras with ColorVu technology monitor wide-area observation and provide detailed images simultaneously. The new TandemVu PTZ Cameras integrate a 4 MP fixed bullet camera with a 4mm lens and a high-performance 4 MP PTZ camera in a single unit. Available with either a 32x optical zoom (DS-2SE7C432MWAEB 14F1) or 42x optical zoom (DS-2SF8C442MXS-DLW 14F1), TandemVu PTZ Cameras are equipped with strobe lights and an audio alarm speaker. www.hikvision.com

The M-8080D Digital Matrix Mixer series is dedicated to commercial and professional audio applications. The M-8080D offers software driven signal processing with extended remote controller options. The powerful onboard DSP provides a full set of audio processing functions while maintaining the versatility to operate in a broad range of system requirements. The M-8080D possesses 8 analogue inputs x 8 analogue outputs, along with an additional 4 digital inputs x 4 digital outputs. DSP functions for mic and line inputs include compressor, ducking and feedback compression. There is also a 5 band EQ (LPF and HPF) for IN and 8 band EQ (LPF and HPF) for OUT.
www.toacanada.com

The new MMZB-21.5G-X Medical displays feature a 21.5” screen with 1920 x 1080 Full HD resolution, wide viewing angles and 350 nits brightness. These models are certified to the latest UL and IEC 60601-1-2 standards. They offer a variety of digital video inputs (HDMI, DVI, DisplayPort), as well as an optional touch screen. Their Zero-Bezel enclosure features a single sheet of glass covering the entire front of the display. These 21.5” Medical Grade monitors are suited for use in hospitals, urgent care centres, and military field hospitals. www.tru-vumonitors.com
C2G’s Thunderbolt 4 USB-C Cable delivers up to 40Gbps to or from a Thunderbolt 3- or Thunderbolt 4-enabled port. It’s a solution for transferring large amounts of information in a very short amount of time. For example, it’s capable of transferring a 5GB file in about a second. It can connect to a high-speed 10 Gigabit Ethernet network or connect two computers over a peer-to-peer network, allowing for the transfer of large volumes of data. www.cablestogo.com


The FLIR RS6780 long-range radiometric infrared camera system is designed for range tracking, target signature, outdoor testing, and science applications in all conditions. Featuring continuous zoom, the camera includes an integrated motorized three-position filter wheel and optional factory calibrations to support thermography applications up to 3000°C. The optional 3x zoom afocal lens attachment provides engineers and scientists the flexibility to change the focal range from the standard 50mm–250mm to up to 150 mm–750 mm. The advanced lens system provides instantaneous, frame-byframe focal position information to enable factory or custom calibrations for thermography and radiometry applications.
www.flir.ca

VIGIL TRENDS incorporates point-of-sale (POS) data, exception-based reporting (EBR), and video. VIGIL TRENDS takes customer POS data (preferably from a central data location) and analyzes the data for customer defined key performance indicators (KPI) to produce exceptions. These exceptions are given a “weight” and displayed via a dashboard displaying employees high scores. In essence, opportunities for corrective action are “bubbled up” to the surface. Employee scores contain specific POS transactions that can be married to video and POS data, allowing for quick review and analysis. www.3xlogic.com

VuWall is launching the Application Server, an appliance for streaming, sharing, controlling and visualizing websites and applications across AV/IT networks. The Application Server is a scalable solution that simplifies video wall deployments by providing quick access to websites, dashboards and applications from a single, centralized source. Centralizing web browser and application deployments in a single appliance eliminates loading times and alleviates processing power from the video wall itself. www.vuwall.com
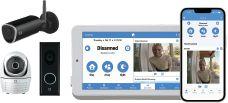
Alula’s video platform features new camera models, AI-based object detection, enhancements to video clip navigation and viewing in the Alula Smart Security App and advanced video capabilities through the new Slimline Touchpad PRO. Three new cameras have been added: an outdoor bullet, a smart doorbell camera and the Indoor 360, featuring responsive pan-tilt operation. All three cameras deliver a high-definition viewing experience, motion detection, extended Wi-Fi range and night vision. With Alula’s Smart Security App, individual camera settings can be adjusted so that system notifications are sent to system users when specific motion activity occurs. App enhancements for navigating stored video clips make it easier for users to find and view clips.
www.alula.com

Qognify VMS combines the core of an enterprise-class VMS with added values such as business process support, advanced ecosystem integrations and cloud readiness. Qognify VMS offers the possibility to store video data in the cloud, enabling customers to keep the hardware footprint small, scale storage space quickly, and benefit from the resiliency of cloud technology. To make on-premise deployments as easy as possible, a wide range of turnkey hardware solutions is available for Qognify VMS. www.qognify.com
The FE9192-H recessed fisheye network camera features a 12-megapixel resolution sensor with a diameter of 82mm. It is equipped with a fisheye lens for 360 degree surround view with no blind spots. The recessed mount design enables discrete surveillance of indoor spaces.

The FE9192-H comes equipped with VIVOTEK’s Smart VCA (Video Content Analysis). With AI-based deep-learning and Smart Motion Detection, Smart VCA will enable users to detect event triggers such as intrusion detection and missing object alerts. www.vivotek.com
Potter announces the Integrated Voice System along with the IPA-4000V and AFC-1000V fire alarm control panels. The Integrated Voice System can be used to address multiple site requirements for the AFC-1000V and IPA-4000V, with capacity including up to 104 programmable push buttons, 31 total system amplifiers, 248 speaker circuits, and remote system control. www.pottersignal.com


The GRP corrosion resistant GNEx and the stainless steel STEx alarm sounder families have been further extended. The new GNExS2H and STExS2H generate a maximum sound output level of 127dB(A) at 1 meter. The other main variants are the GNExS1F and STExS1F short flare horn versions producing up to 115dB(A) SPL with a maximum current consumption of only 221mA and the GNExS1R and STExS1R compact omnidirectional radial horn versions with a SPL of up to 113dB(A). www.e2s.com



AmpliVox
AmpliVox megaphones, in varying sizes, capabilities, and with special features such as hand-held microphones, have been used by first responders, public safety officials and more. AmpliVox battery-powered megaphones are available in a wide range of models and audience ranges: Mini-Meg 10 watt Megaphone, S600; Mini-Meg 20 watt Megaphone, S601; Mity-Meg 25 watt Megaphone, S602; Mity-Meg Plus Megaphone, S602M; Safety Strobe Megaphone, S604; and Safety Wand Megaphone, S606. www.ampli.com

RealNetworks
SAFR from RealNetworks version 3.8 includes SSL support, updated enterprise capabilities and enhanced usability. SAFR’s AI-powered recognition with liveness detection quickly (within 0.3 seconds) and accurately verifies and displays the name of a matched person. SAFR’s 3.8 release adds the ability to conceal age and gender metadata from the live monitoring tools while continuing to utilize all available metadata when searching event history as part of a forensic investigation. SAFR 3.8 expands enterprise capabilities allowing for total control from a central server. Users can now manage all video feeds in one location as well as manage server configuration on all subsidiary servers. www.SAFR.com

Legrand’s Shading Systems Designer Series of decorative brackets and hembar endcaps are available in a wide range of finishes. Designed to fit 2.6-inch and 3.3-inch universal and open-roll adjustable brackets, the decorative brackets slide on to completely conceal mounting brackets from the outside without interfering with the mounting surface. The Designer Series hembar endcaps offer a redesigned, modern shape. Designer Series decorative brackets and hembar endcaps are available in 15 new finish styles across three collections: Premium, Glass and adorne. www.legrand.com

Hanwha Techwin

Tamron announces the launch of three new models of Ø29mm compact-size fixed-focal lenses for machine vision, compatible with 2/3” imagers and 8-megapixel high resolution — Model MA23F12V (12mm), MA23F16V (16mm), and MA23F50V (50mm). These expand the currently available MA23F series — Model MA23F08V (8mm), MA23F25V (25mm), and MA23F35V (35mm). www.tamron-usa.com
The PNM-C12083RVD supports 15fps image capture and true 120dB WDR (Wide Dynamic Range) without compromising the frame rate for each of its 6MP sensors. Motorized vari-focal lenses offer a focal range of 3.54–6.69mm for flexible field of view adjustment in each direction. Similarly, the new PNMC7083RVD supports 30fps with 120dB WDR for each of its 2MP sensors. The camera’s motorized vari-focal lenses support a range of 3.0–6.0mm.
www.hanwhasecurity.com

Command Centre v8.70 introduces enhancements, including a next-generation integration with HALO Smart Sensor. Able to detect substances in the atmosphere, as well as light, pressure, temperature, humidity and sound, the HALO Smart Sensor integration detects abnormalities such as a gunshot or smoke. V8.70 also delivers enhancements to Command Centre’s Site Plans functionality including a background colour selector. security.gallagher.com
The NAPCO HD video WiFi cameras and doorbell offer features including Night Vision or New Ultra StarLight Night Vision, 2-Way Talk and HD resolution video, up 30fps@2.0MP (1920x 1080). Scan the QR code to enroll and connect to any 2.4GHZ wireless router. Plus, 12 months of cloud-based video storage and access is included. Integrate cameras with New Gemini Security/Video/Access and iSecure Connected Home Alarm Apps, or use Standalone iBridge Video App, to offer accounts access from anywhere, from any smart device. www.napcosecurity.com


Video Mount Products
Video Mount Products, a provider of mounting solutions for the security, commercial, CI, residential, and pro audio/video markets, recently announced its new ERWR Series Fixed Wall Mount Racks. The ERWR8 (8-rack space) and ERWR12 (12-rack space), 18inch deep racks have MSRPs of US$147.95 & US$246.95 (respectively).The new ERWR Series mount virtually any standard 19-inch security, AV, and telecommunications components, according to the company. The ERWR Series features steel construction, a load capacity of 65 pounds, and a durable black powder coat finish. Additional features include: standard 10-32 threading, EIA compliance, and tie down slots in top and bottom side supports. www.videomount.com